Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
The Psychology of Phishing: Unraveling the Success Behind Phishing Attacks and Effective Countermeasures
By Tomer Shloman · February 1, 2024
Phishing is one of the most sneaky and widespread attacks in the constantly changing world of cybersecurity threats. This form of cyber attack, deceiving individuals into revealing sensitive information, has grown far beyond its humble origins of dubious emails from foreign princes. Today, phishing encompasses a range of tactics and techniques aimed at exploiting human psychology rather than technological vulnerabilities.
Defining Phishing
At its core, phishing is a type of social engineering attack where the attacker masquerades as a trustworthy entity to dupe victims into opening an email, message, or link. The goal is to steal sensitive data like login credentials (i.e., credential harvesting), credit card numbers, or to install malware on the victim's system. This deceptive practice can take many forms:
- Email Phishing: The most common form, involving emails crafted to appear legitimate.
- Spear Phishing: Targeted attacks on specific individuals or organizations.
- Whaling: A type of spear phishing that targets high-profile individuals like executives.
- Smishing and Vishing: Phishing conducted through SMS texts (Smishing) or voice calls (Vishing).
- Quishing: Phishing that uses QR codes to deceive victims.
The Relevance of Psychological Understanding
In the realm of traditional cybersecurity, the focus is often placed on technical defenses against attacks. However, the understanding of the psychological underpinnings of phishing is crucial for a multitude of reasons. One significant aspect is the exploitation of human vulnerability. Phishing targets human weaknesses, an element far less predictable than hardware or software vulnerabilities. By understanding the psychological tactics employed by phishers, individuals and organizations can better anticipate and recognize these threats.
Additionally, the evolving nature of phishing attacks plays a crucial role. As phishing techniques become increasingly sophisticated, they often rely more on manipulating emotions and cognitive biases. The ability to recognize these tactics is key to developing more effective training and awareness programs.

Understanding Phishing
Historical Perspective
The term "phishing" first appeared in the mid-1990s, with its spelling influenced by an earlier term, "phreaking," which involves fraudulently using electronic devices to avoid telephone call charges. The evolution of phishing began with early attempts like the AOHell program, developed by a Pennsylvania teen, which used credit-card-stealing mechanisms. The first notable phishing attacks targeted AOL users in 1996, where attackers employed social engineering tactics to impersonate AOL employees and gather sensitive information.
Phishing has since evolved, shifting from simple email scams to more sophisticated methods. For example, the Mimail virus in 2003 originated from an email claiming to be from PayPal, persuading users to update credit card information on a fraudulent website.
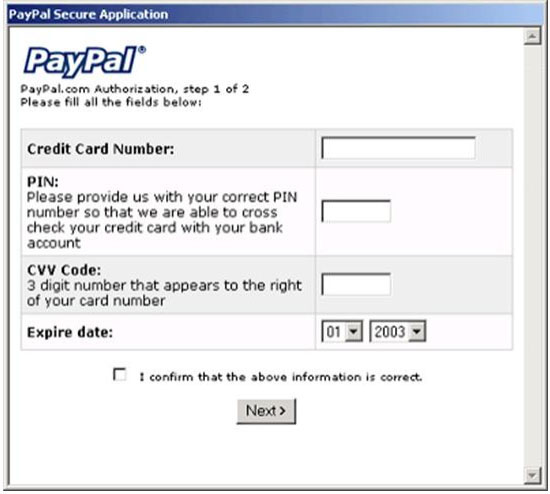
Image Source: https://www.sqasolar.org.uk/solar/material/IS01CGCD/page_32.htm
Today, phishing techniques have diversified and become more advanced, including angler phishing via social media, clone phishing, domain spoofing, search engine phishing, and whaling, which targets executive-level employees.
Statistics on Prevalence and Impact
The prevalence of phishing is highlighted by a survey where 92% of businesses reported falling victim to phishing attacks.
These attacks focus on exploiting human error rather than technical vulnerabilities, making them particularly challenging to combat. The impact of phishing includes potential identity theft, significant financial loss, and compromised personal or organizational security. Given its widespread and evolving nature, phishing remains one of the most significant threats in the cybersecurity landscape.
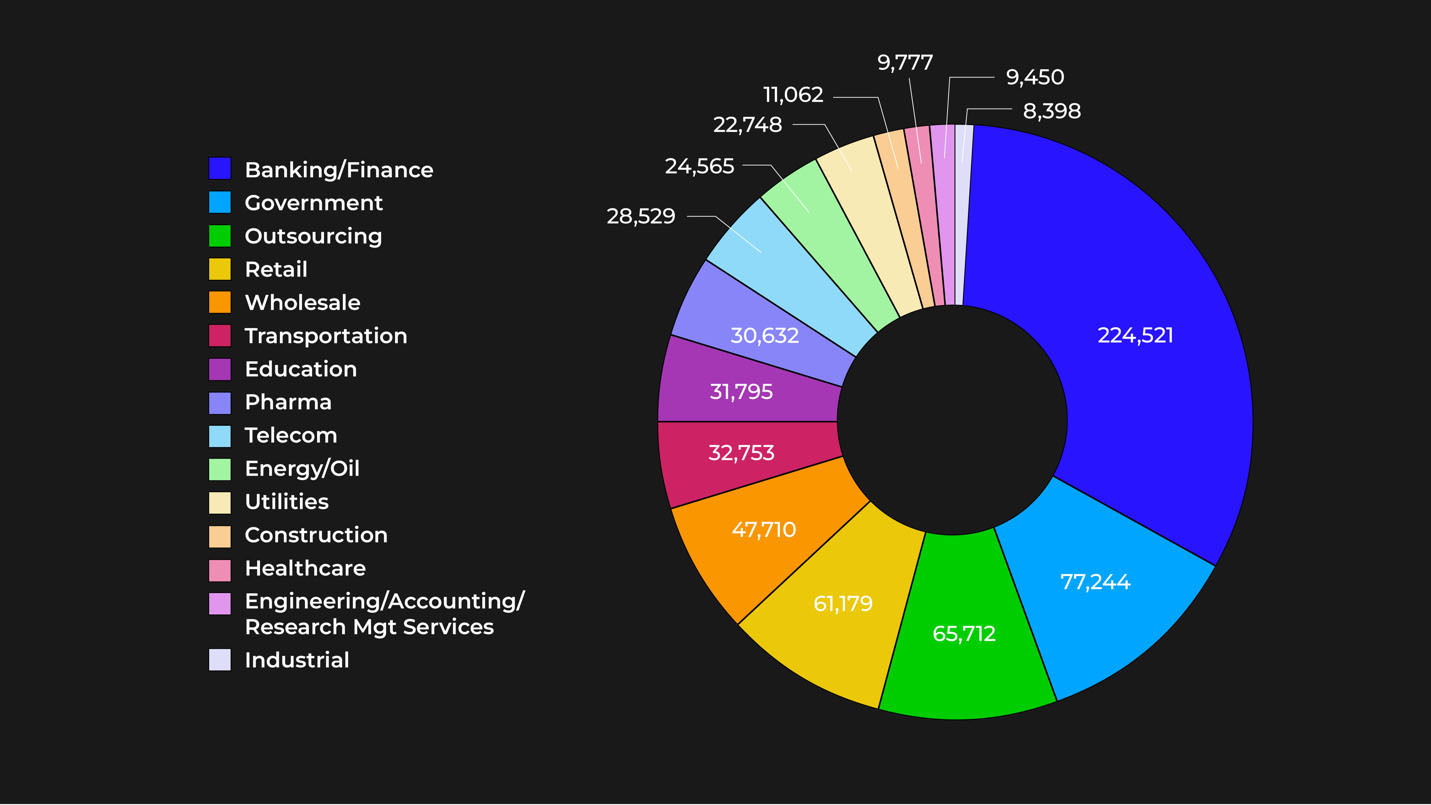
According to Trellix's telemetry data, phishing is a pervasive threat that affects all sectors indiscriminately. This data underscores that no industry or sector is immune to the dangers of phishing attacks, highlighting the universal vulnerability to this type of cyber threat.
The Psychology Behind Phishing Emotional Manipulation
Phishers expertly exploit human emotions like fear, curiosity, and urgency to manipulate their victims. This tactic plays on the innate psychological responses that can override rational thought. For instance, a phishing email might create a sense of urgency by falsely alerting the recipient that their account will be closed if immediate action isn't taken. This urgency can cloud judgment, prompting the recipient to act quickly rather than cautiously.
Similarly, curiosity can be piqued by emails offering exclusive access to content or promising rewards. The fear of missing out (FOMO) can drive individuals to click on links without considering the potential risks. Fear, another powerful emotion, is often exploited by sending alarming messages claiming that the recipient's security has been breached, instilling a sense of panic and urgency to resolve the supposed issue.
Trust Exploitation
Phishers often impersonate trustworthy entities to gain the confidence of their victims. By masquerading as reputable companies, banks, or even government agencies, attackers create a veneer of legitimacy. This deception is enhanced by using official logos, mimicking the tone and language of the legitimate entity, and crafting emails that appear professionally made. Recipients, believing they are interacting with a trusted source, are more likely to divulge sensitive information.
The effectiveness of this tactic lies in the psychological principle of trust – people tend to lower their guard when they believe they are dealing with a reputable organization. This trust is further exploited when attackers use personal information, such as the recipient's name or specific details about their accounts, making the fraudulent communication seem more credible.
The Principle of Authority
The use of authority is a common tactic in phishing attacks. Here, attackers pose as figures of authority, such as senior executives, IT staff, or law enforcement officers. The principle of authority leverages the human tendency to comply with requests from authority figures without question. For example, an email seemingly from a company's CEO asking an employee to transfer funds or provide confidential information can compel compliance based on respect for authority, even if the request seems unusual.
Social Engineering Techniques
Phishers use various social engineering techniques, with pretexting and baiting being prominent examples. Pretexting involves fabricating a scenario or pretext to obtain personal information. This could involve an attacker posing as a researcher conducting a survey and asking for confidential data. Baiting, on the other hand, plays on human curiosity or greed. It involves offering something enticing – such as free software downloads or access to exclusive content – in exchange for personal information or login credentials.
These techniques rely on psychological manipulation, exploiting trust, authority, curiosity, and fear to deceive victims into revealing sensitive information or performing actions that compromise their security.

Why People Fall for Phishing
Cognitive Biases Contributing to Susceptibility
The susceptibility of individuals to phishing attacks is often rooted in certain cognitive biases. These biases are inherent ways of thinking that can skew judgment and decision-making. One such bias is overconfidence, where individuals believe they are less likely to be deceived or are more capable of identifying phishing attempts than they actually are. This false sense of security can lead to a lowered guard and an increased likelihood of falling for phishing scams.
Another common bias is confirmation bias. This occurs when individuals give more weight to information or scenarios that confirm their existing beliefs or expectations. For instance, if an email appears to align with what they expect from their bank or a trusted company, they may overlook red flags that suggest it is a phishing attempt.
The Role of Context and Timing
The context and timing in which a phishing attempt occurs can significantly influence its success. Stressful situations, for example, can impair judgment and critical thinking, making individuals more vulnerable to deception. Under stress, the capacity to meticulously analyze an email or a request diminishes, leading to hasty decisions that might not be made under normal circumstances.
Similarly, the end of the workday, when individuals are tired and their mental resources are depleted, is a time when vigilance may be lower. Phishers may exploit this by timing their attacks to coincide with these periods, increasing the likelihood that their targets will respond without the usual level of scrutiny they might apply.

The Impact of Social Proof and Urgency in Decision-Making
Social proof is a psychological phenomenon where people copy the actions of others in an attempt to undertake behavior in a given situation. In the context of phishing, social proof can be manipulated by attackers who, for instance, craft emails claiming that many others in the organization have already complied with a request. The perception that others are complying can create a false sense of security and legitimacy, leading more individuals to fall for the scam.
Urgency is another tool in the phisher's arsenal. By creating a sense of urgency or an immediate need for action, attackers can prompt recipients to act impulsively. Urgent requests for action, especially when they come from what appears to be a trusted source, can bypass the normal, rational decision-making process. This urgency can be especially effective if it's tied to potential negative consequences, such as the threat of account closure or legal action.
Real-World Cases
The blog post from Trellix discusses cyberattacks targeting Ukraine at the end of 2022.
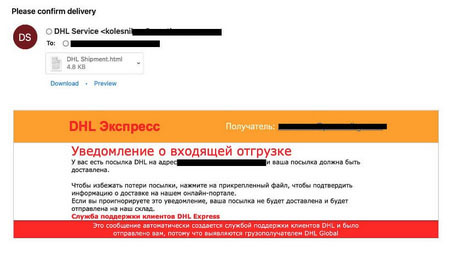
The attacks involved a variety of methods, including malicious emails and URLs aimed at Ukrainian government and military sites. These emails often contained minimal body content but included an attachment designed to catch interest, such as work-related documents.
The attachments were diverse, ranging from spreadsheets to compressed archives, and were used to deliver malware. The cyberattacks also included sophisticated phishing techniques, leveraging the ongoing conflict to exploit the heightened sense of urgency and distraction among the targets.
This case study highlights the evolving nature of cyber threats and the importance of remaining vigilant against such sophisticated phishing attempts.
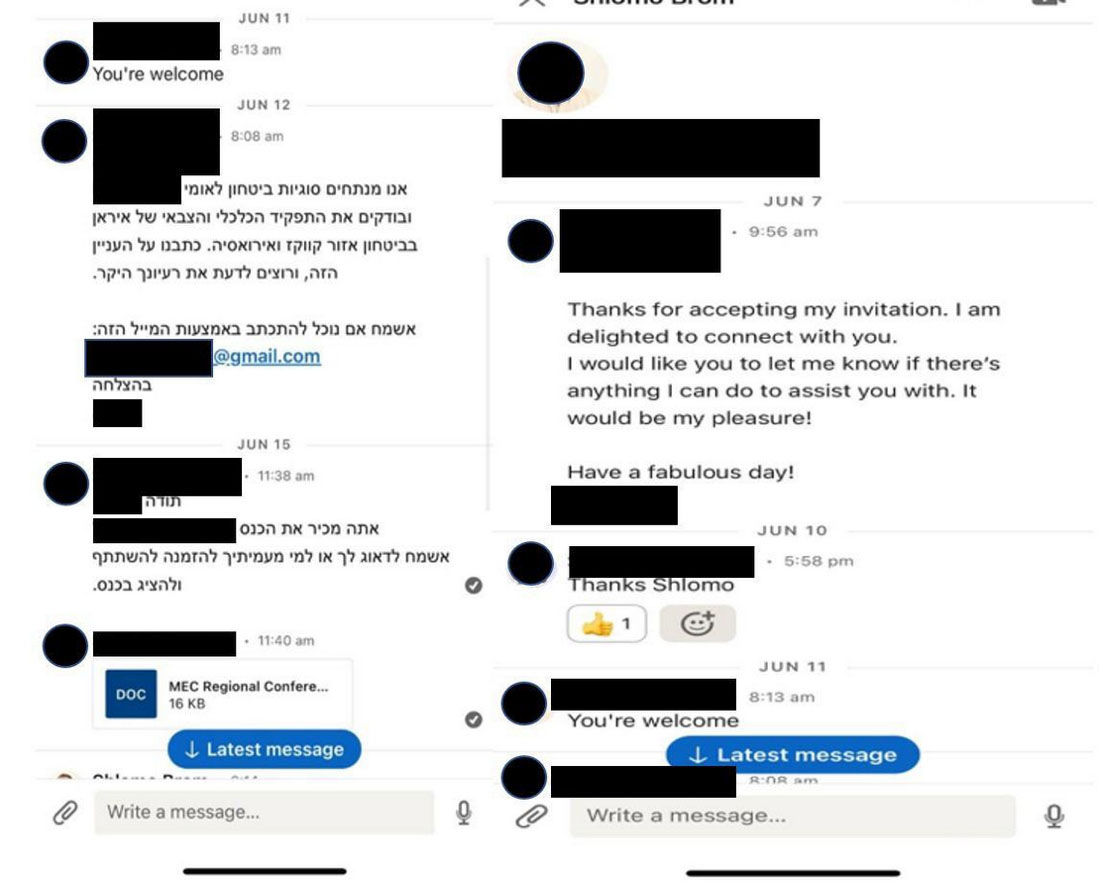
In July 2023, The Times of Israel reported on an Iranian phishing campaign targeting specific Israeli state employees and researchers.
This campaign illustrates a key psychological tactic in phishing: the targeting of individuals with content tailored to their interests. By initiating contact through LinkedIn and transitioning to email, the attackers leveraged the platform's professional context to establish credibility. The use of documents related to conferences or research papers as bait capitalized on the targets' professional interests, making the phishing attempt more compelling and increasing the likelihood of engagement.
The Future of Phishing and Countermeasures
Emerging Phishing Techniques
As technology advances, so do the techniques used in phishing attacks. One significant development is the use of Generative AI in phishing. This technology enhances the realism of traditional phishing methods — like emails and direct messages — by eliminating errors and adopting convincing writing styles. Generative AI can absorb real-time information from various sources, making phishing messages more believable and generating a sense of urgency that compels targets to act. Spear phishing attacks have become particularly convincing with the aid of AI, as demonstrated in experiments where AI-generated phishing emails were more likely to trick recipients than those crafted by humans. This is a testament to the growing sophistication of AI in crafting targeted and persuasive phishing messages.
Deepfake technology is another emerging threat. This technology uses AI to create misleading audio, video, and images, and it's increasingly being used in phishing attacks. For instance, deepfake phishing was used to trick the CEO of a UK-based firm into wiring $243,000 by impersonating the voice of the firm's parent company head. These deepfake phishing campaigns are expected to become more common and more effective, presenting a unique challenge for cybersecurity.
Future Trends in Cybersecurity Defenses
In response to these advanced phishing techniques, cybersecurity defenses are also evolving. AI tools are well-suited to detect AI-powered phishing attempts. Deploying generative AI for email security can significantly aid in preventing these sophisticated attacks.
Conclusion:
Finally, understanding the psychological aspects of phishing empowers individuals, transforming them from passive recipients of technological protections into active participants in the defense mechanism. This shift is instrumental in building a culture of security awareness, which is vital in the ongoing battle against phishing attacks.
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
