What Is Zero Trust Strategy?
Reviewed by Grant McDonald · October 16, 2025
Zero Trust is a cybersecurity model that assumes users and devices inside and outside an organization’s network have been breached and cannot be trusted. "Never trust, always verify" is the core principle of Zero Trust, meaning that no user or device is trusted by default and should be verified, even if it is inside the organization's network.
E-BOOK
The Mind of the CISO: Closing the gap between reaction and readiness
Discover insights on the evolving threat landscape from more than 500 global CISOs.
Instead, all access to applications and data is granted on a least-privileged basis. Users and devices must be continuously assessed for posture, authenticated, and authorized before they are allowed to connect.
Why is Zero Trust important?
Before Zero Trust, previous security frameworks took a "trust but verify" approach. Anything inside the organization’s firewall could be implicitly trusted. But a series of high-profile breaches, including an infamous 2013 Target store cyberattack in which a “trusted” contractor was compromised and leveraged to harvest the data of more than 70 million customers, led to the creation of Zero Trust.
In today's world, where users and devices are increasingly mobile and connected to the internet, the traditional network perimeter has become more and more porous. Zero Trust helps to protect organizations from cyberattacks by applying principles that make it more difficult for attackers to gain access to their systems and data.
What challenges does Zero Trust solve?
Challenge #1: Countering Advanced Persistent Threats (APTs)
By continuously verifying identities and devices, Zero Trust hinders APTs' ability to move laterally within the network.
Challenge #2: Securing Remote Work
Zero Trust ensures secure access to company resources from anywhere without compromising security.
Challenge #3: Thwarting Attackers' Movements
Following a Zero Trust approach, users establish direct connections to the applications and resources they need without relying on network-based connections. This decreases attackers' ability to move laterally in the network.
Benefits of Zero Trust
A Zero Trust Strategy is a proactive and comprehensive approach to bolster your security posture in an increasingly interconnected digital landscape.
Reduced Attack Surface. Strict access controls and microsegmentation shrink the attack surface, making it harder for attackers to move laterally within your network.
Minimized Risk. Zero Trust mitigates the risk of data breaches and insider threats by limiting access to only what is necessary for each user's role.
Improved Compliance. Adherence to regulatory requirements and industry standards is achieved by enforcing strict access policies, auditing user activities, and maintaining comprehensive logs.
Broad Coverage. Zero Trust is adaptable to various IT environments, including cloud, hybrid, and on-premises, making it suitable for modern, dynamic infrastructures.
- Future-proofing. As cyber threats evolve, Zero Trust provides a forward-looking security strategy that can adapt to new challenges and technologies.
What are the 5 pillars of Zero Trust?
Organizations need a framework and maturity model to adopt Zero Trust. The U.S. Cybersecurity and Infrastructure Agency (CISA) has published a maturity model to help organizations transition to a Zero Trust architecture. This model encompasses the following five pillars.
Identities. Rigorously authenticate and authorize users and devices.
Devices. Verify the security postures of all devices accessing the network.
Networks. Segment internal and external network traffic to prevent lateral movement.
Data. Use encryption, access controls, and data loss prevention solutions to protect data.
- Applications & Workloads. Conduct application security testing and vulnerability scanning and deploy an intrusion detection system (IDS) to mitigate attacks.
Organizations should tailor the pillars of Zero Trust to align with their specific security needs.
Zero Trust is more than ZTNA
In the rush to the cloud, many organizations focused on a Zero Trust networking access (ZTNA) approach to their implementation. While ZTNA is an important part of an overall Zero Trust architecture, it represents only one component that is necessary for Zero Trust at scale.
ZTNA focuses on the implementation of Zero Trust principles for access to resources enforcing granular, adaptive, and context-aware policies to applications hosted across clouds and data centers. However, the overall maturity model as published by CISA also includes concepts such as pervasive visibility, analytics, automation, and orchestration that span all pillars of execution.
This, combined with an “assume breach” mentality, brings to light the need for holistic threat detection and response capabilities that overlap with but also broaden a ZTNA approach to on-premises devices, services, and apps. ZTNA alone does not provide this range of capabilities.
Best practices for adopting a Zero Trust strategy
Transitioning to a Zero Trust security model is a critical step in fortifying your organization's cybersecurity posture. However, implementing Zero Trust is a strategic journey, not an overnight transformation. To effectively navigate this transition, consider the following key best practices.
Best Practice #1: Assess Your Current State
Evaluate your existing security infrastructure to identify weaknesses and areas that need improvement. Understand your current security posture to make informed decisions and set clear goals.
Best Practice #2: Define Access Policies
Clearly define who has access to what resources based on their roles and responsibilities. Effective access policies lay the groundwork for Zero Trust.
Best Practice #3: Educate Your Team
Train employees on Zero Trust principles and security best practices to ensure their cooperation with the new security model. A well-informed team is your first line of defense.
Best Practice #4: Implement Incrementally
Develop a phased approach to implementing Zero Trust gradually to minimize disruptions and adapt to the changes. Piloting Zero Trust in specific areas allows for smoother integration.
Best Practice #5: Regularly Audit and Update
Continuously assess and refine your Zero Trust strategy to stay ahead of emerging threats. Regular audits and updates ensure the ongoing effectiveness of your security measures.
Best Practice #6: Engage Leadership Early
Gain executive buy-in and support for Zero Trust policies. When talking with leadership, shape conversations around Zero Trust's positive impact on the business.
Best Practice #7: Use an Integrated, Scalable Platform
Avoid attempting to build a Zero Trust architecture based solely on integrating multiple, specific point solutions. This can lead to needless complexity and inconsistent implementation across diverse environments (multiple clouds, data centers, and device types). Instead, adopt a platform that simplifies IT infrastructure and consolidates security functions.
How to evaluate and choose Zero Trust solutions
There is no single vendor or all-in-one solution that provides everything needed for a complete Zero Trust implementation. Choosing the right Zero Trust solutions requires careful consideration and alignment with the five pillars.
Ensure the chosen solutions offer robust identity verification mechanisms, such as multifactor authentication.
Look for solutions that provide granular access control, allowing you to define and enforce access policies.
Seek tools that enable network segmentation and isolation, providing an additional layer of security.
Choose solutions with real-time monitoring capabilities, enabling swift detection and response to security incidents.
Select solutions that can adapt and integrate seamlessly with your organization's evolving needs and existing infrastructure.
Research vendors to make sure that they are reputable companies with proven track records of delivering secure solutions.
Make sure that each solution is mature and has been tested in production environments.
The CyberThreat Report
Insights gleaned from a global network of
experts, sensors, telemetry, and intelligence
The Trellix solution for Zero Trust
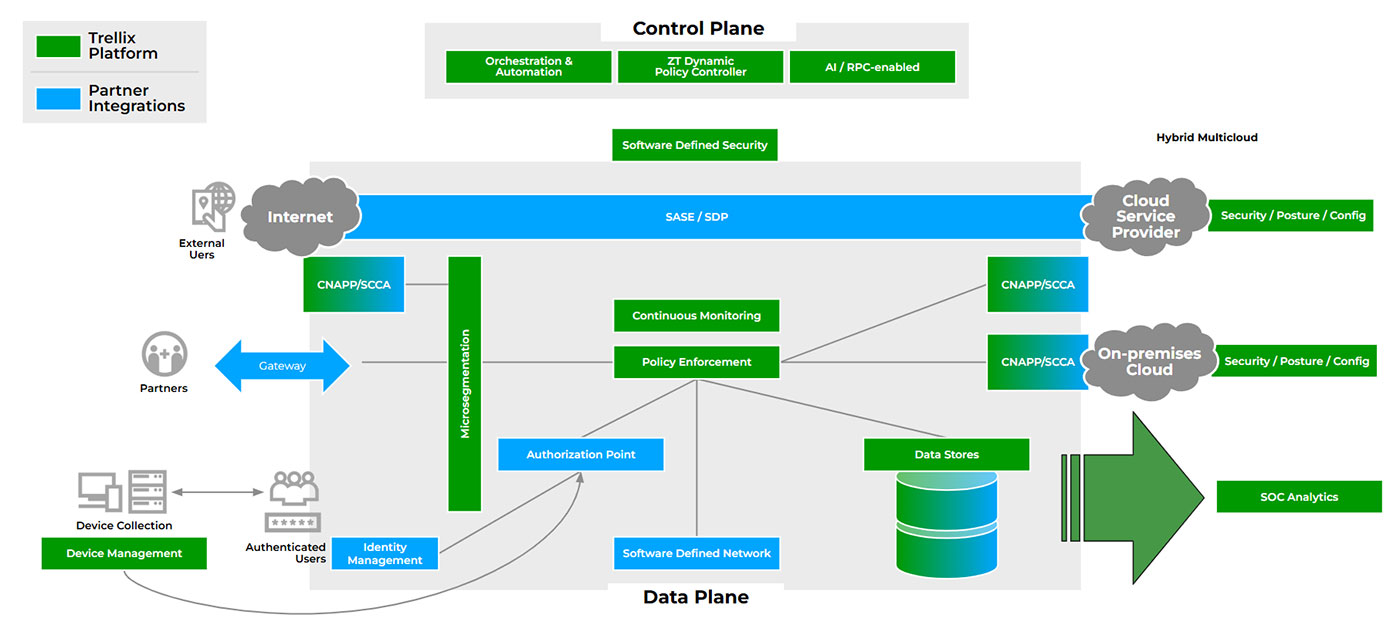
The integrated Trellix Security Platform amplifies your Zero Trust initiatives with its Trellix Wise AI engine, which collects insights from over 1,000 data sources. The Trellix Security Platform simplifies your security environment with consolidated native controls, integrated IAM providers, and a unified console to uncover and eliminate blind spots, ensuring robust Zero Trust implementation.
Figure 1. The open Trellix Security Platform lets you leverage current investments and derive increased value from your security architecture.
To reduce mean time to detect (MTTD), Trellix employs multivector, multivendor detections to prevent breaches and offers automated analysis. We empower SOC teams with guided responses for faster mean time to respond (MTTR) and SecOps playbooks that improve mean time to investigate (MTTI).
Trellix and Trellix partner integrations enhance visibility by providing native monitoring, protection, and threat detection for the five Zero Trust pillars. The Trellix Security Platform assumes a lack of visibility and delivers actionable insights by utilizing data from native and third-party tools, thereby accelerating detection and remediation efforts.
No single vendor possesses all of the tools, skills, or capabilities to complete a Zero Trust implementation. As shown in Figure 1, Trellix offers unmatched integrations with a broad partner ecosystem to speed up your Zero Trust implementation.
Zero Trust FAQ
- Assess Your Current State. Evaluate your current security infrastructure to identify weaknesses and set clear goals.
- Define Access Policies. Clearly define who has access to what resources based on roles and responsibilities.
- Educate Your Team. Train employees on Zero Trust principles and security best practices for cooperation.
- Implement Incrementally. Implement Zero Trust gradually to minimize disruptions and allow for smoother integration.
- Regularly Audit and Update. Continuously assess and refine your Zero Trust strategy to stay ahead of threats.
- Engage Leadership Early. Gain executive buy-in by highlighting Zero Trust's positive business impact.
- Use an Integrated, Scalable Platform. Avoid building a Zero Trust architecture with disparate point solutions, which creates complexity and inconsistent implementation. Instead, use an integrated platform that simplifies IT infrastructure and consolidates security.
Zero Trust resources

Learn how Trellix accelerates Zero Trust implementation with security incident detection, automated response capabilities, and integrated threat intelligence.

We analyze cybersecurity threats, emerging vulnerabilities, and defense strategies to help you stay ahead of cyber risks.

See how Trellix offers public sector and government agencies a robust and integrated platform to effectively manage cybersecurity risks and reduce operational costs.
Grant has over 17 years of experience working in Cybersecurity across a range of technologies including Endpoint, Server Security, Cloud and Data Security. At Trellix he is focused on Security Operations and the Trellix Platform. When he isn't writing, speaking or increasing cybersecurity awareness he enjoys restoring old cars, skiing and watching the latest entertainment from a galaxy far, far away.