What Is the MITRE ATT&CK Framework?
The MITRE ATTACK® framework is a curated knowledge base and model for cyber adversary behavior. It is designed to be used by cybersecurity teams to strengthen their organization’s security posture. The MITRE ATT&CK framework reflects the various phases of an adversary's attack lifecycle and the platforms they are known to target.
The tactics and techniques abstraction in the model provides a common taxonomy of individual adversary actions understood by both offensive and defensive sides of cybersecurity. It also provides an appropriate level of categorization for adversary action and specific ways of defending against it.
The behavioral model presented by ATT&CK contains the following core components:
- Tactics, denoting short-term, tactical adversary goals during an attack (the columns)
- Techniques, describing the means by which adversaries achieve tactical goals (the individual cells)
- Documented adversary usage of techniques and other metadata (linked to techniques) [1]
White Paper
Threat Hunting and Detection Engineering
Get your guide to proactive cyber defense
History of the MITRE ATT&CK framework
MITRE ATT&CK was created in 2013 as a result of MITRE's Fort Meade Experiment (FMX). Researchers emulated both adversary and defender behavior in an effort to improve post-compromise detection of threats through telemetry sensing and behavior analytics.
The key question for the researchers was, "How well are we detecting documented adversary behavior?" To answer that question, the researchers developed ATT&CK, which is used as a tool to categorize adversary behavior. ATT&CK stands for adversarial tactics, techniques, and common knowledge.
Here are three iterations of MITRE ATT&CK:
ATT&CK for Enterprise
Focuses on adversarial behavior in Windows, Mac, Linux, and cloud environments.
ATT&CK for Mobile
Focuses on adversarial behavior on iOS and Android operating systems.
ATT&CK for ICS
Focuses on describing the actions an adversary may take while operating within an industrial control system (ICS) network.
MITRE ATT&CK is used worldwide across multiple disciplines including:
- Intrusion detection
- Threat hunting
- Security engineering
- Threat intelligence
- Red teaming
- Risk management [2]
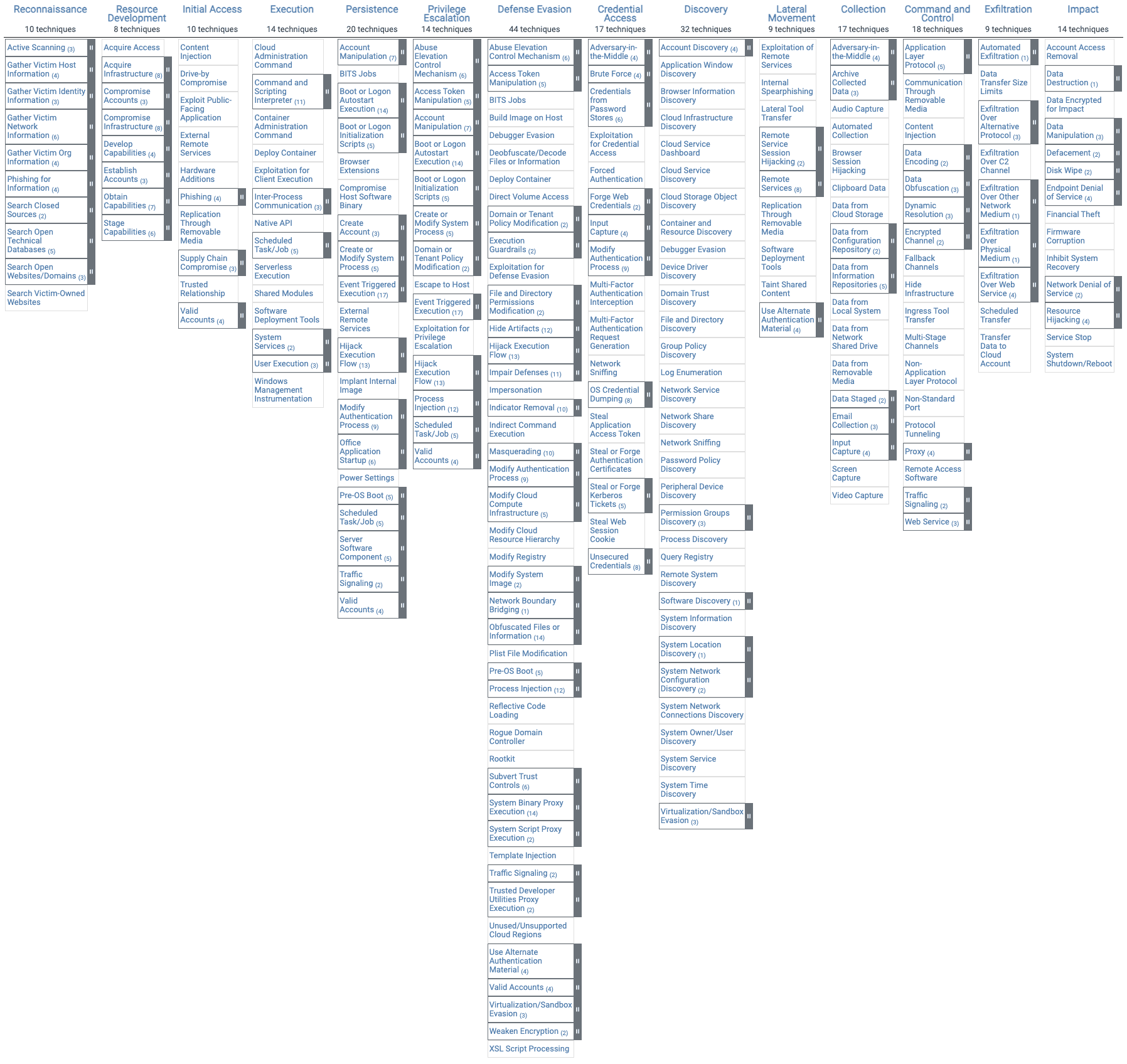
What is in the MITRE ATT&CK Matrix?
The MITRE ATT&CK Matrix contains a set of techniques used by adversaries to accomplish a specific objective. These objectives are categorized as tactics in the ATT&CK Matrix. The objectives are presented linearly from the point of reconnaissance to the final goal of exfiltration or "impact."
The broadest version of ATT&CK is ATT&CK for Enterprise. It includes Windows, macOS, Linux, PRE, Azure AD, Office 365, Google Workspace, SaaS, IaaS, network, and containers.
ATT&CK for Enterprise categorizes the following adversary tactics and techniques:
- Reconnaissance: Gathering information to plan future adversary operations, such as information about the target organization
- Resource Development: Establishing resources to support operations, such as setting up command and control infrastructure
- Initial Access: Trying to get into your network, such as spear phishing
- Execution: Trying to run malicious code, such as running a remote access tool
- Persistence: Trying to maintain their foothold, such as changing configurations
- Privilege Escalation: Trying to gain higher-level permissions, such as leveraging a vulnerability to elevate access
- Defense Evasion: Trying to avoid being detected, such as using trusted processes to hide malware
- Credential Access: Stealing accounts names and passwords, such as keylogging
- Discovery: Trying to figure out your environment, such as by exploring what they can control
- Lateral Movement: Moving through your environment, such as using legitimate credentials to pivot through multiple systems
- Collection: Gathering data of interest to the adversary goal, such as accessing data in cloud storage
- Command and Control: Communicating with compromised systems to control them, such as mimicking normal web traffic to communicate with a victim network
- Exfiltration: Stealing data, such as transferring data to a cloud account
- Impact: Manipulating, interrupting, or destroying systems and data, such as encrypting data with ransomware
Within each tactic of the MITRE ATT&CK matrix there are adversary techniques. These describe the actual activity carried out by the adversary.
Some techniques have subtechniques that explain how an adversary carries out a specific technique in greater detail. The full ATT&CK Matrix for Enterprise from the MITRE ATT&CK navigator is represented below in Figure 1.
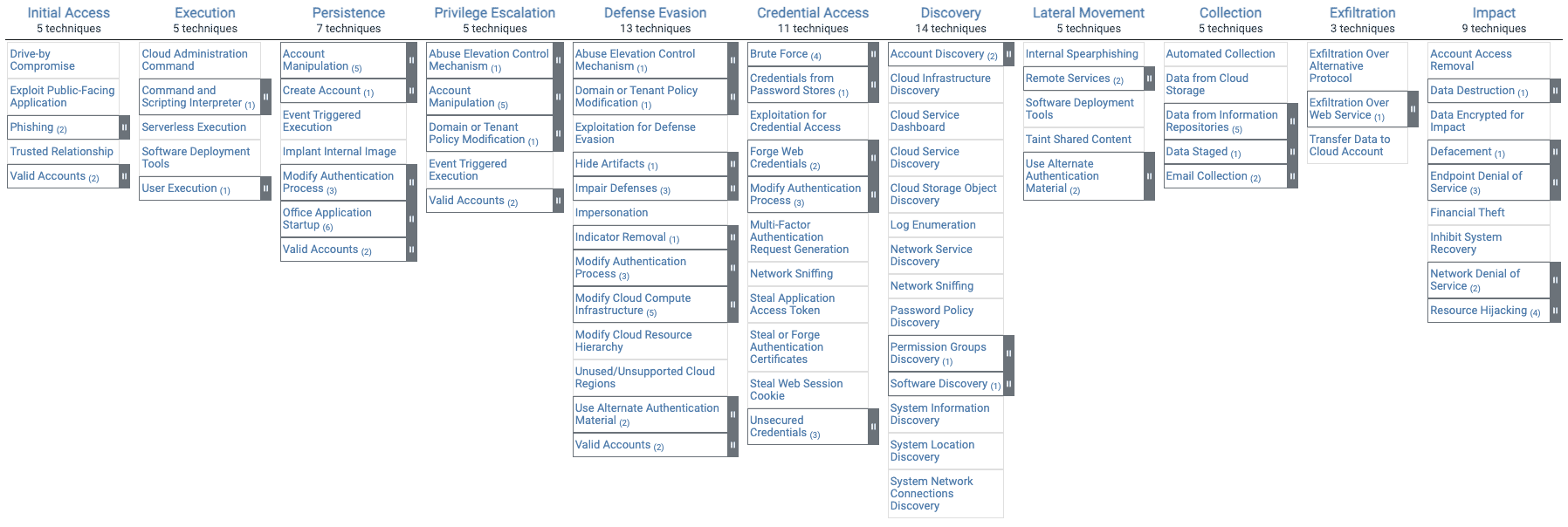
What is different about the MITRE ATT&CK for Cloud Matrix?
Within the MITRE ATT&CK for Enterprise matrix you will find a subsection, the MITRE ATT&CK for Cloud matrix. This contains a subset of the tactics and techniques from the broader ATT&CK Enterprise matrix.
The MITRE ATT&CK Cloud matrix is different from the rest of the Enterprise Matrix. This is because adversary behavior and the techniques used in a cloud attack do not follow the same playbook as attacks on Windows, macOS, Linux, or other enterprise environments.
MITRE ATT&CK techniques in Windows, macOS, Linux, and other related environments typically involve malware and entering a network that is owned and operated by the target organization.
MITRE ATT&CK techniques in AWS, Azure, Office 365, and other related environments do not typically involve malware. This is because the target environment is owned and operated by a third-party cloud service provider like Microsoft or Amazon.
Without the ability to enter the victim's environment, the adversary will most often leverage native features of the cloud service provider to enter the target victim's account, escalate privileges, move laterally, and exfiltrate data. An example of adversary behavior using the ATT&CK for Cloud framework is illustrated in the following example techniques:
Technique
Behavior
Initial Access
Uses stolen credentials to create a new account
Persistence
Adversary spear-phishes the victim, gaining credentials to AWS
Privilege Escalation
Uses valid account to change access permissions
Defense Evasion
Creates a new VM instance to bypass firewall rules
Credential Access
Steals access token to a database
Discovery
Locates target database
Lateral Movement
Uses application access token to access database
Collection
Mines information from the database
Exfiltration
Exfiltrates to adversary account in AWS
You can see the entire ATT&CK for Cloud matrix in Figure 2 below. It shows a subset of the ATT&CK for Enterprise matrix tactics and techniques.
MITRE ATT&CK vs. the Cyber Kill Chain
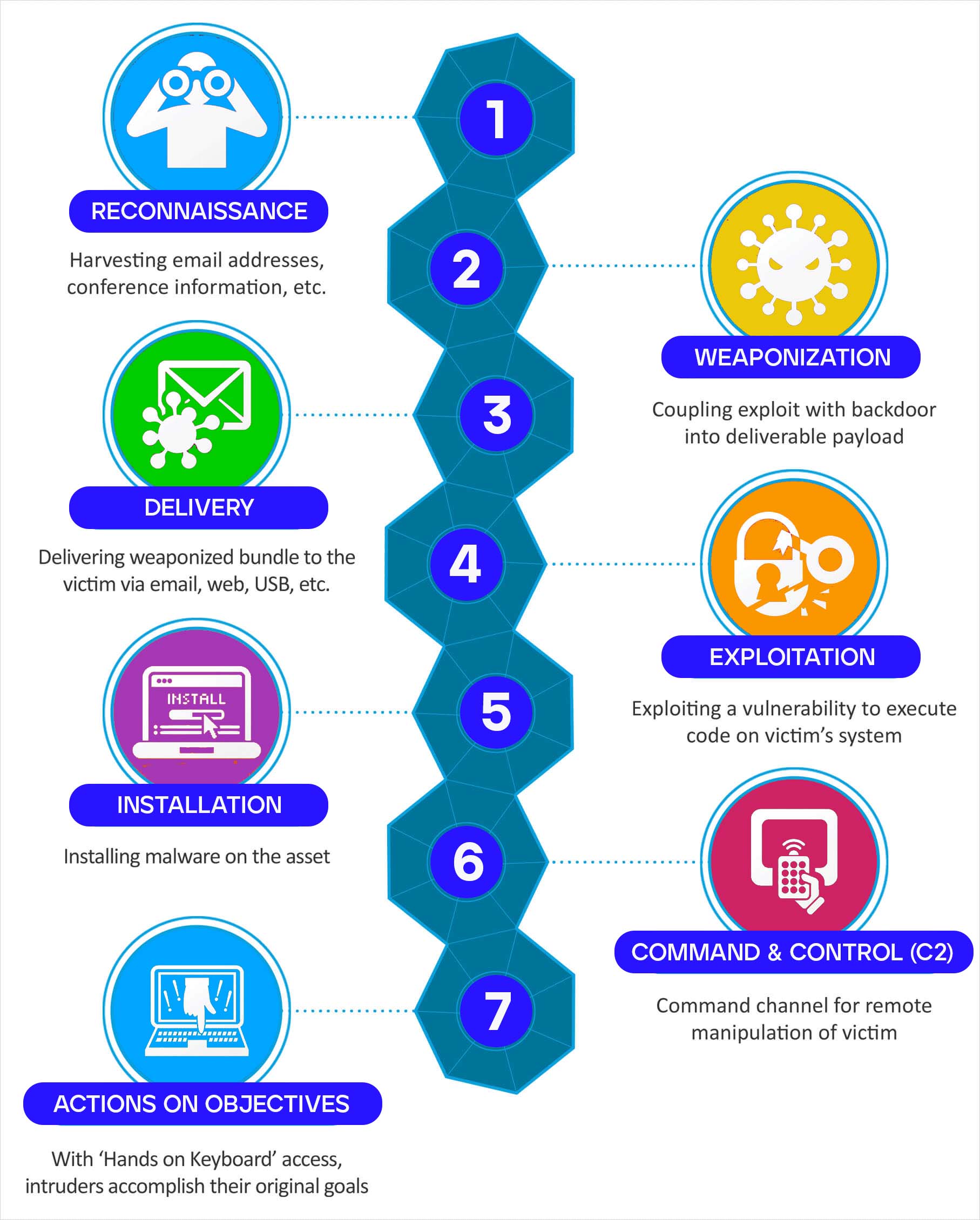
The Lockheed Martin Cyber Kill Chain® is another well-known framework for understanding adversary behavior in a cyber attack. The Kill Chain model contains the following stages, presented in sequence:
- Reconnaissance – Harvests email addresses, conference information, and more
- Weaponization – Couples exploit with back door into deliverable payload
- Delivery – Delivers weaponized bundles to the victim via email, web, USB, and more
- Exploitation – Exploits a vulnerability to execute code on a victim's system
- Installation – Installs malware on the asset
- Command and Control – Includes command channel for remote manipulation
- Actions on Objectives – Using “Hands on Keyboards” access, intruders accomplish their original goals
Lockheed Martin provides more detail on their Cyber Kill Chain framework in Figure 3.
There are two primary differences between MITRE ATT&CK and the Cyber Kill Chain.
- First, the MITRE ATT&CK framework goes into significantly more depth on how each stage is conducted through ATT&CK techniques and subtechniques. MITRE ATT&CK is regularly updated with industry input to keep up with the latest techniques, so defenders update their own practices and attack modeling regularly.
- Second, the Cyber Kill Chain does not factor in the different tactics and techniques of a cloud-native attack, as discussed above. The Cyber Kill Chain framework assumes that an adversary will deliver a payload, such as malware, to the target environment. This method is much less relevant in the cloud.
The CyberThreat Report
Insights gleaned from a global network of
experts, sensors, telemetry, and intelligence
How do you use the MITRE ATT&CK Matrix?
The MITRE ATT&CK framework can help an organization in several ways. In general, the following are applicable benefits to adopting MITRE ATT&CK:
- Adversary Emulation: Assesses security by applying intelligence about an adversary and how they operate to emulate a threat. ATT&CK can be used to create adversary emulation scenarios to test and verify defenses.
- Red Teaming: Acts as an adversary to demonstrate the impact of a breach. ATT&CK can be used to create red team plans and organize operations.
- Behavior Analytics Development: Links together suspicious activity to monitor adversary activity. ATT&CK can be used to simplify and organize patterns of suspicious activity deemed malicious.
- Defensive Gap Assessment: Determines what parts of the enterprise lack defenses and/or visibility. ATT&CK can be used to assess existing tools, or test new tools prior to purchasing, to determine security coverage and prioritize investment.
- SOC Maturity Assessment: Similar to Defensive Gap Assessment, ATT&CK can be used to determine how effective a security operations center (SOC) is at detecting, analyzing, and responding to breaches.
- Cyber Threat Intelligence Enrichment: Enhances information about threats and threat actors. ATT&CK allows defenders to assess whether they are able to defend against specific Advanced Persistent Threats (ATP) and common behaviors across multiple threat actors.
Implementing MITRE ATT&CK typically involves either manual mapping or integration with cybersecurity tools. The most common tools are security information and event management (SIEM), endpoint detection and response (EDR), and cloud access security broker (CASB).
Using MITRE ATT&CK with a SIEM involves aggregating log data from endpoints, networks, and cloud services, identifying threats, and mapping them to MITRE ATT&CK. Changes to security posture are then conducted in the security tools providing their log data such as EDR or CASB.
Using MITRE ATT&CK with EDR involves mapping events observed by the endpoint agent, which allows defenders to determine the phases of a threat event, assess associated risk, and prioritize response.
MITRE ATT&CK FAQ
The core components include:
- Tactics: Short-term, tactical adversary goals during an attack
- Techniques: Describing the means by which adversaries achieve tactical goals
- Documented adversary usage of techniques and other metadata (linked to techniques)
The MITRE ATT&CK framework is used for various purposes, including:
- Intrusion detection
- Threat hunting
- Security engineering
- Threat intelligence
- Red teaming
- Risk management
There are three main iterations:
- ATT&CK for Enterprise: Focuses on adversarial behavior in Windows, Mac, Linux, and cloud environments.
- ATT&CK for Mobile: Focuses on adversarial behavior on iOS and Android operating systems.
- ATT&CK for ICS: Focuses on describing the actions an adversary may take within an industrial control system (ICS) network.
MITRE ATT&CK resources

Learn how we refine Trellix solutions through third-party evaluations including MITRE Engenuity ATT&CK, SE Labs, AV-Test, and AV-Comparatives.

See how this real-world attack emulation demonstrates the power of Trellix products to protect your assets.

See how this real-world attack emulation demonstrates the power of Trellix products to protect your assets.