Conti Leaks: Examining the Panama Papers of Ransomware
By John Fokker, Jambul Tologonov · March 31, 2022
Introduction
It isn’t often the whole world gets an inside look of the business operations of a top tier cybercriminal group. Very early on in the Russian-Ukrainian Crisis the predominantly Russian based ransomware group Conti made a public statement where they expressed their loyalty to the Russian Administration.
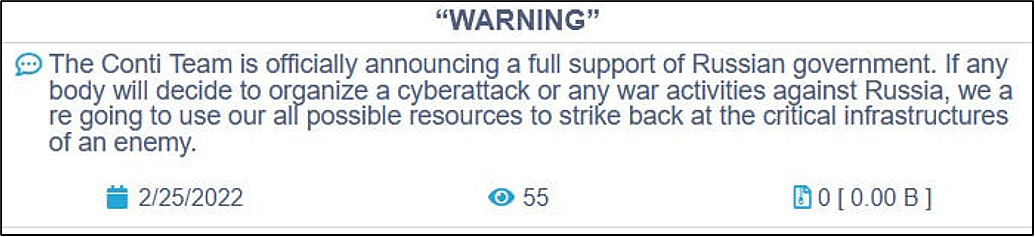
As a reaction to this statement and the current conflict, a Ukrainian security researcher, operating by the twitter handle @contileaks decided to publish years of Conti’s internal Jabber conversations online. The chats that were dumped span across several years consisted of thousands of messages making this the “Panama Papers of Ransomware”.
This wasn’t the first time the Conti gang got hit, last summer a disgruntled affiliate posted their attack playbook online, which was full of very useful intelligence for our customers.
Since it was public, the whole security community jumped to review the chats and within hours the first findings appeared on Twitter. Trellix was also quick to obtain the dataset and realized that this might be one of the largest “crowd-sourced cyber investigations” ever seen. What this means is that as a research team you must devise a flexible dissemination strategy because findings by the crowd will appear online. So, it is constant balance between verification of the published findings by others, investing in your own research goals and adjusting some of these goals based on new information.
Even though it was very tempting to dive down the rabbit hole immediately we did make sure we attacked the dataset with a certain plan.
Dissemination strategy; How to avoid the rabbit hole
Attack infrastructure
The first batch of leaked chats were only a couple of days old and ranging back quite some time. From the start we realized that the criminals might have left valuable data on their attack infrastructure in the chats. We wrote a quick extraction script and compared the mentioned network artifacts to our current dataset and saw a lot of overlap. Not only did we see overlap with infrastructure we attributed to TrickBot and Cobalt Strike in the past, but a good portion of the systems we filtered out were still alive and kicking. To prevent any retaliation by the Conti group directed at our customers, blocking this infrastructure was top priority.
Some of these live systems were actually located in the countries where we have a good relationship with Law Enforcement, so naturally we reached out and made sure they got a heads-up to take appropriate measures quickly.
The intelligence gathered from this was very actionable, but with a short shelf life, the next stop for us was tradecraft.
TTPs and tradecraft
Due to the severity of the leaks, there was a good chance that the Conti gang would rebrand or disperse it members across other ransomware families. In the prior leak where Conti’s playbook got dumped online there were excellent descriptions of the different tools and scripts they would use to attack their victims. So, looking at around 200 thousand leaked messages (Conti & TrickBot leaks combined) span over the period 2020-2022, it was likely members would share custom TTP’s or tradecraft amongst each other.
By filtering tool names and command line structures we found several examples where members discussed tool usage. Given the crowd sourced nature of this dump we would also like to thank The DFIR Report for their excellent findings which they published via their Twitter account.
Affiliates might leave Conti and their network, but wherever they go they will take along their tradecraft. Without an external intervention, like an arrest, we should anticipate that cybercriminals won’t stop their line of business, and thus we can expect to see their TTPs pop up in the future. However, through proper dissemination of the data we were able to empower many of our XDR product teams to improve the product efficacy against this tradecraft and incorporate our findings in MVISION Insights for customer visibility.
Did we ignore the juicy conversations completely? Not at all, fortunately we have a native Russian speaking research capability that made a huge difference while going down the rabbit hole. In the following section we will highlight some of the findings we found interesting to share.
Interesting chats
For transparency purposes we have included both the original Cyrillic and our human translated text to allow readers to delve into the intricacies of some of the Conti’s discussions. For readability purposes we have put the original leaked messages into 1-2-1 conversations to make it easier to understand/follow the context.
Conti as an enterprise
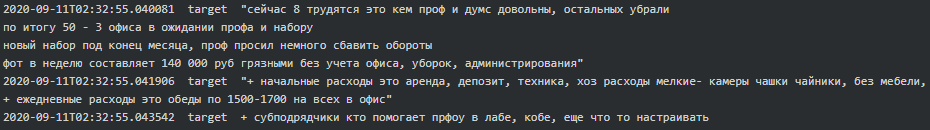
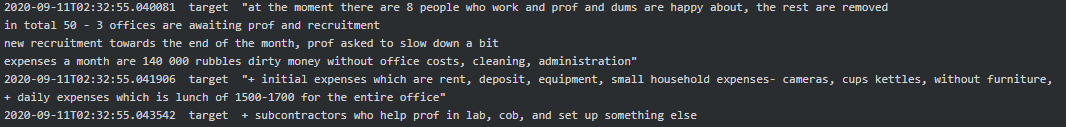
It is fascinating how much Conti resembles an ordinary firm with an office building, HR and other departments (testers, reversers, OSINT, coders, training team, etc.) with their regular salaries on the 15th and 30th of each month. Working hours are 10.00-18.00 Moscow time, five days a week. Stern is the boss who oversees everything and has 100 people on the payroll. “The weekend are the weekends. And nobody cancelled the vacations and sick days. All the other holidays - with the management's agreement” says Salmon (recruiter) to new hire-coder Core. According to Bentley (manager), he worked there for a year, but the company has existed for more than 10 years. Below are excerpts from various chats which provide a good glimpse into Conti’s organization and the presence of a physical office(s) in Russia:
 |
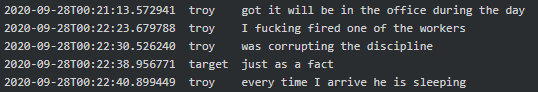 |
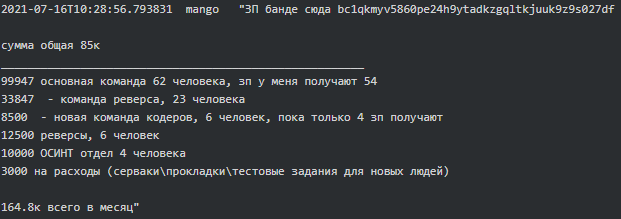 |
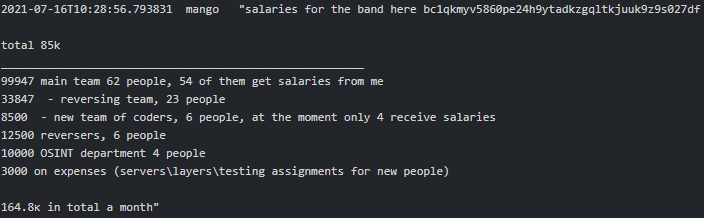 |
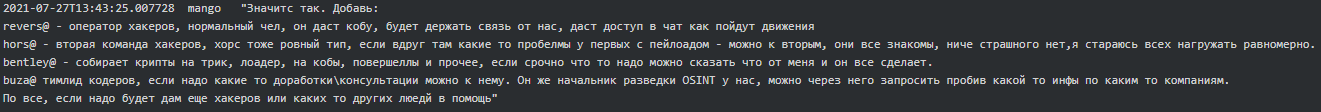
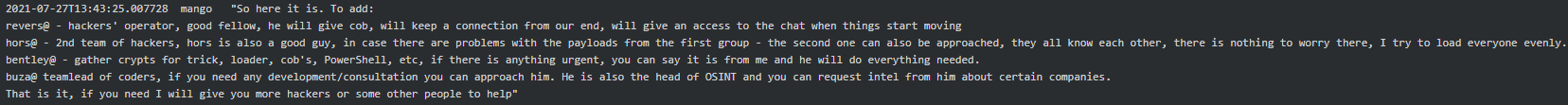
It is particularly interesting that in the Conti-TrickBot enterprise they are very careful about malware code overlapping. They have external experts who scrutinize developed illegal software code and ensure the code fingerprints are unique to each team of coders. Avoiding overlap seems to be important to segregate activities of different sub-teams and make it difficult for security researchers to piece various Russian speaking threat actors’ campaigns together.
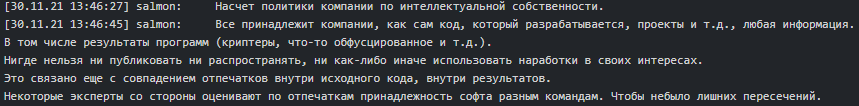
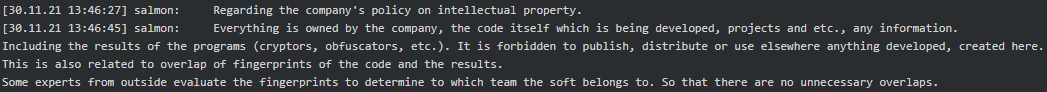
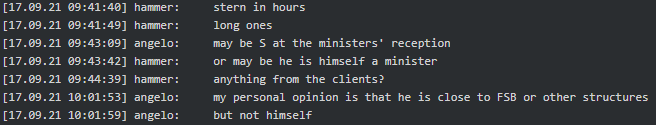
Possible government connections
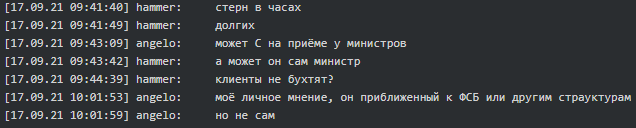
According to Angelo (tester/coder), Stern is closely affiliated with FSB or other structures and works for ‘Pu’. If Stern was not as almighty as God, they all would have ended up as REvil:
 |
 |
 |
 |
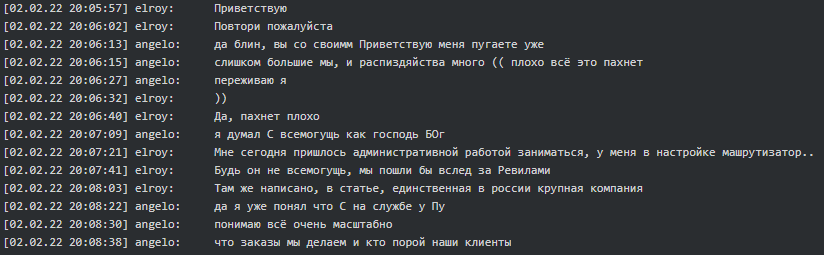
The Conti leadership was concerned over the situation surrounding the REvil ransomware group. However, Conti believed Russian authorities arrested only the lowest ranked members of REvil who were involved in the cash out.
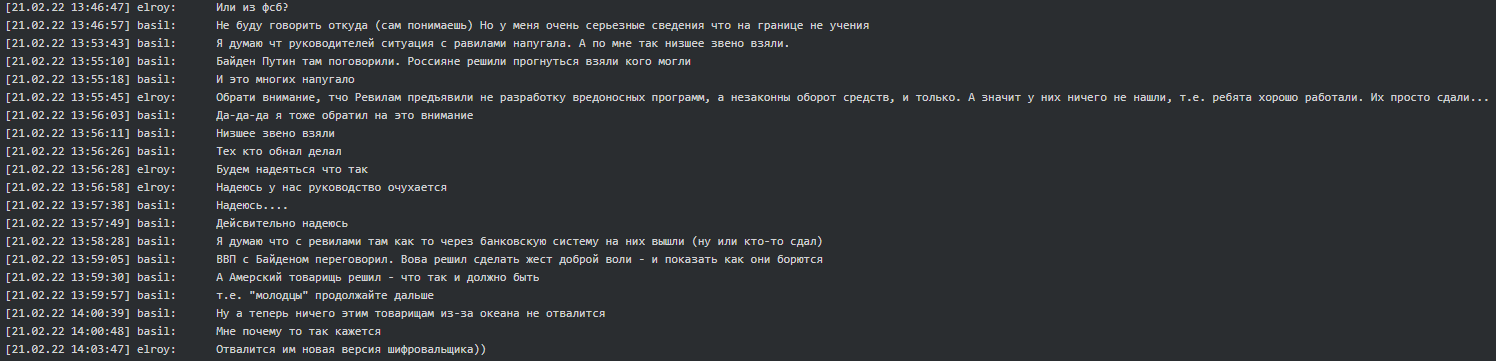
It is worth mentioning that Basil (tester/coder) was asked if he is from FSB, he subsequently replied he had serious intelligence related to Ukrainian border activity. This statement was made seven days prior to Russia’s incursion into Ukraine:
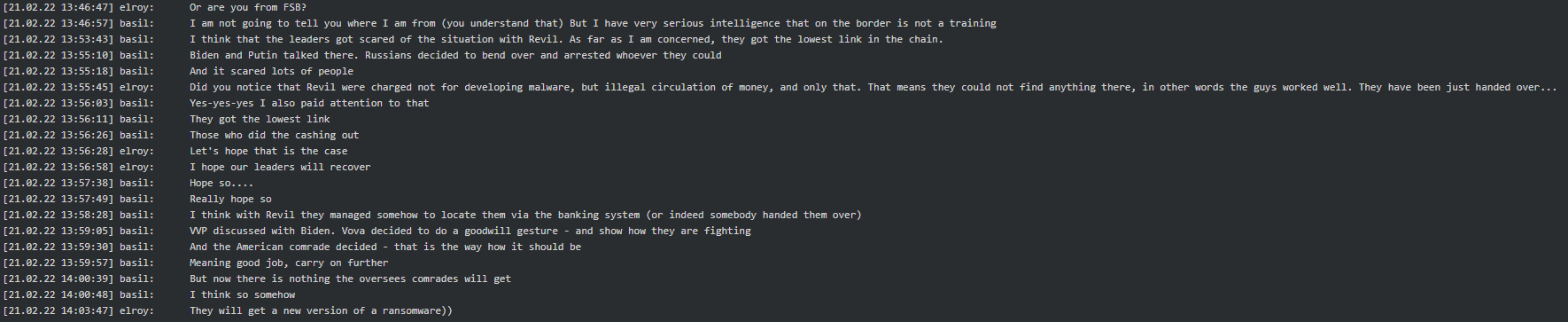
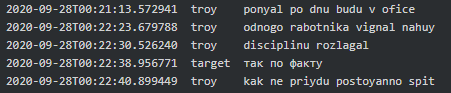
In another conversation involving Target (manager) he stated if they indeed encrypted Credit One Bank Troy (tester/crypter) would get a reward in the Kremlin:
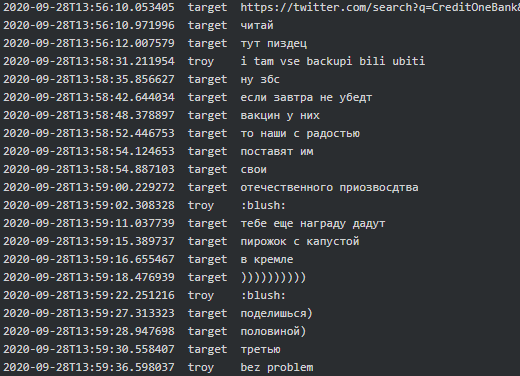 |
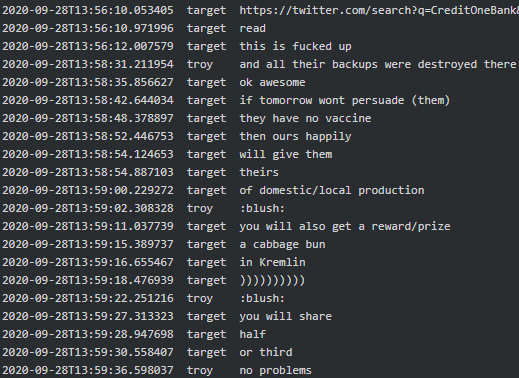 |
Occasionally Conti seems to be asked to do so-called ‘pioneering’ (volunteering) work on a special request from one of two ‘offices’. As Soviet Pioneers (aka scouts) they do their fair share of work similarly to what Cozy Bear does:
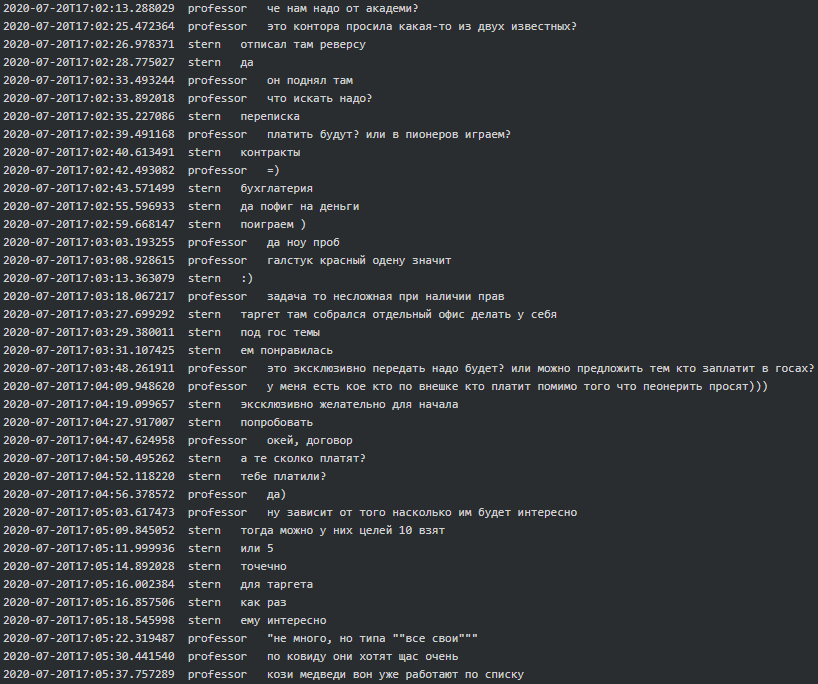
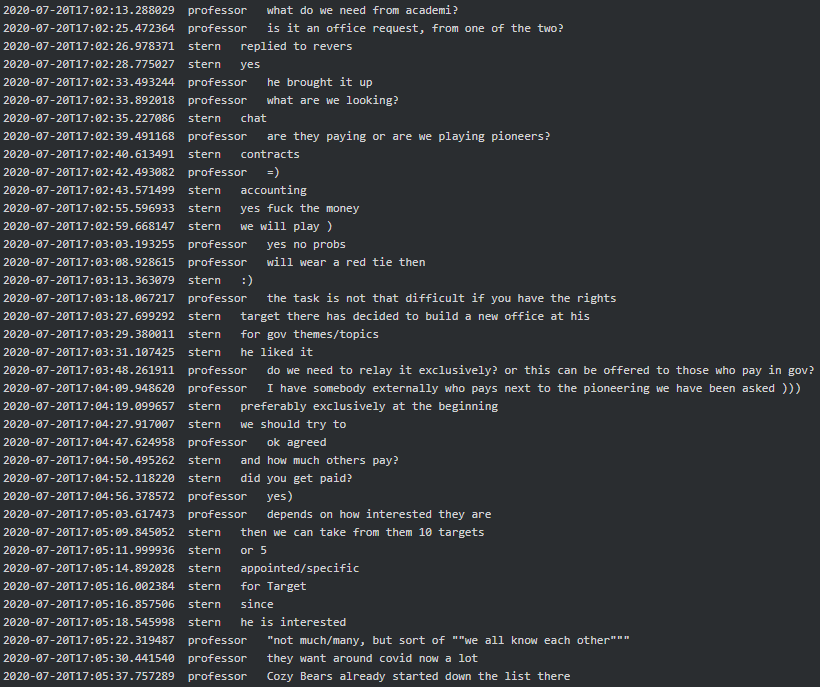
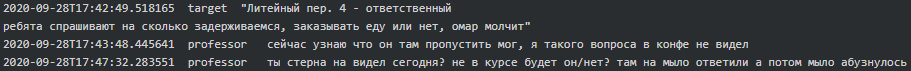
It is probable that one of the two offices is a so-called ‘Bolshoy Dom’ (Big House), an office building located at 4 Liteyny Avenue which serves as the headquarters of Saint Peterburg’s local branch of FSB:
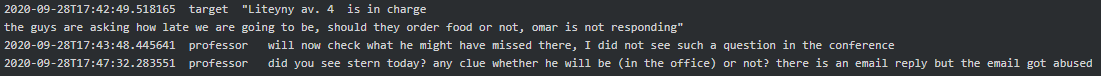
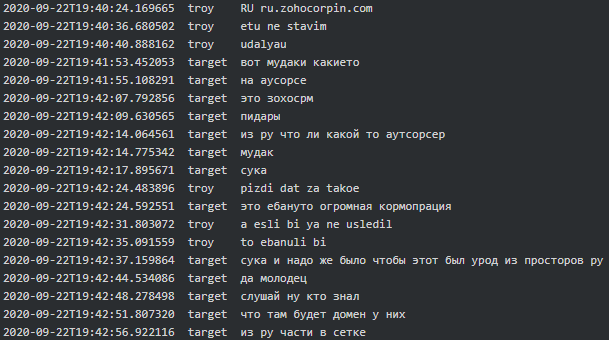
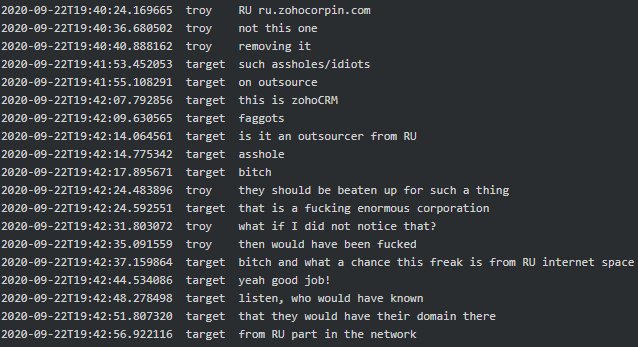
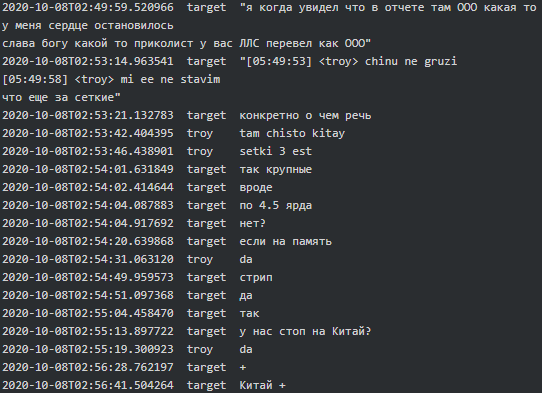
In line with geo-political interests of Russia, Conti seems to have a ‘stop’ on China and get terrified every time they see a Russian company or ‘OOO’ abbreviation (equivalent of ‘LLC’ in CIS countries) in the list of their victims:
 |
 |
 |
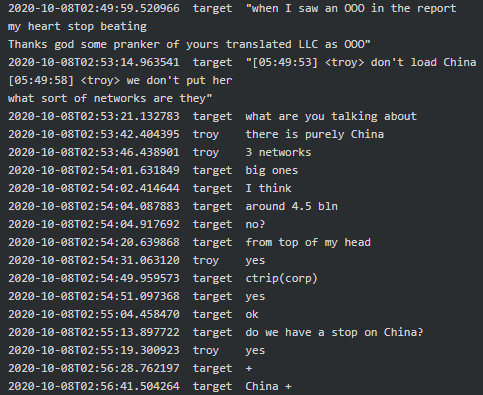 |
All these messages corraborate the fact that Conti-TrickBot enterprise has a close relationship with Russian government and/or act in its interests.
Collaboration with other Malware families
Conti-Ryuk
Collaboration with Ryuk seemed to have started around August 2020 when Stern said, “Ryuk is going start as of Monday.” Target seemed to responsible for updating Stern on how the Conti-Ryuk collaboration was going and if Ryuk team is able to work together and smoothly with his team:
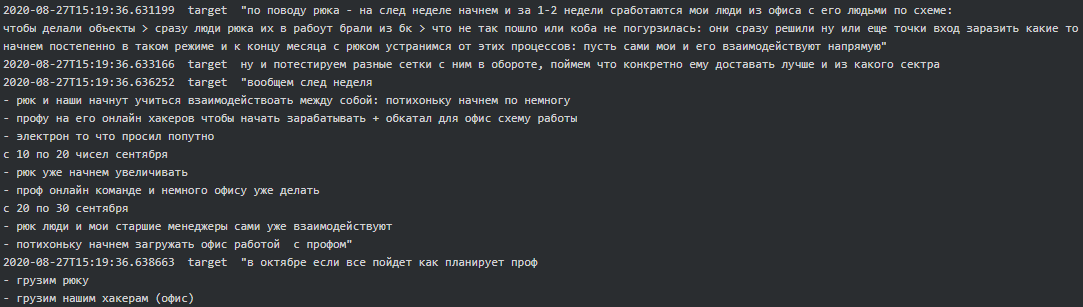
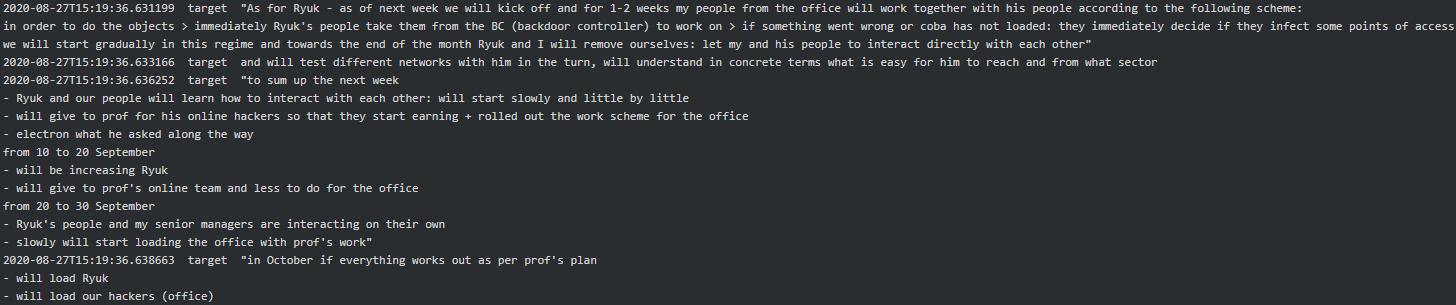
As per the chat between Stern, Target and Troy, it is evident that from September 2020 to October 2020 Conti-Ryuk successfully executed attacks on Sopra Steria, Steelcase, Merieux NutriSciences and Northern Trust and received 1.5 million (currency is unknown) in ransom payments:
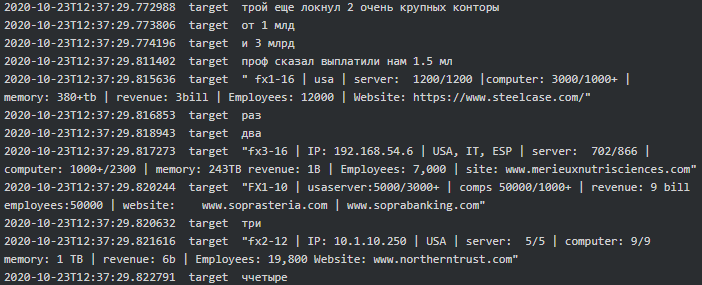 |
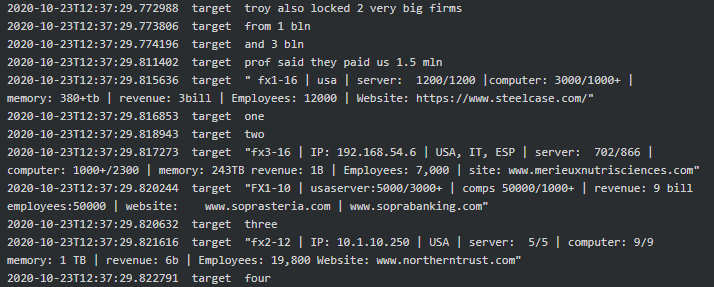 |
Conti-Maze
The first mention of Conti-Maze potential connection dates back July 2020, when Kevin (coder/crypter) says to Stern “Prof took a different locker as far as I understood. Appears to be Maze. Said he has rolled it at night”. Then Kevin suggests to Prof (team lead/manager) that Conti-Maze negotiation should be handled by Stern himself as he is more experienced. He then says Maze will take 25-30%. It seems that Prof contacted developers of Maze and managed to get the ransomware build which was later given to Conti reversers to figure out how it works and build a locker “not worse than Maze, and even better”:
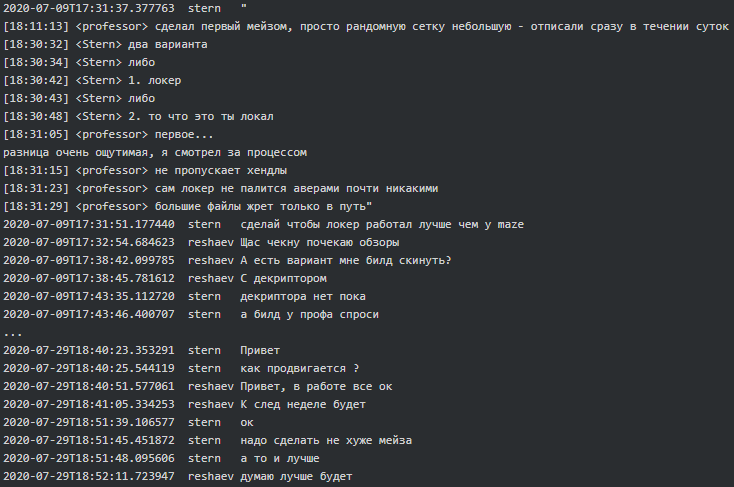 |
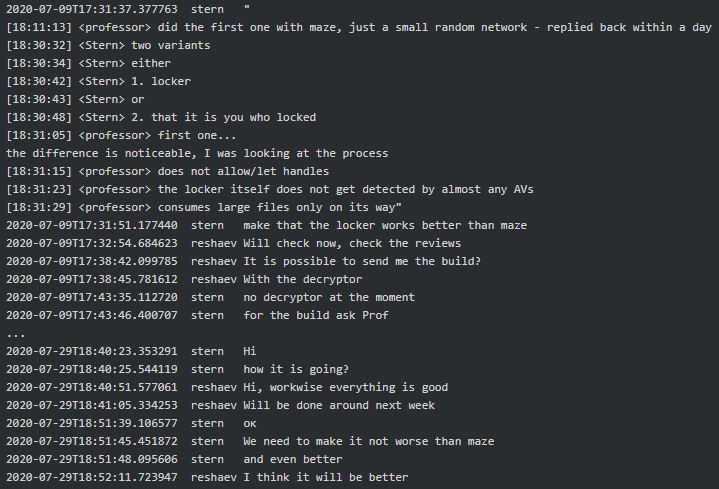 |
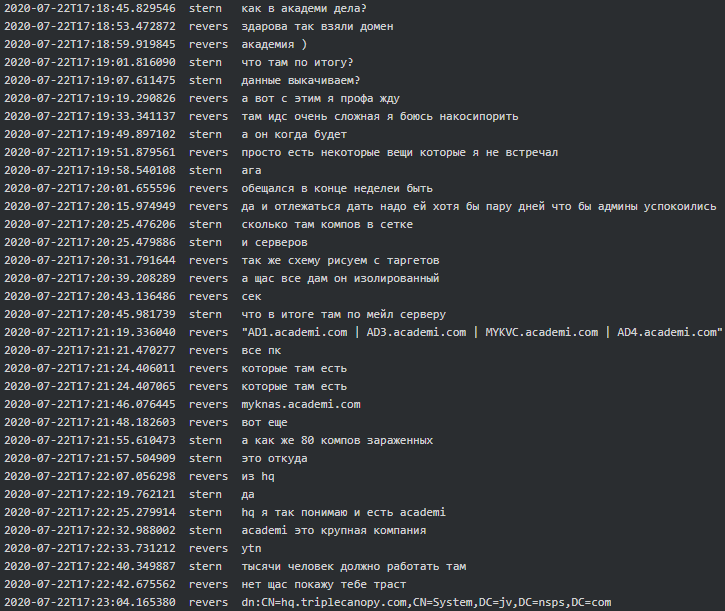
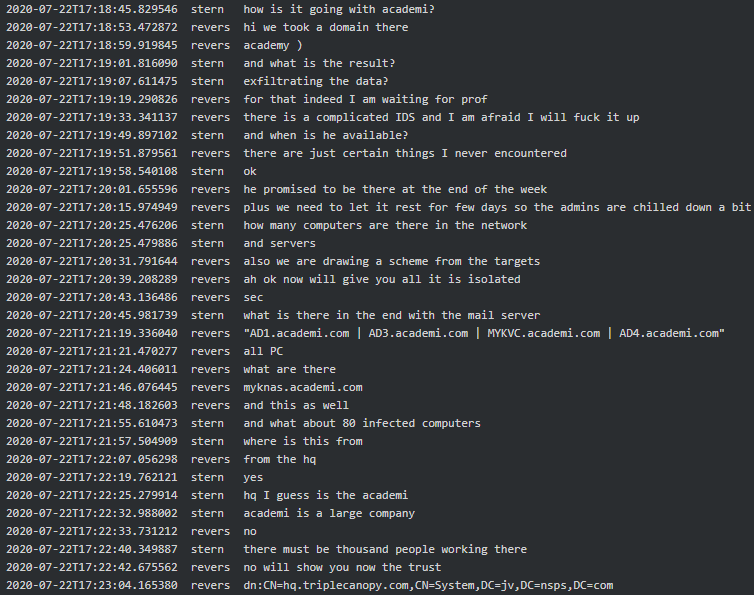
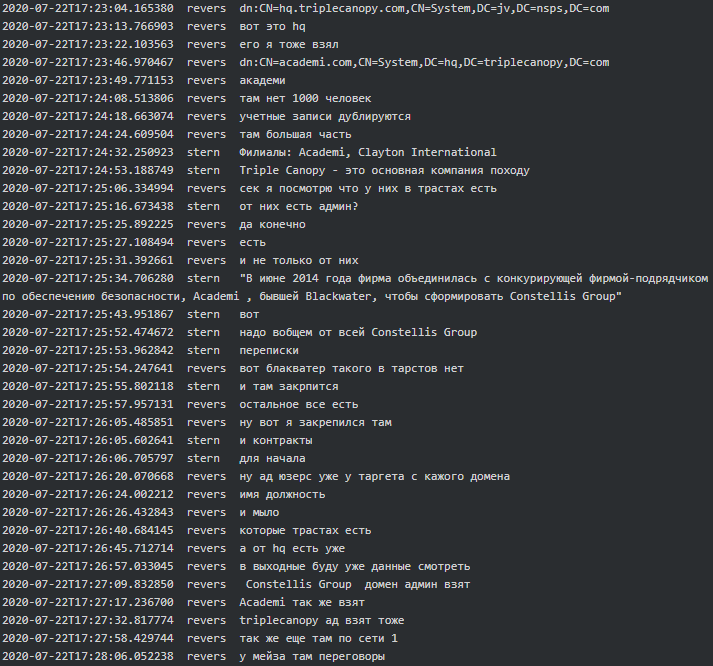
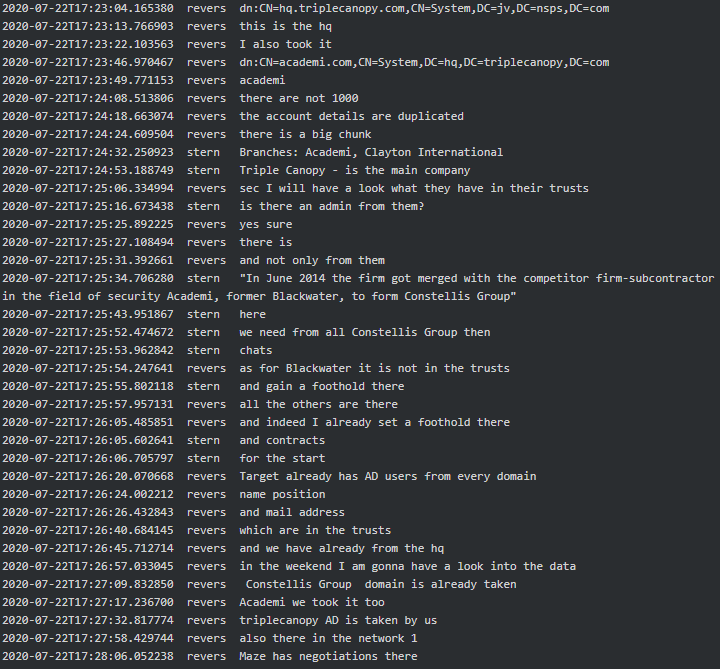
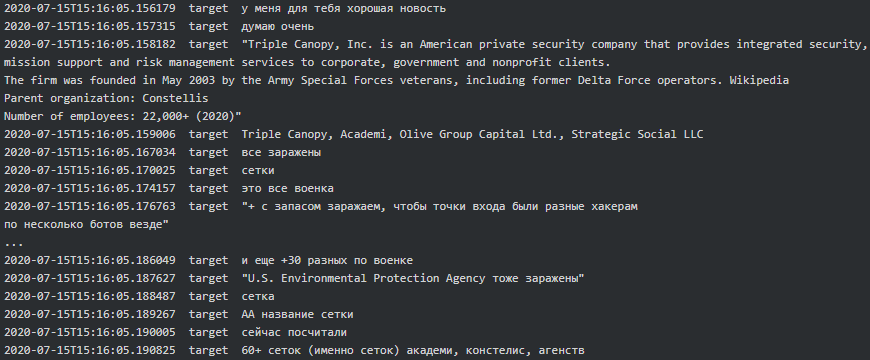
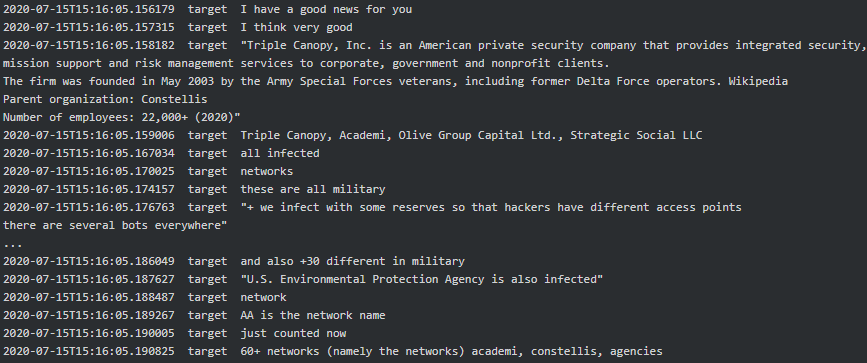
When it comes to Conti-Maze victims, it seems that both were involved in hacking Academi (former Blackwater), a U.S. private military company who provides services to CIA. “We [expletive] Academi for almost a year” says Target to Dandis (tester). Academi and the affiliated Triple Canopy, Olive Group Capital Ltd, Strategic Social LLC and Constellis Group were all infected/hacked around mid-July 2020 and Maze had negotiations in one of the victim’s networks. Stern informed his subordinates that they are primarily looking for chats, contracts, PII, emails and accounting and that the request seems to be originating from one of the two ‘offices’ (see above, the chat where they mentioned Cozy Bear). Target reports to Stern they infected 30+ military companies along with some agencies, one of which is The US Environmental Protection Agency:
 |
 |
 |
 |
 |
 |
Conti-Netwalker
Mid-April 2021 Stern asked Bentley and Professor to add Netwalker’s jabber account to their contact list. In mid-2020, Trellix wrote an in-depth blog on Netwalker explaining not only their malware but how we uncovered a large portion of their funds. In January 2021, Law Enforcement managed to takedown the Netwalker’s dark web site and arrested an affiliate based in Canada. After these interventions, it got really quiet arround Netwalker. Given the appearance date of the Netwalker moniker within the Conti jabber server, it is possible that Netwalker affiliates found a new home within the Conti group.
According to Stern, Netwalker will use the TrickBot botnet to distribute their malware. Bentley was in charge of onboarding Netwalker to their admin panel, VNC, etc. and providing them with tested LNK/XLS files with payload to use in their campaigns. It looks like there was friction in the beginning of the collaboration and Netwalker did not get the promised bonus from Stern, and Stern did not like that Netwalker was passing the Citrix’es given to him to other parties:
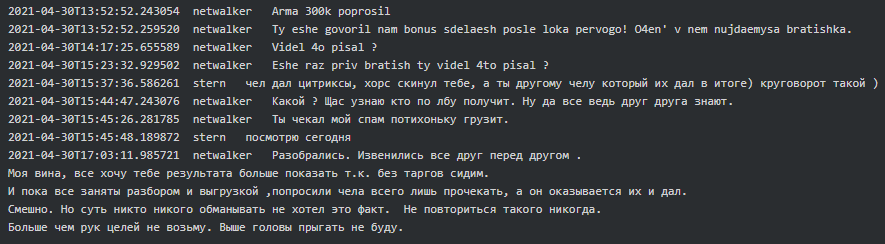
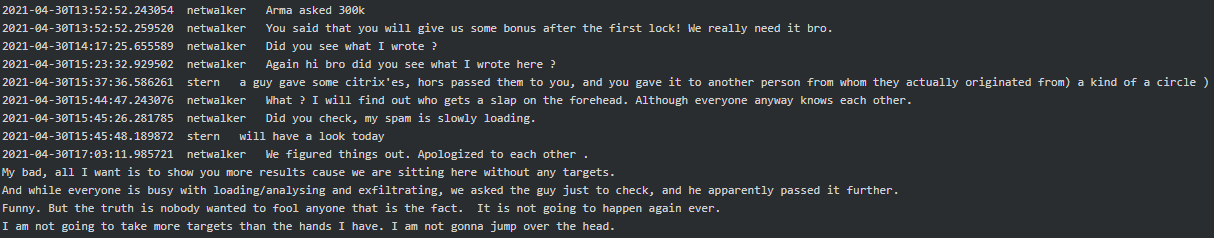
Later in May 2021 Netwalker provided Stern the details of their two potential victims, Blackbaud, Inc. and Ellsworth Adhesives, and asked him to pay to his team as they worked hard:
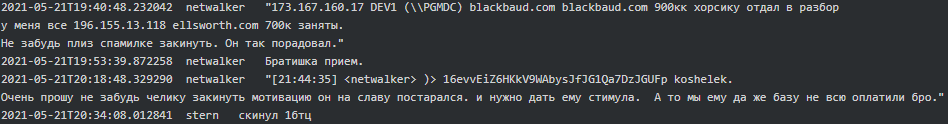
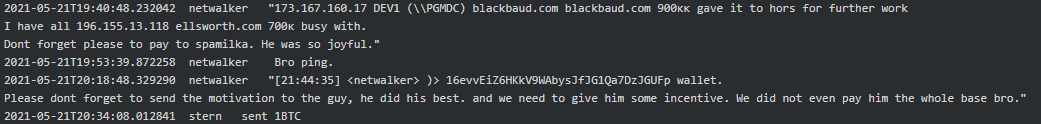
Blackbaud, Inc. disclosed that they indeed paid ransom to the perpetrators but never mentioned who they actually were nor the amount of ransom they paid.
Conti-Lockbit
There is a hint of Conti-TrickBot potentially collaborating with LockBit group. At the beginning of November 2021, Defender (manager) said to Stern that the account Brom was (re)created in Group 6 for LockbitSupp (an alias strongly associated with LockBit ransomware group):
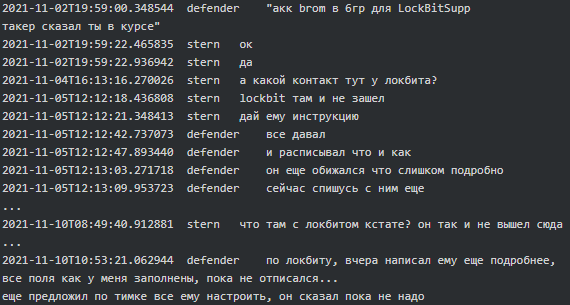 |
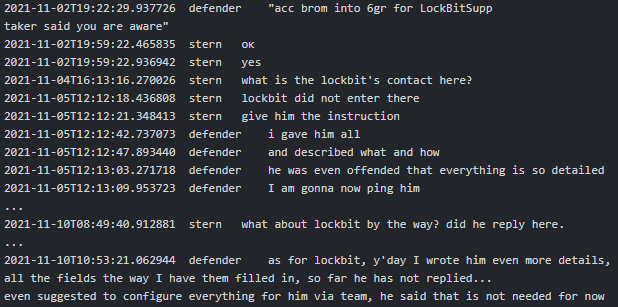 |
Two weeks after, Mango (team lead/manager) told Stern that there was misunderstanding with LockBit and asked him about the percentage of networks and revenue they will take from LockBit in case of successful collaboration:
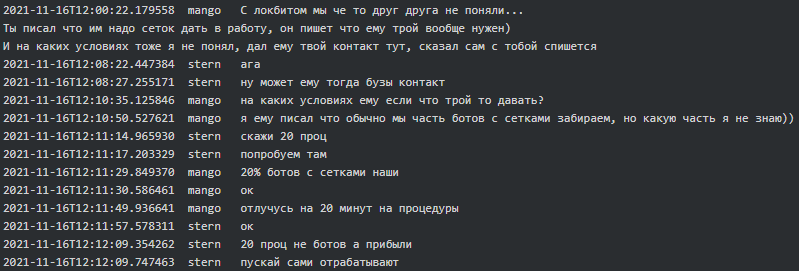 |
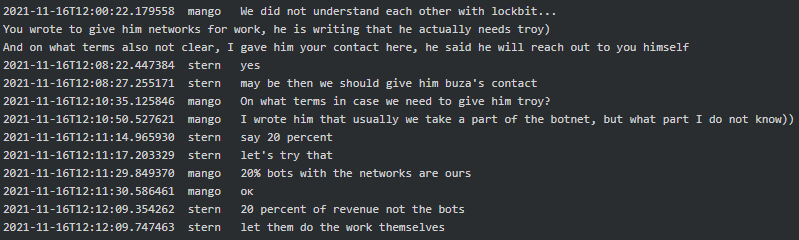 |
TrickBot, Buer, Amadey and IcedID
On June 26, 2020, Taker (tester) who just began the conversation with Stern asked questions around what TrickBot was and how it got started. “It started as a banking bot, gathering logs, logins, and passwords. It was a financial matter” replied Stern. Later in October 2020, Target said to Troy, “They managed to connect Cobalt, Bazar and TrickBot together. They figured that TrickBot is us.” On the August 19, 2021, Professor got furious when somebody mistakenly included the TrickBot module designed to not infect CIS countries into Diavol ransomware (aka Conti) build, which allowed security researchers to attribute TrickBot and Conti teams to the same threat actor:
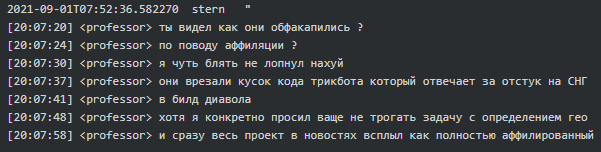 |
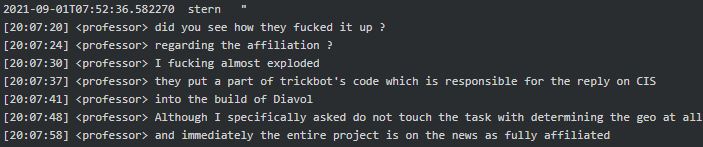 |
Amadey and Buer were also mentioned multiple time in Conti chats as alternative loaders. In June 2020, Price (coder) said to Target, “Hof referred me to a hacker forum, I got access to it (for money) and copied Buer’s entire ins and outs from there.” As for Amadey loader, it looks that Conti team bought it and every time Amadey required a ‘re-crypt’ they would pay for that.
Furthermore, Leo (coder) from Conti gang appears to be the creator of IcedID loader which in May 2021 was ‘on the first place among infections’:
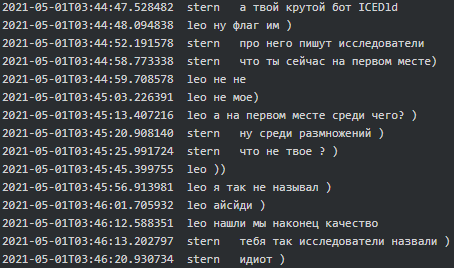 |
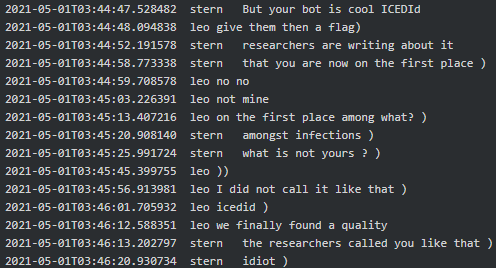 |
Conti’s victims: NGO, Medical institutions among others
We went through the Conti leaked messages and compiled a list of their potential victims which mainly includes EU and U.S. entities across various sectors. Most of the 103 potential victims we have identified were located via a Zoominfo URL Conti used to check a company’s size and revenue to determine a ransom amount to ask. “Found a way of buying a Zoominfo account, 2 managers for Buza, for his pricing research, the price is 2k” advised Mango to Stern. Later Stern said to Mavelek (coder/tester), “@ali has a script to check domains on Zoominfo to get data on number of employees and the revenue of the company.”
Between 2020-2022 Conti and its affiliates targeted and potentially attacked twelve healthcare organizations (clinics, hospitals, care houses including UHS, Prodemica, Geo Group), five educational institutions (schools, colleges, universities, etc.), a charitable organization, a governmental agency, and numerous companies in financial, retail, business services, manufacturing, and other industries:
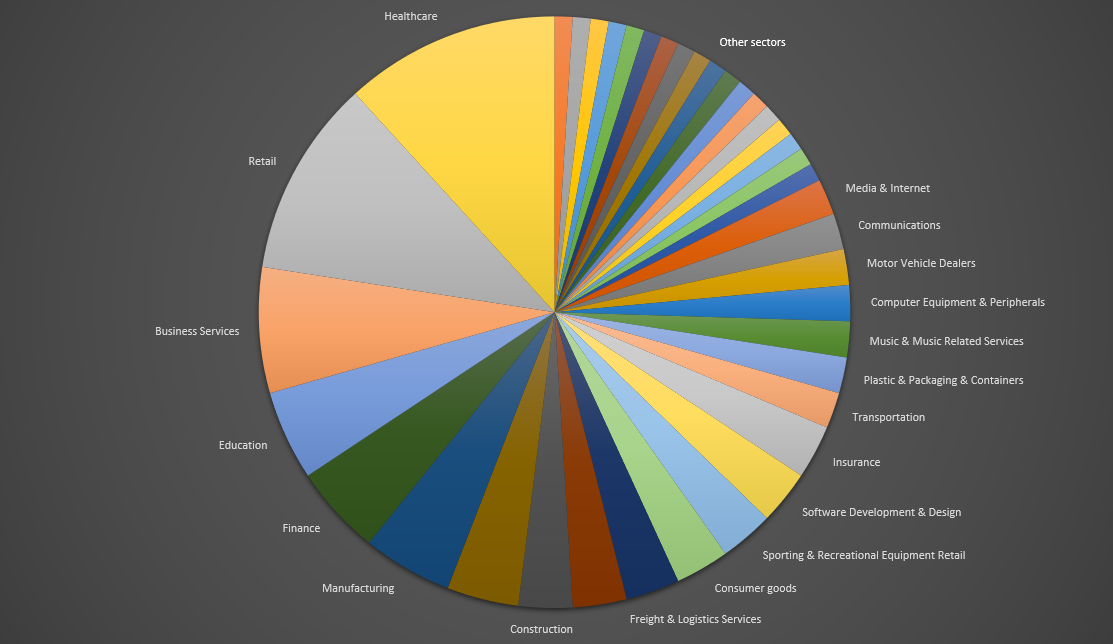
Call center services
Among other departments, Conti has a team of callers. A caller is required to have a good knowledge of spoken English (level B2-C1) and between age 18 and 25. They are recruited by Conti’s HR team to work remotely for ‘an online store’ abroad. The callers earn $450-500 a month (salary increases by $100 - $200 - $300, depending on the success of the call-centre), working hours are 18:00-2:00 Moscow time (correspond to usual working hours in Western hemisphere), and they receive paid holidays but get no official contract as per the Labour Code.
Below are Mango’s messages to Stern where he suggests some improvements around blackmailing/call-center and explains a concept which is ‘more or less’ working for them:
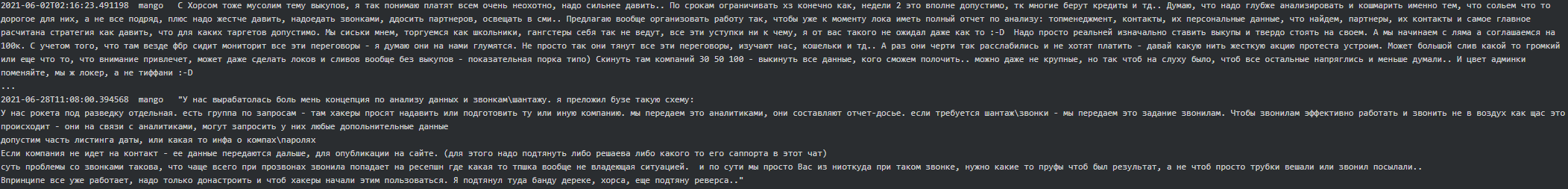
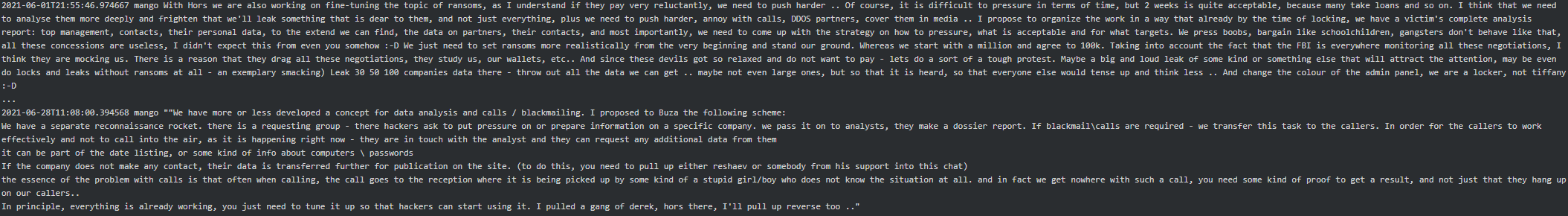
Here is a call sample from Conti’s caller to one of their victims, curtesy of Northwave Security:
Conti call sample.mp3
Cybercriminal entrepreneurship (crypto and Forum)
By end of May 2021 Stern instructed Mango to get in touch with the administrators of exploit forums to see if they were willing to sell to Conti. “Also get a list of forums which can be considered for sale. XSS - find out a list of active users, per day, week, month. The same for Antichat and WWH,” continued Stern. Later Mango replied that WWH had laughed out loud at their offer and that hxxp://korovka32xc3t5cg[.]onion and hxxp://crdclub4wraumez4[.]onion were available for sale. However, he advised those forums are rubbish, a hotbed of grifters, and instead of trying to buy a forum they should create one on their own. The following is Mango’s suggestion to which he got a ‘go-ahead’ from Stern:
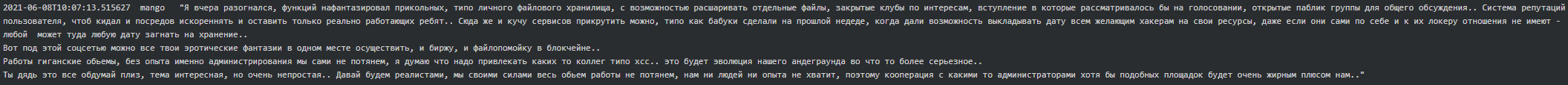
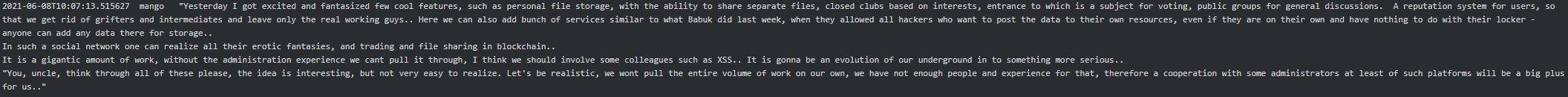
In July 2021, Mango sent two design suggestions for the social network (aka forum) to Stern – one in dark-green and another in dark-blue color schemes. Stern approved the dark-green variant for the forum and suggested it was ready to make it available with a minimum functionality:
 |
 |
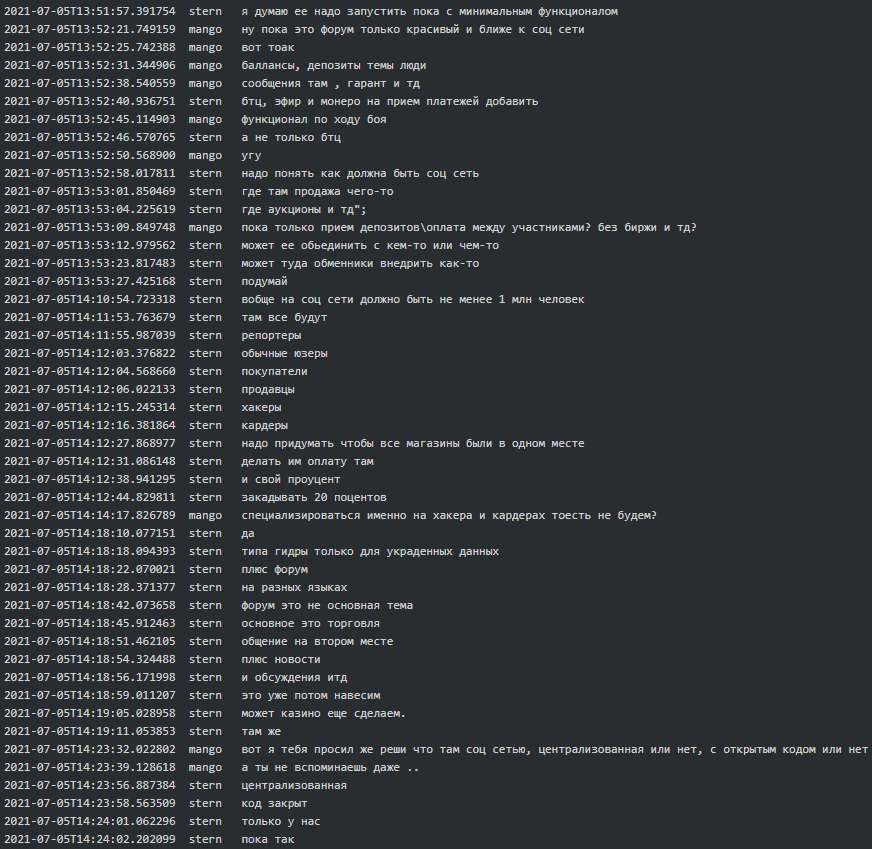
Below are the conversation extracts between Stern and Mango, full of entrepreneurial spirit, where they brainstorm what functionalities the forum should have and what might potentially work for it and what might not:
 |
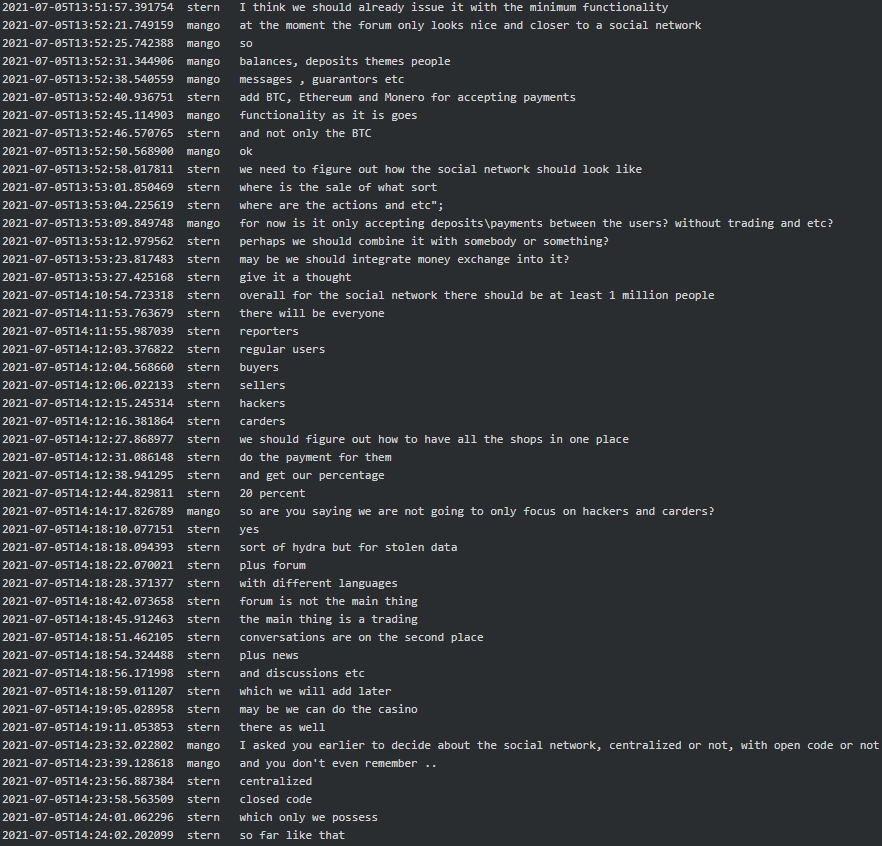 |
Later Mango suggested a potential domain for the forum and a logo for it: “matryoshka[.]space (already with the domain:)) and as a logo matryoshka but angry, in our color scheme, dark-green, and may be draw a laptop next to it. In principle matches the theme. We are one big system amongst the multiple other sub-systems in one place. And it is clear that it is a Russian theme. It is going to be cool, and easy to remember, I think it will resonate with everyone”.
Purchase of Carbon Black and SonicWall
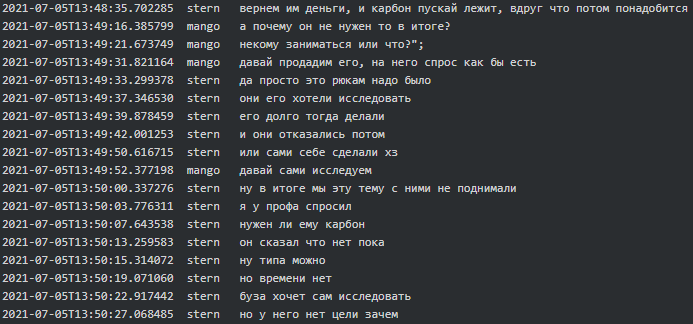
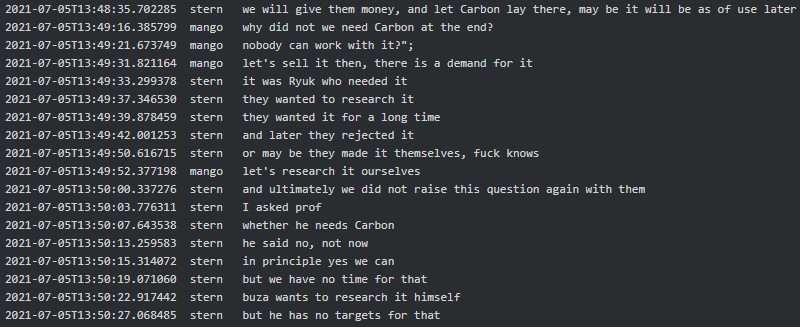
In March 2021 Stern said to Defender that he needs Carbon Black AV. In April 2021 Mango asked Professor if 60k (currency is unknown) is a lot for Carbon, 30k for the firm who buys and 30k for the Carbon itself for 250 PCs. A week later it seems that Mango managed to purchase Carbon Black via a firm in France for 14.8k euros (plus 20% for BTC conversion and 30k for the firm as promised). However, Stern did not take Carbon Black AV and in July 2021 Mango asked him why they aren’t doing anything with Carbon Black to which Stern replied that originally Ryuk needed it and now for some reason they no longer do:
 |
 |
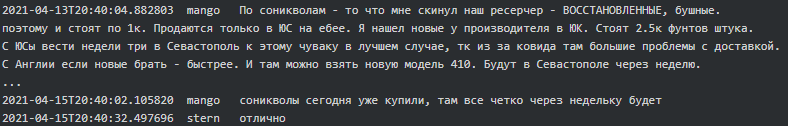
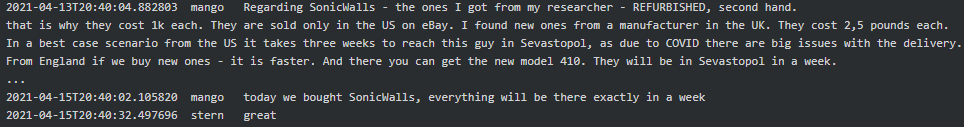
In February 2021 Stern said to Swift (tester/coder) that he also needs SonicWall solution. He broadcast to all the contacts in Jabber “Who can figure out the vulnerability in SonicWall and make a working scanner for it?” to which Ghost (tester/coder) replied “This one, CVE-2020-5135: Critical SonicWall VPN Portal Stack-based Buffer Overflow Vulnerability, right?”. The CVE-2020-5135 is a CVSSv3 9.4/10 critical vulnerability which was fixed around November 2020 and according to SonicWall PSIRT there was no exploitation observed in the wild. Mid-April 2021 Mango advised Stern there are several ways to buy SonicWall (even a new model SMA 410) and later that they manage to buy new as well as refurbished ones:
 |
 |
There is not much further information regarding SonicWall, except that in June 2021 Subzero (tester/coder) advised to Stern that he “figured out the SonicWall”.
Conclusion
Financially motivated cyber criminals have a history of collaboration across borders and often stay away from politics. However, the current Russia-Ukraine conflict isn’t one to ignore, not even for cybercriminals, as they are forced to choose sides.
The ContiLeaks and TrickBotLeaks were a direct result of this conflict. The leaks are of an unprecedented level and show the world how a government backed, multimillion-dollar ransomware gang operates. In some fashion it was almost like a normal business; wages needed to be paid, software licenses obtained, customer service initiated, and strategic alliances had to be formed. However, make no mistake, this business is dealing in top level cybercrime, with a strategic alliance to an intelligence apparatus responsible for several nation-state attacks.
In our line of work, we are often aware of technical innerworkings, partnerships between malware families and suspected nation state relationships but reading the internal conversations and having our suspicions confirmed was very insightful.
RECENT NEWS
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
-
Oct 28, 2025
Trellix AntiMalware Engine secures I-O Data network attached storage devices
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.