Zero Trust Strategy
Don’t just assume breach, prevent it.
Accelerate your Zero Trust implementation with Trellix.
Zero Trust Strategy is a must-have
for good security hygiene
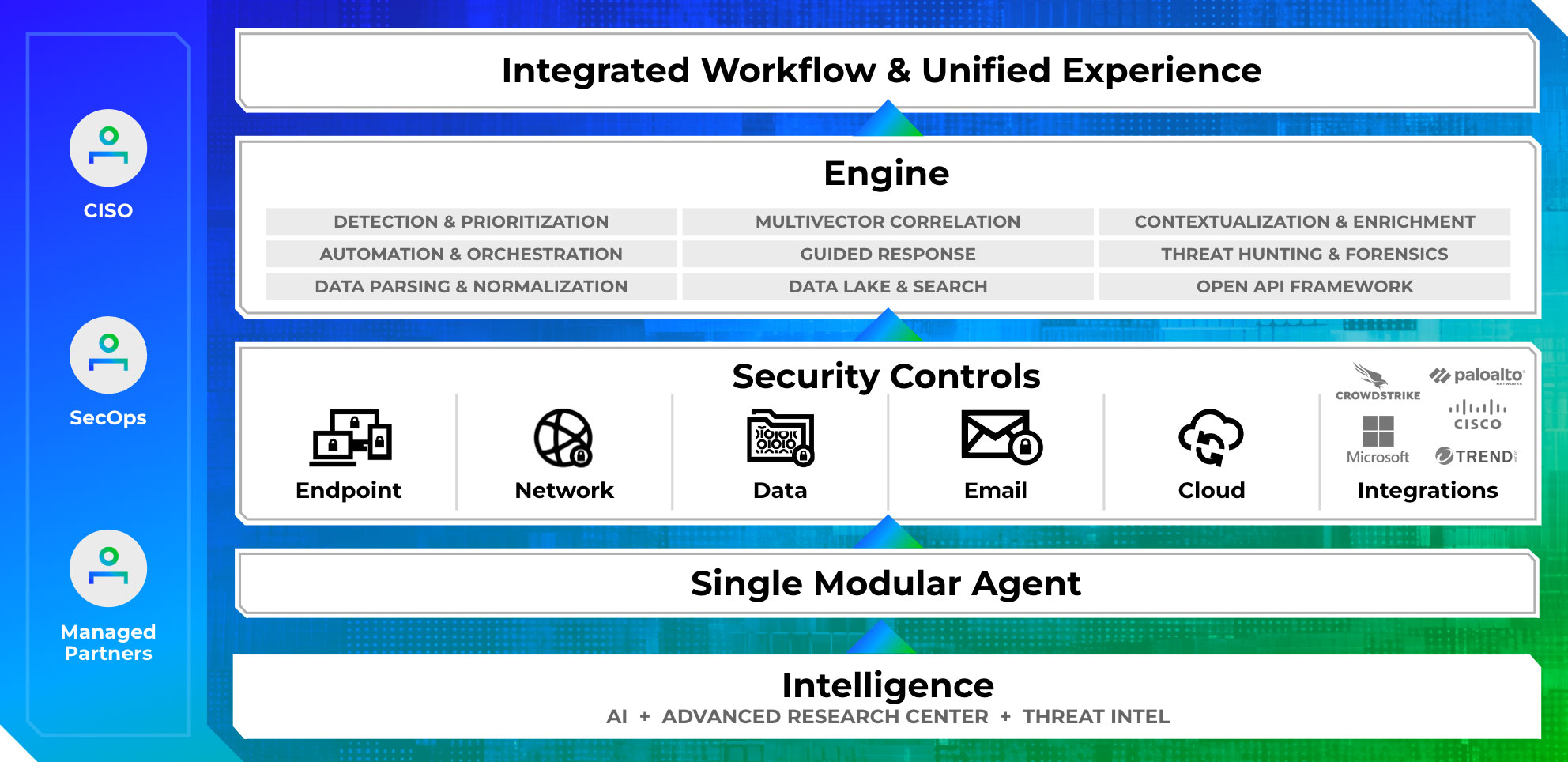
Implementing Zero Trust Strategy requires visibility into endpoint activity, email messages, network traffic, cloud security posture, data security, and many other sources. Only Trellix offers an AI-powered security platform with unparalleled visibility across native security controls and third‑party integrations.
The Trellix advantage
- Increase your visibility and harden your environment against attacks with multi-vector, multi-vendor threat correlation.
- Discover and eliminate blind spots with open integrations, rapid data ingestion, and a single console for your SecOps team.
- Get global, real-time insights into emerging threats from millions of sensors, over 40,000 customers and an elite team of threat researchers.
- Reduce mean time to detect (MTTD), investigate (MTTI), and respond (MTTR) with ML-guided investigations, automated responses, and SecOps playbooks.
- Simplify your environment by consolidating with Trellix native security controls for tighter integrations, reduced alerts, and simplified management.
- Leverage integrations with leading Identity Access Management providers to create context around insider threats, credential theft, or privilege escalations.
Stay secure with the Trellix Platform
The Trellix Security Platform improves and adds to your Zero Trust framework with an open platform that integrates multiple components and correlates data whether you use Trellix native solutions or third‑party tools.