GetSusp
The tool of choice when analyzing a suspect computer
GetSusp (incorporates GetQuarantine)
Trellix GetSusp eliminates the need for deep technical knowledge of computer systems to isolate undetected malware. It does this by using a combination of heuristics and querying the Trellix Global Threat Intelligence (GTI) File Reputation database to gather suspicious files.
GetSusp is recommended as a first tool of choice when analyzing a suspect computer. However, one must follow the existing Trellix support process for escalating suspicious files it finds.
GetSusp includes the following features:
- Delivered as a single executable file with no installation required
- Option to run in several modes—GUI, command line and ePO mode
- Scans URLs, Documents, PDFs in GUI mode
- Option to select files before submitting to Trellix in GUI mode
- Leverages GTI File Reputation to determine if the sample is suspicious
- Records system and installed Trellix product information date of execution and details of suspected files
- GetSusp supports Windows Server 2008 R2 SP1, Windows Server 2012, Windows Server 2016 and Windows 7, 8, 8.1, 10 (up to RS6), 19H1, 19H2, 20H1, 20H2, 21H1, 21H2 and Windows 11
GetQuarantine (Integrated with 32-Bit GetSusp ePO)
Trellix GetQuarantine is an ePO deployable tool. It has been integrated with the Getsusp tool and can be downloaded from the download section below.
- All the GetQuarantine command-line options can be used in the same way as before, however they must be preceded by the "--quarantine" switch.
- The combined ePO binary can be used to run the tool (GetSusp & GetQurantine) separately. Furthermore, this tool can also be used to execute both GetSusp and GetQuarantine together (for GetQuarantine, the command line switch --quarantine is required).
The build should be downloaded and deployed via ePO using command line settings that are identical to those for quarantine, but preceded by the "--quarantine" switch.
Tool Options
Mandatory
Customer email address, used for communicating submission outcomes. Example: --email= email address
--Quarantine-folder
Optional
Quarantine folder location. Default is c:\Quarantine
Example: --Quarantine-folder= quarantine folder path
--Proxy-server
Optional
Network proxy server IP or FQDN. Example: --Proxy-server= Proxy server IP/FQDN
--Proxy-port
Optional
Network proxy server port. Example: --Proxy-port= port number
--Config-script
Optional
Proxy auto configuration file URL (if any). User can either use proxy server and IP combination or PAC file. Example: --Config-script=PAC file URL
Upon successful submission, the customer will receive an acknowledgement to the email address supplied during tool execution.
The tool stores logs at location c:\ProgramData\McAfee\GetQuarantine\log.txt.
Download
GetSusp Binary:
The latest version of GetSusp. When prompted, choose to save the executable file to a convenient location on your hard disk. We recommend creating a folder specifically for GetSusp File.
* Integrated with GetQuarantine
How to use GetSusp
Once GetSusp File is downloaded, launch the GetSusp.exe.

The Trellix GetSusp Interface will be displayed
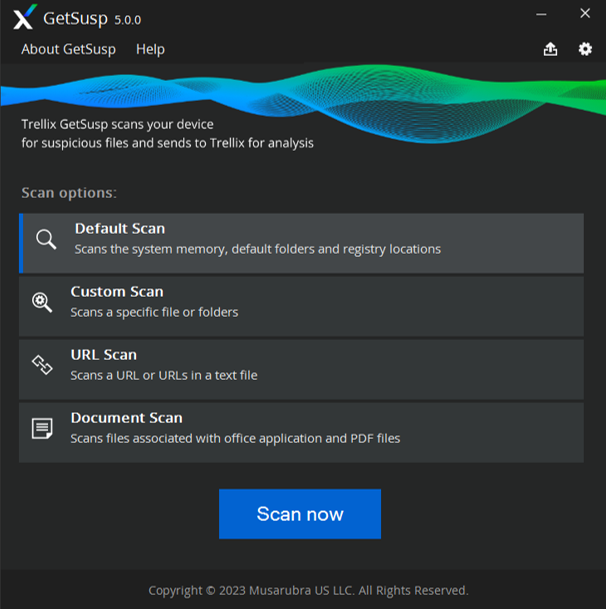
For a list of Frequently Asked Questions on GetSusp, see article KB 69385.
Building a Culture of Security
Businesses have too much to lose if they don't prioritize security at every entry level. With more data to protect and cyberthreats evolving, everyone must play a part in creating a culture of security. Let our Free Tools help implement a security-first mindset across your entire company.
Need a little more protection for your business?