Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Shaping the Future with Trellix Data Security
By Laurie Robb · February 20, 2024
How do you address problems like insider threats and ransomware that can lead to data breaches? How do you speed up compliance activities like reporting and auditing that take too much time today? Is there a way to better understand what information needs protection as your data footprint expands? And how can you streamline tools and manage resources when everyone is short-handed?
These are big questions. They don’t have easy answers, but we can try to tackle them together. That’s why we’re introducing you to Trellix Data Security in 2024. Is Data Security a new concept? No. But we’ll be taking a fresh look at our products, our packages, and how we solve the big (and small) problems that challenge our customers.
What Is Data Security?
One thing we can agree on is that no one agrees on what’s included in a Data Security solution or Data Security Platform (DSP). Definitions vary between vendors, industry analysts, and thought leaders.
For our purposes, let’s say that Data Security solutions should:
- Find and classify sensitive and proprietary information (data)
- Monitor and control how data is shared
- Detect data anomalies
- Enable action when data events are detected
- Deliver reporting, auditing, and forensics on data activity
- Provide coverage across the locations where data is created, shared, and stored
What Is Trellix Data Security?
Our solution combines three key sets of products: Trellix Data Loss Prevention (DLP), Trellix Data Encryption, and Trellix Database Security to provide exceptional visibility across information leakage vectors and deliver comprehensive controls to protect the data that matters. Trellix Data Security checks the boxes listed above to keep information from being exposed on endpoints, through email, on the web, and across network storage locations, while safeguarding devices from unauthorized access.
How Is Trellix Changing?
We’re focused on your challenges and the outcomes you need to achieve. In the past, we probably shared a menu of products to communicate how we could help you. Maybe it was a list of capabilities within that product so you could decide what you wanted. Rarely, did we make a connection between products, capabilities, and real-world problems. We expected that everyone would just connect the dots.
Going forward, we want to identify your biggest challenges and share how we’ve designed a solution to help. We’ve made our offerings more flexible, simplified our product structure, and ensured we have a set of solutions that answer the questions we posed above. While you might not notice big changes right away, we hope our transition to focusing on your use cases will create a better fit long term.
Concerned about insider threats? We can show you how we:
- Identify and classify sensitive data
- Monitor for and prevent exfiltration
- Coach users with explanations, prompt for justification, and block unauthorized activity
- And, control access to devices and data no matter where the user is located
Is compliance too slow and manual? Let’s explore your options for:
- Out-of-the-box rules and policy options aligned with regulatory frameworks
- Scanning and capture to support auditing and forensics
- Reporting - regular and ad-hoc/event-based
- And, audit and forensic investigation records that contain needed evidence
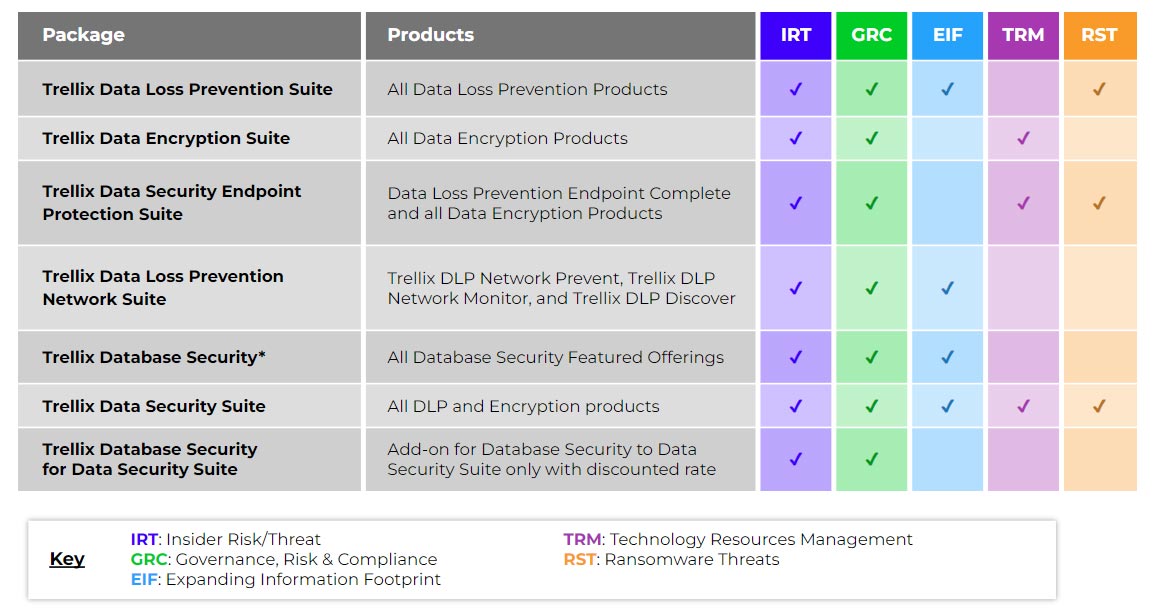
This matrix illustrates how we’ve updated Data Security product packages to address some of the biggest industry challenges.
Taking the Next Step
The secret to every successful Data Security program is understanding your organization. For example, Trellix experts can conduct workshops with new and existing clients so we can identify your challenges and opportunities before recommending the right solution. A workshop can help cross-functional teams better understand how to build a thriving Data Security program and position your organization for long-term success.
If you don’t feel like your current technology and processes do enough to protect your sensitive and proprietary data, it might be time to get a new perspective. If you already have Trellix solutions but feel like they could be doing more for you, let’s find out. Wherever you are on your journey to keep your data safe, consider us your ally. Reach out today and ask how we can help you.
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
