Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Cyber Threats Targeting the US Government During the Democratic National Convention
By Anne An · October 2, 2024
Introduction
Trellix global sensors detected increased threat activities during the days that the Democratic National Convention (DNC) was held in August 2024, culminating into a massive spike in detections halfway through the convention. Our data indicate that these threat activities targeted a wide range of US government organizations, including regional democratic causes, state legislative offices, legislative data centers, election boards, local law enforcement agencies, and public transportation networks.
As we count down the weeks until the November 2024 presidential election, some US states have already started early voting. Vote-by-mail and absentee ballots also began to circulate across the country. The upcoming presidential election could be a very close race. What is at stake is the outcome of the high-stakes US presidential election, which would set US foreign policy over the next four years, particularly on issues such as the Russia-Ukraine war, the trade relationship with China, and the Israel and Hamas conflict.
As a result, nation-state-sponsored threat actors are motivated to pursue their political goals by influencing the US presidential election. The US Federal Bureau of Investigation issued a statement in August 2024 revealing that Iranian threat actors have attempted to compromise former President Trump’s campaign and gain access to sensitive information related to US elections. Nearly a decade ago, Russian threat actors compromised computer networks and election-related organizations during the 2016 US presidential election, with evidence based on a US law enforcement indictment.
Our telemetry data during the days of the DNC shows these threat activities primarily focused on discovery, defense evasion, and privilege escalation. This indicates that threat actors were likely interested in gaining access to information from US government organizations and elections while remaining undetected on networks. Our data also identified multiple spear-phishing attempts targeting state legislative offices from both Republican and Democrat alike during the DNC. These threat attempts likely capitalized on the major political convention to compromise US political organizations involved in campaigns and elections.
Escalating Threats Targeting the US Government During the Democratic National Convention
Trellix telemetry shows that one of the largest spikes in cyber threat activities on August 21, 2024, exactly during the middle of the Democratic National Convention (DNC), compared to detections throughout the last six months. Our telemetry data shows more than 11 million detections of malicious activities against US government organizations in that single day on August 21, exceeding the daily average detections by 55 times.
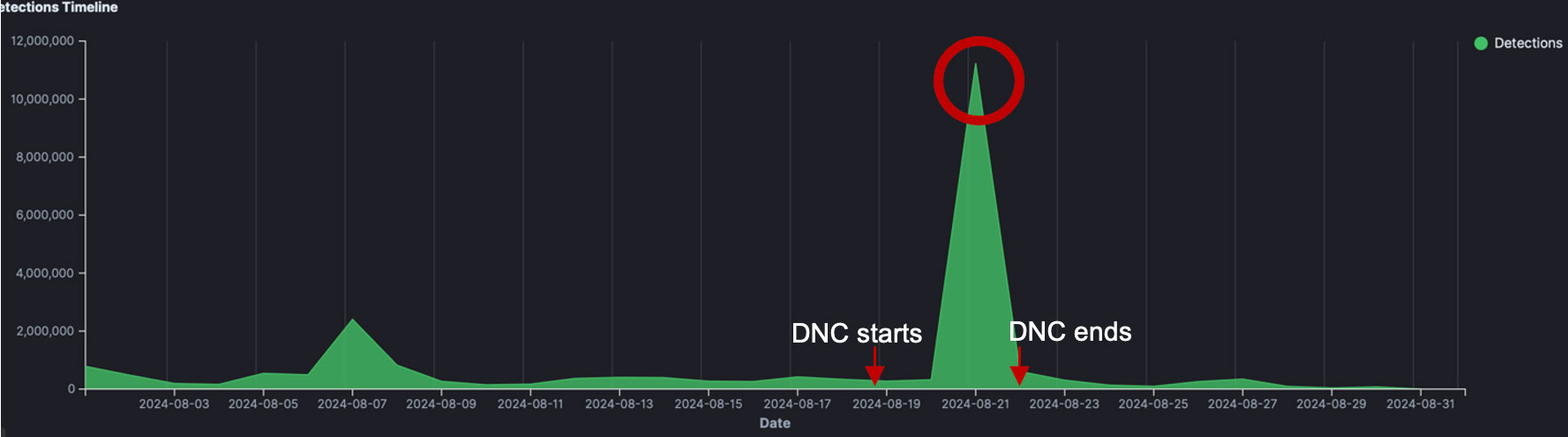
A portion of the malicious cyber threat activities detected by Trellix global sensor networks on August 21, 2024, were directed at the geographical locale of Chicago, where the DNC took place, as well as the city’s public transportation networks. Many DNC participants were expected to use the public transit to attend the political event due to street closures and congested traffic.
We also observe thousands of cyber threat events targeting regional democratic caucuses, legislative data centers, boards of elections, and police departments in various states on August 21, 2024, including Chicago, California, New York, South Carolina, and Pennsylvania. A federal government agency directly involved in US elections was also one of the targets, accounting for over 10,000 detections specifically against the organization on August 21, 2024.
Increased threat activity directed at US government entities during the DNC may suggest that threat actors are interested in exploiting sensitive information about US elections, such as campaign strategies, campaign finance, legislative services, internal communications, constituent information, etc. There is usually an elevated level of email communications between election-related organizations during major political events such as the DNC, so threat actors are likely leveraging the timing and opportunity to gain inside information about the upcoming national and local elections. Threat actors also may find it easier to blend into the email traffic during the time. Government staff are also likely to be more inclined to respond to phishing or malicious emails and less likely to identify suspicious emails due to the sense of urgency during this fast-paced period in American politics.
Targeting Tactics, Techniques, and Procedures
Trellix telemetry data indicate that threat actors targeting US government entities during the DNC primarily used information stealers, Cobalt Strike, and remote access Trojan tools.
Our data also shows that attack methods leveraged by threat actors targeting the US government during the DNC were largely focused on defense evasion, discovery, and privilege escalation. Threat actors appear to leverage compromised credentials to gain higher-level permissions on a system or network, likely intending to explore a network or database of interest. Throughout the process, attackers employed a variety of techniques, including attempting to operate undetected by leveraging trusted processes to masquerade their threat activities, disabling or modifying security software to avoid possible detection, removing non-native files dropped or created on a system during an intrusion to reduce their footprint.
Based on Trellix detection data, the following tactics, techniques, and procedures (TTPs) were utilized to target the US government organizations during the DNC. These adversary techniques are mapped according to the MITRE ATT&CK framework.
Initial Access – T1566.001: Spearphishing Attachment
Initial Access – T1078: Valid Accounts
Execution – T1059.001: PowerShell
Execution – T1047: Windows Management Instrumentation
Privilege Escalation – T1055: Process Injection
Privilege Escalation – T1078: Valid Accounts
Defense Evasion – T1140: Deobfuscate/Decode Files or Information
Defense Evasion – T1112: Modify Registry
Defense Evasion – T1562.001: Disable or Modify Tools
Defense Evasion – T1070.004: File Deletion
Defense Evasion - T1027: Obfuscated Files or Information
Defense Evasion – T1055: Process Injection
Defense Evasion – T1027.002: Software Packing
Defense Evasion – T1078: Valid Accounts
Credential Access – T1003.001: LSASS Memory
Discovery - T1083: File and Directory Discovery
Discovery - T1057: Process Discovery
Discovery – T1082: System Information Discovery
Discovery – T1012: Query Registry
Discovery -1069.002: Domain Groups
Exfiltration – T1567.002: Exfiltration to Cloud Storage
Impact – T1490: Inhibit System Recovery
Impact – T1486: Data Encrypted for Impact
Sample Phishing Emails Targeting State Legislative Offices
On August 21, 2024, in the midst of the DNC, we identified a phishing email sent from a legitimate email account at state legislative office A to three other recipients in state legislative office B in another state. As shown in the image below, the sender from state legislative office A sent an email titled “2024 NLSSA ANNUAL CONFERENCE,” along with two attachments--one appears to be legitimate, and the other attachment was malicious and attempted to redirect to a malicious website: hxxps://qrco[.]de/bd1mCc.
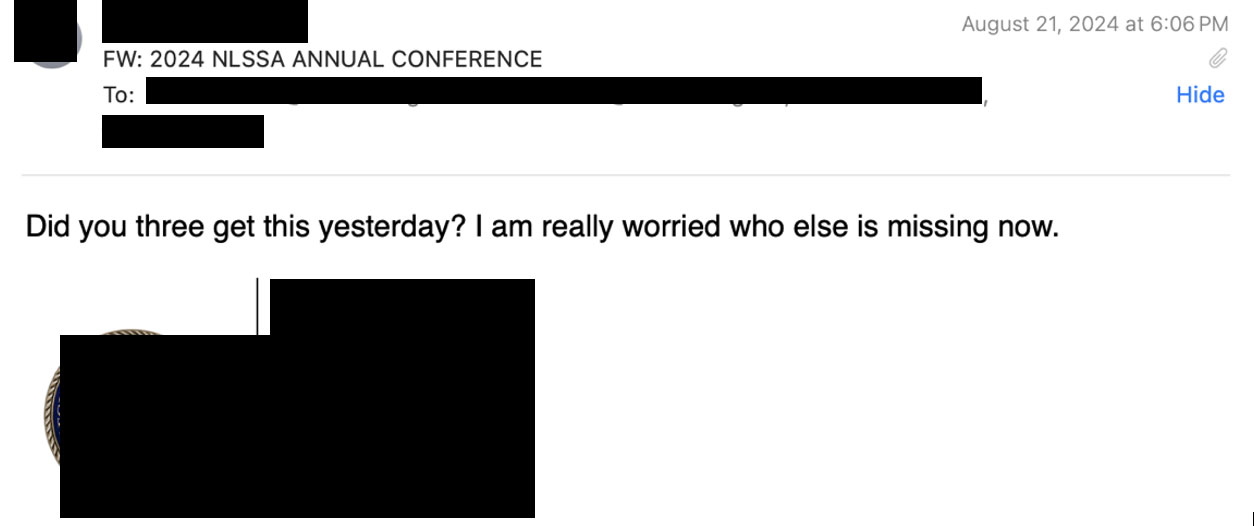
In this case, threat actors could have impersonated the email sender at state legislative office A using their legitimate official email, then the threat actor sent the phishing email with a malicious attachment. If this is the case, the threat actors would likely have compromised the networks of state legislative office A and conducted phishing attacks using compromised valid accounts.
Another possibility is that state legislative office A’s staff member somehow got hold of a malicious document and unknowingly shared it with state legislative office B. In this case, a threat actor might not have access to the staff member’s account. Both possible scenarios suggest that state legislative offices A and B may have been targeted, with some networks compromised.
In addition to this example, we observed other phishing attempts targeting state legislative office B during the exact timeframe of the DNC. Threat actors used the legitimate email account of state legislative office B’s Human Resources Department to send a malicious email to multiple staff members—one at a time. One of the emails was titled: “Staff Payroll for August 2024 Remittance” and contained a malicious link that would redirect the recipient to a malicious phishing website: hxxps://cf-ipfs[.]com/ipfs/bafkreiet7olwidaqbs7ankqng2zcc2o4gmsabav6u2ni24ttnvmnlrxgnq.
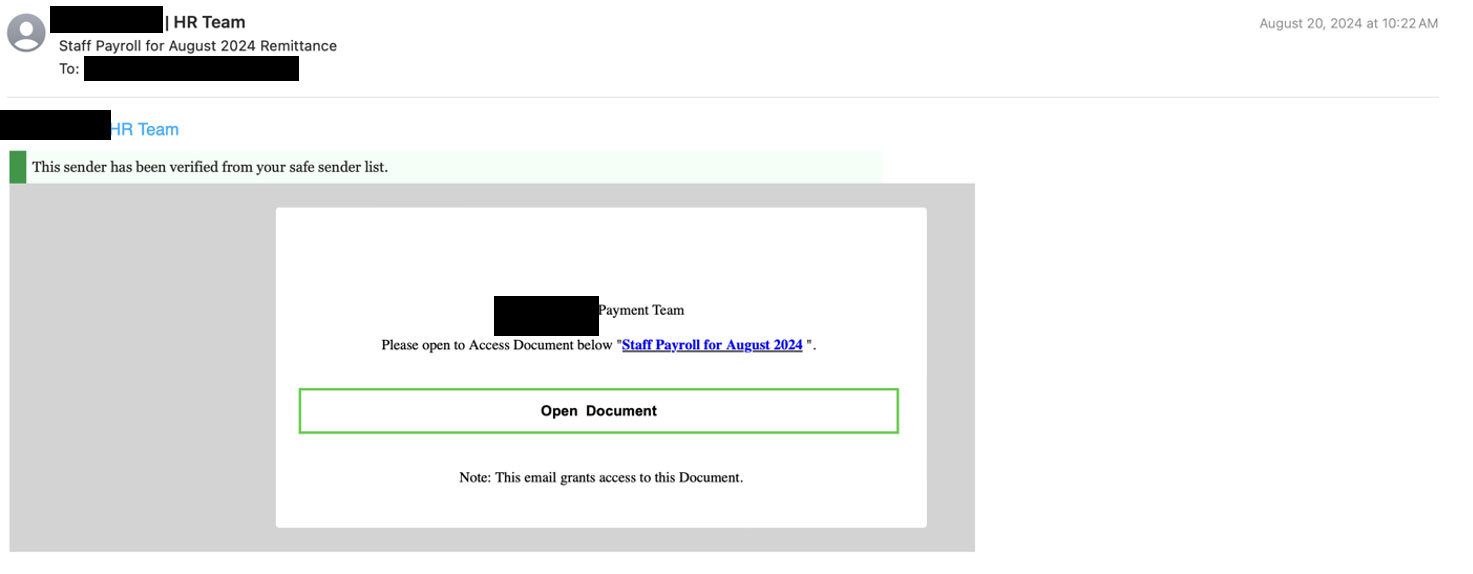
The importance and relevance of the above-mentioned state legislative offices A and B is that there will be state legislative elections held in their states in November 2024, alongside the 2024 presidential election. In particular, state legislative office A is a significant battleground for the Democratic Party. State legislative office B is also important for the Democratic Party as a state it would like to flip to the Democrat side due to its history of favoring Republican candidates.
Conclusion
Threat activities targeting state and local legislative offices, federal and regional election administrative offices, organizations involved in the Democratic National Convention, and other election-related authorities, if successful, may allow threat actors to leverage the data to manipulate, influence, or interrupt upcoming elections in November 2024. For instance, cyberattacks targeting public transit networks may delay the voting process or prevent voting from taking place. Similarly, cyber threats to state and federal law enforcement agencies on election day may impede their ability to respond to physical threats while securing polling booths and ballots. Additionally, attackers may compromise voter registration databases through phishing attempts to cause confusion or postpone voting.
The elevated threats against US government organizations--including local legislative offices, state-level electoral boards, law enforcement agencies, and public transportation networks--during the Democratic National Convention are concerning for the upcoming US elections in November 2024. While Trellix cannot verify whether these threat activities occurring at the Democratic National Convention were part of a coordinated campaign or separate cyber incidents, it is evident that cyber threats have escalated during a major national political convention and will likely continue to evolve as the November elections approach.
Securing and safeguarding free and fair elections are critical to American democracy. As the 2024 US presidential election is quickly approaching, cyber threat activities targeting election-related information and entities involved in the elections are likely to increase. Cyber threat actors have capitalized on a major political event and will continue to look out for opportunities to achieve their objectives.
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
