Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
The Bug Report – May 2023 Edition
By Mark Bereza · June 7, 2023
Why am I here?
In the film The Number 23, Jim Carrey masterfully portrays Walter Sparrow, a man who finds himself obsessed with the number 23 after coming upon a book detailing the 23 enigma, and begins to see it everywhere he looks, driving him to madness. As editor and semi-regular author of the Bug Report, my prior sympathy for Walter’s plight has evolved into empathy, as I find myself endlessly haunted by countless CVE numbers—I even see them when I close my eyes. This is but a small price we pay to heroically deliver to you the most important CVEs month after month via this publication.
This month, of course, is no different. April showers bring May flowers, but what do May flowers bring? If you said “pilgrims,” you’re wrong.

This May brought us three critical, exploited-in-the-wild vulnerabilities, including one you may have overlooked if you were judging solely on CVSS score (and not on our expert opinions, for shame):
- CVE-2023-28771: Zyxel Firewalls
- CVE-2023-2868: Barracuda Email Security Gateway
- CVE-2023-24932: Secure Boot
CVE-2023-28771: Burned by your own firewall
What is it?
For many enterprises, the risk of fully remote exploitation is mitigated somewhat by placing important corporate resources on an internal network, itself gated behind a firewall and accessible from the wider internet only via secure channels like VPN. If your intranet is a trendy nightclub, your firewalls and VPN servers are the bouncers, making sure only the coolest cats (members of your org) can get in. Following this analogy, we were distressed to learn that Zyxel Networks’ bouncers have been sleeping on the job and letting all sorts of shady characters into the VIP area.

Discovered and responsibly disclosed by TRAPA Security, CVE-2023-28771 is an OS command injection vulnerability that affects Zyxel’s ATP, ZyWALL/USG, USG FLEX, and VPN line of products, constituting just about every firewall and VPN device in their product catalogue. According to Zexel’s security advisory, this vulnerability is a result of “improper error message handling,” and allows attackers to achieve RCE on affected products by sending malicious IKEv2 packets (a protocol widely used by VPNs) — all achievable with zero authentication.
Who Cares?
According to Shodan, the owners of over 66,000 affected products likely care. Bear in mind that there may also be many more devices that aren’t internet-facing, but still accessible (and thereby vulnerable) via VPN.
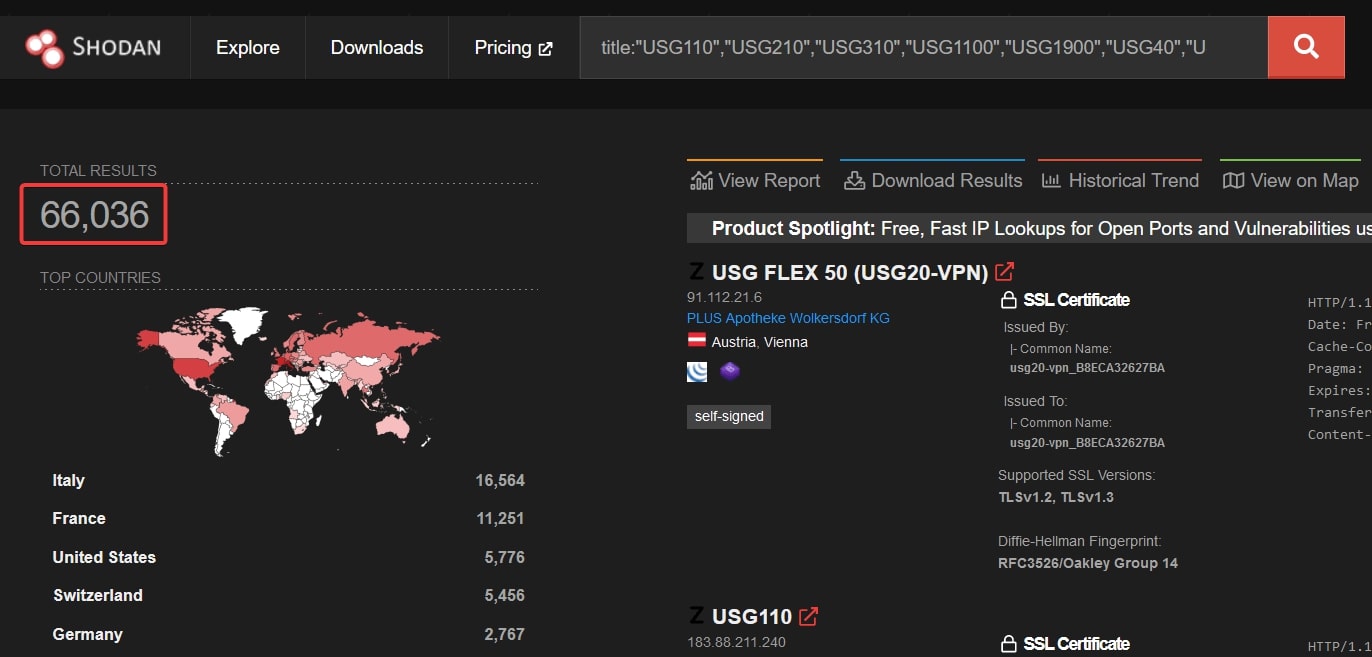
Zyxel themselves markets these products to “small or mid-sized business users,” meaning that although this isn’t going to bring down the Fortune 500 overnight, the threat surface and potential impact is nevertheless substantial. Unfortunately, unlike tax breaks, threat actors don’t overlook the little guys, and CISA reported widespread in-the-wild exploitation of this CVE right at the end of May. Given the reported ease of exploitation, extensive threat surface, and the existence of publicly available PoC code, this was more or less inevitable. Among other exploitation activities, Shadowserver reported on Twitter that threat actors were leveraging CVE-2023-28771 to build a Mirai botnet, typically used for distributed denial-of-service (DDoS) attacks.
What can I do?
As of April 25, Zyxel has released patches that mitigate this vulnerability for all affected products. To determine if your organization is using an affected product/firmware version, consult the following table from Zyxel’s security advisory:
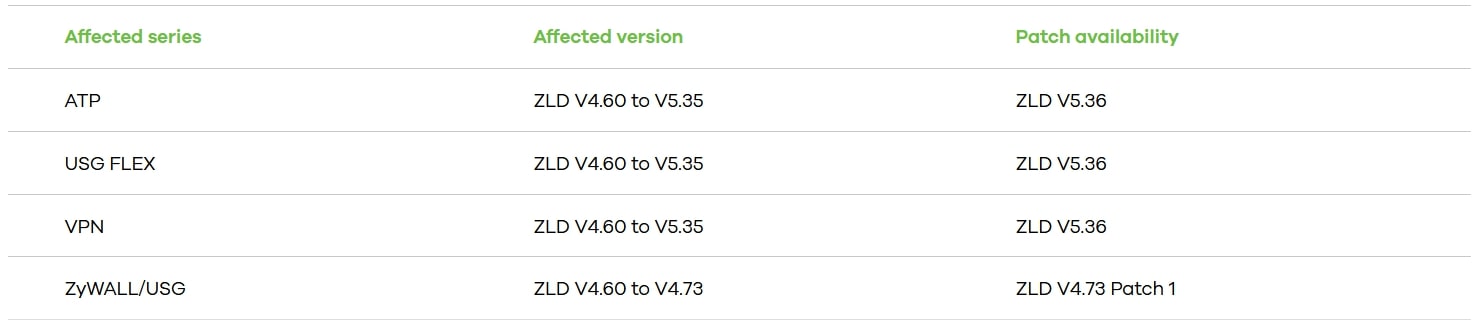
If your device is on the list, your immediate action item is to patch, patch, patch. Those looking to detect exploitation of this vulnerability at the network level will want to inspect IKEv2 traffic sent to destination UDP port 500. The joy of inspecting traffic in real time for a protocol that’s encrypted by design is left as an exercise for the reader.
CVE-2023-2868: Barracuda servers receiving fishy traffic
What is it?
Spring is a time of renewal and awakening. Just as the winter snow recedes to uncover the budding flora underneath, so too did the disclosure of CVE-2023-2868 reveal seven months of in-the-wild exploitation of Barracuda Email Security Gateways (ESGs). Just as various critters are roused from their lengthy hibernation, so too did the infamous 20+ year old cd00r backdoor revive in the form of three new malware variants. In retrospect, I really wish the groundhog spotted its shadow a few more times this year.

Like our previous bug, CVE-2023-2868 is another command-injection vulnerability, this time affecting Barracuda Network’s ESG appliances, whose primary purpose is to (somewhat ironically) protect organizations against “inbound malware, spam, phishing, and Denial of Service attacks.” According to Barracuda’s security advisory, the vulnerability is the result of improper sanitization of email attachments, specifically .tar files. By specially crafting the file names within an attached archive, a malicious actor can exploit this vulnerability to achieve RCE completely unauthenticated.
Who Cares?
If you’re one of more than 200,000 organizations worldwide who utilize Barracuda products, you should probably care. To make matters more dire, most ESG installs will be vulnerable, as the CVE affects devices dating back four major versions (5.1.3.001 through 9.2.0.006) in their default configurations. Somewhat tragically, Barracuda themselves make a compelling case for the extensive impact such an exploit can have in their article “Cost of an email attack can on average exceed $1 million.” You heard it straight from the fish’s mouth.
For organizations utilizing Barracuda ESG, the risk of compromise is far from hypothetical. Although Barracuda has not disclosed the precise scale of exploitation, they have detected exploitation in a subset of their install base dating back over seven months and leveraging at least three different malware variants. Attackers have utilized such malware to create backdoors, exfiltrate data, and establish command and control servers, and they’ve had a long time to make themselves at home on your boxes.
What can I do?
This is normally the easiest part of the blog to write. I tell you to patch and we both move on with our lives. Unfortunately, given how much of a head start the bad guys have in this case and the persistence capability granted by the aforementioned exploits, adequately remediating a network compromised by this vulnerability will be a bit more labor-intensive than simply hitting “update.” The good news is that the folks over at Barracuda have done the legwork to make this process a bit easier. Customers whose installations have been determined to be compromised have been notified both directly by Barracuda reps and via the ESG user interface. For those impacted, Barracuda’s security advisory lays out remediation steps, IOCs for all three identified malware strains, and YARA + SNORT rules for detection. Beyond the standard procedure of updating and checking for IOCs, Barracuda suggests nuking affected devices from orbit and replacing them, along with changing any credentials connected to the ESG. It’s a promising start—I just hope Barracuda isn’t notifying affected customers via email.
CVE-2023-24932: (Not so) Secure Boot
What is it?
It’s finally time for this month’s “dark horse” vuln. CVE-2023-24932, reported by Microsoft during May’s Patch Tuesday, has garnered a rather modest CVSS score of only 6.7. We have historically stressed the importance of looking beyond CVSS scores when assessing the importance of vulnerabilities, and CVE-2023-24932 is a perfect example for us to point to and smugly proclaim “we told you so.”
Despite requiring either physical access or admin privileges, this CVE is nonetheless dangerous in large part because of the component it affects: Secure Boot. For those unaware, Secure Boot is a technology utilized in modern Windows operating systems that secures the Unified Extensible Firmware Interface (UEFI, the successor to the BIOS) and other boot software by ensuring each component is signed by the OEM. Compromising Secure Boot allows an attacker to install a bootkit, a piece of malware that infects the UEFI and is loaded before the operating system. In the case of CVE-2023-24932, threat actors have been exploiting it via the notorious BlackLotus bootkit.
Who Cares?
Okay, so the bad guys can use CVE-2023-24932 to install a BlackLotus bootkit on my machine, but they need either admin privileges or physical access to do so—how much harm could they really cause that they couldn’t already with that kind of access? The answer is: a lot. Because the bootkit is loaded before the operating system, BlackLotus has capabilities greatly surpassing conventional malware in terms of persistence, pervasiveness, and evasion. BlackLotus can disable BitLocker drive encryption, bypass detection by Microsoft Defender, and even exploit the kernel itself. Besides being more or less invisible to antivirus software, it can even persist across OS reinstalls. Perhaps the greatest testament to its danger is its asking price on hacking forums: $5,000. That said, it’s still far from the most expensive Black Lotus on the market—that privilege lies with a 1993 Magic: The Gathering trading card that recently sold at auction for $540,000. A bit pricey for a piece of cardstock, but to quote an old friend of mine, “most drug addictions make cheaper hobbies than Magic: The Gathering.” In any case, beyond sharing a name, these two Black Lotuses are similar in that their true value requires a trained eye to discern.
What can I do?
As with the previous vulnerability, the level of persistence granted by exploiting CVE-2023-24932 via BlackLotus necessitates further remediation steps beyond standard detection and patching efforts. Although BlackLotus is difficult to detect via conventional means, it still leaves behind some breadcrumbs, and Microsoft has put out an advisory that outlines how you can identify its various IOCs. If a device is determined to be compromised, the only surefire remediation is to reformat or restore a backup of all system drives (including both the OS and boot partitions). Even if a device doesn’t demonstrate any evidence of compromise, simply updating isn’t sufficient to be protected. The latest Windows update adds relevant protections to the Windows Boot Manager, but these need to be manually enabled after the patch is applied—refer to this Microsoft KB article for more details.
RECENT NEWS
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
-
Apr 29, 2025
Trellix Invests in Customer Resilience with Threat Intelligence and AI-Powered Security
-
Apr 28, 2025
Trellix Recognized for AI-Powered Threat Detection and Response
-
Apr 7, 2025
Trellix Strengthens Focus on Customer Engagement and Regulated Industries with Executive Appointments
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
