Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
The LockBit’s Attempt to Stay Relevant, Its Imposters and New Opportunistic Ransomware Groups
By Jambul Tologonov and John Fokker · April 11, 2024
The Trellix Advanced Research Center has recently observed an uptick of LockBit-related cyber activity surrounding vulnerabilities in ScreenConnect. This surge suggests that despite the Law Enforcement's (LE) "Operation Cronos" aimed at dismantling LockBit's infrastructure, the ransomware operators somehow managed to survive and stay a float. It appears that the cybercriminals group behind LockBit ransomware partially restored their infrastructure and created an impression that the LE actions did not affect their normal operation. Concurrently, alongside the resurgence of LockBit's exploitation of ScreenConnect vulnerabilities, we have seen other threat actors have either impersonated LockBit ransomware or incorporated LockBit into their own cyber attack campaigns.
Trellix has been diligently monitoring LockBit's activity on the darknet. Since the leak of LockBit's builder for LockBit 3.0 ransomware (also known as Black) in 2022, various threat actors have attempted to impersonate LockBit or leverage the leaked Black builder to encrypt organizations' networks and demand ransom. Additionally, there have been instances where threat actors have used LockBit's leaked builder as a foundation for their own ransomware strain or have masqueraded as LockBit Ransomware-as-a-Service (RaaS) operators to target Russian organizations, aiming to tarnish LockBit's reputation.
In this blog post, we will delve into these cases and provide insights into the changes observed since the new activity of LockBit RaaS.
LockBit Imposters
Since the leak of LockBit Black by a disgruntled developer of LockBit in 2022, we have observed numerous threat actors attempting to capitalize on it by impersonating LockBit ransomware and leveraging their well-known brand for their financial gain. Previously we have seen a similar behavior with the infamous REvil gang where REvil imposters tried to leverage their name by revamping the Revil leaksite and modifying an existing REvil binary. Joining the LockBit affiliate program is typically challenging, requiring individuals to prove themselves and establish a reputation before gaining access. However, the leaked LockBit 3.0 provided an opportunity for threat actors to quickly enter the scene, encrypt smaller enterprises, and reap profits without meeting these stringent requirements.
LockBit Black also enabled LockBit's competitors to undermine their reputation by acting on LockBit's behalf and violating the LockBit RaaS rules. By leveraging LockBit's name and operating outside the established affiliate program rules, these actors sought to discredit LockBit RaaS and gain an advantage in the ransomware market.
In December 24, 2023, the Katholische Hospitalvereinigung Ostwestfalen (KHO), a German healthcare network, became the target of a cyber attack, resulting in the paralysis of operations across three major hospitals in Germany. Initially, the attack was attributed to LockBit ransomware, however LockBit later refuted their involvement. In a private TOX chat with vx-underground, LockBit provided the following clarification on the KHO incident:
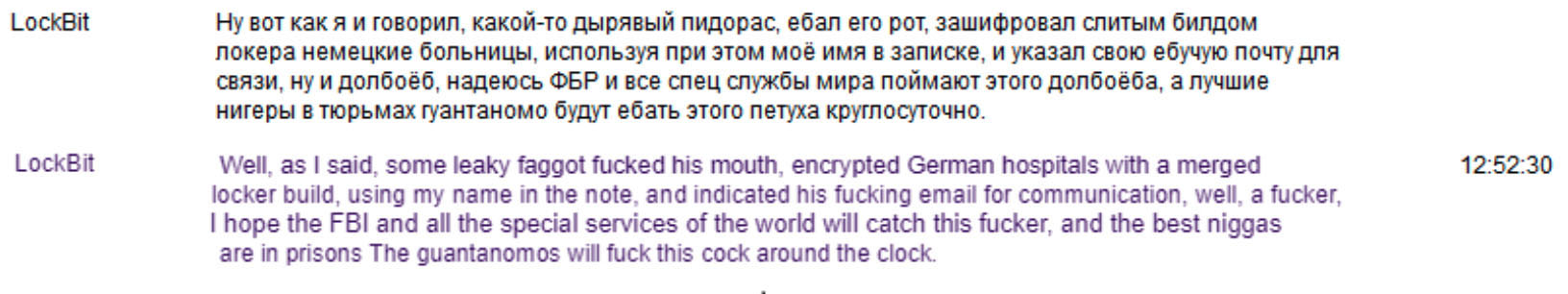
Evidently this cyberattack involved imposters attempting to impersonate LockBit and exploit their brand to enhance their chances of receiving ransom payment.
Another notable example of LockBit’s impersonators has been observed at the end of January 2024 when a Russian security company “AN-Security” was compromised by LockBit imposters who allegedly exfiltrated around 5TB of data and demanded 100 BTCs from the victim organization:
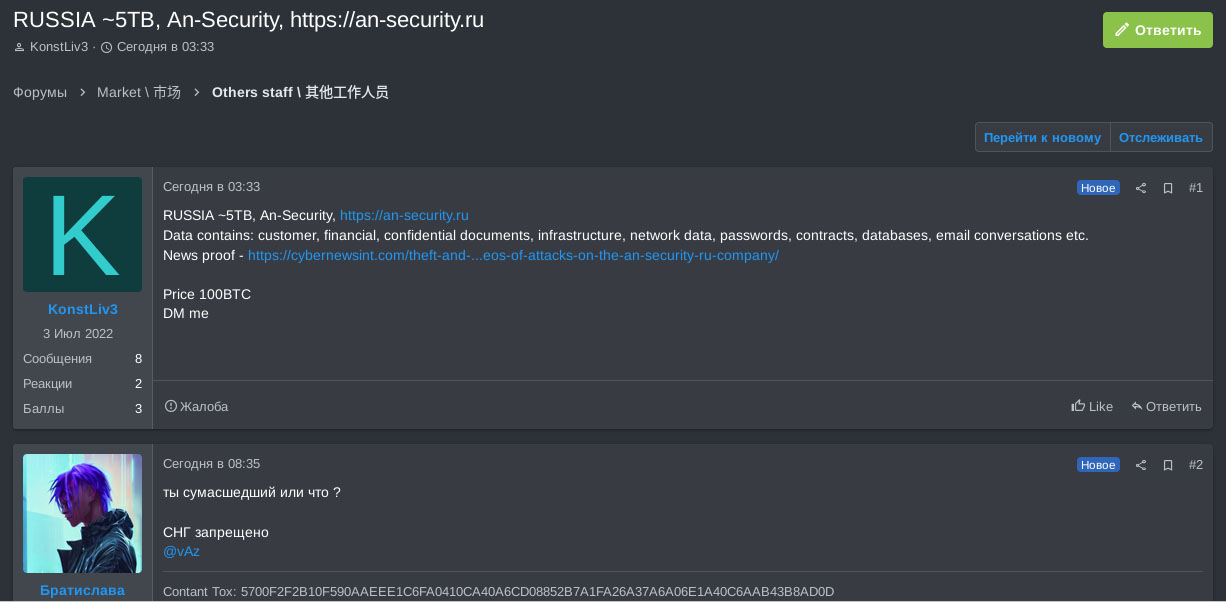
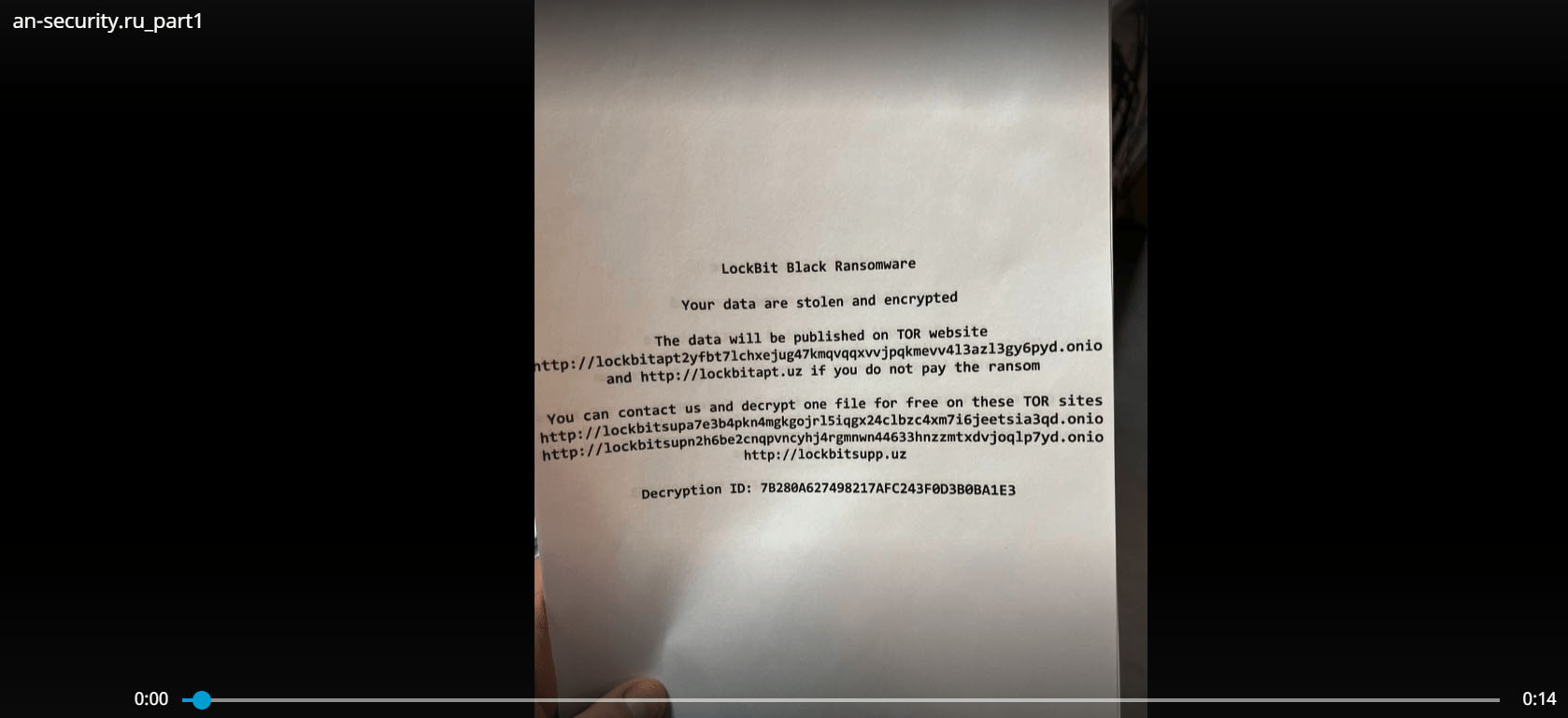
LockBit RaaS admin, LockBitSupp, responded promptly to this incident, emphasizing that LockBit refrains from encrypting companies based in the Commonwealth of Independent States (CIS). Recognizing the severity of the situation, LockBitSupp even extended a gesture of help by reaching out to the affected Russian organization to offer their support:
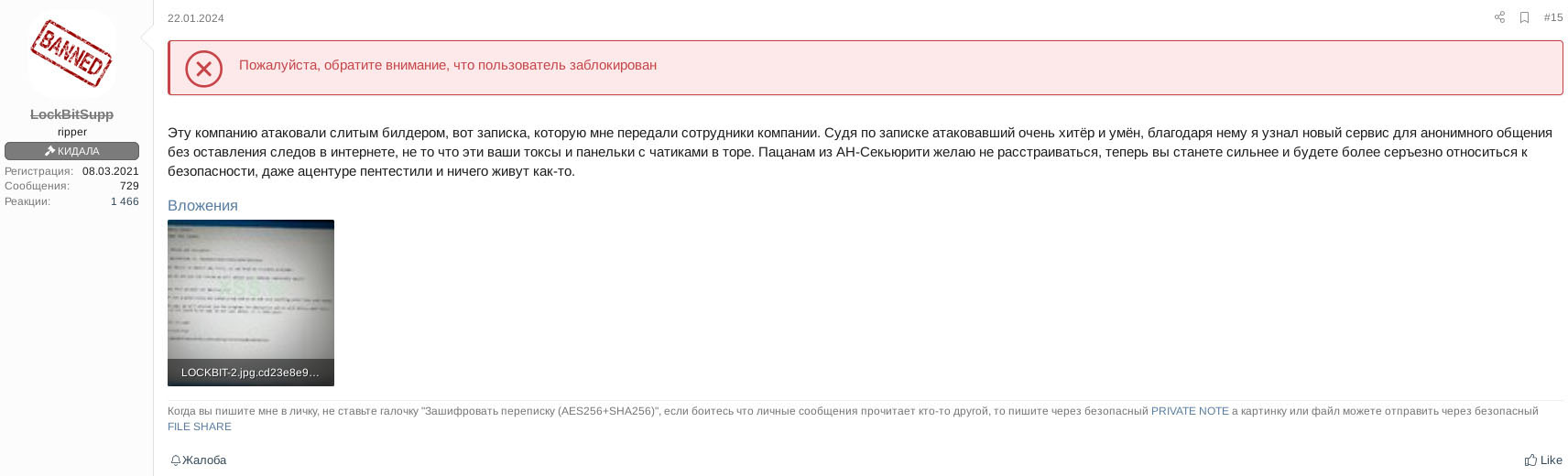
The English translation of the post in Figure 3 as well as the ransom note provided by LockBitSupp are given below:
This company was attacked by a leaked builder, here is the note that the company employees gave me. Judging by the note, the attacker is very cunning and smart, thanks to him I learned a new service for anonymous communication without leaving traces on the Internet, not like these TOXs and panels with chats on TOR. I wish the guys from AN-Security not to be upset, now you will become stronger and will take security more seriously, even Accenture was pentested and somehow they still live.
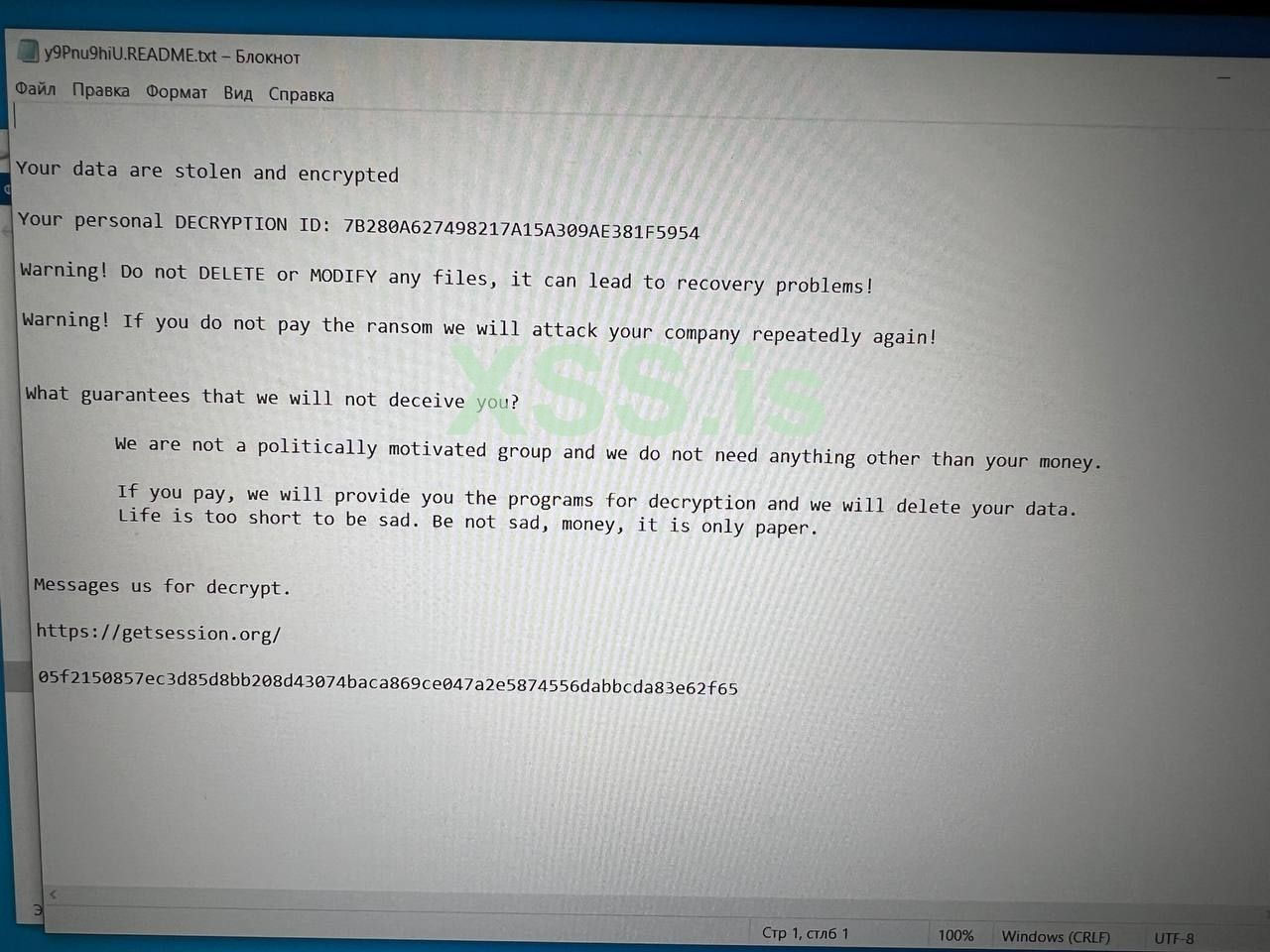
LockBitSupp advised that they found out who attacked the Russian security firm and that it was done by a threat actor Signature who operates & owns Cl0p RaaS. According to LockBitSupp, owner of the Cl0p affiliate program Signature was taking revenge on LockBitSupp in this way for the ban on the “Exploit” forum:
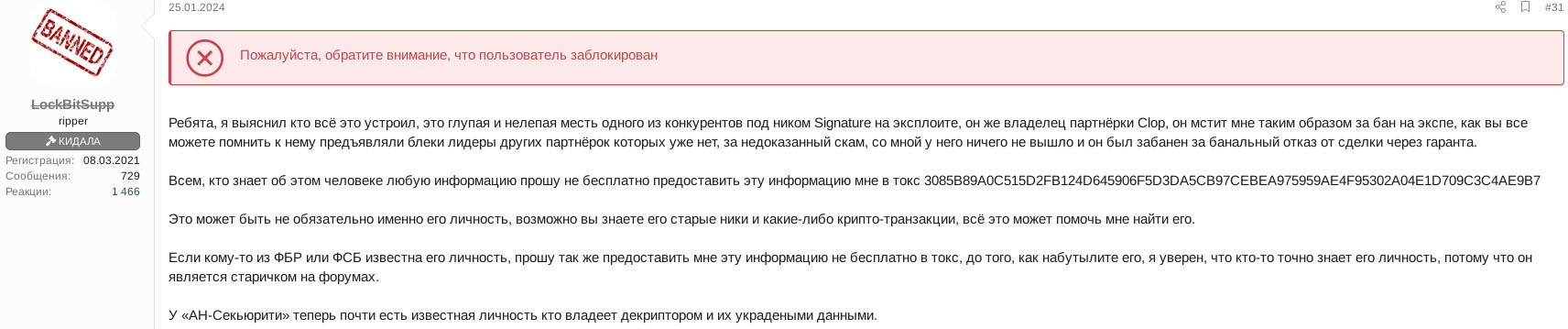
Below is the English translation of the post in Figure 6:
Guys, I found out who arranged all this, this is a stupid and ridiculous revenge of one of the competitors under the nickname Signature on Exploit forum, he is also the owner of the Cl0p affiliate program, he is taking revenge on me in this way for the ban on Exploit, as you all may remember, the leaders of other RaaS programs which no longer exist created Exploit blacks on him for an unproven scam, also with me nothing worked out and he was banned for simply refusing to deal through a guarantor.
Anyone who knows any information about this person, please provide this information to me not for free via TOX
3085B89A0C515D2FB124D645906F5D3DA5CB97CEBEA975959AE4F95302A04E1D709C3C4AE9B7
This may not necessarily be his identity, perhaps you know his old nicknames and any crypto transactions, all these can help me find him.
If anyone from the FBI or FSB knows his identity, please also provide me with this information, not for free via TOX, before you get him, I am sure that someone knows his identity for sure, because he is an old fellow on the forums .
AN-Security now has almost all details of the person who owns their decryptor and their stolen data.
This shows that imposters of LockBit are not only using the leaked builder for their financial benefits, but also attempting to discredit LockBit RaaS and tarnish their reputation, ultimately weakening their position in the ransomware landscape.
Another instance of LockBit imposters was documented by Trend Micro in November 2023. Security researchers were able to capture a screenshot of the imposter's name-and-shame site hosted at http://lockbitblog[.]info. Notably, this site closely resembled the design of the original LockBit leaked data site, indicating an attempt by the imposters to mimic LockBit's brand:
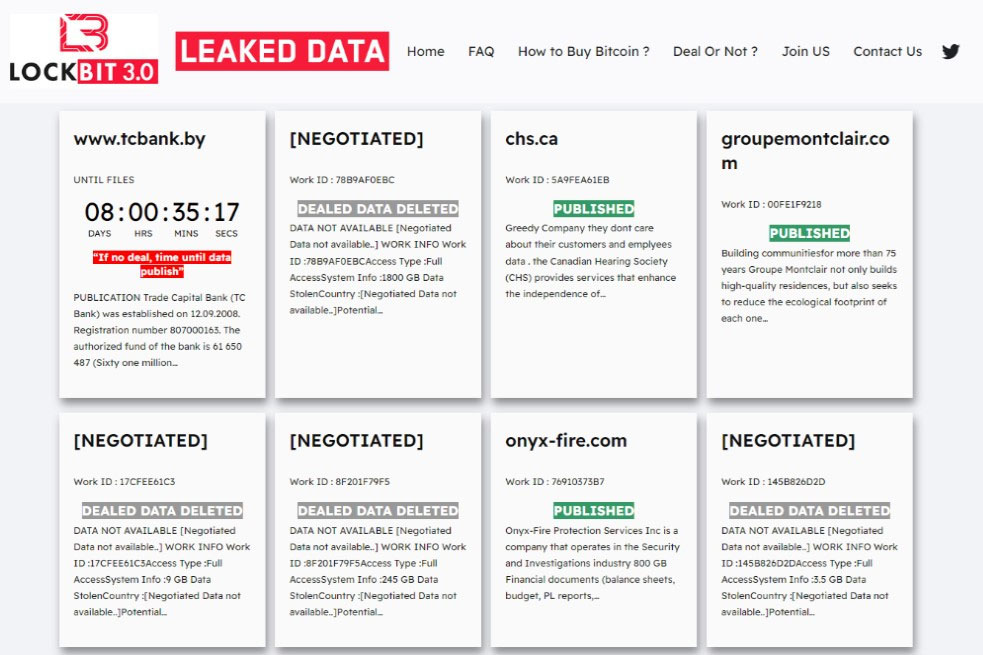
Such imitation demonstrates the deceptive methods employed by LockBit’s imposters to mislead victims into believing they are dealing with LockBit RaaS.
This tactic of impersonation underscores the complexities and challenges in accurately attributing cyber attacks, particularly when threat actors deliberately attempt to mislead investigators by leveraging the reputation of established ransomware groups like LockBit.
LockBit Black Usage by New Ransomware Groups
Trellix has recently observed an increase in the number of new ransomware gangs attempting to exploit the leaked LockBit Black builder. These groups are using it either as the basis for their own ransomware programs or simply leveraging the LockBit 3.0 ransomware builder as it is, while making minor modifications such as changing the ransom note and specifying their own contact details.
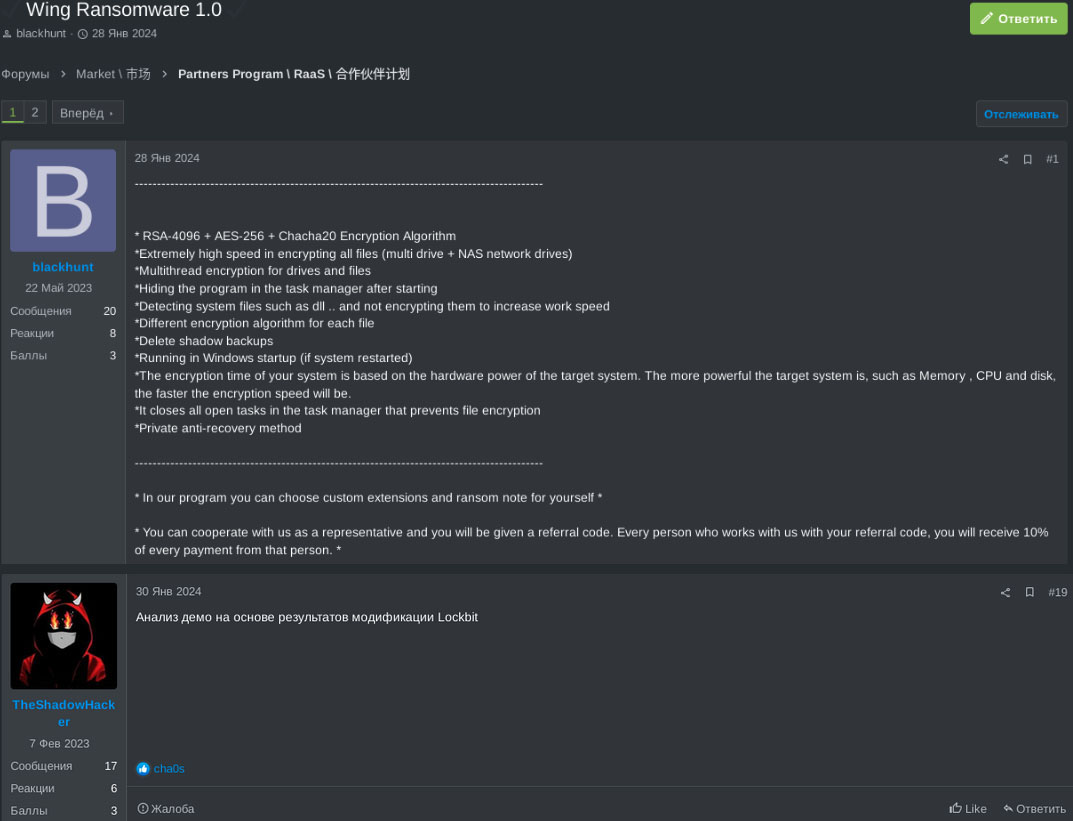
At the end of January 2024 an actor blackhunt introduced on an underground forum “RAMP” a new ransomware called Wing and shared the demo of its work and the technical details. Based on the provided information, another RAMP actor TheShadowHacker advised they analyzed the Wing Ransomware demo and concluded it was based on a modified version of LockBit, which demonstrates the threat actors not only impersonating LockBit but also using the leaked source code of LockBit to come up with their own ransomware strains:
Another example is a relatively new double extortion ransomware gang called Dragonforce who were spotted using LockBit Black ransomware in their attack campaigns in 2023. Based on the open source research, Trellix identified several samples of Dragonforce ransomware strains created using the leaked LockBit 3.0 builder. One of them is a file with SHA256 527f71e2ac55ee18f4376f213a242a20aa63f7ab501a23888b7d41ea8661802b, first seen in the wild in September 2023, which drops the following ransom note:
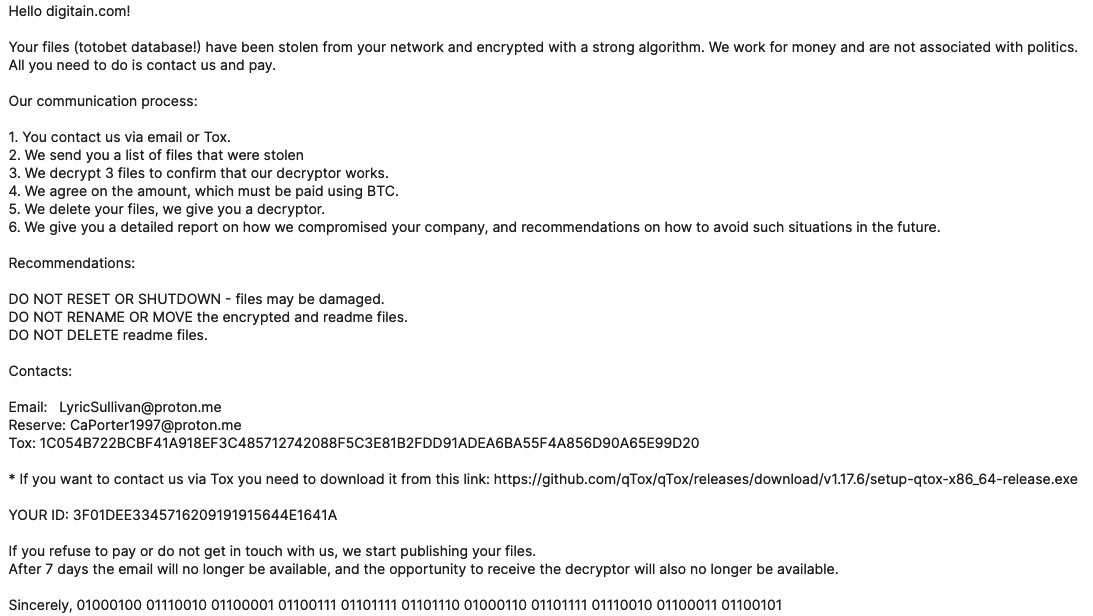
This opportunistic ransomware group used the LockBit Black as it is except for changing the ransom note and the contact details inside the note. The string at the end of the above displayed ransom note “01000100 01110010 01100001 01100111 01101111 01101110 01000110 01101111 01110010 01100011 01100101” means DragonForce in its binary representation.
In November 2023, the Russian cybersecurity firm F.A.C.C.T. reported the emergence of a new ransomware group named Werewolves, which was observed using LockBit 3.0 Black to target organizations in Russia. The Werewolves gang operates as a Russian-English speaking double extortion ransomware group, targeting both Western and Russian organizations. Trellix assesses that the Werewolves group may consist of LockBit affiliates, as both the LockBit group and the Werewolves gang have previously listed the same Western company names on their TOR blogs and shared identical exfiltrated data for some of the victims. Out of 26 company names currently listed on the Werewolves blog there are 10 non-Russian organizations and all 10 of them were listed previously on the LockBit’s leakdata site. It is possible that as soon as the Werewolves gang publicly established themselves on the RaaS market, the ransomware affiliates removed their posts from LockBit’s blog and decided to only display the victim names on the Werewolves blog site. An illustrative example of this interconnectedness is a potential ransomware victim whose data initially appeared on LockBit's leaked data site on January 22, 2024. Subsequently, this victim's data was removed from LockBit's blog and added to the Werewolves RaaS blog on February 14, 2024:
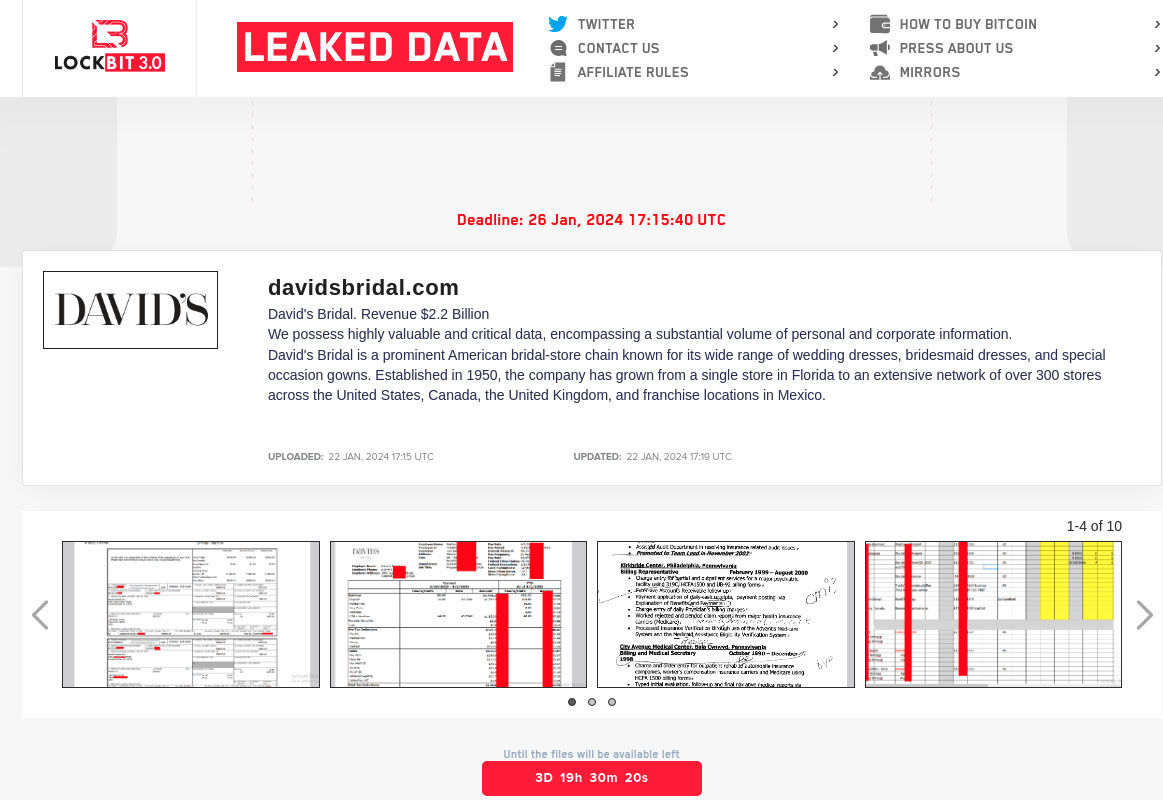
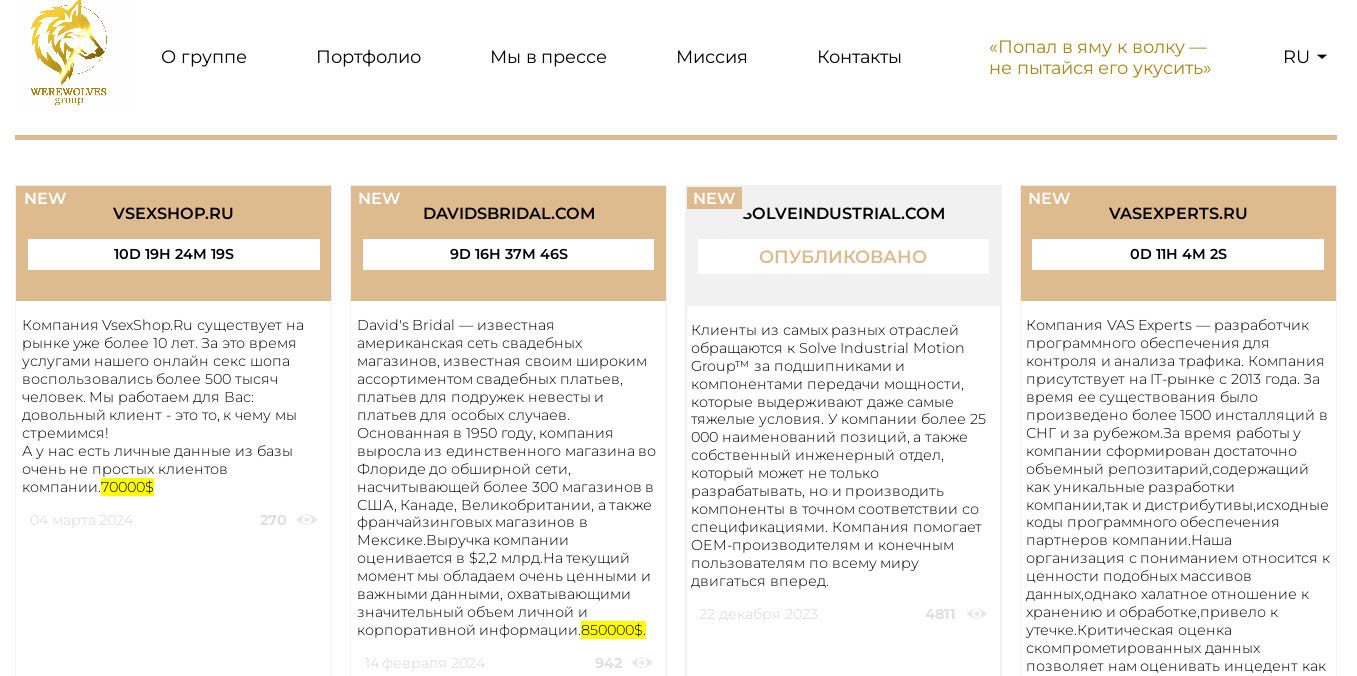
Trellix has observed in the past other ransomware variants such as BuhtiRansom which were created using LockBit 3.0 builder as well as other unknown threat actors leveraging the leaked LockBit in their cyber attacks. With the leaked source codes widely accessible, there is a high likelihood that we will continue to see in the future a proliferation of RaaS programs based on the well established ransomware families such as LockBit.
LockBit Changes After Their Partial Infrastructure Restore
Since LockBit partly restored their RaaS infrastructure four days after the "Operation Cronos," several notable changes have been observed by Trellix.
One significant difference is that LockBit has disabled RaaS panel access for some of their affiliates, leading to a wave of complaints on the “RAMP” forum. Only affiliates with a reputable history of earning money for LockBit's owner were allowed to rejoin the RaaS for free. Others were required to deposit 1 or 2 BTCs to prove their credibility. LockBit justified this deposit requirement as a means to “weed out insecure newbies, cops, FBI agents, journalists, white haters, web pentesters, competitors, and other small rodent pests”. Affiliates also have the option to use escrow services, but in that case, they must earn 5 BTCs within the first month of joining the RaaS to prove their reputation, otherwise the deposit is forfeited to LockBit:
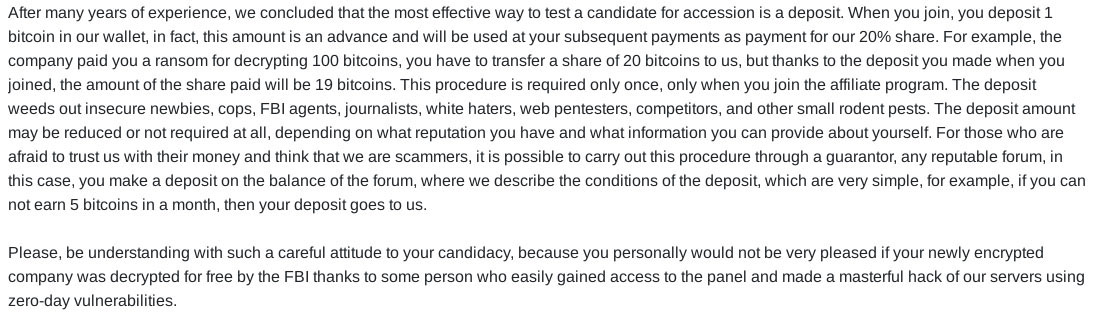
Here is an example of LockBit affiliate raising a complaint against the LockBit admin on the “RAMP” forum, suggesting to ban LockBit following the similar actions on the top-tier underground forums “Exploit” and “XSS” :
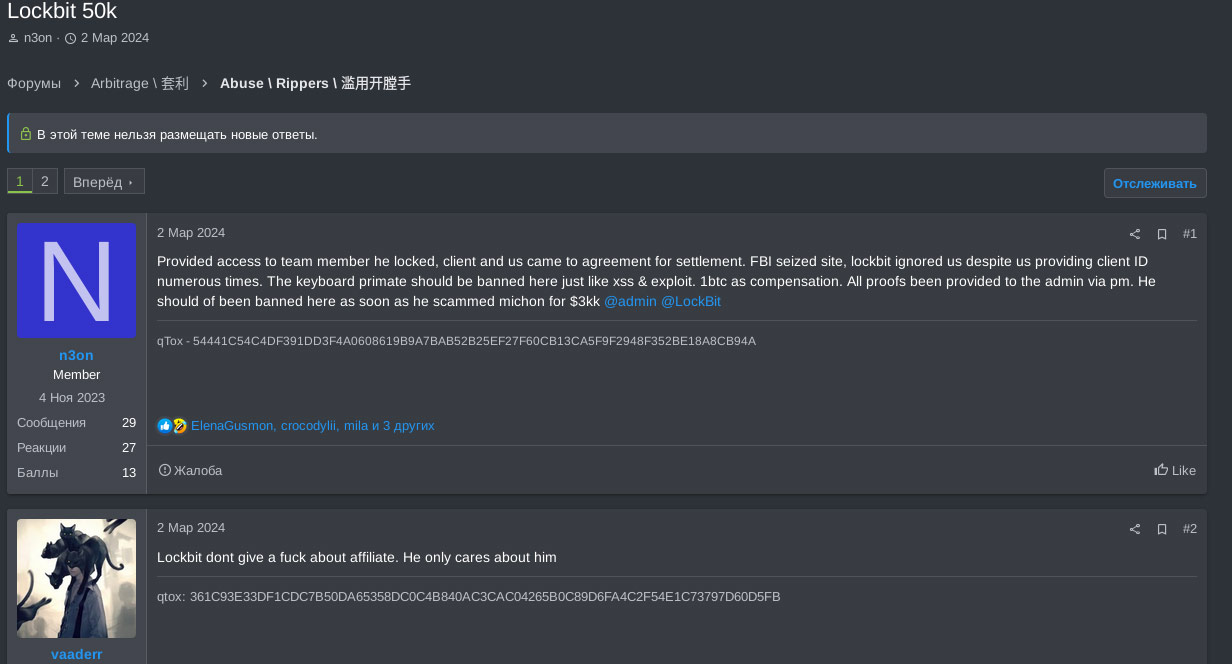
Another disgruntled affiliate of LockBit who potentially lost their access to the affiliate panel posted on the RAMP forum that LockBit RaaS is run by FSB and it is connected to LE. However, no proofs were given for such claims:
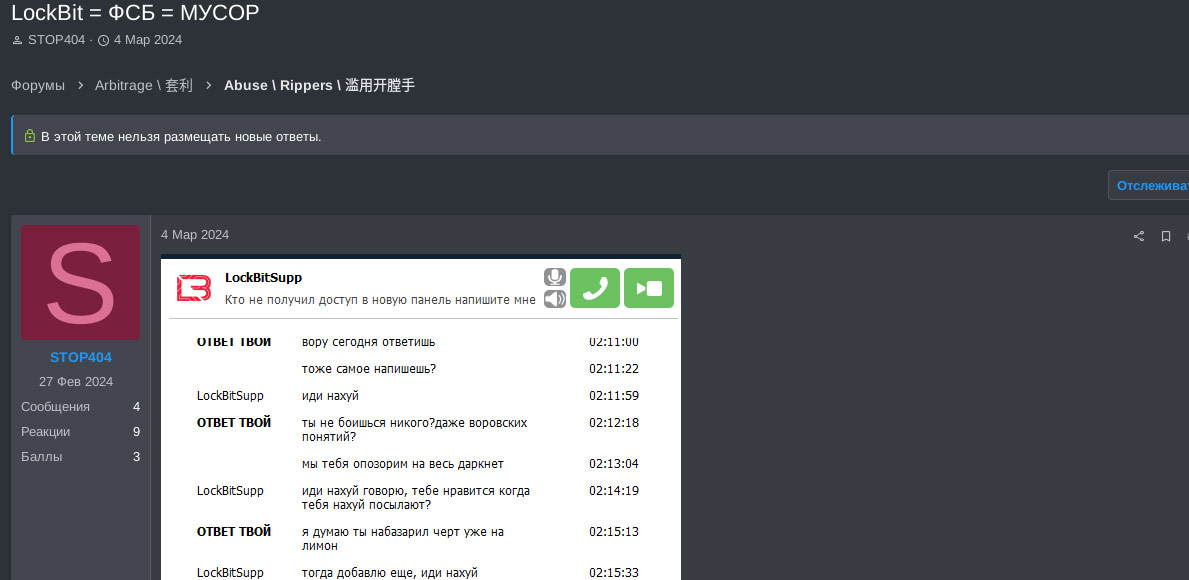
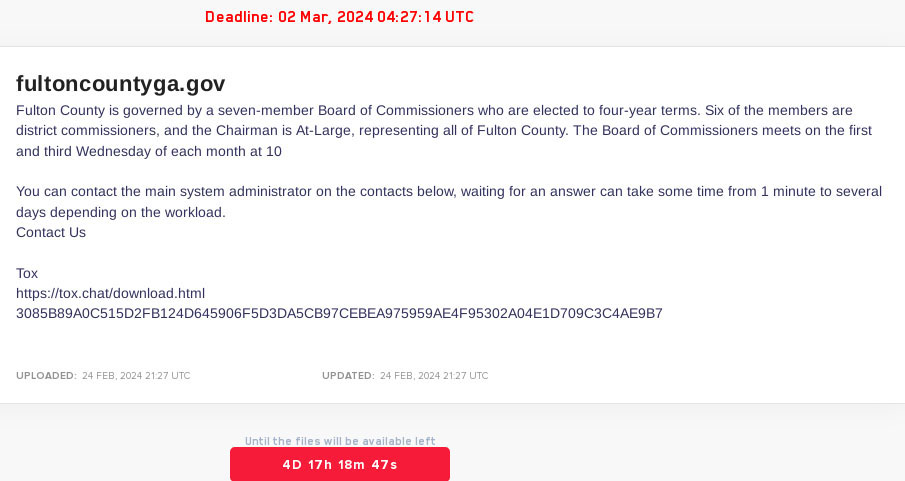
Furthermore, following the partial restoration of LockBit's infrastructure, the threat actor took swift action by posting multiple company names on their name-and-shame website. This move aimed to project an image of resilience and demonstrate that the LE seizure actions had not significantly impacted their operations. However, over the several weeks after LE actions, LockBit began removing and adding victim names on their leaked data site, suggesting that they either did not possess the victim data or had not targeted the organizations in question. This is a common tactic by cyber criminals to publish either fake data or data already in their possession as if they are operating as normal. This data can include data from victims that have previously settled a ransom with the threat actor, showing once more that there are no guarantees when it comes to data deletion by threat actors. An example of this pattern is the case of Fulton County, where a post appeared on LockBit's leaked data site on February 24, 2024. However, before the deadline of March 2, 2024, the post was removed from the site:
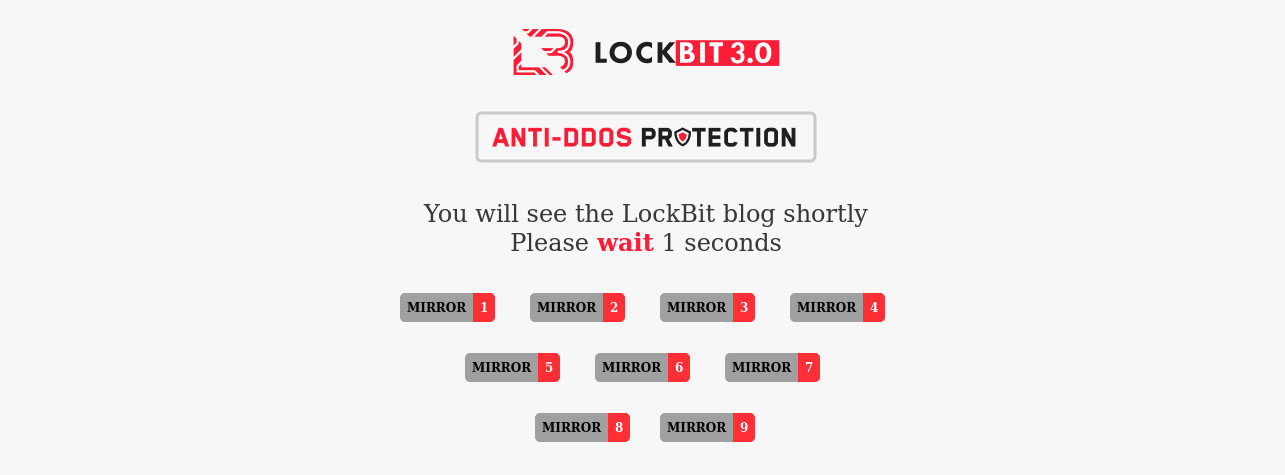
Trellix has also observed that LockBit’s “best anti-DDoS protection” as stated in their current affiliate rules, does not seem to be in place since the infrastructure restore after the “Operation Cronos”. Previously, visitors to the blog would encounter LockBit's anti-DDoS protection being displayed together with a list of blog mirrors, however, this feature is no longer present, suggesting a potential lapse in LockBit's defensive capabilities against DDoS attacks:
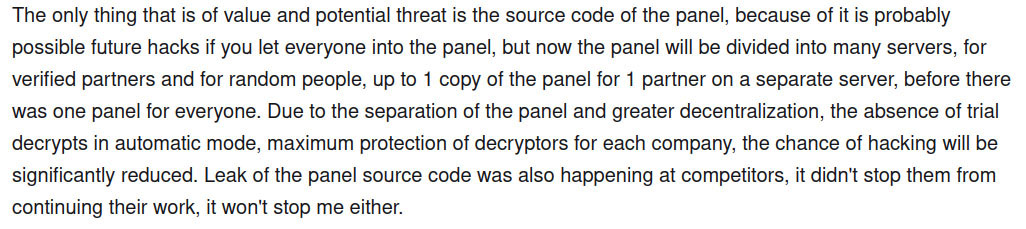
Moreover, LockBit has advised the most valuable data obtained by LE during their operations was the affiliates panel source code. Acknowledging the potential future threat from LE, who may examine the source code to uncover new vulnerabilities, LockBit has taken proactive steps to mitigate this risk. As a mitigation measure, LockBit has divided the single affiliates panel they previously had into multiple servers. This approach ensures greater decentralization and maximum protection of ransomware decryptors for each individual organization. By distributing the affiliates panel across multiple servers, LockBit aims to minimize the impact of any potential future vulnerabilities discovered and exploited by LE to seize their illicit business:
Conclusion
The (partial) re-emergence of LockBit following "Operation Cronos" has unveiled a series of intricate dynamics within the ransomware ecosystem. As expected LockBit is trying to save its lucrative business by restoring infrastructure, however in the cybercriminal underground a server is easier restored than years of trust.
It remains to be seen how much information LE has obtained on LockBit’s operation, persona and its affiliates. This uncertainty creates a huge OPSEC risk for any cyber criminal willing to engage with LockBit and their (former) team.
Alongside LockBit's resurgence, the emergence of imposters of LockBit and opportunistic ransomware groups utilizing the leaked LockBit builder highlighted the complexities of threat actor attribution and ongoing challenges posed by the widespread availability of ransomware. The trend of leveraging leaked source code to establish RaaS operations is concerning as it contributes to the expansion and diversification of the ransomware threat landscape. With tools and techniques of established ransomware families such as LockBit being readily accessible, threat actors can easily launch their own attack campaigns, posing a significant challenge for cybersecurity researchers and LE agencies.
As LockBit may try to continue to evolve their operations, it is imperative for cybersecurity professionals and LE agencies to remain vigilant and employ multifaceted strategies to mitigate the impact of ransomware attacks. Collaboration, threat intelligence sharing, and proactive defense measures are essential in safeguarding organizations against the evolving ransomware threats.
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
