Trellix
Endpoint Forensics
Perform fast, targeted investigations across thousands of endpoints
Benefits
- Prevent cyber-attacks on the endpoint
- Identify attacker behavior and their tactics, techniques, and procedures.
- Analyze live memory—without downloading memory images—to discover hidden malware.
- Detect malware and other signs of compromise on endpoints across the enterprise
- Sweep thousands of endpoints for evidence of compromise, including malware and irregular activities.
- Enable remote investigation securely over any network, without requiring access authorization.
- Collect targeted forensic data with intelligent filtering to return only the data you need.
- Respond to endpoint security incidents faster
- Automatically collect data and analyze suspicious activity based on alerts generated by your SIEM, ticketing system or other applications.
- Integrate with other detection systems to automate triage of hosts with suspicious activity.
- Support open IOCs to allow security analysts to edit and share custom IOCs.
- Automatically collect data and analyze suspicious activity based on alerts generated by your SIEM, ticketing system or other applications.
Gartner® report:
Magic Quadrant™ for
Endpoint Protection
Platforms
Learn why Gartner® named Trellix—formerly McAfee Enterprise—a Magic Quadrant™ Leader.
Download Report
Trellix Insights
Get ahead of the adversary with the first proactive security soluition of its kind.
Learn more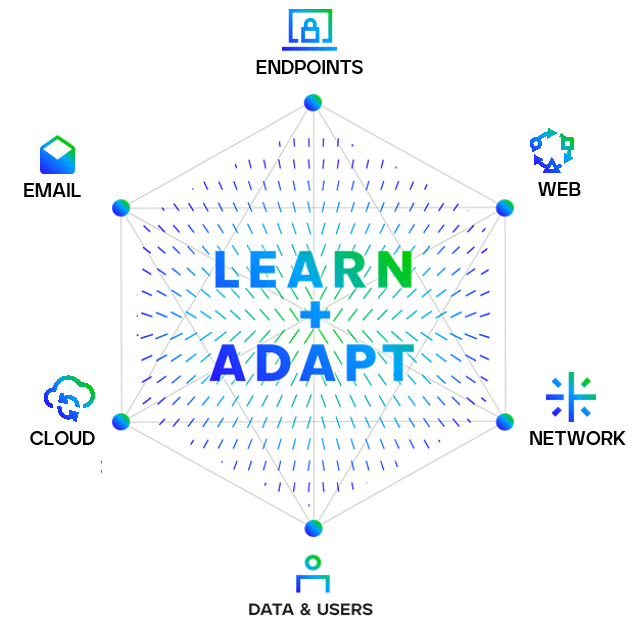
Get to know the Trellix Ecosystem
The Trellix Platform learns and adapts for living protection while delivering native and open connections and providing expert and embedded support for your team.
View ProductsTake the next steps to future-proof your defenses.
Search Tips
Be concise and specific:
Wrong: I want to learn how to migrate to Trellix Endpoint Security
Right: Trellix Endpoint Security migration
Use quotation marks to find a specific phrase:
“migrate to Trellix Endpoint Security”
Use sets of quotation marks to search for multiple queries:
“endpoint security” “Windows”
Punctuation and special characters are ignored:
Avoid these characters: `, ~, :, @, #, $, %, ^, &, =, +, <, >, (, )
The search engine is not case sensitive:
Endpoint security, endpoint security, and ENDPOINT SECURITY will all yield the same results.