Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Using AI to Pivot from Reactive to Adaptive in Security Operations
By Brian Brown · February 21, 2024
AI is currently at peak hype, and many organizations are trying to understand how to protect themselves against misuse and data leakage while simultaneously leveraging AI within their business. In a previous blog our CISO, Harold Rivas, outlined these two potentially conflicting scenarios, and summarized his thoughts with the hypothesis that AI can be used for good and benefit cybersecurity defenders. But where can organizations turn to understand how to start their AI and security journey?
Governing bodies such as ISACA and CISA – and the recent executive order from the Biden administration – outline that oversight is necessary in the fast-changing world of AI. Knowing who to turn to when evaluating what your next step is in the uncertain world of AI and cybersecurity is critical. Within Trellix, we’ve been highly engaged in setting standards for security and AI by contributing to the OWASP Top 10 for LLMs, and showing how our customers can benefit from the use of AI for Security Operations teams to enhance Incident Response via the power of SOAR tools.
Where to start - identify key use cases for AI in security operations
Our goal at Trellix is to help guide our customers through this transitional landscape, to, as said by our CISO, Harold Rivas, "...inspire Security Operations to rethink the reality of AI". While many others are jumping on the AI bandwagon, Trellix, with over a decade of experience in ML and AI modeling, to help guide our customers with impactful use cases. Like many paths in security there has been an evolutionary approach of machine-led technologies that has culminated with the AI of today. We consider this evolution to include 3 “As”: Analytics, Automation and now AI.
At Trellix we’ve followed the 3 “As” and used machine-led analytics that leverage highly trained, and thus accurate, ML models for detection use cases for over a decade. We’ve led the field by combining the power of analytics with automation with SOAR for many years. And for over six years our customers have been using AI-guided investigations and have seen the value of our early adoption of this approach with streamlined and efficient SOC investigative workflows.
As your organization leans into AI and GenAI consider use cases such as:
- Protecting against data leakage when employees are using GenAI via a Data Security solution that prevents sensitive data from being exposed
- Using AI driven analytics for greater data accuracy and predictive analysis in the realm of Threat Intelligence to help combat threat actors who are also leveraging AI
- Augmenting existing workflows that require many manual steps and triage processes that GenAI can handle with speed and scale
- Automating the creation of security content such as SOAR playbooks, YARA or Sigma rules, and searches in threat hunting tools like EDR
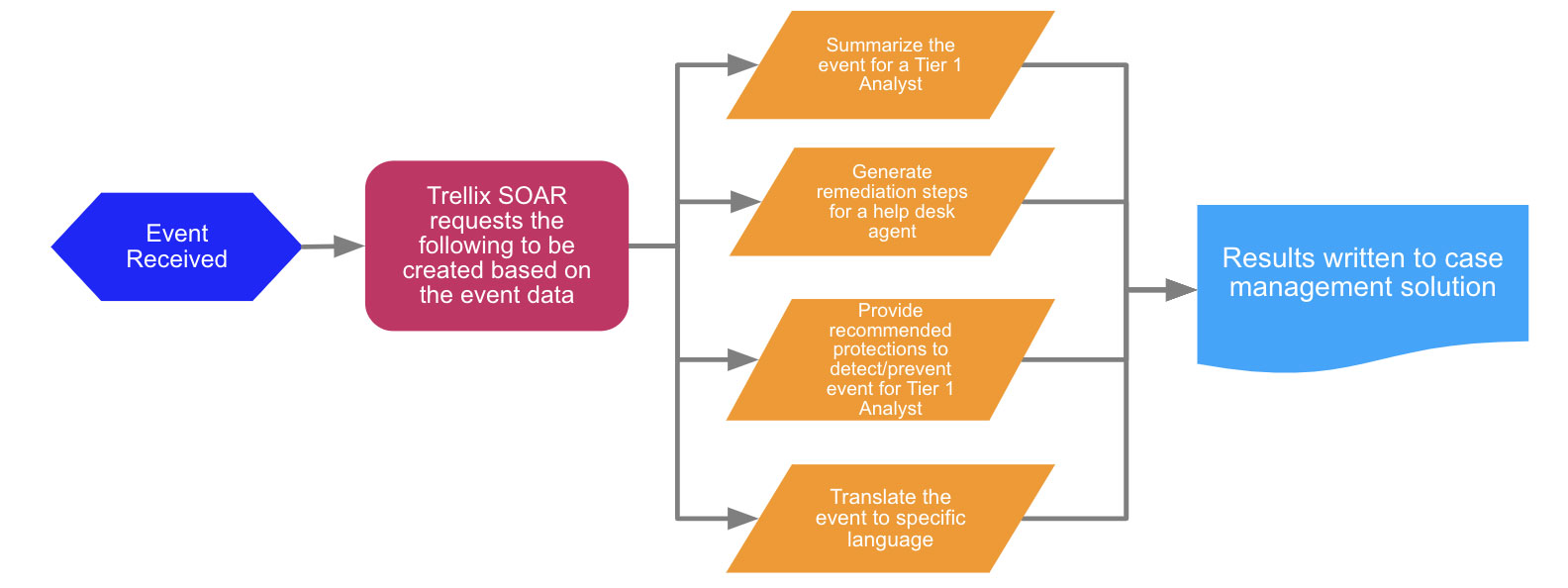
Using AI to foster adaptive security operations
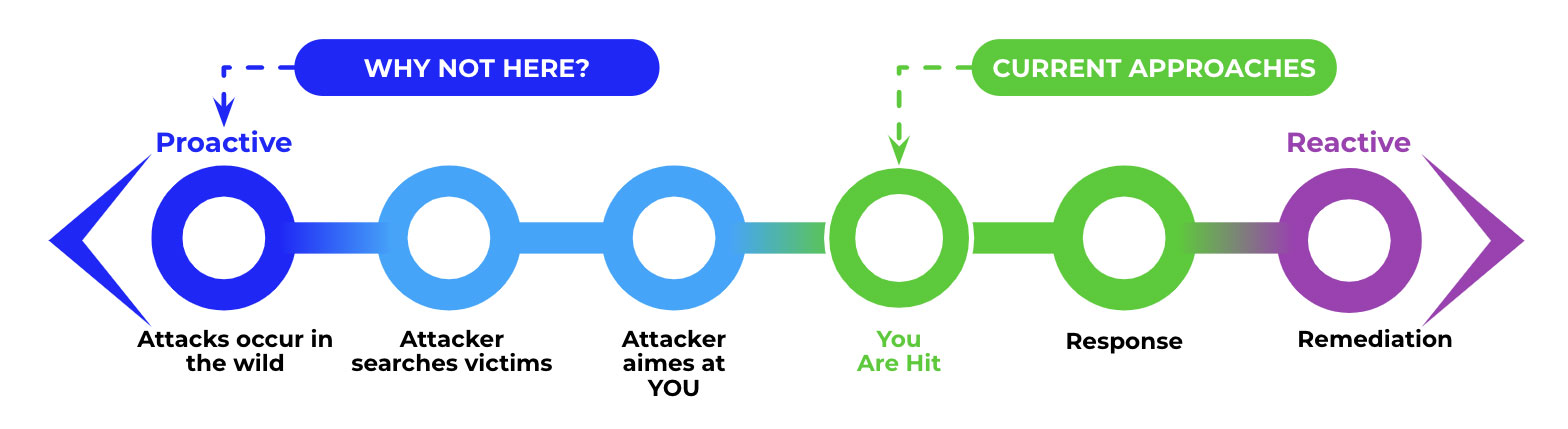
Taking stock of both the risks and opportunities presented by AI can appear to be a daunting task for CISOs. With an approach that centers on the value that the adoption of AI can bring to a security program one can evaluate where and when to provide protective controls or look at AI as an enabler. In both cases the Security Operations environment will need to shift from a “monitor and response” focus to being more proactive and adaptive. Trellix is on the forefront of connecting the dots for a strategic approach to AI by leveraging it internally for data analysis and contextualization of threats, creating opportunities for our customers with AI-driven automation and SOAR, as well as building capabilities and interfaces in our products that operationalize GenAI for maximum benefit.
To learn more, come join us at two virtual events:
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
