Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Connected Healthcare: A Cybersecurity Battlefield We Must Win
By Trellix · June 6, 2022
This blog was written by Charles McFarland
We are commonly taught to prioritize the most critical, severe, or impactful tasks when trying to conquer a list of intimidating problems. Yet, how is this possible when presented with two tasks of equal importance? The medical industry has its work cut out for itself when reviewing its list of intimidating problems. Healthcare providers are entrusted with protecting lives, often in high stress situations while still needing to protect patient data against loss and theft. Both are important and both can be compromised by the efforts of bad actors. The medical industry is at unique risk of attack due to the numerous purpose-built devices used, such as anesthesia machines, IV pumps, point of care systems, MRI machines, and numerous others. Many of these devices are not found in other industries nor the average household. Their lack of ubiquity creates a false sense of security and reduced scrutiny from the security research industry.
Failure to mitigate these risks can have dire consequences for healthcare providers and patients alike. It’s not just routers and computers that are targeted by bad actors. Even seemingly mundane devices can be used for malicious purposes such as printers. Medical devices can allow attackers to get a foothold on a critical network or move laterally across their infrastructure resulting in potentially stealing or destroying patient data. The medical industry needs to be concerned with not only common devices but any device they deploy which can have security vulnerabilities of equal severity to those of more common devices.
Building secure devices and software is difficult, proven time and again by the actions of malicious hackers and state sponsored attacks. Using public data such as CVE databases we have taken the time to analyze the current state of the attack surface in the medical space and evaluate active threats and distribution of discovered vulnerabilities. We believe that more partnerships between medical device vendors, medical care facilities and security researchers in junction with increased security testing is warranted to prevent a growing attack surface from becoming even more attractive to malicious actors.
From the dark web to extortion
It used to be the case that bad actors collected medical data and sold this data in bulk on the dark web. Much of this was likely used for fraudulent purposes such as identity theft and insurance scams. However, times have changed. After extensively searching dark markets we found very little data for sale. It is possible that some data has simply moved to other platforms but ransomware campaigns play a large role as well. For example, hospitals and other facilities have been hit hard and often by ransomware groups such as Conti. In recent years extortion has been on the rise with threats of releasing confidential data belonging to medical institutions not willing to pay cybercriminals. After all, many countries have laws concerning the protection of personal health information (PHI) and the ramifications of a leak could be catastrophic with impacts spanning from fines to criminal prosecution. These leaks have increased the supply of stolen medical data drastically, all but eradicating the market as we know it. Data theft and sales will always be a thing but many of the buyers can now get their data for free. The clear and present danger to the medical industry today is ransomware. Medical devices need to be safe guarded to not only ensure they are not an entry point into the network but the devices themselves can’t be held for ransom.
Understanding the current landscape
To gauge the current state of vulnerabilities in the medical industry, we reviewed 270 reported vulnerabilities from 2019-2022 that are specific to medical devices and software. Some fall into other categories such as mobile apps or other miscellaneous software. It’s surprisingly difficult to locate this information as there isn’t a standard repository for medical vulnerabilities we can search. Three useful ways of enumerating existing vulnerabilities include searching:
- Standard web search engines
- National Vulnerability Database (NVD)
- Industrial Control System (ICS) Medical Advisories from CISA
Using internet search engines (like Google) is typically a good place to start for any project. This basic search method allowed us to find existing research and reports. Collecting this data provides great insight into the current state of research; however, what it lacks is insight into niche or unpopular vulnerabilities. Those are much harder to uncover. That’s where the National Vulnerability Database (NVD) can help. All public vulnerabilities assigned to a CVE can be found within in NVD. We leveraged NVD to gather detailed data about each vulnerability and its impact. Because it’s impossible to understand the specifics of all medical devices and software we are forced to utilize simple filters such as “medical” and “health” then manually determine if each result is applicable. To augment this data, we use ICS Medical Advisories. ICS Medical Advisories are published for incidences considered highly important by CISA to the medical industry. Each advisory may include applicable CVEs, company names, and product names, related to the medical space. Pivoting off product names and companies to further enrich our NVD searches and web searches we combined these methods and resulted with some surprising findings.
Alarming results
When evaluating devices and software we found the most common impact relates to records and management software. This category contributes to about 17% of our samples. It is not all that surprising given software is typically much easier to both obtain and test by security researchers. We do believe this number is quite low as ICSMA-CERT and popular research seems to have a heavier bias to hardware than software. IV pumps closely follow management software at about 14% of samples and patient monitors at about 7% of samples. If IV pumps come to a surprise to you then maybe some of these others will pique your interests. Ultrasounds (CVE-2020-25179), ventilators (CVE-2020-27278), MRI machines (CVE-2021-26262), defibrillators (CVE-2021-27489), diabetes machines (CVE-2020-27276) and even anesthesia machines (CVE-2020-10598) are among other impacted categories demonstrating a wide diversity of impacted hardware which can be seen in Figure 1.
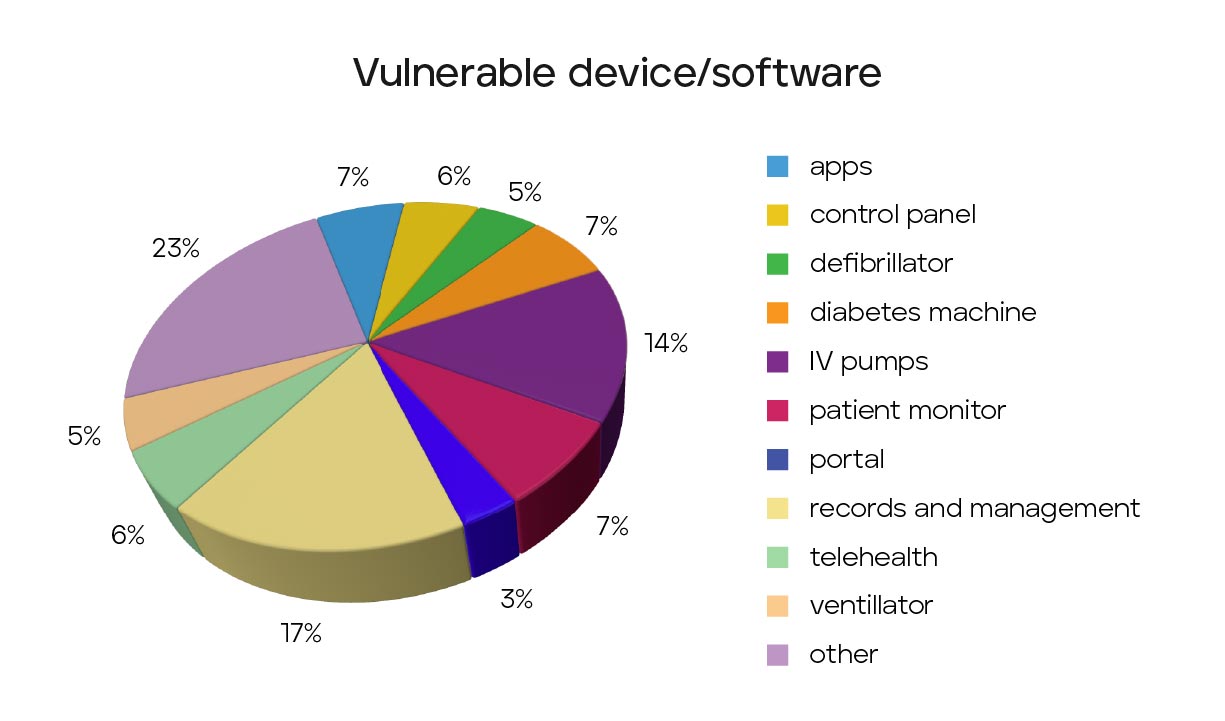
As like all security risks, vulnerabilities must be prioritized based on their severity. Unfortunately, a substantial percentage of medical analyzed CVEs are severe. Just under 30% of sampled CVEs can lead to remote code executable (RCE), the crown jewel for attackers as they can lead to an attacker getting a foothold on the network with little to no user interaction. For example, CVE-2021-27410, a 9.8 CVE (out of 10) for device management and vital monitors, requires no user interaction and is easily exploitable over the network. These should be a high priority for any organization to track and patch and there is no shortage to choose from. A surprisingly high percentage of issues involve authentication vulnerabilities. These can range from exposure of credentials, clear text storage, or even a complete lack of authentication. Just over 33% of sampled CVEs suffer from these types of issues with 19% of them simply being hardcoded credentials. Considering authentication is one of the first forms of protection against unwanted access, this is alarming and indicates a deeper security issue.
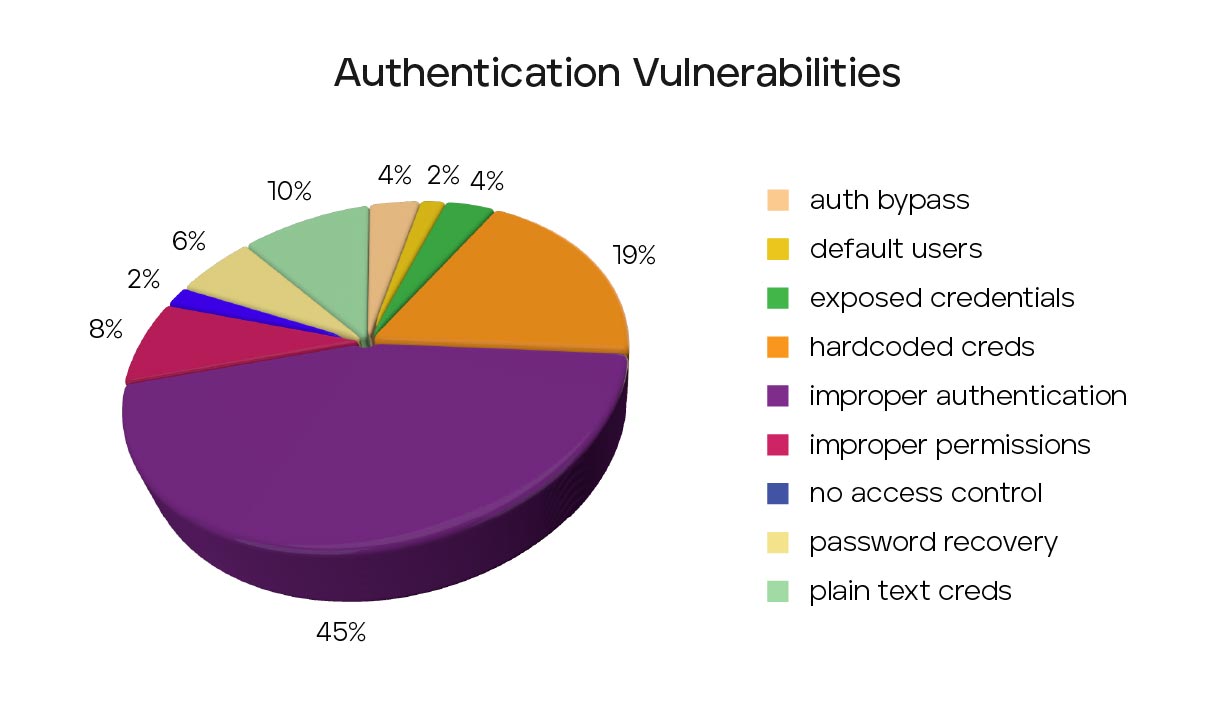
Consider CVE-2022-22766 which suffers from embedded hard coded credentials. This single CVE impacts medical dispensing devices, supply dispensers, and even anesthesia stations. Hardcoded credentials are major mistakes not even considering the potential human impact of compromised medical devices. These mistakes can easily be prevented and should not occur in this day and age. These issues should be handled through developer training, or in the event they do make it through, security testing of the devices. To make matters worse, hardcoded credentials issues on average score 5.75 in the CVSS scoring system. 5.75 is considered a ‘medium’ severity rating and easily overlooked next to the flashier 9.8 scores. Among all authentication issues, the average CVSS score still only rises to an average score of 7.0. The extensive hardcoded credentials, clear-text passwords, and other authentications issues highlights a fundamental issue with medical device security.
These issues do not exist in isolation. As many devices perform the same or similar activities as one another it’s not uncommon for there to be extensive code reuse between them. This is especially true with firmware. Again, let’s consider CVE-2022-22766 where a single vulnerably impacts:
- Medical workflow software
- Anesthesia stations
- Medical Storage devices
- Medical dispensers
- Medical packaging
- RX inventory systems
- Inventory and compliance solutions
- IV prep
- Stock scanners
To exploit each device would typically require tailored work for each but the vulnerability itself can be re-used between them. Attackers can leverage this overlap to ensure they get the most from their effort by targeting device groups.
Seventeen of the sampled CVEs have publicly available exploit code and/or tutorials freely available online. Mostly, these are related to telehealth and management systems including records. There is a lack of publicly available exploit code for hardware devices themselves with few notable exceptions such as CVE-2020-27260, a CVSS 5.3 injection vulnerability on a patient monitor. About 35% of the available exploits can lead to RCE and another 35% can lead to data leaks. An attacker simply needs to add the existing code to their toolset.
Active exploitation
Are hackers actively exploiting these devices? It appears the answer is not likely. However, this doesn’t imply medical networks are without risk of exploitation. After searching for medically related CVEs for active exploits we came across three actively exploited CVEs that could potentially impact the medical devices and software, CVE-2017-1043, CVE-2019-0708, CVE-2020-1938. These exploits are not specific to medical devices and software but can impact them none-the-less. If CVE-2019-0708 sounds familiar that is because it is a widely popular 9.8 remote code execution vulnerability in RDP called BlueKeep. This same vulnerability can be found in a patient monitoring receiver due to its use of the vulnerable code. The other two CVEs are similar in the fact that the vulnerabilities are not specific to the medical space but their inclusion put it at risk. CVE-2020-1938 is another 9.8 vulnerability specific to the JServ Protocol in Apache tomcat. Unfortunately, it is used in several medical imaging software solutions. CVE-2017-0143 is an 8.1 SMB remote code execution flaw also found in an IV Mixture solution. Do not consider this a comprehensive list. Without the manufacturer discovering and reporting the issues it becomes a massive undertaking to discover them externally.
Call to action
The medical industry has been suffering ransomware attacks for several years now. It has been significant enough to even impact on the medical sales market and shows no signs of stopping any time soon. Medical devices and software are falling short in fundamental security practices such as handling credentials and are ripe with RCE vulnerabilities. This is enticing to cybercriminals and we must be on our guard to prevent further attacks as it won’t be an ignored attack surface forever. All stakeholders must acknowledge that the large selection of authentication vulnerabilities indicates the medical space needs more research, both internally and externally, to harden these devices. It’s not simply management systems and other web-based applications we need to focus on, but any network connected medical device needs to be accessed. Currently it doesn’t appear that these devices are being targeted by malicious actors but this doesn’t mean we can relax. There have been plenty of RCE vulnerabilities to choose from and public exploit code for re-use. While attackers are using other methods to attack hospitals and clinics they will search for easier access when those methods run dry. Society as whole cannot allow medical devices and software to continue to be a weak point for attackers to exploit and therefore should encourage both internal and external security testing across developers and researchers alike.
RECENT NEWS
-
Apr 22, 2024
Trellix Enables Customers to Secure Microsoft Office 365
-
Apr 18, 2024
Trellix Recognized as Industry’s Best Email Security
-
Apr 18, 2024
Trellix and Google Chrome Enterprise Enable Integrated Browsing Protection Against Insider Threats
-
Apr 9, 2024
Trellix Collaborates with Google Cloud to Protect Enterprises and Governments
-
Apr 4, 2024
Trellix Accelerates Zero Trust Framework Implementation
RECENT STORIES
The latest from our newsroom
Get the latest
We’re no strangers to cybersecurity. But we are a new company.
Stay up to date as we evolve.
Zero spam. Unsubscribe at any time.