Trellix Enterprise Security Manager
Real-time monitoring and visibility into activity on your systems, networks, databases, and applications
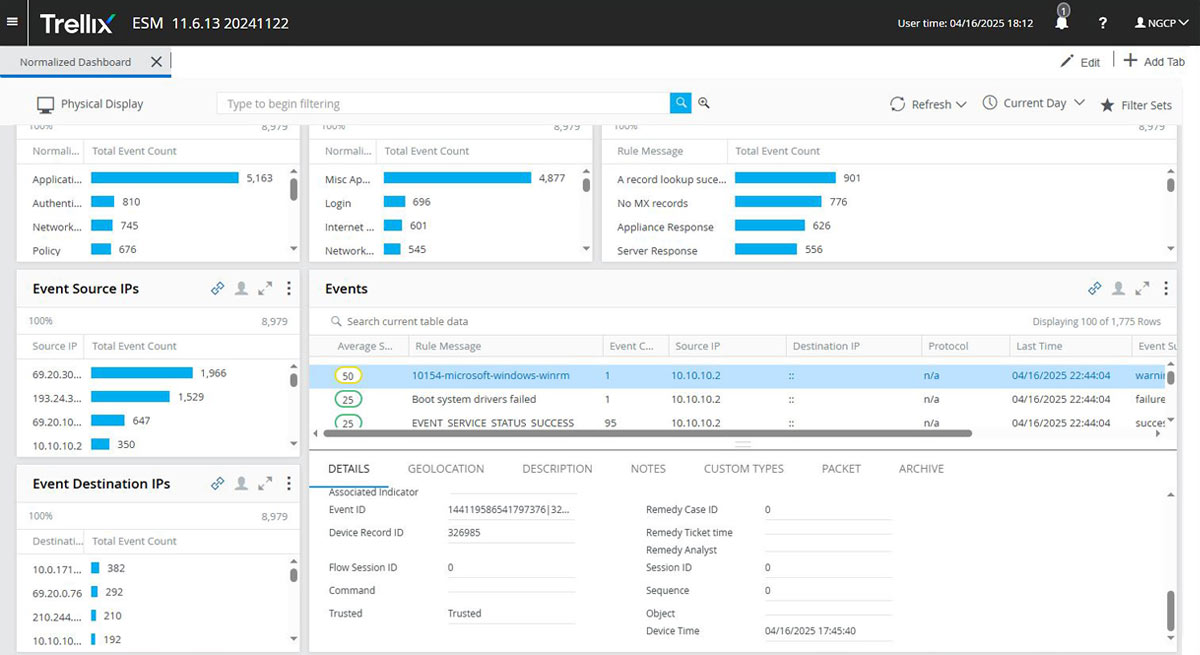
Get visibility across your environment
Integrate and analyze data from across your security infrastructure and gain rapid access to long-term storage of event data. Store billions of events and flows to keep information available for immediate ad hoc queries and future forensics, rules validation, and compliance needs.
Did you know ...
Trellix Enterprise Security Manager statistics
000
Pre-built dashboards
000+
Reports for global regulations and control frameworks
00%
Reduction in manual efforts from our integrated architecture
Why Trellix Enterprise Security Manager?
Broad data collection
Integration collection from over 460 products to analyze and map security events.
Out-of-the-box usability
Utilize customizable reports, views, correlation rules, and alerts.
Scalable, hybrid deployment
Deploy on-premises or via the cloud for access to information that fits your infrastructure.
Product features
Related solutions
Trellix Threat Intelligence
Proactively anticipate and defend against potential cyberattacks.
Trellix Endpoint Detection and Response
Reduce mean time to detection and response with EDR.
Trellix Threat Intelligence Exchange
Deter threats with an interconnected surveillance system.
Complementary services to accelerate your success
Installation and Configuration
Integration and Training
Monitoring and Optimization
Industry recognition
Trellix is recognized as an industry leader by key analyst firms
Security awareness
What is SIEM?
Security Information and Event Management (SIEM) is software that improves security awareness of an IT environment by combining security information management (SIM) and security event management (SEM).
Read MoreWhat is a SOC?
Security Operation Center (SOC) is a centralized function within an organization employing people, processes, and technology to continuously monitor and improve an organization's security posture.
Read More