Trellix Network Forensics
Minimize the impact of network attacks using high-performance packet capture and investigative analysis
Why Trellix Network Forensics?
Centralize Visibility of Threat Data
View specific network metadata and activity with easy-to-create custom dashboards.
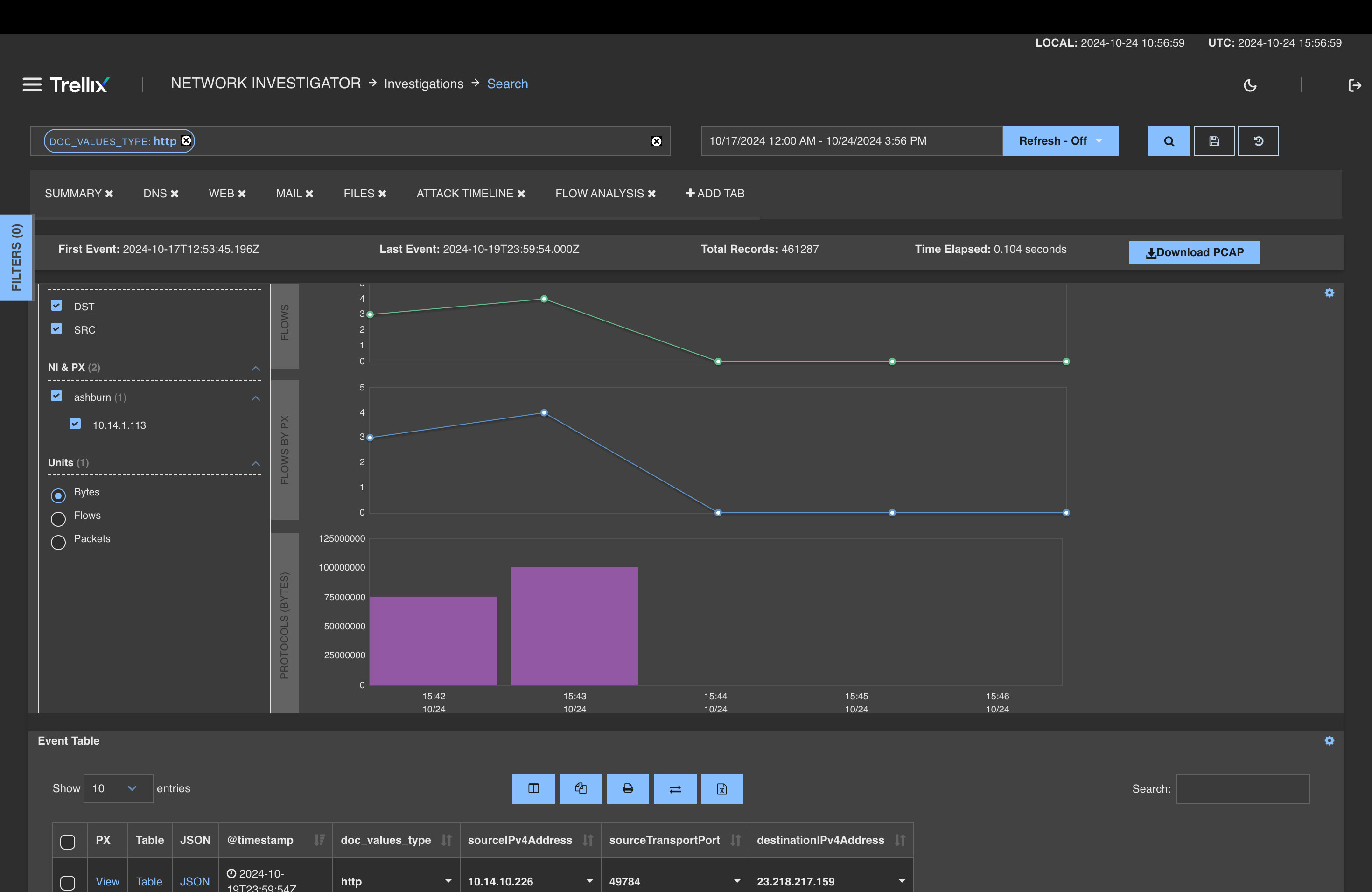
Faster
Results
Search connections and packets quickly across all alerts, captured flow, and metadata.
Effective Threat Hunting
Hunt for anomalies and suspicious activities that may evade your existing tools.
IOC Aggregation Across Tools
Consolidate alerts from other Trellix and third-party products in a single workbench.
Product features
Complementary services to accelerate your success
Installation and Configuration
Integration and Training
Monitoring and Optimization
Industry recognition
Trellix is recognized as an industry leader by key analyst firms
Frequently asked questions
Trellix Network Forensics is a solution that captures and indexes full network packets at high speeds, allowing organizations to identify and resolve security incidents faster. It provides a centralized workbench with an easy-to-use analytical interface for reviewing network packets and sessions before, during, and after an attack. This enables security teams to detect a broad range of security incidents, improve response quality, and accurately quantify the impact of each incident.
Trellix Network Forensics offers high-performance packet capture with several key features: continuous lossless capture with time-stamping at speeds up to 20 Gbps, real-time indexing of all captured packets, ultrafast search and retrieval using patented indexing architecture, and intelligent capture with selective filtering. It also provides rich context through a web-based, drill-down GUI for inspecting packets, connections, and sessions.
Yes, Trellix Network Forensics is designed to integrate with other security tools. It can consolidate alerts from Trellix Network Security, Email Security, and Endpoint Security products, as well as third-party tools and all network metadata in a single workbench. This integration allows for immediate one-click pivot to session data from alerts. The solution also supports the integration of Trellix Threat Intelligence, STIX, and OpenIOC feeds for enhanced threat detection and analysis.
Security awareness
What is Network Security?
A combination of technologies, policies, and practices to protect computer networks and data's confidentiality, availability, and integrity.
Read MoreWhat is NDR?
NDR goes beyond essential intrusion detection to continuously monitor your network traffic for suspicious activity.
Read MoreIDS vs. IPS: Key Differences Explained
IDS and IPS are vital network security tools used to identify cyberattacks. While both aim to protect enterprise networks, their core functions and methods differ.
Read MoreRelated resources

Updates to Trellix NDR include three core advancements: streamlined analyst workflows; advanced detection and investigation capabilities; and comprehensive integrations.

Trellix NDR stands out from competitors with an “Active NDR” approach that combines broad detection with prevention capabilities in a single solution.

As attack surfaces expand and vulnerabilities multiply, Trellix NDR 4.0 delivers the visibility and detection needed to secure hybrid environments with confidence.

Trellix NDR with Trellix Wise leverages on-device LLMs and AI agents to disrupt attacker activity across the cyber kill chain and accelerate investigation and response.