Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Untangling XDR: Our Take on the 2023 Gartner® Market Guide
By Grant McDonald · September 18, 2023
With threats on the rise and organizations using an average of 25 individual security solutions, security professionals look to advanced solutions like Extended Detection and Response (XDR) to reap the benefits of an integrated security approach.
Over the past 18 months, Trellix has been named in Gartner reports1 addressing native security capabilities critical to an XDR solution. Why? We believe it is because Trellix has truly understood the needs of this evolving market, and is delivering on the definition of XDR per the new 2023 Gartner® Market Guide for Extended Detection and Response:
“Extended detection and response (XDR) delivers security incident detection and automated response capabilities for security infrastructure. XDR integrates threat intelligence and telemetry data from multiple sources with security analytics to provide contextualization and correlation of security alerts. XDR must include native sensors, and can be delivered on-premises or as a SaaS offering. Typically, it is deployed by organizations with smaller security teams.”2
This report, which recognizes Trellix as a Representative Vendor, offers strategic guidance for SRM leaders to understand and evaluate the applicability of XDR platforms for their needs. Vendor consolidation, closing threat detection and response gaps, better alert correlation, enriching alerts with greater context, and improving security efficacy and operations are all referenced in the report. Gartner also offers practical guidance throughout to help customers measure a vendor against expected XDR outcomes.
You can read the report here to get the full set of recommendations, but our take on the report focuses on 5 key areas:
Can XDR help with vendor consolidation?
Native security capabilities that address common threat vectors are an early call out, with the bare minimum requirement of an endpoint sensor and one other native security sensor with pre-built integration. A longer list that includes many technologies beyond the endpoint is offered for consideration. This is interesting, as several XDR vendors require that customers adopt their endpoint technology but may lack other components. As Gartner notes about the list of security sensors, “The mandate being that these are threat- and response-focused sensors that can add to the greater whole than the individual items provide on their own.” Buyers should investigate how many native security controls beyond the endpoint are available, particularly if vendor consolidation is a driver for the business.
Can XDR make better, more efficient use of the data you already own?
Data correlation in the form of enrichment, analytics, automation, orchestration, and workflow improvements is a layer within the core elements of XDR. It requires integrations with third-party products and advanced analytics to drive automation and orchestration across threat vectors to create higher-value alerts. Looking at the depth of integrations and data ingestion speed and asking for demonstrations of SOAR capabilities can help you determine how well a vendor can provide SOC efficiency.
How well does XDR create timely threat intelligence?
Making threat intelligence actionable is a practical benefit of XDR. The more data that can be processed across sources and delivered in a prioritized way for teams, the faster they can improve detection and response efficacy. Exploring the volume of sources (native and third-party feeds) a vendor can leverage, along with how fast data can be ingested and presented in a prioritized manner, should be a consideration for buyers.
How well does XDR complement your current team and tools?
As per Gartner, “While XDR cannot replace the need for SIEM in all use cases, XDR can replace or augment the SIEM threat detection and response use case for a specific security domain.” The ability to craft more automated responses and integrate with converging platforms is critical for businesses that lack resources, specialized skills or want fewer tools. In addition to how vendors can replace or augment current tools, it is critical to explore how truly open vendors are when it comes to integrations. Vendors who lack the ability to ingest data from a range of third parties will have a harder time adding value to and making the most of the data you already own.
Does XDR maximize automation with built-in capabilities?
“Gartner has stated that orchestration and automation are mandatory capabilities for a credible XDR.” Guided workflows, user-generated automation, and the ability to share events with other security controls is critical to simplifying security operations. Solutions that perform automated hunting and quickly connect analysts to orchestration and automation can go a long way to help overwhelmed teams. The ability to trigger automated actions in other controls is important, especially with new and emerging threats to quickly halt a threat actor while teams investigate the root cause. Asking for specific SOAR use cases can help uncover how well and how fast vendors perform.
Trellix is recognized as a Representative Vendor in the XDR market. We believe Trellix solves all use cases addressed in the report and meets every XDR requirement listed.
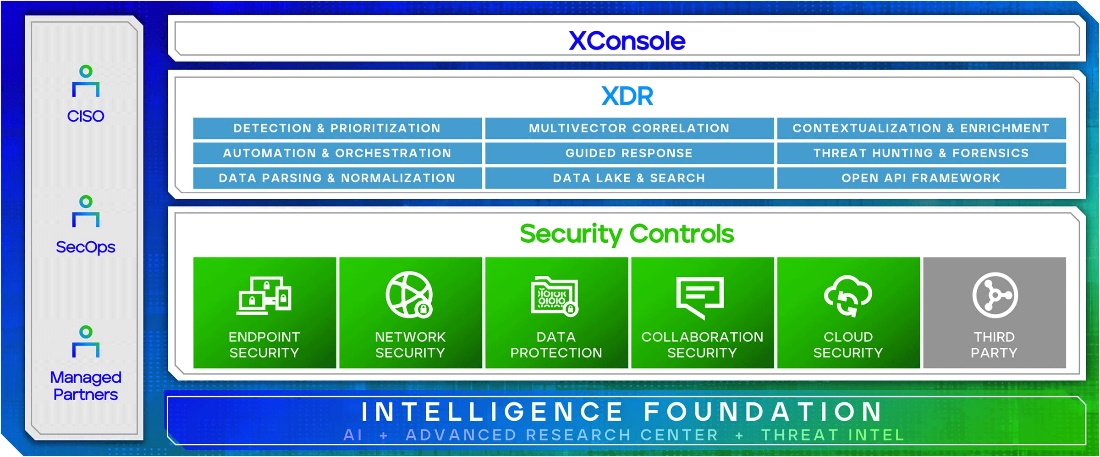
Our open, integrated XDR ingests data from the largest array of native, best-of-breed security controls spanning today’s critical threat vectors as well as more than 1,000 third-party data sources. Leveraging more than 1 billion global threat sensors, Trellix is able to correlate and enrich data so you get timely insights to improve your detection, investigation, and remediation response times.

Unlike competing XDR solutions, we unlock data from the security controls customers already own without requiring a Trellix-native solution. In the same vein, we leverage intelligence from our elite Advanced Research Center team of researchers and more than 40,000 customers as well as numerous third-party feeds, to prioritize and remediate threats for analysts and help them investigate faster with more accurate insights into attack behaviors. Guided investigation and hundreds of built-in SecOps playbooks drive automation and further simplify workflow processes for SecOps teams.
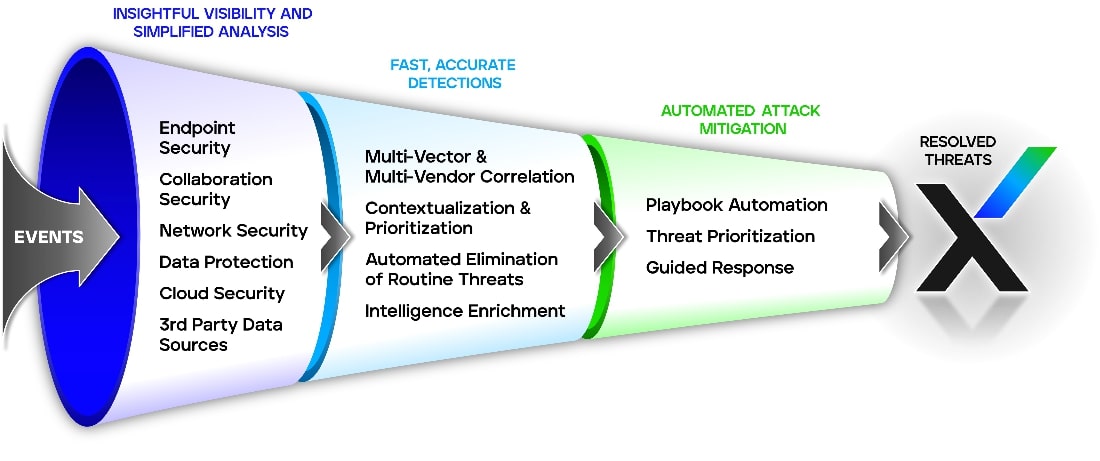
Why Trellix XDR?
- Ingests data from a wide range of Trellix best-of-breed native security controls
- Open data integrations from 1000+ third-party sources out of the box
- Multi-vector, multi-vendor detections that prioritize threats
- Extends contextualization with threat intel from native and third-party sources
- Built-in playbooks for SaaS-based and on-premises response actions and orchestration
You can check out the full report from Gartner here to learn more about the vendor strategies best designed to deliver on the promise of XDR for your business.
1 Gartner, 2022 Magic Quadrant™ for Endpoint Protection Platforms (EPP), By Peter Firstbrook, Chris Silva, 31 December 2022
Gartner, 2022 Market Guide for Data Loss Prevention (DLP), By Ravisha Chugh, Andrew Bales, 19 July 2022.
Gartner, 2022 Market Guide for Network Detection and Response (NDR), By Jeremy D'Hoinne, Nat Smith, Thomas Lintemuth, 14 December 2022
Gartner, 2023 Gartner Market Guide for Email Security, By Ravisha Chugh, Peter Firstbrook, Franz Hinner, 13 February 2023
Gartner, 2023 Market Guide for Mobile Threat Defense (MTD), By Dionisio Zumerle, Chris Silva, 10 January 2023
2 Gartner, 2023 Market Guide for Extended Detection and Response, By Thomas Lintemuth, Peter Firstbrook, 17 August 2023.
Gartner is a registered trademark and service mark and Magic Quadrant is a registered trademark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and are used herein with permission. All rights reserved . Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
