The
Cyberthreat report
The
Cyberthreat report
April 2025
Insights Gleaned from a Global Network of Experts, Sensors, Telemetry, and Intelligence
October 1, 2024 - March 31, 2025
The CyberThreat Report
Authored by the Trellix Advanced Research Center, this report (1) highlights insights, intelligence, and guidance gleaned from multiple sources of critical data on cybersecurity threats and (2) develops expert, rational, and reasonable interpretations of this data to inform and enable best practices in cyber defense. This edition focuses on data and insights captured primarily between October 1, 2024 - March 31, 2025.
- A look into the evolving APT landscape
- Deep dive on China’s threat apparatus
- Leaks and resurgence: Ransomware's evolution and Cl0p’s return
- Cybercriminal use of AI
- Complex attack chains and increased exploitation of vulnerabilities
- Additional attack methods on the rise: Phishing, password sprays, and info-stealers
Preface
“Give us the tools, and we will finish the job.” Winston Churchill said it best, and it’s a mantra we live by in cybersecurity. After all, our work isn’t just about the products and services that look flashy on a marketing campaign, but rather it’s about shared intelligence, rigorous research, and our collective mission to keep the bad guys up at night.
Over the past six months, the Trellix Advanced Research Center has kept its eyes on everything from evolving APT landscapes, to the resurgence of ransomware gangs, and to the ongoing uptick in AI-fueled cybercrime. This may be the most active moment in history when it comes to cyber attacks targeting the United States. Our telemetry shows there was a 136% increase in detections targeting the US in Q1 2025 alone.
As a result, our team has pieced together an ever-sharpening picture of how threats form, flourish, and - most importantly - how they can be stopped. Throughout this report, you’ll find detailed insight into the methods and motivations of criminal adversaries worldwide; often hackers acting as proxies for nation-state affiliates.
Like the safety harness we use when mountain climbing, good threat intelligence isn’t about slowing anyone down; it’s about enabling bolder moves and increasing the likelihood of success. A safety harness allows a climber to reach new heights they otherwise could not have achieved.
Our goal with this report is to share tools with our customers. These tools include the insights, intelligence, and real-world guidance based on the critical data we’ve gathered across a wide range of global threats. It is my sincere hope this information will enable the cybersecurity community to move faster, act smarter, and stop cybercriminals in their tracks.
So, with these tools in hand, let’s now work together to “finish the job.”

Head of Threat Intelligence, Trellix
Introduction
The last six months have realized further intensification of the cyber domain–driven by dramatic shifts in geopolitics, the economy, and technological advancements.
In this report, our Trellix Advanced Research Center takes you through the geopolitical levers changing the course of the cyberscape and details the latest tactics, techniques and procedures gaining favor by threat actors around the world.
Welcome to the CyberThreat Report: April 2025 from the Trellix Advanced Research Center.
Geopolitical events impacting the cyber domain
Intensification of the Russia-Ukraine conflict
As the Russia-Ukraine conflict entered late 2024 and early 2025, the intensity of the war escalated. One of the most striking developments during this period was both sides' intensified use of hybrid warfare tactics. Cyberattacks, disinformation campaigns, and economic warfare became central to the conflict. Specifically, Russia’s cyber capabilities were aggressively deployed to target Ukraine's critical infrastructure, including energy grids, financial systems, and government communications. In response, Ukraine fortified its cyber defenses and launched offensive cyber operations against Russian assets
Trellix telemetry data identified a notable increase in threat activity linked to Russia-aligned cyber actors, particularly the Sandworm team, also known as APT44, during the final quarter of 2024. Russia's Sandworm is widely regarded as one of the most dedicated and persistent cyber groups supporting Russian military operations. Compared to the first and second quarters of 2024, this uptick in cyber operations suggests a possible intensification of cyber warfare strategies targeting Ukrainian infrastructure, with the potential for broader destabilizing effects.
Most notably, Trellix telemetry data shows a substantial uptick in threat activity linked to Sandworm group throughout August 2024. During this same period, Russia executed its largest series of missile and drone attacks against Ukraine since the start of the conflict. The timing and scale of these cyber operations indicate these threat activities were likely strategically timed to coincide with the missile and drone strikes, amplifying the impact of the physical attack. This strategic overlap of cyber and kinetic operations highlights the growing trend of hybrid warfare, where state actors leverage both physical and digital means in parallel to achieve greater strategic objectives.
Detections from Russia’s Sandworm related IoCs
US trade policy shifts
In early 2025, the US government introduced a series of trade measures, including tariffs affecting multiple countries. These policy shifts resulted in responses from major trading partners, such as the European Union, China, and Canada, contributing to broader economic uncertainty globally.
In November 2024, telemetry data identified an increase in cyber activity attributed to China-linked threat actors. This uptick aligned with significant geopolitical events, including the outcome of the US presidential election and the announcement of new tariffs on Chinese imports.
While the timing of the increased cyber activity aligns with these economic developments, establishing a definitive causal relationship remains challenging. Nevertheless, economic policy shifts such as the introduction of tariffs can sometimes correlate with heightened cyber activity, potentially reflecting attempts by threat actors to exert influence, create disruption, or signal broader strategic intentions.
Detections from China-affiliated threat actor group related IoCs
Shifts in US foreign policy and heavy sanctions against Iran
Iran’s cyber operations primarily centered around espionage, information warfare, and destructive activities. From the threat activities observed, most cyberattacks against Israel in 2024 have been carried out by a mix of Iranian state-backed advanced persistent threat groups and hacktivists, acting as a force multiplier to increase the scale and impact of these attacks. These groups leverage cyber tactics as part of a broader strategy to destabilize Israel's digital infrastructure, disrupt critical services, and convey political messages. We’ve seen recurring disruptive attacks against Israeli organizations by Iranian-affiliated groups as well as their proxy groups.
Cyber threats from Iran-linked threat actor groups have largely been consistent throughout the last quarter of 2024, indicating a sustained and ongoing effort in their cyber campaigns. Most notably, Trellix telemetry detected a rise in threat activity from Iran-linked threat groups in February 2025. This increase in cyber operations suggests these groups may have ramped up their efforts in response to specific geopolitical developments or as part of a broader strategic push. Specifically, Trellix assesses with moderate confidence the US reinstatement of heavy sanctions to impose maximum pressure on Iran, including crippling economic sanctions, diplomatic isolation, and military deterrence, coupled with its active role in supporting Israeli military operations against Iranian interests, likely led to an increase in Iranian cyber threat activity in recent months.
Detections of Iranian threat actor group related IoCs
Key Findings
A look into the evolving APT landscape
- Threat landscape intensification: Threat detection volume raised 45% from Q4 2024 to Q1 2025, along with an increase in more sophisticated and targeted attacks, a broader range of active campaigns, and geographical shifts.
- Telecom heavily targeted: The telecommunications sector had the most APT related detections, receiving 47% of all detected activity, followed by transportation and shipping. Notably, APT detections targeting the telecom sector increased 92% in Q1 when compared to the previous quarter.
- China remains prolific: The most active APT groups were China’s APT40 and Mustang Panda, with the two groups generating 46% of all detected APT activity. China-aligned APT41 (113%) showed a significant increase in activity in Q1 2025 relative to the previous quarter.
- Target on the US, Türkiye: For the third consecutive issuance of this report, Türkiye remains the country most often targeted by APT actors, generating 38% of detections. Notably, there was a 136% increase in detections targeting the US in Q1 2025, up from Q4 2024.
Deep dive on China’s threat apparatus
Offensive cyber capabilities: China-affiliated threat actors continued to evolve and refine their tactics to remain effective in their operations while minimizing the risk of attribution.
- Increasing sophistication: There was a notable reliance on exploiting zero-day vulnerabilities and known vulnerabilities in commonly used network edge devices versus traditional methods like spear-phishing and social engineering. Further, the use of Operational Relay Box (ORB) networks in attacks grew considerably.
Leaks and resurgence: Ransomware's evolution and Cl0p’s return
Escalation of threats: The ransomware landscape in Q4 2024 and Q1 2025 was marked by a noticeable escalation in the frequency and impact of cyber incidents.
Cl0p’s comeback: A massive spike in victim posts from Cl0p was observed in March 2025, when Cl0p published more victim posts than any other group in a single month during this reporting period.
RansomHub’s continued dominance: RansomHub maintained its leadership position as the most active group, while LockBit reduced activity. Emerging groups include Funksec and Vanhelsing as new threats, while Babuk 2.0 is an impersonation attempt.
Persistent targeting of critical sectors: The industrial, healthcare, and consumer services were heavily impacted, with the industrial sector the target of more than one-third of ransomware detections.
Continued geographic concentration: The United States remains the primary target of activity and was the reported victim in 58% of ransomware posts, up from 42% in our last report.
Cybercriminal use of AI
Credentials at scale for $0.30 USD: Sophisticated machine learning models with the ability to process, de-duplicate, and validate large volumes of stolen credentials in real-time were found for sale for $0.30 USD on the black market.
Telegram bot powered by Gemini: A bot was for sale for $10 USD a week that leverages AI trained on criminal datasets to enable automated fraud operations and social engineering attacks.
Voice cloning for human-like interaction: Profound developments in AI-based voice synthesis technology were observed, enabling human-like interactions across multiple languages–particularly noteworthy in its ability to clone voices and maintain context-aware conversations.
- ChatGPT to advance ransomware operations: Black Basta was observed to use ChatGPT and other AI tools to create fraudulent formal letters in English, paraphrase text, rewrite C#-based malware in Python, debug code, and collect victim data.
Complex attack chains and increased exploitation of vulnerabilities
Increased volume: It is projected 2025 will see 41,000 to 50,000 new CVEs.
Key vendors: Microsoft, Ivanti, and Fortinet were particularly affected, with malicious actors exploiting their products. Further, an emerging trend indicates increased targeting of security vendors to infiltrate cybersecurity infrastructure.
- Abuse of zero-days: Notably, we observed several zero-day exploits, underscoring the agility and sophistication of modern cyber adversaries.
Additional attack methods on the rise: Phishing, password sprays, and info-stealers
Phishing persists: Phishing remains the most prevalent initial access vector, followed by exploit techniques. A spike in phishing attacks was observed during December and January, due to several attempts to distribute malware disguised as PDFs using MSI installers associated with the Leonem malware group.
Expanding surface for password sprays: While password spray attempts targeting Microsoft 365 grew 21% in Q1 2025 compared to Q4 2024, attempts targeting Cisco ASA VPN increased 399%. Interestingly, attacks targeting Okta had a sharp decrease.
- More use of InfoStealers: An increasing number of InfoStealers has also been observed despite law enforcement action to take down the Redline and Meta stealers late in 2024.
Industry reports, vetted by Trellix Advanced Research Center
Significant attention on government: Government institutions far outpaced other sectors as a target of malicious activity, as the target of 14% of all malicious activity. Government was followed by the finance (8%), manufacturing (7%), IT (5%), technology (4%) and telecom (4%) sectors.
Abuse of legitimate tools: Adversaries continue to manipulate legitimate tools for malicious purposes. Visual Studio Code, GitHub, and PowerShell are among the legitimate applications most abused by threat actors.
Targeting across geos: Several campaigns demonstrated targeting across multiple countries, emphasizing the widespread nature of cyber threats. The US remained the top target of activity (9%), followed by Russia (5%), Ukraine (5%) and India (5%).
- Diverse range of actors: Several campaigns were attributed to known APT groups, including Stonefly (aka APT45, Silent Chollima, Andariel), Mustang Panda (aka CeranaKeeper), FIN7, and UNC5812, indicating the continued activity of state-sponsored actors. Financially motivated groups such as Evil Corp, Key Group, and Black Basta remain active, focusing on ransomware, data theft, and extortion.
Methodology overview
Experts from our Trellix Advanced Research Center gather the statistics, trends, and insights comprising this report from a wide range of global sources, both captive and open. The aggregated data is fed into our Insights and ATLAS platforms. Leveraging AI, machine learning, automation, and human acuity, the team cycles through an intensive, integrated, and iterative set of processes – normalizing the data, analyzing the information, and developing insights meaningful to cybersecurity leaders and SecOps teams on the frontlines of cybersecurity worldwide. For a more detailed description of our methodology, please see the end of this report.
Report analysis, insights, and data
A look into the evolving APT landscape
This report analyzes Advanced Persistent Threat (APT) activities detected during the fourth quarter of 2024 and the first quarter of 2025 based on data from the Trellix ATLAS Detection Data Set. The analysis reveals significant insights into global trends, prominent threat actors, and their evolving tactics, techniques, and procedures (TTPs).
From October 1, 2024 - March 31, 2025, the Trellix Advanced Research Center observed the following:
Threat landscape intensification: Threat detection volume raised 45% from Q4 2024 to Q1 2025. In addition to volume, we observed more sophisticated and targeted attacks, a broader range of active campaigns, and geographical shifts in targeting to focus on developed economies.
Telecom and technology heavily targeted: Critical infrastructure was heavily targeted by APT groups during the period observed in this report. The telecommunications sector had the most APT related detections, receiving 47% of all detected activity, followed by transportation and shipping. Threats to technology increased more than 119% from Q4 2024 to Q1 2025.
China remains prolific: The most active APT groups were China’s APT40 and Mustang Panda, with the two groups generating 46% of all detected APT activity. China-aligned APT41 (113%) showed a significant increase in activity in Q1 2025 compared to the previous quarter. Learn more about the China APT apparatus.
- A more sophisticated set of tools: The Trellix Advanced Research Center observed the development and use of more mature, sector-specific TTPs, including sophisticated obfuscation and enhanced evasion techniques. Living-off-the-land (LOTL) binaries like PowerShell and Command Line Interface (cmd.exe) remained the predominant attack tools, and 56% of tool usage involves built-in Windows utilities.
Security teams should ensure they have advanced monitoring capabilities for legitimate tools so they can detect anomalies. Further, investing in sector-specific defense, tool-based detection, geographic threat modeling, and critical infrastructure protection should be prioritized.
Overview of APT activity by region, sector, actor, and tooling
47
The telecom sector was the target of 47% of all detected APT activity. Additionally, threats to telecom increased 92% from Q4 2024 to Q1 2025.
China-aligned Mustang Panda and APT40 generated a combined 46% of all APT activity, and APT41’s activity increased 113% in Q1 compared to Q4.
Notably, there was a 136% increase in detections targeting the US in Q1 2025, up from Q4 2024.
For the third consecutive issuance of this report, Türkiye remains the country most often targeted by APT actors, generating 38% of detections.
Monthly APT related detection trends
Geographical distribution of APT activity
As the primary target of APT detections, Türkiye accounted for 38% of total detections from October 2024 to March 2025. While Türkiye's dominance decreased but remained significant in Q1 2025, US share increased substantially, and Qatar emerged as a new target.

Why Türkiye?
Potential interest in Türkiye can be attributed to its strategic position as a crucial crossroads between Europe and Asia, its significant role in regional geopolitics, and its involvement in various international diplomatic initiatives. The country’s strategic geopolitical position and its role as a NATO member make it a valuable target for intelligence gathering about Western military and diplomatic activities.
The top 10 affected countries account for 77% of all APT detections:
Geographic distribution of detections
Q4 2024 and Q1 2025 geographic distribution of detections
Threat actor analysis
During the period observed in this report, APT40 overtook Mustang Panda as the most active threat actor, and APT41 (113%) showed a significant increase in activity in Q1 2025 compared to the previous quarter.
Top 10 threat actors responsible for detections
Q4 2024 and Q1 2025 top threat actors by detections
Analysis of most aggressive APT groups
APT40 is a sophisticated Chinese state-sponsored threat actor active since 2009. The group, also known by various aliases, including Leviathan, BRONZE MOHAWK, and Gingham Typhoon, has demonstrated a particular focus on maritime-related targets and industries aligned with China's Belt and Road Initiative, which explains their targeting of India and Indonesia. As for China itself, APT40's activities within China likely focus on domestic entities that may pose challenges to state interests or require monitoring for internal security purposes.
Mustang Panda is a sophisticated Chinese state-sponsored threat actor active since 2014. The group, known by various aliases, including Earth Preta, Bronze President, and Twill Typhoon, primarily targets governmental organizations, telecommunications companies, and non-governmental organizations.
APT29, also known as Cozy Bear or Midnight Blizzard, is a sophisticated state-sponsored cyber-espionage group active since 2008. The group is believed to be operating on behalf of Russia's SVR (Foreign Intelligence Service), with their primary objective being the collection of intelligence from Western governments and their associated organizations. Their operations are notably aligned with events of political significance and foreign affairs that are of interest to the Russian Federation.
India (IN): 72.2%
China (CN): 12.6%
Indonesia (ID): 6.0%
Türkiye (TR): 5.9%
Mexico (MX): 3.3%
Türkiye (TR): 43.8%
Indonesia (ID): 24.7%
United States (US): 15.2%
Germany (DE): 9.6%
Nigeria (NG): 6.7%
Türkiye (TR): 61.0%
United States (US): 28.4%
Germany (DE): 7.7%
Panama (PA): 1.8%
Netherlands (NL): 1.3%
Telecom: 66.3%
Media & Communications: 18.4%
Technology: 6.0%
Transportation & Shipping: 4.8%
Finance: 4.8%
Media & Communications: 62.8%
Telecom: 18.4%)
Transportation & Shipping: 15.9%
Technology: 1.9%
Finance: 0.7%
Transportation & Shipping: 55.0%
Telecom: 40.4%
Finance: 2.2%
Business Services: 2.0%
Technology: 0.2%
PowerShell: 20.3%
IPRoyal Pawns: 19.9%
KrBanker: 19.9%
Netsh: 19.9%
TraffMonetizer: 19.9%
PlugX: 46.9%
Schtasks.exe: 17.1%
Cmd: 14.1%
Rundll32: 11.5%
Tasklist: 10.4%
Cobalt Strike: 29.7%
EnvyScout: 21.3%
Mimikatz: 18.3%
VaporRage: 16.4%
Net: 14.3%
Application Layer Protocol: 19.9%
Command and Scripting Interpreter: 19.9%
Native API: 19.8%
Network Share Discovery: 19.8%
File and Directory Discovery: 19.8%
DLL Side-Loading: 29.2%
File and Directory Discovery: 25.4%
Deobfuscate/Decode Files or Information: 16.0%
Web Protocols: 14.7%
Scheduled Task: 14.4%
Rundll32: 23.9%
Spearphishing Attachment: 20.3%
Web Protocols: 18.9%
Spearphishing Link: 18.8%
Ingress Tool Transfer: 18.1%
Sectoral impact
Analysis of the top affected sectors excluding unknown reveals the telecom sector as heavily targeted. When breaking down by quarters, there is a significant increase in APT detections targeting telecom (92%) and technology (119%).
Top 10 targeted sectors
Q4 2024 and Q1 2025 top targeted sectors
Tools and techniques
Analysis of the tactics, techniques, and procedures (TTPs) of APT groups observed during the period reflected in this report finds actors maturing and utilizing more sophisticated and advanced tooling.
Tool selection patterns: A heavy reliance on legitimate system and native Windows tools is observed, along with the increased use of LOTLbinaries and growing sophistication of post-exploitation tools.
Operational trends: Tools are likely chosen to blend with normal activity, while ensuring they have redundant capabilities and the ability to be used for evasion purposes. Custom malware is used less frequently.
Security implications: Attackers are selecting tools that provide persistent access mechanisms and advanced lateral movement to aid them in executing sophisticated multi-stage attacks.
Defense evasion focus: Memory-resident operations, fileless malware, and signed binaries are being used more frequently to support evasion.
- Future trends: The Trellix Advanced Research Center anticipates further increases in tool sophistication, greater emphasis on evasion, an evolution of post-exploitation frameworks, and more complex attack chains.
Its critical security teams use enhanced PowerShell monitoring to discover misuse and abuse. CISOs should also focus on command-line activity analysis and ensure rigorous credential access monitoring is in place.
Top 5 tool types
Top 5 tools used
PowerShell
16.8%
Used for command execution and automation
Notable increase in fileless malware delivery
Cmd
14.1%
Consistent usage across all threat actors
Often used in initial access and discovery phases
WMIC
9.0%
Primarily used for system enumeration
Significant role in lateral movement
Mimikatz
7.8%
Credential harvesting and privilege escalation
Increased usage in targeted attacks
Cobalt Strike
7.0%
Post-exploitation framework
Advanced persistent threat operations
Top 10 MITRE ATT&CK techniques
Who’s hacking the United States?
The United States was the target of 36% of detected APT activity in the period observed in this report. Notably, there was a 45% increase in detections in Q1 2025, up from Q4 2024. Türkiye precedes and Germany follows the United States as the most targeted by APT groups.
Detections are primarily attributable to APT groups aligned with China (47%)and Russia(35%), and the activity targeted the telecom (64%) and technology (28%) sectors.
Top 5 threat actor countries
Targeting the U.S.
Top 5 threat actor presence
Targeting the U.S.
Top 5 sector distribution
Targeting the U.S.
Top 5 tool usage
Targeting the U.S.
Top 5 MITRE ATT&CK techniques
Targeting the U.S.
Outlook on APTs
The global APT landscape is evolving rapidly, and sophistication is scaling with the use of legitimate tools and advanced evasion techniques. As we look ahead, attacks will likely continue to become more sophisticated and sector-specific, leading to further evolution in TTPs and tool combinations.
Deep dive on China’s threat apparatus
Cyber capabilities play an essential and growing role in China’s broader strategic objectives, serving as a key tool in its military and geopolitical efforts. Over the years, the Chinese government has consistently utilized its offensive cyber capabilities to advance a range of interests, from state-sponsored espionage and intellectual property theft to gaining long-term access to the critical infrastructure of rival nations. These activities enable China to gather sensitive data, disrupt adversarial systems, and maintain a competitive advantage across industries.
We assess with moderate confidence that China-affiliated threat actors will continue to evolve and refine their tactics, techniques, and procedures (TTPs) to remain effective in their operations while minimizing the risk of attribution. A key focus will likely be on ensuring their cyber campaigns remain discreet, making it more challenging for adversaries to directly link attacks to the Chinese government.
To achieve these objectives, China’s APT groups will likely continue to:
Leverage LOTL techniques
Weaponize network edge devices
Establish operational relay box networks for stealthier cyber espionage operations in the future
Targeting Edge Devices for Mass Exploitation
ZERO DAY
There has been notable reliance on exploiting zero-day vulnerabilities versus traditional methods like spear-phishing and social engineering
Based on recent campaign trends, Chinese APT groups have been evolving their strategies, gradually moving away from traditional methods like spear-phishing and social engineering as the primary means for gaining initial access to their targets. These techniques, which have historically been effective for infiltrating specific individuals or organizations through tailored, deceptive communications, are being increasingly supplemented, or in some cases replaced, by more direct and sophisticated approaches.
One notable shift has been the growing reliance on exploiting zero-day vulnerabilities, as well as leveraging known vulnerabilities in commonly used network edge devices—such as routers, firewalls, and other critical infrastructure components. These vulnerabilities allow the threat actors to bypass traditional security defenses more efficiently and gain unauthorized access to systems on a much larger scale. By targeting network edge devices, which often serve as the entry points to an organization’s broader network, Chinese APT groups are able to compromise systems without the need for targeted social engineering efforts.
To combat threats at the edge, organizations should ensure they’re taking action outside of regular patching and firmware updates/upgrades. In practice, this looks like adopting network detection and response (NDR) and implementing strong network segmentation, Zero Trust, virtual patching, and strong operational threat intelligence.
This shift toward exploiting vulnerabilities represents a more automated, scalable approach to cyberattacks.
Mass exploitation campaigns: It enables Chinese threat actors to conduct mass exploitation campaigns that can potentially affect a wide range of targets, including critical infrastructure, government organizations, and private sector networks.
Widespread access: By focusing on these vulnerabilities, attackers can gain widespread access to vulnerable systems, often with a much lower detection risk compared to traditional social engineering techniques.
Efficiency and speed: Additionally, this tactic allows for faster deployment of attacks across multiple targets, enabling the APT groups to achieve their objectives more quickly.
The move away from spear-phishing and social engineering also reflects a broader trend of adapting to increasingly sophisticated defense mechanisms, where relying on direct exploitation of software vulnerabilities allows threat actors to bypass increasingly sophisticated email filters, user-awareness programs, and multi-layered security systems. This shift indicates the changing landscape of cyber threats, with APT groups moving towards more advanced, persistent, and large-scale operations that can impact a broader range of targets simultaneously.
As Chinese APT groups continue to refine their techniques, it is likely the exploitation of network edge devices and the use of zero-day vulnerabilities will become even more prominent in their future campaigns, requiring organizations to adopt more proactive and advanced security measures to detect and mitigate these sophisticated, high-impact attacks.
Use of ORB networks for espionage operations
While Operational Relay Box (ORB) networks have been used for several years, their adoption and sophistication has grown considerably, particularly within Chinese cyber operations. These networks are leveraged by state-sponsored groups to perform highly covert operations spanning multiple industries, from governmental and military targets to intellectual property theft and economic espionage. These ORBs facilitate a range of different threat clusters simultaneously, meaning multiple cyberattack groups can operate within the same network infrastructure without raising suspicion.
The growing popularity and sophistication of Chinese ORBs underscore the increasing reliance on proxy networks to evade detection and expand the reach of cyber espionage campaigns. This trend highlights the need for advanced detection systems capable of monitoring and analyzing network traffic at a granular level, especially when conventional methods may not suffice to identify the use of compromised devices and VPNs. With ORBs evolving in complexity and scale, they represent a significant challenge to cybersecurity professionals tasked with defending against these highly adaptive and stealthy forms of cyberattacks.
Heavy use of living-off-the-land tools
China’s nation-state cyber operators have increasingly relied on LOTL techniques as part of their cyber operations to maintain persistent and undetected access to information technology (IT) networks. LOTL techniques leverage existing legitimate tools, features, and functions present within the target environment to execute their malicious activities. By utilizing tools native to the system or commonly used within an organization, attackers can traverse networks and conduct operations without triggering traditional security alarms.
This approach allows them to blend in with normal network activity, making it far more difficult for security measures to detect their presence or distinguish their actions from legitimate user behavior. As a result, LOTL techniques significantly reduce the likelihood of the attacker being flagged as suspicious, giving them more time to execute their objectives while evading detection. These tactics are increasingly favored because they avoid the need for the attacker to introduce external or easily identifiable tools, making them more stealthy and harder to trace.
Volt Typhoon
As a case in point, Trellix telemetry data shows that Volt Typhoon makes heavy use of command-line tools like Cmd (Command Prompt) and ARP (Address Resolution Protocol) to explore the system and conduct network discovery after gaining initial access to a target environment. The attackers execute a variety of commands to gather data about the system's resources, user accounts, and running processes. At the same time, ARP can help map out network infrastructure by identifying devices and their respective IP addresses.
For lateral movement, our data suggest that Volt Typhoon threat actors utilize Dnscmd (a command-line utility for DNS server management) to manipulate DNS records, enabling further network traversal and persistence through DNS-based changes. They also leverage Impacket, a suite of Python tools, for remote code execution, system enumeration, and maintaining persistent access. For data exfiltration, Volt Typhoon uses 7-Zip to compress stolen data for easier transfer and FRP (Fast Reverse Proxy) for tunneling, bypassing firewalls and NAT (Network Address Translation) devices by establishing reverse shell connections to external systems. These tools enable efficient and covert exfiltration, evading detection by traditional security measures.
To maintain long-term access to the compromised network, Volt Typhoon employs stealthy persistence techniques, as indicated by Trellix detection data. They use tools such as Dnscmd and Ldifde (LDAP Data Interchange Format Directory Exchange) to modify DNS records, ensuring malicious traffic is routed to their command and control servers. Additionally, Ldifde is utilized to manipulate Active Directory (AD) data, creating or altering accounts to maintain access even if initial entry points are detected and blocked. These methods make it difficult to fully remove their presence from the compromised network.
Salt Typhoon
Similarly, many of the top-ranked tools detected in use by Salt Typhoon are legitimate system utilities or widely used software, which makes them particularly effective for evading detection. These tools include, but are not limited to, Comsvcs.dll (a Windows system file for COM+ services), Dnscmd (a command-line utility for DNS server management), Ldifde (a tool for importing and exporting data from Active Directory), and Cmd (the Windows Command Prompt). This strategy of leveraging existing system utilities underscores the group’s advanced tactics for stealthily navigating and compromising target environments.
The above-mentioned top detected tools in Salt Typhoon’s operations show exceptionally high detection counts, indicating these tools are frequently deployed throughout their campaigns. The repeated use of these tools across multiple attacks suggests Salt Typhoon has strategically refined and standardized its toolkit over time, making it a core part of its attack methodology.
Flax Typhoon
Our detection data shows Flax Typhoon frequently uses Unix and Linux native tools in its threat activities, likely suggesting their focus is on targeting Linux-based systems during the reporting period. By tailoring their tactics to exploit vulnerabilities in Linux infrastructures, the threat actor can leverage tools specifically designed for Unix/Linux systems to blend in with normal system operations and avoid detection.
Leaks and resurgence: Ransomware's evolution and Cl0p’s return
The ransomware landscape in Q4 2024 and Q1 2025 was marked by a noticeable escalation in the frequency and impact of cyber incidents. Prominent among these events was the significant exposure of internal operations within the notorious Black Basta ransomware group. The unprecedented chat leaks, analyzed comprehensively in our research, offered an unparalleled glimpse into the inner workings, operational tactics, and strategic planning of one of today's most prolific cybercriminal enterprises.
The Black Basta leaks revealed critical insights into their negotiation tactics, target selection criteria, and the group's sophisticated coordination to maximize both operational efficiency and profitability. Particularly striking was the group's reliance on structured, corporate-style communication channels and their systematic approach to managing ransom negotiations. These revelations have underscored the alarming evolution of ransomware gangs into highly organized, methodical entities, mirroring legitimate enterprises in structure and discipline.
Throughout this period, other noteworthy ransomware operations continued to pose substantial threats, underscoring the urgent need for robust cybersecurity strategies across sectors.
High-profile attacks targeting critical infrastructure, healthcare systems, and major corporations resulted in extensive financial and operational disruptions, emphasizing ransomware's persistent threat to global security and stability.
From October 2024 - March 2025, the Trellix Advanced Research Center observed the following:
Cl0p’s dramatic resurgence: A massive spike in victim posts was observed in February and March 2025
RansomHub’s continued dominance: RansomHub maintained its leadership position as the most active group
Emergence of new threat actors: Following law enforcement action against established groups, new actors filled gaps
Persistent targeting of critical sectors: The industrial, healthcare, and consumer services were heavily impacted
Continued geographic concentration: The United States remains the primary target of activity
This report examines these trends in detail, providing actionable intelligence for security leaders navigating this evolving threat landscape.
The ransomware landscape is constantly evolving, punctuated by insights from the Black Basta leaks; it reinforces the imperative for continuous vigilance, adaptive threat intelligence, and collaborative defense strategies. Organizations must recognize the increasingly sophisticated nature of ransomware groups, preparing accordingly to mitigate potential impacts and safeguard against future disruptions.
34
The industrial sector was the target of more than one-third of ransomware posts
RansomHub maintained position as the ransomware group behind the most victim posts
The US was the target of 58% of ransomware victim posts, up from 42% in our last report. Trellix telemetry also observed more than 40 unique campaigns targeting the US, and the US was the target of 39% of detected ransomware activity.
For this report, the following section looks at two sets of data:
- Victim posts: Public posts from groups sharing the details of their victims
- Trellix telemetry: Data from the Trellix ATLAS campaign and detection data set
Ransomware group activity
The ransomware ecosystem continues to evolve, with RansomHub maintaining its position as the most active group. However, the most notable development is Cl0p’s dramatic resurgence, firmly established as the second most active group. This marks a significant shift from our last report, when Cl0p was not among the top five actors.
Groups with most victim posts
Cl0p’s remarkable comeback
Cl0p’s activity shows a striking pattern over the reporting period.
Cl0p victim posts by month
This exponential growth in activity culminated in March 2025, when Cl0p published more victim posts than any other group in a single month during this reporting period. Our analysis suggests this surge is linked to Cl0p’s exploitation of vulnerabilities in managed file transfer systems, particularly targeting Cleo’s products through CVE-2024-50623 and CVE-2024-55956.
The resurgence of Cl0p demonstrates how quickly ransomware groups can adapt and return to prominence. Security leaders should avoid complacency when major threat actors appear to be in decline, as they often regroup and return with new tactics. Maintain a defense-in-depth approach that addresses current and emerging threats, with particular attention to critical data transfer systems that can serve as entry points for widespread compromise.
LockBit3’s diminished presence
LockBit3, once a dominant force, has seen its activity significantly reduced following sustained law enforcement actions. With just 40 victim posts over the six months (compared to 423 from RansomHub), LockBit3 has fallen out of the top 20 most active groups. This decline demonstrates the potential effectiveness of coordinated international law enforcement efforts when sustained over time.
Emerging groups
Between October 2024 and March 2025, we’ve witnessed several new ransomware operations, with Funksec and Vanhelsing standing out as legitimate new threats, while Babuk 2.0 has been identified as an impersonation attempt.
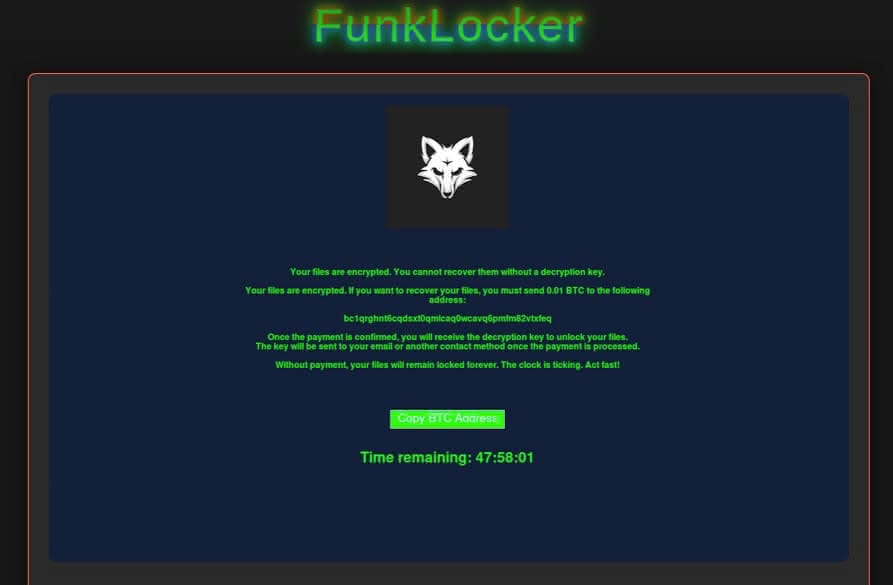
Funksec: The new powerhouse
Funksec has quickly established itself as one of the most sophisticated new ransomware operations. Since its emergence in December 2024, the group has demonstrated a level of technical sophistication and organizational structure that sets it apart from typical newcomers in the ransomware landscape.
The group's ransomware is built using the Rust programming language, demonstrating their technical acumen and focus on modern development practices. Their operation has already evolved to version 2.0, incorporating enhanced anti-detection capabilities and a comprehensive attack infrastructure.
What makes Funksec particularly noteworthy is their business approach. They've established a full-service criminal enterprise, operating a sophisticated Ransomware-as-a-Service (RaaS) model with multiple revenue streams. Their infrastructure includes a blog, auction site (FunkBID), and forum, showing a level of organizational maturity unusual for a new group.
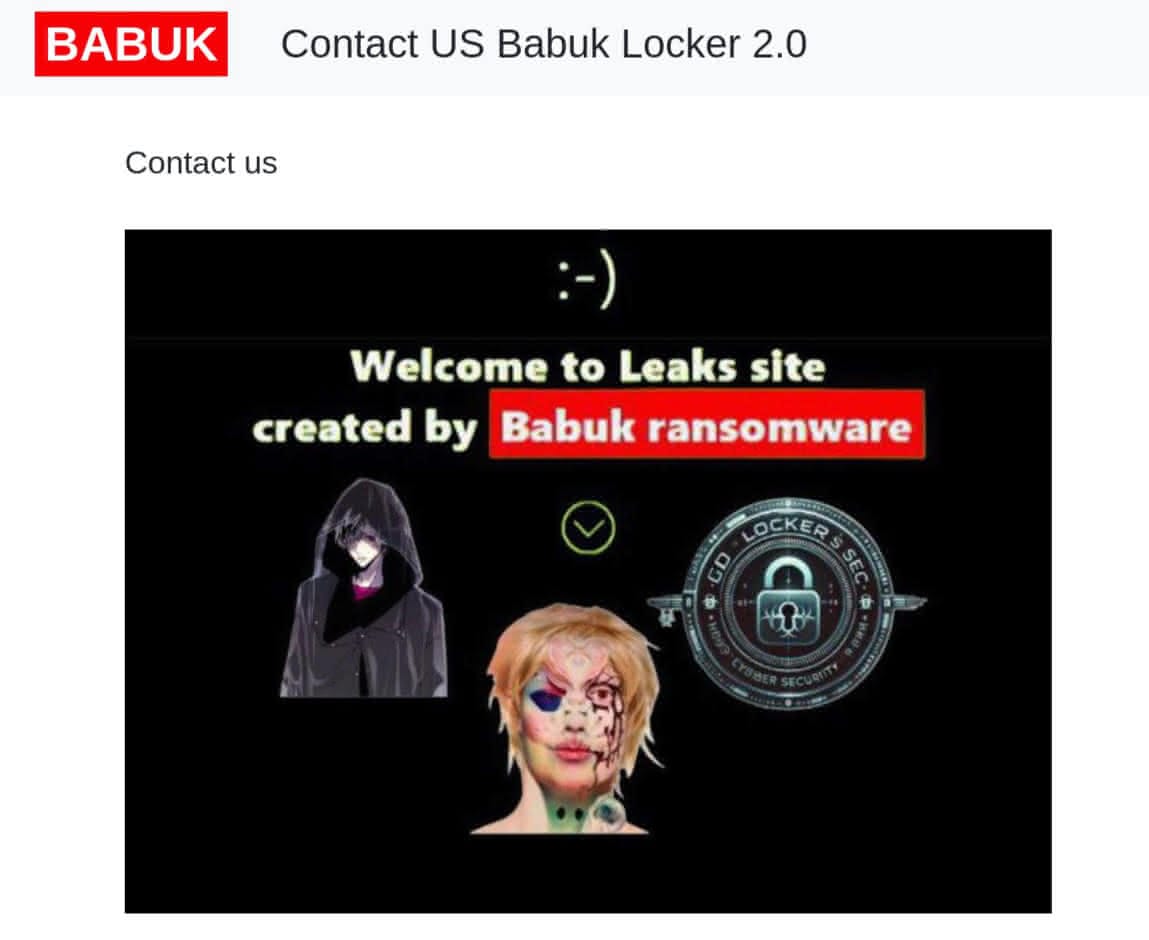
Babuk 2.0: The impersonator
Investigation into the supposed reemergence of Babuk as "Babuk 2.0" in early 2025 has revealed this to be an impersonation attempt rather than a legitimate ransomware operation. The group, operated by an actor using the handle "Bjorka," appears to be focused on data sales rather than traditional ransomware operations.
This impersonation attempt highlights a growing trend in the cybercriminal underground where actors attempt to capitalize on the reputation of established ransomware groups. The operation has been widely identified as fraudulent by underground forum members, primarily focusing on selling allegedly stolen data rather than conducting actual ransomware operations.
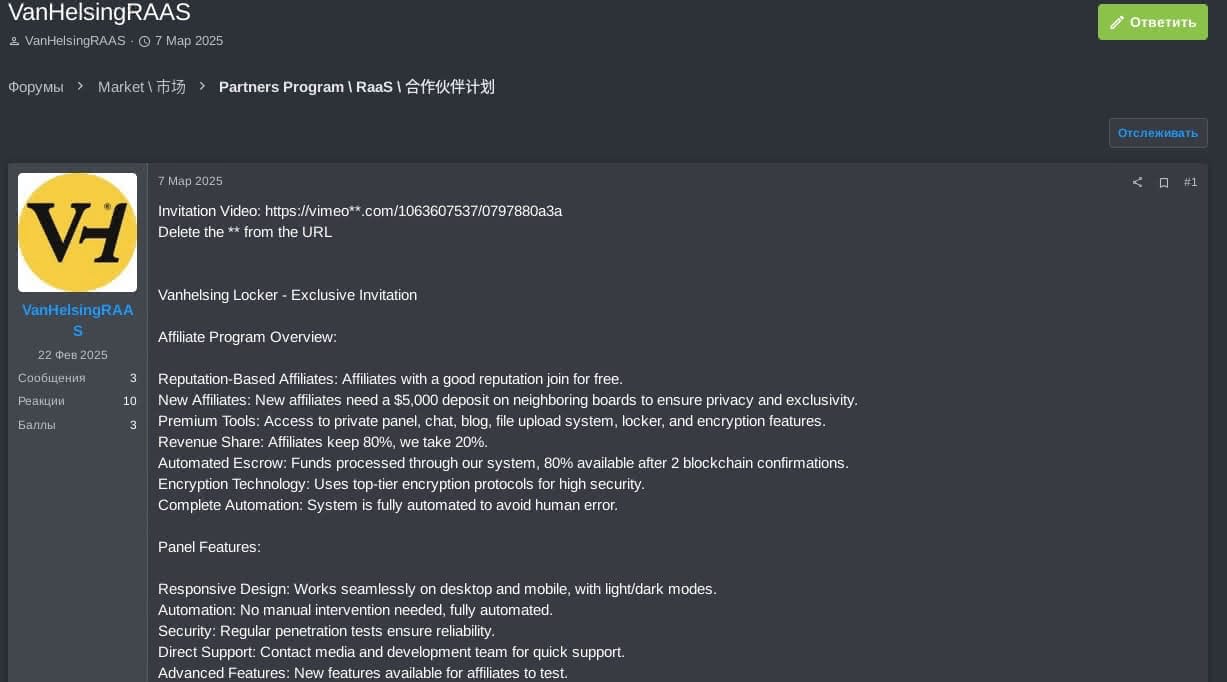
Vanhelsing: The new entrant
Vanhelsing represents the newest addition to the ransomware landscape, having emerged in March 2025. While their operations are still in their infancy, with only four recorded attacks, they've already demonstrated a capacity for sophisticated target selection and global reach.
The group has shown particular interest in high-value sectors, including electronics manufacturing, government institutions, and pharmaceutical companies. Their geographical focus appears to be primarily on Western nations, with confirmed activities in the United States, France, and Italy.
Given their recent emergence, technical details about their ransomware strain remain limited, and their operational patterns are still developing. However, their initial target selection suggests a well-planned and strategic approach to operations.
Targeted sectors
Based on ransomware group sites, the industrial sector emerged as the overwhelming target for ransomware actors, accounting for over a third of all attacks with identified sectors. This represents a significant concentration of activity and suggests ransomware groups are increasingly focused on organizations where operational disruption can create maximum pressure to pay.
Consumer services organizations rank second, highlighting the targeting of businesses that directly interface with customers, where service disruptions can quickly lead to reputational damage and revenue loss. Technology companies remain highly targeted, likely due to their valuable intellectual property and the potential for supply chain attacks that could affect their customers.
Healthcare organizations continue to face significant threats, consistent with previous reporting periods. The persistent targeting of this sector is particularly concerning given the potential impact on patient care and safety.
Finally, the correlation between campaigns and detections shows consistent targeting of critical sectors with government/administration, finance, and manufacturing sectors generating the most detections of ransomware activity.
Sectors with most victim posts
Sectors with most detections
Geographic distribution
The United States continues to be the overwhelming focus of ransomware attacks, accounting for nearly 58% of all victim posts with identified locations. This represents a significant increase from the previous reporting period (42%), suggesting ransomware groups are intensifying their focus on US-based organizations.
While developed Western economies remain primary targets, India’s position in the top five most targeted countries represents a notable shift. This suggests ransomware groups are increasingly expanding their focus to include rapidly developing economies with growing digital infrastructure. India’s rise in the rankings indicates organizations in emerging markets should be particularly vigilant about ransomware threats.
Countries with most victim posts
Countries with most detections
Countries with most campaigns observed
For government agencies, industrial organizations, and financial institutions, enhance monitoring on critical systems such as PowerShell and other command-line tools. Deploying geolocation-based access controls and applying additional security measures in high-risk regions is also recommended.
TTPs detected
PowerShell and Cobalt Strike remain the preferred tools for ransomware operators.
Top 10 tools and malware
Security operations teams should monitor for anomalies in the use of legitimate administrative tools (e.g., Net, PsExec, AnyDesk) and secure file transfer systems through regular patching and enhanced surveillance. This should also include extending security controls beyond Windows to include Linux and mobile platforms.
Ransomware outlook
The October 2024 to March 2025 period reinforces ransomware remains a dynamic and persistent threat. While law enforcement actions have disrupted some major players, the overall ecosystem continues to thrive through adaptation and innovation. The dramatic resurgence of Cl0p, continued dominance of RansomHub, and emergence of new actors all point to a threat landscape that will continue to challenge security teams throughout 2025.
To prioritize operational resilience and adaptability, organizations should:
- Establish robust backup strategies with offline copies and enforce strict incident response planning.
- Conduct frequent security assessments and update playbooks to keep pace with emerging tactics.
- Prioritize industrial security by scrutinizing the interconnection between operational technology (OT) and IT environments.
Cybercriminal use of AI
This section presents significant underground forum advertisements observed since our last report, detailing illicit tools and services offering AI capabilities.
Credentials at scale for $0.30 USD: Sophisticated machine learning models are used to process, de-duplicate, and validate large volumes of stolen credentials in real-time then sell them for profit.
Telegram bot powered by Gemini: A bot for sale for $10 USD a week leverages AI trained on criminal datasets to enable automated fraud operations and social engineering attacks.
Voice cloning for human-like interaction: Profound developments in AI-based voice synthesis technology, enabling human-like interactions across multiple languages–particularly noteworthy in its ability to clone voices and maintain context-aware conversations.
- ChatGPT to advance ransomware operations: Black Basta was observed to use ChatGPT and other AI tools to create fraudulent formal letters in English, paraphrase text, rewrite C#-based malware in Python, debug code, and collect victim data.
Credentials shop with AI-powered records validation
On November 6, 2024, an underground threat actor Gabber77 posted on XSS forum an update to their thread called “GABBERS SHOP” (an online store selling URL:login:password records) stating the following:
Post Translation
Our dear customers. We are happy to inform you that our shop is working again. Thanks to the efforts of our programmer, who could link our database cleaning script with the artificial intelligence (AI), we now have a powerful tool that we can use to constantly clean our URL records for you. We've deleted all the garbage records from the entire database, and we are ready to offer it to you! Now only the correct records will be available in our logs. Also, in the next several days, new sections will be added to our shop: Selling logs from Android, Valid FTPs, IMAP, SMTP and many other features that will be announced this month. Our team works every day to improve our shop for you. Happy shopping.
The threat actor claims their GABBERS SHOP has consolidated over half a billion unique strings and the starting price for a URL begins at $0.30 USD. The Gabber77 allegedly implemented an AI-powered validation system for their criminal marketplace, focusing on automated data cleaning and verification. Their AI software seems to employ pattern recognition mechanisms to validate stolen credentials, significantly improving the efficiency and reliability of their illegal operations.
The automated nature of the system, combined with its high claimed accuracy rate, indicates sophisticated machine learning models are being used to process, de-duplicate, and validate large volumes of stolen credentials in real-time. This represents a significant evolution in the automation of criminal marketplaces, with AI being used to enhance the quality and reliability of illegal services.
AI-based Telegram management console
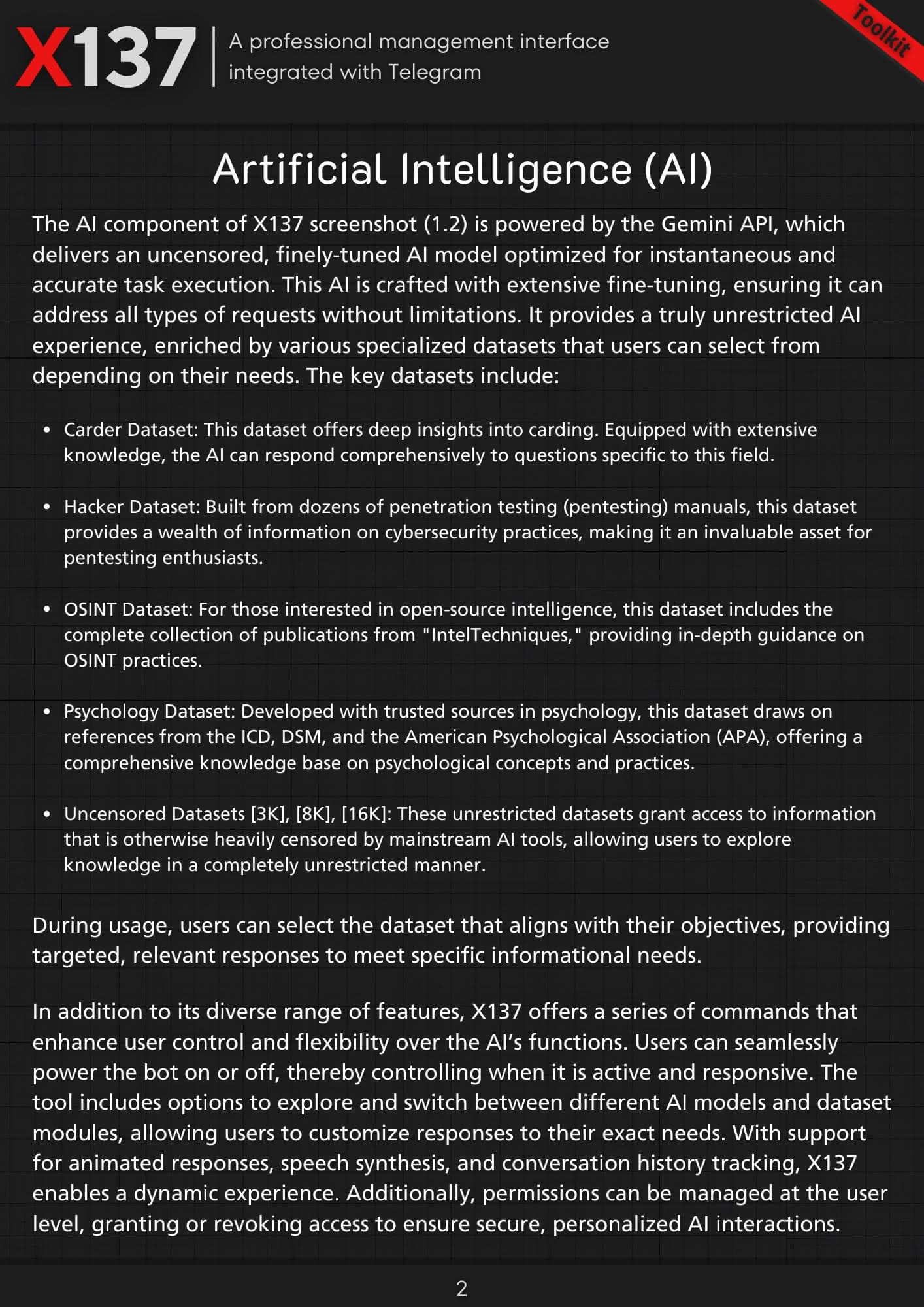
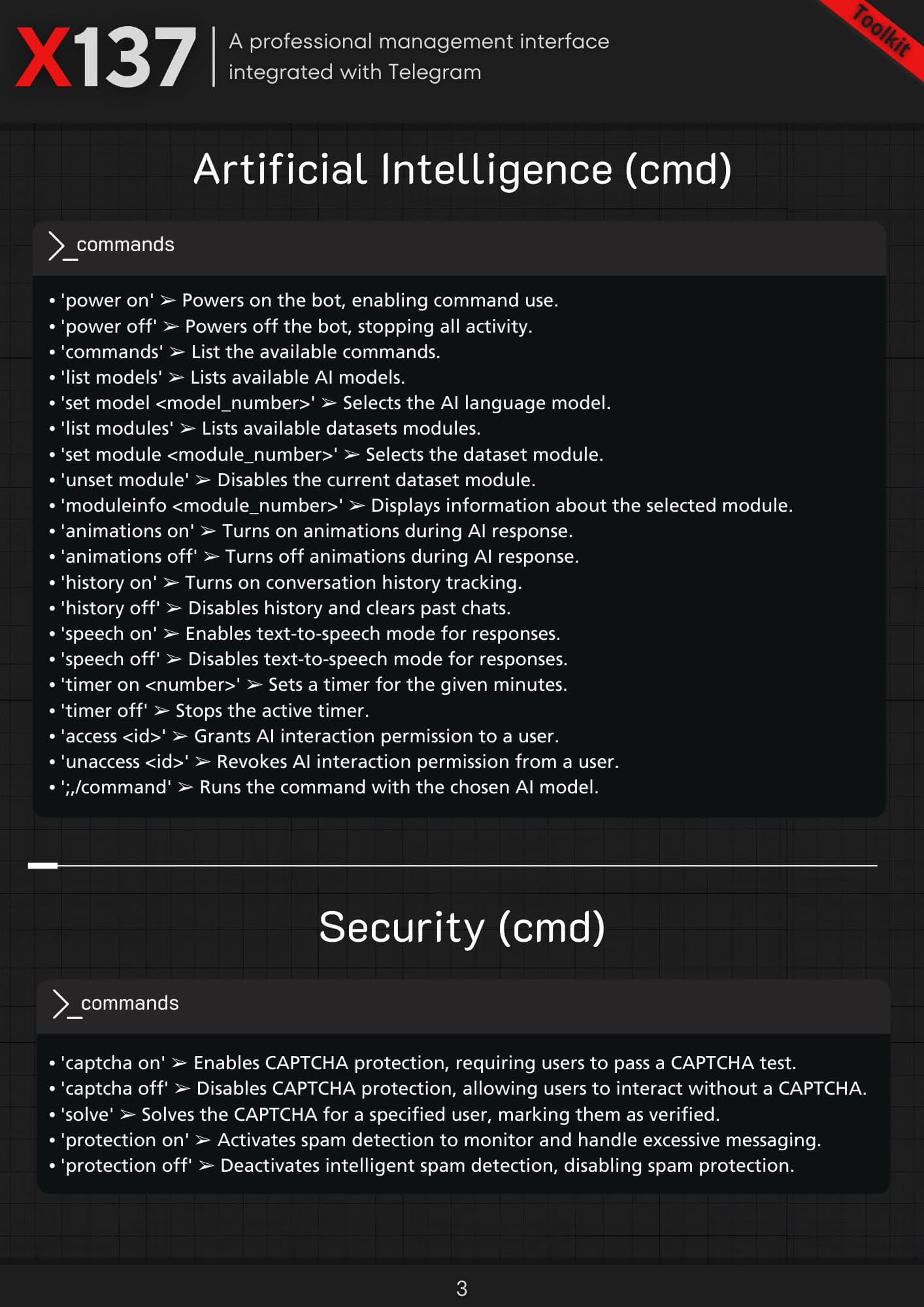
On November 12, 2024, an underground threat actor E-137 on BreachForums advertised their Telegram bot called “X137 Management Console” designed to enhance Telegram user experience. It offers a wide range of powerful features, including an AI component powered by Gemini API.
The actor E-137 advised their pricing varies from 10 USD weekly to 100 USD for 6 months of tool usage. According to the demo shared, the X137 has two AI models: PXS, a lightweight model optimized for speed and ideal for simple tasks, and NEX, a recommended larger model designed for accuracy and best for complex analysis and creative work.
The threat actor developed a sophisticated Telegram automation tool that leverages the Gemini API for censorship-free AI-powered tasks. The system's AI capabilities are specifically trained on criminal datasets, including carding, hacking, OSINT and other uncensored datasets, enabling automated fraud operations and social engineering attacks. The integration of the psychological dataset suggests the X137 tool can potentially leverage human behavior manipulation and exploit psychological vulnerabilities.
The Telegram bot’s AI implementation focuses on automated message analysis and response generation, allowing for scalable social engineering operations across multiple Telegram accounts simultaneously. Including specialized criminal datasets and OSINT capabilities indicates this tool is designed for coordinated fraud campaigns and intelligence-gathering operations, with the uncensored AI models handling target profiling, automated conversations, translation, and data collection.
Phone calls with AI voice cloning
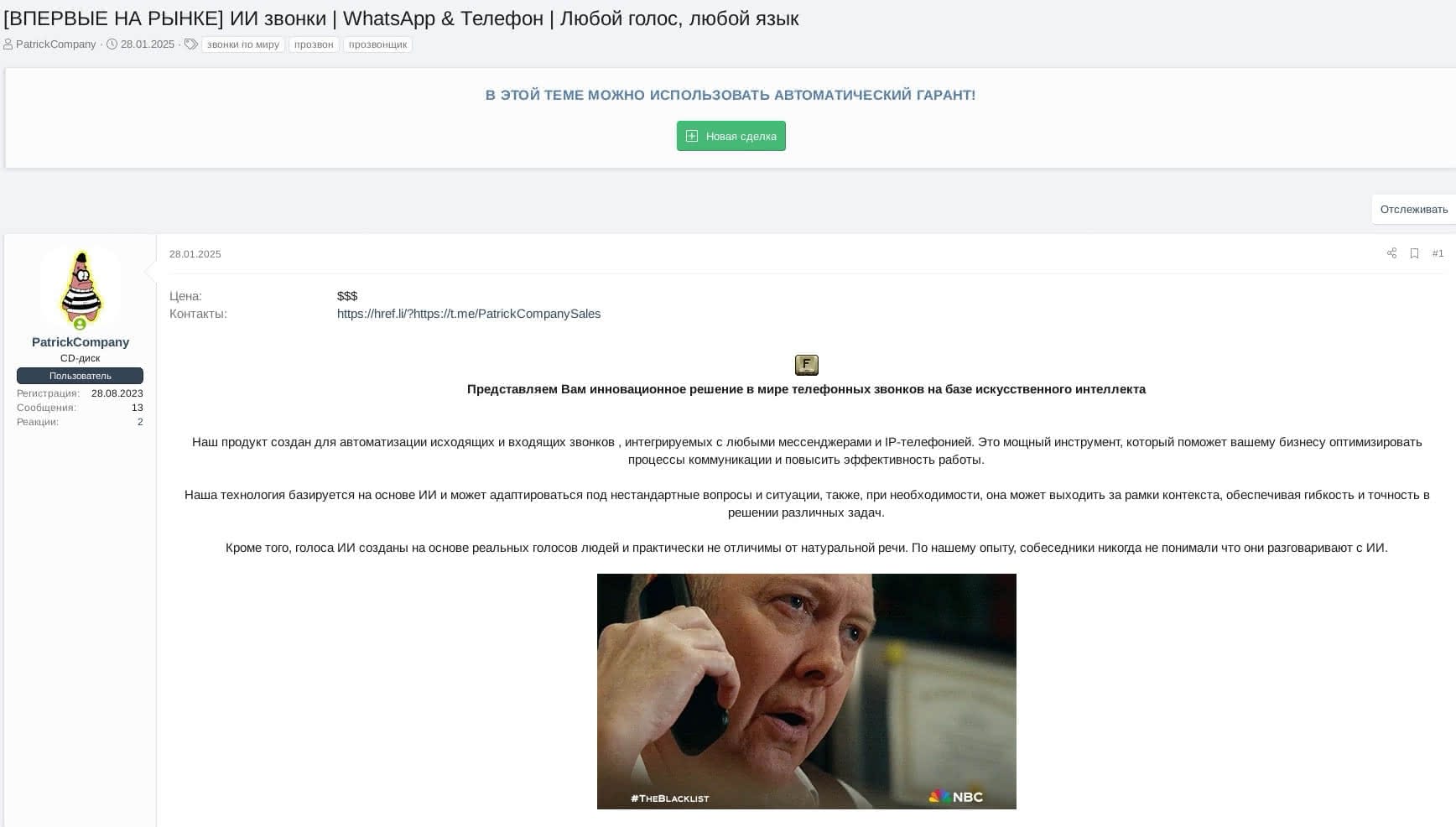
On January 28, 2025, an actor PatrickCompany created a thread on XSS.is forum called “[FIRST TIME ON MARKET] AI calls | WhatsApp & Telephone | Any voice, any language” where they offered an AI-based innovative solution in the world of phone calls.
Post Translation
Price: $$$
Contacts: https://t.me/PatrickCompanySales
We present an innovative solution in the world of phone calls based on artificial intelligence
Our product is designed for automation of outbound and inbound calls, integrating with any messengers and IP telephony. This is a powerful tool that will help your business optimize communication processes and increase work efficiency.
Our technology is based on AI and can adapt to non-standard questions and situations, also, if necessary, it can go beyond context, providing flexibility and accuracy in solving various tasks.
Moreover, AI voices are created based on real human voices and are practically indistinguishable from natural speech. In our experience, interlocutors never understood that they were talking to AI.
Main features of our service:
- Flexible Conversation Structure: Ability to adapt the script to your business processes.
- Real-time Call Monitoring: Quality control of communication and prompt intervention when necessary.
- Call Recording Storage: Complete call history for analysis and efficiency improvement.
- Any Voice and Language: Support for various languages and the ability to choose a unique voice of any gender, age, and tone.
- Multiple Call Lines Setup: Simultaneous processing of large number of requests.
- Notifications about Completed Stages of Current Call: Telegram/Discord notifications about achieving call stages/goals
- Call Transcription: Textual, chronological call history
- Live Operator Transfer: Ability to transfer a live specialist to the line
- Integration with Applications and Websites: Calling various commands, for example, for sending OTP
- Integration with Internet Telephony and Messengers: Ability to integrate your SIP trunks and accounts
- Voice Cloning: Creating an exact speech model from any voice recording
How will this help your business?
Our artificial intelligence will allow you to automate routine call center processes, including:
- Client Data Collection and Storage: Collecting necessary information from clients who called or answered the call.
- Event Information: Notifications about upcoming meetings, promotions, schedule changes, and other important events.
- Social Surveys: Conducting research and collecting feedback from your audience.
- Appointment Scheduling: Organizing appointments for meetings, consultations, or services.
- Product Sales: Automation of primary sales, including product presentation and lead collection.
Who do we see as our clients in grey/black themes:
- Individual Orders - for one-time calls:
- Pranks on acquaintances following any scenario
- Voice confirmations (if you don't speak the language)
- Calls for preliminary arrangements on any topic
- Call Centers - replacement of primary and short stages:
- Problem notification
- OTP sending
- Integration with CRM and databases
- Individual name addressing to each client
- Ability to remember and use any text information
- Handling popular objections
- Scam Teams - additional client processing to increase trust factor:
- Calls on behalf of bank representatives, exchanges, platforms, collectors, police, etc...
The offered service combines advanced conversational AI with remarkably convincing voice synthesis technology, enabling seamless humanlike interactions across multiple languages. What makes this particularly noteworthy is its ability to clone voices from recordings and maintain context-aware conversations that can adapt to unexpected situations. The system's integration capabilities with various communication channels, including traditional telephone and popular messaging platforms like WhatsApp, alongside its ability to handle multiple concurrent calls, suggests a level of sophistication previously unseen in automated calling systems.
The criminal implications of this technology are profound and far-reaching. Imagine a scenario where cybercriminals deploy this system to impersonate bank officials or corporate executives at scale. They could simultaneously target hundreds of victims with convincing, contextually aware conversations, each using a perfectly cloned voice of a trusted authority figure. Financial institutions, in particular, face a significant challenge as their voice-based authentication systems could be compromised by the AI voice cloning capabilities, while their customers become targets of increasingly convincing social engineering attacks.
Black Basta ransomware’s usage of AI
Trellix's recent analysis of Black Basta ransomware chat leaks revealed that ransomware operators internally utilize AI for various malicious purposes. These include creating fraudulent formal letters in English, paraphrasing text, rewriting C#-based malware in Python, debugging code, and collecting victim data. Notably, Black Basta RaaS members frequently employed ChatGPT to facilitate these illicit activities.
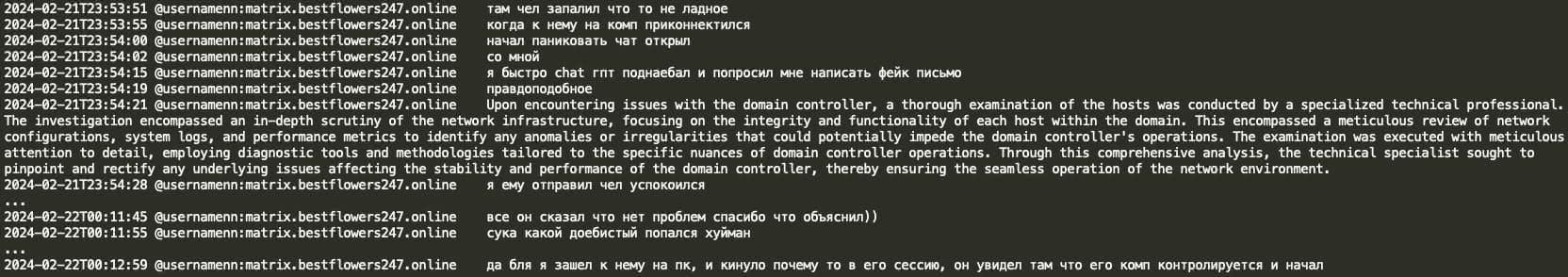
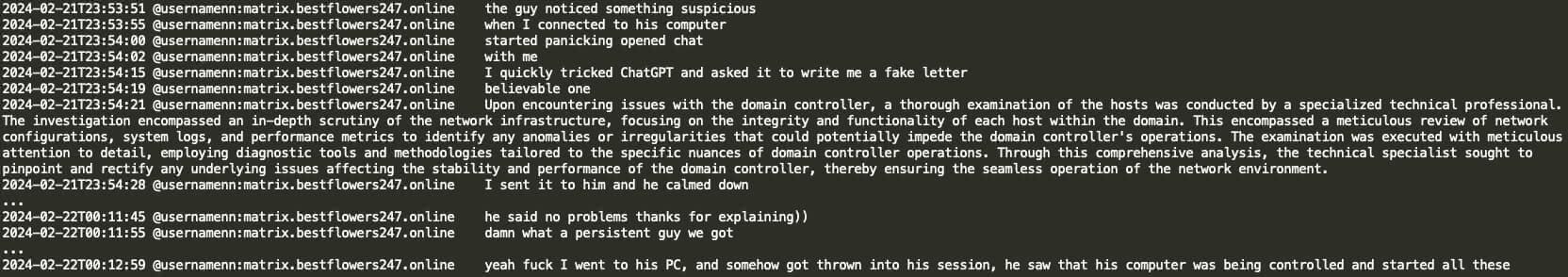
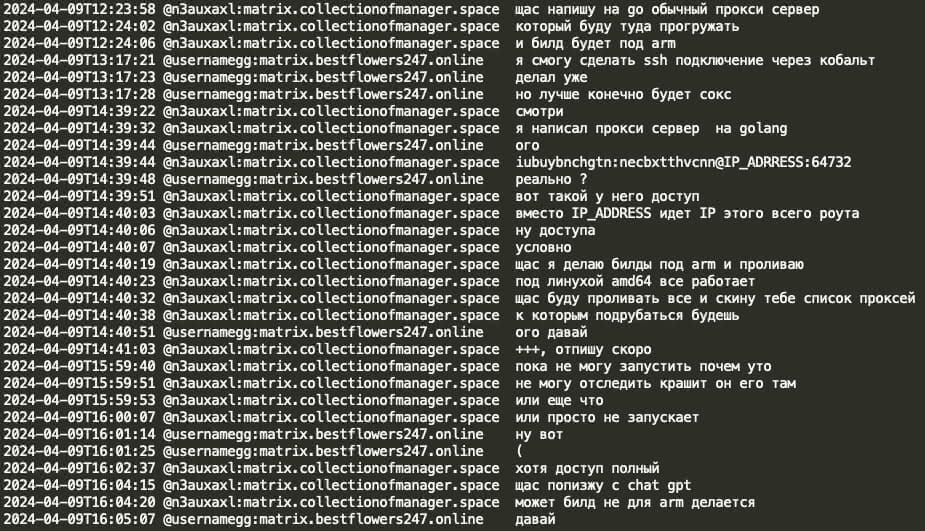
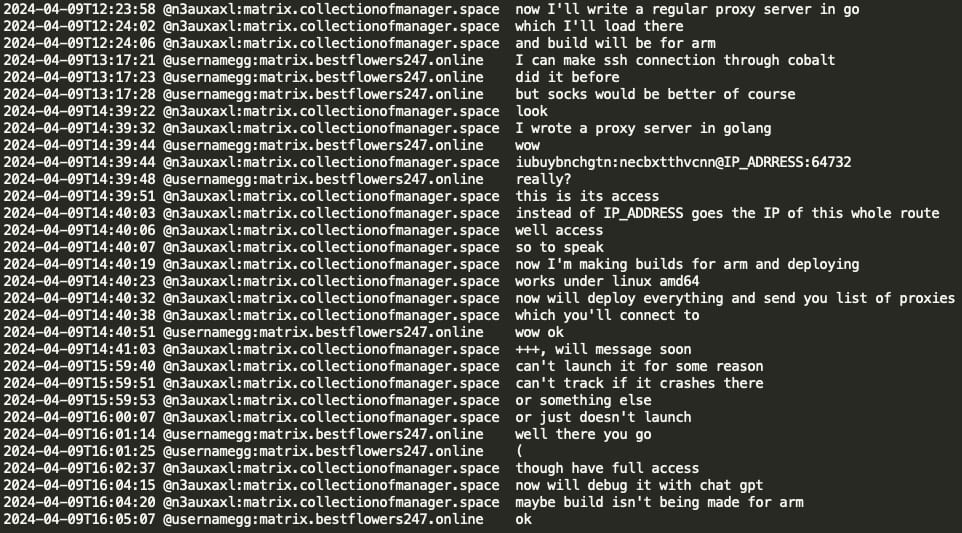
In the case below, Black Basta actor NN unintentionally logged into an active user's PC on the victim organization's network, which notified the user of a remote login within their current session. NN then quickly used ChatGPT to create a deceitful message, falsely claiming that a professional network check was being performed and assuring the user there was no reason for alarm.
The Black Basta coder, mecor, also used ChatGPT to troubleshoot and fix a runtime error in the ARM build of a Go-based proxy server they developed, which included builds for ARM/Linux.
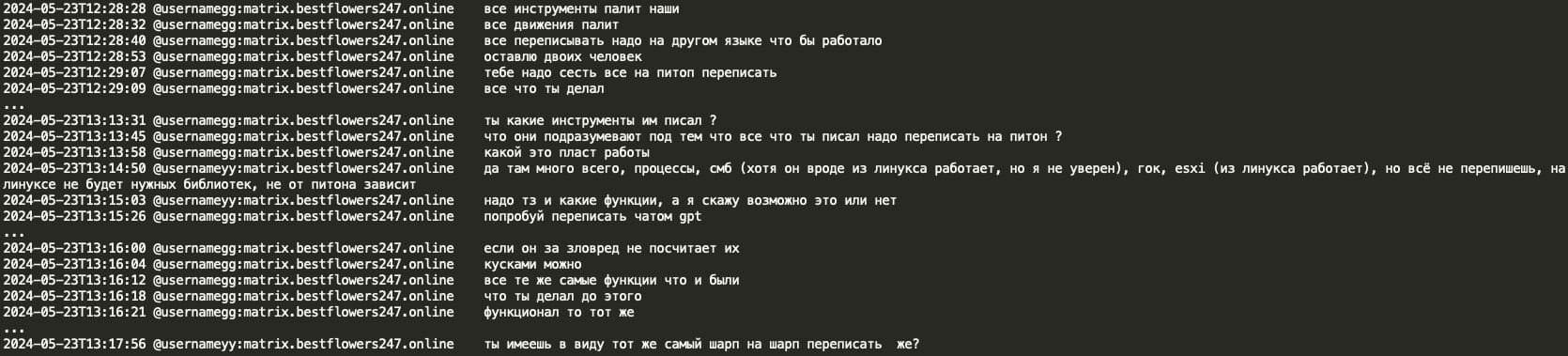
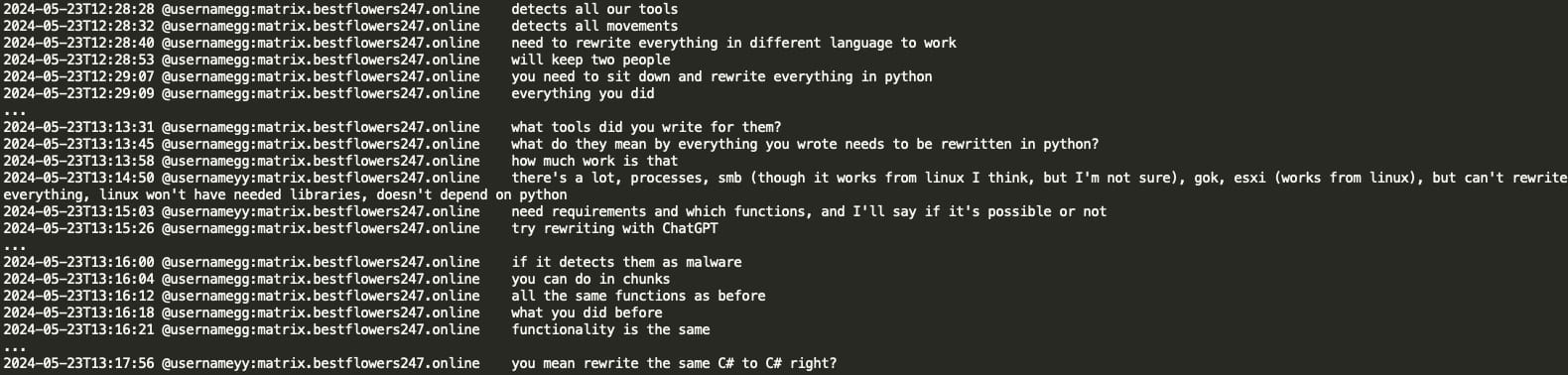
YY (coder of Black Basta) was instructed to rewrite the tools in Python as some of the gang’s malware got detected by AV/EDR. GG (Black Basta ransomware leader) asked YY to use ChatGPT for that, and if ChatGPT would complain about malware, YY can instead provide code in chunks. YY later inquired if GG's suggestion was to rewrite C# in C#, revealing that GG instructed to rewrite the malware from C# to Python using ChatGPT.
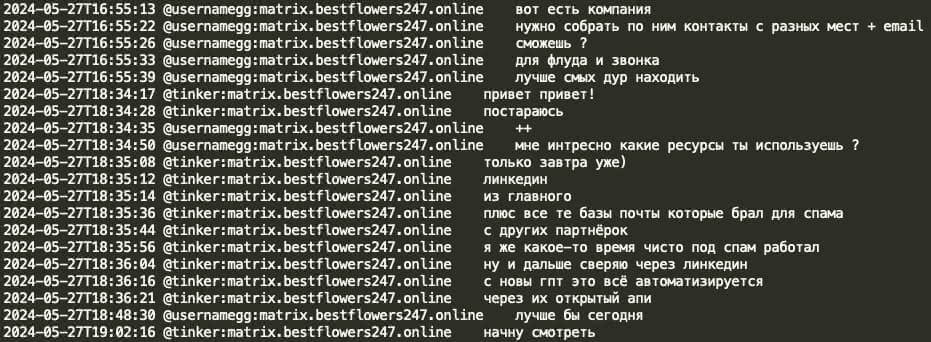
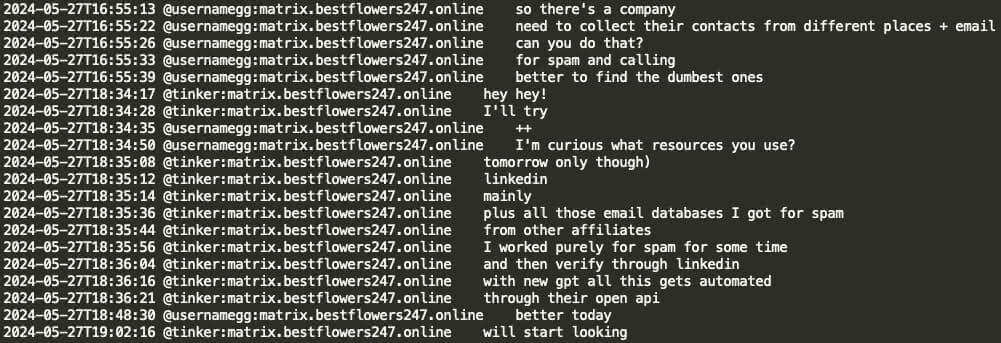
Here GG requested that Tinker (negotiator) gather victim company contacts and emails from various sources for the purpose of spamming and calling. GG inquired about the resources Tinker utilizes, to which Tinker responded he uses an email database for spamming, verifies contacts via LinkedIn, and that with the new ChatGPT, everything is being automated through their API services.
The Black Basta chat leaks present evidence of ransomware groups utilizing AI for operational tasks, malware development, and crafting persuasive text for fraudulent emails. These leaks are a rare opportunity for the Threat Intelligence community to analyze the inner workings of ransomware gangs and witness firsthand how they utilize AI for their illegal activities. This knowledge serves as a reminder that cybercriminals are keeping up with the times and constantly adapting modern technology and AI advancements for their own nefarious purposes.
Complex attack chains and increased exploitation of vulnerabilities
The analysis of the vulnerability landscape between Q4 2024 and Q1 2025 reveals a sustained high level of malicious activity targeting known weaknesses in software and systems. Exploitation attempts continued to rise, indicating an aggressive probing and attack posture from threat actors.
Attacks on key vendors: Microsoft, Ivanti, and Fortinet were particularly affected, with their products, including the ubiquitous Windows operating system, the widely used Ivanti Connect Secure VPN, and the prevalent Fortinet FortiManager security appliance, experiencing a barrage of critical vulnerabilities. Further, an emerging trend indicates increased targeting of security vendors to compromise security infrastructure.
Abuse of zero-days: Notably, we observed several zero-day exploits, underscoring the agility and sophistication of modern cyber adversaries.
Complex exploit chains: Various threat actors actively leveraged vulnerabilities, ranging from financially motivated ransomware groups to APT actors. The complexity of attack chains involving multiple vendors poses a significant detection challenge.

The Windows platform experienced the highest number of CVEs during the analyzed period
38
Operating system components accounted for 38% of new vulnerabilities discovered
Threat actors consistently endeavor to leverage vulnerabilities as a primary method of malicious operations, targeting a wide array of digital assets. These exploitable weaknesses can manifest in multiple forms, including software bugs that arise from errors in code, misconfigurations that stem from improper system setup, or fundamental design flaws inherent in the system's architecture.
These findings emphasize the critical and ongoing need for organizations to prioritize immediate patching of identified vulnerabilities, implement robust and multi-layered security measures, and maintain continuous monitoring of their environments to detect and respond to these evolving threats effectively, thereby strengthening their overall security posture.
Key findings
The Trellix Advanced Research Center has prioritized a subset of the vast number of CVEs published annually for in-depth analysis. While the total number of disclosed vulnerabilities is substantial – projections for 2025 suggest 41,000 to 50,000 new CVEs, while over 11,000 were recorded in Q4 2024 alone.
The most common attack types observed were:
Remote Code Execution
Cross-Site Scripting
Memory Corruption
Elevation of Privilege
Path Traversal
The distribution of the analyzed CVEs across different product categories highlights the foundational nature of operating systems and network devices in IT infrastructure, making them attractive targets for attackers. The significant number of vulnerabilities in enterprise software also underscores the risks associated with business-critical applications. Even the substantial percentage of vulnerabilities in development tools indicates a growing awareness of the potential for supply chain attacks.
Distribution of CVEs across product categories
The top five CVEs Trellix observed in our telemetry are:
CVE-2022-26134 (Atlassian Confluence): This critical vulnerability is an unauthenticated Object-Graph Navigation Language (OGNL) injection flaw that allows for remote code execution (RCE) on affected versions of Atlassian Confluence Server and Data Center products (excluding the Cloud offering). The severity of this vulnerability and relative ease of exploitation make it a desirable target for malicious actors seeking to gain control over vulnerable systems.
CVE-2021-26084 (Atlassian Confluence): Like CVE-2022-26134, this is a critical OGNL injection vulnerability that permits unauthenticated attackers to execute arbitrary code on vulnerable Atlassian Confluence Server or Data Center instances. This type of vulnerability provides attackers with a significant level of control over the affected systems.
CVE-2023-35078 (Ivanti EPMM): This critical vulnerability represents a remote unauthenticated API access flaw in Ivanti Endpoint Manager Mobile (EPMM), previously known as MobileIron Core. Unauthenticated remote actors' access to critical management interfaces poses a significant security risk. Successful exploitation of CVE-2023-35078 can enable unauthorized actors to potentially access users' personally identifiable information (PII) and make limited modifications to the affected server.
CVE-2023-29357 (Microsoft SharePoint): Privilege escalation vulnerabilities are particularly dangerous as they allow attackers who may have gained initial, limited access to a system to elevate their privileges to a higher level, potentially gaining administrative control. CVE-2023-29357 enables unauthenticated attackers to achieve administrator-level privileges to a vulnerable SharePoint Server.
CVE-2023-42793 (JetBrains TeamCity): This vulnerability affects JetBrains TeamCity, a widespread continuous integration and continuous delivery (CI/CD) server used in software development.
Impacted products and platforms
The distribution of vulnerabilities across different environment types revealed Enterprise Infrastructure was the most affected, followed by Development Environment, End-User Systems, and Industrial Systems. This distribution indicates attackers primarily target core enterprise assets, but development environments and end-user systems also represent significant risk areas.
Distribution of vulnerabilities by environment
Several specific products and product categories experienced significant vulnerability during the reporting period.
Microsoft Windows Components, including TCP/IP (CVE-2024-38063), Task Scheduler (CVE-2024-49039), LDAP (CVE-2024-49113), and NTLM (CVE-2024-43451), were heavily affected by vulnerabilities, many of which were actively exploited.
Security infrastructure products from vendors like Fortinet (FortiManager/FortiGate), Ivanti (Connect Secure VPN, EPMM, Cloud Service Application), and Palo Alto Networks (PAN-OS) were also prime targets, experiencing multiple zero-day vulnerabilities and active exploitation by various threat actors.
Network infrastructure products, encompassing Cisco ASA and Cisco IOS, VPN systems, management interfaces, authentication systems, and network management tools, also presented a considerable surface for attack. In network infrastructure, Remote Code Execution dominated 41%, followed by Denial of Service (27%) and Authentication Bypass (19%).
Enterprise applications, such as Microsoft Exchange, Oracle WebLogic, IBM Enterprise products, VMware ESXi, and BeyondTrust security tools, were identified as affected by vulnerabilities. For enterprise applications, SQL injection was the most frequent at 31%, followed by Authentication Bypass (28%) and Information Disclosure (25%).
Web browsers (Mozilla Firefox and TOR Browser) also saw regular exploitation attempts, and Mobile Platforms (Samsung Firmware) showed emerging exploitation patterns.
This underscores the critical importance of having robust threat intelligence capabilities and advanced security solutions that can detect and mitigate novel attacks. The focus on platforms like Windows and essential infrastructure components such as VPN gateways highlights the strategic intent of attackers to gain widespread access and control over targeted environments.
Zero-day analysis
The period from Q4 2024 to Q1 2025 witnessed the concerning trend of multiple zero-day vulnerabilities being actively exploited across a range of software platforms.
Microsoft addressed many of these previously unknown flaws in their monthly security updates. These included:
A security feature bypass in the Microsoft Management Console (CVE-2025-26633)
A remote code execution vulnerability in the Windows Fast FAT File System Driver (CVE-2025-24985)
Multiple information disclosure and remote code execution vulnerabilities in Windows NTFS (CVE-2025-24984, CVE-2025-24991, CVE-2025-24993)
An elevation of privilege vulnerability in the Windows Win32 Kernel Subsystem (CVE-2025-24983)
Zero-day vulnerabilities in Windows Hyper-V and the MSHTML Platform were exploited in October 2024.
Notably, exploitation attempts targeting zero-day vulnerabilities in Ivanti Connect Secure (CVE-2025-0282 and CVE-2025-0283) were detected as early as December 2024, before their public disclosure. Many of these critical zero-day vulnerabilities were identified in Ivanti Connect Secure, including remote code execution and authentication bypass flaws, which are under active exploitation by multiple APT groups.
The rapid weaponization and exploitation of these zero-day vulnerabilities by threat actors, often within days of their discovery or even before patches become available, presents a significant challenge for organizations.
The speed at which zero-day vulnerabilities are being exploited is increasing. Implementing regular security appliance updates is crucial. Hardening management interfaces is essential. Protecting certificate authorities is paramount. Enhancing access control mechanisms is necessary.
Additional attack methods on the rise: Phishing, password sprays, and info-stealers
Over the period of time observed for this report, the Trellix Advanced Research Center observed shifts in threat actor use of phishing, password spray, and info-stealer attacks.
Phishing remains the most prevalent initial access vector, followed by exploit techniques
399
Password spray attempts targeting the Cisco ASA VPN increased 399% in Q1 of 2025 compared to the previous quarter, Microsoft 365 authentication increased 21%
Phishing remains the most prevalent
The primary initial access vectors during the period of this report were phishing and exploit techniques, with a consistent increase in sophisticated attacks. Phishing exploits human vulnerabilities and remains the most prevalent initial access vector. These phishing campaigns often distribute malware or direct users to fraudulent websites to steal sensitive information.
During December and January, Trellix Email Security detection data sources detected an increase in phishing attacks, mainly due to several attempts to distribute malware disguised as PDFs using MSI installers associated with the Leonem malware group.
Malicious email detections by volume
This underscores the importance of continued employee education on phishing attacks through security awareness training and simulated exercises.
Password spray attacks increase
Following Midnight Blizzard’s use of a password spray to access Microsoft's corporate email accounts, our last report detailed this method for the first time. Password sprays are an effective brute-force attack method. They are particularly attractive to cyber threat actors because they can be difficult to attribute as they are most often executed from globally distributed IP addresses leveraging botnets and services, and many organizations don’t have effective brute force detection. This leads to a high return on investment with a relatively low risk of detection, and they can take advantage of weak password policies and partial MFA deployments.
Between 2024 Q4 and 2025 Q1, the Trellix Advanced Research Center observed password spray attempts directed across regions and sectors.
Expanding surface: While password spray attempts targeting Microsoft 365 grew 21% in Q1 2025 compared to Q4 2024, attempts targeting Cisco ASA VPN increased 399%. Interestingly, attacks targeting Okta had a sharp decrease. As attacks against cloud service authentication were rampant in 2024, attackers may be increasingly branching out to more traditional vectors like corporate VPNs. Cloud service providers like Microsoft 365 also offer sophisticated brute force and password spray detection capabilities, while VPN systems may not have such robust monitoring systems.
- Highly targeted: While Microsoft 365 authentication attacks on individual companies reduced the number of targeted organizations by 25%, the total volume of attacks increased quarter over quarter by 21% in Q1 of 2025. This may indicate a more focused approach; threat actors may have obtained a large list of usernames for these particular organizations, or inferred the usernames by learning the username naming pattern and finding a list of employees, to attempt authenticating to each account with a large list of passwords.
Top 5 targeted sectors
1.
Healthcare
2.
Energy
3.
Insurance
4.
Retail
5.
Education
Top 5 targeted countries
1.
United States
2.
Canada
3.
Brazil
4.
Australia
5.
Argentina
Common TTPs observed in InfoStealer malware infections
Like above, our last report also explored InfoStealers for the first time. The relevance of and success of InfoStealers as a method for criminals is rising, with new Arcane malware targeting everything from Discord and Steam, to Ethereum and Skype, to common VPN clients and web browsers. An increasing number of InfoStealers has also been observed despite law enforcement action to take down the Redline and Meta stealers late in 2024.
Initial access and execution
Initial access often relies on social engineering to trick the victim.
ClickFix and fake CAPTCHA campaigns (T1204): The adversary tricks victims into opening a Windows command shell, pasting and executing a malicious command, which usually downloads additional files or retrieves and executes a remote payload. The bait can be a malicious email or website, and the malicious commands often execute legitimate Windows Binaries like PowerShell, CMD, CURL, WGET, and MSHTA.
Fake or trojanized software (T1204): Threat actors trick victims into downloading and running malicious or weaponized software. Infection chains often include archive files and shortcut files. A prevalent technique seen in InfoStealer infections involves executing legitimate binaries, weaponized through DLL sideloading (legitimate binary and malicious DLL distributed via archive files). The bait can be cracked versions of productivity tools, games, books, and movies.
Phishing emails (T1566): The adversary lures victims into downloading and executing weaponized files, which are delivered via attachment or download link. In infostealer infections, it is common to see the usage of archived files that contain scripts (HTA files, JavaScript, VBScript, PowerShell, and CMD batch scripts) or malicious-weaponized binaries.
Defense evasion, execution, and persistence
InfoStealer attacks are designed for defense evasion. Execution is achieved by chaining together different command/scripting technologies; it is common to see chaining of VBScript, JavaScript, PowerShell scripts/commands, and CMD commands and batch scripts. IOCs (files and C2s) are refreshed frequently. In practice, this looks like:
Command and Script interpreters (T1059): One of the most common techniques observed in InfoStealer campaigns is the execution of arbitrary commands and scripts; usually multiple command/scripting technologies are combined.
AutoIT3 (T1059.010): A legitimate scripting/automation technology deserves its own bucket due to its prevalence in InfoStealer campaigns.
DLL sideloading (T1574.002): A common technique used to launch malicious payloads during initial execution and to maintain persistence.
Process Injection: InfoStealer payloads are often injected into legitimate processes, like Windows system processes and processes that belong to the .NET suite.
Windows StartUp folders (TT1547/001) and Scheduled Task (T1053): Common techniques for achieving persistence.
Credential access and collection
Credentials from Password Stores (T1555): InfoStealers commonly attempt to steal sensitive files that belong to web browsers, crypto wallet files, and email applications. This is often achieved via file system (file discovery and access) or registry (querying the registry).
Browser Session Hijacking (T1185): InfoStealers often spawn execution of web browser processes in an attempt to bypass Application-Bound Encryption (implemented recently in chromium-based browsers).
Screen, video and audio capture (T1113, T1125, T1123): InfoStealers commonly have other capabilities like screen, video, and audio capture.
Automated collection of User Documents (T1119): InfoStealers commonly have the capability to collect user documents.
Exfiltration and impact
Exfiltration over C2 channel (T1041): InfoStealers commonly attempt to exfiltrate data via the C2 channel.
Exfiltration over Web Services (T1567): InfoStealers commonly attempt to exfiltrate collected files via legitimate web services (e.g. Telegram).
Impact
The impact of InfoStealing campaigns depends on the motivation of the adversary and the type of information accessed. Security events related to InfoStealer infections need to be tracked and investigated.
To to defend against InfoStealers, organizations should deploy the following:
- Social engineering is often the entry door for InfoStealer infections; user training against phishing and InfoStealers can prevent the Initial Access and Execution
- Block/deny execution of uncommon Windows Binaries and scripting technologies
- Ensure strong MFA is in place to limit the impact stolen credentials can have on an organization
- Deploy EDR to every endpoint
- Make sure EDR alerts are monitored by the security team
- Investigate alerts related to InfoStealer TTPs
- Develop an Incident Response playbook against InfoStealer attacks
Industry reports, vetted by Trellix Advanced Research Center
To this point, our report considers Trellix telemetry layered with the expertise of our team of threat intelligence experts and researchers. However, threat research and intelligence gathering cannot be done in a vacuum.
Based on a meticulous analysis of industry-reported and vetted events, we gathered a comprehensive overview of the current state of global cybersecurity. The cybersecurity landscape in Q4 2024 and Q1 2025 continued to be characterized by sophisticated and adaptable threats. Threat actors demonstrated a persistent reliance on established TTPs while also innovating with new techniques and tools. Ransomware remained a significant threat, with actors employing diverse methods, including double extortion and the use of leaked ransomware builders. Phishing campaigns remained a popular initial access vector, with threat actors using increasingly sophisticated lures and delivery mechanisms.
Significant attention on government: Government institutions far outpaced other sectors as a target of malicious activity. The financial sector, manufacturing, IT, technology, telecom, health, energy and other critical infrastructures continue to be attractive targets for both espionage and financial gain. Industrial sectors were increasingly targeted, as seen in the FatalRAT campaign.
Targeting across geos: Several campaigns demonstrated targeting across multiple countries, emphasizing the widespread nature of cyber threats. While the US remained the top target of activity, attacks highlight the geographical diversity of cyber operations.
Diverse range of actors: Several campaigns were attributed to known APT groups, including Stonefly (aka APT45, Silent Chollima, Andariel), Mustang Panda (aka CeranaKeeper), FIN7, and UNC5812, indicating the continued activity of state-sponsored actors. The Lazarus Group was the most active actor based on the provided data.
Unique and sophisticated TTP combinations: Several campaigns demonstrated the use of novel or sophisticated combinations of TTPs, like a campaign leveraging VS Code for unauthorized access showcased a sophisticated attack chain involving phishing, malicious scripts, legitimate tool abuse, and persistence mechanisms. When it comes to MITRE ATT&CK TTPs, T1071.001 (Web Protocols) was highly prevalent, observed across multiple campaigns, indicating the continued reliance on web-based attack vectors.
Reliance on phishing: Several campaigns were observed in Q1 2025 that demonstrate an ongoing trend of leveraging phishing as an initial access vector, using a variety of lures and delivery methods, from malicious attachments to compromised websites.
Ransomware persists: The continued prevalence of ransomware and its evolution, with variants like BabyLockerKZ and Akira, indicates that ransomware remains a primary concern. Financially motivated groups such as Evil Corp, Key Group, and Black Basta remain active, focusing on ransomware, data theft, and extortion. Ransomware variants such as Prince, Chaos, Akira, and BlackPanther, are used for the same purpose.
Backdoors and InfoStealers: Threat actors employ a variety of malicious tools to achieve their objectives. Stealers such as RedLine Stealer, PureStealer, and SparkCat were deployed to exfiltrate sensitive information, while backdoors like TONESHELL, GobRAT, and perfctl were used for persistent access and command and control.
- Abuse of legitimate tools: Adversaries continue to LOTL, manipulating legitimate tools for malicious purposes. Visual Studio Code, GitHub, and PowerShell are among the legitimate applications most abused by threat actors.
Top 10 reported victim countries
- USA: 9.26%
- Russia: 5.29%
- Ukraine: 5.12%
- India: 4.96%
- South Korea: 4.46%
- Germany: 4.3%
- China: 4.3%
- United kingdom: 4.13%
- Brazil: 3.47%
- Canada: 3.14%
Top 10 reported sectors
Top 10 reported actors
Top 10 reported malware
Top 10 dual-use tools
Top MITRE ATT&CK techniques
Comparison with previous six months
Compared to the previous report covering Q2-Q3 2024, several trends remain consistent, while others show evolution:
The abuse of dual-use tools like PowerShell and CMD remains a persistent challenge
Ransomware continues to be a major threat, with new variants and tactics emerging
Phishing remains a prevalent initial access vector, with threat actors continuously refining their techniques
There is a continued diversity in threat actors, ranging from APT groups to financially motivated cybercriminals
Both reports highlight the targeting of a wide range of sectors, with government and finance remaining key targets
A notable difference is the increased visibility of attacks leveraging Linux-specific malware and techniques, which may indicate a shift or expansion in targeting by threat actors. Additionally, the emergence of AI-based social engineering tactics, as seen in the FIN7 campaign, suggests an ongoing evolution in attack sophistication.
Outlook for CISOs
The cybersecurity landscape in Q4 2024 and Q1 2025 saw persistent threats, evolving tactics, and a diverse range of threat actors. Organizations must remain vigilant and proactive in their cybersecurity efforts, focusing on:
Threat Intelligence: Staying informed about emerging threats, TTPs, and threat actors
Defense in Breadth: Deploying security controls throughout your organization’s IT infrastructure, software, and applications, to ensure layers of visibility and protection
Security Awareness Training: Educating employees about phishing, social engineering, and other attack vectors
Vulnerability Management: Identifying and addressing vulnerabilities in systems and applications
Incident Response Planning: Developing and maintaining a comprehensive incident response plan to minimize the impact of security incidents
By adopting a proactive and adaptive approach to cybersecurity, organizations can better defend themselves against the evolving threats in the digital landscape.
Methodology
Collection: Trellix and the world-class experts from our Advanced Research Center gather the statistics, trends, and insights that comprise this report from a wide range of global sources.
Captive sources: In some cases, telemetry is generated by Trellix security solutions on customer cybersecurity networks and defense frameworks deployed around the world in both public and private sector networks, including those delivering technology, infrastructure, or data services. These systems, which number in the millions, generate data from a billion sensors.
Open sources: In other cases, Trellix leverages a combination of patented, proprietary, and open-source tools to scrape sites, logs, and data repositories on the internet, as well as the dark web, such as “leak sites” where malicious actors publish information about or belonging to their ransomware victims.
Normalization: The aggregated data is fed into our Insights and ATLAS platforms. Leveraging machine learning, automation, and human acuity, the team cycles through an intensive, integrated, and iterative set of processes – normalizing the data, enriching results, removing personal information, and identifying correlations across attack methods, agents, sectors, regions, strategies, and outcome.
Analysis: Next, Trellix analyzes this vast reservoir of information, with reference to (1) its extensive threat intelligence knowledge base, (2) cybersecurity industry reports from highly respected and accredited sources, and (3) the experience and insights of Trellix cybersecurity analysts, investigators, reverse engineering specialists, forensic researchers, and vulnerability experts.
Interpretation: Finally, the Trellix team extracts, reviews, and validates meaningful insights that can help cybersecurity leaders and their SecOps teams (1) understand the most recent trends in the cyber threat environment, and (2) use this perspective to improve their ability to anticipate, prevent, and defend their organization from cyberattacks in the future.
Application: How to Use This Information
It’s imperative that any industry-leading assessment team and process understand, acknowledge and, where possible, mitigate the effects of bias – the natural, embedded, or invisible inclination to either accept, reject, or manipulate facts and their meaning. The same precept holds true for consumers of the content.
Unlike a highly structured, control-base mathematical test or experiment, this report is inherently a sample of convenience – a non-probability type of study often used in medical, healthcare, psychology, and sociology testing that makes use of data that is available and accessible.
In short, our findings here are based on what we can observe and, pointedly, do not include evidence of threats, attacks, or tactics that evaded detection, reporting, and data capture.
In the absence of “complete” information or “perfect” visibility, this is the type of study best suited to this report’s objective: to identify known sources of critical data on cybersecurity threats and develop rational, expert, and ethical interpretations of this data that inform and enable best practices in cyber defense.
How to Understand the Analysis in this Report
Understanding the insights and data in this report requires briefly reviewing the following guidelines:
A snapshot in time: Nobody has access to all the logs of all the systems connected to the internet, not all security incidents are reported, and not all victims are extorted and included in the leak sites. However, tracking what we can leads to a better understanding of the various threats, while reducing analytical and investigative blind spots.
False positives and false negatives: Among the high-performance technical characteristics of Trellix’s special tracking and telemetry systems to collect data are mechanisms, filters, and tactics that help counter or remove false positive and negative results. These help to elevate the level of analysis and the quality of our findings.
Detections, not infections: When we talk about telemetry, we talk about detections, not infections. A detection is recorded when a file, URL, IP address, or other indicator is detected by one of our products and reported back to us.
Uneven data capture: Some data sets require careful interpretation. Telecommunications data, for example, includes telemetry from ISP clients operating in many other industries and sectors.
Nation-state attribution: Similarly, determining nation-state responsibility for various cyberattacks and threats can be very difficult given the common practice among nation-state hackers and cybercriminals to spoof one another, or disguise malicious activity as coming from a trusted source.
Acknowledgements
The Advanced Research Center and team members across all of Trellix contribute to this report. We would like to thank those below for their efforts to pour over telemetry, provide detailed analysis and context, write, edit, design, and layout this report.
- Adithya Chandra
- Ale Houspanossian
- Alfred Alvarado
- Anil Ramabhatta
- Anne An
- Anthony Berglund
- Bing Sun
- Chrissy Polchito
- Daksh Kapur
- Duy-Phuc Pham
- Ernesto Fernández Provecho
- Haowei Ren
- Henry Bernabe
- Ian Shefferman
- Ilya Kolmanovich
- Jambul Tologonov
- Jeff Payne
- Jeffrey Sman
- Joao Marques
- John Fokker
- Jonathan Omakun
- Lennard Galang
- Max Kersten
- Megan Haley
- Melanie Maben
- Pavan Pothamsetti
- PJ Mullen
- Pranay Balaji
- Rohan Shah
- Ryan Stelzer
- Sarah Erman
- Srini Seethapathy
- Tim Hux
- Wesley Porter
About The Trellix Advanced Research Center
The Trellix Advanced Research Center is at the forefront of research into the emerging methods, trends, and tools used by cyber threat actors across the global cyber threat landscape. Our elite team of researchers serve as the premier partner of CISOs, senior security leaders, and their security operations teams worldwide. The Trellix Advanced Research Center provides operational and strategic threat intelligence through cutting-edge content to security analysts, powers our industry leading AI-powered cybersecurity platform, and offers intelligence products, and services to customers globally.
About Trellix
Trellix is a global company redefining the future of cybersecurity and soulful work. The company’s comprehensive, open and native cybersecurity platform helps organizations confronted by today’s most advanced threats gain confidence in the protection and resilience of their operations. Trellix, along with an extensive partner ecosystem, accelerates technology innovation through artificial intelligence, automation, and analytics to empower over 50,000 business and government customers with responsibly architected security.
This document and the information continued herein describes computer security research for educational purposes only and the convenience of Trellix customers. Trellix conducts research in accordance with its Vulnerability Reasonable Disclosure Policy I Trellix. Any attempt to recreate part or all of the activities described is solely at the user’s risk, and neither Trellix nor its affiliates will bear any responsibility or liability.
Trellix is a trademark or registered trademark of Musarubra US LLC or its affiliates in the US and other countries. Other names and brands may be claimed as the property of others.