Trellix Advanced Threat Landscape Analysis System
Giving customers a unique insight into malicious file, domain, and IP detections seen worldwide.
Advanced Threat Landscape Analysis System (ATLAS) data is aggregated from various Trellix data sources to provide the latest global emerging threats with enriched data such as industry sector and geolocation. ATLAS correlates these threats with campaign data containing research from Trellix’s Advanced research Center (ARC) and Threat Intelligence Group (TIG), as well as open-source data, to provide a dedicated view for campaigns consisting of events, dates, threat actors, IOCs, and more.
Features
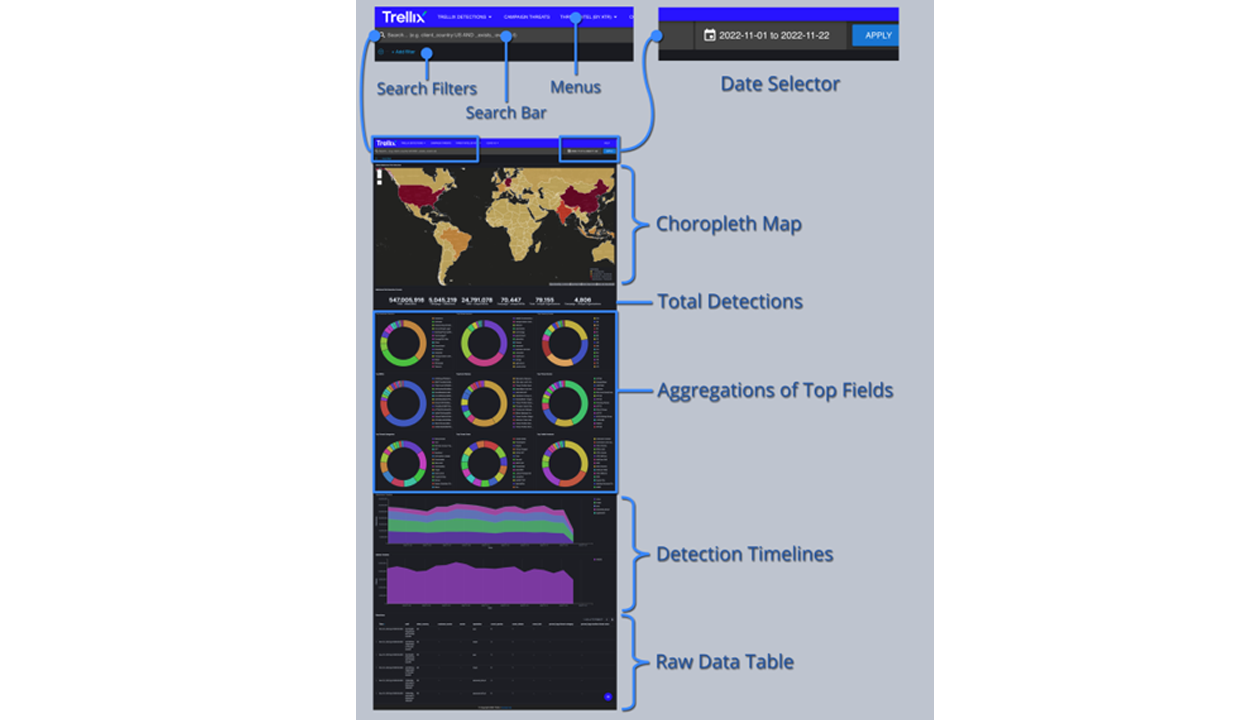
ATLAS includes several standard dashboards for indicators of compromise (IOCs), threat actors and campaigns. Dashboards vary slightly from one another but share similar design elements, visualizations, and workflows.
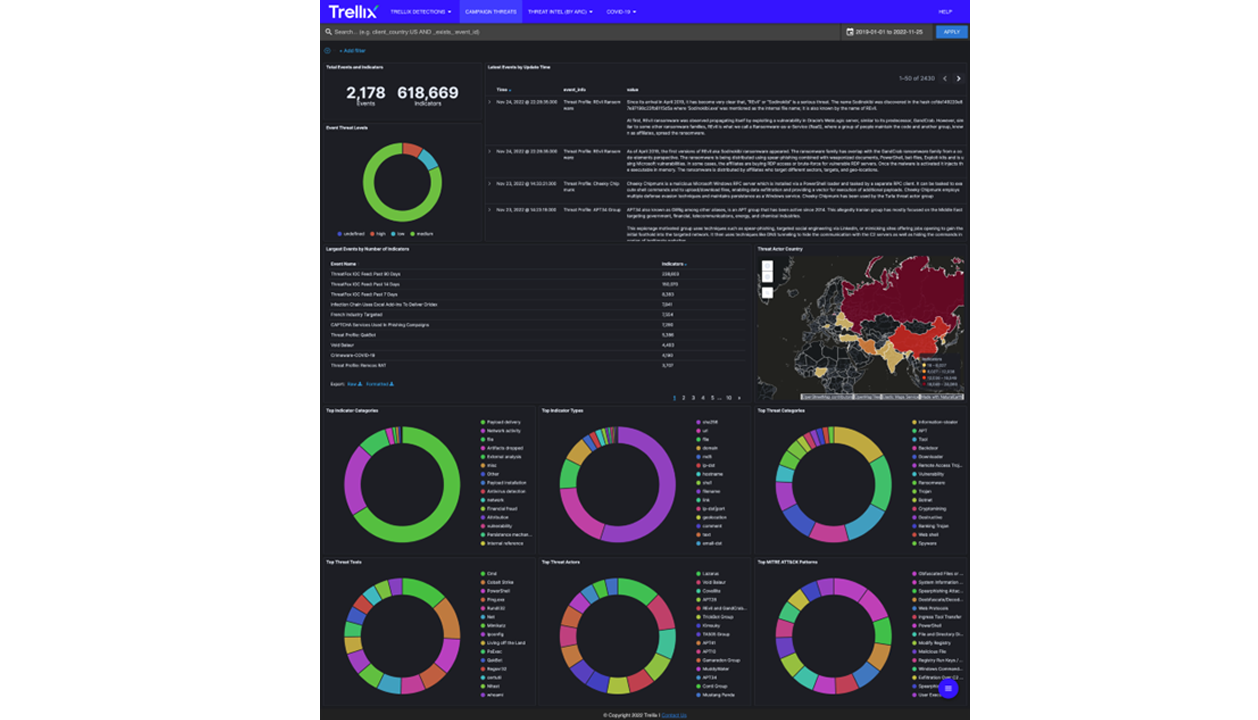
Campaigns Dashboard
- Click on Campaign Threats in the menu to view the latest intelligence from our team of industry-leading researchers. The campaign dashboard collates the latest analysis of thousands of emerging threats into one location. Here you will find cutting-edge research from Trellix specialists, as well as open-source intelligence from around the world.
Campaign data is imported from Trellix’s backend intelligence platform MISP. As part of this process, ATLAS automatically enriches our prevalence data with campaign IOCs.
Vulnerability Intelligence
- The vulnerability dashboard collates the analysis of the latest high impact vulnerabilities. The analysis and triage are performed by the Advanced Research Center’s industry experts on vulnerabilities. These researchers, who specialize in reverse engineering and vulnerability analysis, continuously monitor the latest vulnerabilities and how threat actors are utilizing these in their attacks to provide remediation guidance. This concise and highly technical expert advice allows you to filter the signal from the noise and to focus on the most impactful vulnerabilities that can affect your organization allowing you to react faster.
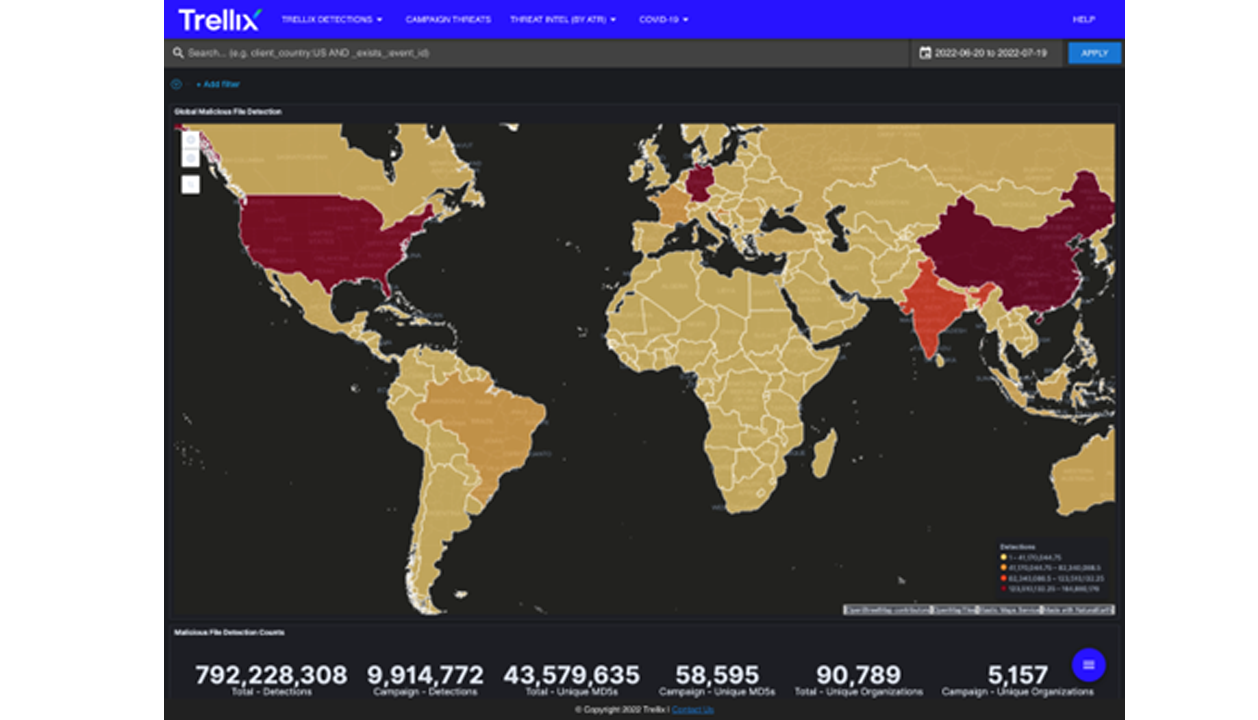
ATLAS Detections Dashboards include several visualization types for prevalence of malicious IP addresses, files, and URLs that empower customers with comprehensive situational awareness of the global threat landscape.
Prevalence Dashboards
- Within the menu dropdown labelled Trellix Detections are links to the prevalence dashboards. Each of these dashboards is dedicated to one class of IOC and are populated daily with detections from the full range of Trellix products.
Within each prevalence dashboard you will find:- Which attacks are most relevant to your organization.
- When and where they are occurring.
- What industry sectors are affected.
- Whether they belong to any organized campaigns.
File Prevalence
Includes malicious file hash detections in MD5 and SHA256 formats. Each hash is classified by reputation and trust score.
URL Prevalence
Includes detections of client interactions with malicious domains, hosts, and URLs. Detections are further categorized by risk, site function, and any malicious files that they deploy.
IP Prevalence
A catalog of attempted connections to known malicious IP addresses.