Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
The Symbiont Attacks: An Insider Threat
By Robert Foster, Liberty Williams · December 4, 2023
Walter Smith is a highly experienced Data Engineer who has been working with NKSA for more than three decades. Over the years, he has witnessed and actively participated in the evolution of data usage within the agency. His extensive knowledge and expertise in the field have enabled him to locate and manage all the critical data assets of NKSA successfully. Walter is a valuable member of the team, and his contributions have been critical in ensuring the agency's data infrastructure is efficient and secure.
Once the Symbiont had taken control, it had access Secret Lair information on Earth’s most valiant heroes.
The Symbiont attempted to exfiltrate the data by posting it to “Large Cloud Providers” storage, attaching itself to the USB port, and even running custom code to encrypt and hold the data ransom to the NKSA. However, all attempts were blocked.
As the Symbiont fought to retain control of Walter, Axel skillfully strategized to gain the upper hand. With a combination of quick reflexes and calculated movements, Axel was able to separate Walter from the Symbiont. The Symbiont, now without its host, was left powerless against Axel's strength. The battle was intense, but Axel ultimately emerged victorious, having successfully eliminated the Symbiont and remediating the threat .
How was Binary’s team able to detect the insider threat so quickly and precisely?
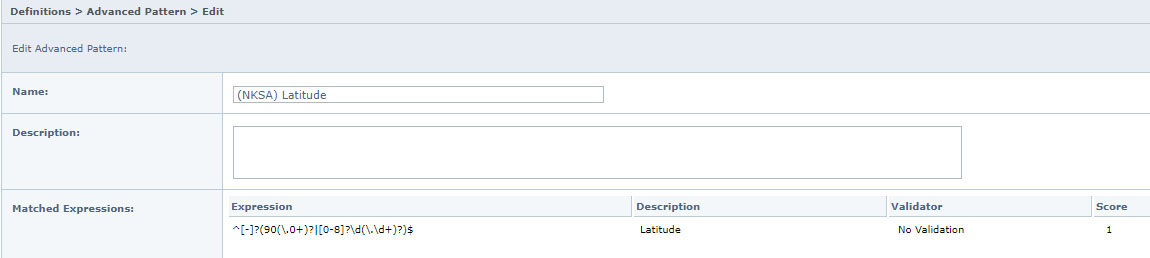
During the Trellix Professional Services engagement, Depth Charge explained how Critical Data Elements are quality - checked within SIMS.
Trellix Professional Services then matched patterns used by the Data Engineers to patterns in the DLP Policy, allowing them to quickly detect any malicious behavior.
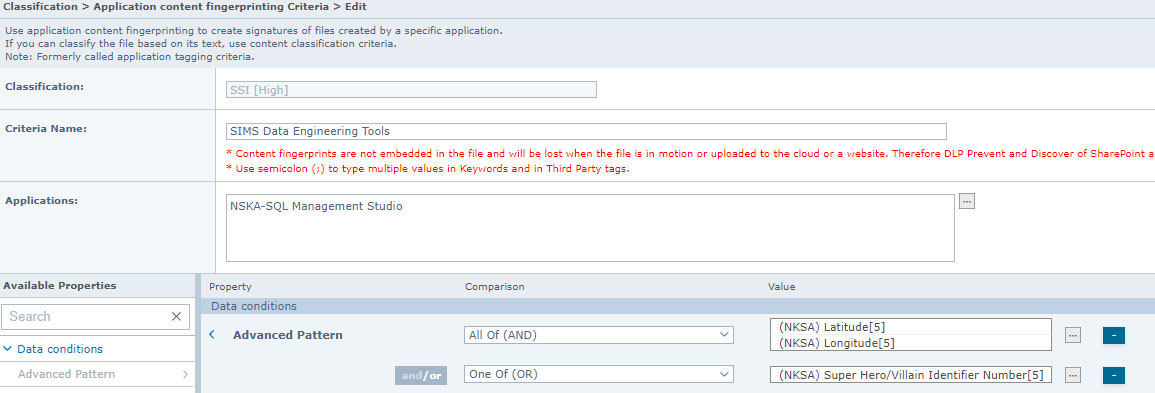
Depth Charge also explained how his staff managed data and provided a list of tools they used to complete their mission.
Trellix DLP can classify those tools and use text extractors to read the contents of the data. When combined with Critical Data Element patterns, NKSA fingerprinted the data and raised the Classification to High probability.
To protect your organizations data, It’s critical to understand how business units are using the data and build your DLP policy from there.
Even superhero CISOs find it challenging to get buy-in from other departments, but it’s vital to acknowledge that insider threats can happen to anyone, including Walter.
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.