Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
ARCHIVED STORY
BlackMatter Ransomware Analysis; The Dark Side Returns
By Alexandre Mundo and Marc Elias · September 22, 2021
BlackMatter is a new ransomware threat discovered at the end of July 2021.
This malware started with a strong group of attacks and some advertising from its developers that claims they take the best parts of other malware, such as GandCrab, LockBit and DarkSide, despite also saying they are a new group of developers. We at McAfee Enterprise Advanced Threat Research (ATR), have serious doubts about this last statement as analysis shows the malware has a great deal in common with DarkSide, the malware associated with the Colonial Pipeline attack which caught the attention of the US government and law enforcement agencies around the world.
The main goal of BlackMatter is to encrypt files in the infected computer and demand a ransom for decrypting them. As with previous ransomware, the operators steal files and private information from compromised servers and request an additional ransom to not publish on the internet.
COVERAGE AND PROTECTION ADVICE
McAfee’s EPP solution covers BlackMatter ransomware with an array of prevention and detection techniques.
ENS ATP provides behavioral content focusing on proactively detecting the threat while also delivering known IoCs for both online and offline detections. For DAT based detections, the family will be reported as Ransom-BlackMatter!<hash>. ENS ATP adds 2 additional layers of protection thanks to JTI rules that provide attack surface reduction for generic ransomware behaviors and RealProtect (static and dynamic) with ML models targeting ransomware threats.
Updates on indicators are pushed through GTI, and customers of Insights will find a threat-profile on this ransomware family that is updated when new and relevant information becomes available.
TECHNICAL DETAILS
BlackMatter is typically seen as an EXE program and, in special cases, as a DLL (Dynamic Library) for Windows. Linux machines can be affected with special versions of it too but in this report, we will only be covering the Windows version.
This report will focus on version 1.2 of BlackMatter while also noting the important changes in the current version, 2.0.
BlackMatter is programmed in C++ and has a size of 67Kb.
The compile date of this sample is the 23rd of July 2021. While these dates can be altered, we think it is correct; version 1.9 has a compile time of 12 August 2021 and the latest version, 2.0, has a date four days later, on the 16th of August 2021. Is clear that the malware developers are actively improving the code and making detection and analysis harder.
The first action performed by BlackMatter is preparation of some modules that will be needed later to get the required functions of Windows.
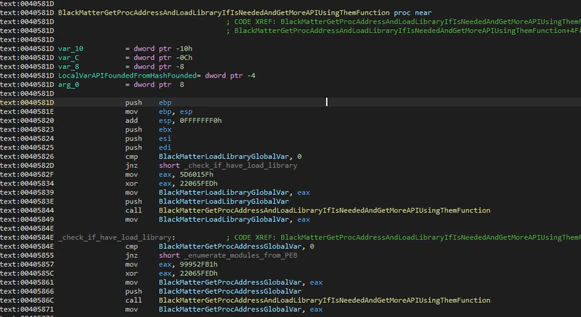
BlackMatter uses some tricks to try and make analysis harder and avoid debuggers. Instead of searching for module names it will check for hashes precalculated with a ROT13 algorithm. The modules needed are “kernel32.dll” and “ntdll.dll”. Both modules will try to get functions to reserve memory in the process heap. The APIs are searched using a combination of the PEB (Process Environment Block) of the module and the EAT (Export Table Address) and enumerating all function names. With these names it will calculate the custom hash and check against the target hashes.
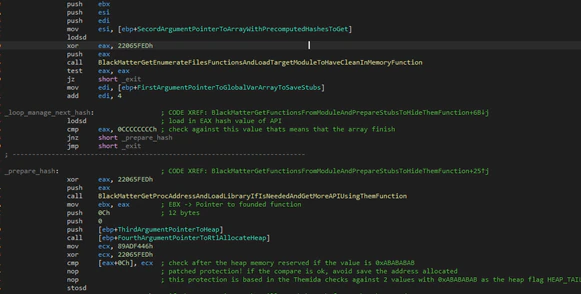
At this point BlackMatter will make a special code to detect debuggers, checking the last 2 “DWORDS” after the memory is reserved, searching for the bytes “0xABABABAB”. These bytes always exist when a process reserves memory in the heap and, if the heap has one special flag (that by default is set when a process is in a debugger), the malware will avoid saving the pointer to the memory reserved so, in this case, the variables will keep a null pointer.
In Windows operating systems the memory has different conditions based on whether a program is running in normal mode (as usual) or in debugging mode (a mode used by programmers, for example). In this case, when the memory is reserved to keep information, if it is in debugging mode, Windows will mark the end of this memory with a special value, “0xABABABAB”. BlackMatter checks for this value and, if found, the debugger is detected. To avoid having it run normally it will destroy the function address that it gets before, meaning it will crash, thus avoiding the execution.
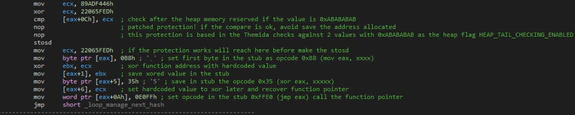
After this check it will create a special stub in the reserved memory which is very simple but effective in making analysis harder as the stub will need to be executed to see which function is called and executed.
This procedure will be done with all functions that will be needed; the hashes are saved hardcoded in the middle of the “.text” section in little structs as data. The end of each struct will be recognized by a check against the “0xCCCCCCCC” value.
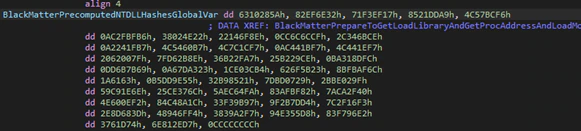
This behavior highlights that the BlackMatter developers know some tricks to make analysis harder, though it is simple to defeat both by patching the binary.
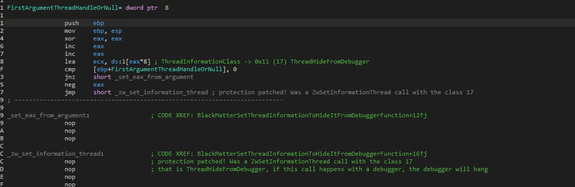
After this, the ransomware will use another trick to avoid the use of debuggers. BlackMatter will call the function “ZwSetInformationThread” with the class argument of 0x11 which will hide the calling thread from the debuggers.
If the malware executes it correctly and a debugger is attached, the debugging session will finish immediately. This code is executed later in the threads that will be used to encrypt files.
The next action is to check if the user that launched the process belongs to the local group of Administrators in the machine using the function “SHTestTokenMembership”. In the case that the user belongs to the administrator group the code will continue normally but in other cases it will get the operating system version using the PEB (to avoid using API functions that can alter the version) and, if it is available, will open the process and check the token to see if that belongs to the Administrators group.
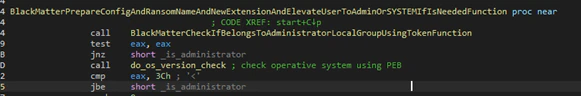
In the case that the user does not belong to the Administrator group the process token will use a clever trick to escalate privileges.
The first action is to prepare the string “dllhost.exe” and enumerate all modules loaded. For each module it will check one field in the initial structure that all executables have that keeps the base memory address where it will be loaded (for example, kernel32.dll in 0x7fff0000) and will compare with its own base address. If it is equal, it will change its name in the PEB fields and the path and arguments path to “dllhost.exe” (in the case of the path and argument path to the SYSTEM32 folder, where the legitimate “dllhost.exe” exists). This trick is used to try and mislead the user. For each module found it will check the base address of the module with its own base address and, at that moment, will change the name of the module loaded, the path, and arguments to mislead the user.
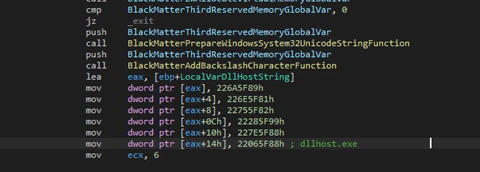
The process name will be “dllhost.exe” and the path will be the system directory of the victim machine. This trick, besides not changing the name of the process in the TaskManager, can make a debugger “think” that another binary is loaded and remove all breakpoints (depending on the debugger used).
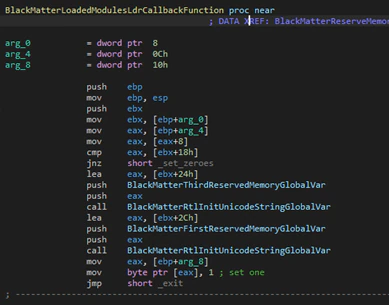
The second action is to use one exploit using COM (Component Object Model) objects to try to elevate privileges before finishing its own instance using the “Terminate Process” function.
For detection, the module uses an undocumented function from NTDLL.DLL, “LoadedModulesLdrCallback” that lets the programmer set a function as a callback where it can get the arguments and check the PEB. In this callback the malware will set the new Unicode strings using “RtlInitUnicodeString”; the strings are the path to “dllhost.exe” in the system folder and “dllhost.exe” as the image name.
The exploit used to bypass the UAC (User Access Control), which is public, uses the COM interface of CMSTPLUA and the COM Elevation Moniker.
In the case that it has administrator rights or uses the exploit with success, it will continue making the new extension that will be used with the encrypted files. For this task it will read the registry key of “Machine Guid” in the cryptographic key (HKEY LOCAL MACHINE).
This entry and value exist in all versions of Windows and is unique for the machine; with this value it will make a custom hash and get the final string of nine characters.
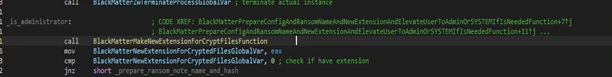
Next, the malware will create the ransom note name and calculate the integrity hash of it. The ransom note text is stored encrypted in the malware data. Usually the ransom note name is “%s.README.txt”, where the wildcard is filled with the new extension generated previously.
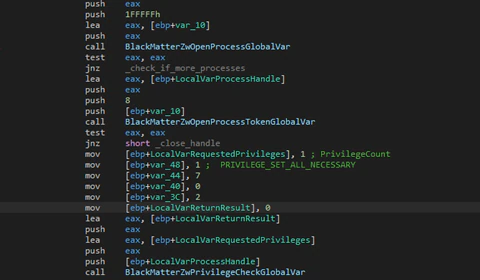
The next step is to get privileges that will be needed later; BlackMatter tries to get many privileges:
| · SE_BACKUP_PRIVILEGE · SE_DEBUG_PRIVILEGE, SE_IMPERSONATE_PRIVILEGE · SE_INC_BASE_PRIORITY_PRIVILEGE · SE_INCREASE_QUOTA_PRIVILEGE · SE_INC_WORKING_SET_PRIVILEGE · SE_MANAGE_VOLUME_PRIVILEGE · SE_PROF_SINGLE_PROCESS_PRIVILEGE · SE_RESTORE_PRIVILEGE · SE_SECURITY_PRIVILEGE · SE_SYSTEM_PROFILE_PRIVILEGE · SE_TAKE_OWNERSHIP_PRIVILEGE · SE_SHUTDOWN_PRIVILEGE |
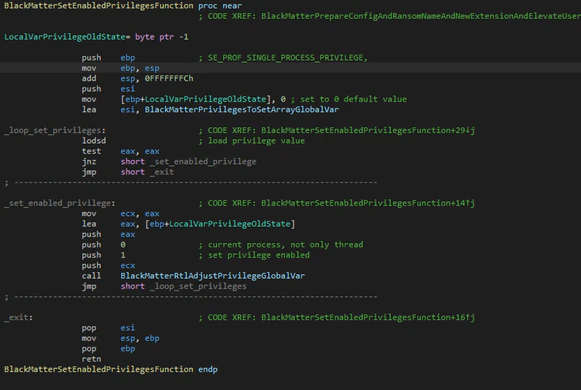
After getting the privileges it will check if it has SYSTEM privileges, checking the token of its own process. If it is SYSTEM, it will get the appropriate user for logon with the function “WTSQueryUserToken”. This function only can be used if the caller has “SeTcbPrivilege” that, by default, only SYSTEM has.
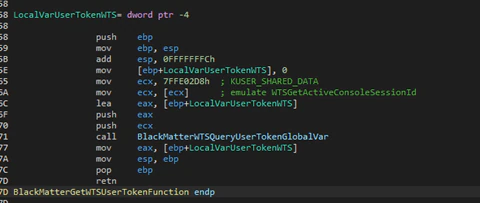
After getting the token of the logged on user the malware will open the Windows station and desktop.
In the case that it does not have SYSTEM permissions it will enumerate all processes in the system and try to duplicate the token from “explorer.exe” (the name is checked using a hardcoded hash), if it has rights it will continue normally, otherwise it will check again if the token that was duplicated has administrator rights.
In this case it will continue normally but in other cases it will check the operating system version and the CPU (Central Processing Unit) mode (32- or 64- bits). This check is done using the function “ZwQueryInformationProcess” with the class 0x1A (ProcessWow64Information).
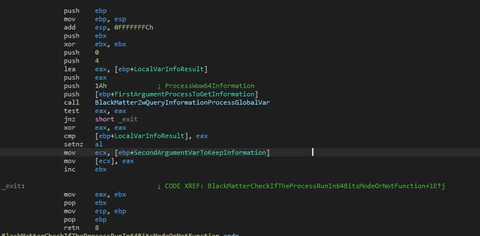
In the case that the system is 32-bits it will decrypt one little shellcode that will inject in one process that will enumerate using the typical “CreateRemoteThread” function. This shellcode will be used to get the token of the process and elevate privileges.
In the case that the system is 64-bits it will decrypt two different shellcodes and will execute the first one that gets the second shellcode as an argument.
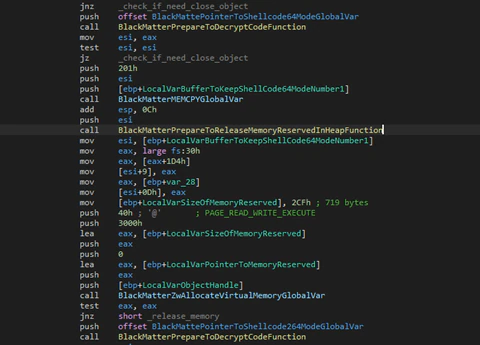
These shellcodes will allow BlackMatter to elevate privileges in a clean way.
Is important to understand that to get the SYSTEM token BlackMatter will enumerate the processes and get “svchost.exe”, but not only will it check the name of the process, it will also check that the process has the privilege “SeTcbPrivilege”. As only SYSTEM has it by default (and it is one permission that cannot be removed from this “user”) it will be that this process is running under SYSTEM and so it becomes the perfect target to attack with the shellcodes and steal the token that will be duplicated and set for BlackMatter.
After this it will decrypt the configuration that it has embedded in one section. BlackMatter has this configuration encrypted and encoded in base64.
This configuration has a remarkably similar structure to Darkside, offering another clear hint that the developers are one and the same, despite their claims to the contrary.
After decryption, the configuration can get this information:
|
After getting the configuration and parsing it, BlackMatter will start checking if it needs to make a login with some user that is in the configuration. In this case it will use the function “LogonUser” with the information of the user(s) that are kept in the configuration; this information has one user and one password: “test@enterprise.com:12345” where “test” is the user, “@enterprise.com” is the domain and “12345” the password.
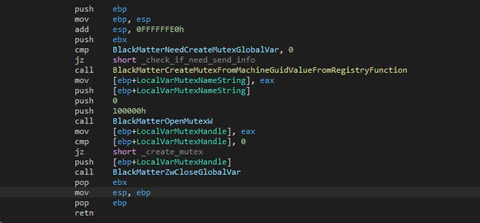
The next action will be to check with the flag to see if a mutex needs to be created to avoid having multiple instances.
This mutex is unique per machine and is based in the registry entry “MachineGuid” in the key “Cryptography”. If the system has this mutex already the malware will finish itself.
Making a vaccine with a mutex can sometimes be useful but not in this case as the developers change the algorithm and only need to set the flag to false to avoid creating it.
After, it will check if it needs to send information to the C2. If it does (usually, but not always) it will get information of the victim machine, such as username, computer name, size of the hard disks, and other information that is useful to the malware developers to know how many machines are infected.
This information is encoded with base64 and encrypted with AES using the key in the configuration.
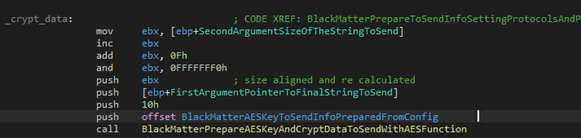
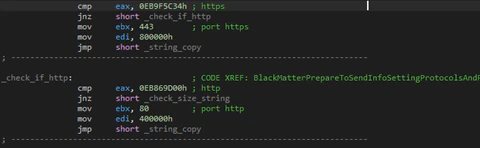
The C2 addresses are in the configuration (but not all samples have them, in this case the flag to send is false). The malware will try to connect to the C2 using a normal protocol or will use SSL checking the initial “http” of the string.
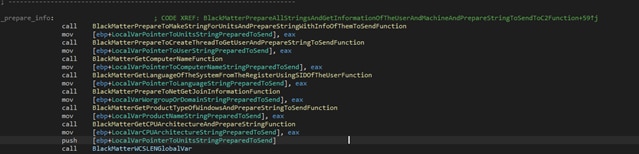
The information is prepared in some strings decrypted from the malware and sent in a POST message.
The message has values to mislead checks and to try and hide the true information as garbage. This “fake” data is calculated randomly.
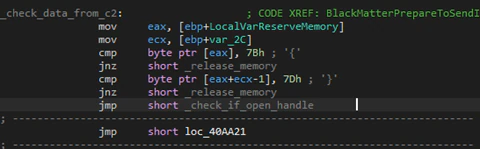
The C2 returns garbage data but the malware will check if it starts and ends with the characters “{“ and “}”; if it does the malware will ignore sending the information to another C2.
BlackMatter is a multithread application and the procedure to send data to the C2 is done by a secondary thread.
After that, BlackMatter will enumerate all units that are FIXED and REMOVABLE to destroy the recycle bin contents. The malware makes it for each unit that has it and are the correct type. One difference with DarkSide is that it has a flag for this behavior while BlackMatter does not.
The next action is to delete the shadow volumes using COM to try and avoid detection using the normal programs to manage the shadow volumes. This differs with DarkSide that has a flag for this purpose.
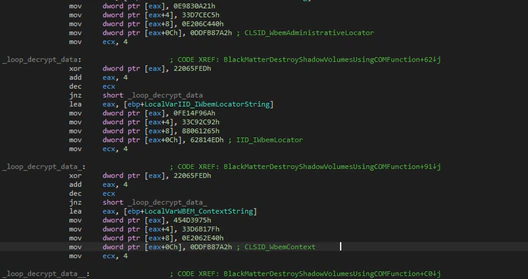
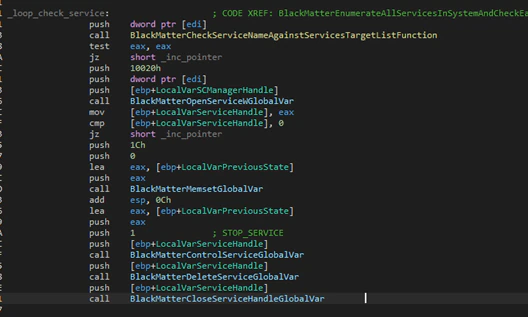
BlackMatter will check another flag and will enumerate all services based on one list in the configuration and will stop target services and delete them.
This behavior is the same as DarkSide.
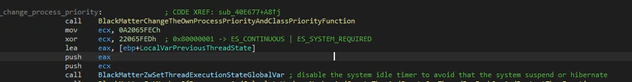
Processes will be checked and terminated as with DarkSide, based on other configuration flags.
After terminating the processes BlackMatter will stop the threads from entering suspension or hibernating if someone is using the computer to prevent either of those outcomes occurring when it is encrypting files. This is done using the function “ZwSetThreadExecutionState”.
The next action will be to enumerate all units, fixed and on the network, and create threads to encrypt the files. BlackMatter uses Salsa20 to encrypt some part of the file and will save a new block in the end of the file, protected with the RSA key embedded in the configuration with the Salsa20 keys used to encrypt it. This makes BlackMatter slower than many other ransomwares.
After the encryption it will send to the C2 all information about the encryption process, how many files were crypted, how many files failed, and so on. This information is sent in the manner previously described, but only if the config is set to true.
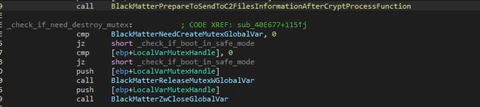
If one mutex was created in this moment it will be released. Later it will check the way that the machine boots with the function “GetSystemMetrics”. If the boot was done in Safe Mode BlackMatter will set some keys for persistence in the registry for the next reboot and then attack the system, changing the desktop wallpaper.
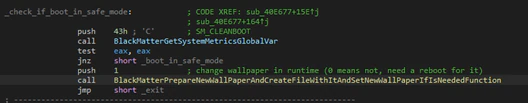
Of course, it will disable the safeboot options in the machine and reboot it (it is one of the reasons why it needs the privilege of shutdown).
To ensure it can launch in safe mode, the persistence key value with the path of the malware will start with a ‘*’.
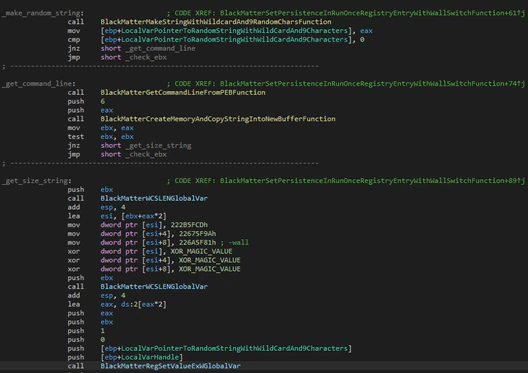
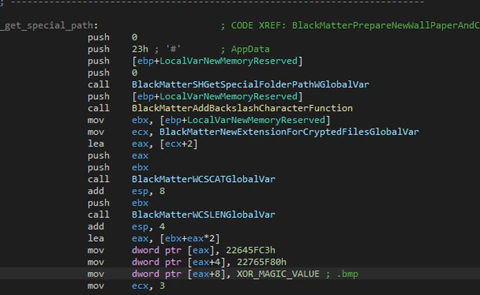
If the machine starts in the normal way, it will change the desktop wallpaper with an alternative generated in runtime with some text about the ransom note.
VERSIONS 1.9 AND 2.0
The new versions have some differences compared with versions 1.2 to 1.6:
- Changes in the stub generation code. Previously only one type of stub was used, but in more recent versions several types of stubs are employed, with one chosen randomly per function. Anyways the stubs can be removed without any problem by patching the binary.
- A new byte flag in the configuration that remarks if it needs to print the ransom note using the available printer in the system. Very similar to Ryuk but instead BlackMatter uses APIs from “winspool.drv”.
- Removed one C2 domain that was shut down by the provider.
Additional changes in version 2.0:
- This version changes the crypto algorithm to protect the configuration making it more complex to decrypt it.
- Removed the last C2 that was shut down by the provider.
- Added a new C2 domain.
These changes suggest the developers are active on social media, with an interest in malware and security researchers.
VACCINE
Unlike some ransomware we’ve seen in the past, such as GandCrab , BlackMatter has good code, but it does have some design flaws that can be used in some cases to avoid having the malware encrypt the files.
This vaccine is not intended to be used in the normal way, rather only in special cases as, while it works, other programs can be affected (we obviously cannot test all third party programs but potential issues are likely to include data corruption and unpredictable behavior), and the fix is not permanent.
Steps to make the vaccine (proceed at your own risk):
- Open regedit (or another registry editor) and go to the key in HKEY_LOCAL_MACHINE> Cryptography.
- In this key can be seen a string value named “MachineGuid” with a special value. This value is unique for the machine and is used for some applications to identify the machine. BlackMatter uses it to make the mutex and, very importantly, the new extension for the encrypted files.
- Make a new value of type string with a random name and put the same value as seen in “MachineGuid” to have a backup of it.
- Remove the “MachineGuid” value, and then make it again but with the binary type Instead of string type, with the same name, “MachineGuid”.
- Close the registry editor.
In this moment BlackMatter cannot affect the machine as it needs the registry key to make the ransom extension, and the most important thing is, if it cannot make it, it will return the function WITHOUT decrypting the config that is needed too. In this case it will destroy the recycle bin and shadow volumes anyways but later it will finish as it does not have any behavior to do, RSA Key to protect the files, or anything to send to the C2 as the flag was never read from the config (and the default values are false for all of them).
Though the behavior of other programs may be unpredictable, the vaccine is easy to make, and the system will boot, showing that the BlackMatter programmers made a mistake in the design of the code.
This vaccine works for all versions, including 2.0.
MITRE ATT&CK
The sample uses the following MITRE ATT&CK™ techniques: