Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Cyberattack on Democracy: Escalating Cyber Threats Immediately Ahead of Taiwan’s 2024 Presidential Election
By Anne An · February 13, 2024
Preface
Cybersecurity has become an integral part of election security. Nation-state actors and other politically motivated groups are likely to try to influence public opinion or target election infrastructure to undermine democratic processes. As a litmus test, our new detections show that Taiwan recently experienced elevated cyber threats ahead of its 2024 presidential election held on January 13, 2024, likely aimed at discrediting a political party or candidates. The detections indicate that attackers would have likely been able to employ living off-the-land techniques to gather policing, banking, and political information while evading security detections through remote endpoints.
As US voters prepare for a series of caucuses and primaries leading up to the November 2024 US presidential election, there are cybersecurity lessons learned and warnings from Taiwan’s recent presidential election. The cross-strait political context is that Taiwan’s presidential election results defied Beijing's wishes and handed the ruling party a historic third consecutive presidential victory. As background, China had openly opposed William Lai from Taiwan's ruling party, the Democratic Progressive Party (DPP) before he won the island's presidential election with more than 40 percent of the vote. The Chinese authorities also cautioned that the election could shift the cross-strait relationship away from peace if the DPP gets reelected. Similarly, there are countries and nation-state threat actors that prefer certain specific outcomes in US elections and might be willing to manipulate public opinion to achieve their goals.
Elevated cyber threats immediately before the Taiwan election
In terms of cyber threat activity, Trellix telemetry detected a spike in activity targeting organizations in Taiwan 24 hours before Taiwan's presidential election on January 13, 2024—which is a finding that has not been mentioned in the news or other industry reports to date. Specifically, malicious cyber activity rose significantly from 1,758 detections on January 11 to over 4,300 on January 12, 2024, the highest detection since the prior month of December 2023. Interestingly, Trellix telemetry shows that threat activity dropped dramatically on election day, with a little over 1,000 detections on January 13, 2024.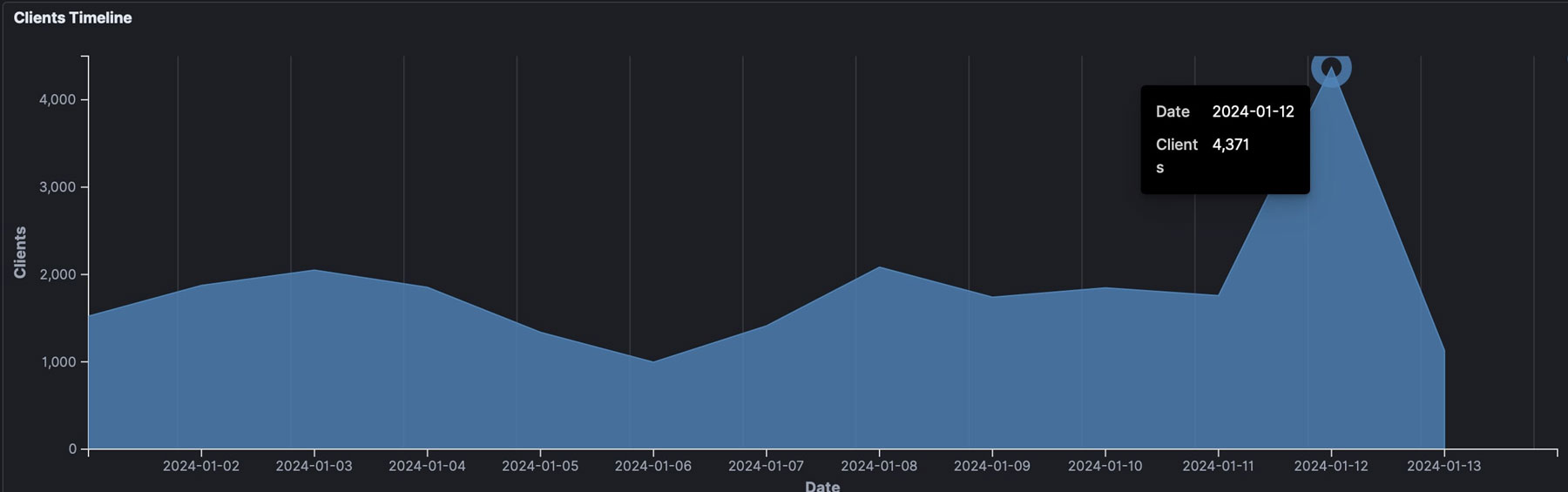
Why would cyber threat activity against Taiwan spike just 1 day before the election?
Taiwan’s local polling stations do not employ electronic technology to cast and tabulate votes. Each step of the voting process, which began almost 90 years ago, is done manually and in person, including verifying identities, distributing paper ballots, sealing ballot boxes, and tallying each ballot. As a result, cyber hacking is unlikely to have a significant impact on the election “infrastructure.”
“Kompromat” / 抹黑
We assess with medium confidence that one likely explanation for the increased malicious cyber activity would be for last-minute “kompromat” efforts and attempts—a Russian word from the Soviet-era describing the strategy of collecting damaging information about a political opponent that can be deliberately used across political, electoral, and media domains to influence public opinion--given the timing and characteristics of the attacks as well the intended targets. It is a common tactic used during elections around the world. In Mandarin Chinese, the same “kompromat” term and practice is dubbed 抹黑 (mo hei).
Although we don’t have direct qualitative evidence to corroborate the hypothesis without further examination of the data from suspected breaches or cyberattacks, the timing and attack methods, based on Trellix detection data, indirectly support the hypothesis. Specifically, the timing of threat activity explains why the threat activity peaked 24 hours before the election and quickly dropped off on election day. Presenting damaging materials, regardless of fake or real, against a political opponent 24 hours before a critical election would swing the results and deny the targeted political candidate an opportunity to respond. It would drop off since the information would have little effect as soon as the voting begins.
Targeting tactics
Additionally, Trellix detection data suggests that the attack methods leveraged by threat actors 24 hours before Taiwan’s presidential election were primarily focused on defense evasion, discovery, and command and control. Attackers appeared to subvert system defenses to gather information about accounts, systems, and networks. Specifically, threat actors attempted to hunt for local accounts, files, and directories in specific areas of a host or network share to obtain certain information from a file system. Attackers likely established command and control to facilitate information collection from a remote system. It is apparent that the threat actor is single-mindedly focused on digging for information in the hours leading up to the election date.
As shown in the following figure, we use the MITRE ATT&CK framework to map out the top attack tactics, techniques, and procedures (TTP) leveraged by attackers on January 12, 2024. The specific attack methods detected by Trellix’s global sensor are highlighted in blue.
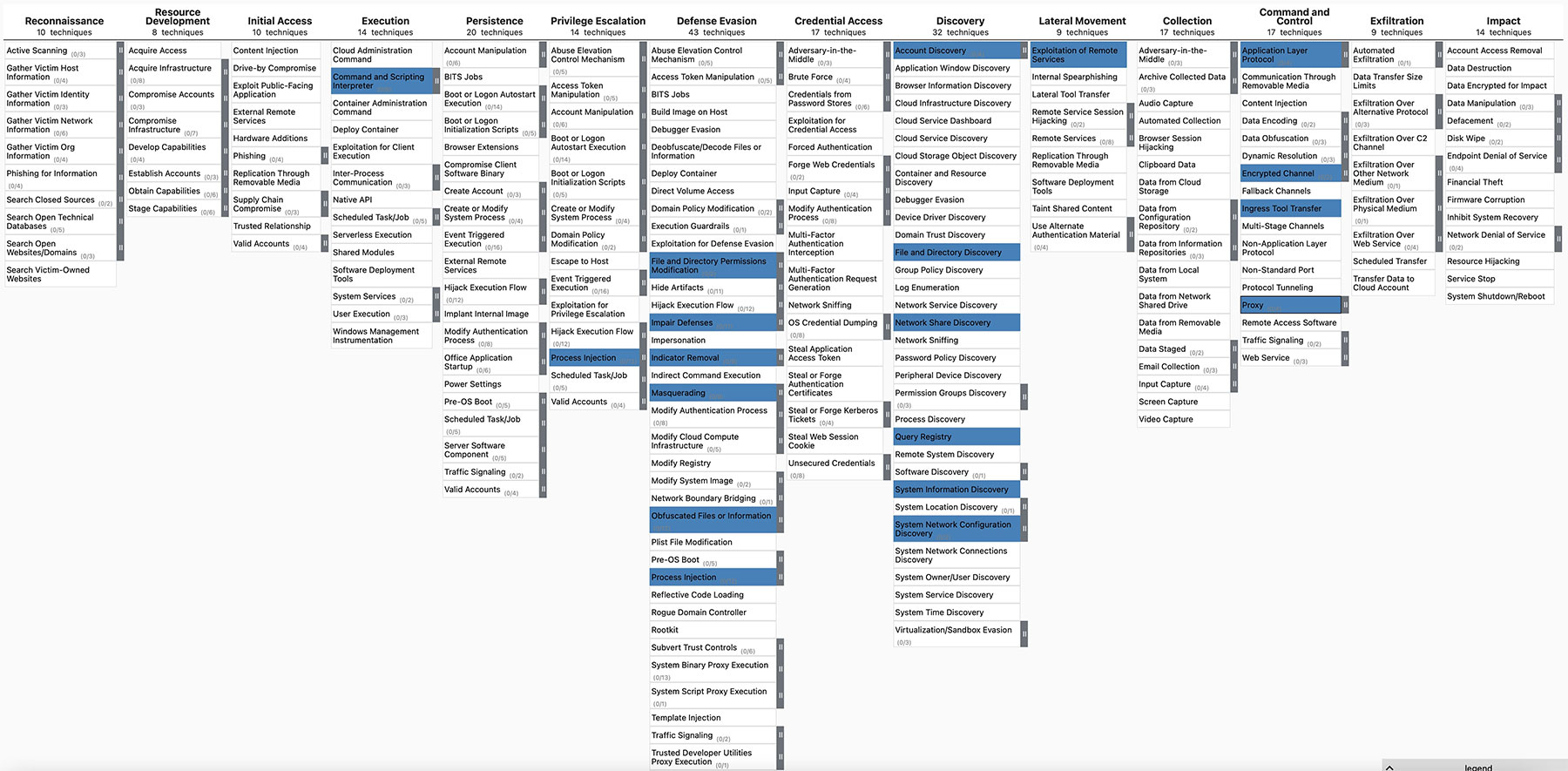
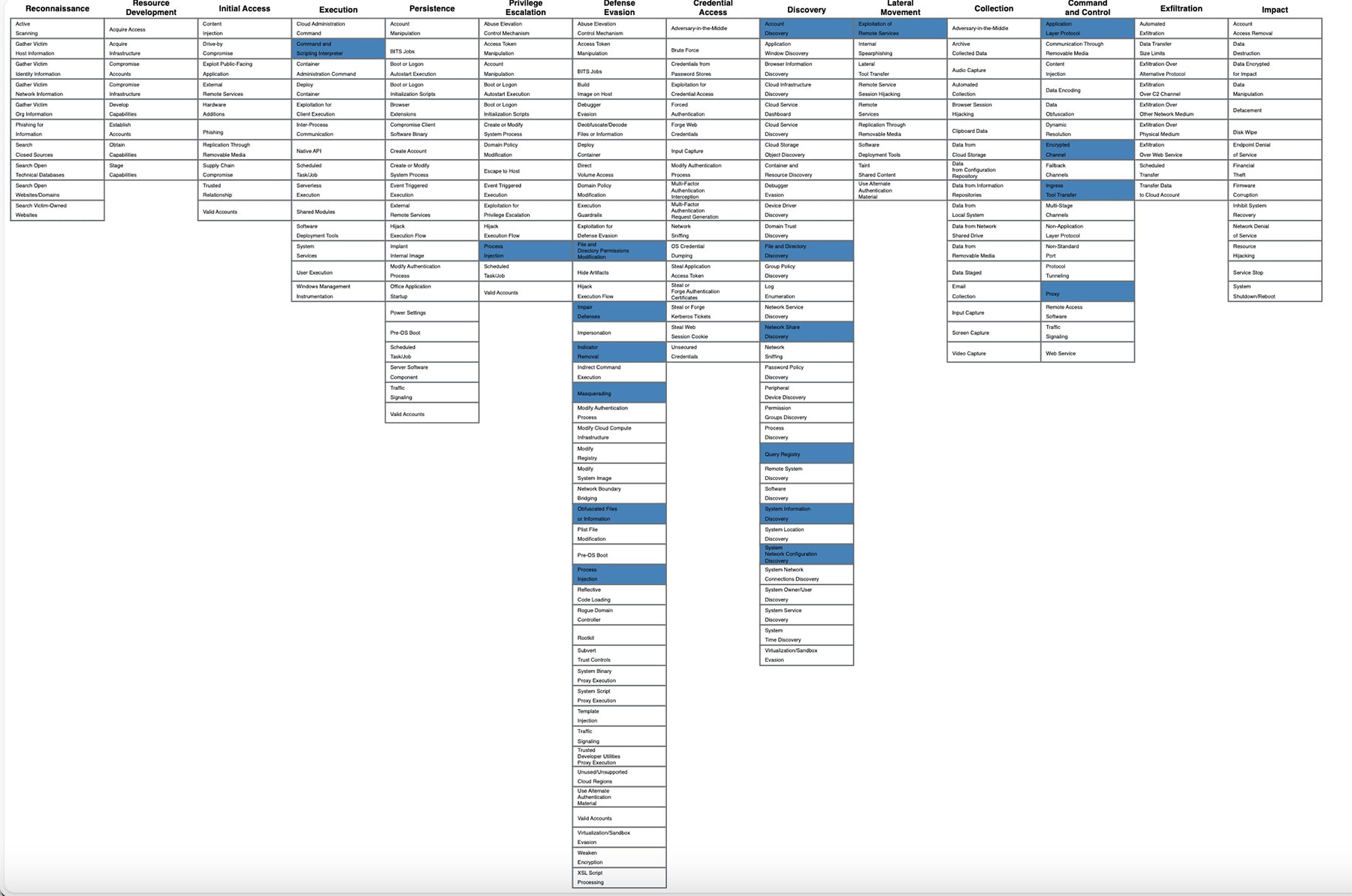
Targeting profiles
Furthermore, according to Trellix telemetry data, a portion of the malicious traffic targets a variety of organizations, such as government offices, local police departments, and financial institutions. This indicates that threat actors were likely interested in police reports, criminal records, bank statements, insurance information, as well as internal government communications. Such information can be very politically relevant at that specific moment. In sum, the attack timeframe, attack methods, and targeting profiles support the above hypothesis.
At this time, we are not able to verify whether threat actors achieved their objective or gained any valuable information. Judging from the news, there were no political scandals in the lead-up to the Taiwan election. The election proceeded smoothly and predictably. Perhaps the cyber threat activities were not successful or did not uncover sensitive information about the targeted political candidates. Perhaps Taiwan’s election defenses were seasoned and hardened to ward off such attempts.
Detailed threat activity targeting Taiwan
Beyond 24 hours, a look at the Trellix telemetry data in the 48 hours preceding Taiwan’s presidential election between January 11 and 12, 2024 indicates that over 47 percent of the malicious traffic targeted Taiwan's financial sector, while 14 percent of the threat activity was directed at Taiwan's government sector. Financial data and government information are particularly politically relevant during elections.
To provide additional context, the same set of data also shows that threat actors operating behind these malicious activities leverage a number of living off-the-land tools, such as NETSH, Windows command prompts, reg, and PowerShell. Specifically, the Windows NETSH tool is commonly used for communication between a victim and a command and control (C2). Reg is a Windows program that allows a user to query, modify, and remove information from the Windows Registry using a command-line interface. Mimikatz, China Chopper, and Cobalt Strike are among the top tools based on Trellix detection data.
Conclusion
As the political battleground has expanded into the cyber domain, the cyber front has become an integral part of election security. This new year is a year of opportunities for cybercriminals, nation-state actors, and politically motivated groups to target public opinions, and election infrastructure to undermine and control democratic processes. Taiwan recently experienced elevated cyber threats ahead of its presidential election, with the timing suspiciously suggesting a goal of influencing election outcomes. Particularly, attackers are likely to employ living off-the-land techniques to gather policing, banking, and political information to achieve their goals. They also likely simultaneously and stealthily evaded security detections from remote endpoints. Similar strategies may be leveraged for the upcoming November presidential elections in the United States.
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
