Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Dark Web Roast - January 2026 Edition
By Trellix Advanced Research Center · February 11, 2026
Executive Summary
Welcome to January 2026's underground intelligence roundup, where criminal masterminds continue to demonstrate that the phrase "honour among thieves" remains the greatest oxymoron in cybercrime. This month brought us Ukrainian death-fakers with costume shop police badges, RAMP forum administrators who concluded their operational run like a digital Don Quixote, and malware entrepreneurs frustrated by Google's unreasonable hostility to virus distribution. From $4.5 million Android exploit dreams to the emergence of "avatar detectives" who identify ransomware affiliations by profile picture, the underground continues to prove that sometimes the best cybersecurity defence is simply letting criminals be themselves.
This Month in the DarkRoast
💀 Ukrainian IcedID operator stages own death, gets arrested 200 meters from freedom
The actor INC. on Verified delivered the month's peak operational security comedy when a Ukrainian IcedID operator literally faked his own death by bribing law enforcement to misidentify a random corpse. This mastermind got a legitimate death certificate issued and thought he was home free from FBI pursuit, only to get arrested 200 meters from the Slovak border while carrying a fake "Committee for Combating Corruption" ID that looked like a knockoff police badge from a costume shop. The court set his bail at $9.2 million because, apparently, staging your own death and living in a border zone screams "flight risk". This genius laundered $1.45 million through relatives' real estate while supposedly being dead - because nothing says "low profile" like your deceased relative suddenly buying luxury apartments.

🎯 Malware entrepreneur frustrated by Google's unreasonable hostility to virus distribution
Actor slattlight on Exploit is facing the modern cybercriminal's ultimate first-world problem: how to efficiently deliver malware when all the major platforms keep shutting down their infrastructure within 12 hours. They've got a beautiful PowerShell script wrapped in PDFs, a solid YouTube channel owner database for spam campaigns, and the business acumen to register legitimate-looking domains. But Google keeps ruining their day by detecting their malicious links, and social media platforms are being unreasonably hostile to their "advertising" efforts. The post reads like a frustrated startup founder asking for advice on scaling their business, except their business model involves tricking people into downloading malware.
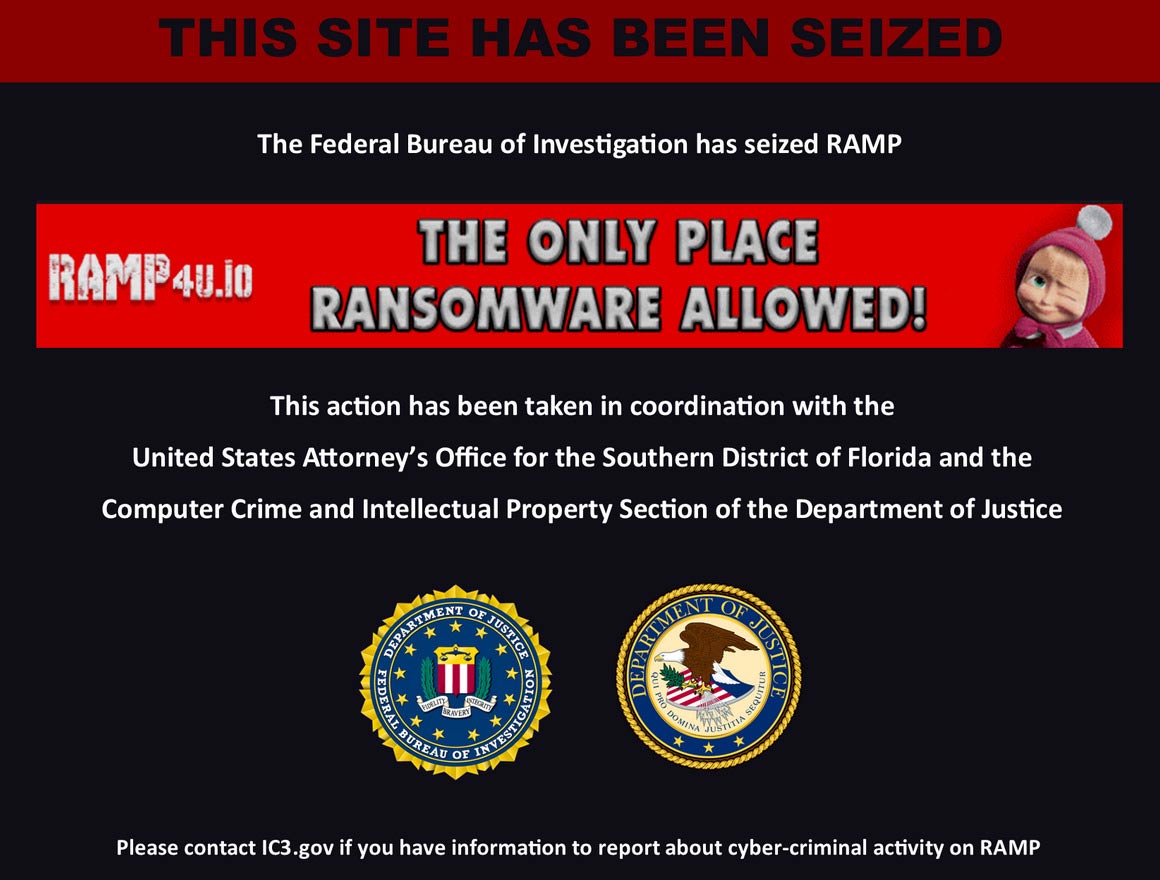
🎭 The RAMP forum farewell tour
RAMP Forum concluded its operational run like a digital Don Quixote, tilting at windmills until the very end when the FBI decided to crash their farewell party. Their final act involved administrators posting goodbye messages with all the dignity of a band playing while the Titanic sank. The forum's last days read like a tragic comedy where everyone knew the ending but pretended they were in a different movie. Their farewell tour had all the pomp and circumstance of a retirement party where the retiree forgot to mention they were being escorted out by security.
💎 Android exploit dreamer asks $4.5 million for code, offers "budget option" of only $400K
Shinymontana from BreachStars is asking for $4.5 million for an Android exploit source code, with a "budget option" of just $400K for the shellcode. This absolute legend thinks he's selling the crown jewels when he's probably peddling some recycled CVE from 2019. The best part? He's got three different price tiers like he's running a SaaS business - "Limited devices exploit" for the bargain price of $100k because apparently his malware has commitment issues. Someone needs to tell this entrepreneur that putting random numbers after "Android" doesn't make it cutting-edge technology.
🕵️ Paranoid user develops elaborate theory about federal forum fragmentation, proves own point
The actor bmwE32 on Rehub developed an elaborate theory that law enforcement is systematically destroying large forums to fragment the cybercrime community into smaller, mutually suspicious groups. His timeline: "Fall 2024 - Telegram carding channels cleaned out, Summer 2025 - XSS fell, Winter 2026 - RAMP died." He's convinced this is a master plan to make criminals "tear each other apart with bad words" until there's nobody left to organize crime. The beautiful irony is that he's posting this paranoid rant on yet another fragmented forum while proving his own point about community distrust. When your conspiracy theory about law enforcement psychological warfare is posted on the very platform that proves your theory correct, you've achieved peak criminal self-awareness.

🕵️ The avatar detective
An “unnamed” security researcher has emerged as the underground's answer to Sherlock Holmes, capable of identifying ransomware affiliations simply by examining profile pictures. This digital detective claims that certain avatars "scream ransomware gang" with the subtlety of a foghorn, though they've yet to publish their peer-reviewed methodology on criminal iconography. The underground community now lives in fear that their carefully selected anime profile pictures might be inadvertently broadcasting their criminal CVs. This has sparked an underground avatar crisis, with threat actors now second-guessing whether their chosen image of a sunset truly conveys the professional menace they were aiming for.
Conclusion
January 2026 proved that the underground economy operates on a perfect storm of ambition, incompetence, and spectacular self-sabotage. From death-faking Ukrainians with costume shop badges to forum admins selling tickets to their own FBI raids, this month's criminals demonstrated that sometimes the best threat mitigation strategy is simply providing them with enough rope. As we watch malware entrepreneurs frustrated by Google's unreasonable hostility to virus distribution and Android exploit dreamers price themselves out of their own fantasies, one thing becomes clear: the real threat to cybercriminal operations isn't advanced security measures - it's basic common sense, which appears to be in critically short supply.
Disclaimer
While these incidents are genuinely amusing, they represent real criminal activities causing significant harm. This content is for threat intelligence and educational purposes only.

Discover the latest cybersecurity research from the Trellix Advanced Research Center: https://www.trellix.com/advanced-research-center/
RECENT NEWS
-
Mar 02, 2026
Trellix strengthens executive leadership team to accelerate cyber resilience vision
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
