Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Exploiting Tragedy: Fake Donation Scams Amid Earthquake in Turkey & Syria
By Daksh Kapur · February 23, 2023

The recent earthquake that shook Syria and Turkey left a devastating trail of destruction. The whole world has shown its support and solidarity, attempting to bring those impacted by the tragedy to a state of normalcy. Unfortunately, this tragedy has also attracted cybercriminals looking to take advantage of the people’s sympathy with fake donation scams.
These scams come in various forms, but the most common include fake donation emails and websites. These emails often appear to come from a legitimate charity, though they are actually sent by cybercriminals who are hoping to take advantage of people's goodwill. The emails often feature a link that directs users to a malicious website, which then asks them to enter their financial information or ask the victims to send their donations to the attacker's cryptocurrency wallet address.
Cybercriminals have been seen creating fake donation websites that look the same as legitimate donation sites and feature similar branding, logos, and pages, so it can be hard to differentiate them. The websites also contain images of the devastation caused by the earthquake coupled with well written sympathetic content appealing to the reader to donate to the victims.
Use of QR codes
We have also observed the attackers using QR codes along with malicious email or URLs which can be used to quickly make a payment to the attacker’s account. As QR codes make it more convenient for the user to make the payment, it increases the probability of the victim being tricked into making the payment.
Social media donation scams
Cybercriminals are also increasingly using social media to run fake donation scams, taking advantage of people’s generosity and creating false hopes in vulnerable populations. Others are taking donations for legitimate causes but pocketing the money for themselves. Scammers are typically very creative in their tactics, creating convincing stories and images to make their fake campaigns seem legitimate.
These scams take the form of bogus crowdfunding campaigns and donation requests that have been created by cybercriminals. The scammers use images of children and families affected by the earthquake in their posts to evoke an emotional response from users, in order to lure people into donating money to their fraudulent campaigns. The money that is collected then goes directly into the pockets of the hackers.
The articles published by Bleeping Computer and BBC News also talk about scammers utilizing TikTok & PayPal to run donation scams. To make their donation campaigns look legitimate, scammers deposit a considerable amount to their own donation campaign in an attempt to make the campaign look legitimate.
Malicious posts on social media
We observed various posts on social media as an appeal for donations which would contain cryptocurrency wallet address of the attacker.
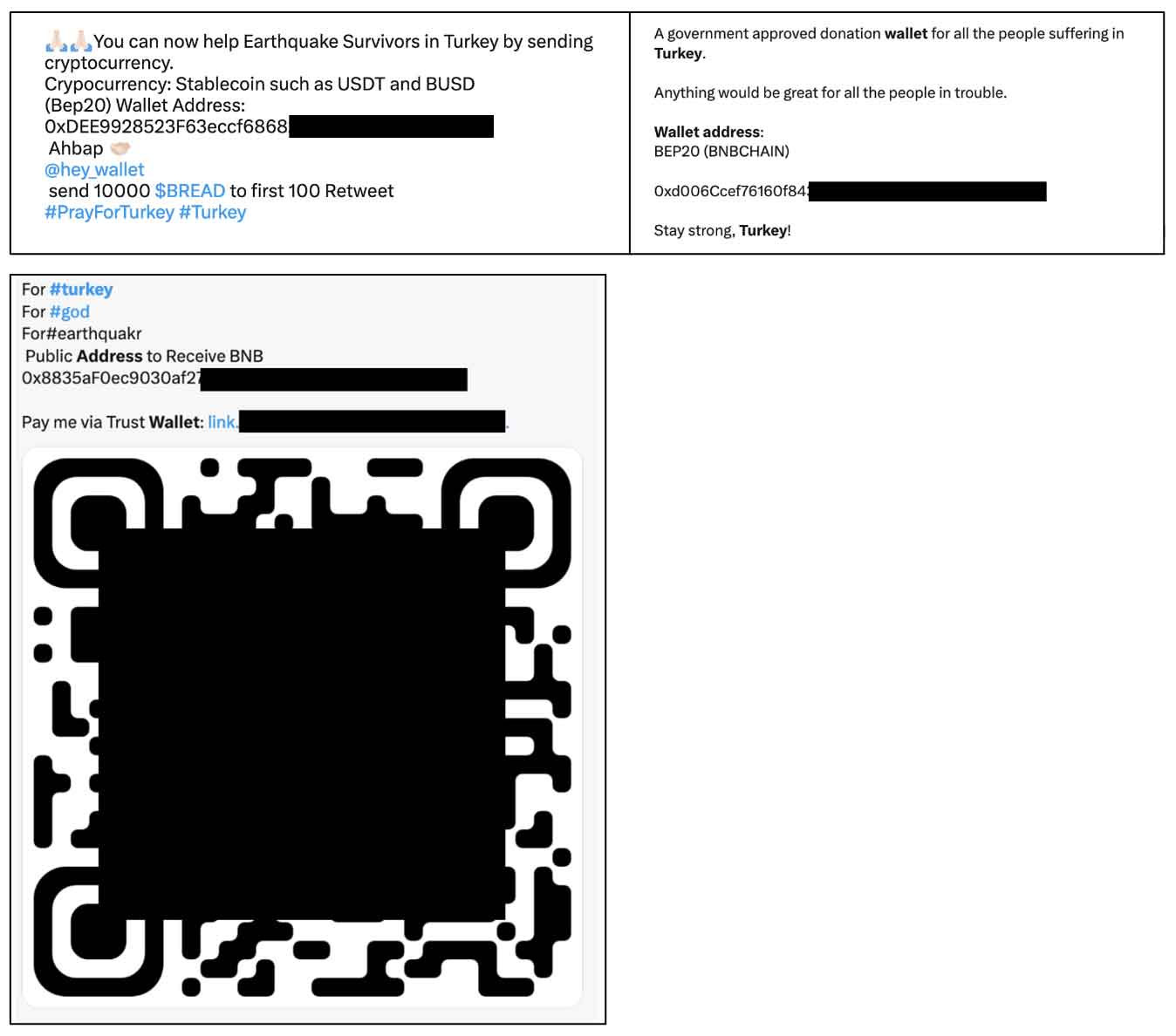
Malicious emails
Trellix Advanced Research Center researchers found different styles of fake donation spam campaigns. The emails either come as an appeal for donations which would contain a recipient financial information or a URL directing the victim to a fake donation website.
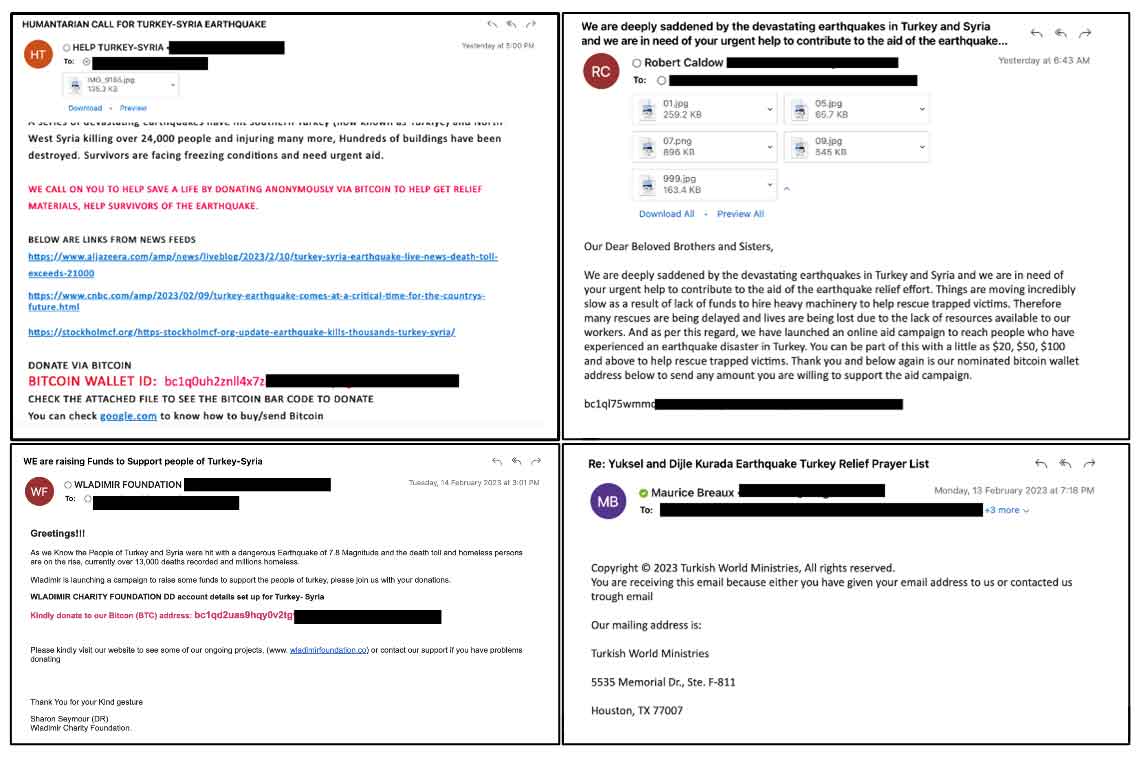
Malicious URLs
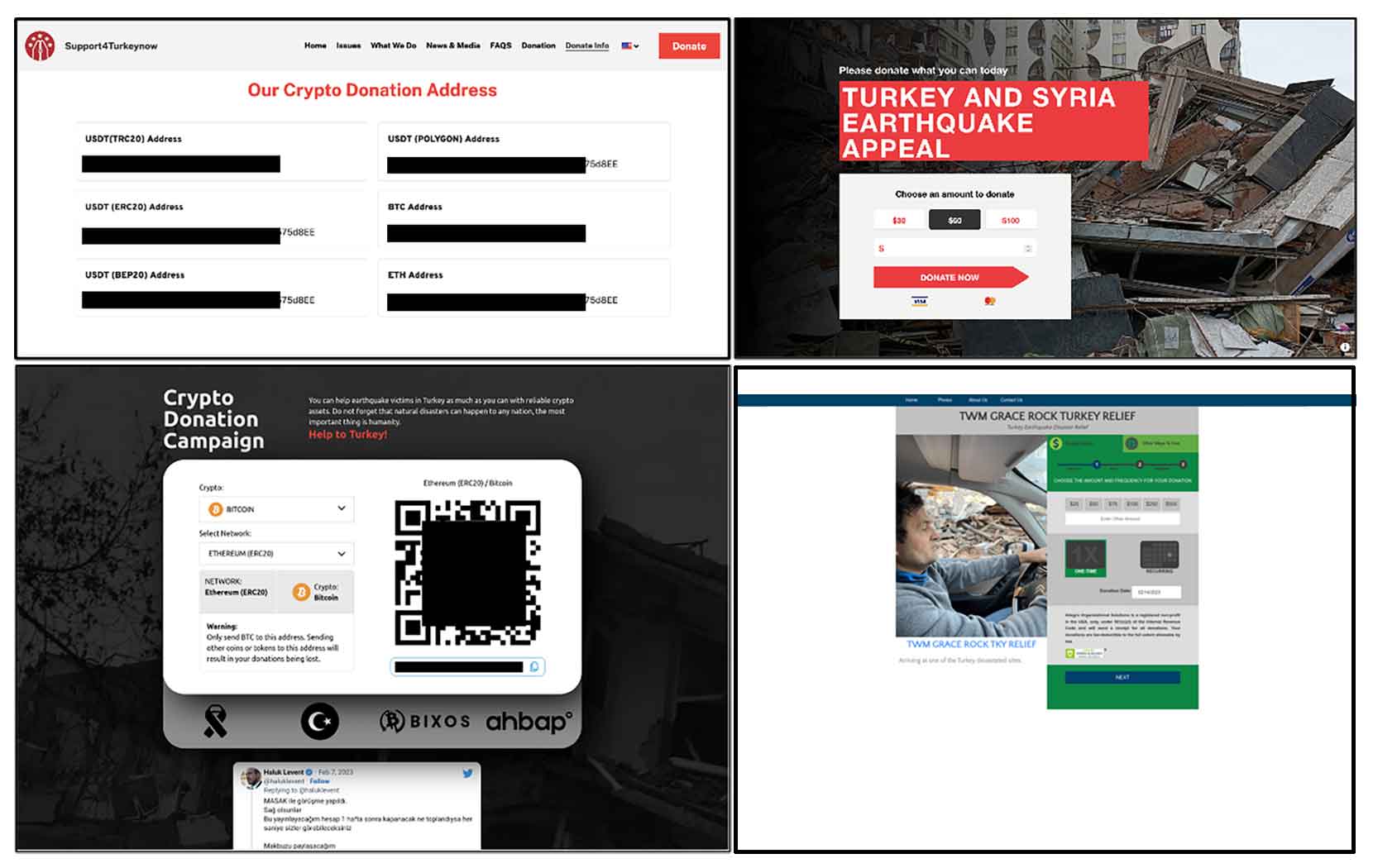
The following are some of the malicious web pages being utilized to run fake charity scams. The pages contain images of devastation caused by the earthquake along with an appeal to help the victims along with the recipient’s financial information.
Trellix email protection
Trellix Email Security provides comprehensive protection from such attacks via a multi-layered approach that includes checks on the URL, email, network and attachment levels to ensure that any potential threat is detected and prevented from causing harm. Our product continuously monitors and updates its threat intelligence database to stay ahead of new and evolving threats.
The following is some a subset of the Trellix’s email-based detections that have been observed for the ongoing campaigns:
- EL_BTC_RPBL
- BITCOIN_SCAM_04
- EL_CHARITY_HUNTI
- EL_BTC_EXPL1
- BTC_SCAM
Conclusion
We urge everyone to be extra vigilant when making donations and to not trust any untrusted source. With sufficient caution and due diligence, it is possible to make sure donations reach the right place. People should also make sure to research the organization they are donating to and make sure they are legitimate before making any payments.
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
