Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Hacktivist Groups: The Shadowy Links to Nation-State Agendas
By Ernesto Fernández Provecho · December 16, 2024
Introduction
Hacktivism, the intersection of hacking and activism, has emerged as a potent force in the digital age. It involves using technology to achieve social or political goals, often by disrupting or manipulating online systems. From exposing government corruption to advocating for social justice, hacktivists have employed their skills to challenge authority, disrupt and promote change.
The recent conflicts between Ukraine and the Middle East have seen a surge in hacktivist activity, with groups aligned with both sides engaging in cyberattacks. Notably, both Russia and Iran administrations have been accused of sponsoring hacktivist groups to further their geopolitical interests. This link to state-backed actors with more resources and expertise, is posing a significant threat to cybersecurity and national security.In this blog we will cover a large set of Hacktivist groups, by no means is this an exhaustive list of all the groups.
Hacktivist groups that have known links to Nation-States
Russia
Russian aligned hacktivist groups have been common over the years, but, since the beginning of the Ukraine invasion, their number has increased dramatically. The majority of these groups have been created by individuals that want to collaborate with the Russian agenda by attacking Ukrainian and Ukrainian-aligned countries' infrastructure, however, they do not have any links with the government.
On the other hand, there are a few groups that seem to be backed by the government, maybe not directly, but using some threat actors as intermediaries like Sandworm Team (APT44), a group supposedly coordinated by the Russian Main Intelligence Directorate (GRU) [1].
The activities performed by such groups can be categorized in four categories, denial of service attacks, defacement attacks, propaganda dissemination and information leakage.
State-sponsored hacktivist groups
Cyber Army of Russia Reborn (CARR)
CARR is a Russian-aligned hacktivist group that started its activity in 2022, after the beginning of the Ukrainian war. The group is specialized in distributed denial of service (DDoS) attacks, but it also has disseminated sensitive information of their targets, which suggests that the group may have performed more advanced attacks or is collaborating with other entities, which makes sense if you compare the attacks performed by the Russian threat actor Sandworm Team, also known as APT44, and the information leaked by CARR, a behavior also noticed in other groups like XakNet or Infoccentr [1].
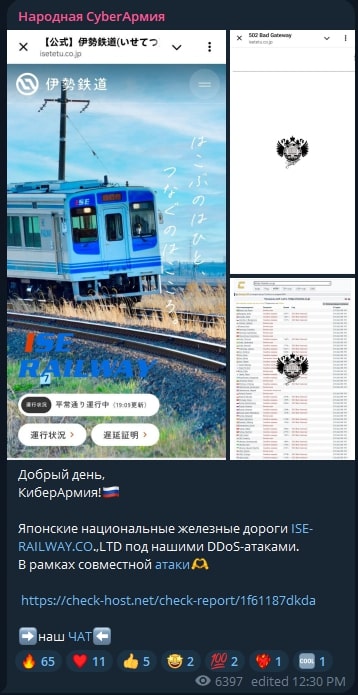
The group operates in Telegram in the channel “CyberArmyofRussia_Reborn”, in which the administrators, “T96_KA”, “MotherOfBears”, and “error_404_smoke”, publish the different attacks performed by the group and news about the group and Russia.
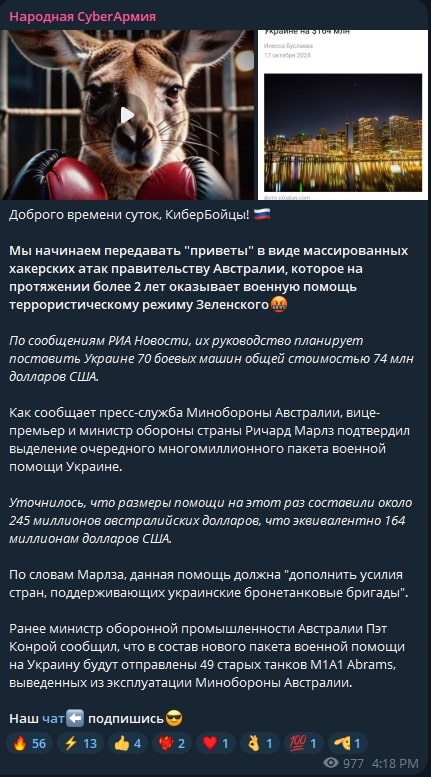
One of the administrators, “MotherOfBears”, whose real name seems to be Юля, Yuliya in Russian, has posted different pictures in Telegram in which her face and, presumably, the administrator of NoName057(16), another hacktivist group, can be spotted, suggesting a relationship between both entities. Also, in her biography, “MotherOfBear” states to be the channel coordinator of NoName057(16).
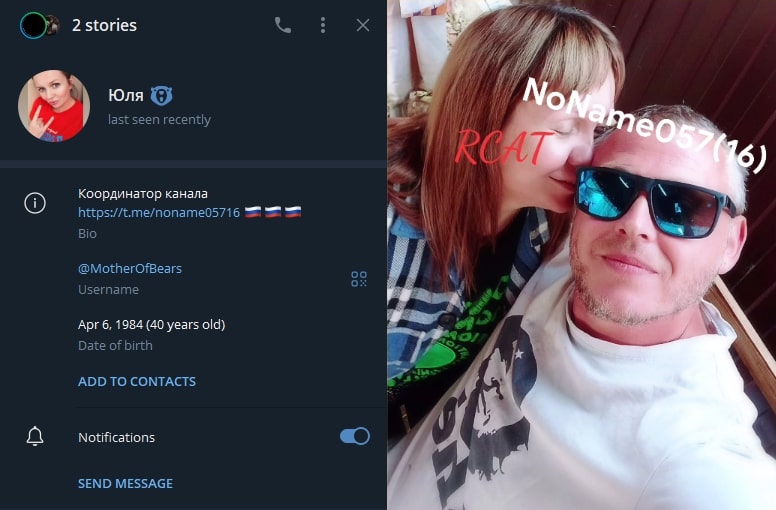
In July 2024, the US Treasury sanctioned and exposed the identity of “MotherOfBears”, Yuliya Vladimirovna Pankratova, and another CARR member, Denis Olegovich Degtyarenko [2].
NoName057(16)
NoName057(16) is a group created in 2022 exclusively focussed on DDoS and defacement attacks against targets in countries that support the Ukrainian government and, in recent months, the Israeli government. To perform such attacks, the group operates in Telegram under the channel “noname05716” and relies on a self-developed tool called DDoSia, which anyone can use to support the interests of the group by joining the DDoSia Group Telegram handle (https://t[.]me/+igupZcC_O45jMGY1), which gives access to 8 different channels [3].
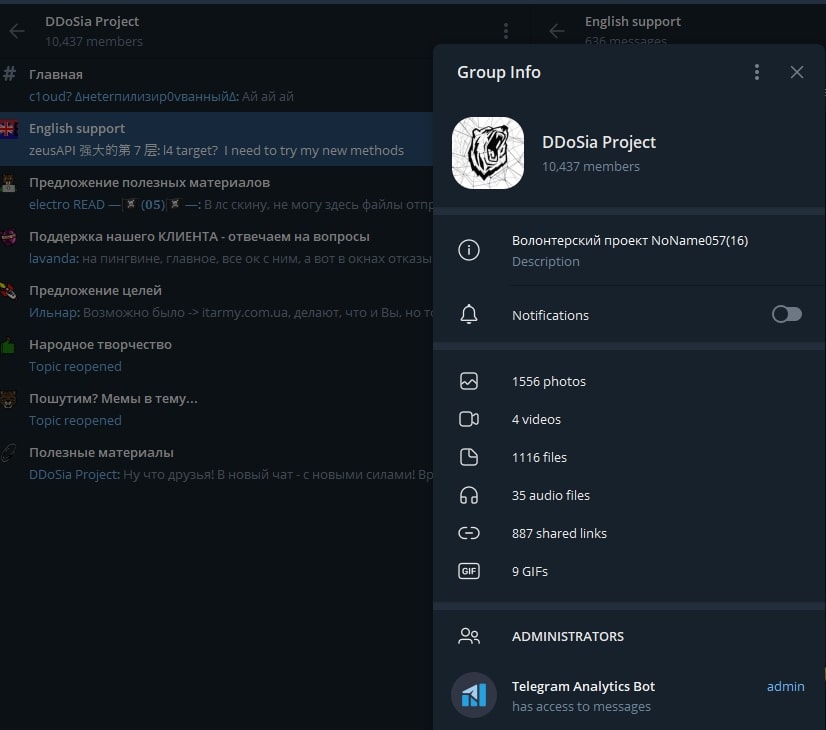
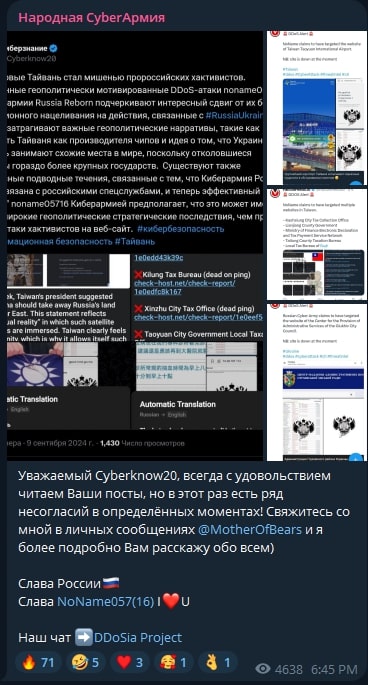
The group has created alliances with many other hacktivist groups to support their efforts with the DDoS attacks. However, the fact that one of the previous CARR administrators, “MotherOfBears”, has joined NoName057(16), the continuous forwarding of CARR posts, and previous statements, suggest that both groups seem to collaborate closely, which can also indicate a cooperation with Sandworm Team.
XakNet
Hacktivist group linked to Sandworm Team that was active from 2022 to 2023, they were focussed on DDoS attacks and information leakage [1].
Infoccentr
Infoccentr is a hacktivist group linked to Sandworm Team that operates in Telegram in the channel “infoccentr”, where administrators post Russian propaganda about the ongoing war to deter Ukrainian morale and boost Russian [1].
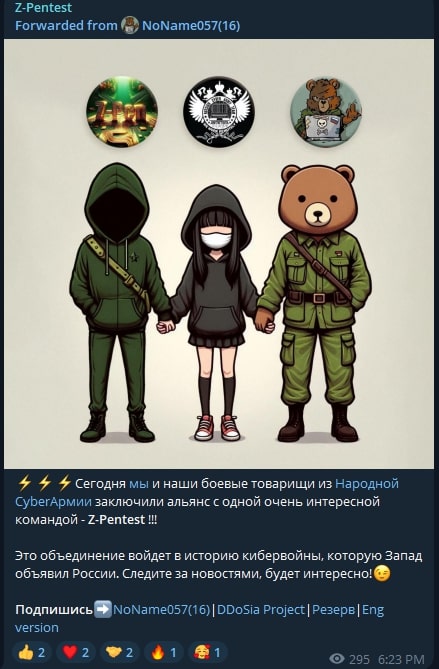
Z-Pentest
Z-Pentest, “z_pentest” in Telegram, is one of the latest Russian hacktivist groups, established in September 2024. Specialized in “hack and leak” operations and defacement attacks, the group formed an alliance with CARR and NoName057(16) to support their operations only a few days after they started to operate, a situation that may indicate a possible addition to the Sandworm Team hacktivist portfolio, something we haven’t confirmed yet.
Iran
Iran is well known for its hacktivist groups targeting Israel and the United States, a situation that has grown exponentially since the beginning of the Hamas-Israel 2023 conflict. Many different individuals and organizations have started to perform cyber incursions, mostly denial of service and defacement attacks, a set of activities that matches the Russian hacktivist modus operandi.
However, in the case of those groups allegedly backed by the Iranian government, they tend to rely more on information leakage, system disruption, and propaganda dissemination, as an attempt to disrupt normal activities and confuse the citizens. This way, Iran pretends to affect the ongoing war in Palestine and the 2024 elections in the United States [4].
Unlike Russian groups, Iranians tend to be directly managed by the government using either an internal institution like the Islamic Revolutionary Guard Corps (IRGC) or the Ministry of Intelligence and Security (MOIS), or an external company, which will create the groups and coordinate their actions [5].
Threat actors
Emennet Pasargad
Emennet Pasargad is an Iranian company, previously named Eeleyanet Gostar and Net Peygard Samavat Company, that presumably works for the Islamic Revolutionary Guard Corps (IRGC) of Iran since 2020 to carry out cyber operations against institutions from the United States, Europe, Israel and other Middle East countries. These campaigns are performed through hacktivist groups in an attempt to hide its real origin [4][6].
Hacktivist groups created by Emennet Pasargad tend to share different characteristics:
- The group has social media accounts on different platforms, such as Instagram, Twitter, and Telegram.
- The graphics shared by the group, as well as their logo and backgrounds, are well crafted. Also, they tend to have a similar iconography.
- The tactics and techniques are quite similar, relying on attacks against poorly secured web pages.
- Hack and leak operations are their main modus operandi.
Based on the prior characteristics, the following hacktivists groups have been categorized as Emennet Pasargad with medium confidence (some groups may not exist anymore):
- ALTOUFAN TEAM
- AMC239
- Anzu Team
- Atlas Group
- Black Magic
- Byte Blitz
- Cyber Cheetahs
- Cyber Flood
- Deus
- For Humanity
- Forces of Light
- Generous Thief
- Hackers of Savior
- Holy Souls
- Islamic Resistance Movement
- Jewish Peach Advocate
- Market of Data
- Menelaus
- Sangkancil
- Yemen Cyber Army

Moses Staff
Moses Staff is a hacktivist group supposedly sponsored by the Iranian IRGC. They started to operate in 2021, encrypting and leaking sensitive information from several Israeli companies [6].
Hacktivist groups linked with Moses Staff tend to share different characteristics:
- The group has social media accounts on different platforms, such as Instagram, Twitter, and Telegram.
- The logo and the name tend to have religious iconography.
- The tactics and techniques are quite similar, exploiting a known vulnerability on a public facing application. Once inside, the attacker spreads across the network and drops a backdoor to exfiltrate sensitive data. Then, to cause a bigger impact, the group detonates a ransomware to encrypt the infrastructure data without asking for a rescue payment [6].
At the moment, only Abraham’s Ax hacktivist group has been linked to Moses Staff.

CyberAveng3rs
Another IRGC hacktivist cluster, CyberAveng3rs, which also includes Soldiers of Solomon, was specialized in hack and leak operations, which, in many cases, included false or magnified information [4][6]. Currently, both groups are no longer active.
Agrius
Agrius is a threat actor that has mainly been focussed on attacking Israeli entities. It is believed to be operating under the direction of the MOIS of Iran.
Initial access is performed exploiting a known vulnerability, subsequently deploying a backdoor or a webshell. Then, the modus operandi of the group is mainly about the disruption of the victims’ normal activities by deploying either a ransomware or a wiper [6].
Currently, the following hacktivist groups have been attributed to Agrius: Malek Team, Sharp Boys, Justice Blade, and MoneyBird [4]. None of these groups are active nowadays.
China
In the case of China, there are different hacktivist groups that are aligned with the interests of the Chinese Communist Party. However, there is little evidence of hacktivist groups backed by the government, one example can be the initial access broker “Uteus”, also known as UNC5174, which has exploited systems worldwide using N-day exploits such as CVE-2023-46747 [7].
Conclusion
In conclusion, hacktivist groups with a Nation-state linked, either state-sponsored, state-influenced or allowed present a complex and evolving threat landscape. Often acting as a proxy, these groups can leverage their resources to carry out cyberattacks. While their traditional tactics may seem less severe, involving attacks like DDoS and defacement, their capability to escalate to more destructive attacks, such as ransomware and wiper malware, cannot be underestimated.
The alignment of their activities with geopolitical events further underscores their strategic importance. As the geopolitical landscape evolves and cyber threats will continue to be a part of the conflict. We expect the frequency and severity of these attacks only to rise. Organizations must remain vigilant, adapt their security measures, and understand the motivations, capabilities of these groups via extensive threat intelligence, to effectively mitigate the risks they pose.
References
[1] https://cloud.google.com/blog/topics/threat-intelligence/gru-rise-telegram-minions/
[2] https://home.treasury.gov/news/press-releases/jy2473
[3] https://blog.sekoia.io/following-noname05716-ddosia-projects-targets/
[5] https://services.google.com/fh/files/misc/tool-of-first-resort-israel-hamas-war-cyber.pdf
[6] https://www.trellix.com/blogs/research/the-iranian-cyber-capability/
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
