Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
ARCHIVED STORY
IoT Devices: The Gift that Keeps on Giving… to Hackers
By Tim Hux · November 16, 2017
McAfee Advanced Threat Research on Most Hackable Gifts
You’ve probably noticed the recent increase in Internet connected drones, digital assistants, toys, appliances and other devices hitting the market and maybe even showing up in your own home. The sale of these “Internet-of-Things” (IoT) devices is expected to reach 600 million units this year and, unfortunately, security has sometimes become a casualty of the race among manufacturers to be the first to sell these smart gadgets into millions of homes. This has provided potentially millions of opportunities for hackers to see what devices they can compromise and possible even control. In the past year hackers and security researchers were able to bypass the security of a range of these IoT devices.
Toys
It was discovered early this year the Cayla doll could allow hackers to take control of the toy and record video and audio without the user’s consent. A demonstration by the National Cyber Security Centre in London also shows the doll could be used to unlock smart locks allowing criminals to compromise your home through the front door. The flaw is so serious Germany’s Federal Network Agency required retailers to pull the dolls off shelves, banning them throughout the country. In the United States, the Federal Bureau of Investigation (FBI) also released a public service announcement alerting the public to the potential risk Internet connected toys pose. The defect in the Cayla doll lies in the insecure Bluetooth connection, allowing anyone to listen and converse through the doll using an ordinary mobile phone.
Similar security flaws were recently found in multiple children’s watches being sold across Europe and the UK. Security experts commissioned by the Norwegian Consumer Council found the smart watches could allow outsiders to track the child through the GPS signal, access personal data on the device, disable the emergency SOS function, and remotely listen to the youngster without the knowledge of a parent or guardian. On a positive note, the manufacturers behind the watches have responded responsibly and either have or are in the process of correcting the defects.
Cameras
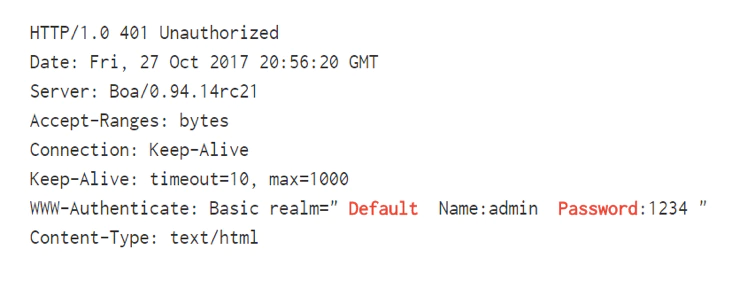
Internet connected cameras and baby monitors have been around for a few years, but manufactures are still shipping insecure devices. A quick search on the IoT search engine Shodan for the word “IPCamera” shows more than 39,000 in total. This year saw multiple stories surface involving hackers able to remotely control cameras, record video and audio, and even speak to children. We often see consumers configure cameras with remote access, but fail to put in place the correct security controls. Failure to change default passwords or use of weak passwords is a common offense among users. In other instances, the manufacturer of the device uses outdated third party software or leaves ports open by default.

Digital Assistants
Controlling your smart devices with digital assistants from Apple, Amazon, Google, and others are a neat way to control lights, appliances, and the home’s A/C unit. Researchers from Zheijiang University in China released a report in August showing it’s possible to interact with the assistant using inaudible ultrasound commands. The scientists dubbed their findings the “DolphinAttack” and could issue commands to the device at a very high frequency that is too high for humans to hear but was still understood by a range of assistants, including Siri, Google Now, Cortana, and Alexa. The researchers demonstrated it’s possible for someone to issue a range of commands from a distance without anyone near the device realizing the assistant was being controlled remotely. Although no real-world hacks are known at this time it’s safe to say hackers are well aware of the vulnerability.
Drones
Drones will most certainly be at the top of many a Christmas list this year. The market has exploded and the sale of drones for personal use are expected to be over $2 billion globally in 2017. With that many drones in the sky, and ample evidence that the devices can be hijacked, the security world has taken serious notice. Security researcher Jonathan Andersson demonstrated how he was able take control of a drone mid-flight, resulting in the owner losing complete control. The flaw lies in the wireless transmission control protocol DSMx, which is used in the communication between radio controllers and many remote-control devices, including drones. The researcher created a hardware device which takes advantage of the DSMx protocol flaw, and allows him to make the hijacked drone perform a range of movements, including stopping, starting, and steering. The good news is the hacking device was not made public, but that won’t stop hackers from attempting to make their own similar gadget to take control of drones from unsuspecting users.
It’s not uncommon for hackers to prey on the latest popular Internet connected devices. Millions of IoT devices will be purchased this holiday season, and consumers will be well-served to do their homework. You don’t need to become an expert, but reading the user’s manual before connecting a device to the Internet is a good practice to make sure the gadget is setup properly. Make sure to also keep the device’s firmware up to date, downloading any manufacturer updates to safely fix any newly discovered vulnerability flaws. If you’re purchasing an IoT device as a gift, make sure to research it first for known vulnerabilities to make sure you don’t get caught giving a gift that could turn out to be security risk. It only takes one hacked device that is connected to your home’s Wifi to allow personal data to be stolen, devices to be hijacked, or your connected gadgets themselves becoming part of a botnet of infected systems that hackers use to launch attacks on other home and business systems.
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.