Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
ARCHIVED STORY
‘Popcorn Time’ Ransomware Sure to Cause Indigestion
By Tim Hux · December 19, 2016
In early December the new ransomware “Popcorn Time” was discovered. It gives the victim the option of paying the ransom or infecting two other individuals and getting them to pay. “Popcorn Time” is a legitimate application for streaming movies and series. The ransom note gives the victim seven days to choose either option or the files will be lost forever. This is the first time we have seen a threat actor give the victim an option to gain access to the decryption keys. It seems like a crude way to spread ransomware but malware writers will do anything to stand out from the countless number of variants we see every day. Details in the unfinished code also shows the ransomware will start deleting random files if a user enters the wrong decryption key four times. The malicious software pretends to be a legitimate copy of the real Popcorn Time.
The first sample discovered targeted only a test folder on the Windows desktop but current samples show the ransomware will encrypt files located in My Documents, My Pictures, My Music, as well as on the desktop. The ransomware also attempts an emotional appeal by claiming all monies collected will go to food, medicine, and shelter for people living in Syria. Malware writers pretending to claim their actions are beneficial is nothing new in the world of ransomware.
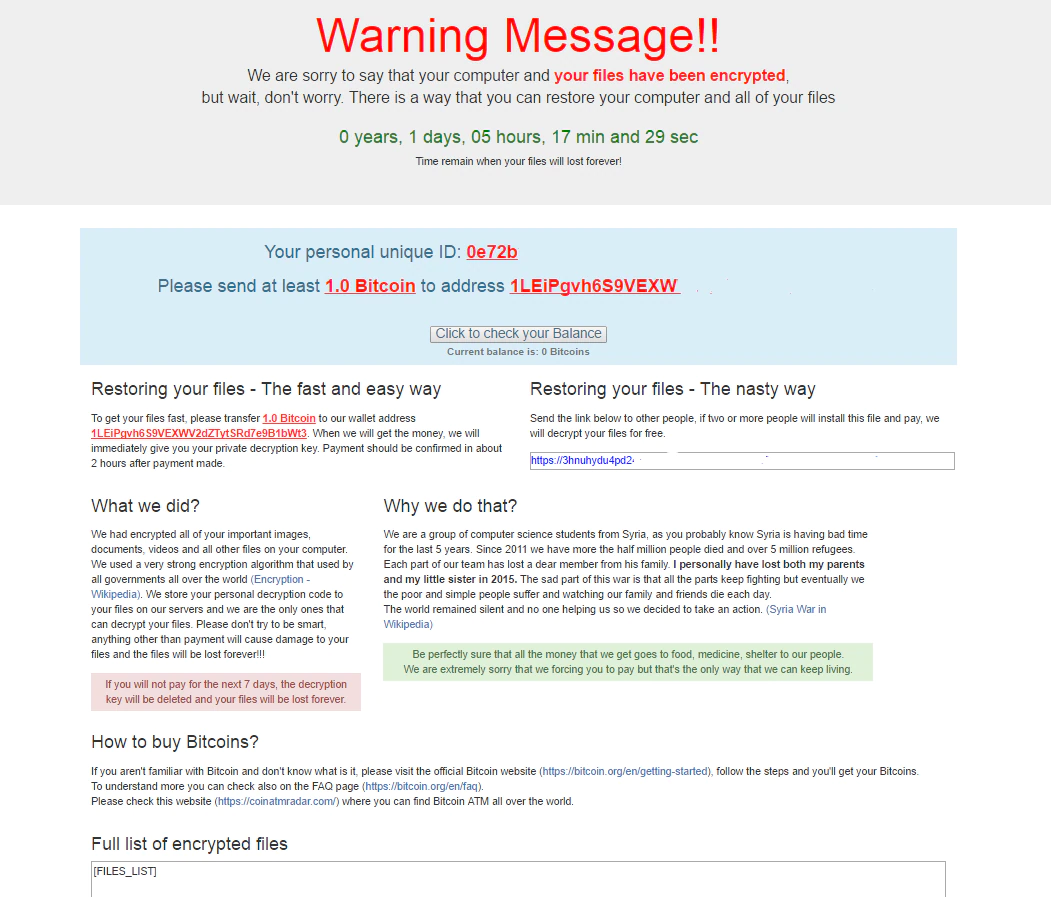
At the time of this writing, the ransomware does not appear to be spreading as quickly as prominent ransomware such as Locky or Cerber. We have seen a very small discovery rate, with detections in North America, Western Europe, and Eastern Europe. Also, the Bitcoin address associated with Popcorn Time shows that no one has paid the ransom. The low rate of samples and with no funds coming in may explain why we continue to see updated versions of the ransomware. It is not uncommon for malware authors to continuously update their code to infect as many victims as possible. For example, the following program database files found during analysis shows five versions of the ransomware to date:
- C:\<…..>\VERSIONS\V1.1-29.11.2016\Popcorn Time\Popcorn Time\obj\x86\Debug\Popcorn Time.pdb
- C:\<…..>\VERSIONS\V1.2-30.11.2016\Popcorn Time\Popcorn Time\obj\x86\Debug\Popcorn Time.pdb
- C:\<…..>\VERSIONS\V1.2\Popcorn Time\Popcorn Time\obj\x86\Release\Popcorn Time.pdb
- C:\<…..>\VERSIONS\V1.3\Popcorn Time\Popcorn Time\obj\x86\Release\Popcorn Time.pdb
- C:\<…..>\VERSIONS\V2.0\Popcorn Time\Popcorn Time\obj\x86\Release\Popcorn Time.pdb
This ransomware demonstrates the same techniques as most others (disguised as a legit app, encrypts files, demands ransom) but it reminds us that malware writers will continue to find unique ways to stand out.
Popcorn Time is based on the open-source “educational” ransomware Hidden Tear. As we have seen many times before, “educational” ransomware can be abused, resulting in real-world malware that cannot be decrypted without infecting others or paying the ransom.
All samples related to this ransomware are detected by McAfee’s endpoint products.
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.