
Trellix Global Defenders: Utilizing the Adaptive Defense Model Against Information Stealers
By Taylor Mullins · May 23, 2022
Trellix is continuing to observe the continued growth in usage and general availability of Information Stealers that have the functionality to collect passwords, cookies, credit card information, autocomplete data, browsing history, and file download history from browsers. Certain variants of Information Stealers have the additional capabilities of keylogging and collecting the digital fingerprint of the victim machine.

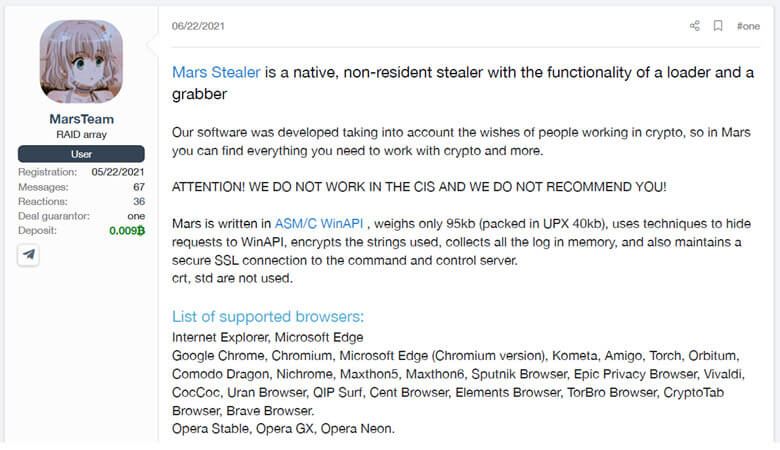
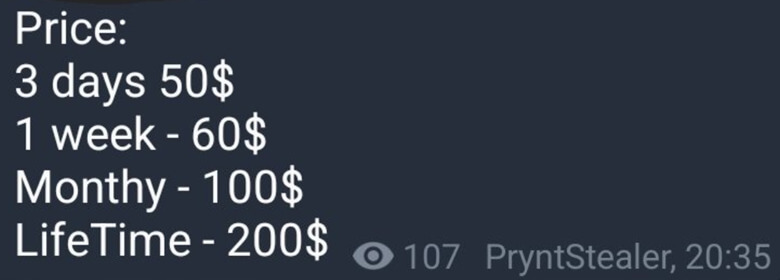
One of the reasons for the growth in usage of Information Stealers is due to the vast availability of variants advertised on the Dark Web that range in cost from as little as $100 to free for users of certain Threat Actor Telegram Communities. Prynt Stealer malware targets applications and services to extract data from a target machine including browsers, file transfer programs, secure communication software, social media applications, crypto wallets, and gaming applications. Prynt Stealer makes the claim that the info stealer is Fully Undetectable (FUD).
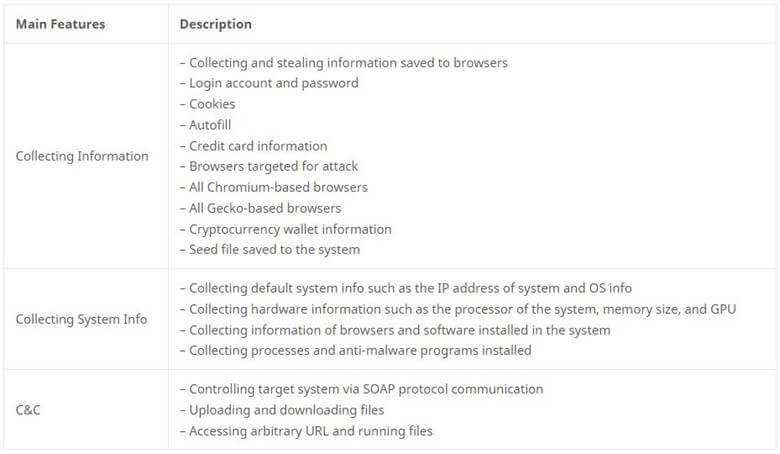
Redline Infostealer is one of the most used information stealers currently observed across the globe that is marketed as a tiered subscription allowing threat actors to use the information stealer, subscribe at different costs and purchase specific access levels. While Redline is often associated as being a password stealer, Redline also has the capabilities to steal login information, autocomplete data, passwords, and credit cards information from browsers. Threat actors can collect user and system info including target location, installed software and has the capability to steal cryptocurrency cold wallets.
Applying the Trellix Adaptive Defense Model
Security teams can utilize the Trellix Adaptive Defense Model to combat the Tactics, Techniques, and Procedures (TTPs) of Information Stealers for each phase in the attack lifecycle (before, during, after). Defensive playbooks help in adjusting the defender’s strategy based on progressive insights, providing the ability to adapt quickly to improve resiliency and mitigate impact.
Trellix Adaptive Defense Model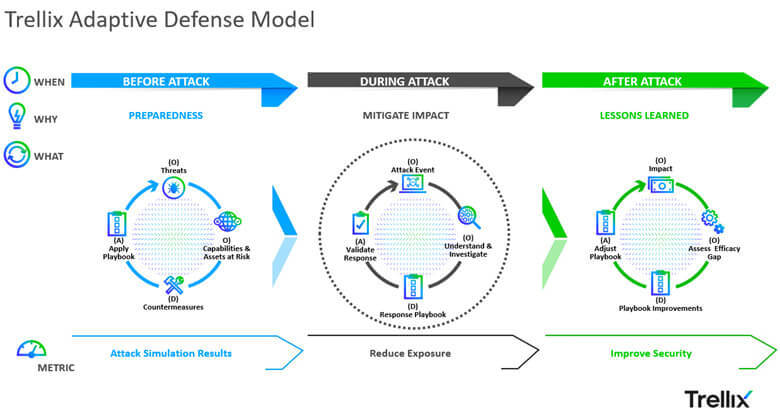
Before the Attack – Applying Countermeasures
Deploying countermeasures before entry and execution of an information stealer can help in alleviating the damage and additional Tactics, Techniques, and Procedures (TTPs) often associated with these types of attacks.
Initiative-taking mitigations can prevent initial access, credential storage, and exfiltration of data. While Web browsers typically store the credentials in an encrypted format within a credential store; methods exist to extract plaintext credentials from these credential stores. Even if the users decline to store their credentials on the browser, the password management system will still add an entry to indicate that the website is "blacklisted." While the adversaries may not possess the actual passwords for the "blacklisted" accounts, it does tell them of the account existence, thus allowing them to perform credential stuffing or social engineering/phishing attacks.
- Review the CISA alert on areas routinely exploited for Initial Access and apply recommendations to your environment and security stack.
- Utilizing two-factor authentication can help reduce the successful reuse of stolen credentials.
- Incorporating third-party password managers that can provide additional security controls.
- Prevent storage of browser credentials by disabling the ability for users to utilize Browser Password Managers via the local settings or Group Policy Object.
- Keep endpoint security current on signature and malware behavior content releases
- Practice least privilege on end user permissions, threat actors target end users with links claiming to be Windows 11 Operating System Upgrades.
- Limit the file types allowed for web downloads to only those necessary for job duties.
- Recent attacks have utilized remote services and IM applications such as Telegram for data exfiltration, utilizing Data Loss Protections can notify or stop data exfiltration attempts via remote applications.
- Apply hunting Rules and threat intelligence across the security stack for early detection and identification of the Tactics, Techniques, and Procedures (TTPs) associated with information stealers.
- Educate users on identifying phishing emails and visiting suspicious websites.
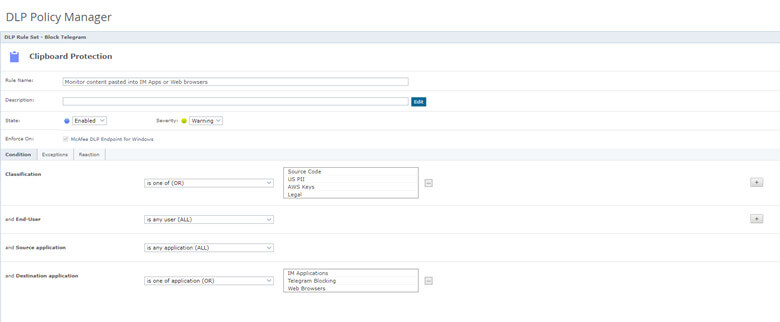
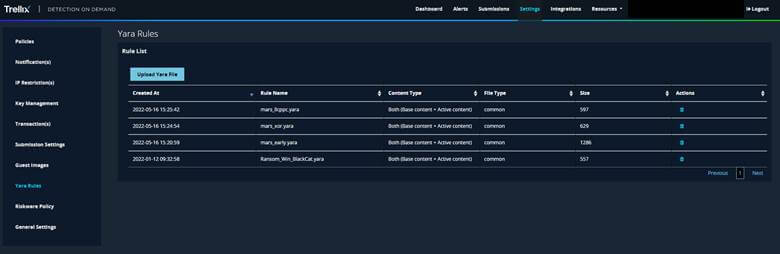
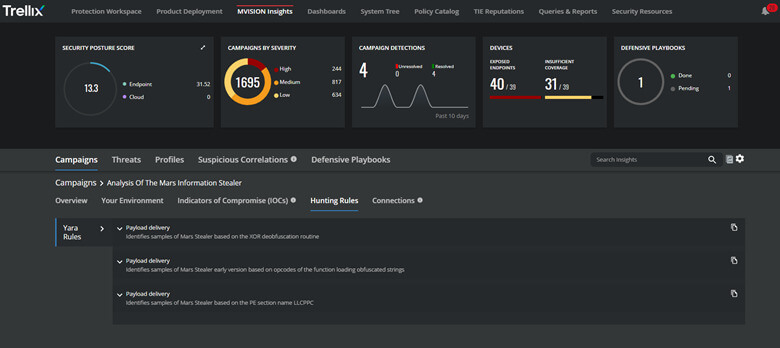
During the Attack – Incident Response Playbook to Mitigate Impact
Creating incident response playbooks to specific threat types is important so effective responses are utilized during an incident response.
For Information Stealers the below responses can help alleviate the damage and further spread of malware throughout your environment.
- Identify malicious networks connections and block domains/IPs to terminate Command and Control connections that transmit stolen credentials and data.
- Quarantine any device that has detection for information stealers or suspicious activity.
- Terminate running processes related to the attack.
- Immediately change or reset the password for all accounts used on the infected machine, including corporate VPN and email accounts, and other personal accounts even if the credentials are not stored locally.
- Execute full endpoint scans with high level threat sensitivity to detect files or malicious tools dropped by the adversary.
- Implement Incident Response policies to limit the spread of malware and further execution.
- Utilize Endpoint detection and response (EDR) solutions to detect lateral movement using stolen credentials.
- Investigate for evidence of persistence, often information stealers such as SolarMarker will leave .lnk files in the registry and startup folder to establish persistence.
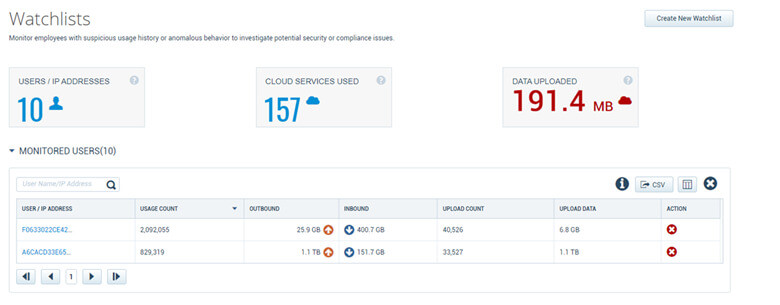
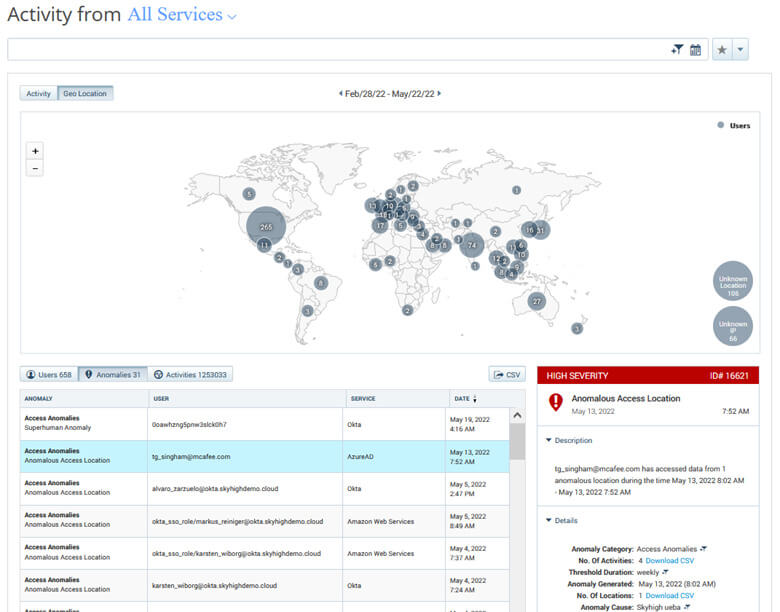
- Monitor user behavior analytics for unusual activity or access to your environment from unusual locations or unmanaged devices.
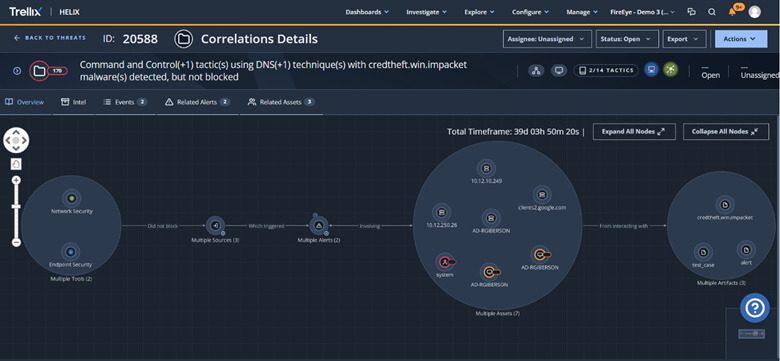
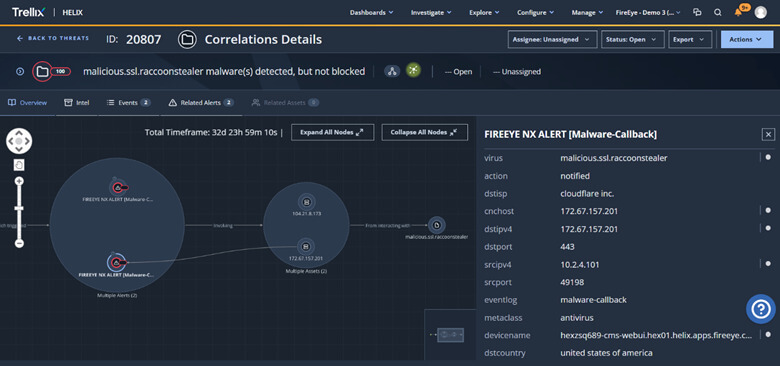
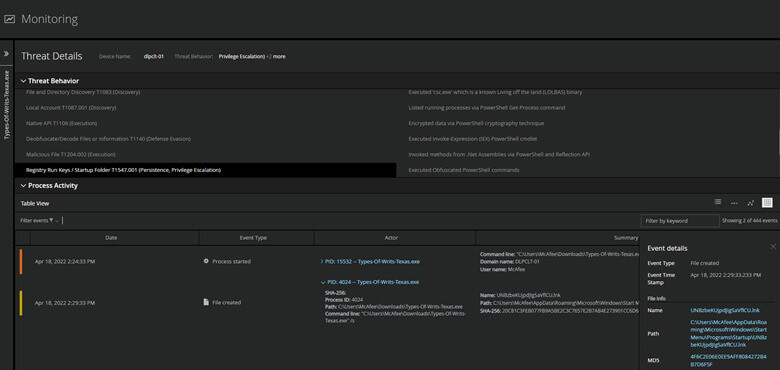
After the Attack – Returning to business levels while applying lessons learned
The Lessons Learned stage and return to normal business levels can sometimes be overlooked after an attack but identifying where improvement is needed is critical to prevent future attacks.
- Identify vector for initial access and review security controls to prevent future attacks.
- Return scheduled endpoint scans to their normal business levels.
- Continually monitor accounts across your environment for signs of compromise and attempts at credential stuffing or social engineering/phishing attacks.
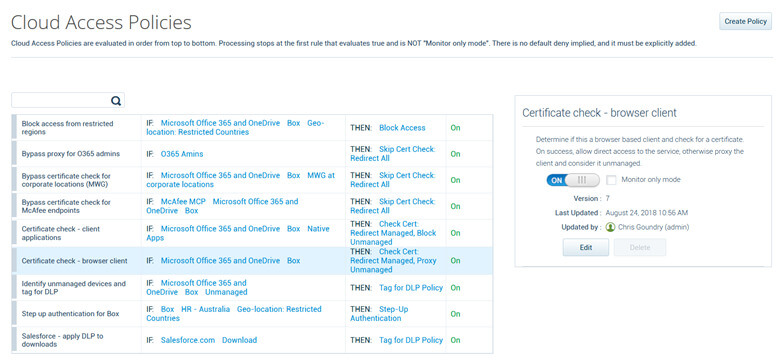
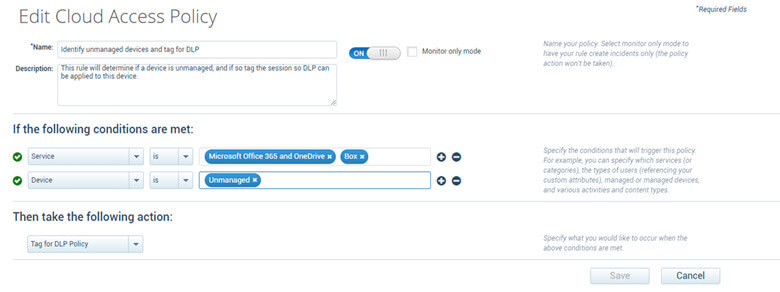
- If data loss occurred during an attack, review Data Loss Prevention policies to prevent future data exfiltration through successful vectors from the attack.
- Review visibility into events, adjusting log levels and sources can assist in reducing alert fatigue which can lead to overlooking of early indicators of infection and critical alerts.
- Implement Security Orchestration, Automation, and Response (SOAR) solution to automate incident response and reduce mean time to detect and respond with customized playbooks.
- Limit the access into your cloud accounts from unmanaged devices or suspicious locations, adding impacted users to watchlists can help with monitoring for non-business-related activity.
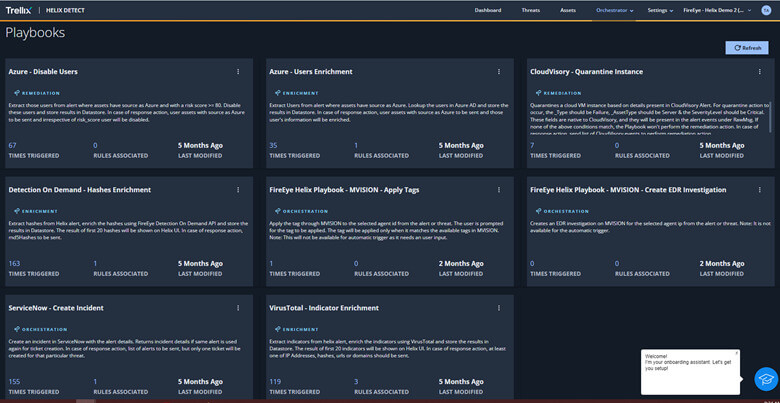
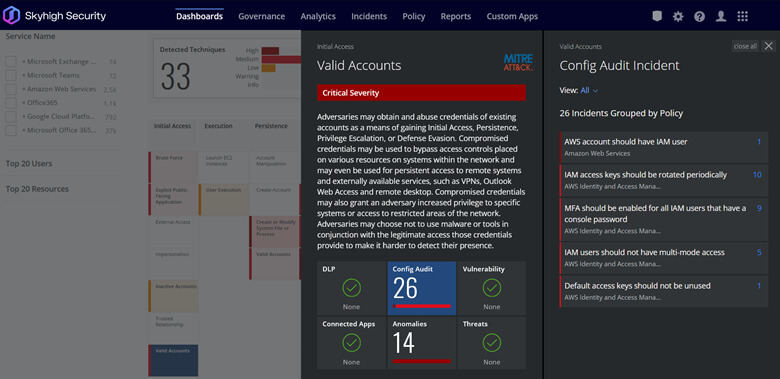
Additional Resources
Trellix Threat Labs Research Report: April 2022
Trellix Global Defenders: Invasion of the Information Snatchers - Protecting against RedLine Infostealer
Trellix Cyber Readiness Research
Understanding XDR: A Brief Glimpse Through the Lens of Enterprise Data
Skyhigh Security - Detect and Mitigate Threats
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.