Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Yanluowang Ransomware Leaks Analysis: Organization, Collaboration with HelloKitty, Babuk and Conti
By Jambul Tologonov· November 22, 2022
Introduction
On October 31, 2022, Yanluowang’s TOR site was hacked displaying a message “check and mate!! Yanluowang Matrix chat hacked @yanluowangleaks Time’s up!! :) you screwed!! Time’s up!”:
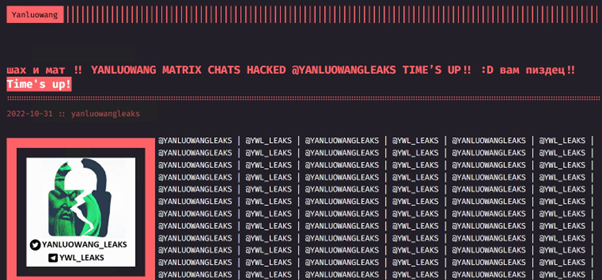
On the same day a Twitter handle @yanluowangleaks shared dumps of Yanluowang’s Matrix chat messages. We immediately downloaded the internal chat logs and began our investigation.
The name “Yanluowang” comes from Chinese mythology (Yanluo Wang is a Chinese deity), suggesting the ransomware gang is potentially of Chinese origin. However, all the communications in the leaked chats were in Russian language and it appears that the name was chosen deliberately to masquerade as a Chinese threat actor.
The ransomware group was first discovered by Symantec back in October 2021. Yanluowang has been used in human-operated, highly targeted attacks predominantly against Western enterprises such as Cisco, Walmart and others.
The recently leaked Yanluowang messages span from mid-January to September 2022 and include around 2.7K messages. However, from this relatively small dataset we have gained a valuable intel on Yanluowang threat actor, their innerworkings, victims and possible collaboration with other Russian ransomware groups. Further details are provided in the below sections.
Interesting chats
Gang’s organization
Based on internal chat messages, Saint seems to be the “boss” of the Yanluowang ransomware group and oversees payroll. In mid-February 2022 while instructing Killanas (aka coder0) on their new TOR infrastructure requirements and its design, he mentioned “Felix is a tester, I pay his salary for that”:
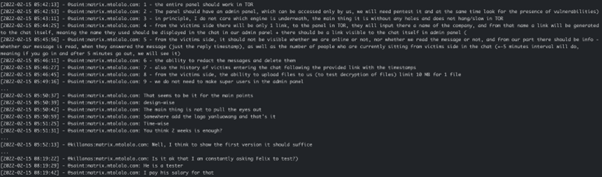
In a conversation with a pentester, Shoker, whom Saint tasked with testing their TOR admin panel, he advises “If you need to test something write here to Felix, coder of Win locker is coder0, (coder of) Nix/Win32 is Stealer.”
Coder0/Killanas seems to be the developer of a Windows ransomware locker and he has a team of coders. “Coder1 is the second developer of his (Killanas’s) team” says Stealer to the boss Saint. A potential identity of Killanas, who calls himself in the leaked chats ‘an InfoSec specialist’, was doxed at Doxbin[.]com by a handle Xander2727 as a “Lead developer of Yanluowang ransomware”:

According to Xander2727, this individual is a network administrator at Russian Federation Ministry of Defense. If one looks carefully at the doxed image in Figure 3, you can spot an emblem resembling the logo of Russian Ground Forces on the collar of a supposed military uniform.
The intelligence on the potential real identity of Killanas is not found in the Yanluowang leaked chats, therefore we cannot validate Xander2727’s claim nor have details on how they got to the person's identity.
Leader Saint appears to be behind the “sailormorgan32” moniker who in February 2021 claimed to hack SonicWall and receive 5 million USD from them:
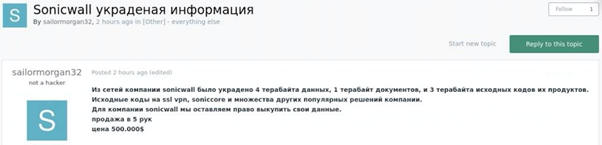
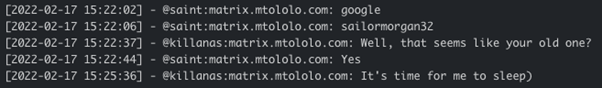
It appears Yanluowang hacked SonicWall itself in January 2021 prior to Conti trying to acquire SonicWall VPN appliance in March 2021 and exploit it:

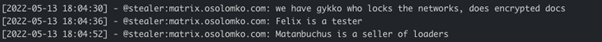
In mid-May 2022, Stealer, who is himself a developer of *Nix/Win32 Yanluowang locker, advises Guki (a new joiner of Yanluowang Matrix chat) they also have Gykko who locks victims’ networks and Matanbuchus who is the seller of Yanluowang’s loaders:
Possible collaboration with other ransomware families
Yanluowang-HelloKitty
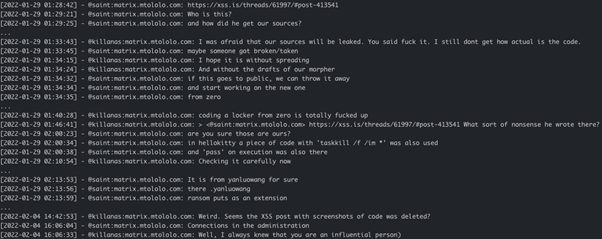
First hints of Yanluowang-HelloKitty collaboration date end of January 2022 when Saint shares a link to an XSS post where Yanluowang source code was posted with Killanas. While examining the leaked source code, Saint initially doubts if it is indeed Yanluowang’s code as “in HelloKitty a piece of code with 'taskkill /f /im *' was also used, as well as a 'pass' on execution.” However, after a careful analysis, they conclude that indeed that is the source code of Yanluowang as it adds an extension “.yanluowang” to the encrypted files. Later, Saint tells to Killanas via his connections with the administration he managed to have the related XSS post removed:
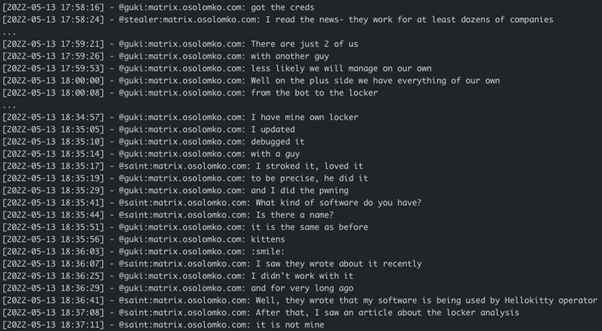
Guki who joined Yanluowang Matrix room chat in mid-May 2022 seems to be behind HelloKitty ransomware. In conversation with Saint, Guki mentions he’s got working credentials for at least dozens of companies, however there are only two of them on his team, and he is afraid they will not manage on their own to follow up on all those companies. Guki advises they have developed everything of their own, from bot to locker: the guy he works with is the developer and he himself does the ‘pwning’ (compromising the networks). When Saint asked him what software they use, Guki replied “the same as before, kittens”:
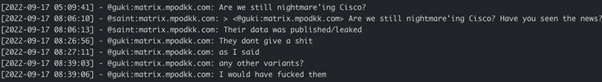
It appears that both threat actors were involved in Cisco compromise as later in September 2022 Saint advised Guki that their data was published on Yanlouwang’s data leak site:
Yanluowang-Babuk
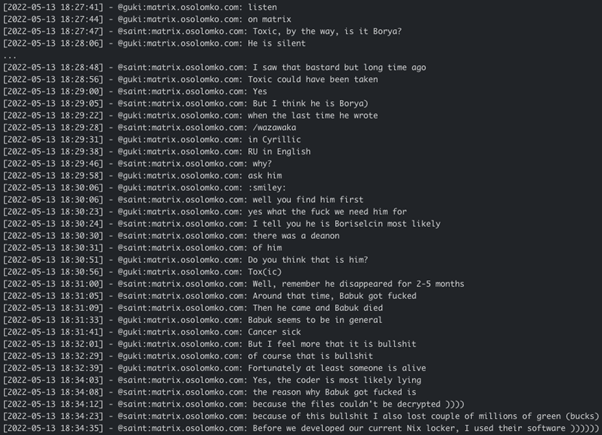
It seems that before Yanluowang developed their own Linux/Unix ransomware locker, they used a Linux locker from Babuk ransomware gang. In the below conversation between Saint and Guki, Saint implies that Babuk died because of the hacker Wazawaka’s (aka Boriselcin) return, and that Saint himself lost a couple of millions dollars due to Babuk locker not decrypting the files as it should:
Moreover, in February 2022, while discussing SentinelOne’s article on the evolution of the Evil Corp gang, where SentinelLabs attributed PayLoadBIN ransomware and a new, possibly experimental variant of it, dubbed Cypherpunk to EvilCorp, Saint mentioned that Cypherpunk is his profile name on Exploit forum and there was an effort to recruit hackers in forum where they used PayLoadBIN, and he is wondering why this activity was attributed to Evil Corp group:
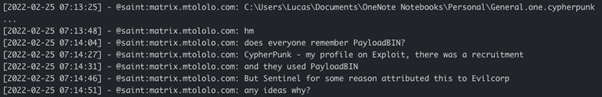
In April-May 2021 Babuk gang quit ransomware encryption and decided to focus on data-theft extortion. They renamed their data leak site to Payload[.]bin and one of the first leaks published on their site was a source code of a game Cyberpunk 2077, allegedly stolen by HelloKitty ransomware group. Having the similarities in naming, PayloadBIN < - > Payload[.]bin and Cypherpunk < - > Cyberpunk 2077, it is probable that Babuk/HelloKitty/Yanluowang gangs were behind this cluster of activity, and it potentially was misattributed to Evil Corp.
Yanluowang-Conti
It is interesting that Guki from HelloKitty ransomware was afraid that his name/moniker will appear in Conti-leaks and/or in the U.S. Department of State’s reward on Conti group members:
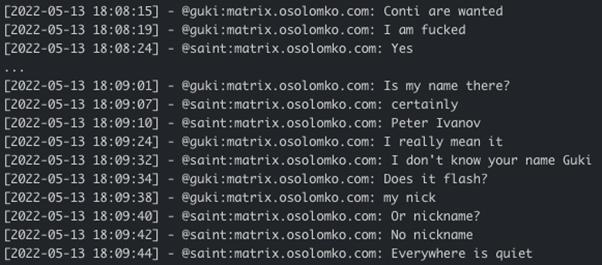
This indeed reinforces the hypothesis of Conti-HelloKitty ransomware groups being affiliated.
Furthermore, in March 2022, when Saint asked Killanas for his Bitcoin wallet, he gave the following BTC address: bc1q8svd69626nauxh2gvvyp8tndet8fntfph4jnz4. We have investigated the wallet and tracked the related transactions and managed to find a possible link to Conti ransomware BTC wallets:
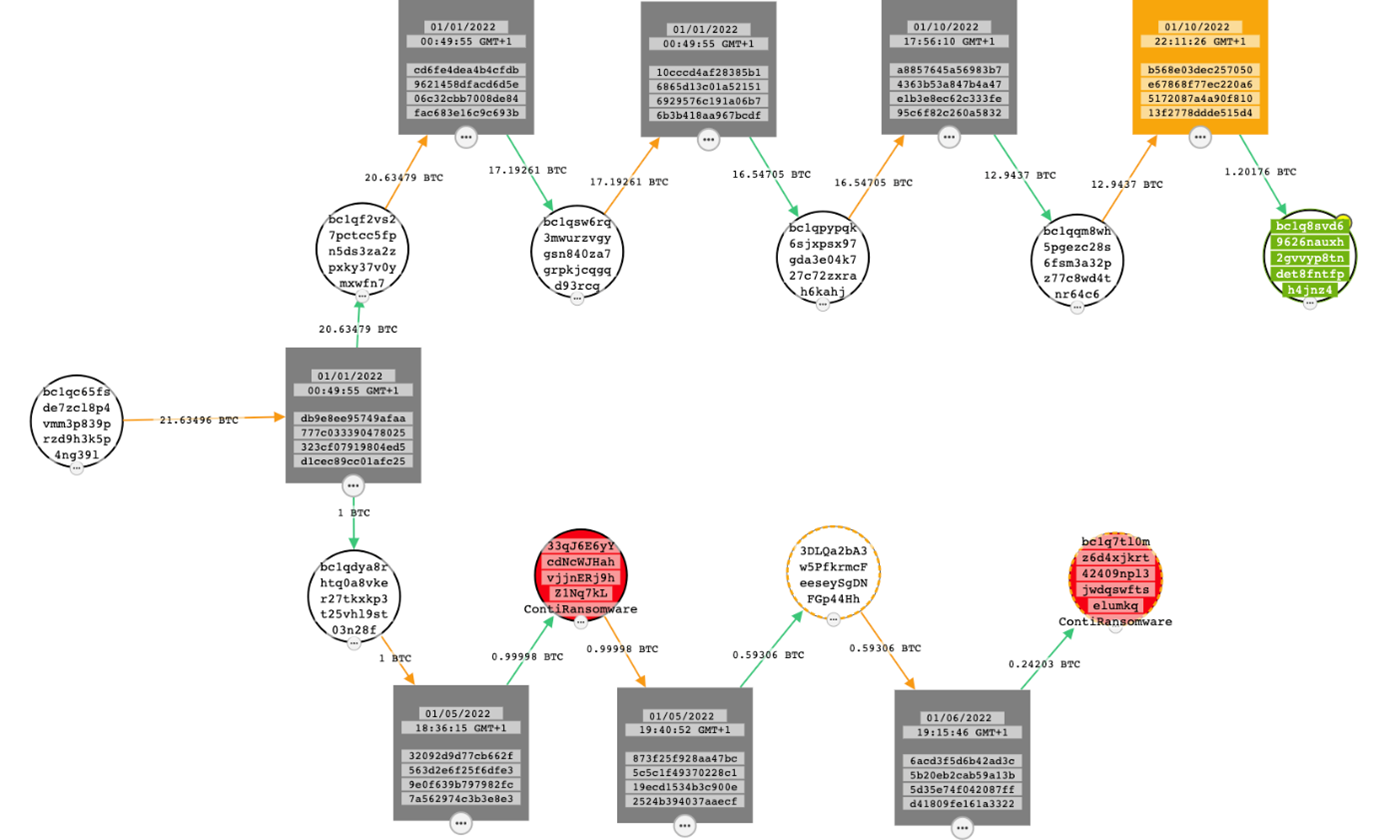
As can be seen from Figure 14, in the beginning of 2022 Conti received 1 BTC out of 21.6 BTC from the wallet bc1qc65fsde7zcl8p4vmm3p839przd9h3k5p4ng39l, and 10 days after Killanas received 1.2 BTC to his wallet from the remaining 20.6 BTC. When it comes to cashing out, the Conti and Yanluowang gangs seem to have similar schemes: BTC > Monero > Monero > cash via local exchange offices in large cities. Below is the excerpt of chat extracted from Conti-leaks in comparison with the chat logs from Yanluowang-leaks:
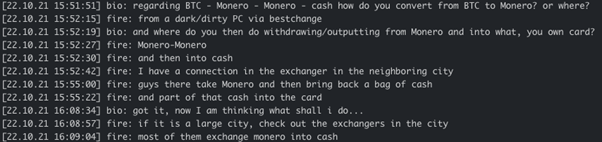
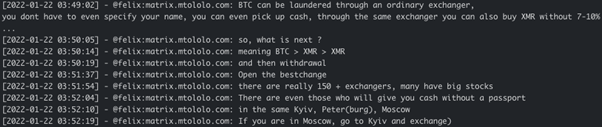
However, we also have observed some differences in Yanluowang’s money laundering scheme in comparison to Conti’s. Killanas seems to exchange BTC to QR codes via LockBit:
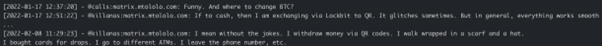
It is unclear from the leaked chats how Yanluowang members collaborate with the LockBit ransomware group. It is possible that LockBit provides cryptocurrency exchange services to certain cybercriminals where BTC can be cashed out via their QR codes.
Chinese of Ukrainian Origin
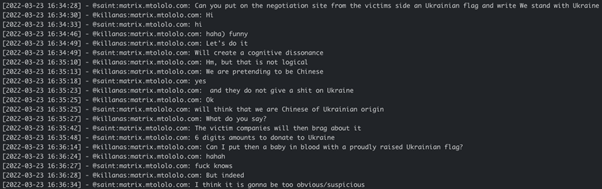
What’s interesting is that at some point Yanluowang wanted to place a Ukrainian flag and write “We stand with Ukraine” on their negotiation site to increase their chances of ransom being paid, however they were concerned it would blow up their Chinese actor cover story, so they decided to drop the idea:
Kaspersky’s Yanluowang decryptor
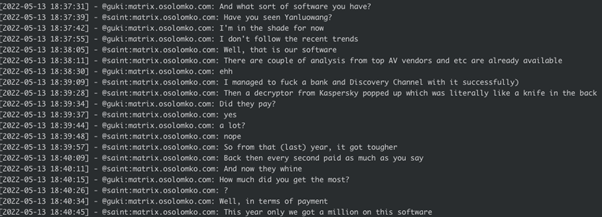
In April 2022 Kaspersky researchers found a vulnerability in Yanluowang’s encryption algorithm and created a free decryptor tool to help victims to recovery their files. According to Yanluowang boss Saint, this was “literally like a knife in the back” and made things difficult for Yanluowang. Nonetheless, within the first five months of 2022 Yanluowang ransomware managed to get one million (currency unknown) through use of their ransomware:
Conclusion
The analysis of Yanluowang internal chat messages provided us valuable insights on who is behind the ransomware group and what are their affiliates. It was fascinating to read their internal communications and find answers to attack’s which took place in the last two years.
This is the second largest internal chat leak from a Russian ransomware group following the leaks from Conti. The intelligence acquired from such data is extremely important as it sheds a light on how sophisticated Russian ransomware ecosystem is, how agile and adaptable threat actors are, and to what extend all these cybercriminal groups are linked to each other.
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
