Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Amazon GuardDuty Detected a Malicious Object on S3! What Now?
Automatically Detect, Investigate, and Respond to Malicious Objects in S3 with Amazon GuardDuty and Trellix Wise
By Martin Holste · August 6, 2024
Amazon GuardDuty was recently updated with an important new capability: The ability to detect malicious files written to S3. Why is this so important? S3 is used for many things, but one significant use case is the storage for files uploaded by customers in business applications. Accepting unknown input is always a security risk, and storing files uploaded by customers puts a burden on the app owner to prevent malicious files from entering the environment. Now with Amazon GuardDuty Malware Protection available, AWS has made it easy to turn on these protections.
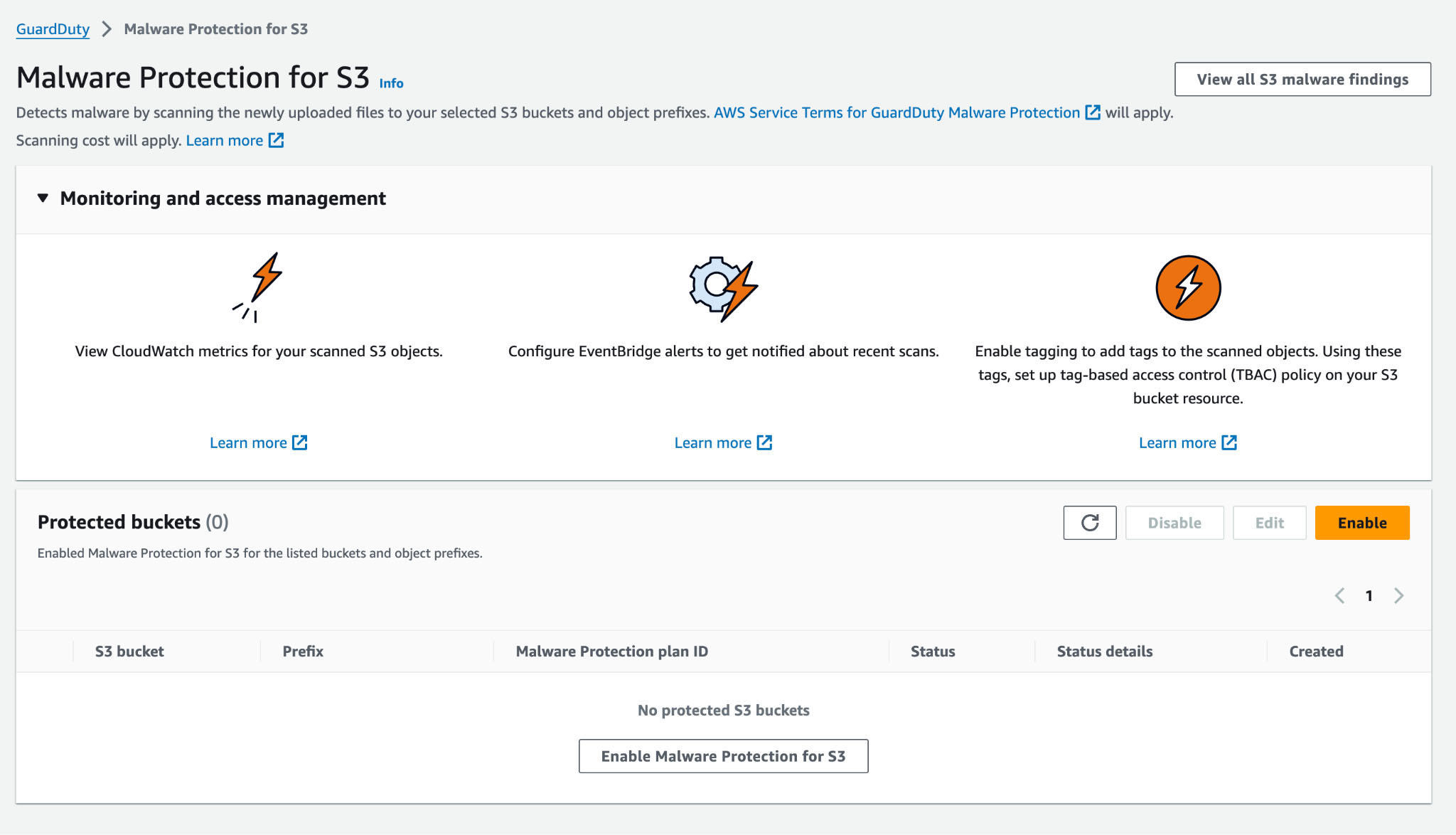
But a big question remains: How would you notice if Amazon GuardDuty detects something malicious, and what would you do next? In this post, we’ll illustrate how the partnership between Trellix and AWS makes the answer simple and effective by showing how the Amazon Bedrock-powered Trellix Wise automates the investigation and response.
How Trellix integrates with Amazon GuardDuty
You’re already familiar with Amazon GuardDuty, but what is Helix Connect? At Trellix, we believe in having an open XDR ecosystem in which Helix Connect, our platform for detection, investigation, and response is connected to all of the data sources that matter to our customers. In this case, that means Amazon GuardDuty.
The Helix Connect Integration Hub makes it easy to harness the synergy of AWS and Trellix. It will create a CloudFormation template that makes onboarding easy, safe, and repeatable across large enterprise cloud environments.
Using its connection from an AWS account’s default event bus via Amazon EventBridge, Helix Connect will receive Amazon GuardDuty events like this:
{
"version": "0",
"id": "72c7d362-737a-6dce-fc78-9e27a0171419",
"detail-type": "Amazon GuardDuty Malware Protection Object Scan Result",
"source": "aws.guardduty",
"account": "111122223333",
"time": "2024-02-28T01:01:01Z",
"region": "us-east-1",
"resources": [arn:aws:guardduty:us-east-1:111122223333:malware-protection-plan/b4c7f464ab3a4EXAMPLE],
"detail": {
"versionId": "1.0",
"scanStatus": "COMPLETED",
"resourceType": "S3_OBJECT",
"s3ObjectDetails": {
"bucketName": "DOC-EXAMPLE-BUCKET",
"objectKey": "resume.pdf",
"eTag": "ASIAI44QH8DHBEXAMPLE"
},
"scanResultDetails": {
"scanResultStatus": "THREATS_FOUND",
"threats": [
{
"name": "EICAR-Test-File (not a virus)"
}
]
}
}
}
Receiving an event like this initiates the auto investigation and remediation workstream in which the impact of the malicious object is scoped and remediation actions are identified.
Trellix IVX
Trellix boasts a rich history in sandbox technology from its FireEye heritage with over 30 patents on the world’s leading file forensics platform. This is a perfect complement to Amazon GuardDuty Malware Protection for S3, because it can describe all of the actions that a newly-discovered malicious object would take, if executed. These actions are described in an operating system change report “OS Change Report” that Trellix Wise in Helix Connect understands and can leverage. When Helix Connect receives a Amazon GuardDuty finding for S3, it can submit the offending object to Trellix IVX, then process the change report as a blueprint for an investigation.
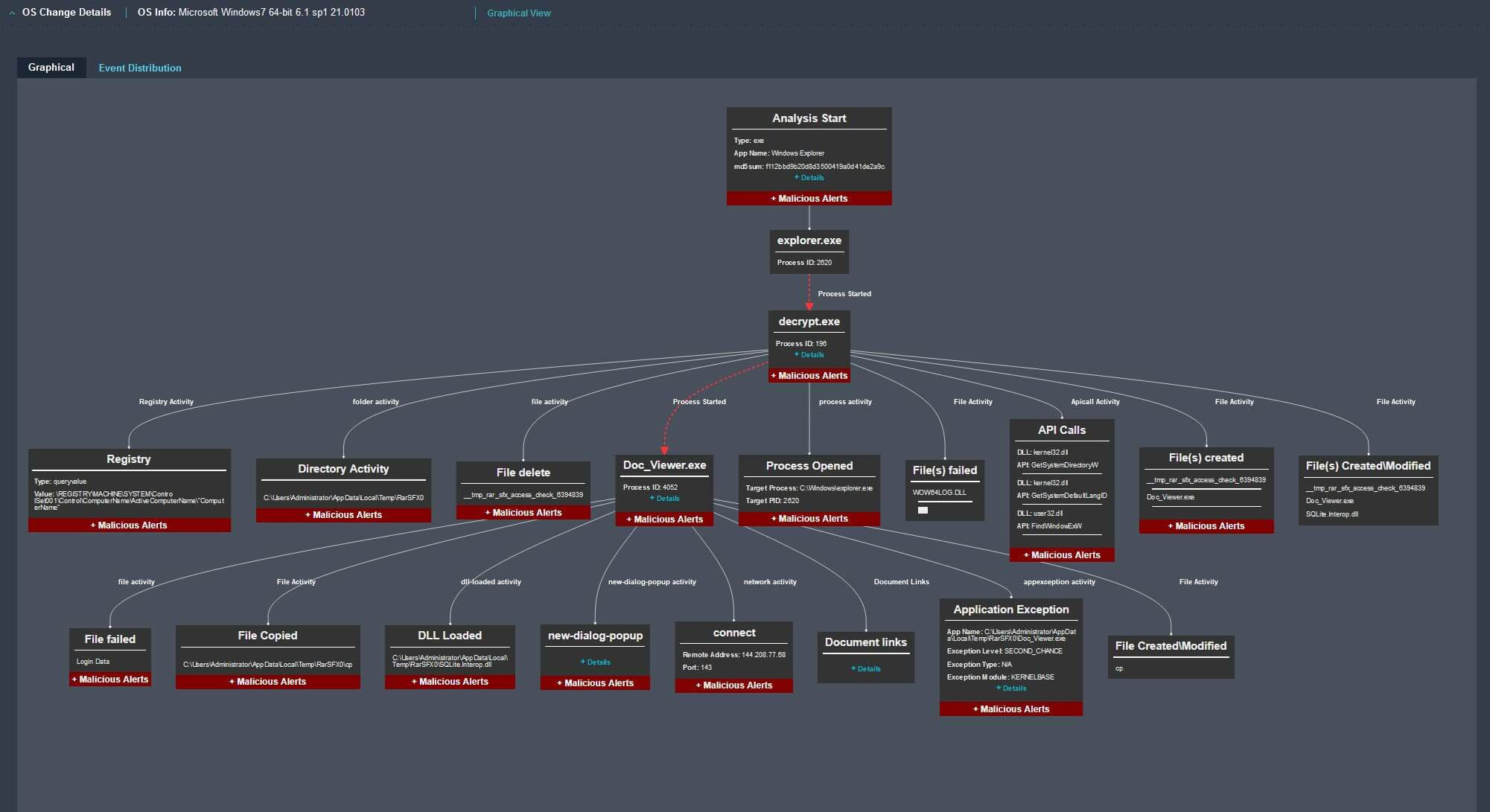
The example Amazon GuardDuty event shows a malicious hit for object resume.pdf in bucket DOC-EXAMPLE-BUCKET. Trellix Wise for Helix will get the Trellix IVX sandbox report and scour its indexed data lake for everything it knows about that object and the report, including who uploaded it, who downloaded it, has anyone accessed any command and control IP addresses or domains, and any other relevant host, network, or AWS information, and many other questions. These questions are created by the Trellix Advanced Research Center (ARC), and the answers are automatically interpreted by the Amazon Bedrock-powered Trellix Wise.
In the diagram below, you can see the complete process: Amazon GuardDuty will detect malicious files and Trellix Helix Connect will be notified via a connector. It will invoke the Trellix Intelligent Virtual Execution (IVX) sandbox which will determine exactly what the malicious file would do. The output is then sent back to Helix Connect, which will use Trellix Wise generative AI to determine if anyone has executed the sample by using the sandbox report to see if it applies to any activity in the environment.
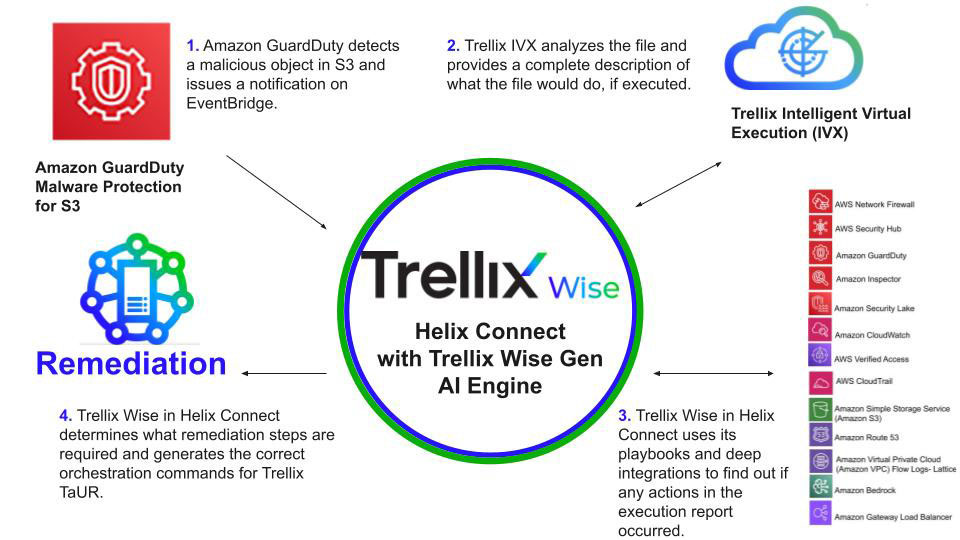
Finally, Trellix Wise will determine what remediation actions are required, and if configured, automatically quarantine objects, hosts, create firewall rules, disable users, or any other of the hundreds of actions possible with Trellix Automated Response (TaUR).
The Trellix Wise plugin for Helix Connect is now available to all Helix Connect customers!
- Watch Our Latest Webinar: See the Trellix Wise plugin in action and gain valuable insights on our latest webinar.
- Attend a Trellix & AWS XDR Dev Day: Don't miss out on an in-depth, hands-on experience. Register now for one of our upcoming Virtual Dev Days!
Enhance your security capabilities and take advantage of these opportunities today!
To explore further possibilities with AWS and Trellix, contact us at AWS@Trellix.com or visit us at Trellix.com.
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
