Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Building Blocks of Protection: Key Elements for a Robust XDR Solution
By Kathy Trahan · June 21, 2023
Imagine being able to integrate, automate, and coordinate all your security efforts within a single platform. This is the promise of an Extended Detection and Response (XDR) solution, where proactive defense against multi-vector attacks is the name of the game. From detection to response, there's a lot that goes into an effective XDR solution. But what are the essential cyberthreat defense tools and components that can bring an effective XDR solution to life? Let's explore the critical XDR elements that are redefining the cybersecurity landscape.
The Critical Vectors for an Effective XDR Solution
Overall, adopting an XDR solution can strengthen an organization's cybersecurity posture, making it more resilient to potential threats that likely traverse across many vectors. To understand how we can leverage XDR to achieve our cyber resiliency goals, let us first examine how XDR solutions collect and correlate data from multiple security layers to detect, investigate, and remediate multi-vector threats more efficiently. Specifically, why endpoint protection, email security, network security, and identity and access management security are critical vectors that improve the effectiveness of an XDR solution. And how threat data feed sources from these areas contribute to a more comprehensive and efficient XDR solution. Away we go!

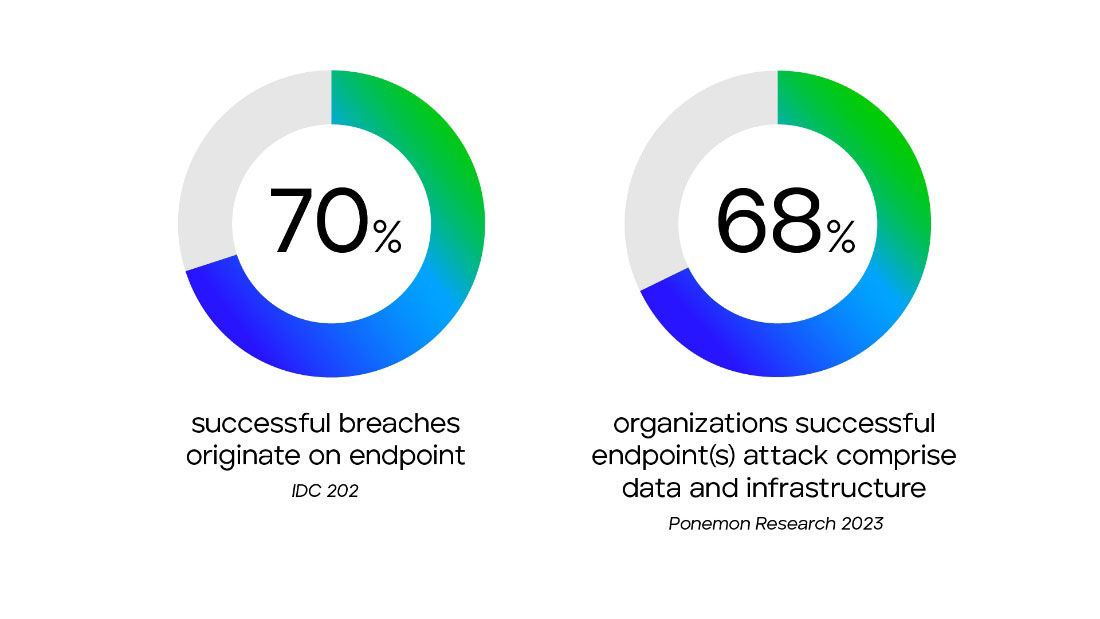
Endpoint Protection (EPP/EDR) is a must-have technology for an effective XDR solution, since endpoints are most often the ultimate target for cybercriminals trying to obtain valuable datasets, like PII, credentials, intellectual property, data theft, etc. They do this with increasingly sophisticated attacks that result in malware or ransomware, which can cost an organization millions of dollars in response, remediation, business down time, and even regulatory fines. In fact, it is predicted every 11 seconds, there will be a successful cyber or ransomware attack, with the damage costs to reach over $20 billion1. The financial ramifications of an endpoint-targeted attack are severe, but these attacks are also widespread. According to a 2021 report, 68% of organizations experienced an endpoint attack that compromised data or IT infrastructure.2 Not only is endpoint a key target, but because if the widespread and mobile nature of an organization’s endpoint footprint, the potential financial opportunity for a cybercriminal is that much larger. By integrating endpoint protection data into the XDR platform, organizations can gain deeper insights into potential threats, detect anomalies, and respond faster and more effectively to security incidents. Because of all this there is a natural and obvious linkage between EDR and XDR. An intelligent XDR solution that seamlessly integrates with a robust endpoint protection can help deliver a more robust security posture for the entire organization.
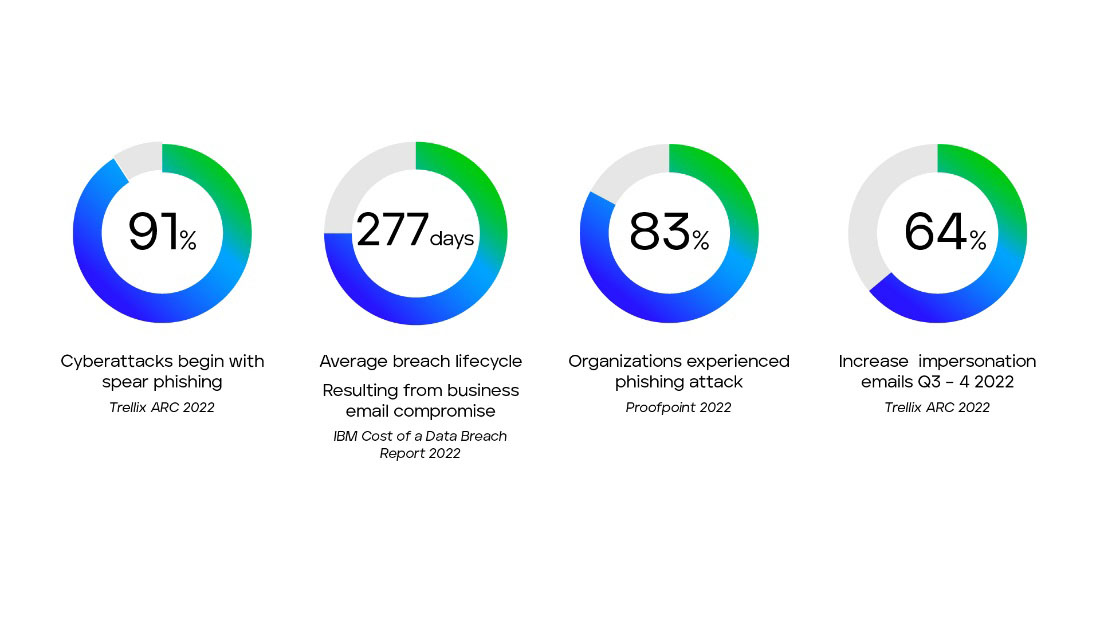
Email continues to be the #1 attack vector for cybercriminals, making email security a vital component of any comprehensive XDR solution. According to the 2020 Verizon Data Breach Investigations Report, 94% of malware was delivered via email. And the average breach cycle is 277 days for business email compromises. This gives the adversary plenty of time to do damage. If your organization’s data (residing on the endpoint) is the ultimate target you want to protect, it might be best to start by locking the door through which the attackers are entering – email. By incorporating email security data feeds into the XDR platform, organizations can detect and respond to threats such as phishing attacks, malware, and business email compromise at the outset of an attack. But to do this, you need tight integration between your email and XDR threat intelligence systems to combat the constant barrage of email-based attacks. The integration of email security data with other security layers ensures that the XDR solution can identify and remediate threats before they can be the cause of significant financial/monetary damage.
https://cybersecurityventures.com/cybercrime-damage-costs-10-trillion-by-2025/ 50 Endpoint Security Stats You Should Know In 2023 We’ve collated the latest endpoint security statistics to help you keep up to date on one of the most important security topics facing the modern workplace https://expertinsights.com/insights/50-endpoint-security-stats-you-should-know/#:~:text=According%20to%20a%20study%20by,increased%20since%20the%20year%20before. IBM Cost of a Data Breach Report 2022
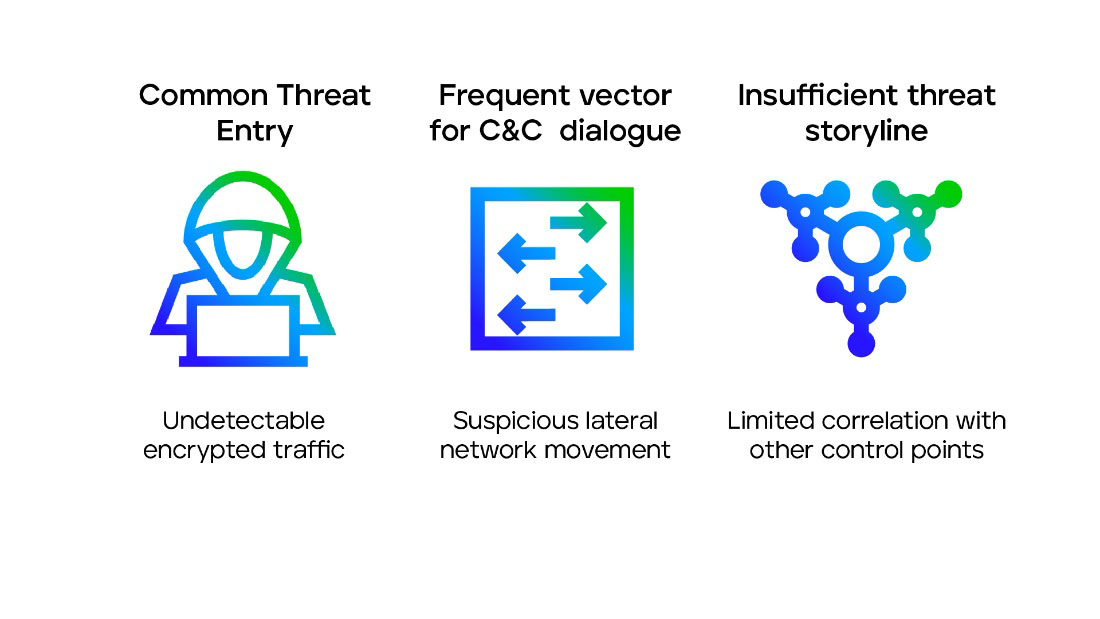
. Network security is another essential aspect of a comprehensive XDR solution. A 2021 study found that 43% of data breaches involved web application vulnerabilities, emphasizing the importance of network security. It is also a frequent vector used for the adversary to provide command and control dialogue during an attack. For this reason, network-based threat intelligence is critical to both preempting threats and stopping attacks once they have begun, to prevent further spread. By incorporating network security data feeds, an XDR solution can monitor traffic patterns, detect anomalous behavior, and identify potential threats that may bypass other security layers. This enables the XDR platform to provide a more in-depth analysis of the organization's network security posture and improve overall threat detection and response capabilities.
Home » Security Bloggers Network » 43% of Data Breaches Connected to Application Vulnerabilities: Assessing the AppSec Implications
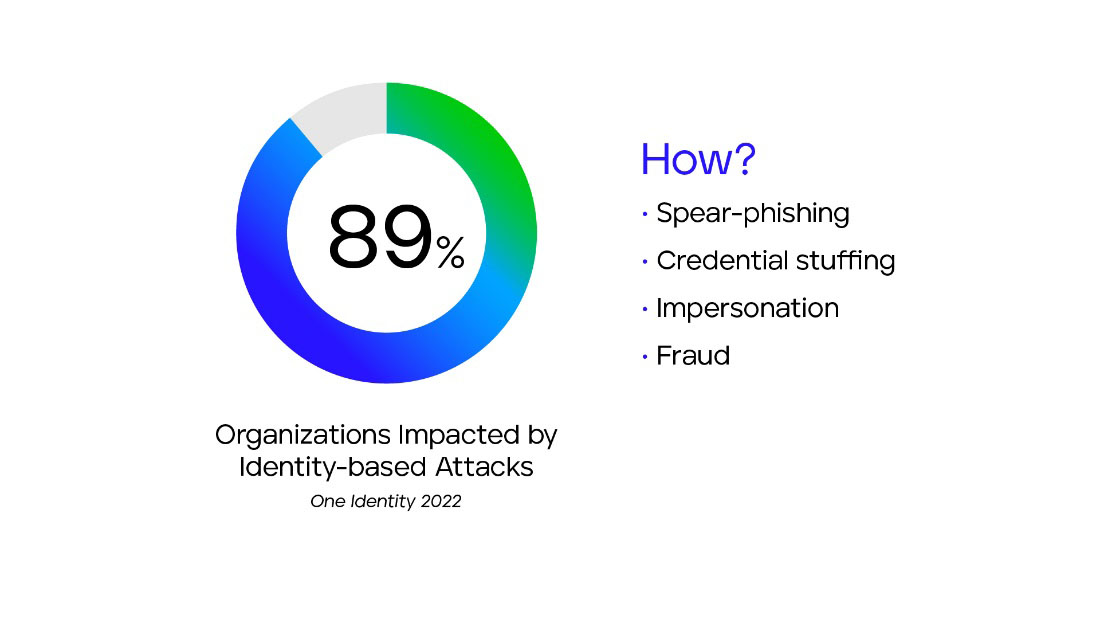
Identity and access management (IAM) security plays a critical role in securing an organization's digital assets by controlling user access and privileges. According to a 2021 survey, 89% of organizations have experienced an IAM-related security incident. Likewise, the increase in spear phishing, credential stuffing and impersonations continues. As a result, many organizations are adopting “Zero-Trust” models that advocate robust identity security controls. By inserting IAM security telemetry into the XDR platform’s defense, organizations can gain greater insight into user activities and detect suspicious behavior that may signal unauthorized access or potential insider threats. By integrating identity information into XDR, critical user context is weighed in to drive more comprehensive security coverage and helps to prevent unauthorized access to sensitive data.
The Identity Defined Security Alliance (IDSA), a nonprofit that provides vendor-neutral resources to help organizations reduce the risk of a breach by combining identity and security strategies, today unveiled its 2022 Trends in Securing Digital Identities report, based on an online survey of over 500 identity and security professionals
Integrating Threat Intelligence (TI) for a more comprehensive XDR solution
So, we’ve established that the efficiency and comprehensiveness of an XDR solution can be greatly improved by leveraging multiple threat data feed sources and integrating various security technologies. By unifying various security controls, XDR solutions can offer a more comprehensive view of an organization's security landscape, but also leverage the individual parts to strengthen the entire security fabric as a whole. The glue that ties an effective XDR solution all together is advanced threat intelligence and analytics. Advanced threat intelligence help to better analyze threat patterns and predict future attacks and can ultimately help to better deliver the desired security outcomes for your organization. A 2020 survey by Security Week revealed that organizations using advanced threat intelligence experienced a reduction in attack dwell time from 24 days to 21 days (six years earlier dwell time was 205 days.) By integrating advanced threat intelligence along with automated analysis and response, your XDR solution can identify patterns, trends, and emerging threats, enabling your security operations teams to proactively respond to potential attacks. Additionally, integrating threat intelligence allows for greater visibility and contextualization of threats, improving the accuracy of threat detection and reducing false positives (which are a major sink for SOC operators and threat analysts)
The promise of XDR solutions is not delivered unless you are detecting attacks on the most prominent targets (endpoints) and defending the most entered pathways for cyberattacks (email). To achieve your security posture goals, the system needs to integrate data from multiple security functions and sources to detect and respond to threats effectively. The more data feeds and threat vector detectors incorporated into an XDR solution, the more efficient and comprehensive the solution becomes--making the entire organization it is protecting safer.
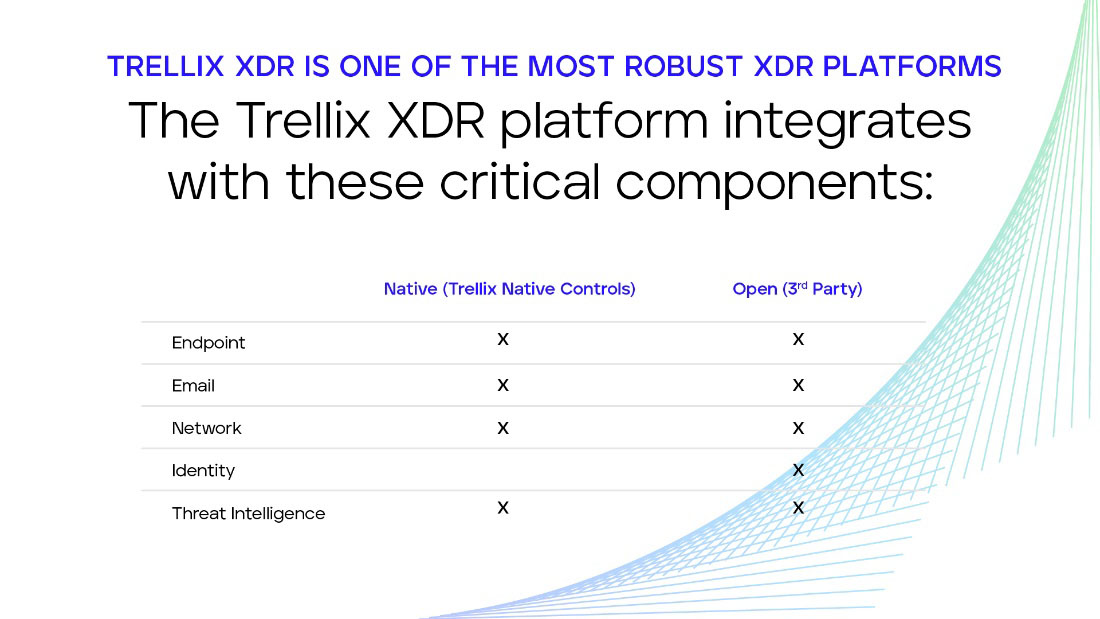
Comprehensive and time-tested. Trellix has a proven track record of over 4 years of integrating over 1000 data sources. Trellix has a solid credible reputation of understanding the essential telemetry and control points required for XDR. Clearly not everyone can claim this!
Disclaimer: This document and the information contained herein describes computer security research for educational purposes only and the convenience of Trellix customers.
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
