ARCHIVED STORY
Sharing is Caring: FireEye Helix Connects to Netskope to Block Threats
By Christopher Unick, Mahmoud Eraqi · July 14, 2021
FireEye Helix is a SaaS security operations platform that allows organizations to take control of any incident from detection to response and remediation. We introduced Helix in 2017 to simplify, integrate and automate security operations, and along the way we made many enhancements and introduced various features to improve the user experience.
Today we are excited to announce a new integration that customers of Helix and Netskope can leverage to block threats between our products. This expands on our previous integration—ingesting data from Netskope into Helix to identify threats—by closing the loop to help customers of Netskope block threats that are found anywhere in their suite of security and business tools.
Finding Threats With Helix
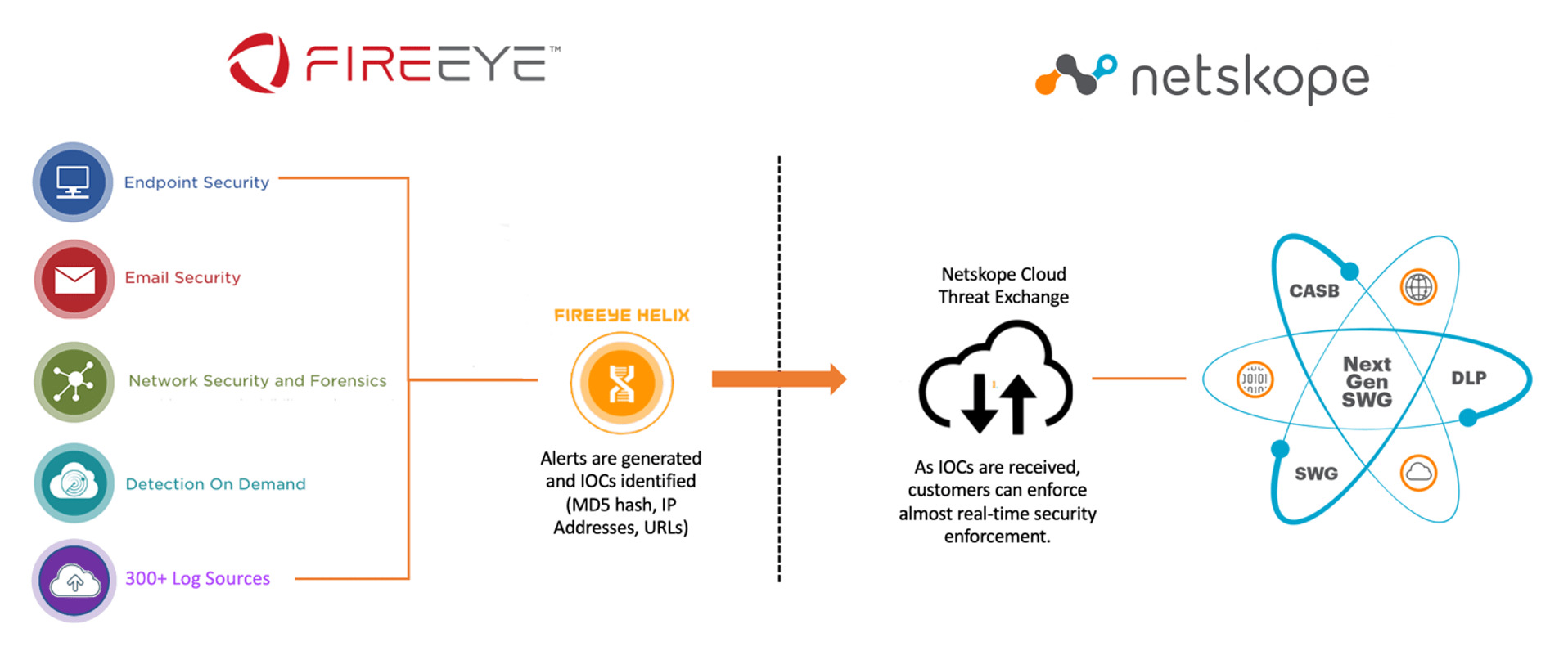
It is imperative that security teams have visibility into what's happening across the business so they can respond to and investigate security incidents. FireEye Helix is able to analyze events in over 300 security and business tools and is enriched with FireEye expertise to identify the threats happening in an organization.
The good news is the median dwell time is currently 24 days (per M-Trends 2021), meaning organizations are identifying threats more than twice as fast as in 2020. These improvements in detection are very important, and organizations must ensure their response is just as quick. This integration allows those threats to be shared with Netskope in mere minutes to block threats seen throughout the business.
FireEye Helix alerts on and shares the following alerts (and many more) with Netskope:
- Malware on the endpoint: MD5 Hash will be identified when FireEye Endpoint Security discovers malware on a customer’s endpoint.
- Files containing ransomware: Identify malicious content (MD5 hash) shared via email, found on endpoints and more.
- Malware callback alerts: Network activity (malicious IP address) that matches a malware command and control (C2) signature.
- Third party content: Malicious files (MD5 Hash) being shared to you by third parties or suppliers (via cloud storage like AWS S3 and 30+ others).
- Malicious IPs and URLs from log files: Ingesting logs from our partners (like Netskope) that find malicious activity and share the corresponding IOCs.
Netskope Cloud Threat Exchange (CTE)
Netskope Cloud Threat Exchange is a near real-time threat ingestion, curation, and sharing tool that enables Netskope customers and FireEye to exchange IOCs. Security teams can integrate IOCs that contain malicious URLs and file hashes from any Helix source, including FireEye Endpoint Security, Network Security and Email Security tools, third-party firewalls, cloud logs, and secure web-gateways.
Mutual customers of this integration can:
- Ingest, manage and share all IOCs seen in a customer’s environment.
- Leverage FireEye’s industry leading detection capabilities.
- Ensure all users and devices are protected with up-to-date indicators.
- Respond faster and block threats across a customer’s ecosystem.
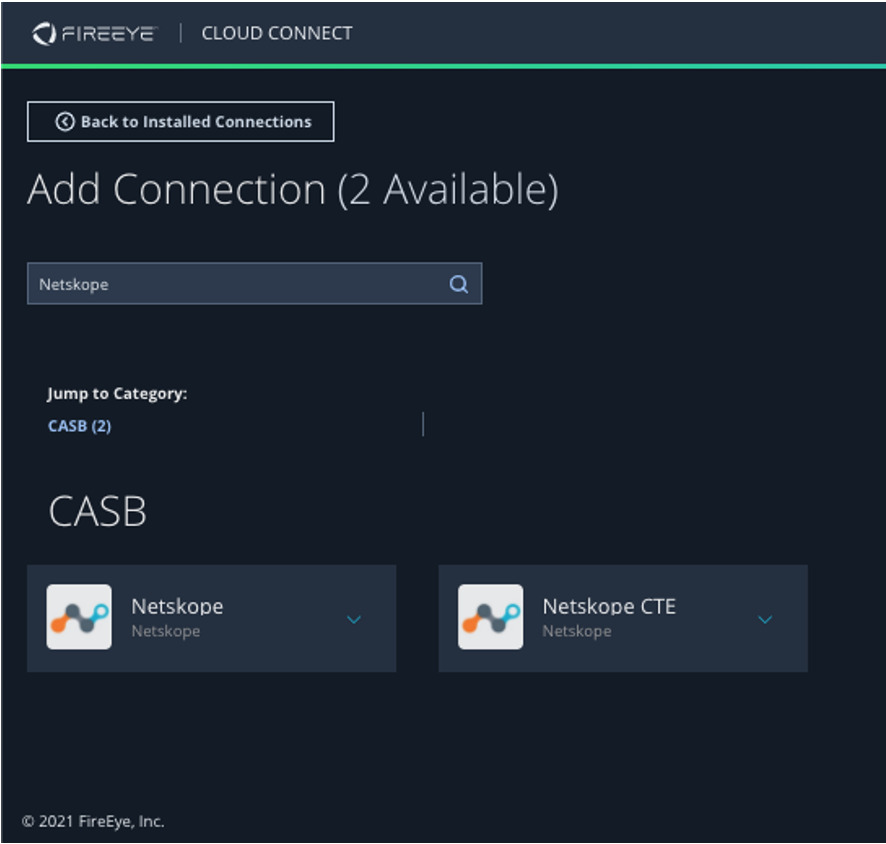
How to Enable This Integration in Minutes
Navigate to the FireEye Helix CloudConnect portal and select Netskope CTE.
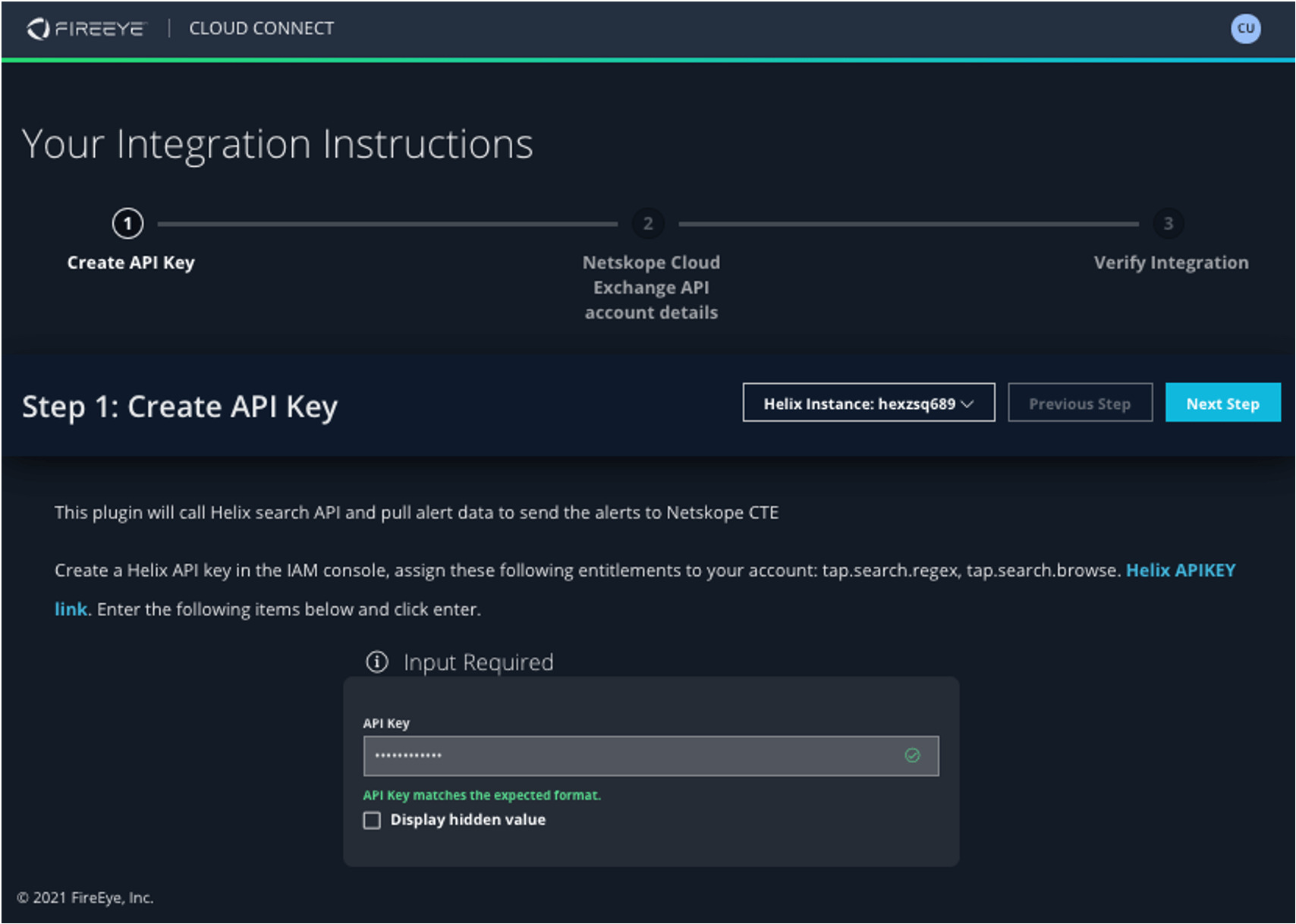
Select your FireEye Helix Instance and drop in your API Key (found in your IAM setup).
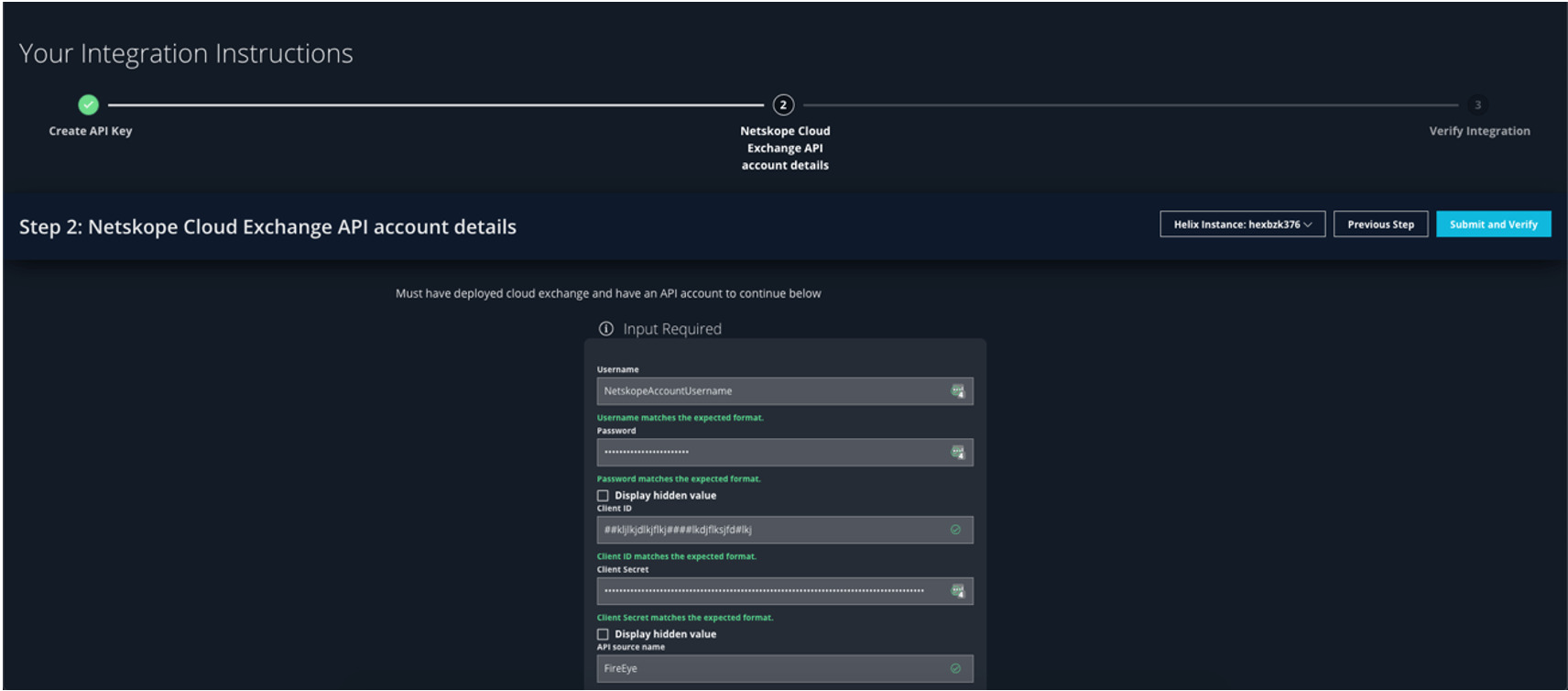
Fill in your Netskope credentials to enable the integration, and you are all set!
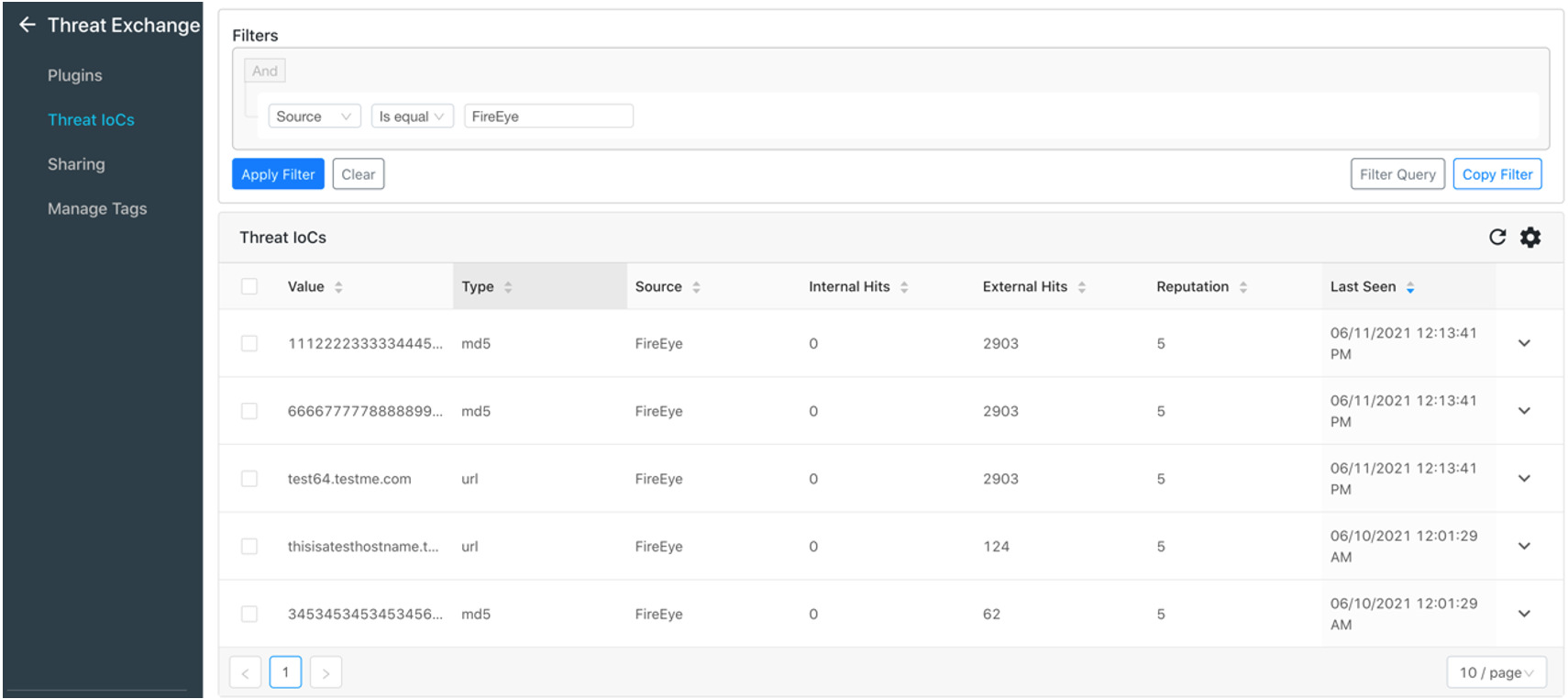
As you navigate to the Netskope CTE dashboard, you’ll see IOCs that are shared from Helix that will actively block/restrict items based on your configuration in your Netskope solution.
Ready to get started? Connect with us today to see a demo and to learn more. Already using Helix, but not familiar with the latest integrations available? Reach out to your sales engineer to get more information and a walkthrough of how we can help!
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.