Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Lateral Movement the Silent Spread: Use Case and Mitigating the Risk
By Shay Appelboim · October 2, 2023
Lateral Movement is a technique to spread an attack around the organization systems while maintaining persistent control over them. Adversaries use lateral movement to get a wide position to make sure they will stay longer in the network and continue running under the radar until they can move to their next step of the attack.
The objective is to propagate through various systems, ensuring sustained unauthorized access and enhancing their foothold. Adversaries exploit lateral movement to broaden their scope within the network, which helps in evading detection and facilitating prolonged unauthorized presence. This process is often a preparatory phase that paves the way for subsequent attack stages.
Although malware and human attackers may employ diverse methodologies, their objectives during the infiltration phase are often aligned. Upon compromising an initial system, their aim typically involves mapping the network topology, extracting valuable information, and acquiring additional credentials. By leveraging the lateral movement technique, adversaries can effectively compromise multiple systems, deploy their malicious payloads, and persistently operate undetected by unsuspecting users.
Moreover, attackers often exploit legitimate administrative tools and known system vulnerabilities for lateral movement. Tools such as PowerShell, WMI, PsExec (Living off the land tools), or existing susceptibilities in operating systems and authentic applications can be manipulated. This not only enables easier propagation across remote systems but also challenges cyber defense teams, as these activities may camouflage themselves amidst regular network operations.
An apt analogy for this technique is the behavior of ant colonies. Starting from a single point of penetration, ants systematically extend their influence, creating an intricate network, similar to how an attacker infiltrates and expands control within a target system.
Reasons to protect against lateral movement
Every organization, equipped with critical assets like customer databases, financial records, and intellectual property, stands vulnerable to adversaries who often see these as primary targets.
To counteract this vulnerability, many organizations are emphasizing the prevention of lateral movement. This strategy serves dual purposes:
First, it acts as a containment measure, ensuring that even if an adversary does compromise one system, their malicious reach is confined to that point, preventing widespread damage across the network.
Secondly, it is a cost-efficient approach. Containing a breach to a single system is far less resource-intensive than addressing multiple compromised systems, saving organizations from both direct repair costs and indirect repercussions like reputational loss, diminishing customer trust, and potential regulatory fines.
Moreover, this focus on preventing lateral movement underscores an organization's proactive defense posture, signaling to would-be attackers that the entity is both vigilant and prepared, thereby acting as a potential deterrent.
Furthermore, by nipping this lateral movement in the bud, companies safeguard their operational continuity, ensuring that disruptions do not ripple across departments, thereby preserving productivity and consistent revenue flows.
Methods to protect against lateral movement
Protection begins with comprehension. Recognize that lateral movement follows the primary infiltration. An adversary typically gains a foothold through techniques like phishing, exploiting zero-day or unpatched vulnerabilities, or deploying malware. This is the way to understand the Attack Lifecycle.
- Defensive Layering: Do not rely solely on a single line of defense. Multi-layered security measures, starting from perimeter defense to internal monitoring, can dramatically reduce the risks associated with lateral movement.
- Internal Network Segmentation: Implement network segmentation to restrict communications within subnets. Most end-user systems do not need to communicate directly with one another; they typically interact with servers. By limiting communication inside the subnet, you can impede an adversary's ability to move laterally.
- Robust Firewall Configurations: Firewalls between subnets are crucial. Ensure they are appropriately configured to block unnecessary or suspicious activities. This not only protects against external threats but also checks and controls internal communications, which can be crucial during a lateral movement.
- Endpoint Protection Solutions: Utilize advanced endpoint protection solutions like Trellix Endpoint Security. These tools can be configured to block communications between systems in the same subnet or across different subnets, offering granular control and heightened protection against lateral movement attempts.
By understanding the intricacies of lateral movement and implementing these protective measures, organizations can significantly bolster their defenses, ensuring that potential adversaries find it exceedingly challenging to navigate and exploit their networks.
How to block lateral movement with Trellix Endpoint Security (ENS)
All unnecessary communication between systems in a subnet can be blocked and only the necessary protocol/port/application can be open to communication, as needed.
To block communication in the local subnet we need to create a rule in the Trellix ENS Firewall.
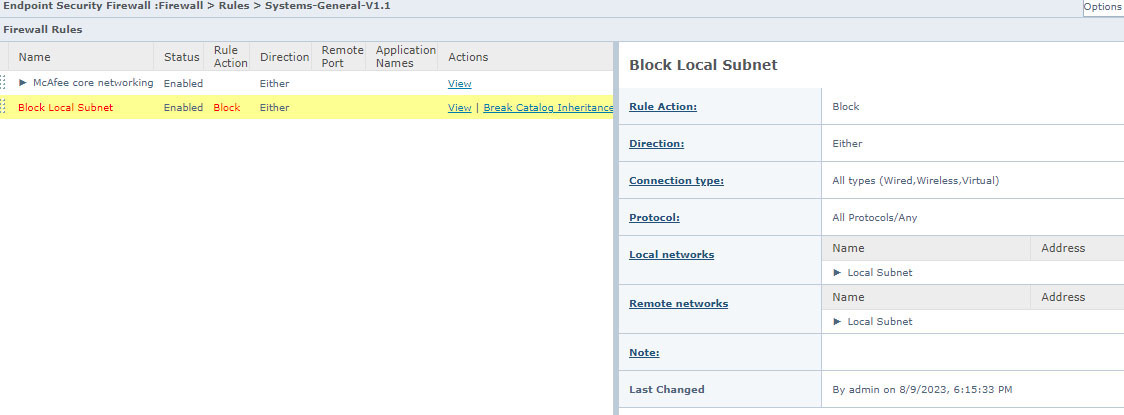
To create the rule:
- In ePO, Go to Policy Catalog-> Endpoint Security Firewall -> Rules
- Create a new policy or edit an existing one
- Click “Add Rule”
- Write a Name
- Mark “Enable rule”
- Actions: mark “Block”
- Direction “Either”
- Mark “Any Protocol”
- Connection Type mark all
- Specify networks:
- Click Add (local)
- Write a name
- Click on “Add IP Address” and choose “Local subnet”
- Click Save
- Click Add (Remote)
- Write a name
- Click on “Add IP Address” and choose “Local subnet”
- Click Save
- Click Save
To block between systems in different subnets, configure the subnet in the “Specify network” (Step10).
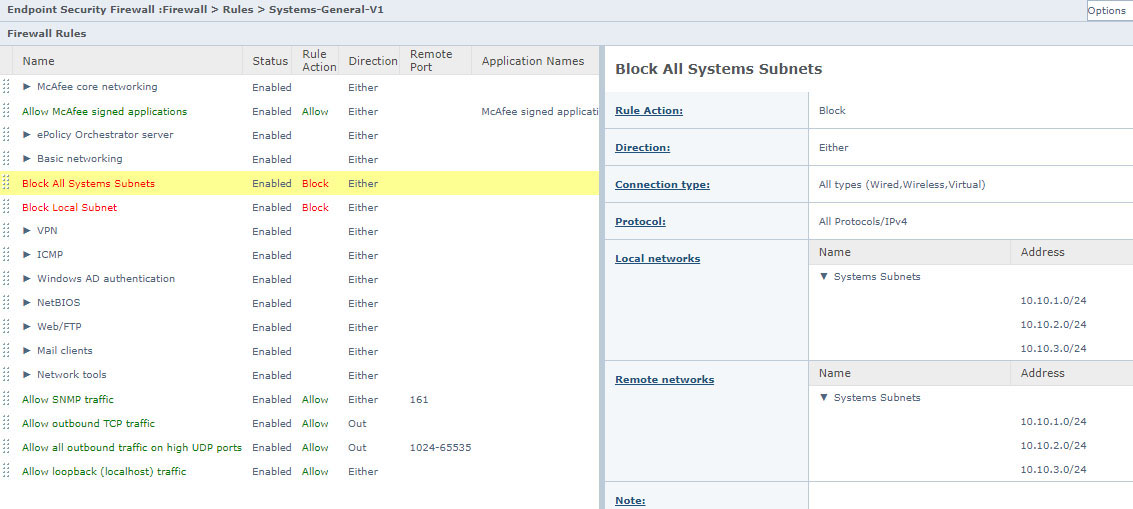
IMPORTANT:
Before applying any new or modified policy across the organization, any changes to the ENS must first be tested on a sample group that accurately represents the organization.
Conclusion
In an era of increasing cyber threats, understanding and mitigating lateral movement has emerged as a paramount concern. Are you unsure about the readiness of your organization against lateral movement threats? Do not leave your organization's safety to chance. Equip yourself with the right tools and guidance. Let our team help you on this journey. Contact the Trellix Sales team for more information about how Professional Services can help.
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
