Trellix leverages Amazon GuardDuty Malware Protection for Extended Detection and Response (XDR)
By Christopher Unick · July 26, 2022
Welcome to the new normal in cybersecurity—where every organization must go beyond mere prevention. To achieve resiliency against threats, customers must be able to monitor their environments in real time and address incidents the moment they arise. Trellix Helix analyzes telemetry from a customer’s security and business tools, leverages machine learning and advanced analytics to detect anomalies and empowers customers to respond to issues. This is eXtended Detection and Response (XDR). Trellix is at the forefront of the XDR revolution —pioneering a brand-new way to bring detection, response, and remediation together in a single living security solution. The Trellix XDR platform seamlessly integrates with our broad portfolio of endpoint, email, network, cloud, and an additional 650+ products. Today we are excited to announce our newest AWS integration with Amazon GuardDuty’s new Malware Protection, bringing Trellix to 9 critical AWS integrations that help drive key visibility across a customer’s cloud infrastructure.

What is Amazon GuardDuty?
Amazon GuardDuty is a threat detection service that continuously monitors your AWS accounts and workloads for malicious activity and delivers detailed security findings for visibility and remediation. These include use of compromised credentials, simplified forensics and continuous monitoring of all security events seen in an AWS customers environment. With the announcement of new Malware Production, GuardDuty will scan EBS-backed EC2 instances with malicious behavior based on GuardDuty’s existing findings and report malware detected on EC2 and containers running on EC2 and instantly send data to Trellix Helix.
How can GuardDuty and Helix help my security operations?
Mutual customers can leverage any of the 9 integrations between Trellix Helix and AWS to gain visibility in mere minutes by ingesting metadata from AWS. This data is then enriched with threat intelligence and evaluated with behavior analysis and machine learning to prioritize those alerts that are most actionable.
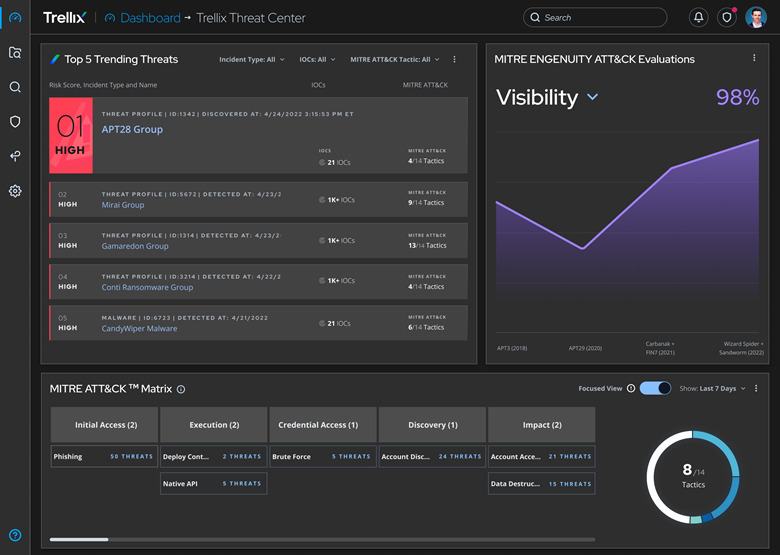
Trellix Helix provides investigate content and rules against AWS data, helping security analysts understand the security event faster. This new integration with Amazon GuardDuty events would help assist a security investigation, like a known malicious source IP address or known ransomware, as key context from AWS would be automatically added to a threat that Trellix Helix identifies.
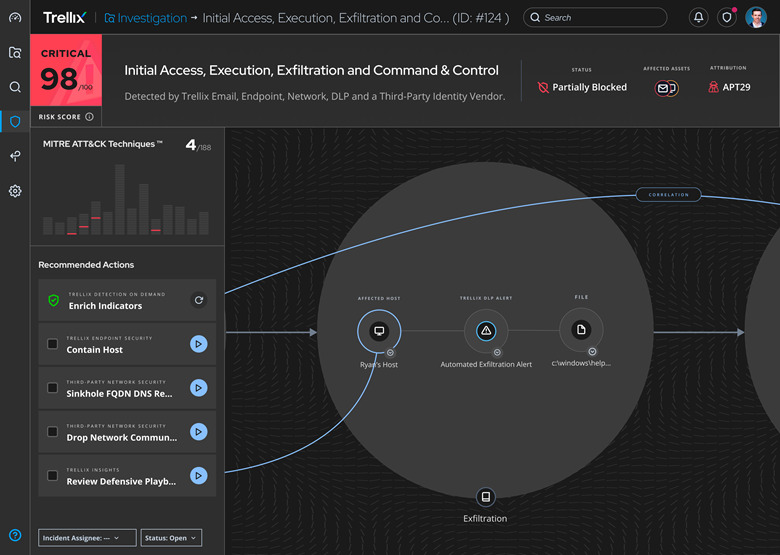
The holistic view of the incident then drives the response to any known issues, such as quarantining an endpoint with Trellix Endpoint Security, automatically blocking traffic with Trellix Network Security or one of 100’s of automated playbooks that are available for security teams to use today.
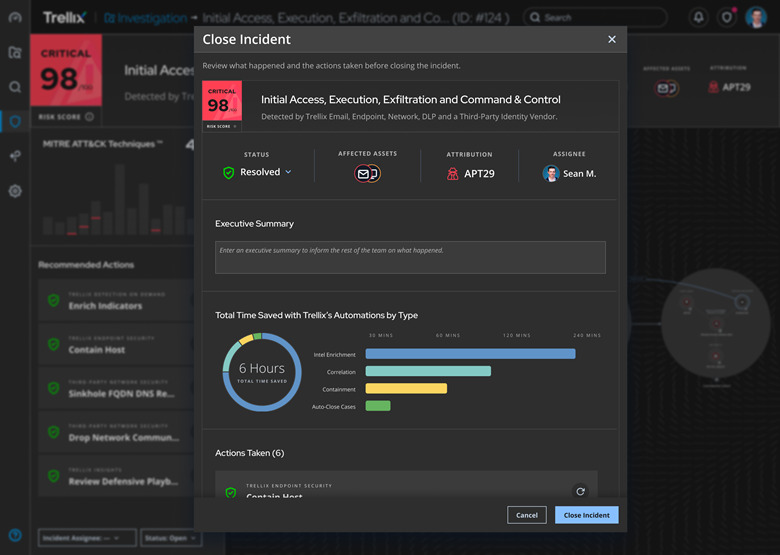
This fulfills the promise of XDR, by allowing customers to identify and respond to threats faster, saving them hours of time researching and correlating data.
Start leveraging the speed and efficiency used between Amazon GuardDuty and Trellix Helix to respond to security issues today. Please reach out to AWS@Trellix.com to learn more or join our latest XDR workshop to get hands-on with Trellix today!
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.