Quiet the XDR noise and take a proactive approach
By Kathy Trahan · January 19, 2022
XDR (extended detection and response) continues to be a technical acronym thrown around in the cybersecurity industry, and it comes with many promises. Every security vendor has an XDR song to sing, but many miss a beat or are out of tune because XDR is still an emerging market.
This abundance of information can be frustrating for security professionals who are heads down defending against persistent threats. In this blog, we’ll sift through the noise and clarify XDR so you can understand the relevant information and make informed cybersecurity decisions.
What is XDR?
Let’s begin by defining XDR. It promises to consolidate multiple products into a cohesive, unified security incident detection and response platform, and is the next evolution of endpoint detection and response (EDR). “Extended” refers to going beyond the endpoint to network and cloud infrastructure. This cross-infrastructure or cross-domain capability is the common denominator for XDR.
But is XDR a solution to purchase or a security strategy approach to adopt? Many vendors are announcing XDR products or capabilities to buy. But to fully realize the benefits of the technology, organizations will need to move to an XDR ecosystem that shifts processes and encourages tighter coordination between different functions and roles, like SOC analysts, hunters, incident responders, and IT administrators.
According to Gartner, XDR is “a SaaS-based, vendor-specific, security threat detection and incident response tool that natively integrates multiple security products into a cohesive security operations system that unifies all licensed components.” Gartner notes three primary requirements of an XDR system: centralization of normalized data primarily focused on the XDR vendor’s ecosystem, correlation of security data and alerts into incidents, and centralized incident response capability that can change the state of individual security products as part of incident response or security policy setting.
ESG defines XDR as an integrated suite of security products spanning hybrid IT architectures, designed to interoperate and coordinate on threat prevention, detection, and response. In other words, XDR unifies control points, security telemetry, analytics, and operations into one enterprise system. The cross-vector analytics must be enhanced to track advanced multistage attacks, and implementation guidance such as reference architecture is needed to assure successful integrated workflows.
Forrester views XDR as a next generation of EDR that will integrate endpoint, network, and application telemetry. Integration can be native when it’s with one vendor’s portfolio, or hybrid when a vendor integrates with other security vendors. Key goals include empowering analysts with incident-driven analytics for root cause analysis, offering prescriptive remediation with the ability to orchestrate it, and mapping use cases using MITRE ATT&CK techniques and chaining them into complex queries that describe behaviors instead of individual events.
XDR themes
A common XDR theme is multiple security functions, integrated and curated data, and control vectors working together to achieve better security operational efficiency while responding to a threat. The emphasis is on removing complexity and offering better detection and understanding of the risk in the environment to identify a response more quickly.
The range of detect and response capabilities suggests that it can’t be achieved by one exclusive vendor. Many security professionals advocate for an integrated partnership approach to unify defenses and streamline efforts across domains and vectors. That’s a more realistic method since most organizations don’t fulfill their entire security function with one vendor. While buying an XDR suite that includes most of the needed tools can be easier, some critical security functions from another vendor should be included to drive more effective detect and response.
While many vendors claim to have fully unified and integrated XDR, you must carefully look under the hood. They may have a unified view in a single console. But has data from all separate vectors been automatically assessed and triaged, and has the system provided meaningful and actionable next steps?
Another XDR theme is accelerating investigation efforts by offering automatic analysis of findings and incidents to constantly improve assessment. Increasing the speed of investigations is critical and could potentially decrease the frequency of your reactive cycles.
A final key theme of XDR is threat prioritization. This function helps you determine which threats are high priority based on factors like whether a threat is impacting assets with highly sensitive data and your organization’s industry and location.
Who is XDR for?
XDR can work for any organization, but realizing XDR’s SOC efficiency benefits is dependent on the organization’s current cybersecurity maturity and readiness to embrace the processes required. However, the promise to correlate data across the entire enterprise means some of the manual effort to make sense of data and create a better and actionable understanding of a threat is removed—a benefit for organizations of all maturity levels.
Less mature organizations that don’t have resources or expertise and don’t consume data intelligence will appreciate this correlation and investigation step. Medium to high maturity cybersecurity organizations with expertise won’t need to do manual work to make sense of data, so the difference for them comes with the next steps of further investigating and deciding on remediation. This is the biggest impact point: helping more mature organizations move quickly to respond to a potential threat or threat in progress.
XDR functions
The core functions of XDR all focus on improving security operations during an attack, which make XDR a reactive approach. They include:
| Core XDR functions | Benefits |
|---|---|
| Coverage across infrastructure/vectors | Get comprehensive visibility and control across your entire organization and stop operating in silos Reduce disparate efforts between tools, data, and functional areas . |
| Distilled data and correlated alerts across the organization | Eliminate manual discovery and make sense of your data |
| Unified management with a common experience | Improve response time and accuracy with a common view that removes jumping between consoles and data pools |
| Automatic exchange of data and triggering of actions | Automate security functions like detection and response |
Beyond the basics, leading solutions like Trellix XDR offer features that can help organizations stay one step ahead of threats, such as:
| Advanced XDR functions | Benefits |
|---|---|
| Actionable intelligence on potentially relevant threats | Harden your environment proactively before an attack |
| Rich context that includes threat intelligence and organizational impact insight | Prioritize your threat remediation efforts |
| Security working together with minimal effort | Create a united front and optimize security investments |
Key Outcomes
The endgame of XDR is better security operational efficiencies. This can be expressed in an outcomes checklist that’s helpful when assessing XDR providers:
| Visibility | Control |
|---|---|
| More accurate detection | More accurate prevention. |
| Better adaptability to changing technologies and infrastructure | Better adaptability to changing technologies and infrastructure |
| Fewer blind spots | Fewer gaps. |
| Faster time to detect or mean time to detect (MTTD) | Faster time to remediate or mean time to respond (MTTR) |
| Better views and searchability | More prioritized hardening across portfolio—not isolated efforts |
| Faster and more accurate investigations (fewer false positives) | Better control across the entire IT infrastructure |
Take a proactive approach with Trellix XDR
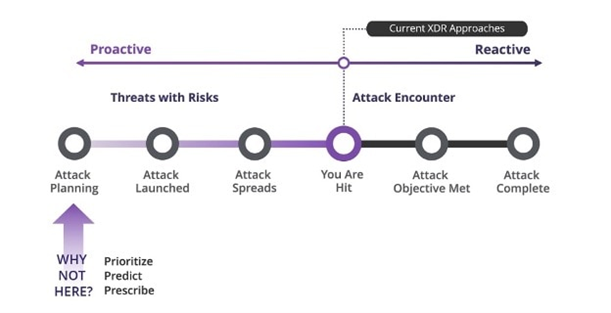
Trellix XDR delivers living security to help organizations stay one step ahead of adversaries, adapt to new threats, and accelerate detection and correction. This security ecosystem goes beyond basic XDR capabilities and focuses on proactively predicting and prioritizing threats instead of just reacting after an attack. This means your SOC spends less time on error-prone fire drills with weeks of investigation and can respond faster to protect your organization.
Ready to find out how Trellix can help you transform your security and become a more resilient, confident, and agile organization?
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.