
Trellix Global Defenders: LAPSUS$ Data Breaches and Proactive Protections
By Taylor Mullins · March 23, 2022
Trellix is continuing to monitor the threat activity related to the LAPSUS$ threat group and their recent breaches of large organizations such as NVIDIA, Samsung, Microsoft, and Okta. This monitoring is being done from a threat landscape view and the security posture of our own internal environment. As we learn more information about these breaches, we will continue to keep our customers informed on how they can proactively protect their infrastructure.
Background on LAPSUS$ Threat Group and their Attack Techniques
Currently a lot is still unknown about the LAPSUS$ group and the entry point they are using for initial access into each of these organizations but one technique that has been noted is their recruitment of insiders within large organizations to provide their credentials. LAPSUS$ also has a strong focus on the Cloud environments of the large corporations, successfully leveraging misconfigured systems.
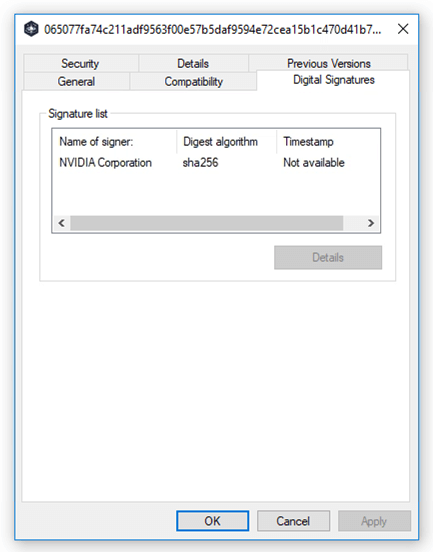
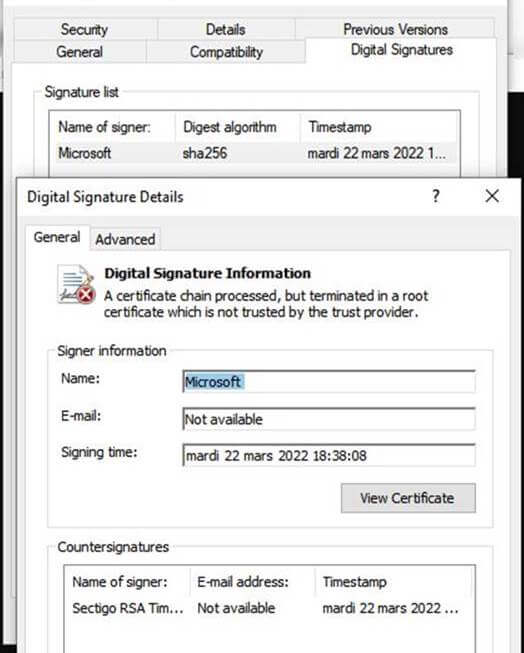
Along with the exfiltration of data, the exploitation of stolen certificates from the Microsoft and NVIDIA breaches have been observed in attacks using tools such as QuasarRAT. QuasarRAT is an open-source, remote access tool that is publicly available on GitHub, some of the recent attacks using this tool have been seen using the stolen certificates from the NVIDIA attack by LAPSUS$. While both stolen NVIDIA certificates were expired, Windows will still allow a driver signed with the expired certificates to be loaded in the operating system. The using of these stolen certificates gives the threat actors an advantage by making their programs look like legitimate NVIDIA programs and allowing malicious drivers to be loaded by Windows.
Recommended Mitigations to Proactively Protect Against Data Breaches
As noted above many of the Tactics, Techniques, and Procedures (TTPs) for LAPSUS$ are still unknown, but there are steps that can be taken to harden your environment and monitor for data exfiltration.
- Cookies should be deleted after every browser session to prevent Cookie Hijacking, a technique LAPSUS$ also used to bypass MFA
- Utilizing two-factor authentication across the board to mitigate against credential theft
- Perform audits or scans of systems, permissions, insecure software, insecure configurations, etc. to identify potential weaknesses
- Proactive monitoring of accounts for anomaly activities
- Encrypt Sensitive Information
- Auditing of data access and what roles can access sensitive files and directories
- Hardening of Data Protection policies against sensitive data being exfiltrated along with the movement of large amounts of data to external cloud services
LAPSUS$ Threat Intelligence from the Trellix Advanced Threat Research Team and MVISION Insights
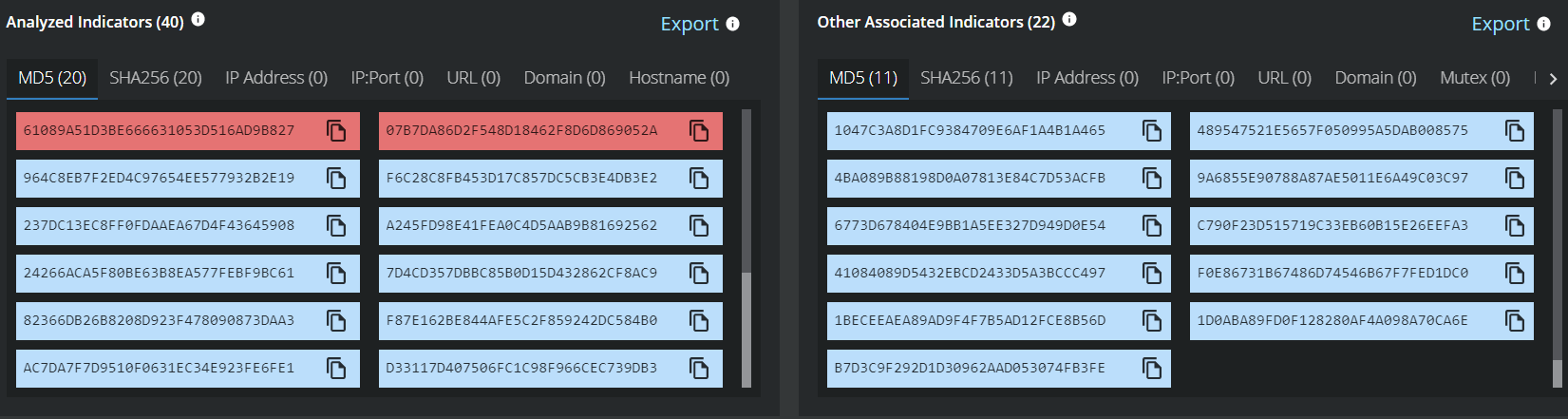
MVISION Insights will provide the current threat intelligence and known indicators for the LAPSUS$ threat group. MVISION Insights will also alert to detections and process traces that have been observed in your environment and systems that require additional attention to prevent widespread infection. MVISION Insights will also include Hunting Rules for threat hunting and further intelligence gathering of the threat activity as it is being discovered.
Campaign Names - LAPSUS$ Intelligence update and Malware Using NVIDIA's Stolen Code Signing Certificates
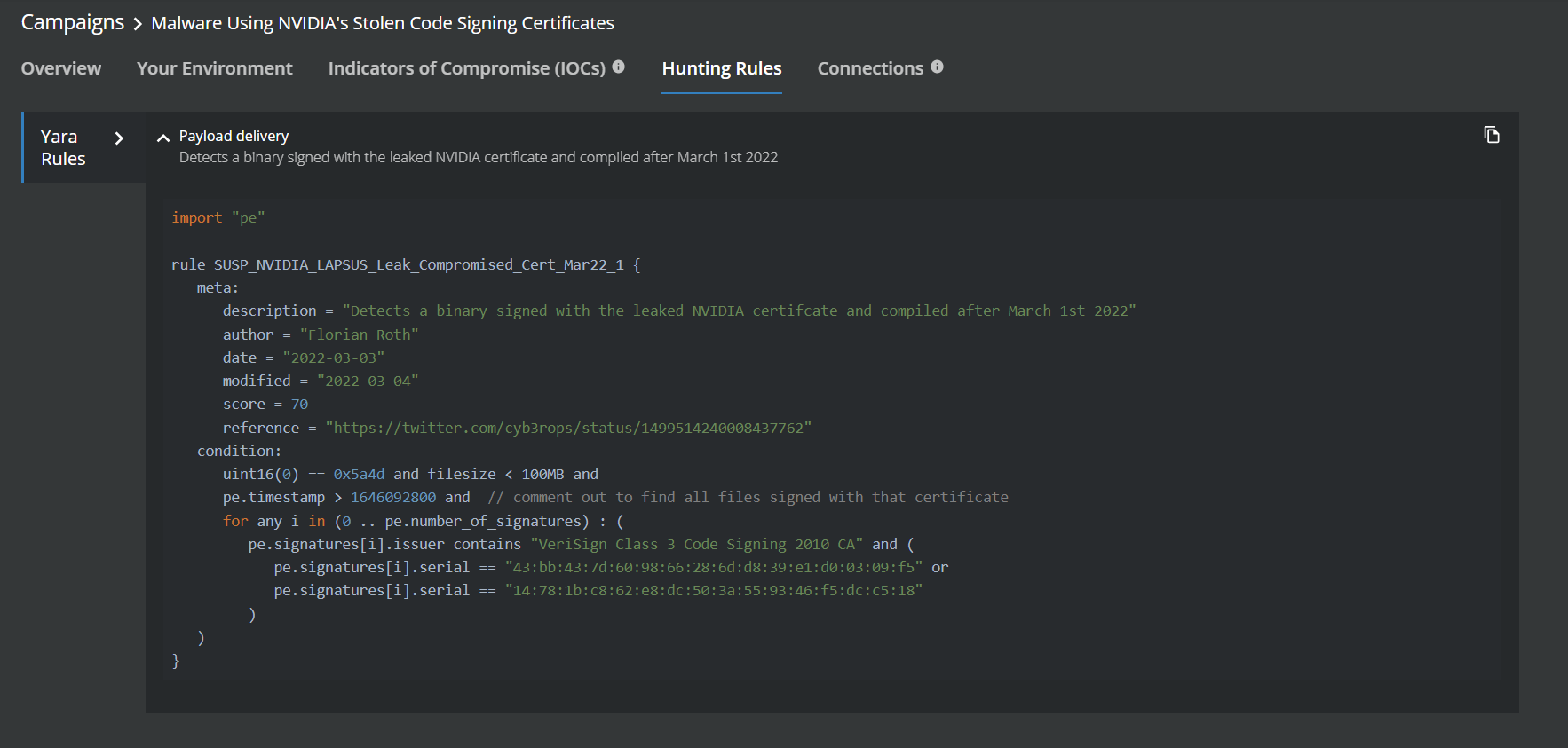
Block Remote Application Data Transfers with DLP Endpoint
Ransomware groups in recent attacks have utilized remote applications such as RDP, AnyDesk, Team Viewer, or Skype for Business to exfiltrate data out of organizations that often go undetected. The below KB article will outline the steps to create policies in the Trellix Endpoint DLP to block file transfers using remote applications to protect against data exfiltration.
How to block file transfer through remote applicationsMonitoring of Cloud Account Activity for User Anomalies
If an adversary such as LAPSUS$ can gain access to employee credentials as has been suspected in these attacks, monitoring for anomalous behavior can be necessary to stop the adversary before they are able to complete their activity. Skyhigh Security SSE (MVISION Cloud/Unified Cloud Edge) provide UEBA capabilities that can alert to abnormalities across your cloud environment looking at numerous Anomaly Categories to detect possible abnormal and malicious behavior. Additionally, adding impacted users to watchlists can help alert to suspicious activity from monitored users that might have their credentials compromised. UEBA can also alert to uncharacteristic data transfers from users that do not normally move large amounts of data.
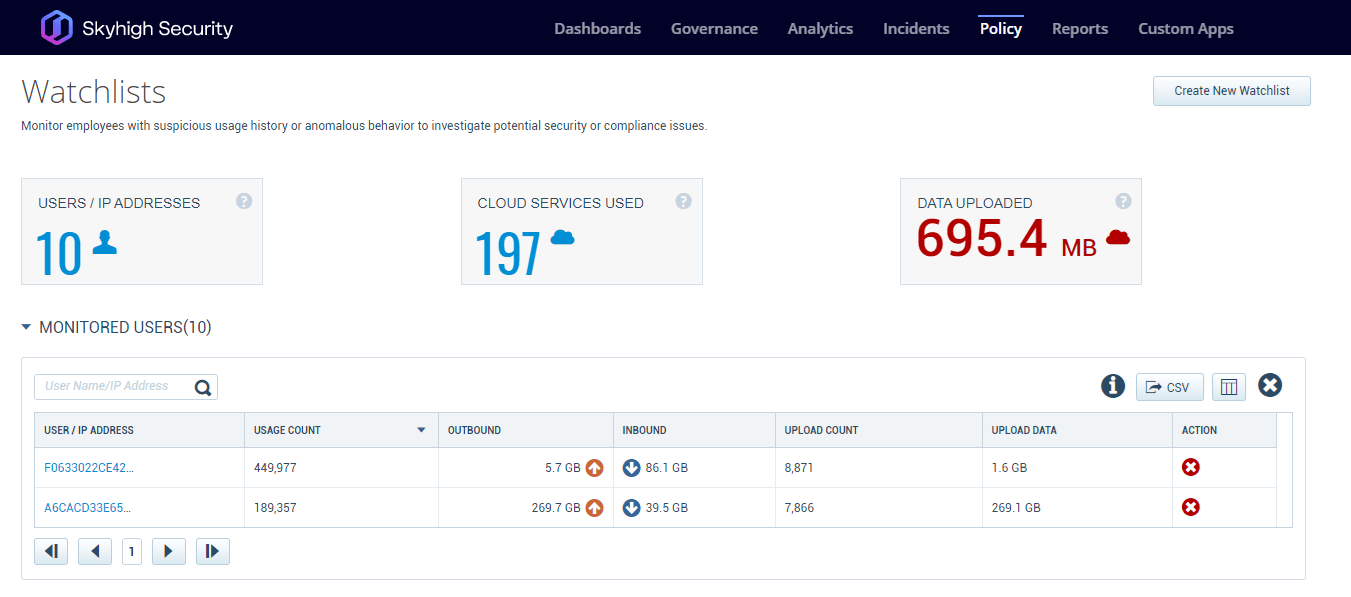
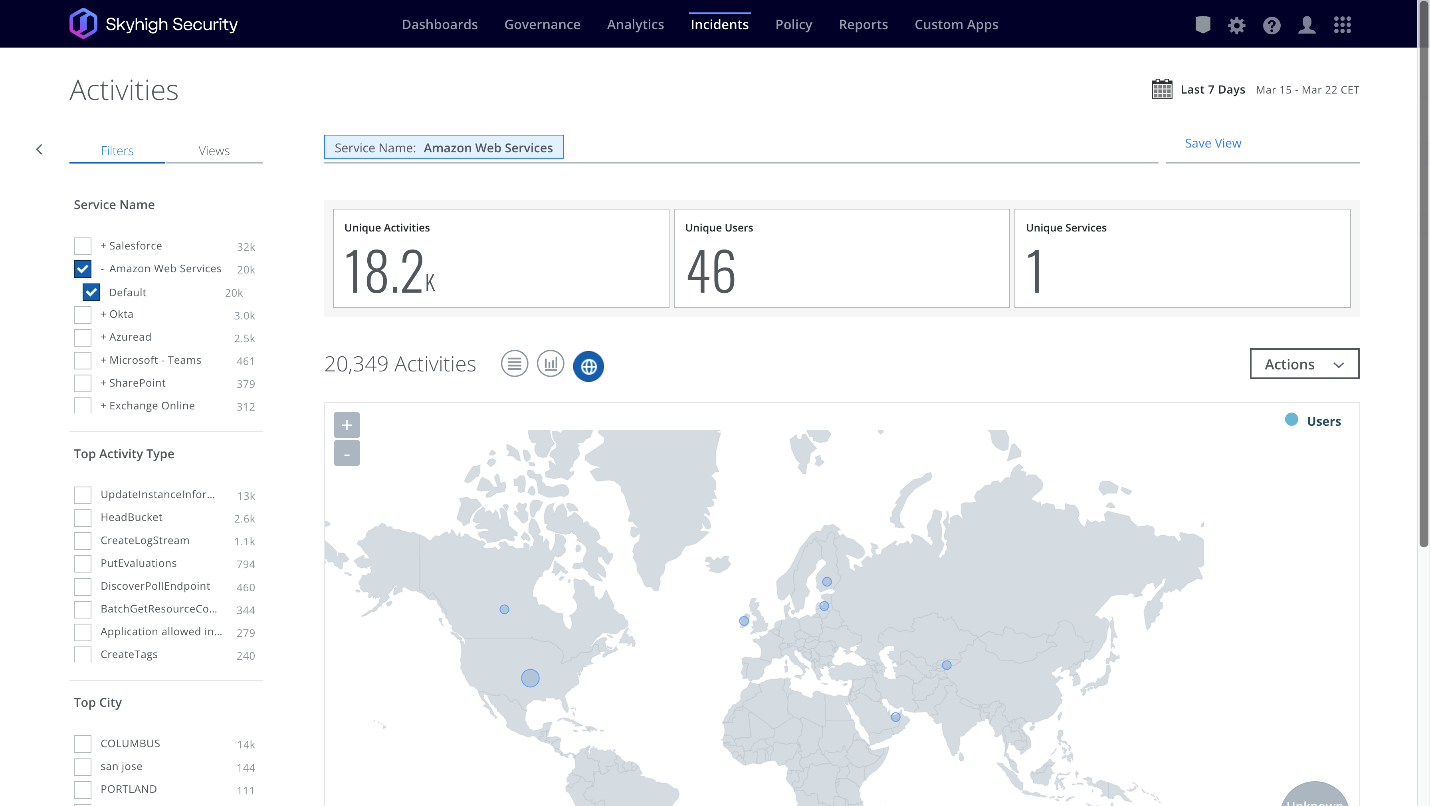
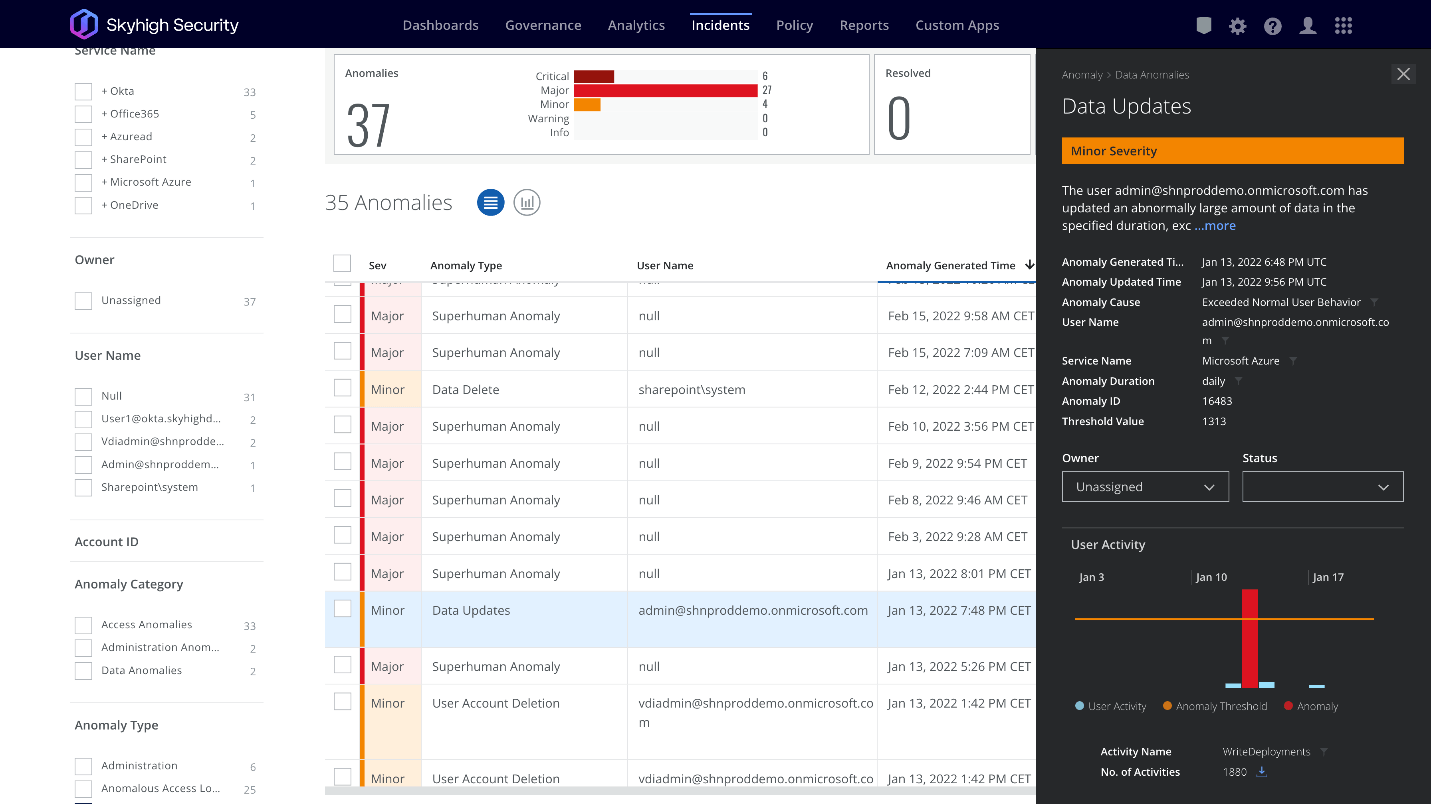
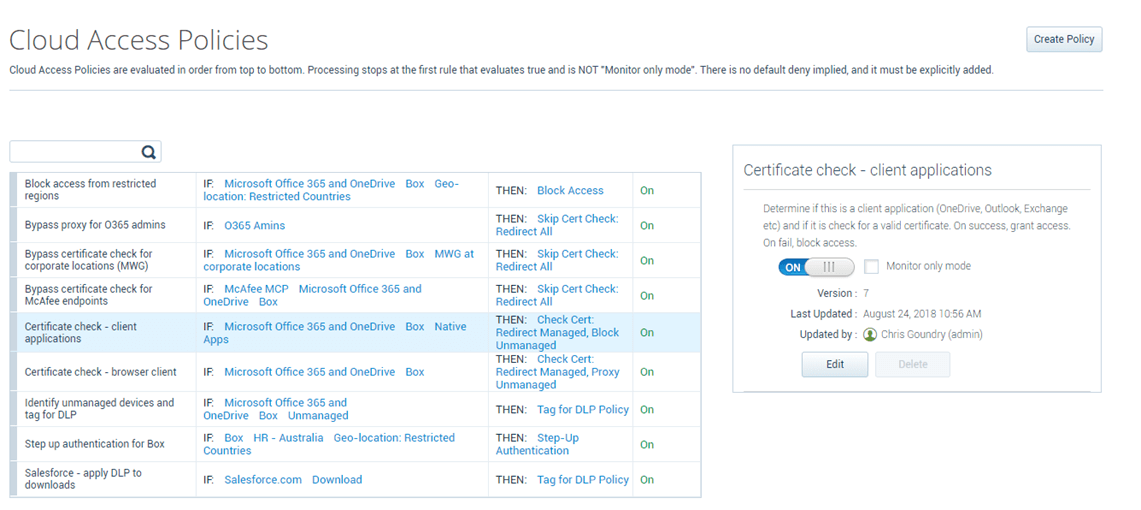
Along with tracking user anomalies, an additional protection that can be utilized is setting Cloud Access Policies to block access to your cloud applications by Unmanaged Devices or connections from Restricted Countries. Setting cloud access policies can help stop the successful reuse of stolen cloud application credentials being utilized on unmanaged company devices.
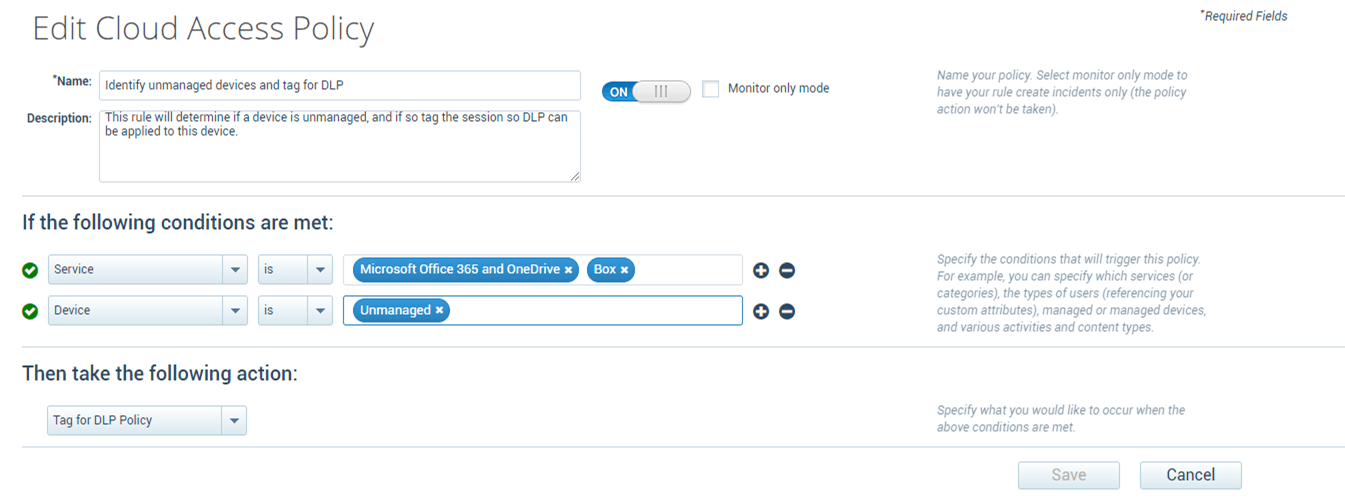
The cloud access policy protections can also apply specific data protection policies on unmanaged devices to limit the types and sensitivity of data that is allowed to be accessed and to prevent the downloading of data based on specific cloud applications.
Cloud Account IAM Activity Monitoring with Helix Sec Ops Platform
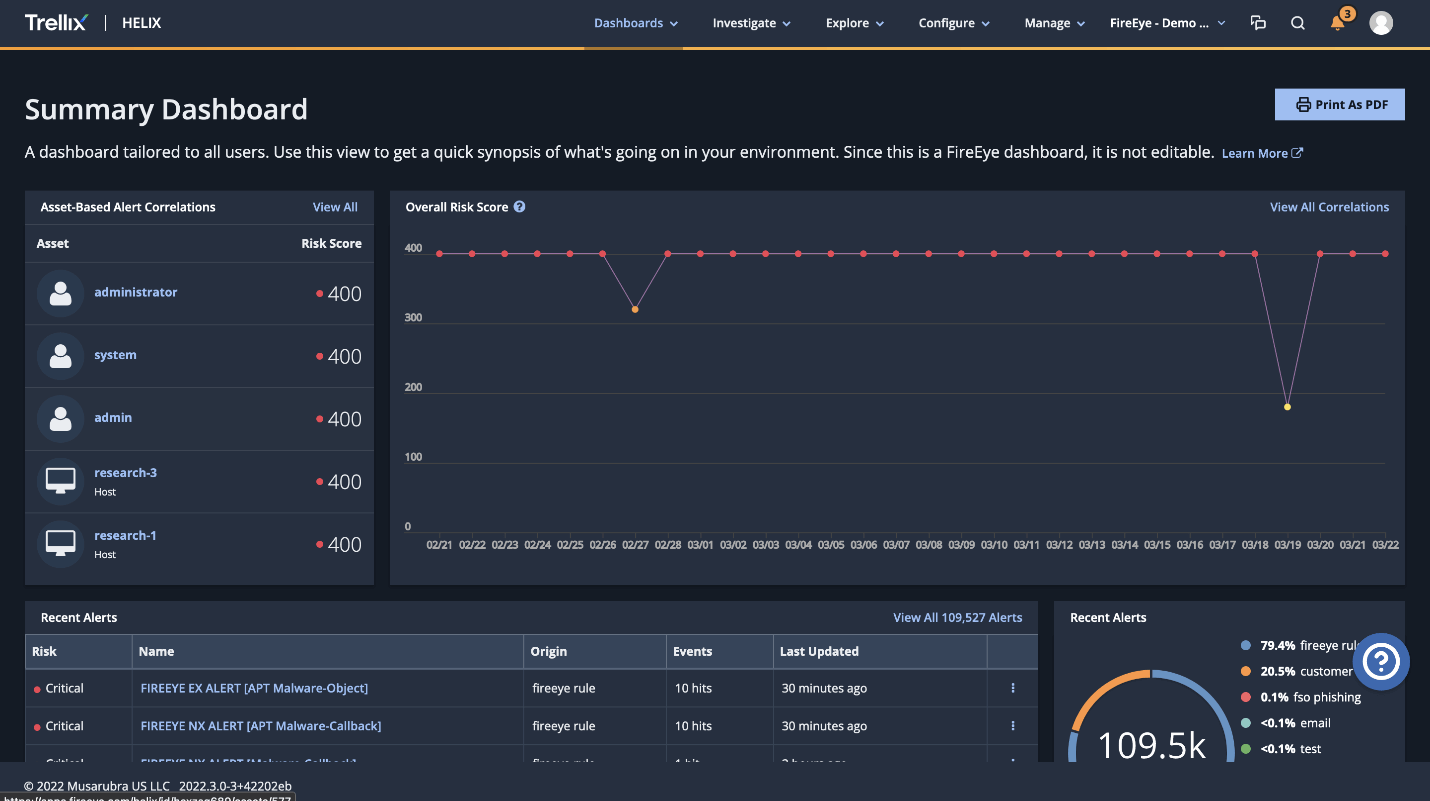
Helix supports ingestion of telemetry such as user activity from IAM providers, including Okta. Using this telemetry, Helix offers numerous OKTA-specific detection rules and analytics such as account bypass attempts, brute force attempts, administrative password changes/resets, logon failures, and more. Helix customers can find a complete list in the console by navigating to Configure → Rule Packs → FireEye Rule Packs and selecting “Vendor – Okta”. Additionally, custom rules can be created to monitor for suspicious behavior in a central dashboard.
Incident response playbooks can also be built to help investigate and contain suspicious behavior using over twenty-five pre-planned response options.
Please reach out to the Trellix team if you need assistance implementing these preventative measures.
RECENT NEWS
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
-
Oct 28, 2025
Trellix AntiMalware Engine secures I-O Data network attached storage devices
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.