Validate the efficacy of your Endpoint Security controls continuously with Breach and Attack Simulations
By Nicolas Stricher, Trellix XDR solution Architect, EMEA and Doron RosenbergTrellix Senior Sales Engineer, Israel · March 4, 2022
Efficacy of Trellix Endpoint Security
At Trellix we are proud to highlight all the great industry recognitions and awards of our Endpoint Security platform. You can simply trust them. On the other hands if you want to run your own validations, especially for your specific setup and configuration, Breach and Attack Simulations can help you run a continuous assessment of your security posture against the latest threats.
Breach and Attack Simuations
According to the Gartner® Hype Cycle™ for Security Operation 2021, Breach and Attack simulation (BAS) is a field in the Peak of Inflated and has a market penetration of 5% to 20% of the target audience.*
The two main use cases of BAS solutions are:
- Security Control Validation
- Security Posture Assessment
Essentially, your Security Operations can review the BAS reports to fine tune your security posture.
Other key use cases include:
- Security Operations processes and playbooks assessment and practice
- Evaluation of multiple vendors solutions
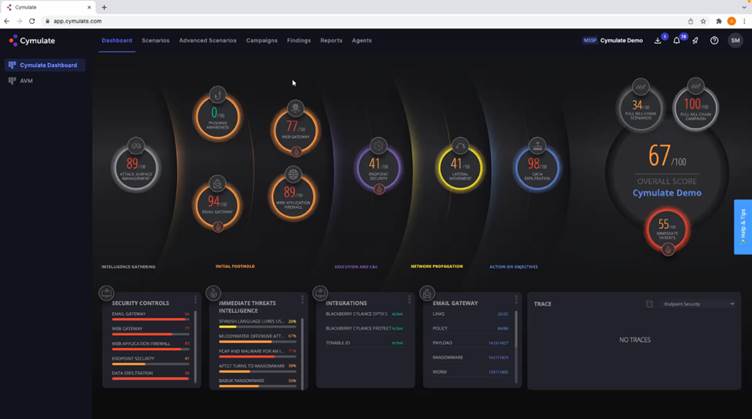
Validating the efficacy of your Trellix Endpoint Security controls continuously with Breach and Attack Simulations
In January 2022, Doron Rosenberg from Trellix, tested two configurations of McAfee ENS (Endpoint Security) 10.7, against 490 Cymulate Endpoint Security scenarios.
First, he tested a misconfigured ENS environment with some of the common misconfigurations we see from our customers such as:
- disabling GTI (Global Threat Intelligence) reputation look up
- setting ATP (Adaptive Threat Protection) or DAC (Dynamic Application Containment) to observe modes
- setting Real Protect (Machine Learning) to low
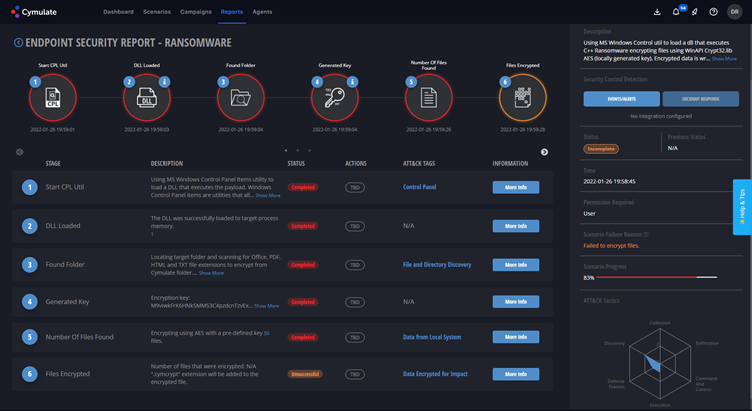
The result against this misconfigured ENS was a 17% penetration ratio, with some attacks completing almost entirely as showed in Figure 2.
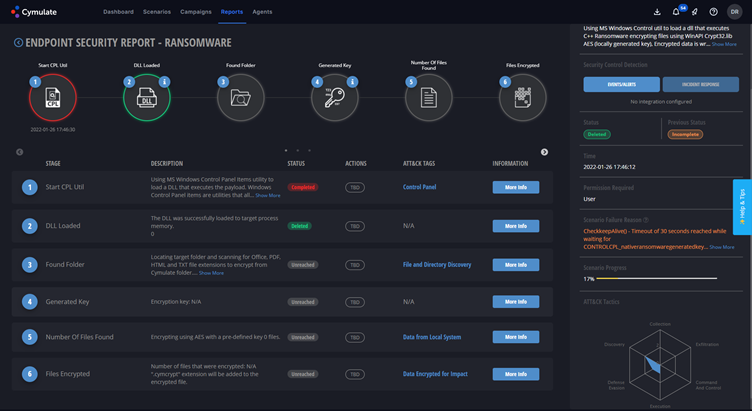
Then, Doron tested an ENS environment with the default ENS configuration. The result was a 1% penetration ratio, with many attacks stopped at early stages of the attack lifecycle, as showed below in Figure 2.
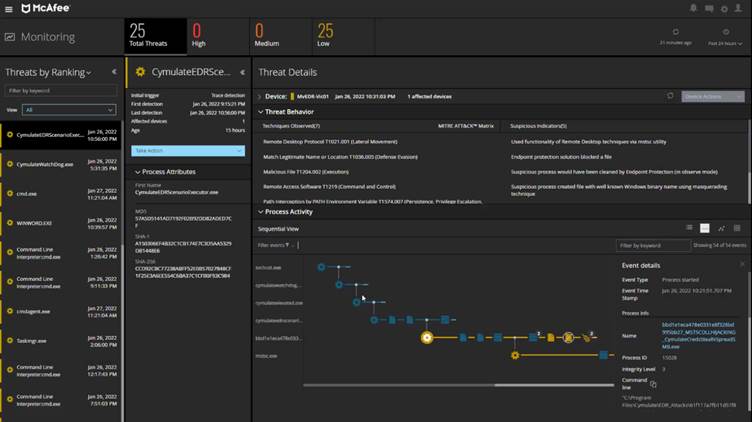
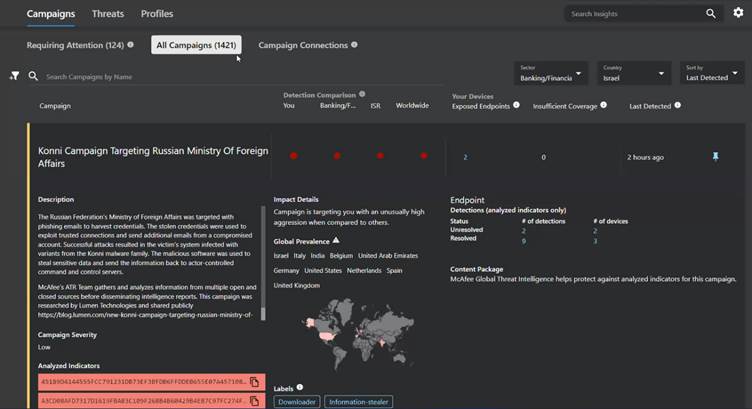
On February 7th 2022 the integration of Trellix MVISION EDR with Cymulate to has been released to validate detection as shown on Figure 6.
Summary
Cymulate uses these multi-stage simulated attacks leveraging a full range of known TTP to gain foothold on the device. The sooner an attack can be detected and stopped by Trellix Endpoint Security Platform the lower the risk of a successful breach, damage to assets, and exfiltration of critical information. Using the built-in ‘McAfee Default’ best practice policy, customers may shift left and better prevent threats before they can gain a foothold in their environment
If you want to learn more about this topic and see a live demonstration you can watch the replay of our joined EMEA Webinar on January 27, 2022.
*Gartner, “Hype Cycle for Security Operations 2021”, Pete Shoard, Shilpi Handa, 23 July 2021. GARTNER and HYPE CYCLE are a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and are used herein with permission.
RECENT NEWS
-
Mar 02, 2026
Trellix strengthens executive leadership team to accelerate cyber resilience vision
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.